Access Control List
Access Control Lists (ACL S) are instruction lists applied to router interfaces. These instruction lists are used to tell the router which packets can be received and which packets need to be rejected. Whether a packet is received or rejected can be determined by specific indication conditions such as source address, destination address, port number, etc.
I. ACL function
- flow control
- Matching streams of interest
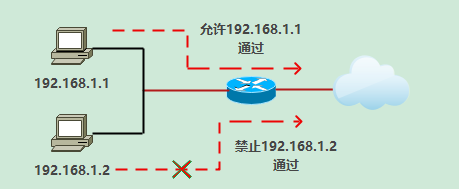
1.1 limit network traffic and improve network performance. For example, ACL can specify that this type of packet has a higher priority according to the packet protocol. In the same case, it can be processed by network devices in advance
1.2 provide control means for communication flow.
1.3 provide basic security means for network access
1.4 at the network equipment interface, determine which type of communication traffic is forwarded and which type of communication traffic is blocked.
For example, users can allow e-mail traffic to be routed and reject all Telnet traffic. For example, a department requires that it can only use the WWW function, which can be realized through ACL; For another example, for the sake of the confidentiality of a department, it is not allowed to access the Internet or the Internet. It can be realized through ACL
Two types of ACL
-
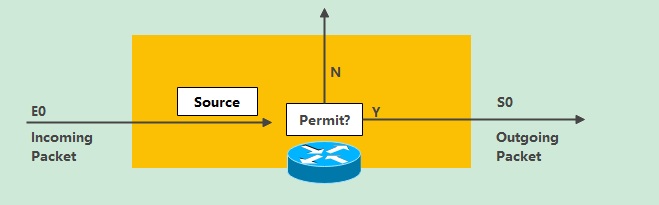
Standard access control list
1. You can only filter according to the source address
2. Take relevant actions (allowed or prohibited) for the whole agreement
-
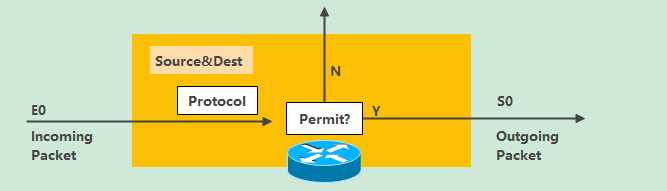
Extended access control list
1. Be able to filter according to source, destination address, port, etc
2. Be able to allow or reject specific agreements
III. ACL configuration
1. Standard ACL configuration
1.1 Router(config)#access-list access-list-number {permit|deny} source [wildcard mask]
- Access list number: access control list number. The standard ACL value is 1-99.
- Allow deny: allow / deny if the rule is met
- Source: the source address of the packet, which can be either a host address or a network address.
- Source wildcard: wildcard mask, also known as inverse code, that is, the subnet mask is de inverted. For example, if the normal subnet mask 255.255.255.0 is reversed, it is 0.0.0.255.
1.2 Router(config-if)#ip access-group access-list-number {in | out}
- Application in interface
- The inbound or outbound direction is associated when applying, and the outbound direction is the default
1.3 delete the established standard ACL syntax as follows:
Router (config) #no access list access list number / / the whole ACL list will be deleted
2. Extend ACL configuration
2.1 Router(config)#access-list access-list-number {permit|deny} protocol {source souce-wildcard destination destination-wildcard} [operator operan]
- Access list number: access control list number. The extended ACL value is 100-199.
- Allow deny: allow / deny if the rule is met.
- Protocol: used to specify the type of protocol, such as IP, TCP, UDP, ICMP, etc.
- Source and destination: source and destination, which are used to mark the source address and destination address respectively.
- Souce wildcard and destination wildcard: subnet inverse code. Souce wildcard is the source inverse code and destination wildcard is the target inverse code.
- Operator operator: LT (less than), GT (greater than), EQ (equal to), NEQ (not equal to) a port number.
2.2 ACL syntax
The syntax for deleting the established extended ACL is as follows:
Router(config)#no access-list access-list-number
For example, 192.168.1.0/24 is allowed to access 192.168.2.0/24, while all other hosts are denied access.
Router(config)#access-list 101 permit ip 192.168.1.0 0.0.0.255 192.168.2.0 0.0.0.255
Router(config)#access-list 101 deny ip any any
For example, the network 192.168.1.0/24 is denied access to the FTP server 192.168.2.100/24, while other hosts are allowed to access it.
Router(config)#access-list 102 deny tcp 192.168.1.0 0.0.0.255 host 192.168.2.100 eq 21
Router(config)#access-list 102 permit ip any any
For example, it is forbidden to ping the host in the network 192.168.1.0/24 with the server 192.168.2.200/24, but allow other hosts to access.
Router(config)#access-list 103 deny icmp 192.168.1.0 0.0.0.255 host 192.168.1.200 echo
Router(config)#access-list 103 permit ip any any
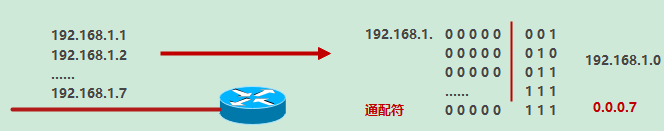
Four wildcards
- Wildcard matching (0 means strict matching, 1 means it doesn't matter)
0 0 0 0 0 0 0 0 0 0 0 matches all
0 0 0 0 0 1 matches two IP S
0 0 0 0 0 1 1 matches four IP S
1 1 1 1 1 1 1 1 1 1 1 does not match all bits
2. Wildcard abbreviations
192.168.1.1 0.0.0 = host 192.168.1.1 exactly matches the IP address 192.168.1.1
0.0.0.0 255.255.255 = any matches all IP S
Experimental environment
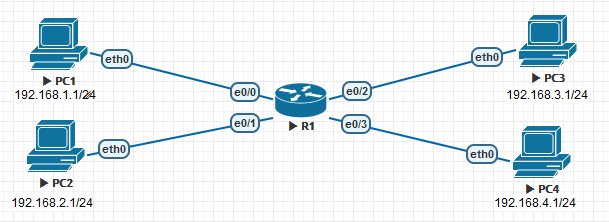
1.1 configure pc ip address and router interface ip
PC1> ip 192.168.1.1 255.255.255.0 192.168.1.254 #Configure R1 router Router(config)#ho R1 R1(config)#int e0/0 R1(config-if)#ip add 192.168.1.254 255.255.255.0 R1(config-if)#no sh #Configure other PC and router interfaces in the same way
2.1 experimental objectives
PC1 can access PC2, but not PC3. PC4 is configured as follows:
R1(config)#access-list 100 permit ip 192.168.1.1 0.0.0.0 192.168.2.1 0.0.0.0 // Extended ACL
R1(config)#int e0/0
R1(config-if)#ip access-group 100 in // Enter the in direction of the interface and call the ACL number
R1(config-if)#end
R1#sh run | s list // View ACl
access-list 100 permit ip host 192.168.1.1 host 192.168.2.1
R1#show ip access
Extended IP access list 100
10 permit ip host 192.168.1.1 host 192.168.2.1
Router(config)#
Verification results:
PC1> ping 192.168.2.1 //Can ping through 84 bytes from 192.168.2.1 icmp_seq=1 ttl=63 time=2.264 ms 84 bytes from 192.168.2.1 icmp_seq=2 ttl=63 time=0.428 ms 84 bytes from 192.168.2.1 icmp_seq=3 ttl=63 time=0.559 ms 84 bytes from 192.168.2.1 icmp_seq=4 ttl=63 time=0.702 ms 84 bytes from 192.168.2.1 icmp_seq=5 ttl=63 time=0.441 ms PC1> ping 192.168.3.1 //Unable to ping *192.168.1.254 icmp_seq=1 ttl=255 time=0.900 ms (ICMP type:3, code:13, Communication administratively prohibited) *192.168.1.254 icmp_seq=2 ttl=255 time=0.280 ms (ICMP type:3, code:13, Communication administratively prohibited) *192.168.1.254 icmp_seq=3 ttl=255 time=0.328 ms (ICMP type:3, code:13, Communication administratively prohibited) *192.168.1.254 icmp_seq=4 ttl=255 time=0.528 ms (ICMP type:3, code:13, Communication administratively prohibited) *192.168.1.254 icmp_seq=5 ttl=255 time=0.307 ms (ICMP type:3, code:13, Communication administratively prohibited)
2.2 experimental objectives
192.168.1.0 can access the 192.168.2.0 network segment, but other network segments cannot. The configuration is as follows:
Router(config)#int e0/0
Router(config-if)#
Router(config-if)#no access-list 100 permit ip 192.168.1.1 0.0.0.0 192.168.2.1 0.0.0.0
Router(config-if)#exit
Router(config)#access-list 100 permit ip 192.168.1.0 0.0.0.255 192.168.2.0 0.0.0.255
Router(config)#do sh ip access
Extended IP access list 100
10 permit ip 192.168.1.0 0.0.0.255 192.168.2.0 0.0.0.255