this chapter is set to enter the wrong password 5 times and lock it for 15 minutes when logging in or connecting to the system remotely through ssh. This configuration can be well used to prevent the system password from being brutally cracked.
1. Environment operating system
Server 8.3 (derived from CentOS 8.3)
2. Modify the configuration file / etc / PAM D / system auth and / etc / PAM d/password-auth
Refer to 5.4 of CIS_CentOS_Linux_8_Benchmark_v1.0.1 for modification Chapter 2 Contents
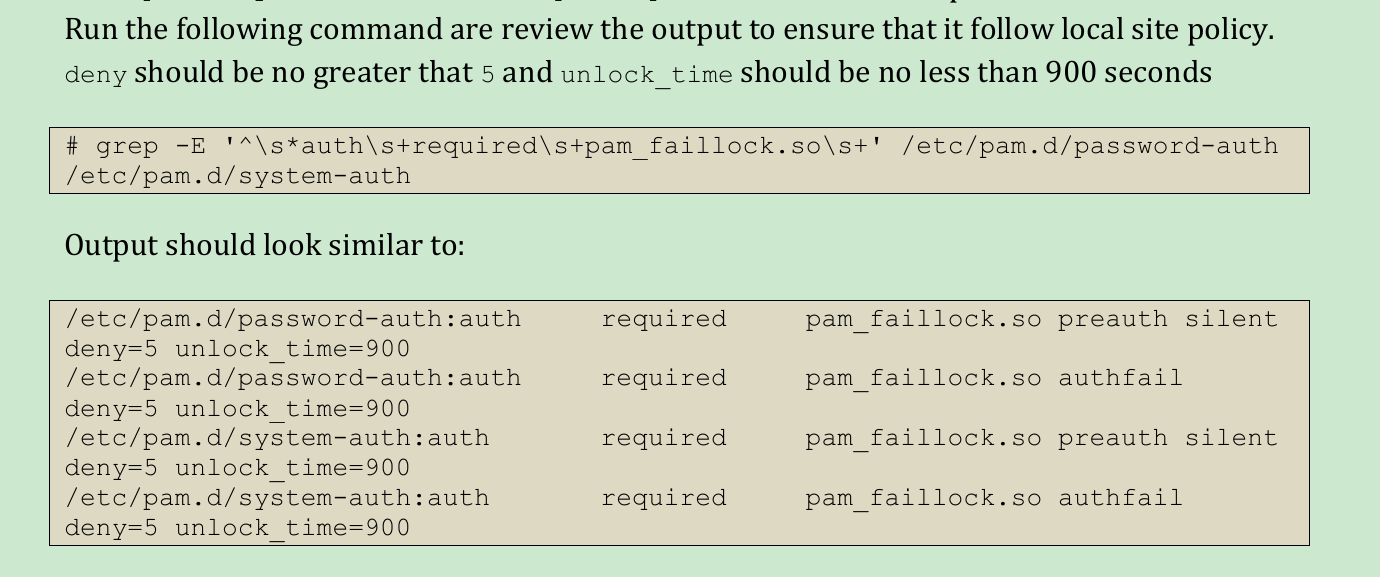
The number after deny: indicates the number of times corresponding to the wrong input. After reaching the corresponding number, the account login function will be locked; unlock_ The number after time indicates the locking time (unit: seconds). After the locking time is reached, the account login function will be unlocked.
because I want to solidify the modification into the Server 8.3 system, I need to modify the software package to implement it/ etc/pam. D / system auth and / etc / PAM D / password auth belongs to the software package authselect. Here is my modified patch
diff --git a/profiles/sssd/password-auth b/profiles/sssd/password-auth
index 3e1886f..7155a1f 100644
--- a/profiles/sssd/password-auth
+++ b/profiles/sssd/password-auth
@@ -1,4 +1,5 @@
auth required pam_env.so
+auth required pam_faillock.so preauth silent deny=5 even_deny_root unlock_time=900
auth required pam_faildelay.so delay=2000000
auth required pam_deny.so # Smartcard authentication is required {include if "with-smartcard-required"}
auth required pam_faillock.so preauth silent {include if "with-faillock"}
@@ -7,6 +8,7 @@ auth required pam_u2f.so cue nouserok
auth [default=1 ignore=ignore success=ok] pam_usertype.so isregular
auth [default=1 ignore=ignore success=ok] pam_localuser.so
auth sufficient pam_unix.so {if not "without-nullok":nullok} try_first_pass
+auth required pam_faillock.so authfail deny=5 even_deny_root unlock_time=900
auth [default=1 ignore=ignore success=ok] pam_usertype.so isregular
auth sufficient pam_sss.so forward_pass
auth required pam_faillock.so authfail {include if "with-faillock"}
@@ -20,7 +22,7 @@ account sufficient pam_usertype.so issyste
account [default=bad success=ok user_unknown=ignore] pam_sss.so
account required pam_permit.so
diff --git a/profiles/sssd/system-auth b/profiles/sssd/system-auth
index 4b4b43e..95b8fff 100644
--- a/profiles/sssd/system-auth
+++ b/profiles/sssd/system-auth
@@ -1,5 +1,6 @@
{imply "with-smartcard" if "with-smartcard-required"}
auth required pam_env.so
+auth required pam_faillock.so preauth silent deny=5 even_deny_root unlock_time=900
auth required pam_faildelay.so delay=2000000
auth required pam_faillock.so preauth silent {include if "with-faillock"}
auth [success=1 default=ignore] pam_succeed_if.so service notin login:gdm:xdm:kdm:xscreensaver:gnome-screensaver:kscreensaver quiet use_uid {include if "with-smartcard-required"}
@@ -12,6 +13,7 @@ auth [default=1 ignore=ignore success=ok] pam_localuser.so
auth [default=2 ignore=ignore success=ok] pam_localuser.so {include if "with-smartcard"}
auth [success=done authinfo_unavail=ignore ignore=ignore default=die] pam_sss.so try_cert_auth {include if "with-smartcard"}
auth sufficient pam_unix.so {if not "without-nullok":nullok} try_first_pass
+auth required pam_faillock.so authfail deny=5 even_deny_root unlock_time=900
auth [default=1 ignore=ignore success=ok] pam_usertype.so isregular
auth sufficient pam_sss.so forward_pass
auth required pam_faillock.so authfail {include if "with-faillock"}
@@ -25,7 +27,7 @@ account sufficient pam_usertype.so issyste
account [default=bad success=ok user_unknown=ignore] pam_sss.so
account required pam_permit.so
As for why the content in the sssd / directory is modified, you can see one or two through the authselect command.
It should be noted that 1) after modifying the source package and compiling, you can't see the modifications directly after installation! After I retype iso, I can see the changes. 2) Only account login is restricted here, and switching from other users via su command will not be affected
3 interface provided by the system - faillock
since you want to judge the number of user input errors, there must be a place in the system to record the number of current input errors. This data is recorded in / var/run/faillock by default.
3.1 faillock
Linux system provides a tool for viewing and modifying authentication failure record files - faillock.
NAME
faillock - Tool for displaying and modifying the authentication failure record files
SYNOPSIS
faillock [--dir /path/to/tally-directory] [--user username] [--reset]
3.1. 1. Continuously input the wrong password for 5 times, and record the authentication failure in the system
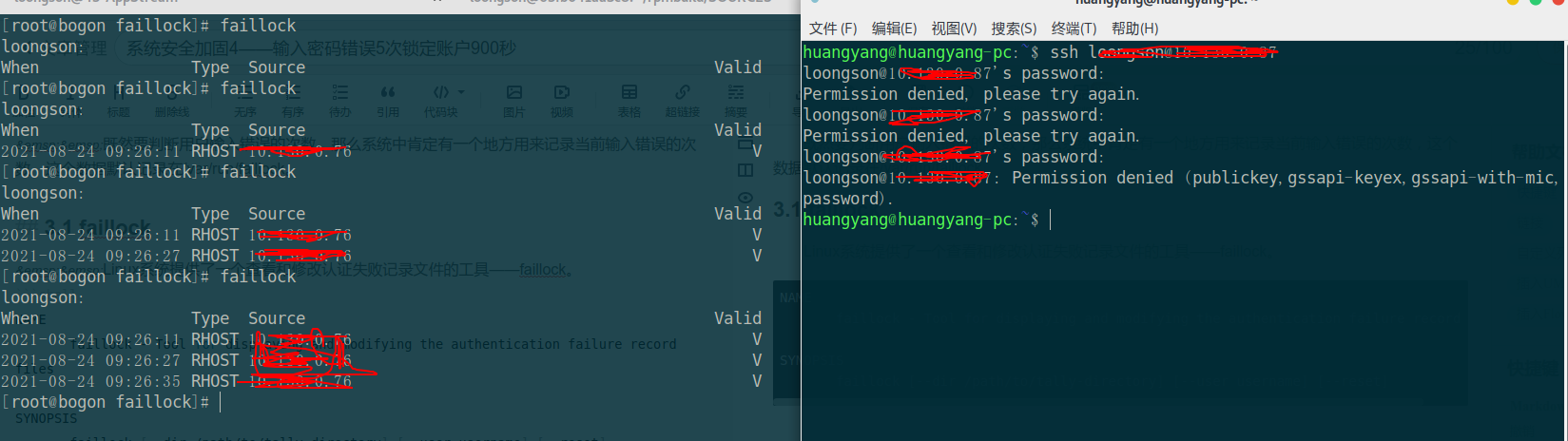
at the beginning, execute the faillock command. Because you log in to the system correctly, there is no content here. I connect to the host through ssh from another terminal and deliberately input the wrong password once. Before that, the terminal executes faillock to view the authentication failure record data in the system. The figure above records the wrong password three times.
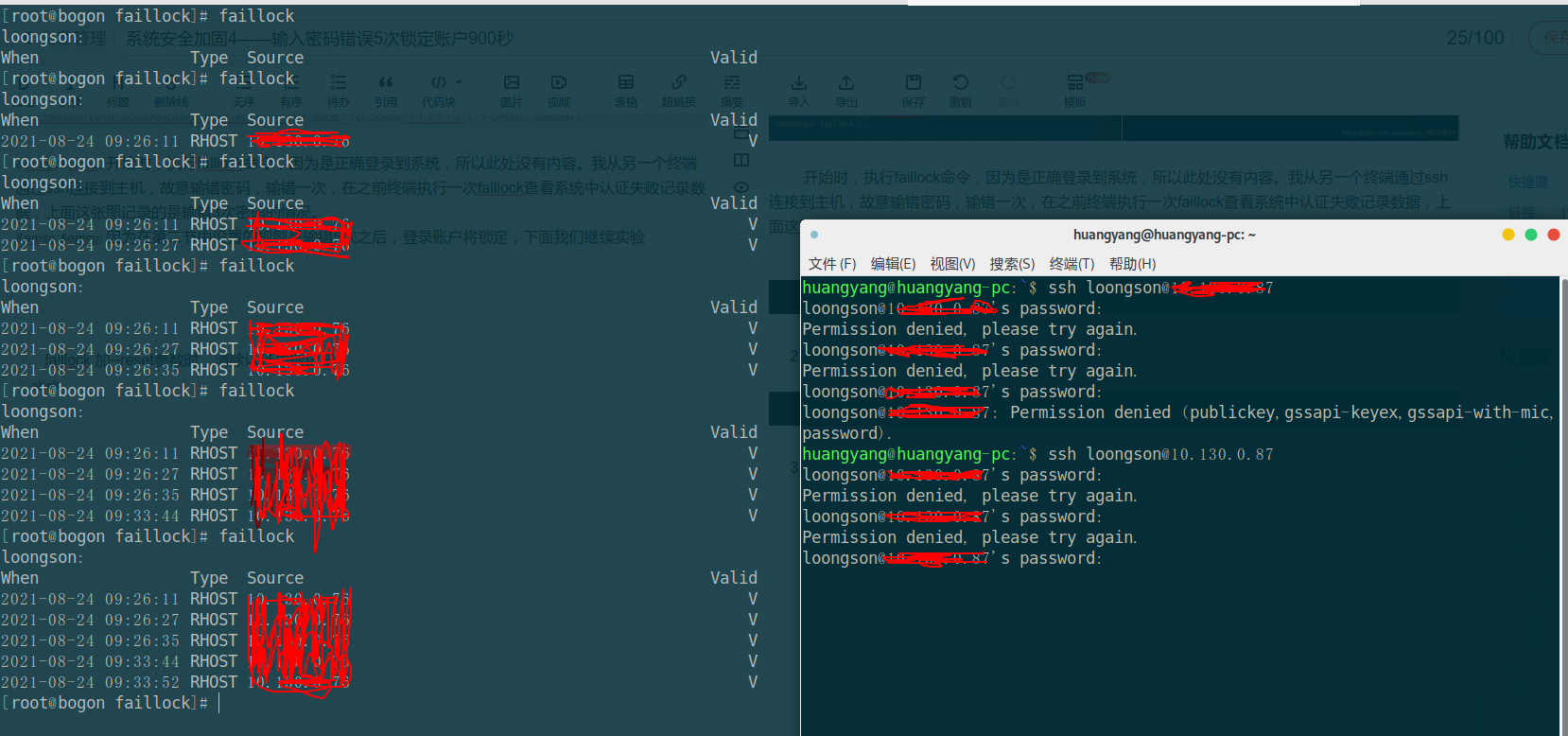
because the rule set in Section 2 is that the login account will be locked after 5 wrong entries. Let's continue the experiment. This figure shows the case of 5 wrong entries. At this time, the account login has been locked, and entering the correct password cannot log in to the system.
3.1. 2 after 15 minutes of locking time, enter the correct password and record the authentication failure in the system
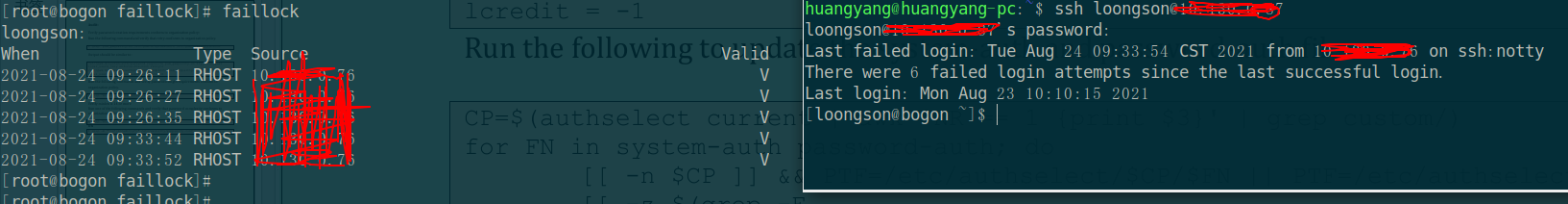
after the locking time, enter the correct password to log in to the system and check that the login failure record has not changed. At this time, exit the system, verify the wrong password again, and then view the faillock information as follows:
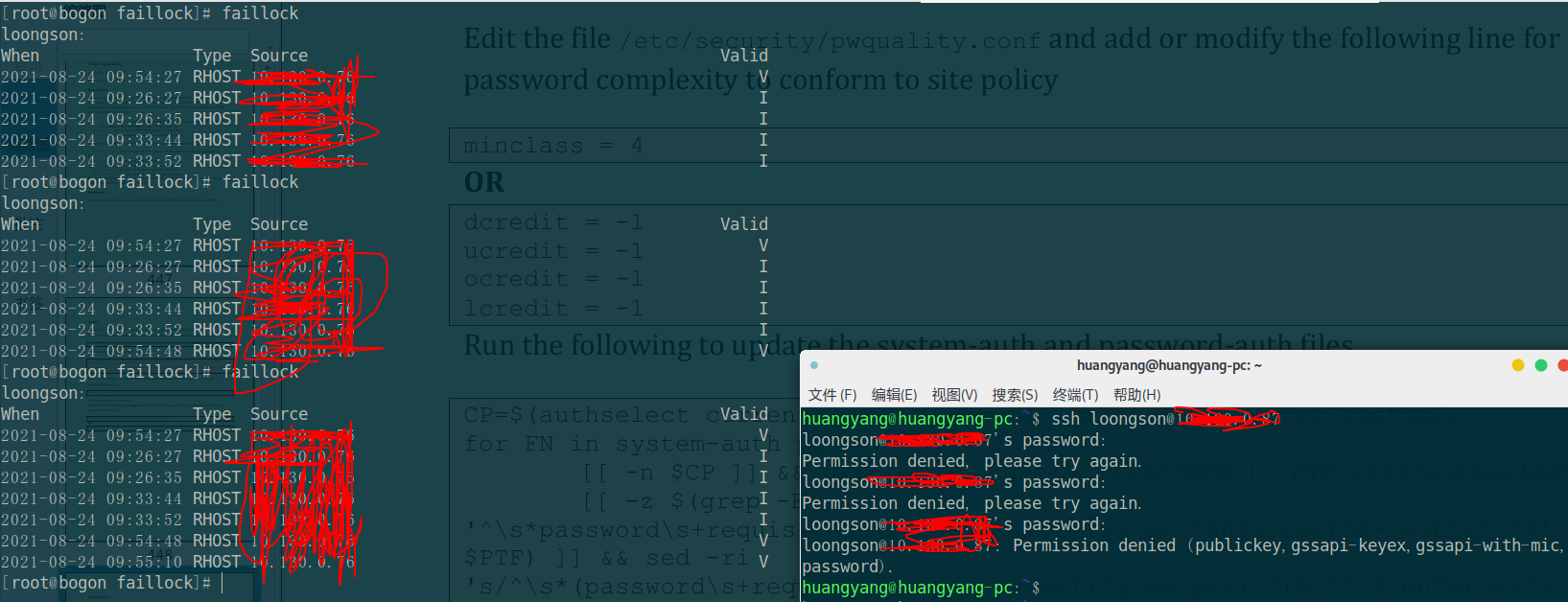
in addition to the validity indicated by "V", the invalid column indicated by "I" in the record file is invalid. It may not be clear if you just read the article here. If you verify it yourself, you will understand!
3.1. 3. Execute faillock to clear the authentication failure record in the system
[root@bogon faillock]# faillock loongson: When Type Source Valid 2021-08-24 09:54:27 RHOST x.x.x.x V 2021-08-24 09:26:27 RHOST x.x.x.x I 2021-08-24 09:26:35 RHOST x.x.x.x I 2021-08-24 09:33:44 RHOST x.x.x.x I 2021-08-24 09:33:52 RHOST x.x.x.x I 2021-08-24 09:54:48 RHOST x.x.x.x V 2021-08-24 09:55:10 RHOST x.x.x.x V [root@bogon faillock]# faillock --reset [root@bogon faillock]# faillock loongson: When Type Source Valid [root@bogon faillock]#
3.1. 4. Input the wrong password for 4 times, and record the authentication failure in the system
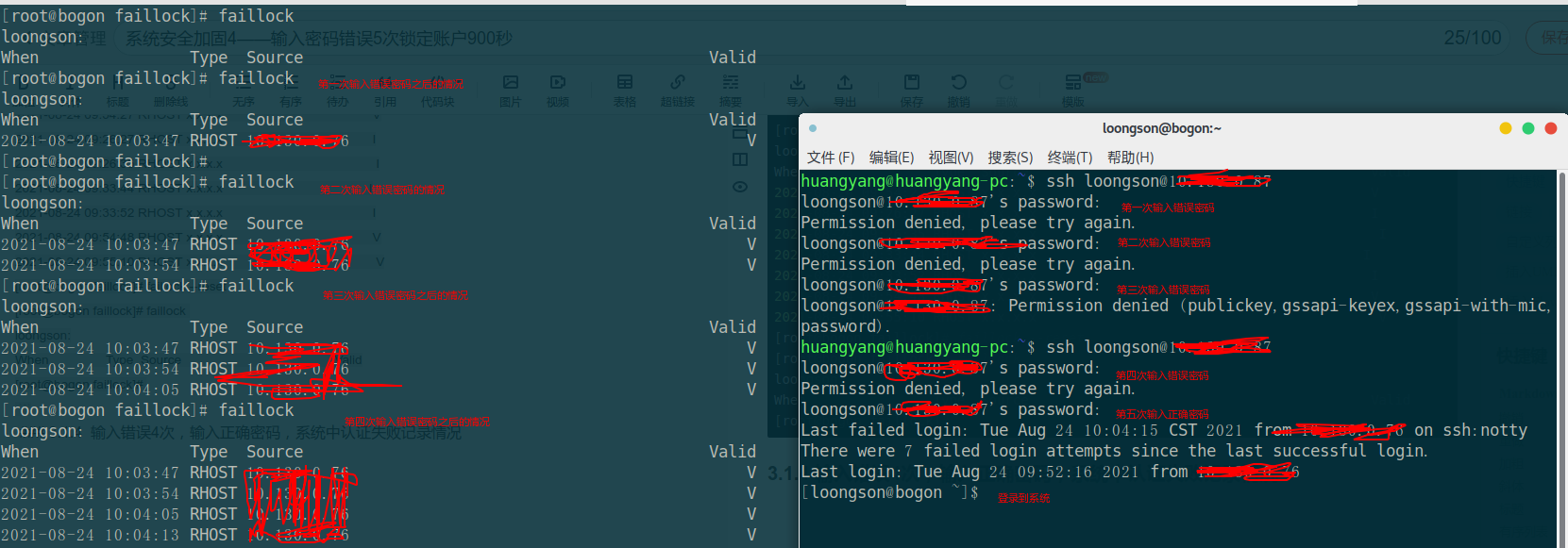
what I want to verify in this chapter is that after entering the wrong password four times, enter the correct password once to log in to the system. Whether the authentication failure record of the system will be cleared 0 and the counting will be restarted. Now I log out, enter the wrong password twice, and then enter the correct password to verify whether I can log in to the system
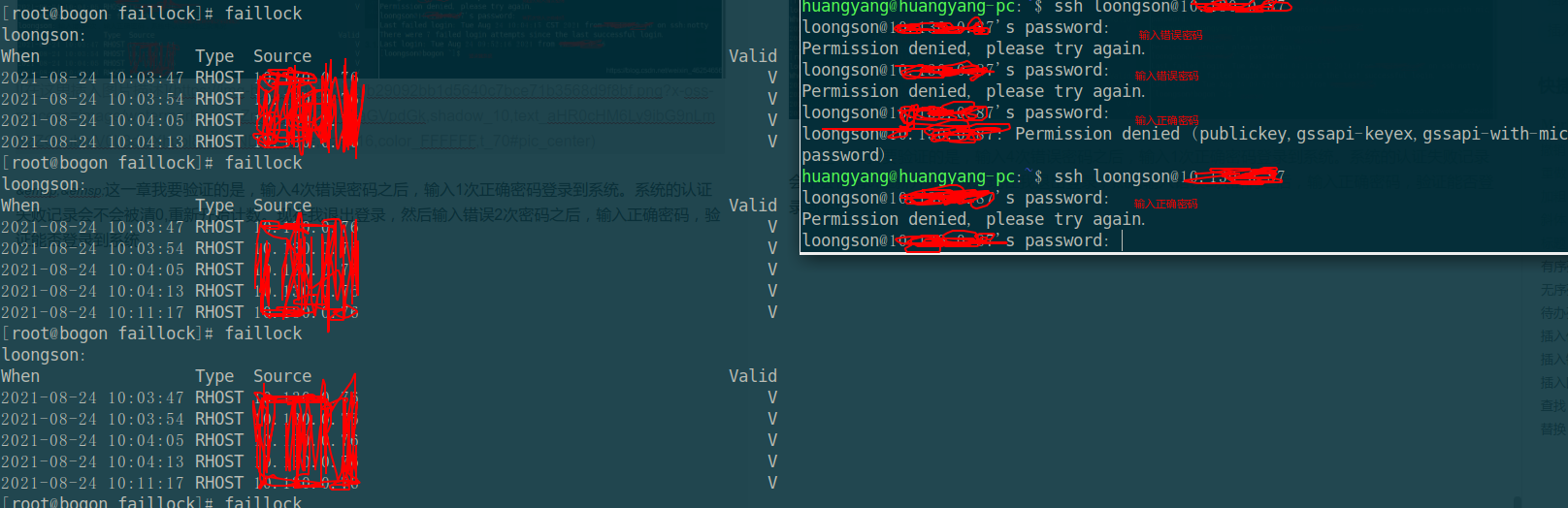
conclusion: after 4 login errors, entering the correct password to log in to the system does not clear the number of login failures to 0! (it should be noted that the premise of this conclusion is the result of configuration according to the configuration file in Chapter 2)