Author: Zhang Yongli
1, Environment description of this example
- JDK 1.8
- CAS 5.3
- apache-maven-3.6.0
- mysql-5.6.32
- SuperMap iServer 10.1.3
- SuperMap iPortal 10.1.3
2, CAS 5.3 basic environment construction and verification
Need reference CAS 5.3 server setup Set up the environment, and use the system default user name and password to verify.
3, CAS 5.3 combined with MySQL configuration
Need reference CAS 5.3 login using MySQL database , and use the user-defined user name and password in MySQL database to verify.
4, CAS 5.3 dependencies for configuring SuperMap
4.1 increase maven dependency of CAS
Modify cas-overlay-template-5.3 \ POM XML file
<!--SuperMap need-->
<dependency>
<groupId>org.apereo.cas</groupId>
<artifactId>cas-server-support-saml</artifactId>
<version>${cas.version}</version>
</dependency>
<dependency>
<groupId>org.apereo.cas</groupId>
<artifactId>cas-server-support-json-service-registry</artifactId>
<version>${cas.version}</version>
</dependency>
<dependency>
<groupId>org.apereo.cas</groupId>
<artifactId>cas-server-core-authentication-attributes</artifactId>
<version>${cas.version}</version>
</dependency>
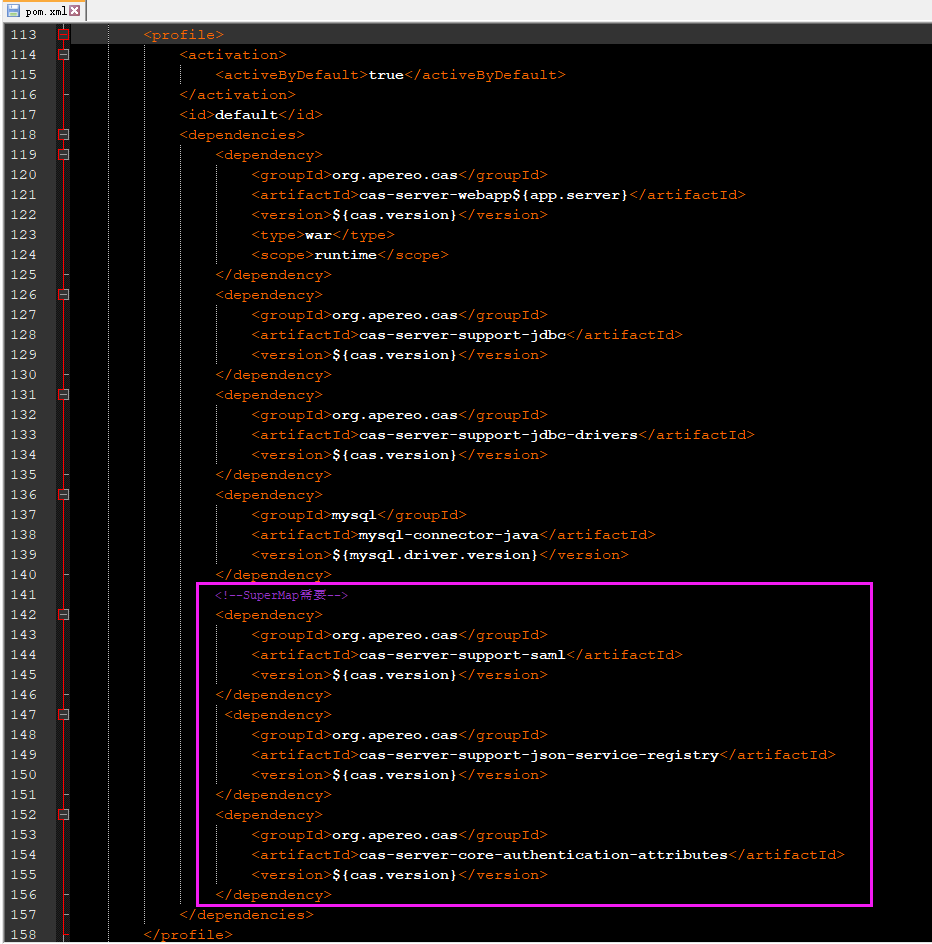
Explanation:
- CAS server support SAML, SAML 1 is followed between iServer (or iPortal, iEdge) and CAS 1 protocol to implement ticket verification response, so CAS needs to include the above dependencies to enable saml1 1 support
- CAS server support JSON service registry. CAS registers services in JSON format, so it needs to include JSON dependency packages to support JSON
- CAS Server Core authentication attributes. When implementing the ticket authentication response between iServer (or iPortal, iEdge) and CAS, you need to obtain the field representing the role (the role field in the self built user table) to verify the type of permission. Therefore, you need to add an attribute to return the dependent package
4.2 add httpsandimaps-10000001 for CAS JSON configuration
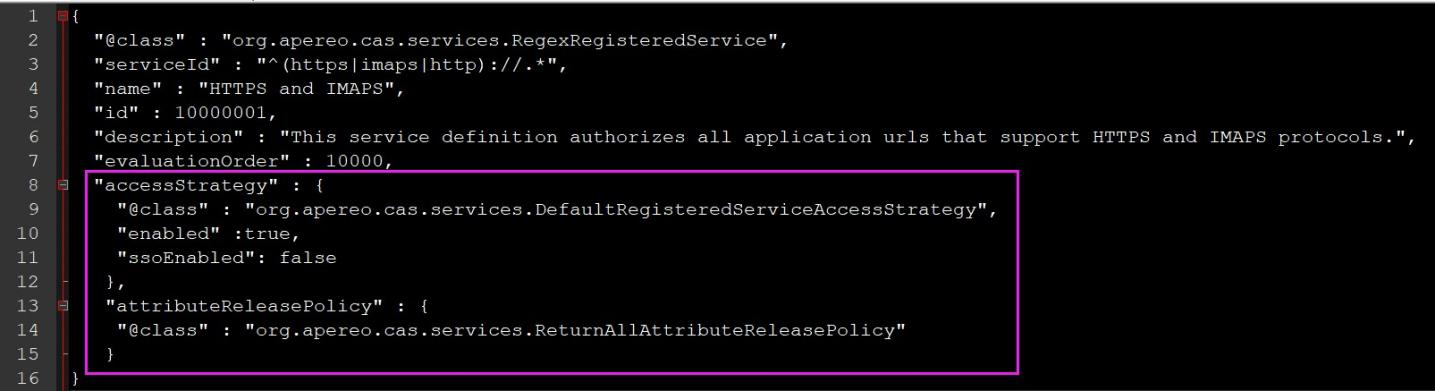
Modify cas-overlay-template-5.3 \ SRC \ main \ resources \ services \ httpsandimaps-10000001 JSON file, add the following
"accessStrategy" : {
"@class" : "org.apereo.cas.services.DefaultRegisteredServiceAccessStrategy",
"enabled" :true,
"ssoEnabled": false
},
"attributeReleasePolicy" : {
"@class" : "org.apereo.cas.services.ReturnAllAttributeReleasePolicy"
}
4.3 modify CAS custom application Properties configuration
Open cas-overlay-template-5.3 \ SRC \ main \ resources \ application Properties file, add the following configuration
#Set service registration profile location
cas.serviceRegistry.json.location=classpath:/services
#Turn on single line properties
cas.authn.attributeRepository.jdbc[0].singleRow=true
#Set the mapping relationship of query results between database table and cas server, which is subject to the field name of the database
cas.authn.attributeRepository.jdbc[0].attributes.username=login_name
cas.authn.attributeRepository.jdbc[0].attributes.password=password
cas.authn.attributeRepository.jdbc[0].attributes.role=role
cas.authn.attributeRepository.jdbc[0].order=0
#Return all properties
cas.authn.attributeRepository.jdbc[0].requireAllAttributes=true
#SQL statement to query all attribute fields
cas.authn.attributeRepository.jdbc[0].sql=SELECT * FROM user WHERE {0}
#Specify the above SQL query criteria
cas.authn.attributeRepository.jdbc[0].username=login_name
#Database connection
cas.authn.attributeRepository.jdbc[0].url=jdbc:mysql://127.0.0.1:3306/test?useUnicode=true&characterEncoding=UTF-8
#Database user name
cas.authn.attributeRepository.jdbc[0].user=root
#Database user password
cas.authn.attributeRepository.jdbc[0].password=own Mysql Password for
#Database driven
cas.authn.attributeRepository.jdbc[0].driverClass=com.mysql.jdbc.Driver
Explanation:
- cas.authn.attributeRepository.jdbc[0].attributes.XXX is a fixed writing method, and the following values are the field names in the database table. The following figure shows the fields in the database table
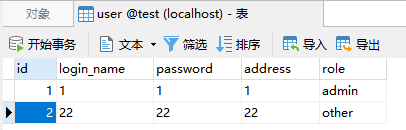
- cas. authn. attributeRepository. jdbc[0]. The SQL parameter is only the SQL statement used by CAS to query the database. It has great freedom. It is also feasible to use other correct query statements.
4.4 execute build script
.\build.cmd run
5, SuperMap iServer/iEdge configuration and verification
(the configuration method of SuperMap iEdge is the same as that of iServer. iServer is used for configuration verification below)
5.1 visit the homepage of SuperMap iServer
Browser access http://localhost:8090/iserver
Click the login button in the upper right corner to log in with the administrator account
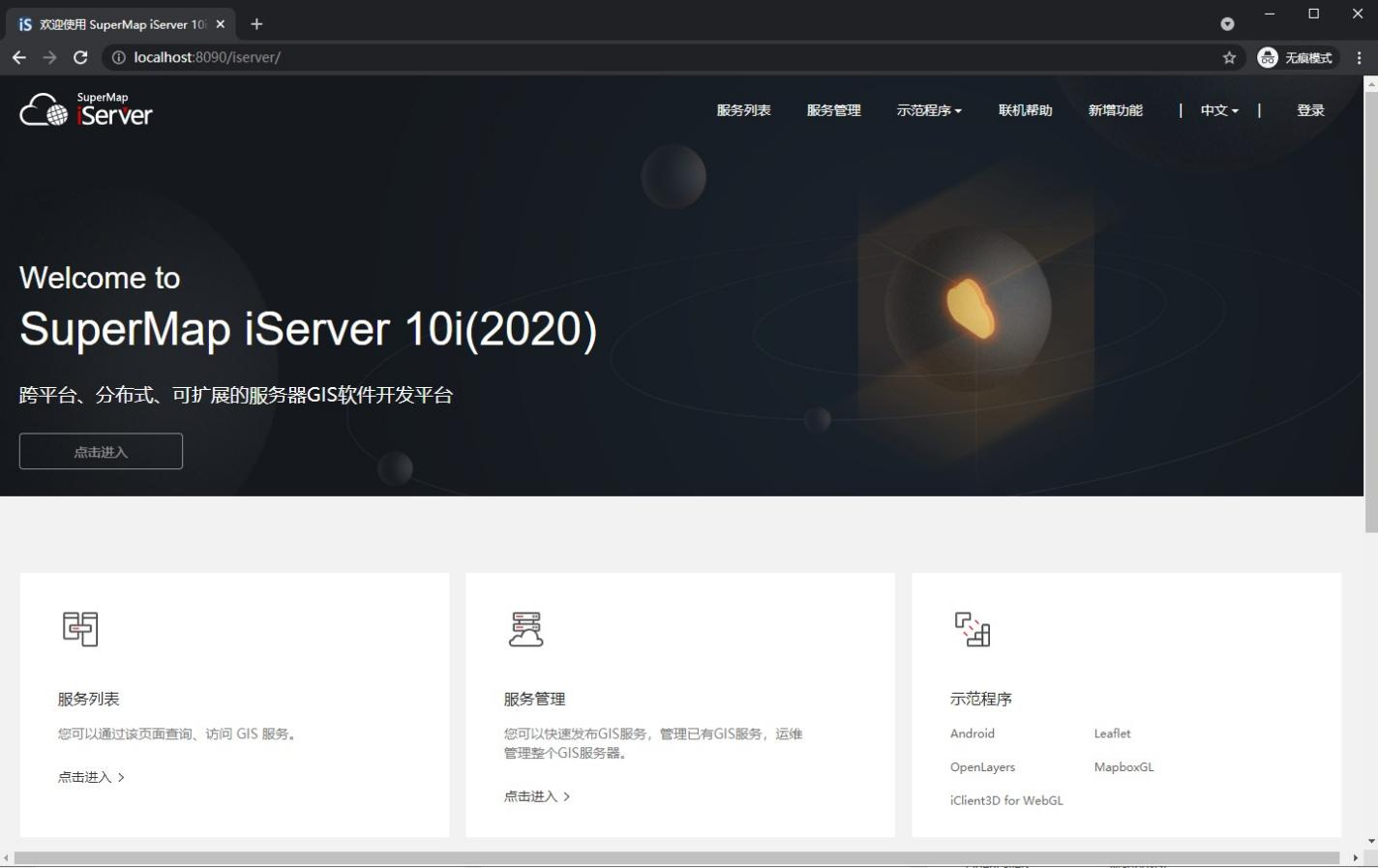
5.2 configuring CAS Information in SuperMap iServer
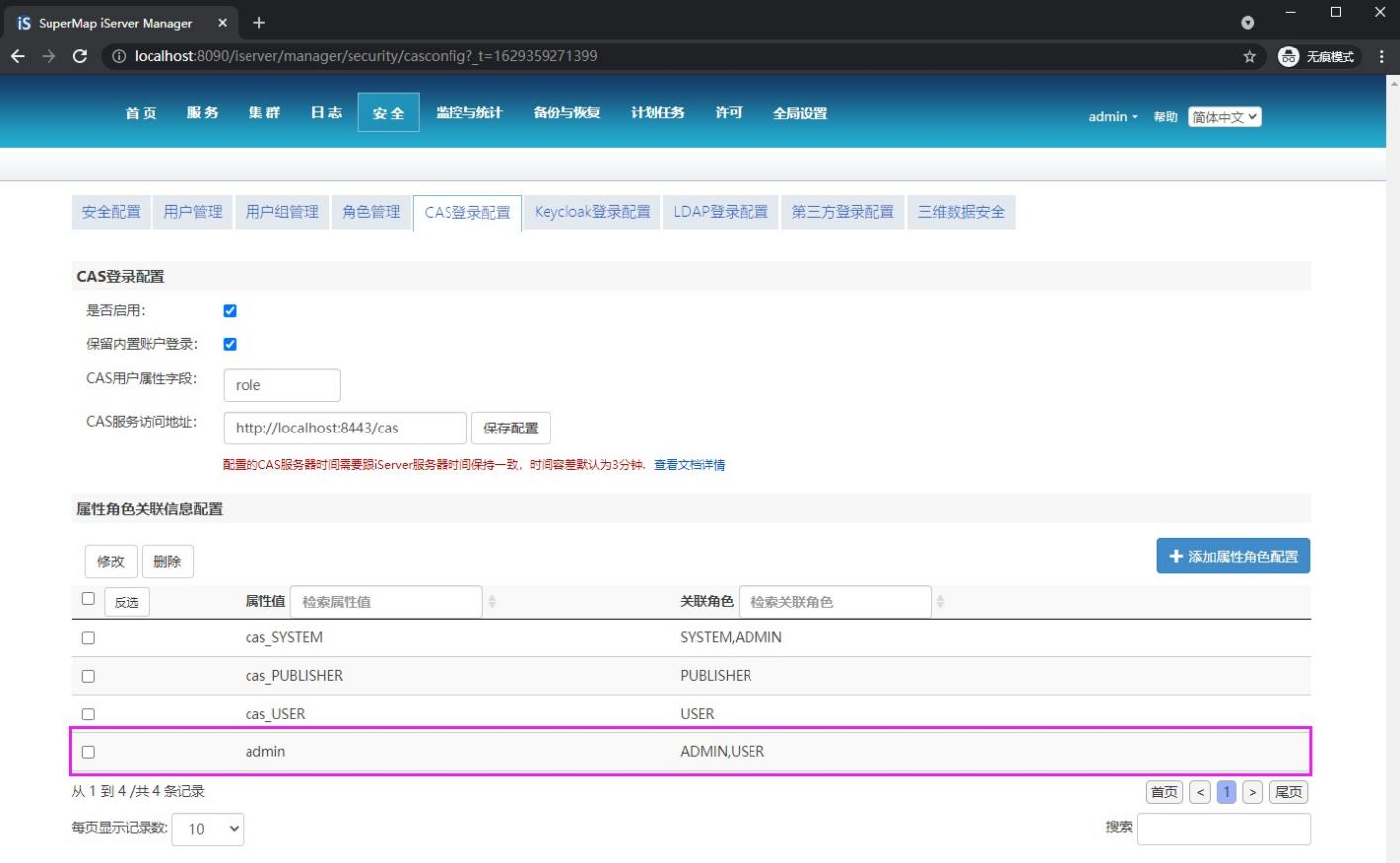
1) Click Security - > CAS login configuration, check available, fill in the permission role field and CAS login address in the database user table to save

2) Add the administrator role in the database to the mapping, and click the "add attribute role configuration" button

3) Fill in the role field in the database with the attribute value and add the ADMIN permission to the right

4) The results after adding are as follows
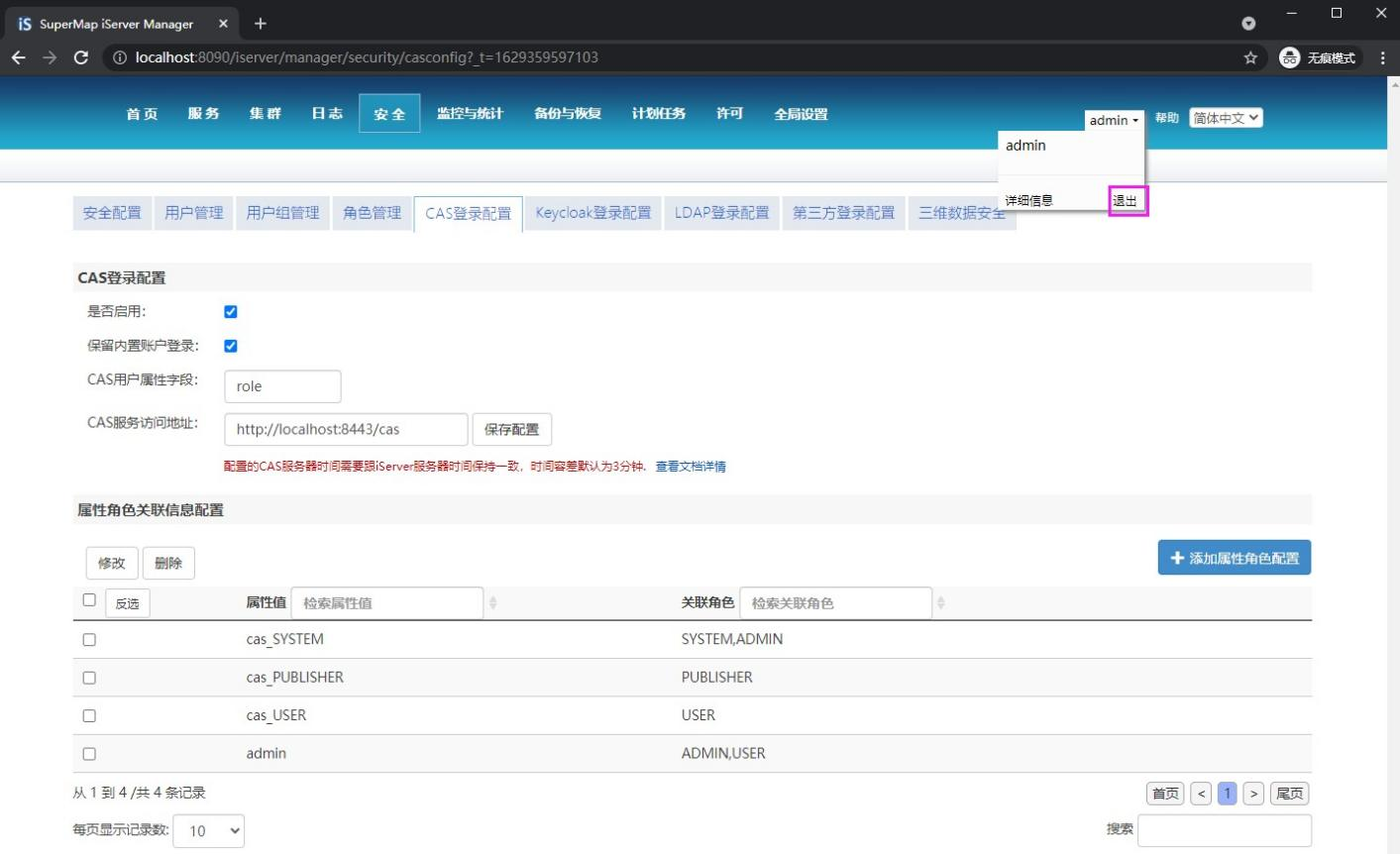
5.3 click the current login user name and choose to exit the current user
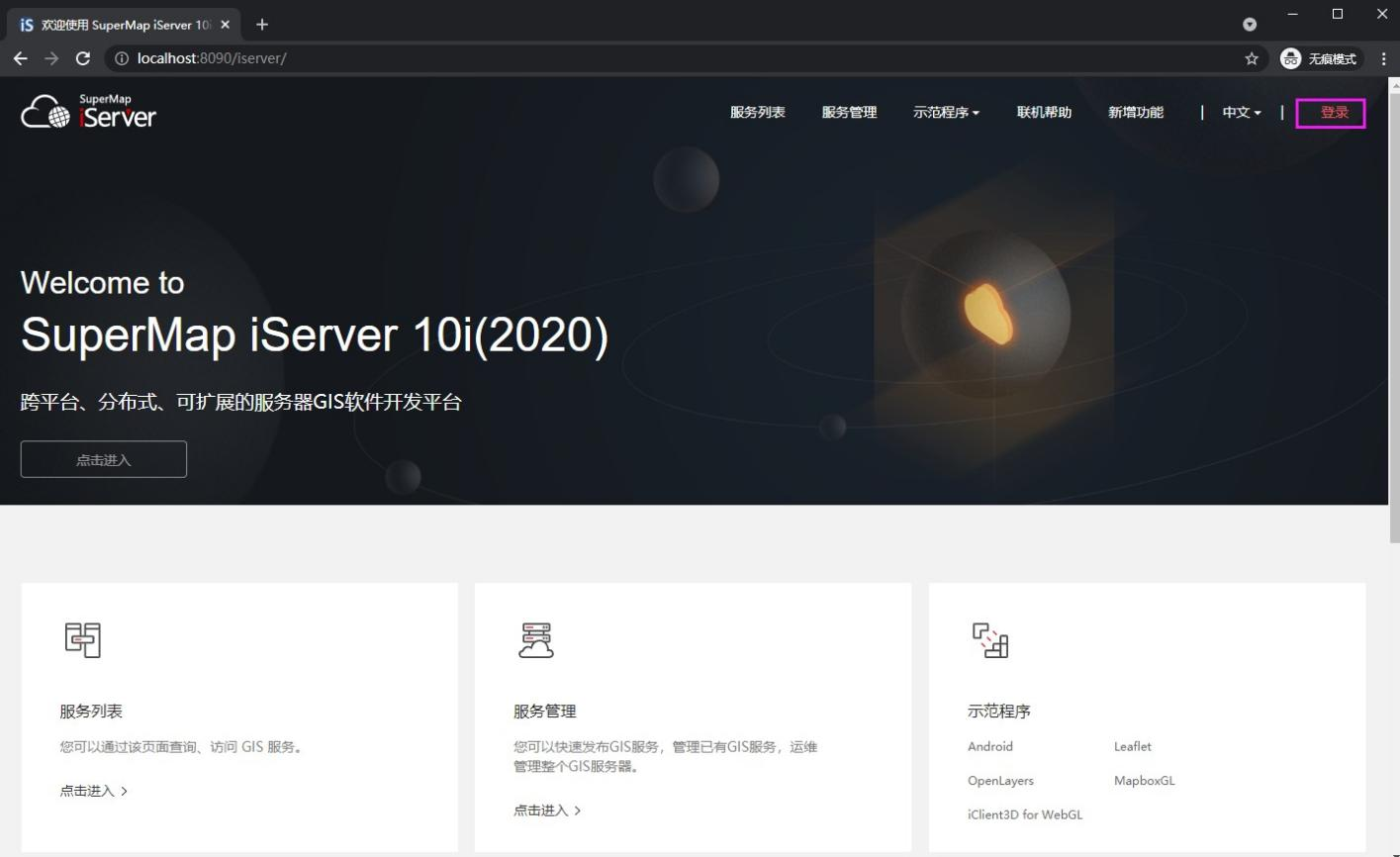
5.4 click the login button in the upper right corner again
5.5 select "log in with CAS account"
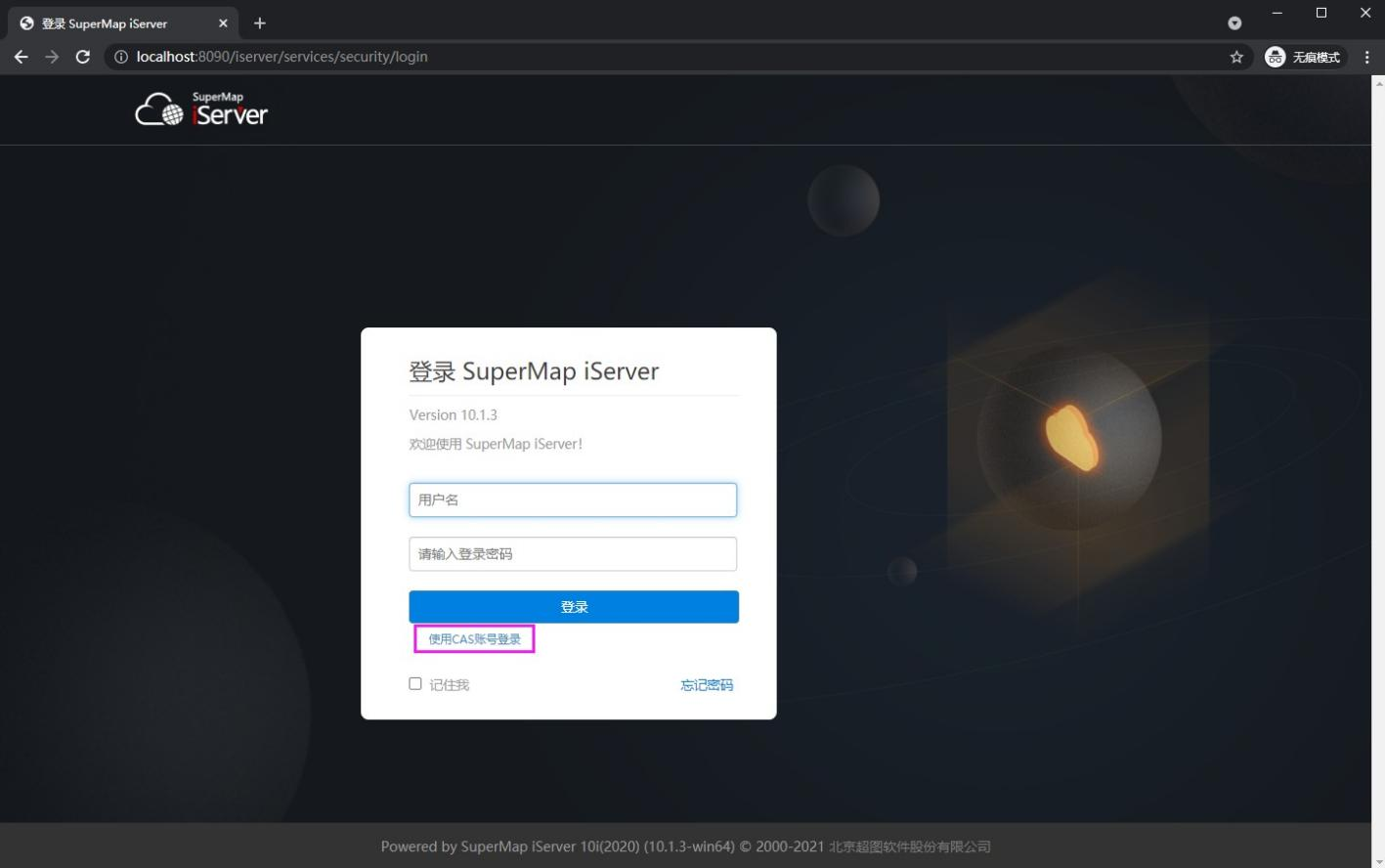
5.6 enter the user name and password of user-defined administrator authority in MySQL

5.7 login success will automatically jump
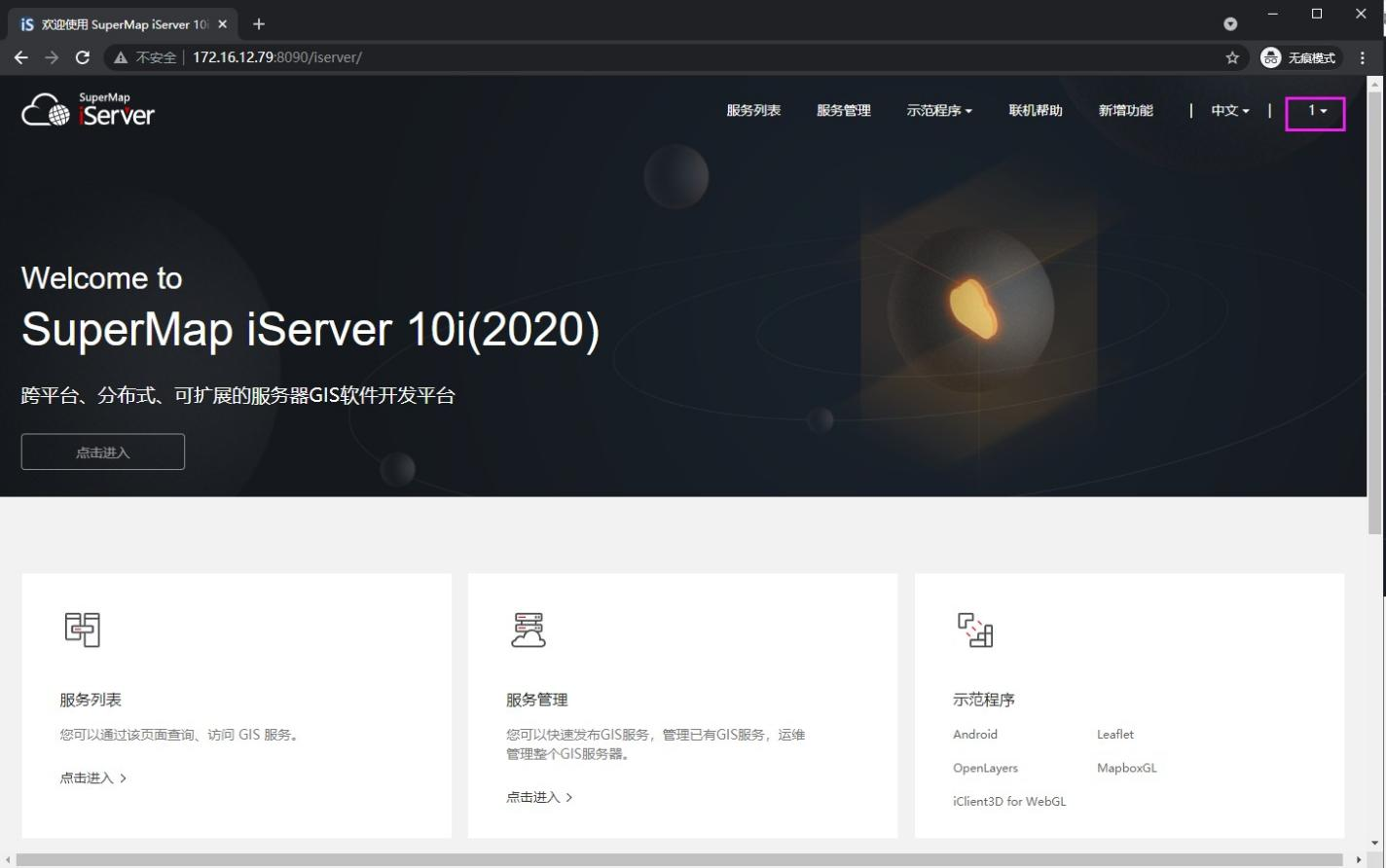
5.8 click my account in the upper right corner to view permissions and complete the single sign on function
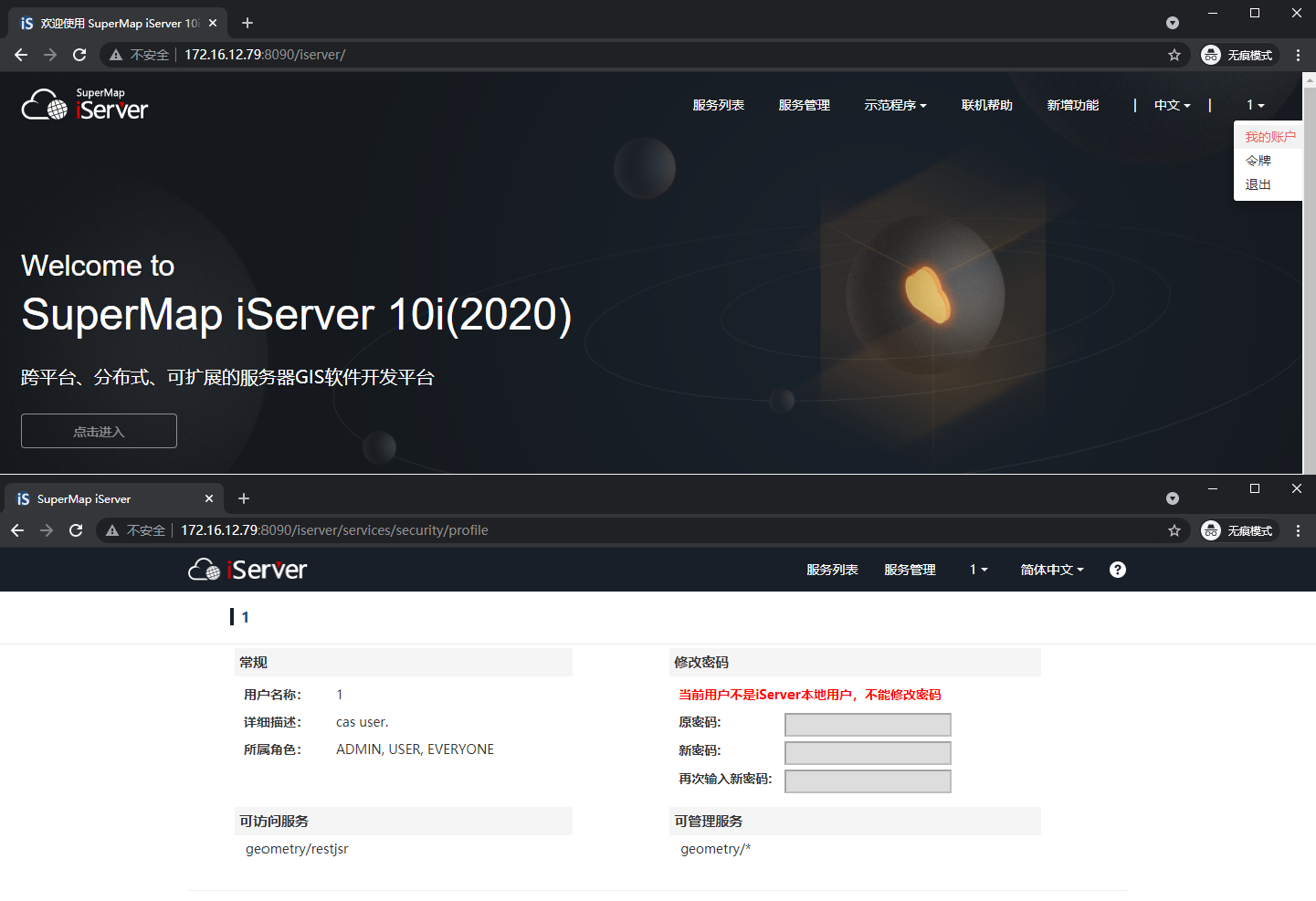
So far, SuperMap iServer has successfully integrated CAS to realize single sign on function.
6, SuperMap iPortal configuration and verification
6.1 visit the home page of SuperMap iPortal
Browser access http://localhost:8190/iportal
Click the login button in the upper right corner to log in with the administrator account
6.2 configuring CAS Information in SuperMap iPortal
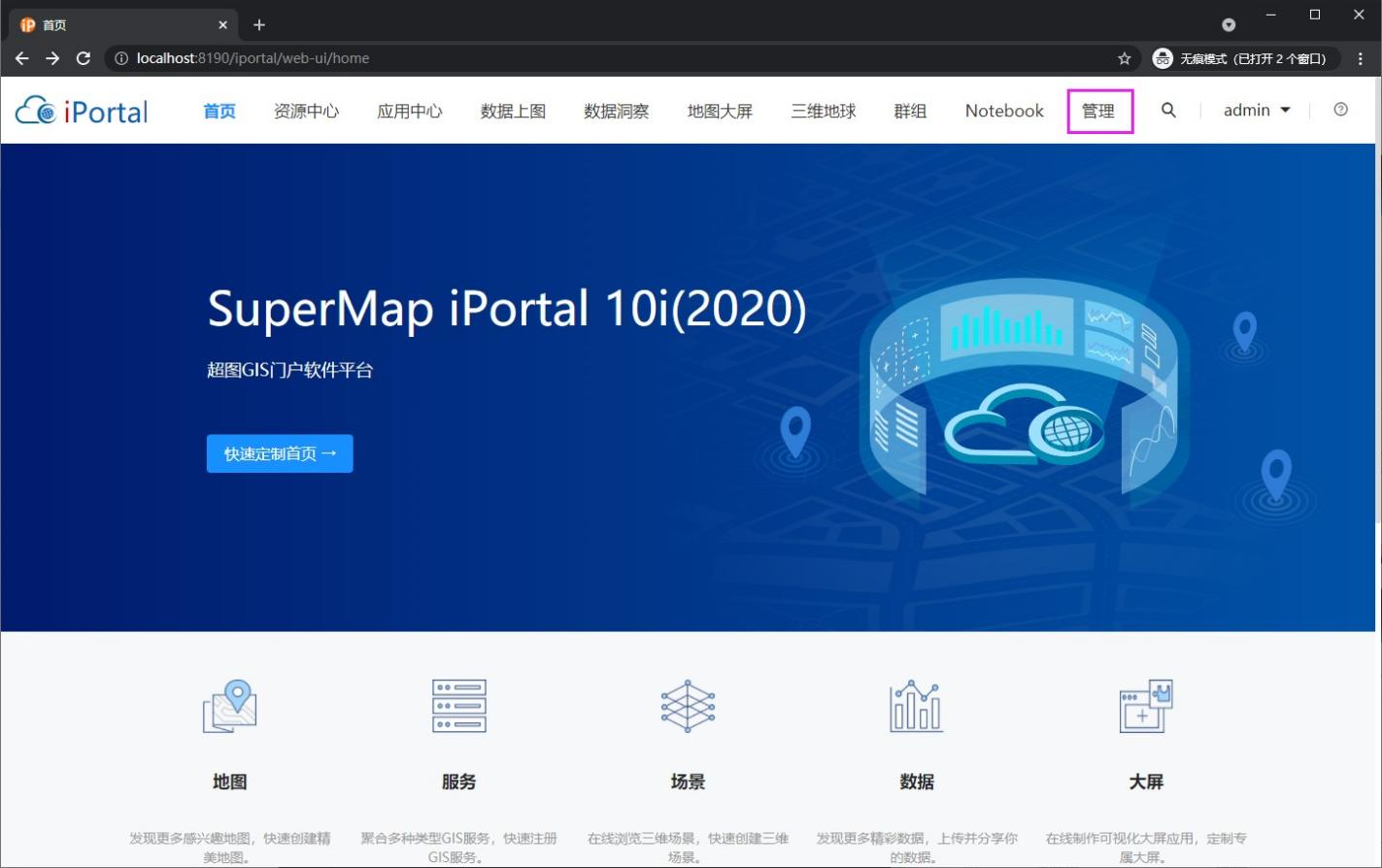
1) After successful login, click the management button to enter the iPortal management page
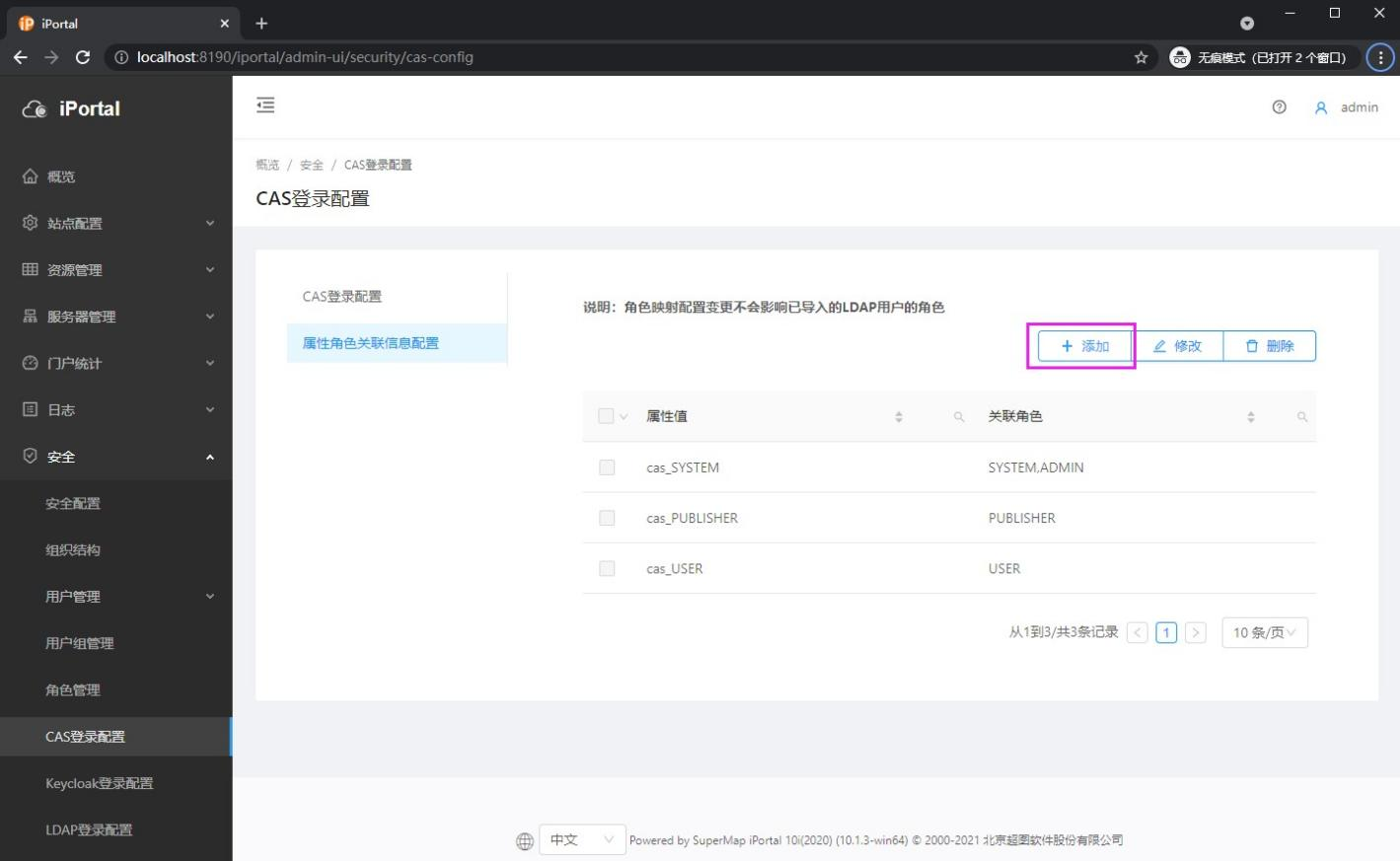
2) Enter "security" - > "CAS login configuration", enable CAS, fill in the permission role field in the database user table and save the CAS login address

3) Select attribute role association information configuration

4) Click the add role button
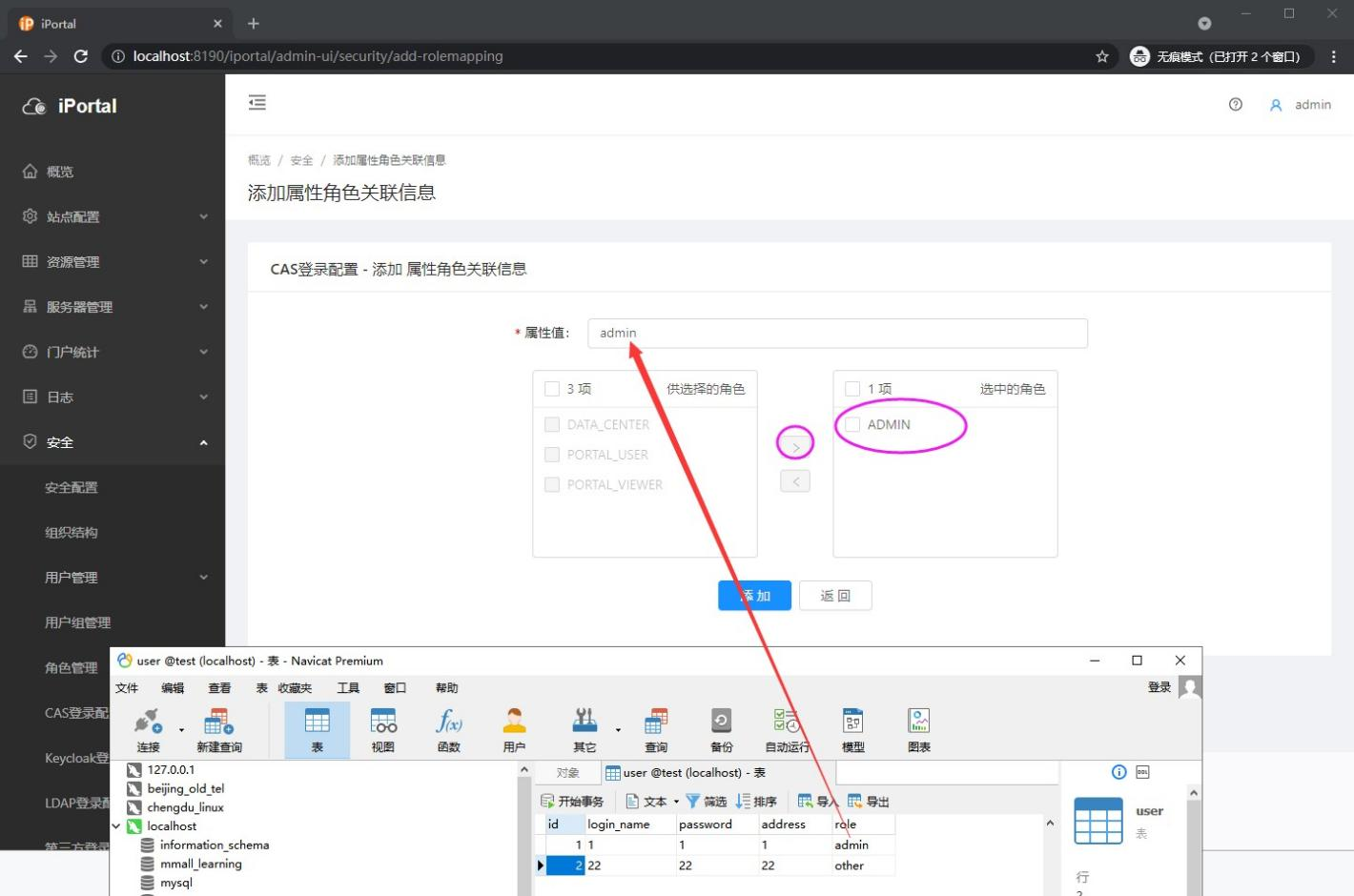
5) Fill in the role field in the database with the attribute value, add the ADMIN permission to the right, and finally add the button
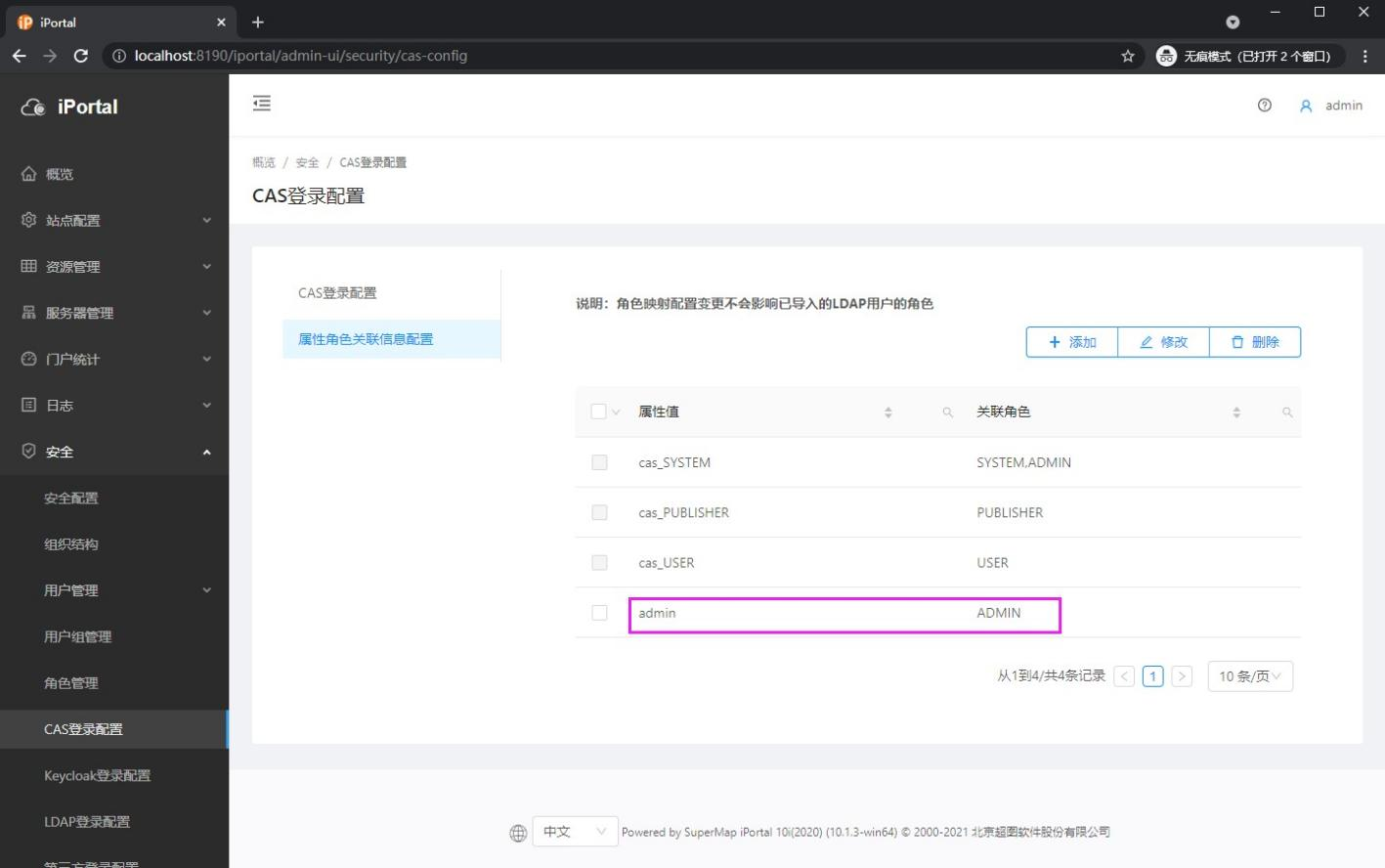
6) The results after adding are as follows
6.3 click the current login user name and choose to exit the current user
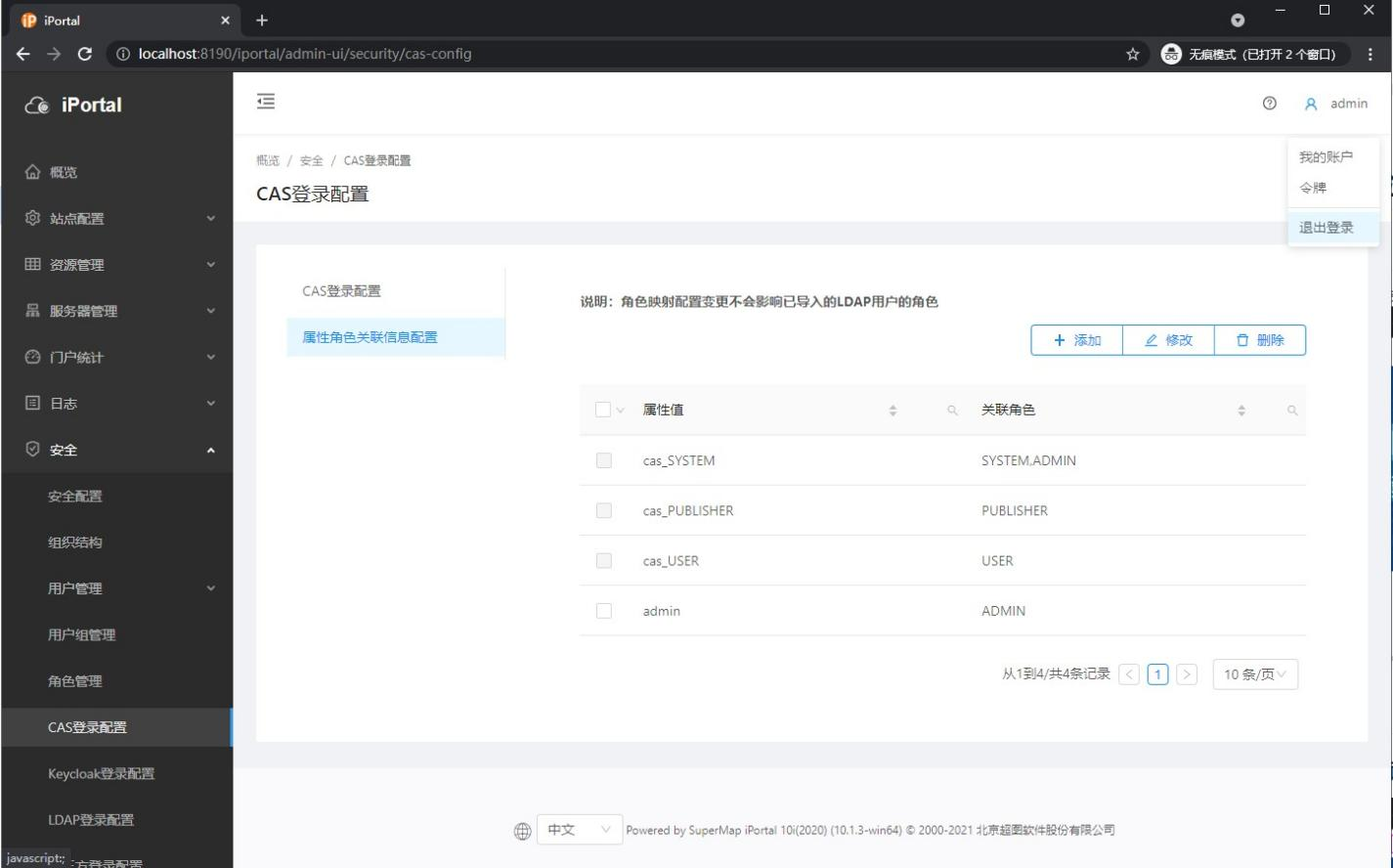
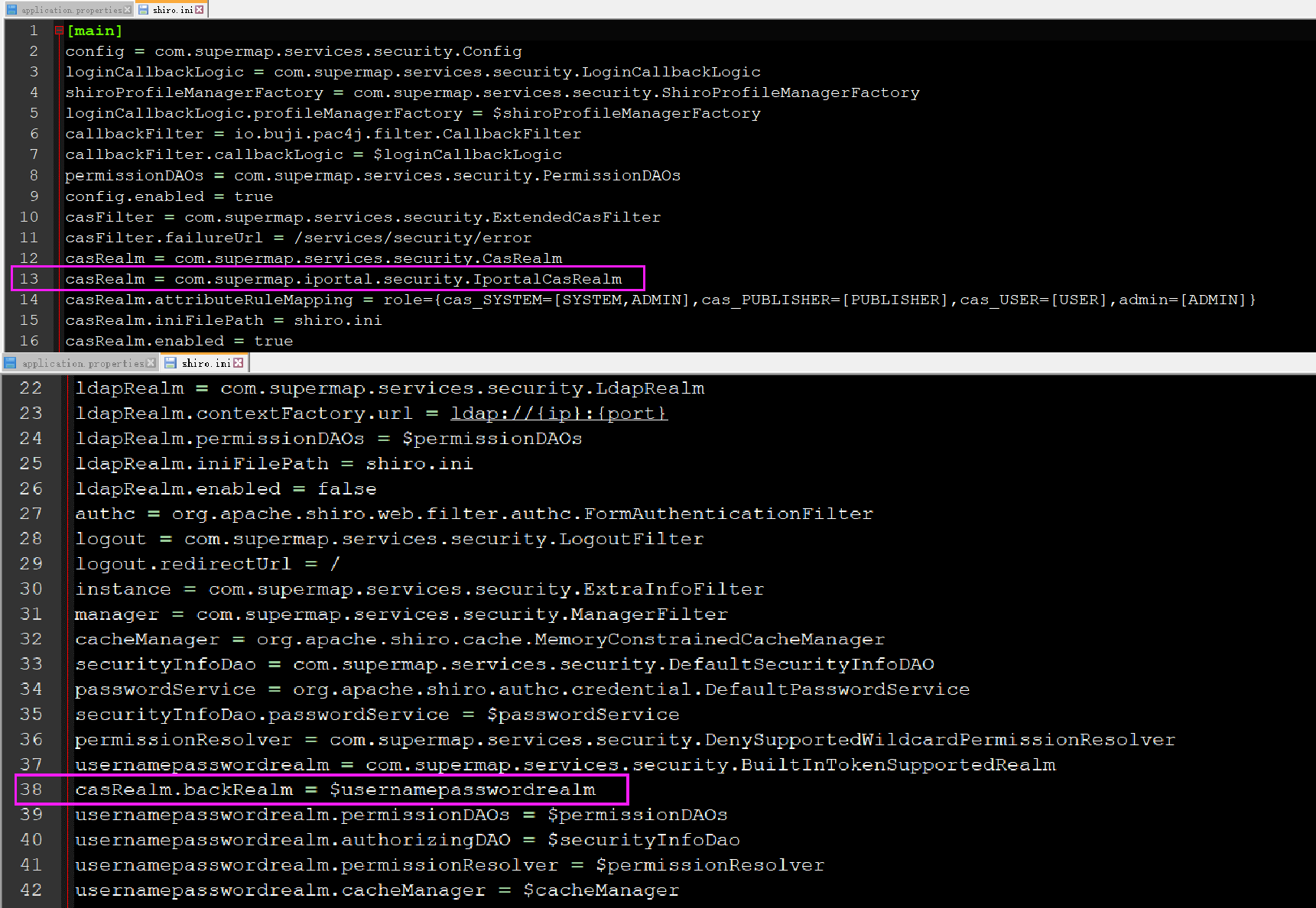
6.4 configure Shiro of iPortal INI file
Open in supermap-i portal-10.1 3-win64-zip\webapps\iportal\WEB-INF\shiro. The following two parameters are added to the INI file at the same position as me (because there is a variable reference relationship)
casRealm = com.supermap.iportal.security.IportalCasRealm casRealm.backRealm = $usernamepasswordrealm
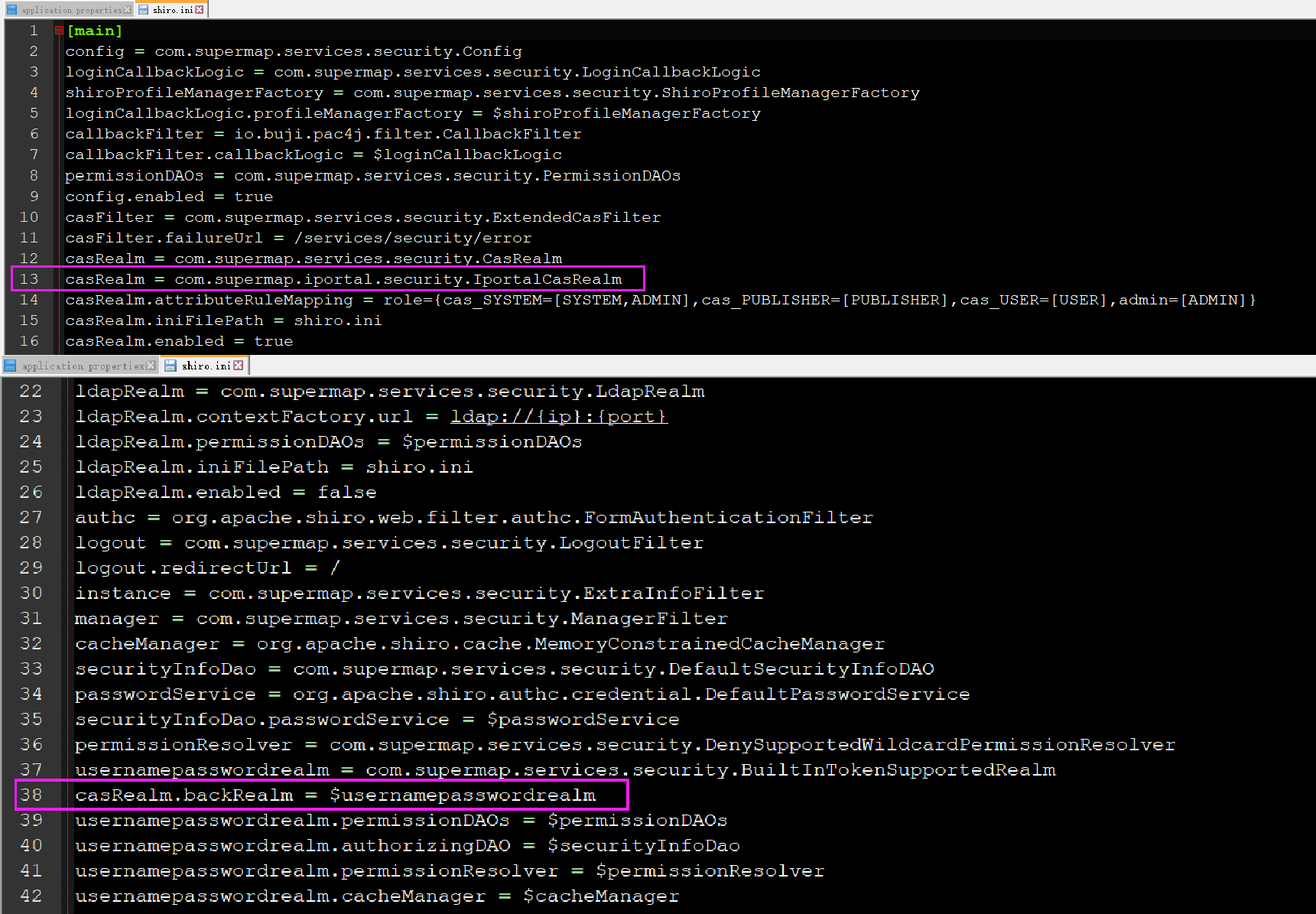
6.5 is revised to Shiro INI file, restart the SuperMap iPortal service
6.6 click the login button in the upper right corner again
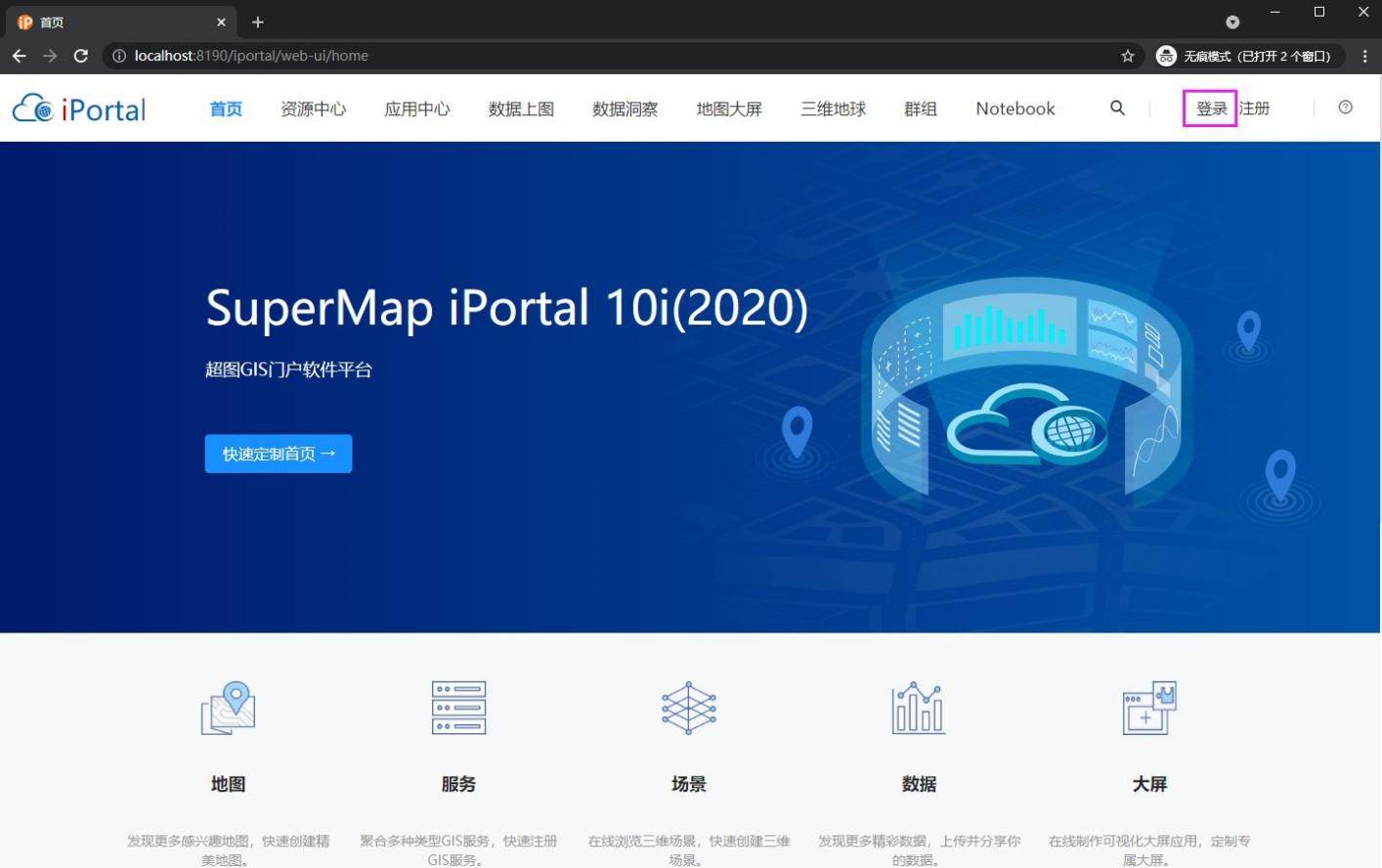
6.7 select "CAS login"

6.8 enter the user name and password of user defined administrator authority in MySQL

6.9 automatic jump after successful login
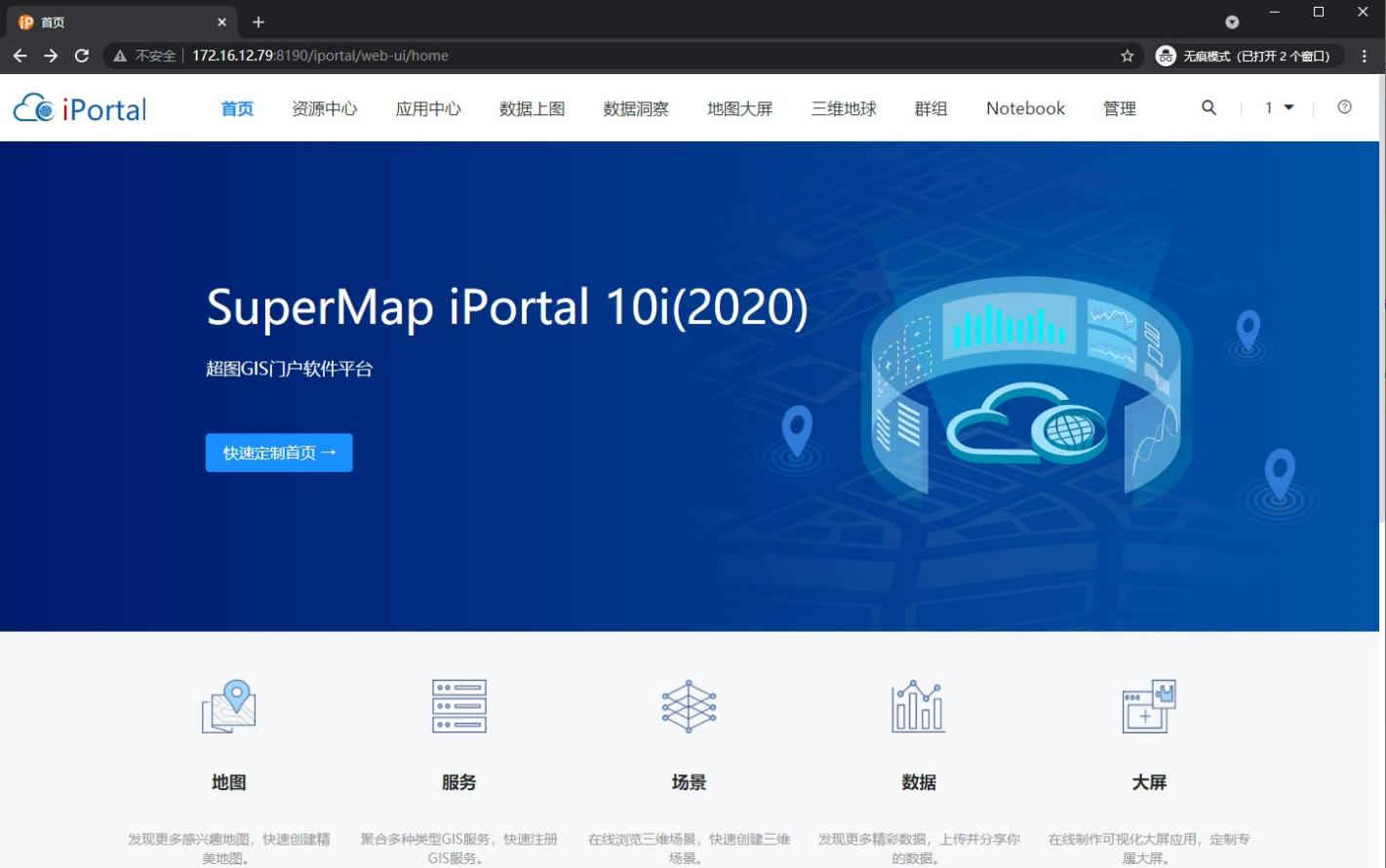
So far, SuperMap iPortal has successfully integrated CAS to realize single sign on function.
7, Precautions
7.1 SuperMap iServer CAS can log in normally, but does not have permission
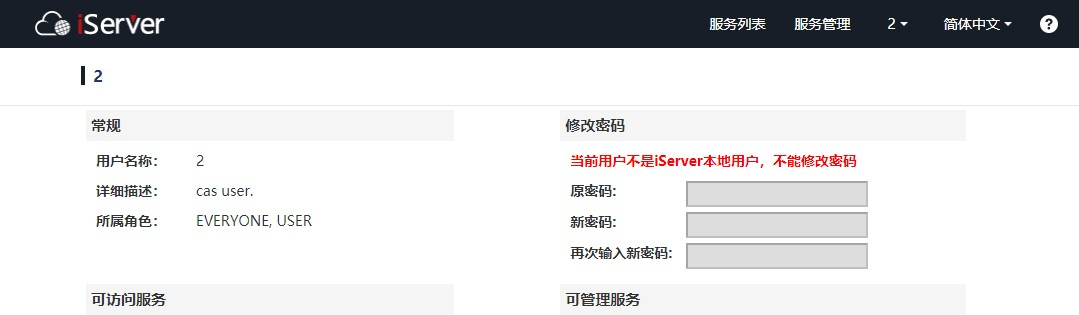
The reason is the application of CAS CAS. In properties authn. attributeRepository. JDBC [0] did not add database contact information
Attach complete configuration information
cas.tgc.secure=false
cas.serviceRegistry.initFromJson=true
#Set service registration profile location
cas.serviceRegistry.json.location=classpath:/services
# Query the account password SQL, which must include the password field
cas.authn.jdbc.query[0].sql=select * from user where login_name=?
# Specify the above SQL query field name (required)
cas.authn.jdbc.query[0].fieldPassword=password
# Database connection
cas.authn.jdbc.query[0].url=jdbc:mysql://127.0.0.1:3306/test?useUnicode=true&characterEncoding=UTF-8
# Database user name
cas.authn.jdbc.query[0].user=root
# Database user password
cas.authn.jdbc.query[0].password=own Mysql Password for
# Database driven
cas.authn.jdbc.query[0].driverClass=com.mysql.jdbc.Driver
#Single line attribute
#Turn on single line properties
cas.authn.attributeRepository.jdbc[0].singleRow=true
#Set the mapping relationship of query results between database table and cas server, which is subject to the field name of the database
cas.authn.attributeRepository.jdbc[0].attributes.username=login_name
cas.authn.attributeRepository.jdbc[0].attributes.password=password
cas.authn.attributeRepository.jdbc[0].attributes.role=role
cas.authn.attributeRepository.jdbc[0].order=0
#Return all properties
cas.authn.attributeRepository.jdbc[0].requireAllAttributes=true
#SQL statement to query all attribute fields
cas.authn.attributeRepository.jdbc[0].sql=SELECT * FROM user WHERE {0}
#Specify the above SQL query criteria
cas.authn.attributeRepository.jdbc[0].username=login_name
#Database connection
cas.authn.attributeRepository.jdbc[0].url=jdbc:mysql://127.0.0.1:3306/test?useUnicode=true&characterEncoding=UTF-8
#Database user name
cas.authn.attributeRepository.jdbc[0].user=root
#Database user password
cas.authn.attributeRepository.jdbc[0].password=own Mysql Password for
#Database driven
cas.authn.attributeRepository.jdbc[0].driverClass=com.mysql.jdbc.Driver
7.2 SuperMap iPortal CAS can log in normally, but has no permission
The reason is the Shiro of iPortal INI file is incorrectly configured or not configured
Open in supermap-i portal-10.1 3-win64-zip\webapps\iportal\WEB-INF\shiro. The following two parameters are added to the INI file at the same position as me (because there is a variable reference relationship)
casRealm = com.supermap.iportal.security.IportalCasRealm casRealm.backRealm = $usernamepasswordrealm
7.3 CAS login prompt: "the service record of CAS is empty and there is no service defined. Applications that want to pass CAS authentication must be recorded in the service record“
The cause is application The location of registered configuration file is missing in properties. Add the following configuration and restart CAS
#Set service registration profile location cas.serviceRegistry.json.location=classpath:/services
7.4 why does single sign on authentication fail after configuring CAS authentication server?
If the CAS authentication server and GIS Server are not on the same machine, the login verification may not succeed due to the time difference between the two machines. At this time, it is necessary to adjust the time of the two machines to be consistent, or extend the fault tolerance interval. The default time difference tolerance of iPortal is 3 minutes. The way to modify the tolerance of fault tolerance time difference is to edit Shiro Ini (under WEB-INF), modify the casRealm.tolerance parameter (unit: ms), and restart the iPortal service after modification
casRealm.tolerance = 180000