previously on
Today, when using peer to create a channel, the following error was reported
2021-07-02 10:27:43.446 CST [common.deliver] Handle -> WARN 01a Error reading from 192.168.81.134:46572: rpc error: code = Canceled desc = context canceled 2021-07-02 10:27:43.447 CST [comm.grpc.server] 1 -> INFO 01b streaming call completed grpc.service=orderer.AtomicBroadcast grpc.method=Deliver grpc.peer_address=192.168.81.134:46572 error="rpc error: code = Canceled desc = context canceled" grpc.code=Canceled grpc.call_duration=6.21135ms 2021-07-02 10:27:45.623 CST [cauthdsl] deduplicate -> ERRO 01c Principal deserialization failure (MSP OrdererMSP is unknown) for identity 0 2021-07-02 10:27:45.623 CST [orderer.common.broadcast] ProcessMessage -> WARN 01d [channel: mychannel] Rejecting broadcast of config message from 192.168.81.134:46578 because of error: implicit policy evaluation failed - 0 sub-policies were satisfied, but this policy requires 1 of the 'Writers' sub-policies to be satisfied: permission denied 2021-07-02 10:27:45.623 CST [comm.grpc.server] 1 -> INFO 01e streaming call completed grpc.service=orderer.AtomicBroadcast grpc.method=Broadcast grpc.peer_address=192.168.81.134:46578 grpc.code=OK grpc.call_duration=2.682517ms
problem analysis
Search Baidu and google: (0 sub policies were satisfied, but this policy requires 1 of the 'Admins' sub policies to be)
It is said on the Internet that the following methods are not right, at least not right for me:
- 1. Solution: configtx Yaml capabilities paragraph is incorrect, refer to the official version; In fact, I think it doesn't matter whether you add it or not. Finally, the successful configtx JSON, I didn't write this paragraph either
- 2. The reason is that the channel name used when generating the genesis block through the configtxgen command is the same as the channel name used when creating the channel; I'm creating the genesis block The block file does not carry - channelID name. The command used is... / bin / configtxgen - profile configtx json -profile TwoOrgsOrdererGenesis -outputBlock ./ genesis. block; testchild is automatically selected by default
There are three reasons that should be investigated correctly
- 1. Is the LocalMSPID of the orderer in the configuration file consistent? For example, I use OrdererMSP, but in configtx The OrderersMSP is written in JSON (which is also a problem caused by the fact that it is not defined as a template)
- 2. One is that I generate genesis The configuration file is not specified during block; Use in case of error:... / bin / configtxgen - profile twoorgorderergenesis - outputblock/ genesis.block -channelID mychannel; The correct should be:... / bin / configtxgen - profile configtx json -profile TwoOrgsOrdererGenesis -outputBlock ./ genesis.block
- 3. Check configtx JSON file, because I'm a configtx generated by the web backend JSON, this configtx JSON is in the form of a configuration file. When calling asynchronously, some parameters start with @ 4. It doesn't handle asynchrony well. Before the template is replaced, it is used to generate genesis Block, of course, it will report an error
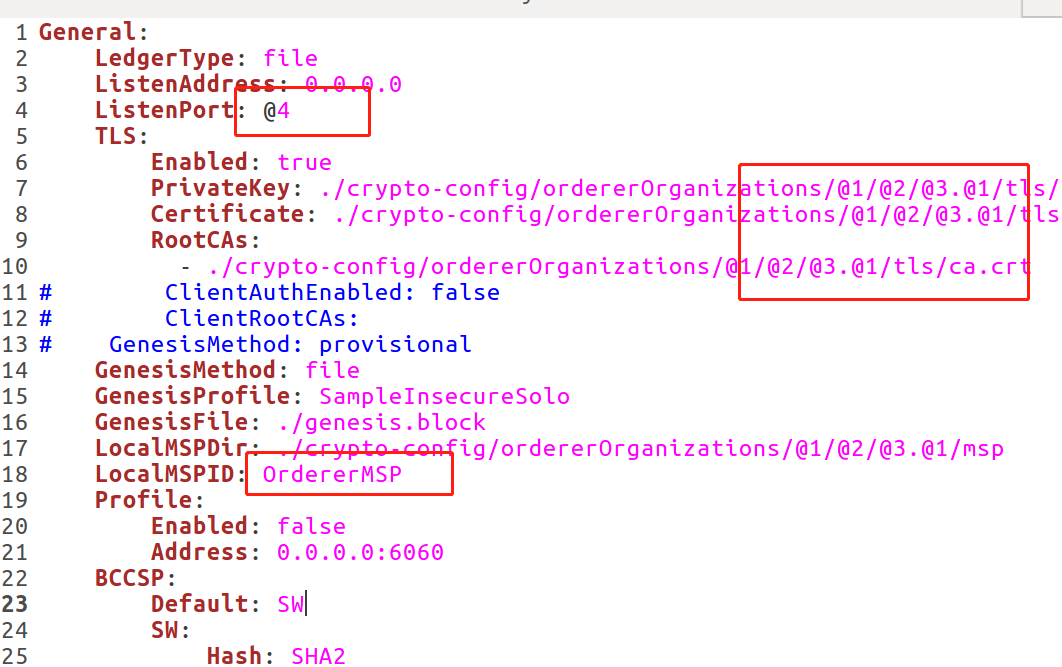
Finally, I can make complaints about what orderer has done.
ERRO 01c Principal deserialization failure (MSP OrdererMSP is unknown) for identity 0 2021-07-02 10:27:45.623 CST [orderer.common.broadcast] ProcessMessage -> WARN 01d [channel: mychannel] Rejecting broadcast of config message from 192.168.81.134:46578 because of error: implicit policy evaluation failed - 0 sub-policies were satisfied, but this policy requires 1 of the 'Writers' sub-policies to be satisfied: permission denied
This prompt is also reported for the above problem. It is also prompted when a node does not have permission.
Finally, post the configtx I finally generated json
{
"Organizations": [
{
"Name": "OrderersMSP",
"ID": "OrderersMSP",
"MSPDir": "./crypto-config/ordererOrganizations/zeng.com/msp",
"Policies": {
"Readers": {
"Type": "Signature",
"Rule": "OR('OrderersMSP.member')"
},
"Writers": {
"Type": "Signature",
"Rule": "OR('OrderersMSP.member')"
},
"Admins": {
"Type": "Signature",
"Rule": "OR('OrderersMSP.admin')"
}
}
},
{
"Name": "Org1MSP",
"ID": "Org1MSP",
"MSPDir": "./crypto-config/peerOrganizations/org1.zeng.com/msp",
"Policies": {
"Readers": {
"Type": "Signature",
"Rule": "OR('Org1MSP.admin', 'Org1MSP.peer', 'Org1MSP.client')"
},
"Writers": {
"Type": "Signature",
"Rule": "OR('Org1MSP.admin', 'Org1MSP.client')"
},
"Admins": {
"Type": "Signature",
"Rule": "OR('Org1MSP.admin')"
}
},
"AnchorPeers": []
},
{
"Name": "Org2MSP",
"ID": "Org2MSP",
"MSPDir": "./crypto-config/peerOrganizations/org2.zeng.com/msp",
"Policies": {
"Readers": {
"Type": "Signature",
"Rule": "OR('Org2MSP.admin', 'Org2MSP.peer', 'Org2MSP.client')"
},
"Writers": {
"Type": "Signature",
"Rule": "OR('Org2MSP.admin', 'Org2MSP.client')"
},
"Admins": {
"Type": "Signature",
"Rule": "OR('Org2MSP.admin')"
}
},
"AnchorPeers": []
}
],
"Orderer": {
"OrdererType": "solo",
"Addresses": [
"orderer.zeng.com:7050"
],
"BatchTimeout": "2s",
"BatchSize": {
"MaxMessageCount": 10,
"AbsoluteMaxBytes": "99 MB",
"PreferredMaxBytes": "512 KB"
},
"Organizations": null,
"Policies": {
"Readers": {
"Type": "ImplicitMeta",
"Rule": "ANY Readers"
},
"Writers": {
"Type": "ImplicitMeta",
"Rule": "ANY Writers"
},
"Admins": {
"Type": "ImplicitMeta",
"Rule": "MAJORITY Admins"
},
"BlockValidation": {
"Type": "ImplicitMeta",
"Rule": "ANY Writers"
}
}
},
"Application": {
"Organizations": null
},
"Profiles": {
"TwoOrgsOrdererGenesis": {
"Orderer": {
"OrdererType": "solo",
"Addresses": [
"orderer.zeng.com:7050"
],
"BatchTimeout": "2s",
"BatchSize": {
"MaxMessageCount": 10,
"AbsoluteMaxBytes": "99 MB",
"PreferredMaxBytes": "512 KB"
},
"Organizations": {
"Name": "OrderersMSP",
"ID": "OrderersMSP",
"MSPDir": "./crypto-config/ordererOrganizations/zeng.com/msp",
"Policies": {
"Readers": {
"Type": "Signature",
"Rule": "OR('OrderersMSP.member')"
},
"Writers": {
"Type": "Signature",
"Rule": "OR('OrderersMSP.member')"
},
"Admins": {
"Type": "Signature",
"Rule": "OR('OrderersMSP.admin')"
}
}
},
"Policies": {
"Readers": {
"Type": "ImplicitMeta",
"Rule": "ANY Readers"
},
"Writers": {
"Type": "ImplicitMeta",
"Rule": "ANY Writers"
},
"Admins": {
"Type": "ImplicitMeta",
"Rule": "MAJORITY Admins"
},
"BlockValidation": {
"Type": "ImplicitMeta",
"Rule": "ANY Writers"
}
}
},
"Consortiums": {
"SampleConsortium": {
"Organizations": [
{
"Name": "Org1MSP",
"ID": "Org1MSP",
"MSPDir": "./crypto-config/peerOrganizations/org1.zeng.com/msp",
"AnchorPeers": []
},
{
"Name": "Org2MSP",
"ID": "Org2MSP",
"MSPDir": "./crypto-config/peerOrganizations/org2.zeng.com/msp",
"AnchorPeers": []
}
]
}
}
},
"TwoOrgsChannel": {
"Consortium": "SampleConsortium",
"Application": {
"Organizations": [
{
"Name": "Org1MSP",
"ID": "Org1MSP",
"MSPDir": "./crypto-config/peerOrganizations/org1.zeng.com/msp",
"AnchorPeers": []
},
{
"Name": "Org2MSP",
"ID": "Org2MSP",
"MSPDir": "./crypto-config/peerOrganizations/org2.zeng.com/msp",
"AnchorPeers": []
}
]
}
}
}
}
Reference link
- 0 sub policies were satisfied, but this policy requires 1 of the 'Writers' sub policies to be SA
- Error: got unexpected status: FORBIDDEN — Failed to reach implicit threshold of 1 sub-policies, required 1 remaining: permission denied
- this policy requires 1 of the 'Writers' sub policies to be
- Summary of stepping on pits (VII)