1, Keepalived overview and installation
(1) Introduction to Keepalived
Keepalived is a health examination tool specially designed for LVS+HA
It supports the following functions:
(1) Support automatic Failover
(2) Support node Health Checking
Official website: http://www.keepalived.org/
logo:

(2) Hot standby mode of Keepalived
1.VRRP (Virtual Router Redundancy Protocol)
Example diagram:
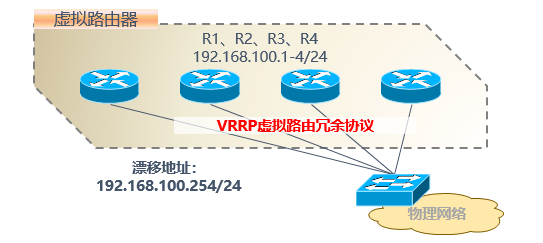
2. One active + multiple standby share the same ip address, but the priority is different
Note: if multiple standby servers need to be used, the state should be set to backup, but their priorities should not be the same
Example diagram:
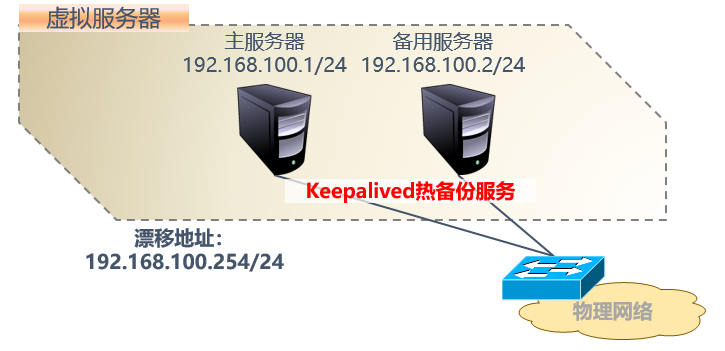
(3) Installation of Keepalived
Experimental environment:
| Server name | IP address | Play a role |
|---|---|---|
| keepalived-1 | 192.168.100.1 | master server |
| keepalived-2 | 192.168.100.2 | Standby server |
Drift address: 192.168 one hundred point two five four
The application services provided are: Web
This experiment uses Centos7 operating system
Master server configuration
******(1)Basic configuration first
[root@centos7-007 ~]# hostnamectl set-hostname keepalived-1
[root@centos7-007 ~]# su
[root@keepalived-1 ~]# systemctl stop firewalld
[root@keepalived-1 ~]# setenforce 0
setenforce: SELinux is disabled
[root@keepalived-1 ~]# mount /dev/cdrom /media/cdrom/
mount: /dev/sr0 Write protected, will mount as read-only
******(2)use yum Install the necessary components
[root@keepalived-1 ~]# yum -y install keepalived ipvsadm httpd
. . . . . .
complete!
******(2)to write web Pages, settings keepalived Is self starting
[root@keepalived-1 ~]# echo "1111111111" > /var/www/html/index.html
[root@keepalived-1 ~]# systemctl enable keepalived
Created symlink from /etc/systemd/system/multi-user.target.wants/keepalived.service to /usr/lib/systemd/system/keepalived.service.
******(3)to configure keepalived Configuration file (back up before doing it to form a habit)
[root@keepalived-1 ~]# mv /etc/keepalived/keepalived.conf /etc/keepalived/keepalived.conf.bak
[root@keepalived-1 ~]# vim /etc/keepalived/keepalived.conf (write a new configuration file)
write in:
global_defs {
router_id A1
}
vrrp_instance VI_1 {
state MASTER
interface ens33
virtual_router_id 1
priority 100
advert_int 1
authentication {
auth_type PASS
auth_pass 123456
}
virtual_ipaddress {
192.168.100.254
}
}
Save exit
-------------------Gorgeous split line——————————————————————————————————————
Profile item resolution:
router_id A1 ##The name of this server (this name is optional)
vrrp_instance VI_1 { ##Define VRRP hot spare instance
state MASTER ##MASTER indicates the primary server, and BACKUP is filled in for the BACKUP server
interface ens33 ##Physical interface hosting VIP address
virtual_router_id 1 ##The ID number of the virtual router. The ID number of the primary server should be consistent with that of the backup server
priority 100 ##Priority. The higher the value, the higher the priority. The priority of the backup server is lower than that of the primary server
advert_int 1 ##Notification interval seconds (heartbeat rate)
authentication { ##Authentication information
auth_type PASS ##Certification Type
auth_pass 123456 ##Password string
}
virtual_ipaddress {
192.168.200.254 ##Specify the drift address (VIP), and the primary server should be consistent with the backup server
------------------------------------------—
******(4)start-up keepalived and httpd
[root@keepalived-1 ~]# systemctl start keepalived
[root@keepalived-1 ~]# systemctl start httpd
[root@keepalived-1 ~]# curl 127.0.0.1 (test whether it starts normally)
11111
******(5)use ip a Command view vip Is it on the primary server
[root@keepalived-1 ~]# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:0c:29:44:ad:db brd ff:ff:ff:ff:ff:ff
inet 192.168.100.1/24 brd 192.168.100.255 scope global noprefixroute ens33
valid_lft forever preferred_lft forever
inet 192.168.100.254/32 scope global ens33 (find vip (on primary server)
valid_lft forever preferred_lft forever
inet6 fe80::7762:f351:dbfc:cb0e/64 scope link noprefixroute
valid_lft forever preferred_lft forever
Backup server configuration
******Same as primary server configuration
[root@centos7-008 ~]# hostnamectl set-hostname keepalived-2
[root@centos7-008 ~]# su
[root@keepalived-2 ~]# systemctl stop firewalld
[root@keepalived-2 ~]# setenforce 0
setenforce: SELinux is disabled
[root@keepalived-2 ~]# mount /dev/cdrom /media/cdrom/
mount: /dev/sr0 Write protected, will mount as read-only
[root@keepalived-2 ~]# yum -y install keepalived ipvsadm httpd
. . . . . .
complete!
[root@keepalived-2 ~]# echo "22222222222" > /var/www/html/index.html
[root@keepalived-2 ~]# systemctl enable keepalived
Created symlink from /etc/systemd/system/multi-user.target.wants/keepalived.service to /usr/lib/systemd/system/keepalived.service.
[root@keepalived-2 ~]# mv /etc/keepalived/keepalived.conf /etc/keepalived/keepalived.conf.bak
[root@keepalived-2 ~]# vim /etc/keepalived/keepalived.conf
write in:
gglobal_defs {
router_id A2
}
vrrp_instance VI_1 {
state BACKUP
interface ens33
virtual_router_id 1
priority 99
advert_int 1
authentication {
auth_type PASS
auth_pass 123456
}
virtual_ipaddress {
192.168.100.254
}
}
Save exit
[root@keepalived-2 ~]# systemctl start keepalived
[root@keepalived-2 ~]# systemctl start httpd
[root@keepalived-2 ~]# curl 127.0.0.1
22222
[root@keepalived-2 ~]# ip a (check the address, because it is a backup server, so vip is not on this server)
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:0c:29:bc:67:07 brd ff:ff:ff:ff:ff:ff
inet 192.168.100.2/24 brd 192.168.100.255 scope global noprefixroute ens33
valid_lft forever preferred_lft forever
inet6 fe80::2ff4:55fa:6c3d:65e0/64 scope link noprefixroute
valid_lft forever preferred_lft forever
verification
Open a testing machine and visit 192.168 100.254(vip)
It is found that the access is to the master server. At this time, ifdown the network card of the master server, and then access it again (if the network card is turned off without switching, turn off the master server)
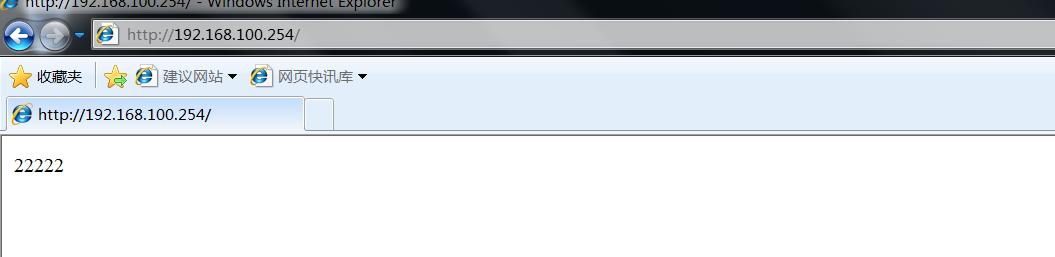
Turn on the master server network card, and then use the test machine to Ping the VIP. In the process, turn off the master server network card again to see how long it takes to restore communication
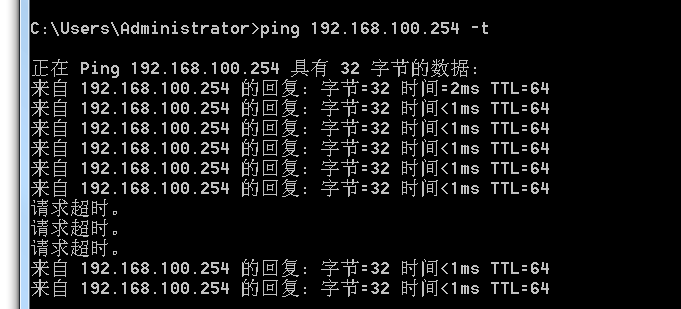
So far, the Keepalived deployment is completed!!
2, Build a highly available load balancing cluster with kept + LVS
Experimental environment
| Server name | ip address | Play a role |
|---|---|---|
| master | 192.168.100.1 | Main regulator |
| backup | 192.168.100.2 | Standby scheduler |
| web1 | 192.168.100.3 | Node server |
| web2 | 192.168.100.4 | Node server |
Drift address: 192.168 one hundred point two five four
The following experiments are carried out on the basis of the above experiments
Main regulator configuration
******(1)Basic configuration
[root@Centos7 ~]# hostnamectl set-hostname master
[root@Centos7 ~]# su
[root@master ~]# systemctl stop httpd
[root@master ~]# yum -y remove httpd (remove httpd because the previous installation was for testing only)
******(2)modify keepalived Configuration file for
[root@master ~]# vim /etc/keepalived/keepalived.conf (modify the main configuration file to)
global_defs {
router_id A1
}
vrrp_instance VI_1 {
state MASTER
interface ens32
virtual_router_id 1
priority 100
advert_int 1
authentication {
auth_type PASS
auth_pass 123456
}
virtual_ipaddress {
192.168.100.254
}
}
virtual_server 192.168.100.254 80 {
delay_loop 15
lb_algo rr
lb_kind DR
protocol TCP
real_server 192.168.100.3 80 {
weight 1
TCP_CHECK {
connect_port 80
connect_timeout 3
nb_get_retry 3
delay_before_retry 4
}
}
real_server 192.168.100.4 80 {
weight 1
TCP_CHECK {
connect_port 80
connect_timeout 3
nb_get_retry 3
delay_before_retry 4
}
}
}
Save exit
------------------—Gorgeous split line -——————————————————————————————————————
Details of new configuration items:
virtual_server 192.168.100.254 80 {#Fill in the vip address and port number here
delay_loop 15 #Health check interval seconds
lb_algo rr #Scheduling algorithm, here is polling. For more information, please click the hyperlink at the beginning of the article
lb_kind DR #Cluster working mode, here is DR mode. For more information, please click the hyperlink at the beginning of the article
! persistence_timeout 50 #Connection hold time
protocol TCP #Protocol adopted by application service
real_server 192.168.100.3 80 { #Fill in the address and port of the node server here. Multiple nodes can be written, and each node can be written in this way
weight 1 #weight
TCP_CHECK { #Health examination method
connect_port 80 #Target port
connect_timeout 3 #connection timed out
nb_get_retry 3 #retry count
delay_before_retry 3 #retry interval
}
} #Be sure to pay attention to {} integrity
------------------------------------------—
******(3)Load the service module of the system kernel, etc
[root@master ~]# modprobe ip_vs (load module)
[root@master ~]# lsmod | grep ip_vs (view module status)
ip_vs 141092 0
nf_conntrack 133387 1 ip_vs
libcrc32c 12644 3 xfs,ip_vs,nf_conntrack
[root@master ~]# echo "modprobe ip_vs" >> /etc/rc. Local (add the service item that the module starts for startup)
[root@master ~]# Systemctl restart kept
Backup scheduler configuration
It is basically consistent with the configuration of the main regulator
[root@Centos7 ~]# hostnamectl set-hostname backup
[root@Centos7 ~]# su
[root@backup ~]# systemctl stop httpd
[root@backup ~]# yum -y remove httpd
[root@backup ~]# vim /etc/keepalived/keepalived.conf
Modification:
global_defs {
router_id A2
}
vrrp_instance VI_1 {
state BACKUP
interface ens32
virtual_router_id 1
priority 99
advert_int 1
authentication {
auth_type PASS
auth_pass 123456
}
virtual_ipaddress {
192.168.100.254
}
}
virtual_server 192.168.100.254 80 {
delay_loop 15
lb_algo rr
lb_kind DR
protocol TCP
real_server 192.168.100.3 80 {
weight 1
TCP_CHECK {
connect_port 80
connect_timeout 3
nb_get_retry 3
delay_before_retry 4
}
}
real_server 192.168.100.4 80 {
weight 1
TCP_CHECK {
connect_port 80
connect_timeout 3
nb_get_retry 3
delay_before_retry 4
}
}
}
Save exit
[root@backup ~]# modprobe ip_vs
[root@backup ~]# lsmod | grep ip_vs
ip_vs 141092 0
nf_conntrack 133387 1 ip_vs
libcrc32c 12644 3 xfs,ip_vs,nf_conntrack
[root@backup ~]# echo "modprobe ip_vs" >> /etc/rc.local
[root@backup ~]# systemctl restart keepalived
web1 node server configuration
******(1)Make basic configuration first and use yum install httpd And writing web page
[root@Centos7 ~]# hostnamectl set-hostname web1
[root@Centos7 ~]# su
[root@web1 ~]# mount /dev/cdrom /mnt/
mount: /dev/sr0 Write protected, will mount as read-only
mount: /dev/sr0 Already mounted or /mnt busy
/dev/sr0 Already mounted to /mnt upper
[root@web1 ~]# yum -y install httpd
. . . . . .
complete!
[root@web1 ~]# echo "1111111111" > /var/www/html/index.html
******(2)Write network card configuration
[root@web1 ~]# cd /etc/sysconfig/network-scripts/
[root@web1 network-scripts]# cp ifcfg-lo ifcfg-lo:0
write in:
DEVICE=lo:0
IPADDR=192.168.100.254
NETMASK=255.255.255.255
ONBOOT=yes
Save exit
[root@web1 network-scripts]# systemctl restart network
[root@web1 network-scripts]# ip a (check whether the addition is successful)
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet 192.168.100.254/32 brd 192.168.100.254 scope global lo:0
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
. . . . . .
[root@web1 network-scripts]# cd
******(3)Add route, next hop is vip address
[root@web1 ~]# echo "route add -host 192.168.100.254 dev lo:0" >> /etc/rc.local
[root@web1 ~]# route add -host 192.168.100.254 dev lo:0
[root@web1 ~]# route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
192.168.100.0 0.0.0.0 255.255.255.0 U 100 0 0 ens32
192.168.100.254 0.0.0.0 255.255.255.255 UH 0 0 0 lo
******(4)Add no response arp Strategy of
[root@web1 ~]# vim /etc/sysctl.conf (modify)
# sysctl settings are defined through files in
# /usr/lib/sysctl.d/, /run/sysctl.d/, and /etc/sysctl.d/.
#
# Vendors settings live in /usr/lib/sysctl.d/.
# To override a whole file, create a new file with the same in
# /etc/sysctl.d/ and put new settings there. To override
# only specific settings, add a file with a lexically later
# name in /etc/sysctl.d/ and put new settings there.
#
# For more information, see sysctl.conf(5) and sysctl.d(5).
net.ipv4.conf.all.arp_ignore = 1
net.ipv4.conf.all.arp_announce = 2
net.ipv4.conf.default.arp_ignore = 1
net.ipv4.conf.default.arp_announce = 2
net.ipv4.conf.lo.arp_ignore = 1
net.ipv4.conf.lo.arp_announce = 2
Save exit
[root@web1 ~]# sysctl -p (effective immediately)
net.ipv4.conf.all.arp_ignore = 1
net.ipv4.conf.all.arp_announce = 2
net.ipv4.conf.default.arp_ignore = 1
net.ipv4.conf.default.arp_announce = 2
net.ipv4.conf.lo.arp_ignore = 1
net.ipv4.conf.lo.arp_announce = 2
******(5)open httpd service
[root@web1 ~]# systemctl start httpd
[root@web1 ~]# curl 127.0.0.1
1111111111
web2 node server configuration
and web1 The node server configuration is basically the same
[root@Centos7 ~]# hostnamectl set-hostname web2
[root@Centos7 ~]# su
[root@web2 ~]# mount /dev/cdrom /mnt/
mount: /dev/sr0 Write protected, will mount as read-only
mount: /dev/sr0 Already mounted or /mnt busy
/dev/sr0 Already mounted to /mnt upper
[root@web2 ~]# yum -y install httpd
. . . . . .
complete!
[root@web2 ~]# echo "222222222" > /var/www/html/index.html
[root@web2 ~]# cd /etc/sysconfig/network-scripts/
[root@web2 network-scripts]# cp ifcfg-lo ifcfg-lo:0
[root@web2 network-scripts]# cat <<aa> ifcfg-lo:0
> DEVICE=lo:0
> IPADDR=192.168.100.254
> NETMASK=255.255.255.255
> ONBOOT=yes
> aa
[root@web2 network-scripts]# systemctl restart network
[root@web2 network-scripts]# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet 192.168.100.254/32 brd 192.168.100.254 scope global lo:0
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens32: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 00:0c:29:ed:7c:e7 brd ff:ff:ff:ff:ff:ff
inet 192.168.100.4/24 brd 192.168.100.255 scope global ens32
valid_lft forever preferred_lft forever
inet6 fe80::34f4:cad:16ae:5b4d/64 scope link
valid_lft forever preferred_lft forever
[root@web2 network-scripts]# cd
[root@web2 ~]# echo "route add -host 192.168.100.254 dev lo:0" >> /etc/rc.local
[root@web2 ~]# route add -host 192.168.100.254 dev lo:0
[root@web2 ~]# route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
192.168.100.0 0.0.0.0 255.255.255.0 U 100 0 0 ens32
192.168.100.254 0.0.0.0 255.255.255.255 UH 0 0 0 lo
[root@web2 ~]# cat <<aaa>> /etc/sysctl.conf
> net.ipv4.conf.all.arp_ignore = 1
> net.ipv4.conf.all.arp_announce = 2
> net.ipv4.conf.default.arp_ignore = 1
> net.ipv4.conf.default.arp_announce = 2
> net.ipv4.conf.lo.arp_ignore = 1
> net.ipv4.conf.lo.arp_announce = 2
> aaa
[root@web2 ~]# sysctl -p
net.ipv4.conf.all.arp_ignore = 1
net.ipv4.conf.all.arp_announce = 2
net.ipv4.conf.default.arp_ignore = 1
net.ipv4.conf.default.arp_announce = 2
net.ipv4.conf.lo.arp_ignore = 1
net.ipv4.conf.lo.arp_announce = 2
[root@web2 ~]# systemctl start httpd
[root@web2 ~]# curl 127.0.0.1
222222222
test
Open the tester to access vip192 168.100. 254, refresh several times to check whether the load balancing is normal
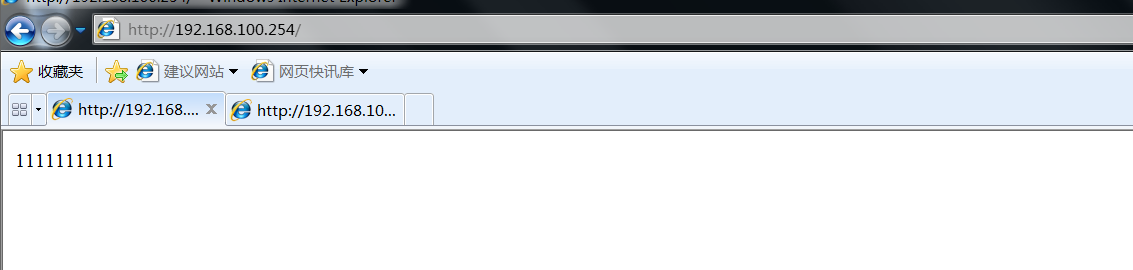
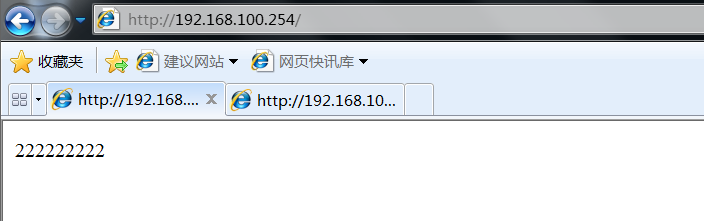
After confirming that the load balancing is normal, turn off the network card of the main regulator or turn off the main regulator

Then visit again to see if it can be accessed normally
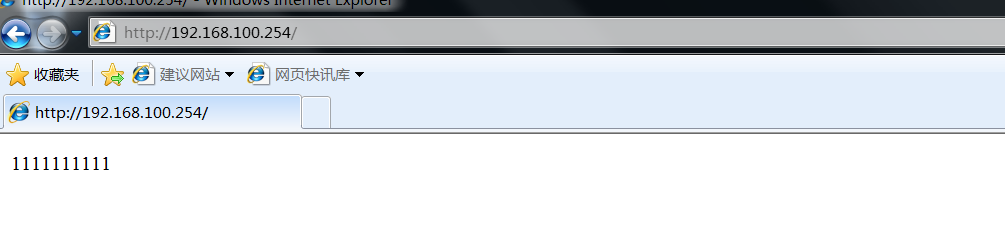
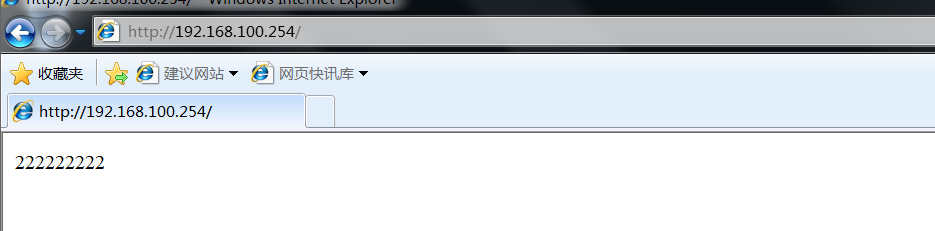
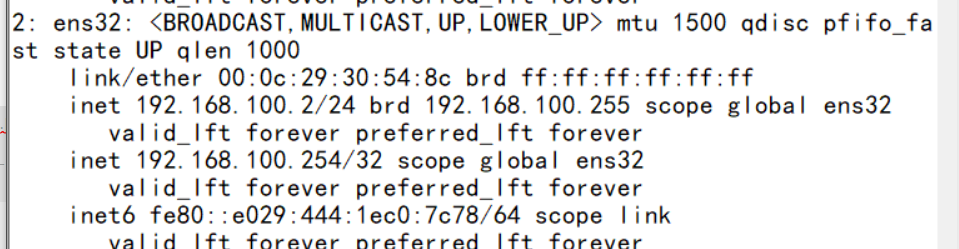
Check the standby scheduler and find that vip has successfully drifted to the standby scheduler
So far, the highly available load balancing cluster of LVS + kept (HA) has been deployed!!!!