1, Introduction
In all the cases I mentioned before, the whole Azure Resource is deployed to the same subscription, and the environment to be deployed is not flexibly selected before the operation of Azure Pipeline. In the actual project development, we will also encounter that these infrastructure resources are deployed to DEV,UAT,PRD and other environments after verification. So let's start today's analysis with the whole problem.
--------------------I am the dividing line--------------------
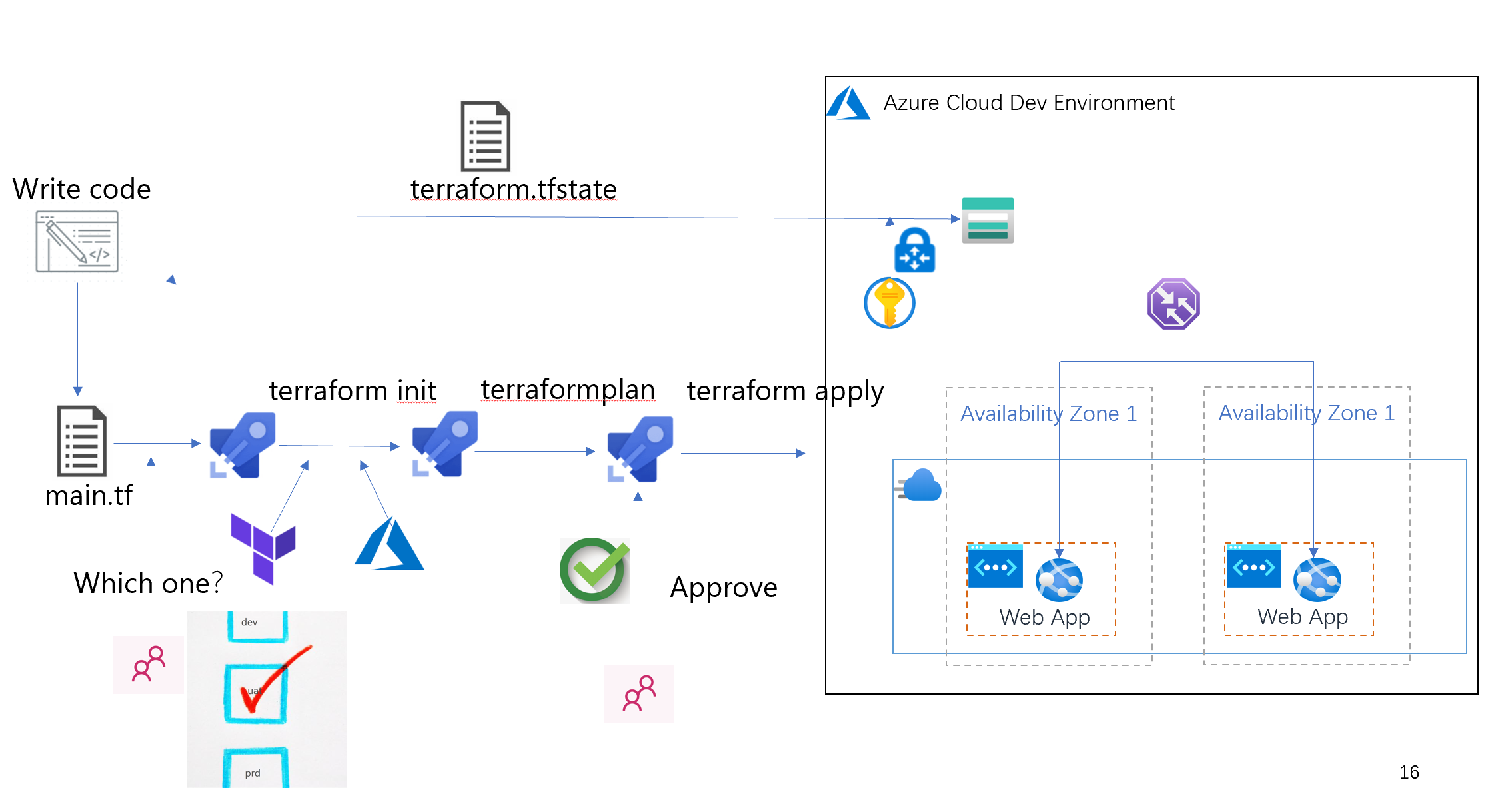
--------------------Azure terrain series--------------------
1. Introduction to azure terrain (I)
2. Detailed explanation of azure terrain (II) syntax
3. Azure Terraform (III) deploying Web applications
4. Azure terrain (IV) status file storage
5. Azure terrain (V) realize automatic deployment of basic resources by using Azure DevOps
6. Azure terrain (VI) Common Module
7. Azure terrain (VII) realize automatic deployment of basic resources by using Azure DevOps (supplementary)
8. Azure Terraform (VIII) uses Azure DevOps to realize Infra resources and NET CORE Web application continuous integration and deployment
9. Azure terrain (IX) uses the approval of Azure DevOps Pipeline to control the process release
10. Azure terrain (x) uses the conditional statements of Azure DevOps to select the publishing environment
2, Text
1. Conditional statements in Azure DevOps Pipeline
First, we need to define parameters to select which environment to use when Pipeline is running
parameters:
- name: deployEnv
displayName: Select a Deployment Environment???
type: string
default: 'dev'
values:
- dev
- uat
- prd
Next, the value of the variable setting the conditional statement can change according to the value of "deployEnv"
variables:
- name: tf_version
value: 'latest'
- name: env_name
${{ if eq(parameters['deployEnv'],'dev') }}:
value: 'dev'
${{elseif eq(parameters['DeployEnv'],'uat') }}:
value: 'uat'
${{elseif eq(parameters['DeployEnv'],'prd') }}:
value: 'prd'
The above two sections of code are not difficult for us to see, veriables env_ The value of name depends on parameters The value of deployenv is filtered by conditional statements and re assigned
Copy the above two pieces of code to azure pipelines In YML
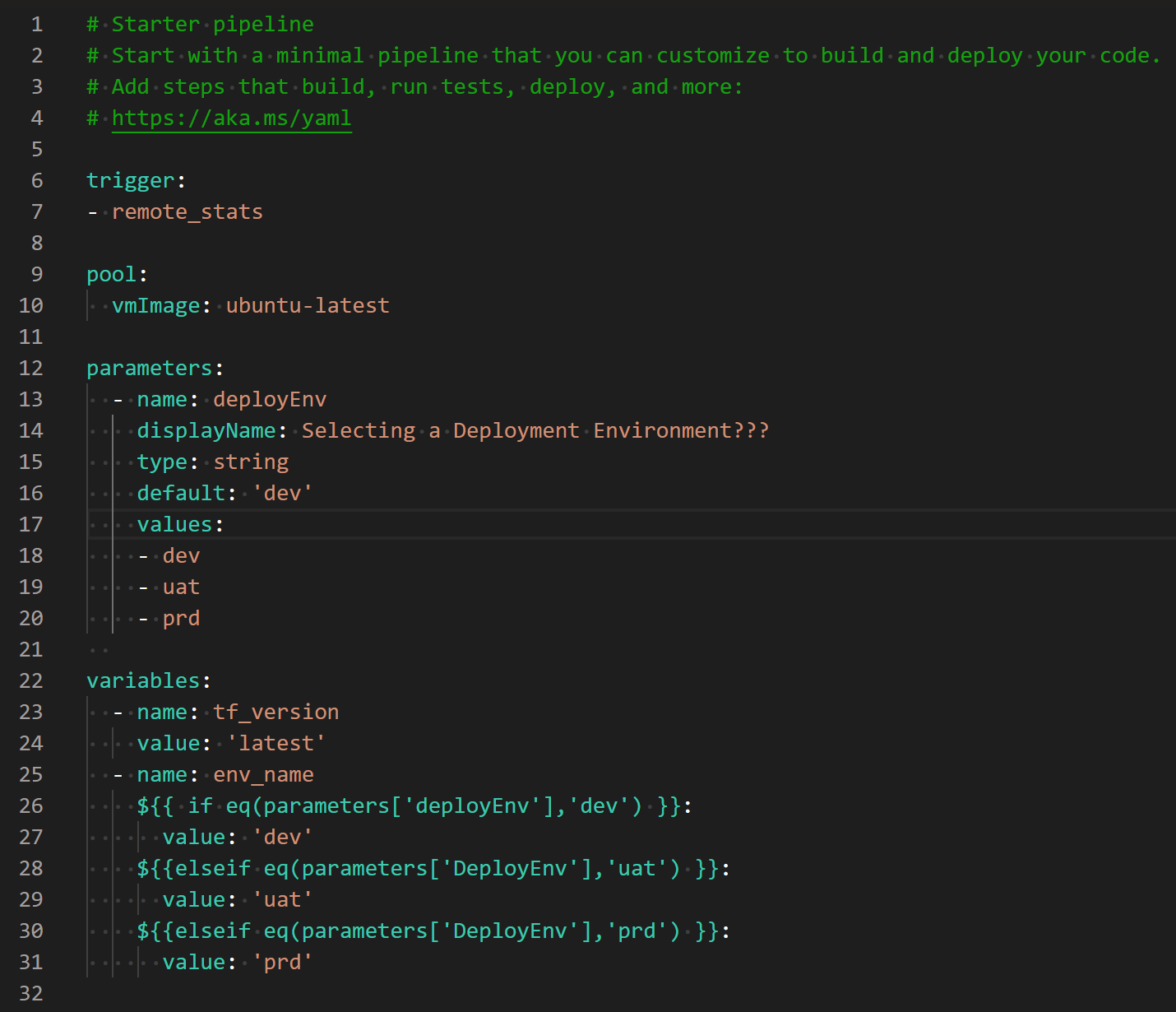
azure-pipeline.yml complete code
1 # Starter pipeline 2 # Start with a minimal pipeline that you can customize to build and deploy your code. 3 # Add steps that build, run tests, deploy, and more: 4 # https://aka.ms/yaml 5 6 trigger: 7 - remote_stats 8 9 pool: 10 vmImage: ubuntu-latest 11 12 parameters: 13 - name: deployEnv 14 displayName: Selecting a Deployment Environment??? 15 type: string 16 default: 'dev' 17 values: 18 - dev 19 - uat 20 - prd 21 22 variables: 23 - name: tf_version 24 value: 'latest' 25 - name: env_name 26 ${{ if eq(parameters['deployEnv'],'dev') }}: 27 value: 'dev' 28 ${{elseif eq(parameters['DeployEnv'],'uat') }}: 29 value: 'uat' 30 ${{elseif eq(parameters['DeployEnv'],'prd') }}: 31 value: 'prd' 32 33 stages: 34 - stage: script 35 jobs: 36 - job: azure_cli_script 37 steps: 38 - task: AzureCLI@2 39 displayName: 'Azure CLI :Create Storage Account,Key Vault And Set KeyVault Secret' 40 inputs: 41 azureSubscription: 'Microsoft Azure Subscription(xxxx-xxx-xxx-xxxx)' 42 scriptType: 'bash' 43 scriptLocation: 'inlineScript' 44 inlineScript: | 45 # create azure resource group 46 az group create --location eastasia --name $(terraform_rg) 47 48 # create azure storage account 49 az storage account create --name $(storage_account) --resource-group $(terraform_rg) --location eastasia --sku Standard_LRS 50 51 # create storage account container for tf state 52 az storage container create --name $(storage_account_container) --account-name $(storage_account) 53 54 # query storage key and set variable 55 ACCOUNT_KEY=$(az storage account keys list --resource-group $(terraform_rg) --account-name $(storage_account) --query "[?keyName == 'key1'][value]" --output tsv) 56 57 # create azure keyvault 58 az keyvault create --name $(keyvault) --resource-group $(terraform_rg) --location eastasia --enable-soft-delete false 59 60 # set keyvault secret,secret value is ACCOUNT_KEY 61 az keyvault secret set --name $(keyvault_sc) --vault-name $(keyvault) --value $ACCOUNT_KEY 62 63 - task: AzureKeyVault@2 64 displayName: 'Azure Key Vault :Get Storage Access Secret' 65 inputs: 66 azureSubscription: 'Microsoft Azure Subscription(xxxx-xxx-xxx-xxxx)' 67 KeyVaultName: '$(keyvault)' 68 SecretsFilter: 'terraform-stste-storage-key' 69 RunAsPreJob: false 70 71 - stage: terraform_validate 72 jobs: 73 - job: terraform_validate 74 steps: 75 - task: TerraformInstaller@0 76 inputs: 77 terraformVersion: ${{variables.tf_version}} 78 - task: TerraformTaskV2@2 79 displayName: 'terraform init' 80 inputs: 81 provider: 'azurerm' 82 command: 'init' 83 # commandOptions: '-backend-config="access_key=$(terraform-stste-storage-key)"' 84 backendServiceArm: 'Microsoft Azure Subscription(xxxx-xxx-xxx-xxxx)' 85 backendAzureRmResourceGroupName: $(terraform_rg) 86 backendAzureRmStorageAccountName: $(storage_account) 87 backendAzureRmContainerName: $(storage_account_container) 88 backendAzureRmKey: $(container_key) 89 workingDirectory: '$(System.DefaultWorkingDirectory)/src/model/' 90 - task: TerraformTaskV2@2 91 inputs: 92 provider: 'azurerm' 93 command: 'validate' 94 workingDirectory: '$(System.DefaultWorkingDirectory)/src/model/' 95 96 - stage: terraform_plan 97 dependsOn: [terraform_validate] 98 condition: succeeded('terraform_validate') 99 jobs: 100 - job: terraform_plan 101 steps: 102 - task: TerraformInstaller@0 103 inputs: 104 terraformVersion: ${{ variables.tf_version }} 105 - task: TerraformTaskV2@2 106 displayName: 'terraform init' 107 inputs: 108 provider: 'azurerm' 109 command: 'init' 110 # commandOptions: '-backend-config="access_key=$(terraform-stste-storage-key)"' 111 backendServiceArm: 'Microsoft Azure Subscription(xxxx-xxx-xxx-xxxx)' 112 backendAzureRmResourceGroupName: $(terraform_rg) 113 backendAzureRmStorageAccountName: $(storage_account) 114 backendAzureRmContainerName: $(storage_account_container) 115 backendAzureRmKey: $(container_key) 116 workingDirectory: '$(System.DefaultWorkingDirectory)/src/model/' 117 - task: TerraformTaskV2@2 118 inputs: 119 provider: 'azurerm' 120 command: 'plan' 121 environmentServiceNameAzureRM: 'Microsoft Azure Subscription(xxxx-xxx-xxx-xxxx)' 122 workingDirectory: '$(System.DefaultWorkingDirectory)/src/model/' 123 124 - stage: terraform_apply 125 dependsOn: [terraform_plan] 126 condition: succeeded('terraform_plan') 127 jobs: 128 - deployment: terraform_apply 129 continueOnError: false 130 environment: 'Approve_Production' 131 timeoutInMinutes: 120 132 strategy: 133 runOnce: 134 deploy: 135 steps: 136 - checkout: self 137 - task: TerraformInstaller@0 138 inputs: 139 terraformVersion: ${{ variables.tf_version }} 140 - task: TerraformTaskV2@2 141 displayName: 'terraform init' 142 inputs: 143 provider: 'azurerm' 144 command: 'init' 145 # commandOptions: '-backend-config="access_key=$(terraform-stste-storage-key)"' 146 backendServiceArm: 'Microsoft Azure Subscription(xxxx-xxx-xxx-xxxx)' 147 backendAzureRmResourceGroupName: $(terraform_rg) 148 backendAzureRmStorageAccountName: $(storage_account) 149 backendAzureRmContainerName: $(storage_account_container) 150 backendAzureRmKey: $(container_key) 151 workingDirectory: '$(System.DefaultWorkingDirectory)/src/model/' 152 - task: TerraformTaskV2@2 153 inputs: 154 provider: 'azurerm' 155 command: 'plan' 156 environmentServiceNameAzureRM: 'Microsoft Azure Subscription(xxxx-xxx-xxx-xxxx)' 157 workingDirectory: '$(System.DefaultWorkingDirectory)/src/model/' 158 - task: TerraformTaskV2@2 159 inputs: 160 provider: 'azurerm' 161 command: 'apply' 162 commandOptions: '-auto-approve' 163 environmentServiceNameAzureRM: 'Microsoft Azure Subscription(xxxx-xxx-xxx-xxxx)' 164 workingDirectory: '$(System.DefaultWorkingDirectory)/src/model/' 165 166 # - stage: terraform_apply 167 # dependsOn: [terraform_plan] 168 # condition: succeeded('terraform_plan') 169 # jobs: 170 # - job: terraform_apply 171 # steps: 172 # - task: TerraformInstaller@0 173 # inputs: 174 # terraformVersion: ${{ variables.tf_version }} 175 # - task: TerraformTaskV2@2 176 # displayName: 'terraform init' 177 # inputs: 178 # provider: 'azurerm' 179 # command: 'init' 180 # # commandOptions: '-backend-config="access_key=$(terraform-stste-storage-key)"' 181 # backendServiceArm: 'Microsoft Azure Subscription(xxxx-xxx-xxx-xxxx)' 182 # backendAzureRmResourceGroupName: $(terraform_rg) 183 # backendAzureRmStorageAccountName: $(storage_account) 184 # backendAzureRmContainerName: $(storage_account_container) 185 # backendAzureRmKey: $(container_key) 186 # workingDirectory: '$(System.DefaultWorkingDirectory)/src/model/' 187 # - task: TerraformTaskV2@2 188 # inputs: 189 # provider: 'azurerm' 190 # command: 'plan' 191 # environmentServiceNameAzureRM: 'Microsoft Azure Subscription(xxxx-xxx-xxx-xxxx)' 192 # workingDirectory: '$(System.DefaultWorkingDirectory)/src/model/' 193 # - task: TerraformTaskV2@2 194 # inputs: 195 # provider: 'azurerm' 196 # command: 'apply' 197 # commandOptions: '-auto-approve' 198 # environmentServiceNameAzureRM: 'Microsoft Azure Subscription(xxxx-xxx-xxx-xxxx)' 199 # workingDirectory: '$(System.DefaultWorkingDirectory)/src/model/' 200 201 - stage: terraform_destroy 202 dependsOn: [terraform_apply] 203 condition: succeeded('terraform_apply') 204 jobs: 205 - job: terraform_destroy 206 steps: 207 - task: TerraformInstaller@0 208 inputs: 209 terraformVersion: ${{ variables.tf_version }} 210 - task: TerraformTaskV2@2 211 displayName: 'terraform init' 212 inputs: 213 provider: 'azurerm' 214 command: 'init' 215 # commandOptions: '-backend-config="access_key=$(terraform-stste-storage-key)"' 216 backendServiceArm: 'Microsoft Azure Subscription(xxxx-xxx-xxx-xxxx)' 217 backendAzureRmResourceGroupName: $(terraform_rg) 218 backendAzureRmStorageAccountName: $(storage_account) 219 backendAzureRmContainerName: $(storage_account_container) 220 backendAzureRmKey: $(container_key) 221 workingDirectory: '$(System.DefaultWorkingDirectory)/src/model/' 222 - task: TerraformTaskV2@2 223 inputs: 224 provider: 'azurerm' 225 command: 'plan' 226 environmentServiceNameAzureRM: 'Microsoft Azure Subscription(xxxx-xxx-xxx-xxxx)' 227 workingDirectory: '$(System.DefaultWorkingDirectory)/src/model/' 228 - task: TerraformTaskV2@2 229 inputs: 230 provider: 'azurerm' 231 command: 'destroy' 232 commandOptions: '-auto-approve' 233 environmentServiceNameAzureRM: 'Microsoft Azure Subscription(xxxx-xxx-xxx-xxxx)' 234 workingDirectory: '$(System.DefaultWorkingDirectory)/src/model/'
2. Running effect of Azure Pipeline conditional statement
After saving the yml file, click "Run" to manually trigger the Pipeline
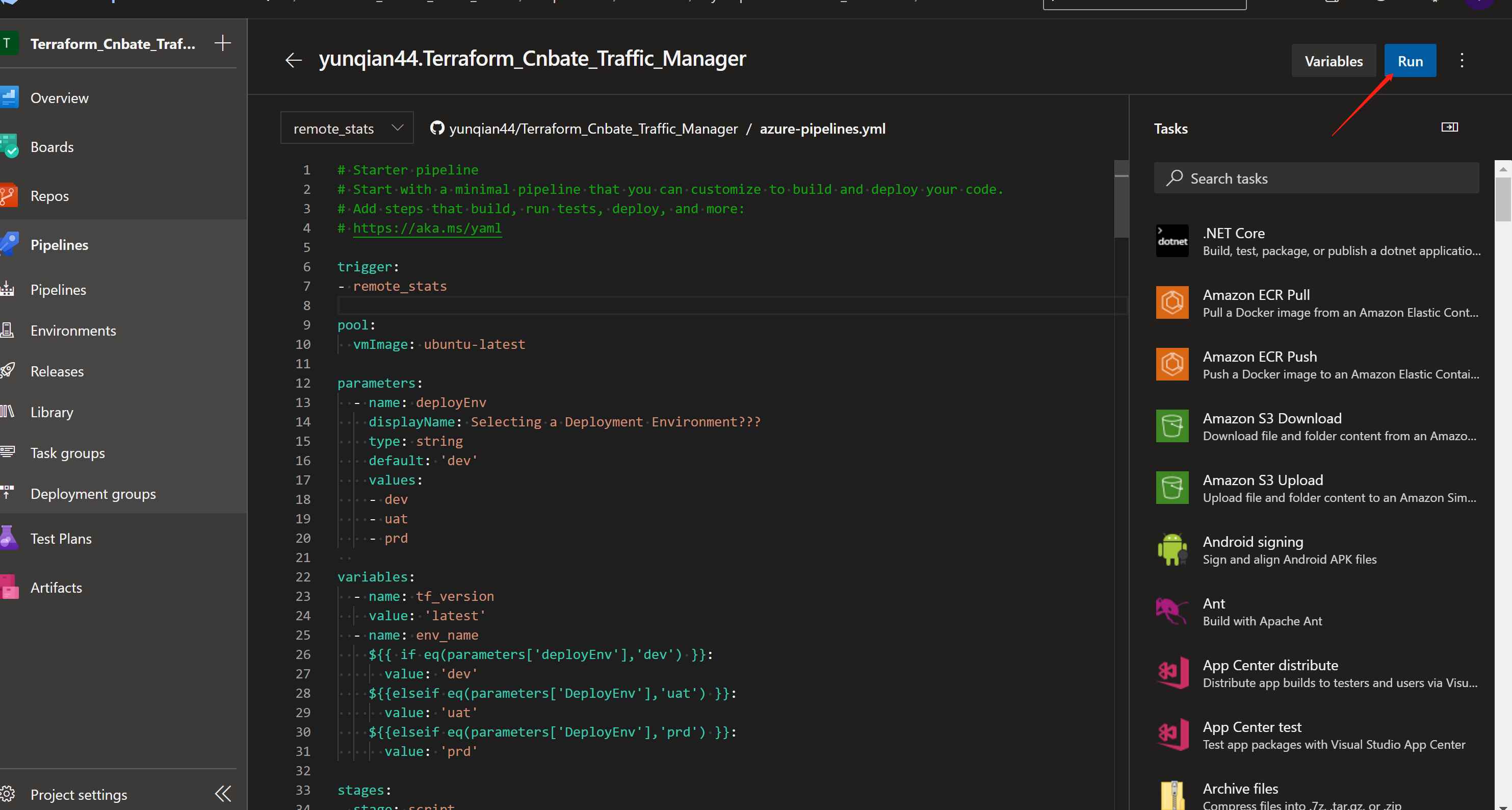
You can see that in addition to the default branch of the default Run pipeline, you also need to select our customized parameters - "deployenv"
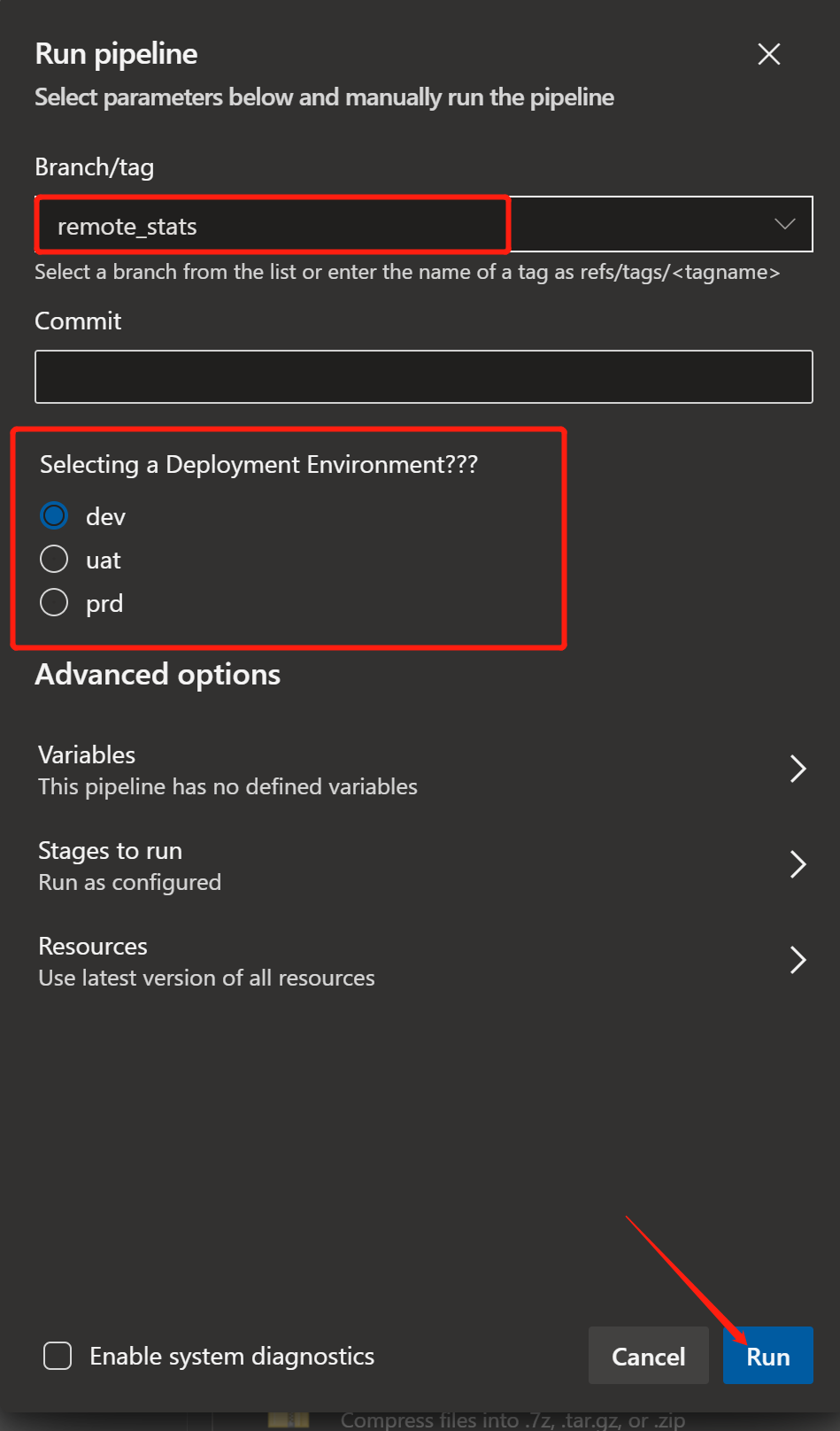
bingo !! Our goal has been achieved. Through the judgment of this conditional statement, we can replace some deployment variables, so as to achieve the purpose of deploying different environments.
3, End
Let's practice more about the above contents. In the next article, we will continue to introduce the deployment of Azure Pipeline in multiple environments
reference material: Terraform official,Azure Pipeline document
Terraform_Cnbate_Traffic_Manager github Address: https://github.com/yunqian44/Terraform_Cnbate_Traffic_Manager
Welcome to the blogger's blog: https://allenmasters.com/
Author: Allen
Copyright: please indicate the author and source in the obvious position of the article. If mistakes are found, criticism and correction are welcome.