This article is the third of my study notes on reverse cracking shelling in the great God forum. It is my review and summary of what I have learned in the past. There may be fallacies. You are welcome to point out.
Notes will be released one after another, hoping to help Mengxin who wants to get started and make progress together
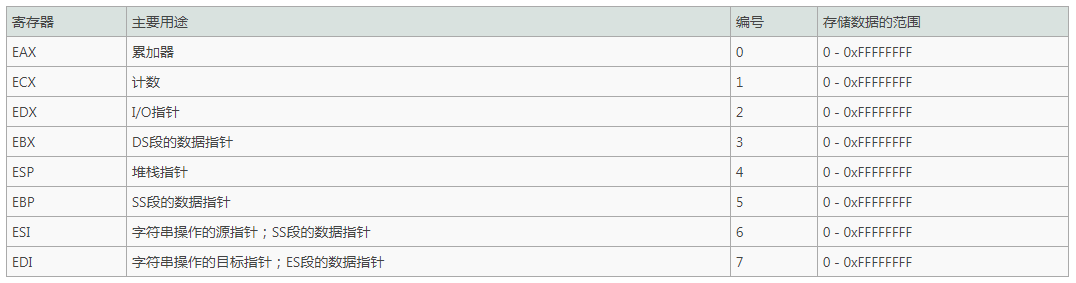
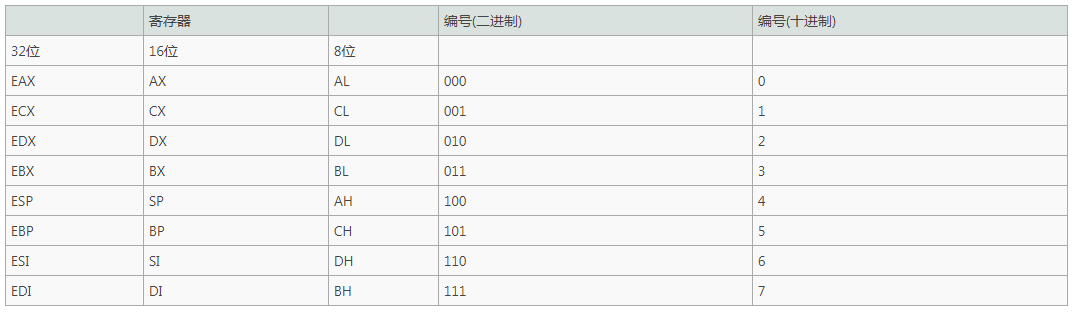
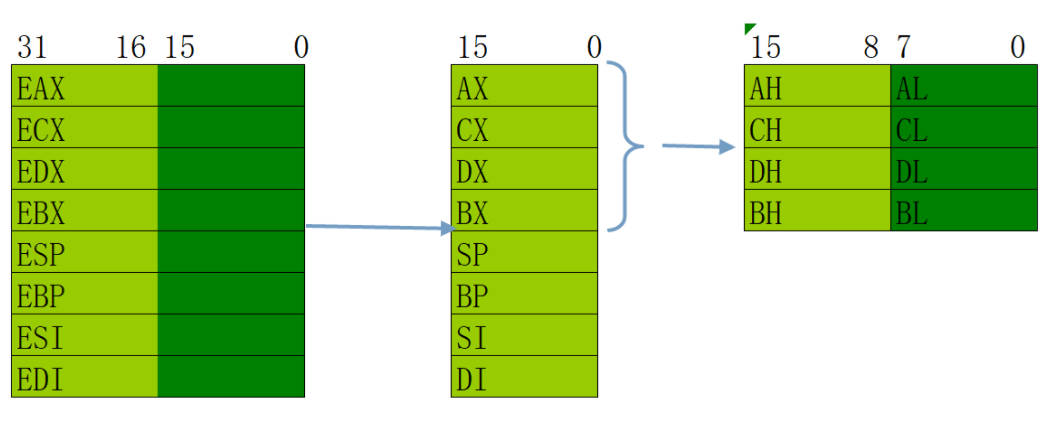
32-bit general purpose register
The purpose of the 32-bit general purpose register is as follows:
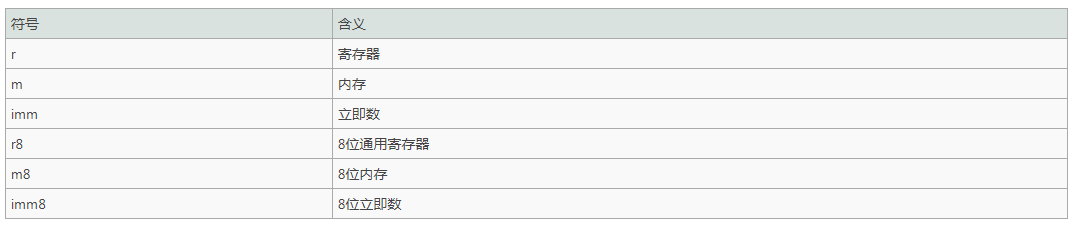
Assembly instruction
MOV instruction
Syntax of MOV:
MOV r/m8,r8 MOV r/m16,r16 MOV r/m32,r32 MOV r8,r/m8 MOV r16,r/m16 MOV r32,r/m32 MOV r8, imm8 MOV r16, imm16 MOV r32, imm32
MOV destination operand, source operand
Role: copy the source operand to the destination operand
The source operand can be an immediate, a general-purpose register, a segment register, or a memory unit The destination operand can be a general-purpose register, a segment register, or a memory unit Operands must be the same width The source operand and destination operand cannot be both memory units
ADD instruction
ADD syntax:
ADD r/m8, imm8 ADD r/m16,imm16 ADD r/m32,imm32 ADD r/m16, imm8 ADD r/m32, imm8 ADD r/m8, r8 ADD r/m16, r16 ADD r/m32, r32 ADD r8, r/m8 ADD r16, r/m16 ADD r32, r/m32
ADD destination operand, source operand
Function: adds the source operand to the destination operand
SUB instruction
Syntax of SUB:
SUB r/m8, imm8 SUB r/m16,imm16 SUB r/m32,imm32 SUB r/m16, imm8 SUB r/m32, imm8 SUB r/m8, r8 SUB r/m16, r16 SUB r/m32, r32 SUB r8, r/m8 SUB r16, r/m16 SUB r32, r/m32
SUB destination operand, source operand
Function: reduces the source operand to the destination operand
AND instruction
Syntax of AND:
AND r/m8, imm8 AND r/m16,imm16 AND r/m32,imm32 AND r/m16, imm8 AND r/m32, imm8 AND r/m8, r8 AND r/m16, r16 AND r/m32, r32 AND r8, r/m8 AND r16, r/m16 AND r32, r/m32
AND destination operand, source operand
Function: saves the result to the destination operand after the source operand and destination operand are summed
OR instruction
Syntax of OR:
OR r/m8, imm8 OR r/m16,imm16 OR r/m32,imm32 OR r/m16, imm8 OR r/m8, r8 OR r/m16, r16 OR r/m32, r32 OR r8, r/m8 OR r16, r/m16 OR r32, r/m32
OR destination operand, source operand
Function: saves the result to the destination operand after the source operand and destination operand or operation
XOR instruction
XOR syntax:
XOR r/m8, imm8 XOR r/m16,imm16 XOR r/m32,imm32 XOR r/m16, imm8 XOR r/m8, r8 XOR r/m32, r32 XOR r8, r/m8 XOR r16, r/m16 XOR r32, r/m32
XOR destination operand, source operand
Function: save the result to the destination operand after XOR operation between the source operand and the destination operand
NOT instruction
Syntax of NOT:
NOT r/m8 NOT r/m16 NOT r/m32 NOT Operand Function: reverse
LEA instruction
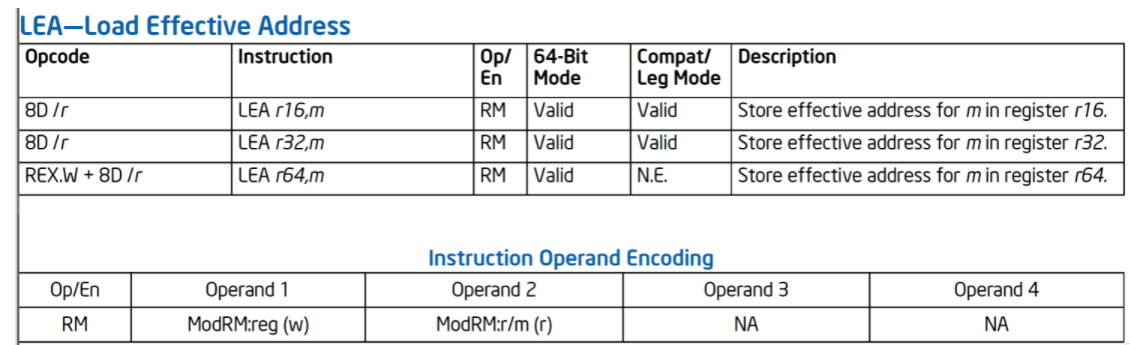
ea:Load Effective Address,That is, loading a valid address means that its operand is the address lea r32,dword ptr ds:[Memory number(address)] Assign a memory address to a 32-bit general-purpose register lea It's an address, mov It's value transfer. Pay attention to the difference
Memory
The amount of memory is so huge that each memory unit cannot have a name, so it is replaced by a number. We call the computer CPU 32-bit or 64 bit, which mainly refers to the width of the memory number, not the width of the register.
Many books say that it is called a 32-bit computer because the width of the register is 32 bits, which is inaccurate, because many registers are larger than 32 bits
Generally speaking, the 32-bit computer refers to the CPU word length of 32 bits
Each byte of computer memory will have a number (that is, the unit of memory number is bytes)
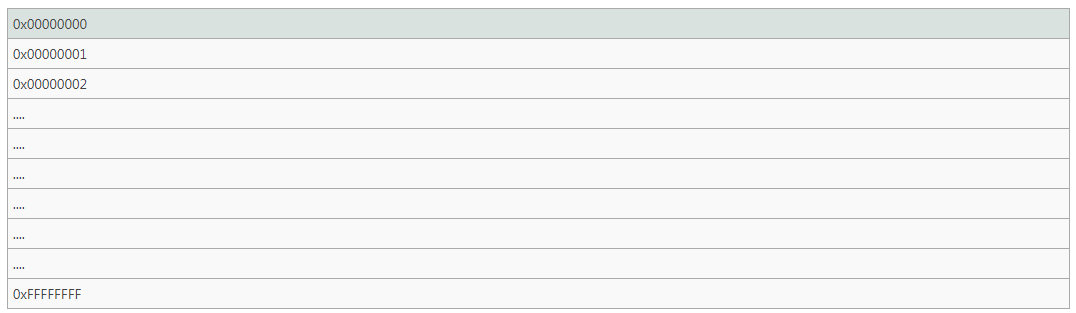
The maximum number of 32-bit computer is 32 bits, that is, 32 1s are replaced by hexadecimal FFFFFFFF, that is, the maximum range of memory addressing of 32-bit computer is ffffff + 1
The unit of memory is bytes. The maximum information that can be stored in memory is ffffff + 1 bytes, that is, 4G. This is why it is meaningless for us to have more than 4G physical memory on an XP system
As long as it is a 32-bit computer, the maximum recognized memory is 4G, right?
incorrect. You can patch or expand the operating system. The addressing mode is determined by the operating system
Memory format
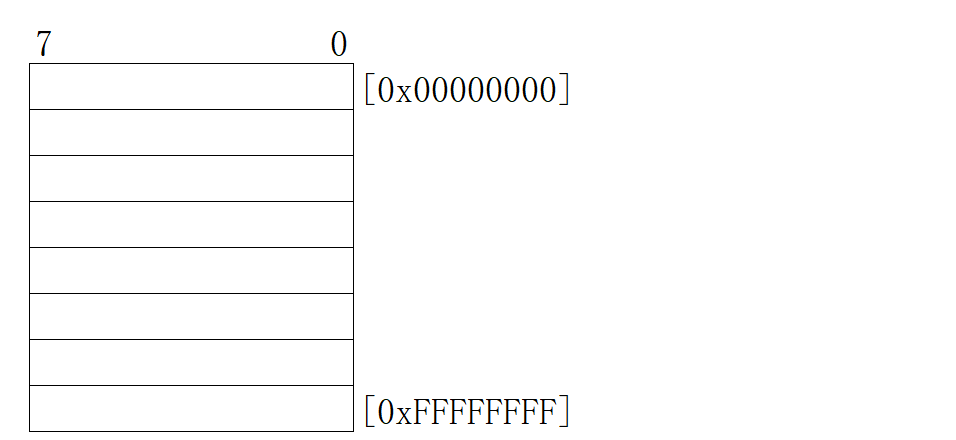
The width of each memory cell is 8 [number]Called address, with[]To separate the number and memory address Function of address: when we want to read data from memory or write data to memory, we should first find the location to read and write. It's like writing an address.
Write / read data from specified memory
As long as it involves memory reading and writing, be sure to specify the width of memory
mov read / write data width ptr ds: [address], XXXX
Example:
mov eax,dword ptr ds:[0x0012FF34] dword : To read/How much is 32 bit (byte Byte 8 bit word Word 16 bit dword Doubleword 32 bit) ds: Segment register here is data segment (segment register will be discussed later) 0x0012FF34 The memory number must be 32 bits, and the preceding 0 can be omitted Note: do not write the memory number casually, because the memory is protected, and not all memory can be read and written directly(Special treatment required)
Addressing formula
Addressing Formula 1: [immediate]
Read the value of memory:
MOV EAX,DWORD PTR DS:[0x13FFC4] MOV EAX,DWORD PTR DS:[0x13FFC8]
Write data to memory:
MOV DWORD PTR DS:[0x13FFC4],eax MOV DWORD PTR DS:[0x13FFC8],ebx
Get memory number:
LEA EAX,DWORD PTR DS:[0X13FFC4] LEA EAX,DWORD PTR DS:[ESP+8]
Addressing formula 2: [Register]
reg stands for register, which can be any of 8 general-purpose registers
Read the value of memory:
MOV ECX,0x13FFD0 MOV EAX,DWORD PTR DS:[ECX]
Write data to memory:
MOV EDX,0x13FFD8 MOV DWORD PTR DS:[EDX],0x87654321
Get memory number:
LEA EAX,DWORD PTR DS:[EDX]
Addressing formula 3: [reg + immediate]
Read the value of memory:
MOV ECX,0x13FFD0 MOV EAX,DWORD PTR DS:[ECX+4]
Write data to memory:
MOV EDX,0x13FFD8 MOV DWORD PTR DS:[EDX+0xC],0x87654321
Get memory number:
LEA EAX,DWORD PTR DS:[EDX+4]
Addressing formula 4: [reg+reg{1,2,4,8}]*
Read the value of memory:
MOV EAX,13FFC4 MOV ECX,2 MOV EDX,DWORD PTR DS:[EAX+ECX*4]
Write data to memory:
MOV EAX,13FFC4 MOV ECX,2 MOV DWORD PTR DS:[EAX+ECX*4],87654321
Get memory number:
LEA EAX,DWORD PTR DS:[EAX+ECX*4]
Addressing formula 5: [reg+reg{1,2,4,8} + immediate]*
Read the value of memory:
MOV EAX,13FFC4 MOV ECX,2 MOV EDX,DWORD PTR DS:[EAX+ECX*4+4]
Write data to memory:
MOV EAX,13FFC4 MOV ECX,2 MOV DWORD PTR DS:[EAX+ECX*4+4],87654321
Get memory number:
LEA EAX,DWORD PTR DS:[EAX+ECX*4+2]
More reverse shelling and software reverse learning articles are in the post link below. Welcome to communicate: