1. Check whether SSH is installed: it is generally installed by default
[changairjb@localhost ~]$ rpm -qa | grep ssh libssh-0.9.5-1.oe1.aarch64 openssh-8.2p1-13.oe1.aarch64 openssh-server-8.2p1-13.oe1.aarch64 //Server libssh2-1.9.0-6.oe1.aarch64 openssh-clients-8.2p1-13.oe1.aarch64 //client
2. If not installed: enter the following command to download
$ sudo yum install openssh-clients-8.2p1-13.oe1.aarch64 //client $ sudo yum install openssh-server-8.2p1-13.oe1.aarch64 //Server
3. Install the missing package and configure SSH:
# yum install openssh*
4. Understanding SSH configuration services
Use rpm -ql to check which files are released after the SSH package is installed. We can see that the configuration file of the ssh server is in / etc / SSH / sshd_ In config, in addition, there is SSH in the same directory of the file_ Config is also about SSH configuration, but it belongs to the client configuration file.
root@localhost:/etc/ssh# rpm -ql openssh-server
/etc/ima/digest_lists.tlv/0-metadata_list-compact_tlv-openssh-server-8.2p1-9.oe1.x86_64
/etc/ima/digest_lists/0-metadata_list-compact-openssh-server-8.2p1-9.oe1.x86_64
/etc/pam.d/sshd
/etc/ssh/sshd_config
/etc/sysconfig/sshd
5. Notes to configuration file:
1 # $OpenBSD: sshd_config,v 1.103 2018/04/09 20:41:22 tj Exp $
2
3 # This is the sshd server system-wide configuration file. See
4 # sshd_config(5) for more information.
5
6 # This sshd was compiled with PATH=/usr/local/bin:/usr/bin:/usr/local/sb in:/usr/sbin
7
8 # The strategy used for options in the default sshd_config shipped with
9 # OpenSSH is to specify options with their default value where
10 # possible, but leave them commented. Uncommented options override the
11 # default value.
12
13 # If you want to change the port on a SELinux system, you have to tell
14 # SELinux about this change.
15 # semanage port -a -t ssh_port_t -p tcp #PORTNUMBER
16 #
17 #Port 22
18 #AddressFamily any
19 #ListenAddress 0.0.0.0
20 #ListenAddress ::#Disable root account login. If you log in with root user, please enable it
PermitRootLogin yes
#Do you want sshd to check the permission data of the user's home directory or related files,
#This is to worry that users may cause some problems by setting the permissions of some important files incorrectly.
#For example, the user's ~ When ssh / permission is set incorrectly, users are not allowed to log in under some special circumstances
StrictModes no
#Whether users are allowed to log in using the paired key system is only for version 2.
#The self - made public key data is placed in the user's home directory ssh/authorized_ In keys
RSAAuthentication yes
PubkeyAuthentication yes
AuthorizedKeysFile .ssh/authorized_keys
#With a certificate to log in, disable password login. Security matters
PasswordAuthentication no
17. The default listening port is port 22
18which protocol family does IPv4 and IPV6 support? any means both
19 indicates the listening address, 0.0 0.0 means that all addresses of this machine can be logged in
20 indicates all address formats of IPV6 to be monitored,:: indicates that all local addresses are supported
22 default rsa private key authentication
23 support dsa private key authentication
24 support ecdsa private key authentication
25 support ed25519 private key authentication
37 the grace time for login is 2 minutes. By default, if no password is entered, the connection will be automatically disconnected
38. Whether the administrator is allowed to log in directly. Yes means yes
39 do you want sshd to check the permission data of the user's home directory or related files? Yes means yes
40 maximum number of authentication attempts, 6 means that there are only 6 opportunities at most. It takes a long time to enter the password again after you continue to enter the wrong password
41 maximum number of sessions allowed. 10 indicates that up to 10 sessions are opened
43 public key authentication, on
When the server recognizes the public key, it will match ssh / is named authorized_keys file, and then send the public key to the client, so we need to change the file name of the public key to this name.
65 is password based authentication allowed? Yes
69 is any password authentication allowed, no
71 whether kerberos (third-party based authentication, such as LDAP) authentication is supported. The default is no
115 is DNS enabled? Yes (if it is disabled, it can be faster when connecting to the server)
113 the default authentication information is transmitted based on SFTP. If "#" is added before this text, SFTP connection is not supported
Note:
The above # beginning English line indicates that the system is implemented by default. If you want to modify it, it is recommended not to delete the original text, remove # another line and write your own configuration, and the original default will no longer take effect.
6. Modify the configuration file:
(1) After modifying the port number to 2222 in line 17, the login format is ssh 192.168.112.132 2222 (note that there is no space between IP and port number):). The command is as follows. After modifying, restart the service. Let the firewall allow it and press enter to display success (if the firewall is closed, there is no need to write these). Add a custom port to the service, and then press enter without error, but if the prompt ValueError: Port tcp/4444 already defined doesn't matter, we can try another port.
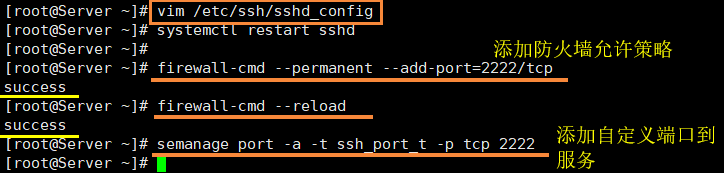
- Start ssh service:
systemctl start sshd.service
- Set boot to automatically start ssh service
systemctl enable sshd.service
7. Set up SSH service remotely
Experimental environment: a server of openEuler system and a Windows 10.0 with openEuler system virtual machine
Password based connection.
Input command ssh changairjb@10.10.1.27 - p 22, then enter the password of the server, and then successfully log in remotely. (cahngairjb is the user name of the server and the user login password of the entered password. If the port number 22 is changed, it needs to be changed to the modified port, and the default is 22 If not added) as follows:
root@localhost:~# ssh changairjb@10.10.1.27 Authorized users only. All activities may be monitored and reported. changairjb@10.10.1.27's password: Authorized users only. All activities may be monitored and reported. Activate the web console with: systemctl enable --now cockpit.socket Last login: Tue Dec 14 13:05:26 2021
--------
Realize SSH mutual trust and login free. Refer to the following link:
https://blog.csdn.net/a1766855068/article/details/86741063