preface
The day before yesterday, a test web page was added to the W800 project( Modify web page configuration on W800 development board ), how to make the W800 development board interact with this web page. I studied for a day yesterday and got it.
There are few programming materials for the online W800 application layer, so I found one, and the student talked about his ideas. It is of little use for actual engineering maintenance.
winnermicro official sdkwm_ sdk_ w800_ The rotated array file (wm_sdk_w800_20210513\src\app\web\fsdata_lwip.c) in 20210513 does not match the html(wm_sdk_w800_20210513\src\app\web\fs_basic*.html) in the project. Convert the html in the project into fsdata_lwip.c, the compiled project can not realize the interaction of web page fields This should be a mistake of WM's official research and development. It's a bug But we are also R & D. I understand this situation. The project is so large that without a full-time test team, it is difficult to test all bugs in the project In particular, this problem needs to be tested by R & D. Professional test engineers only test finished products because they are not R & D. It is difficult to find such code problems.
If the original fsdata in the project is used_ lwip. c. It can realize web page field interaction. But demo is demo, fsdata_lwip.c is already an array. I don't know what the original content is. If you want to add a few fields, or make a new web page for your front-end colleagues, and then turn html into fsdata_lwip.c. Even if the fields are consistent with the original fields, the interaction of web pages cannot be realized after compilation.
Specifically, why can't we interact? We need to understand the implementation of the W800 official project and find out the points that can't interact and repair them.
Because I didn't buy the CK-LINK debugger, I can only rely on the debugging information printed out by W800 serial port 0 and analyze it together with the code. Yesterday from morning till 2:30 at night It's enough trouble.
There are many details of web page interaction on W800. The access of each html field should be controlled by itself. There are a lot of maintenance points. It's OK to make a small web page. There are too many html fields. It's really uncomfortable.
experiment
I used local git for version control. I have now exported the archived original W800SDK version and the now prepared W800SDK version, compared them with BC4, and recorded the modification points. Regardless of the order of modification points, they are written to where they are compared according to the file list order of BC4.
Experimental html, use the html made in the last blog( Modify web page configuration on W800 development board)
Modify point - turn on the required compilation switch
wm_sdk_w800_20210513\demo\wm_demo.h
//demo console #define DEMO_CONSOLE DEMO_ON //connect demo #define DEMO_CONNECT_NET (DEMO_ON && DEMO_CONSOLE) //http demo #define DEMO_HTTP (DEMO_ON && DEMO_CONSOLE)
Modify point - confirm whether the hotspot and other wifi connections are successful
During debugging, it is found that the W800 does not succeed in establishing wifi hotspots and connecting external wifi hotspots every time.
You need to print debugging information in the code for establishing wifi hotspots and connecting external wifi hotspots. If this is not successful, connect again.
In my experiment, I'm sure I can connect successfully within 3 times. Most of them can connect successfully at one time.
wm_sdk_w800_20210513\demo\wm_softap_demo.c
MEMCPY(ipinfo->dnsname, "local.wm", sizeof("local.wm"));
ret = tls_wifi_softap_create(apinfo, ipinfo);
wm_printf("\n2 ap create %s ! \n", (ret == WM_SUCCESS) ? "Successfully" : "Error");
wm_sdk_w800_20210513\demo\wm_apsta_demo.c
ret = tls_wifi_softap_create((struct tls_softap_info_t * )&apinfo, (struct tls_ip_info_t * )&ipinfo);
wm_printf("\n1 ap create %s ! \n", (ret == WM_SUCCESS) ? "Successfully" : "Error");
return ret;
}
static int connect_wifi_demo(char *ssid, char *pwd)
{
Modification point - add the access location index of web page field in on-chip FLASH
wm_sdk_w800_20210513\include\platform\wm_params.h
/** BT&BLE param */ #define TLS_PARAM_ID_BT_ADAPTER (55) #define TLS_PARAM_ID_BT_REMOTE_DEVICE_1 (56) // #define TLS_PARAM_ID_BT_REMOTE_DEVICE_2 (57) // #define TLS_PARAM_ID_BT_REMOTE_DEVICE_3 (58) // #define TLS_PARAM_ID_BT_REMOTE_DEVICE_4 (59) // #define TLS_PARAM_ID_BT_REMOTE_DEVICE_5 (60) // #define TLS_PARAM_ID_BT_REMOTE_DEVICE_6 (61) // #define TLS_PARAM_ID_BT_REMOTE_DEVICE_7 (62) // #define TLS_PARAM_ID_BT_REMOTE_DEVICE_8 (63) // #define TLS_PARAM_ID_BT_REMOTE_DEVICE_9 (64) // #define TLS_PARAM_ID_BT_REMOTE_DEVICE_10 (65) #define TLS_PARAM_ID_MY_PARAM1 (57) #define TLS_PARAM_ID_MY_PARAM2 (58) #define TLS_PARAM_ID_MY_PARAM3 (59) #define TLS_PARAM_ID_MY_PARAM4 (60) #define TLS_PARAM_ID_MY_PARAM5 (61) #define TLS_PARAM_ID_MY_PARAM6 (62) #define TLS_PARAM_ID_MY_PARAM7 (63) #define TLS_PARAM_ID_MY_PARAM8 (64) #define TLS_PARAM_ID_MY_PARAM9 (65) #define TLS_PARAM_ID_MY_PARAM10 (66) #define TLS_PARAM_ID_MAX (67)
TLS should be commented out here_ PARAM_ ID_ BT_ REMOTE_ DEVICE_ 2 ~ TLS_ PARAM_ ID_ BT_ REMOTE_ DEVICE_ 10. If you add a little more variables, after W800 downloads the firmware, there will be a CPU exception and hang up.
My first feeling was that I used too much memory. I tried it and it turned out to be. When debugging, I feel it is very important to set a correct experimental direction and avoid detours.
void UserMain(void)
{
printf("\n>> UserMain() \n");
printf("\n test_w800 V2021_0624_2220\n");
printf("\nsizeof(bt_remote_device_t) = %d\n", sizeof(bt_remote_device_t));
#if DEMO_CONSOLE
CreateDemoTask();
#endif
//User's own task
}
Print TLS in UserMain()_ PARAM_ ID_ BT_ REMOTE_ DEVICE_ The size of the variable structure corresponding to X is 220 bytes each.
The original implementation of W800 is to add five TLS_ PARAM_ ID_ BT_ REMOTE_ DEVICE_ 10. However, there are still five macros to comment out. After I added my own field and hung up, I understood that the W800 R & D also found the problem of insufficient memory:)
Three TLS were removed_ PARAM_ ID_ BT_ REMOTE_ DEVICE_ 10. Added its own field variables, a 32 byte array of variables, plus 10. This time, I can run normally.
Add your own html field variables
wm_sdk_w800_20210513\platform\common\params\wm_param.h
bt_adapter_t adapter_t;
// sizeof(bt_remote_device_t) = 220
bt_remote_device_t remote_device1;
// Only 1 ~ 2 Bluetooth variables are reserved, or there is not enough memory
#if 0
bt_remote_device_t remote_device2;
bt_remote_device_t remote_device3;
bt_remote_device_t remote_device4;
bt_remote_device_t remote_device5;
bt_remote_device_t remote_device6;
bt_remote_device_t remote_device7;
bt_remote_device_t remote_device8;
bt_remote_device_t remote_device9;
bt_remote_device_t remote_device10;
#endif
// The memory space here is very tight, if the BT above_ remote_ device_ T there are 5, and the memory space is full
// Running again will crash, even if there is no code added elsewhere
char my_param1[32];
char my_param2[32];
char my_param3[32];
char my_param4[32];
char my_param5[32];
char my_param6[32];
char my_param7[32];
char my_param8[32];
char my_param9[32];
char my_param10[32];
};
struct tls_param_flash {
Modification point - add flash access to html field variables
wm_sdk_w800_20210513\platform\common\params\wm_param.c
There are several modification points in this file
case TLS_PARAM_ID_BT_REMOTE_DEVICE_1:
MEMCPY(&dest->remote_device1, &src->remote_device1, sizeof(bt_remote_device_t));
break;
#if 0
// case TLS_PARAM_ID_BT_REMOTE_DEVICE_2:
// MEMCPY(&dest->remote_device2, &src->remote_device2, sizeof(bt_remote_device_t));
// break;
// case TLS_PARAM_ID_BT_REMOTE_DEVICE_3:
// MEMCPY(&dest->remote_device3, &src->remote_device3, sizeof(bt_remote_device_t));
// break;
// case TLS_PARAM_ID_BT_REMOTE_DEVICE_4:
// MEMCPY(&dest->remote_device4, &src->remote_device4, sizeof(bt_remote_device_t));
// break;
// case TLS_PARAM_ID_BT_REMOTE_DEVICE_5:
// MEMCPY(&dest->remote_device5, &src->remote_device5, sizeof(bt_remote_device_t));
// break;
//
// case TLS_PARAM_ID_BT_REMOTE_DEVICE_6:
// MEMCPY(&dest->remote_device6, &src->remote_device6, sizeof(bt_remote_device_t));
// break;
//
// case TLS_PARAM_ID_BT_REMOTE_DEVICE_7:
// MEMCPY(&dest->remote_device7, &src->remote_device7, sizeof(bt_remote_device_t));
// break;
// case TLS_PARAM_ID_BT_REMOTE_DEVICE_8:
// MEMCPY(&dest->remote_device8, &src->remote_device8, sizeof(bt_remote_device_t));
// break;
// case TLS_PARAM_ID_BT_REMOTE_DEVICE_9:
// MEMCPY(&dest->remote_device9, &src->remote_device9, sizeof(bt_remote_device_t));
// break;
// case TLS_PARAM_ID_BT_REMOTE_DEVICE_10:
// MEMCPY(&dest->remote_device10, &src->remote_device10, sizeof(bt_remote_device_t));
// break;
#endif
case TLS_PARAM_ID_MY_PARAM1:
{
MEMCPY(&dest->my_param1, &src->my_param1, sizeof(src->my_param1));
}
break;
case TLS_PARAM_ID_MY_PARAM2:
{
MEMCPY(&dest->my_param2, &src->my_param2, sizeof(src->my_param2));
}
break;
case TLS_PARAM_ID_MY_PARAM3:
{
MEMCPY(&dest->my_param3, &src->my_param3, sizeof(src->my_param3));
}
break;
case TLS_PARAM_ID_MY_PARAM4:
{
MEMCPY(&dest->my_param4, &src->my_param4, sizeof(src->my_param4));
}
break;
case TLS_PARAM_ID_MY_PARAM5:
{
MEMCPY(&dest->my_param5, &src->my_param5, sizeof(src->my_param5));
}
break;
case TLS_PARAM_ID_MY_PARAM6:
{
MEMCPY(&dest->my_param6, &src->my_param6, sizeof(src->my_param6));
}
break;
case TLS_PARAM_ID_MY_PARAM7:
{
MEMCPY(&dest->my_param7, &src->my_param7, sizeof(src->my_param7));
}
break;
case TLS_PARAM_ID_MY_PARAM8:
{
MEMCPY(&dest->my_param8, &src->my_param8, sizeof(src->my_param8));
}
break;
case TLS_PARAM_ID_MY_PARAM9:
{
MEMCPY(&dest->my_param9, &src->my_param9, sizeof(src->my_param9));
}
break;
case TLS_PARAM_ID_MY_PARAM10:
{
MEMCPY(&dest->my_param10, &src->my_param10, sizeof(src->my_param10));
}
break;
default:
err = TLS_PARAM_STATUS_EINVALIDID;
goto exit;
}
#endif
flash_param.magic = TLS_PARAM_MAGIC;
flash_param.length = sizeof(flash_param);
if (modify_count < 0){
case TLS_PARAM_ID_BT_REMOTE_DEVICE_1:
MEMCPY(¶m->remote_device1, argv, sizeof(bt_remote_device_t));
break;
#if 0
// case TLS_PARAM_ID_BT_REMOTE_DEVICE_2:
// MEMCPY(¶m->remote_device2, argv, sizeof(bt_remote_device_t));
// break;
// case TLS_PARAM_ID_BT_REMOTE_DEVICE_3:
// MEMCPY(¶m->remote_device3, argv, sizeof(bt_remote_device_t));
// break;
// case TLS_PARAM_ID_BT_REMOTE_DEVICE_4:
// MEMCPY(¶m->remote_device4, argv, sizeof(bt_remote_device_t));
// break;
// case TLS_PARAM_ID_BT_REMOTE_DEVICE_5:
// MEMCPY(¶m->remote_device5, argv, sizeof(bt_remote_device_t));
// break;
//
// case TLS_PARAM_ID_BT_REMOTE_DEVICE_6:
// MEMCPY(¶m->remote_device6, argv, sizeof(bt_remote_device_t));
// break;
//
// case TLS_PARAM_ID_BT_REMOTE_DEVICE_7:
// MEMCPY(¶m->remote_device7, argv, sizeof(bt_remote_device_t));
// break;
// case TLS_PARAM_ID_BT_REMOTE_DEVICE_8:
// MEMCPY(¶m->remote_device8, argv, sizeof(bt_remote_device_t));
// break;
// case TLS_PARAM_ID_BT_REMOTE_DEVICE_9:
// MEMCPY(¶m->remote_device9, argv, sizeof(bt_remote_device_t));
// break;
// case TLS_PARAM_ID_BT_REMOTE_DEVICE_10:
// MEMCPY(¶m->remote_device10, argv, sizeof(bt_remote_device_t));
// break;
#endif
case TLS_PARAM_ID_MY_PARAM1:
{
MEMCPY(param->my_param1, argv, sizeof(param->my_param1));
}
break;
case TLS_PARAM_ID_MY_PARAM2:
{
MEMCPY(param->my_param2, argv, sizeof(param->my_param2));
}
break;
case TLS_PARAM_ID_MY_PARAM3:
{
MEMCPY(param->my_param3, argv, sizeof(param->my_param3));
}
break;
case TLS_PARAM_ID_MY_PARAM4:
{
MEMCPY(param->my_param4, argv, sizeof(param->my_param4));
}
break;
case TLS_PARAM_ID_MY_PARAM5:
{
MEMCPY(param->my_param5, argv, sizeof(param->my_param5));
}
break;
case TLS_PARAM_ID_MY_PARAM6:
{
MEMCPY(param->my_param6, argv, sizeof(param->my_param6));
}
break;
case TLS_PARAM_ID_MY_PARAM7:
{
MEMCPY(param->my_param7, argv, sizeof(param->my_param7));
}
break;
case TLS_PARAM_ID_MY_PARAM8:
{
MEMCPY(param->my_param8, argv, sizeof(param->my_param8));
}
break;
case TLS_PARAM_ID_MY_PARAM9:
{
MEMCPY(param->my_param9, argv, sizeof(param->my_param9));
}
break;
case TLS_PARAM_ID_MY_PARAM10:
{
MEMCPY(param->my_param10, argv, sizeof(param->my_param10));
}
break;
default:
TLS_DBGPRT_WARNING("invalid parameter id - %d!\n", id);
err = TLS_PARAM_STATUS_EINVALIDID;
goto exit;
}
if (to_flash && !updp_mode) {
err = param_to_flash(id, -1, -1);
TLS_DBGPRT_INFO("write the parameter to spi flash - %d.\n", err);
}
exit:
tls_os_sem_release(sys_param_lock);
return err;
}
/**********************************************************************************************************
* Description: This function is used to get system parameter.
*
* Arguments : id param id,from TLS_PARAM_ID_SSID to (TLS_PARAM_ID_MAX - 1)
* argc store parameters
* from_flash whether the parameter is readed from flash,1 read from flash
* Returns : TLS_PARAM_STATUS_OK success
* TLS_PARAM_STATUS_EINVALID invalid param
**********************************************************************************************************/
int tls_param_get(int id, void *argv, bool from_flash)
{
case TLS_PARAM_ID_BT_REMOTE_DEVICE_1:
MEMCPY(argv,&src->remote_device1, sizeof(bt_remote_device_t));
break;
#if 0
// case TLS_PARAM_ID_BT_REMOTE_DEVICE_2:
// MEMCPY(argv,&src->remote_device2, sizeof(bt_remote_device_t));
// break;
//
// case TLS_PARAM_ID_BT_REMOTE_DEVICE_3:
// MEMCPY(argv,&src->remote_device3, sizeof(bt_remote_device_t));
// break;
// case TLS_PARAM_ID_BT_REMOTE_DEVICE_4:
// MEMCPY(argv,&src->remote_device4, sizeof(bt_remote_device_t));
// break;
//
// case TLS_PARAM_ID_BT_REMOTE_DEVICE_5:
// MEMCPY(argv,&src->remote_device5, sizeof(bt_remote_device_t));
// break;
//
// case TLS_PARAM_ID_BT_REMOTE_DEVICE_6:
// MEMCPY(argv,&src->remote_device6, sizeof(bt_remote_device_t));
// break;
//
// case TLS_PARAM_ID_BT_REMOTE_DEVICE_7:
// MEMCPY(argv,&src->remote_device7, sizeof(bt_remote_device_t));
// break;
// case TLS_PARAM_ID_BT_REMOTE_DEVICE_8:
// MEMCPY(argv,&src->remote_device8, sizeof(bt_remote_device_t));
// break;
// case TLS_PARAM_ID_BT_REMOTE_DEVICE_9:
// MEMCPY(argv,&src->remote_device9, sizeof(bt_remote_device_t));
// break;
// case TLS_PARAM_ID_BT_REMOTE_DEVICE_10:
// MEMCPY(argv,&src->remote_device10, sizeof(bt_remote_device_t));
// break;
#endif
case TLS_PARAM_ID_MY_PARAM1:
{
MEMCPY(argv, src->my_param1, sizeof(src->my_param1));
}
break;
case TLS_PARAM_ID_MY_PARAM2:
{
MEMCPY(argv, src->my_param2, sizeof(src->my_param2));
}
break;
case TLS_PARAM_ID_MY_PARAM3:
{
MEMCPY(argv, src->my_param3, sizeof(src->my_param3));
}
break;
case TLS_PARAM_ID_MY_PARAM4:
{
MEMCPY(argv, src->my_param4, sizeof(src->my_param4));
}
break;
case TLS_PARAM_ID_MY_PARAM5:
{
MEMCPY(argv, src->my_param5, sizeof(src->my_param5));
}
break;
case TLS_PARAM_ID_MY_PARAM6:
{
MEMCPY(argv, src->my_param6, sizeof(src->my_param6));
}
break;
case TLS_PARAM_ID_MY_PARAM7:
{
MEMCPY(argv, src->my_param7, sizeof(src->my_param7));
}
break;
case TLS_PARAM_ID_MY_PARAM8:
{
MEMCPY(argv, src->my_param8, sizeof(src->my_param8));
}
break;
case TLS_PARAM_ID_MY_PARAM9:
{
MEMCPY(argv, src->my_param9, sizeof(src->my_param9));
}
break;
case TLS_PARAM_ID_MY_PARAM10:
{
MEMCPY(argv, src->my_param10, sizeof(src->my_param10));
}
break;
default:
TLS_DBGPRT_WARNING("invalid parameter id - %d!\n", id);
err = TLS_PARAM_STATUS_EINVALIDID;
break;
}
#if USE_TWO_RAM_FOR_PARAMETER
#else
if (curflashparm)
{
tls_mem_free(curflashparm);
}
#endif
tls_os_sem_release(sys_param_lock);
return err;
}
/**********************************************************************************************************
* Description: This function is used to write parameter to flash.
*
* Arguments : id param id,from TLS_PARAM_ID_ALL to (TLS_PARAM_ID_MAX - 1)
*
* Returns : * Returns : TLS_PARAM_STATUS_OK success
* TLS_PARAM_STATUS_EINVALID invalid param
* TLS_PARAM_STATUS_EIO error
**********************************************************************************************************/
int tls_param_to_flash(int id)
{
Modification point - add debugging information of wifi hotspot connection results
wm_sdk_w800_20210513\platform\sys\tls_sys.c
#if TLS_CONFIG_AP
case NETIF_WIFI_SOFTAP_SUCCESS:
TLS_DBGPRT_INFO("3 softap create success.\n");
tls_sys_net2_up();
break;
case NETIF_WIFI_SOFTAP_FAILED:
TLS_DBGPRT_INFO("4 softap create failed.\n");
tls_sys_net2_fail();
break;
case NETIF_WIFI_SOFTAP_CLOSED:
TLS_DBGPRT_INFO("softap closed.\n");
tls_sys_net2_down();
break;
case NETIF_IP_NET2_UP:
#if TLS_CONFIG_TLS_DEBUG
ethif = tls_netif_get_ethif2();
TLS_DBGPRT_INFO("net up ==> ip = %d.%d.%d.%d\n" ip4_addr1(ip_2_ip4
(ðif->ip_addr)), ip4_addr2(ip_2_ip4(ðif->ip_addr)),
ip4_addr3(ip_2_ip4(ðif->ip_addr)), ip4_addr4(ip_2_ip4(ðif
->ip_addr)));
#endif
break;
#endif
default:
break;
}
}
//-------------------------------------------------------------------------
int tls_sys_init()
{
Modify point - modify the wifi hotspot name you created
wm_sdk_w800_20210513\src\app\oneshotconfig\wm_wifi_oneshot.c
#define APSKT_MAX_ONESHOT_NUM (8) #define APSKT_SSID_MAX_LEN (32) #define ONESHOT_AP_NAME "my_ap"
Print debugging information of AP establishment results
/*END CONFIG_UDP_ONE_SHOT*/
#endif
#if TLS_CONFIG_AP_MODE_ONESHOT
int soft_ap_create(void)
{
struct tls_softap_info_t apinfo;
struct tls_ip_info_t ipinfo;
u8 ret=0;
u8 ssid_set = 0;
char ssid[33];
u8 mac_addr[6];
tls_get_mac_addr(mac_addr);
ssid[0]='\0';
u8 ssid_len = sprintf(ssid, "%s_%s_%s_%s_%s_%02x%02x", ONESHOT_AP_NAME, "192", "168", "8", "1", mac_addr[4], mac_addr[5]);
printf("\nssid_len = %d\n", ssid_len);
tls_param_get(TLS_PARAM_ID_BRDSSID, (void *)&ssid_set, (bool)0);
if (0 == ssid_set)
{
ssid_set = 1;
tls_param_set(TLS_PARAM_ID_BRDSSID, (void *)&ssid_set, (bool)1); /*Set BSSID broadcast flag*/
}
memset(&apinfo, 0, sizeof(struct tls_softap_info_t));
MEMCPY(apinfo.ssid, ssid, ssid_len);
apinfo.ssid[ssid_len]='\0';
apinfo.encrypt = 0; /*0:open, 1:wep64, 2:wep128*/
apinfo.channel = 5; /*channel random*/
/*ip information: ip address?ê?netmask?ê?dns*/
// After the soft ap is established, the IP address cannot be 192.168.1.1 Because the general network is 192.168.1 x
ipinfo.ip_addr[0] = 192;
ipinfo.ip_addr[1] = 168;
ipinfo.ip_addr[2] = 8;
ipinfo.ip_addr[3] = 1;
ipinfo.netmask[0] = 255;
ipinfo.netmask[1] = 255;
ipinfo.netmask[2] = 255;
ipinfo.netmask[3] = 0;
MEMCPY(ipinfo.dnsname, "local.wm", sizeof("local.wm"));
ret = tls_wifi_softap_create((struct tls_softap_info_t* )&apinfo, (struct tls_ip_info_t* )&ipinfo);
printf("\n5 ap create %s ! \n", (ret == WM_SUCCESS)? "Successfully" : "Error");
return ret;
}
#if TLS_CONFIG_SOCKET_MODE
Modify point - Open http debugging information
Because you didn't buy a hardware debugger, you need to print debugging information, so that you can know what you're returning when http returns the package.
wm_sdk_w800_20210513\src\app\web\httpd.h
#define INCLUDE_HTTPD_DEBUG #ifdef INCLUDE_HTTPD_DEBUG #define DEBUG_PRINT printf #else #define DEBUG_PRINT(s, ...) #endif
Modification point - html file needs to be processed with live data
When the http request is sent to the W800 project, you need to judge which html needs to live the data and make a mark.
If you do not need to reactivate data, you can directly return to fsdata_lwip.c defined fixed data.
wm_sdk_w800_20210513\src\app\web\httpd.c
The flag that needs to reactivate data is FILEFLAG_FILTER
#endif
// If there is a filter flag, these values should be from the saved parameters
if (hs->file_flag & FILEFLAG_FILTER)
{
int memlen=len+10;
Temp=mem_malloc(memlen);
if(Temp==NULL)
{
err = ERR_MEM;
return;
}
do {
#if 1
int templen=0,j=0;
filelen=0;
memset(Temp,0,memlen);
do
/*
* We found a CGI that handles this URI so extract the
* parameters and call the handler.
*/
count = extract_uri_parameters(hs, params);
strcpy(Url, g_pCGIs[i].pfnCGIHandler(i, count, hs->params, hs->param_vals,&NeedRestart));
if(NeedRestart==1)
{
send_jump_html(hs,pcb);
DEBUG_PRINT("Sending jump html\n\r");
resethandler();
return 0;
}
break;
}
}
}
#endif
DEBUG_PRINT("ls debug : Opening %s\n\r", Url);
file = fs_open(Url);
// If it is a file to get the latest data from the parameter area, bring FILEFLAG_FILTER tag
// "Hed" here, we used to judge whether the HTML name contains "hed", which can explain why the index comes with the project The src specified by frame in html is hedbasic HTML, but why is hedbasic not provided in the HTML directory of the SDK html? How does this make users play?
if (strstr(Url, "basic.html")){
hs->file_flag |= FILEFLAG_FILTER;
}
if(file == NULL) {
file = fs_open("/404.html");
}
#ifdef INCLUDE_HTTPD_SSI
else {
Modification point - determines which array the fixed packet is c Documents
wm_sdk_w800_20210513\src\app\web\fs.c
#ifdef FSDATA_IN_EXT_FLASH #define FS_ROOT (FSDATA_BASE_ADDR+4) #else #if WEB_SERVER_RUSSIAN // #include "fsdata_lwip_russian.c" #elif WEB_SERVER_BASIC // #include "fsdata_lwip_basic.c" #elif WEB_SERVER_RUIGONG // #include "fsdata_lwip_ruigong.c" #else #include "fsdata_lwip.c" / / through the shielding method, it can be seen that this is used by default in the project c. If you regenerate (html to. c), you should also generate this file with the same name #endif #endif // Web_parse_line I changed it and added a parameter tableid // If you understand the process of web page interaction, this function does not need to be changed, but only for debugging. extern u16 Web_parse_line(char * id_char,u16 * after_id_len,char * idvalue,u16 * Value_Offset,u8 * Id_type, u8* tableid);
To understand the splicing principle when the packet back is live data, you need to add some debugging statements
All packets are returned in fs_read_line(), the version I added debugging information is as follows
Only when you understand this function can you understand the web_ parse_ Web used in line_ id_ How to fill in the read-write definition of the new field in TBL []?
I think it took a long time to splice the package back. At this time, it highlights how cool it is to have a hardware debugger. It's worth spending money to buy time. Sometimes it's worth a try.
There was also a project in the past. Because the anti debugging restriction was made in the running environment, it was necessary to check the logic errors by typing the file log. It took three days to write 500 lines of code for a plug-in module before it was written correctly.
/*-----------------------------------------------------------------------------------
// Description: Read one line text into buffer s, and return its length
// Parameters: file:
char buffer :buffer to store the text read from file
// max_length: max length of one line
*/
int fs_read_line(const void *ori_data, char *buffer, int max_length, int *tembuflen)
{
#define MAX_ID_VALUE_BUFFER_LEN 2048
int len=0;
char * temp, *data = NULL;
char * idvaluebuffer=NULL;///[MAX_ID_BUFFER_LEN];
u16 beforeidlen=0;
u16 Idlen=0;
u16 startatfteid=0;
u16 Lenchange=0;
u8 IdType=0;
u8 u8_tableid = 0;
#ifdef FSDATA_IN_EXT_FLASH
data = ext_flash_read_line((unsigned int)ori_data);
#else
data = (char *)ori_data;
#endif
if(*tembuflen >= 1024)
{
return -1;
}
idvaluebuffer = mem_malloc(MAX_ID_VALUE_BUFFER_LEN);
if(idvaluebuffer == NULL)
{
return -1;
}
memset(idvaluebuffer, 0, MAX_ID_VALUE_BUFFER_LEN);
temp = (char *)data;
while(*temp++ != '\n')
{
if(*temp == 'i' && *(temp+1) == 'd' && *(temp+2) == '=')
{
if(*(temp+3) == '"')
{
printf("\n >> (temp+4) = %c%c%c%c%c%c%c%c%c%c\n",
temp[4 + 0],
temp[4 + 1],
temp[4 + 2],
temp[4 + 3],
temp[4 + 4],
temp[4 + 5],
temp[4 + 6],
temp[4 + 7],
temp[4 + 8],
temp[4 + 9]);
u8_tableid = 0;
Idlen=Web_parse_line(temp+4,&beforeidlen,idvaluebuffer,&startatfteid,&IdType, &u8_tableid);
if ((u8_tableid >= 67 /*Web_Id_my_param1*/) && (u8_tableid <= 76 /*Web_Id_my_param10*/)) {
printf("\nWeb_parse_line from Web_Id_my_param1 to Web_Id_my_param10, u8_tableid = %d\n", u8_tableid);
printf("\nidvaluebuffer = %s\n", idvaluebuffer);
}
if(Idlen!=0)
{
if(Idlen>startatfteid)
{
Lenchange=Idlen-startatfteid;
}
beforeidlen+=(len+1);
}
}
}
len++;
}
len++;
printf("\nIdType = %d\n", IdType);
if(IdType==0x00)
{
printf("\nlen = %d, Lenchange = %d, beforeidlen = %d, startatfteid = %d\n", len, Lenchange, beforeidlen, startatfteid);
if (len+Lenchange<= max_length)
{
if(Idlen==0)
{
printf("\nIdlen == 0, copy old html\n");
memcpy(buffer, data, len);
* tembuflen+=len;
}
else
{
printf("\nIdlen = %d, copy new html\n", Idlen);
printf("\nbeforeidlen = %d\n", beforeidlen);
printf("\n1. buffer = %s\n", buffer);
memcpy(buffer,data,beforeidlen);
printf("\n2. buffer = %s\n", buffer);
* tembuflen+=beforeidlen;
strcpy(buffer+beforeidlen,idvaluebuffer);
printf("\n3. buffer = %s\n", buffer);
* tembuflen+=Idlen;
memcpy(buffer+beforeidlen+Idlen,((char *)data+beforeidlen+startatfteid),(len-beforeidlen-startatfteid));
printf("\n4. buffer = %s\n", buffer);
* tembuflen+=(len-beforeidlen-startatfteid);
}
}
else
{
printf("\nlen = -1\n");
len = -1;
}
}
else if(IdType==0x01)
{
if(beforeidlen+Lenchange<= max_length)
{
if(Idlen==0)
{
memcpy(buffer, data, len);
* tembuflen+=len;
}
else
{
memcpy(buffer,data,beforeidlen);
* tembuflen+=beforeidlen;
strcpy(buffer+beforeidlen,idvaluebuffer);
* tembuflen+=Idlen;
}
}
else
{
len = -1;
}
}
else
{
len = -1;
}
if(idvaluebuffer)
mem_free(idvaluebuffer);
return len;
}
Main implementation of modification point web page field interaction logic
wm_sdk_w800_20210513\src\app\web\web.c
ID_VALUE is the field processing information to be filled in when adding an html field.
Understand FS_ read_ The ID can be understood through the back packet splicing processing of line()_ How to fill in value. I annotated and gave examples.
typedef struct _ID_VALUE{
// Data format of key value
// id="Ssid" value="my_wifi"
char *IdName; // Name of id "Ssid"
u8 tableid; // Index of id e.g. Web_Id_my_param1
u8 Idlen; // The length of id="Ssid" value = "plus the Idlen length will reach the actual value of copy value
u8 Value_Offset; // Value initializes the length of the value. If you skip this length, you can splice the values after the original html value
// For the following key value
// id="Ssid" value="value_at_init"
// IdName = "Ssid"
// tableid is defined by itself, as long as it is related to the web_ id_ If only the location index in TBL is the same
// Idlen = len(id="Ssid" value=") = 17
// Value_Offset = len(value_at_init) = 13
} ID_VALUE;
Add field index
#define Web_Id_my_param1 67 #define Web_Id_my_param2 68 #define Web_Id_my_param3 69 #define Web_Id_my_param4 70 #define Web_Id_my_param5 71 #define Web_Id_my_param6 72 #define Web_Id_my_param7 73 #define Web_Id_my_param8 74 #define Web_Id_my_param9 75 #define Web_Id_my_param10 76 #define ENCRYPT_TYPE_OPEN_SYS 0///open #define ENCRYPT_TYPE_WEP_64_BITS 1 #define ENCRYPT_TYPE_WEP_128_BITS 2
Add field definitions to process
{
"AutoHiden",
Web_AutoHidden_Id,
22,
1,
},
// my 10 param
{
"my_param1",
Web_Id_my_param1,
22,
6,
},
{
"my_param2",
Web_Id_my_param2,
22,
6,
},
{
"my_param3",
Web_Id_my_param3,
22,
6,
},
{
"my_param4",
Web_Id_my_param4,
22,
6,
},
{
"my_param5",
Web_Id_my_param5,
22,
6,
},
{
"my_param6",
Web_Id_my_param6,
22,
6,
},
{
"my_param7",
Web_Id_my_param7,
22,
6,
},
{
"my_param8",
Web_Id_my_param8,
22,
6,
},
{
"my_param9",
Web_Id_my_param9,
22,
6,
},
{
"my_param10",
Web_Id_my_param10,
23,
7,
}
#if 0
,
NULL,
#endif
};
#if 0
char * Encry_Open[]={
Processing of changing packet back data to survival data
Web_parse_line() function adds the processing of packet return field
Debugging statements and added tableid outgoing parameters are debugging, not required.
Web_ parse_ The line () function is relatively large because it is handled by switch case. The more variables, the longer the function.
You can remove the html fields provided in the demo that we don't use, so as to save some code space.
Will Web_parse_line() all posted here.
u16 Web_parse_line(char * id_char,u16 * after_id_len,char * idvalue,u16 * Value_Offset,u8 * Id_type, u8* tableid)
{
/*
char idbuffer[MAX_ID_BUFFER_LEN];
u8 j=0, mode, encrypt;
ID_VALUE *idtble;
u8 tableid=0;
struct tls_param_ip ip_param;
short channellist;
struct tls_param_key param_key;
u8 auto_mode;
struct tls_param_socket remote_socket_cfg;
struct tls_param_bssid bssid;
struct tls_param_uart uart_cfg;
*/
char idbuffer[MAX_ID_BUFFER_LEN];
u8 j=0, mode;//, encrypt;
ID_VALUE *idtble;
// u8 tableid=0;
struct tls_param_ip ip_param;
struct tls_param_key param_key;
int k;
// printf("\n>> Web_parse_line(after_id_len = %d, id_char = %s)\n", after_id_len, (NULL != id_char) ? id_char : "NULL");
// printf("\n>> Web_parse_line(after_id_len = %d, id_char)\n", after_id_len);
memset(idbuffer,0,MAX_ID_BUFFER_LEN);
* Id_type=0;
while(*(id_char+j)!='"')
{j++;}
memcpy(idbuffer,id_char,j);
for (k = 0; k < sizeof(web_id_tbl) / sizeof(ID_VALUE); k++)
{
idtble = (ID_VALUE *)&web_id_tbl[k];
if (strcmp(idbuffer,idtble->IdName) == 0)
{
*tableid=idtble->tableid;
break;
}
}
//#if 0
// for (idtble = (ID_VALUE *)&web_id_tbl[0]; idtble->IdName; idtble++)
// {
// if (strcmp(idbuffer,idtble->IdName) == 0)
// {
// tableid=idtble->tableid;
// break;
// }
// }
//#endif
printf("###kevin debug Web_parse_line = %s\n\r",idbuffer);
tls_param_get(TLS_PARAM_ID_IP, &ip_param, FALSE);
switch((int)(*tableid))
{
case Dhcp_Id:
/*
tls_param_get(TLS_PARAM_ID_WPROTOCOL, (void* )&mode, FALSE);
if(ip_param.dhcp_enable)
{
sprintf(idvalue, "οnclick=\"dhcp1()\" value=\"1\" checked=\"CHECKED\" %s/>Auto IP Enable</label></td>\n", mode==IEEE80211_MODE_AP ? "disabled=\"disabled\" " : "");
}
else
{
sprintf(idvalue, "οnclick=\"dhcp1()\" value=\"1\" %s/>Auto IP Enable</label></td>\n", mode==IEEE80211_MODE_AP ? "disabled=\"disabled\" " : "");
}
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
* Id_type=0x01;
*/
break;
case Web_Ip_Id:
/*
tls_param_get(TLS_PARAM_ID_WPROTOCOL, (void* )&mode, FALSE);
if(!ip_param.dhcp_enable || mode==IEEE80211_MODE_AP)
{
sprintf(idvalue, "%d.%d.%d.%d", \
ip_param.ip[0], ip_param.ip[1],\
ip_param.ip[2], ip_param.ip[3]);
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
}
else
{
sprintf(idvalue, "%d.%d.%d.%d\" disabled=\"disabled\" ", \
0, 0,\
0, 0);
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset+1;
}
*/
break;
case Web_Sub_Id:
/*
tls_param_get(TLS_PARAM_ID_WPROTOCOL, (void* )&mode, FALSE);
if(!ip_param.dhcp_enable || mode==IEEE80211_MODE_AP)
{
sprintf(idvalue, "%d.%d.%d.%d", \
ip_param.netmask[0], ip_param.netmask[1],\
ip_param.netmask[2], ip_param.netmask[3]);
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
}
else
{
sprintf(idvalue, "%d.%d.%d.%d\" disabled=\"disabled\" ", \
0,0,\
0, 0);
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset+1;
}
*/
break;
case DNS_Gate_Id:
/*
tls_param_get(TLS_PARAM_ID_WPROTOCOL, (void* )&mode, FALSE);
if((!ip_param.dhcp_enable)&&(mode != IEEE80211_MODE_AP))
{
sprintf(idvalue, "%d.%d.%d.%d", \
ip_param.gateway[0], ip_param.gateway[1],\
ip_param.gateway[2], ip_param.gateway[3]);
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
}
else
{
sprintf(idvalue, "%d.%d.%d.%d\" disabled=\"disabled\" ",\
0, 0,\
0, 0);
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset+1;
}
*/
break;
case DNS_Dns_Id:
/*
tls_param_get(TLS_PARAM_ID_WPROTOCOL, (void* )&mode, FALSE);
if((!ip_param.dhcp_enable)&&(mode != IEEE80211_MODE_AP))
{
sprintf(idvalue, "%d.%d.%d.%d", \
ip_param.dns1[0], ip_param.dns1[1],\
ip_param.dns1[2], ip_param.dns1[3]);
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
}
else
{
sprintf(idvalue, "%d.%d.%d.%d\" disabled=\"disabled\" ",\
0, 0,\
0, 0);
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset+1;
}
*/
break;
case Web_DnsName_Id:
/*
{
u8 dnsname[32];
tls_param_get(TLS_PARAM_ID_WPROTOCOL, (void* )&mode, FALSE);
tls_param_get(TLS_PARAM_ID_DNSNAME, dnsname, FALSE);
if(mode == IEEE80211_MODE_AP)
{
{
sprintf(idvalue, "%s", (char *)dnsname);
}
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
}
else
{
sprintf(idvalue, "%s\" disabled=\"disabled\" ", (char *)dnsname);
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset+1;
}
}
*/
break;
case Web_Encry_Id:
{
char str[100];
struct tls_scan_bss_t *scan_res = NULL;
struct tls_bss_info_t *bss_info;
u8 *bssBuff = NULL;
bssBuff = tls_mem_alloc(BSS_INFO_SIZE);
memset(bssBuff, 0, sizeof(BSS_INFO_SIZE));
tls_wifi_scan_result_cb_register(scan_result_cb);
while (WM_SUCCESS !=tls_wifi_scan()) {
tls_os_time_delay(HZ/5);
}
while( scan_done == 0 ) {
tls_os_time_delay(HZ/5);
}
scan_done = 0;
tls_wifi_get_scan_rslt(bssBuff, BSS_INFO_SIZE);
scan_res = (struct tls_scan_bss_t *)bssBuff;
bss_info = scan_res->bss;
DEBUG_PRINT("scan: %d\r\n", scan_res->count);
strcpy(idvalue, "arentNode.previousSibling.value=this.value\">\n");
sprintf(str, "<option value=\"\"></option>\n");
strcat(idvalue, str);
for(u8 i=0; i<scan_res->count && i<40; i++)
{
if( bss_info->ssid != NULL && bss_info->ssid_len != 0 ){
*(bss_info->ssid + bss_info->ssid_len) = '\0';
sprintf(str, "<option value=\"%s\">%s</option>\n", bss_info->ssid, bss_info->ssid);
strcat(idvalue, str);
bss_info->ssid[bss_info->ssid_len] = '\0';
DEBUG_PRINT("legal: %s\r\n", bss_info->ssid);
}
else
{
bss_info->ssid[bss_info->ssid_len] = '\0';
DEBUG_PRINT("illegal: %d, %s\r\n", bss_info->ssid_len, bss_info->ssid);
}
bss_info ++;
}
if( bssBuff != NULL ) {
tls_mem_free(bssBuff);
bssBuff = NULL;
}
*after_id_len = idtble->Idlen-4;
*Value_Offset = idtble->Value_Offset;
*Id_type = 0x01;
}
break;
case Web_Ssid_Id:
{
struct tls_param_ssid ssid;
tls_param_get(TLS_PARAM_ID_SSID, (void *)&ssid, FALSE);
memcpy(idvalue, ssid.ssid, ssid.ssid_len);
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
printf("\nget idvalue = %s, *after_id_len = %d, *Value_Offset = %d\n", idvalue, *after_id_len, *Value_Offset);
}
break;
/*
case Web_Encry_Id:
{
int i = 0;
char str[100];
tls_param_get(TLS_PARAM_ID_WPROTOCOL, (void* )&mode, FALSE);
tls_param_get(TLS_PARAM_ID_ENCRY, (void *)&encrypt, FALSE);
if(mode == IEEE80211_MODE_INFRA)
{
//strcpy(idvalue, " disabled=\"disabled\">");
strcpy(idvalue, " >");
for(i=0;i<6;i++){
sprintf(str, "<option value=\"%d\" %s>%s</option>", i, \
(i == 0)? "selected=\"selected\"" : "", Encry_Open[i]);
strcat(idvalue, str);
}
*after_id_len = idtble->Idlen-4;
*Value_Offset = idtble->Value_Offset;
*Id_type = 0x01;
}
else if(mode == IEEE80211_MODE_AP)
{
for(i=0;i<7;i++){
sprintf(str, "<option value=\"%d\" %s>%s</option>", i, \
(i == encrypt)? "selected=\"selected\"" : "", Encry_Open[i]);
strcat(idvalue, str);
}
*after_id_len=idtble->Idlen;
*Value_Offset = idtble->Value_Offset;
*Id_type = 0x01;
}
else
{
for(i=0;i<3;i++){
sprintf(str, "<option value=\"%d\" %s>%s</option>", i, \
(i == encrypt)? "selected=\"selected\"" : "", Encry_Open[i]);
strcat(idvalue, str);
}
*after_id_len=idtble->Idlen;
*Value_Offset = idtble->Value_Offset;
*Id_type = 0x01;
}
}
break;
*/
case Web_Key_Id:
tls_param_get(TLS_PARAM_ID_WPROTOCOL, (void* )&mode, FALSE);
tls_param_get(TLS_PARAM_ID_KEY, (void *)¶m_key, FALSE);
// tls_param_get(TLS_PARAM_ID_ENCRY, (void *)&encrypt, FALSE);
if((mode & IEEE80211_MODE_INFRA) ||(IEEE80211_MODE_AP & mode))// (encrypt != ENCRYPT_TYPE_OPEN_SYS))
{
DEBUG_PRINT("key:%s, keyLen:%d\n", param_key.psk, param_key.key_length);
sprintf(idvalue, "%s", param_key.psk);
idvalue[param_key.key_length] = '\0';
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
}
else
{
//sprintf(idvalue, "%d\" disabled=\"disabled\" ", 0);
sprintf(idvalue, "\" disabled=\"disabled\" ");
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset+1;
}
printf("\nget idvalue = %s, *after_id_len = %d, *Value_Offset = %d\n", idvalue, *after_id_len, *Value_Offset);
break;
case KeyType_Id:
/*
tls_param_get(TLS_PARAM_ID_KEY, (void *)¶m_key, FALSE);
tls_param_get(TLS_PARAM_ID_WPROTOCOL, (void* )&mode, FALSE);
tls_param_get(TLS_PARAM_ID_ENCRY, (void *)&encrypt, FALSE);
if((mode == IEEE80211_MODE_INFRA)
|| (encrypt == ENCRYPT_TYPE_OPEN_SYS))
{
if(param_key.key_format ==1)///Sever
{
sprintf(idvalue," disabled=\"disabled\"> <option value=\"0\">HEX</option> <option value=\"1\" selected=\"selected\">ASCII</option>\n");
}
else //Client
{
sprintf(idvalue," disabled=\"disabled\"> <option value=\"0\" selected=\"selected\">HEX</option> <option value=\"1\">ASCII</option>\n");
}
*after_id_len=idtble->Idlen-2;
*Value_Offset=idtble->Value_Offset;
* Id_type=0x01;
}
else
{
if(param_key.key_format ==1)
{
strcpy(idvalue,"<option value=\"0\">HEX</option> <option value=\"1\" selected=\"selected\">ASCII</option>\n");
}
else
{
strcpy(idvalue,"<option value=\"0\" selected=\"selected\">HEX</option> <option value=\"1\">ASCII</option>\n");
}
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
* Id_type=0x01;
}
*/
break;
case Web_Auto_Id:
/*
tls_param_get(TLS_PARAM_ID_AUTOMODE, (void *)&auto_mode, FALSE);
#if 1
if(auto_mode)
{
strcpy(idvalue,Auto_type[1]);
}
else
{
strcpy(idvalue,Auto_type[0]);
}
#else
{
sprintf(idvalue, "οnclick=\"auto()\" value=\"%d\" %s /> Far mode < / label > < / td > \ n "\
(!auto_mode), \
(!auto_mode) ? Web_null : Web_checked);
}
#endif
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
* Id_type=0x01;
*/
break;
case Web_AutoHidden_Id:
/*
tls_param_get(TLS_PARAM_ID_AUTOMODE, (void *)&auto_mode, FALSE);
if(auto_mode)
{
strcpy(idvalue, "1");
}
else
{
strcpy(idvalue, "0");
}
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
*/
//* Id_type=0x01;
break;
case Web_Protocol_Id:
/*
tls_param_get(TLS_PARAM_ID_DEFSOCKET, &remote_socket_cfg, FALSE);
tls_param_get(TLS_PARAM_ID_AUTOMODE, (void *)&auto_mode, FALSE);
if(auto_mode==1)
{
if(remote_socket_cfg.protocol)
{
sprintf(idvalue,"%s",Protocol_type[1]);
}
else TCP
{
sprintf(idvalue,"%s",Protocol_type[0]);
}
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
* Id_type=0x01;
}
else
{
if(remote_socket_cfg.protocol)
{
sprintf(idvalue,"disabled=\"disabled\" %s",Protocol_type[1]);
}
else TCP
{
sprintf(idvalue,"disabled=\"disabled\" %s",Protocol_type[0]);
}
*after_id_len=idtble->Idlen-2;
*Value_Offset=idtble->Value_Offset;
* Id_type=0x01;
}
*/
break;
case Web_Cs_Id:
/*
tls_param_get(TLS_PARAM_ID_DEFSOCKET, &remote_socket_cfg, FALSE);
tls_param_get(TLS_PARAM_ID_AUTOMODE, (void *)&auto_mode, FALSE);
if(auto_mode==1)
{
if(remote_socket_cfg.client_or_server)///Sever
{
strcpy(idvalue,Cs_type[1]);
}
else //Client
{
strcpy(idvalue,Cs_type[0]);
}
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
* Id_type=0x01;
}
else
{
if(remote_socket_cfg.client_or_server)///Sever
{
sprintf(idvalue,"disabled=\"disabled\" %s",Cs_type[1]);
}
else //Client
{
sprintf(idvalue,"disabled=\"disabled\" %s",Cs_type[0]);
}
*after_id_len=idtble->Idlen-2;
*Value_Offset=idtble->Value_Offset;
* Id_type=0x01;
}
*/
break;
case Web_Domain_Id:
/*
tls_param_get(TLS_PARAM_ID_DEFSOCKET, &remote_socket_cfg, FALSE);
tls_param_get(TLS_PARAM_ID_AUTOMODE, (void *)&auto_mode, FALSE);
if(auto_mode==1)
{
if(remote_socket_cfg.client_or_server && remote_socket_cfg.protocol == 0)
{
sprintf(idvalue, "%s \" disabled=\"disabled\"", "0.0.0.0");
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset+1;
break;
}
else
{
sprintf(idvalue, "%s", (char *)remote_socket_cfg.host);
}
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
}
else
{
sprintf(idvalue, "%s\" disabled=\"disabled\" ", "0.0.0.0");
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset+1;
}
*/
break;
case Web_Port_Id:
/*
tls_param_get(TLS_PARAM_ID_DEFSOCKET, &remote_socket_cfg, FALSE);
tls_param_get(TLS_PARAM_ID_AUTOMODE, (void *)&auto_mode, FALSE);
if(auto_mode==1)
{
sprintf(idvalue, "%d", remote_socket_cfg.port_num);
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
}
else
{
sprintf(idvalue, "%d\" disabled=\"disabled\" ", 0);
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset+1;
}
*/
break;
case Wep_KeyIndex_Id:
/*
tls_param_get(TLS_PARAM_ID_WPROTOCOL, (void* )&mode, FALSE);
tls_param_get(TLS_PARAM_ID_KEY, (void *)¶m_key, FALSE);
tls_param_get(TLS_PARAM_ID_ENCRY, (void *)&encrypt, FALSE);
if((mode != IEEE80211_MODE_INFRA) && (encrypt==ENCRYPT_TYPE_WEP_64_BITS||encrypt==ENCRYPT_TYPE_WEP_128_BITS))
{
if(param_key.key_index==1)///Sever
{
sprintf(idvalue, "%s","checked=\"CHECKED\" />\n");
}
else
{
sprintf(idvalue, "%s","/>\n");
}
}
else
{
sprintf(idvalue, "%s","disabled=\"disabled\" />\n");
}
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
* Id_type=0x01;
*/
break;
case Wep_KeyIndex2_Id:
/*
tls_param_get(TLS_PARAM_ID_WPROTOCOL, (void* )&mode, FALSE);
tls_param_get(TLS_PARAM_ID_KEY, (void *)¶m_key, FALSE);
tls_param_get(TLS_PARAM_ID_ENCRY, (void *)&encrypt, FALSE);
if((mode != IEEE80211_MODE_INFRA) && (encrypt==ENCRYPT_TYPE_WEP_64_BITS||encrypt==ENCRYPT_TYPE_WEP_128_BITS))
{
if(param_key.key_index==2)//
{
sprintf(idvalue, "%s","checked=\"CHECKED\" />\n");
}
else
{
sprintf(idvalue, "%s","/>\n");
}
}
else
{
sprintf(idvalue, "%s","disabled=\"disabled\" />\n");
}
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
* Id_type=0x01;
*/
break;
case Wep_KeyIndex3_Id:
/*
tls_param_get(TLS_PARAM_ID_WPROTOCOL, (void* )&mode, FALSE);
tls_param_get(TLS_PARAM_ID_KEY, (void *)¶m_key, FALSE);
tls_param_get(TLS_PARAM_ID_ENCRY, (void *)&encrypt, FALSE);
if((mode != IEEE80211_MODE_INFRA) && (encrypt==ENCRYPT_TYPE_WEP_64_BITS||encrypt==ENCRYPT_TYPE_WEP_128_BITS))
{
if(param_key.key_index==3)///
{
sprintf(idvalue, "%s","checked=\"CHECKED\" />\n");
}
else
{
sprintf(idvalue, "%s","/>\n");
}
}
else
{
sprintf(idvalue, "%s","disabled=\"disabled\" />\n");
}
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
* Id_type=0x01;
*/
break;
case Wep_KeyIndex4_Id:
/*
tls_param_get(TLS_PARAM_ID_WPROTOCOL, (void* )&mode, FALSE);
tls_param_get(TLS_PARAM_ID_KEY, (void *)¶m_key, FALSE);
tls_param_get(TLS_PARAM_ID_ENCRY, (void *)&encrypt, FALSE);
if((mode != IEEE80211_MODE_INFRA) && (encrypt==ENCRYPT_TYPE_WEP_64_BITS||encrypt==ENCRYPT_TYPE_WEP_128_BITS))
{
if(param_key.key_index==4)///
{
sprintf(idvalue, "%s","checked=\"CHECKED\" />\n");
}
else
{
sprintf(idvalue, "%s","/>\n");
}
}
else
{
sprintf(idvalue, "%s","disabled=\"disabled\" />\n");
}
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
* Id_type=0x01;
*/
break;
case Web_Mode_Id:
/*
tls_param_get(TLS_PARAM_ID_WPROTOCOL, (void* )&mode, FALSE);
#if WEB_SERVER_RUSSIAN
if(gCurHtmlFile)
{
strcpy(idvalue,Web_Mode[mode + 3]); // get russian str
}
else
{
strcpy(idvalue,Web_Mode[mode]);
}
#else
strcpy(idvalue,Web_Mode[mode]);
#endif
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
* Id_type=0x01;
*/
break;
case Web_Bg_Id:
/*
{
struct tls_param_bgr wbgr;
tls_param_get(TLS_PARAM_ID_WBGR, (void *)&wbgr, FALSE);
if(wbgr.bg==0)/bg
{
strcpy(idvalue,"<option value=\"0\" selected=\"selected\">B/G</option> <option value=\"1\">B</option><option value=\"2\">B/G/N</option>\n");
}
else if(wbgr.bg==2) //bgn
{
strcpy(idvalue,"<option value=\"0\" >B/G</option> <option value=\"1\">B</option><option value=\"2\" selected=\"selected\">B/G/N</option> \n");
}
else b
{
strcpy(idvalue,"<option value=\"0\" >B/G</option> <option value=\"1\" selected=\"selected\">B</option><option value=\"2\">B/G/N</option>\n");
}
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
* Id_type=0x01;
}
*/
break;
case Web_Rate_Id:
/*
#if 0
strcpy(idvalue,Web_Rate[wbgr.max_rate]);
#else
{
int i;
char str[] = "<option value=\"11\" selected=\"selected\">54M</option> ";
struct tls_param_bgr wbgr;
tls_param_get(TLS_PARAM_ID_WBGR, (void *)&wbgr, FALSE);
if(wbgr.bg ==0)/bg
{
for(i=0;i<12;i++){
sprintf(str, "<option value=\"%d\" %s>%s</option>", i, \
(i == wbgr.max_rate)? "selected=\"selected\"" : "", Web_Rate[i]);
strcat(idvalue, str);
}
}
else if(wbgr.bg ==2) //bgn
{
for(i=0;i<29;i++){
sprintf(str, "<option value=\"%d\" %s>%s</option>", i, \
(i == wbgr.max_rate)? "selected=\"selected\"" : "", Web_Rate[i]);
strcat(idvalue, str);
}
}
else
{
for(i=0;i<4;i++){
sprintf(str, "<option value=\"%d\" %s>%s</option>", i, \
(i == wbgr.max_rate)? "selected=\"selected\"" : "", Web_Rate[i]);
strcat(idvalue, str);
}
}
strcat(idvalue, "\n");
}
#endif
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
* Id_type=0x01;
*/
break;
case Web_Bssid_Id:
/*
{
tls_param_get(TLS_PARAM_ID_BSSID, (void *)&bssid, FALSE);
tls_param_get(TLS_PARAM_ID_WPROTOCOL, (void* )&mode, FALSE);
u8 Bssid[6];
if(mode==0)
{
if(bssid.bssid_enable==1)
{
memcpy(Bssid, bssid.bssid, 6);
sprintf(idvalue, "%02X%02X%02X%02X%02X%02X", Bssid[0],Bssid[1],Bssid[2], Bssid[3],Bssid[4], Bssid[5]);
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
}
else
{
memset(Bssid, 0, 6);
sprintf(idvalue, "%02X%02X%02X%02X%02X%02X \" disabled=\"disabled\" ", Bssid[0],Bssid[1],Bssid[2], Bssid[3],Bssid[4], Bssid[5]);
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset+1;
}
}
else
{
memset(Bssid, 0, 6);
sprintf(idvalue, "%02X%02X%02X%02X%02X%02X\" disabled=\"disabled\" ", Bssid[0],Bssid[1],Bssid[2], Bssid[3],Bssid[4], Bssid[5]);
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset+1;
}
}
*/
break;
case Web_Channel_Id:
/*
{
u8 channel;
u8 channel_en;
tls_param_get(TLS_PARAM_ID_CHANNEL, (void *)&channel, FALSE);
tls_param_get(TLS_PARAM_ID_CHANNEL_EN, (void *)&channel_en, FALSE);
#if 0
strcpy(idvalue,Web_Channel[channel]);
#else
{
int i;
char str[] = "<option value=\"0\" selected=\"selected\">Auto </option>";
if (!channel_en){
strcpy(idvalue, str);
}
else{
strcpy(idvalue, "<option value=\"0\" >Auto </option>");
}
for(i=1;i<=14;i++){
sprintf(str, "<option value=\"%d\" %s>%d</option>", i, \
((channel_en)&&(i == channel))? "selected=\"selected\"" : "", i);
strcat(idvalue, str);
}
strcat(idvalue, "\n");
}
#endif
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
* Id_type=0x01;
}
*/
break;
case Web_ChannlListCh1_Id:
/*
tls_param_get(TLS_PARAM_ID_CHANNEL_LIST, (void *)&channellist, FALSE);
if(channellist&(0x01<<0))
{
strcpy(idvalue,"checked=\"CHECKED\" />\n");
}
else
{
strcpy(idvalue,"/>\n");
}
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
* Id_type=0x01;
*/
break;
case Web_ChannlListCh2_Id:
/*
tls_param_get(TLS_PARAM_ID_CHANNEL_LIST, (void *)&channellist, FALSE);
if(channellist&(0x01<<1))
{
strcpy(idvalue,"checked=\"CHECKED\" />\n");
}
else
{
strcpy(idvalue,"/>\n");
}
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
* Id_type=0x01;
*/
break;
case Web_ChannlListCh3_Id:
/*
tls_param_get(TLS_PARAM_ID_CHANNEL_LIST, (void *)&channellist, FALSE);
if(channellist&(0x01<<2))
{
strcpy(idvalue,"checked=\"CHECKED\" />\n");
}
else
{
strcpy(idvalue,"/>\n");
}
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
* Id_type=0x01;
*/
break;
case Web_ChannlListCh4_Id:
/*
tls_param_get(TLS_PARAM_ID_CHANNEL_LIST, (void *)&channellist, FALSE);
if(channellist&(0x01<<3))
{
strcpy(idvalue,"checked=\"CHECKED\" />\n");
}
else
{
strcpy(idvalue,"/>\n");
}
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
* Id_type=0x01;
*/
break;
case Web_ChannlListCh5_Id:
/*
tls_param_get(TLS_PARAM_ID_CHANNEL_LIST, (void *)&channellist, FALSE);
if(channellist&(0x01<<4))
{
strcpy(idvalue,"checked=\"CHECKED\" />\n");
}
else
{
strcpy(idvalue,"/>\n");
}
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
* Id_type=0x01;
*/
break;
case Web_ChannlListCh6_Id:
/*
tls_param_get(TLS_PARAM_ID_CHANNEL_LIST, (void *)&channellist, FALSE);
if(channellist&(0x01<<5))
{
strcpy(idvalue,"checked=\"CHECKED\" />\n");
}
else
{
strcpy(idvalue,"/>\n");
}
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
* Id_type=0x01;
*/
break;
case Web_ChannlListCh7_Id:
/*
tls_param_get(TLS_PARAM_ID_CHANNEL_LIST, (void *)&channellist, FALSE);
if(channellist&(0x01<<6))
{
strcpy(idvalue,"checked=\"CHECKED\" />\n");
}
else
{
strcpy(idvalue,"/>\n");
}
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
* Id_type=0x01;
*/
break;
case Web_ChannlListCh8_Id:
/*
tls_param_get(TLS_PARAM_ID_CHANNEL_LIST, (void *)&channellist, FALSE);
if(channellist&(0x01<<7))
{
strcpy(idvalue,"checked=\"CHECKED\" />\n");
}
else
{
strcpy(idvalue,"/>\n");
}
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
* Id_type=0x01;
*/
break;
case Web_ChannlListCh9_Id:
/*
tls_param_get(TLS_PARAM_ID_CHANNEL_LIST, (void *)&channellist, FALSE);
if(channellist&(0x01<<8))
{
strcpy(idvalue,"checked=\"CHECKED\" />\n");
}
else
{
strcpy(idvalue,"/>\n");
}
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
* Id_type=0x01;
*/
break;
case Web_ChannlListCh10_Id:
/*
tls_param_get(TLS_PARAM_ID_CHANNEL_LIST, (void *)&channellist, FALSE);
if(channellist&(0x01<<9))
{
strcpy(idvalue,"checked=\"CHECKED\" />\n");
}
else
{
strcpy(idvalue,"/>\n");
}
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
* Id_type=0x01;
*/
break;
case Web_ChannlListCh11_Id:
/*
tls_param_get(TLS_PARAM_ID_CHANNEL_LIST, (void *)&channellist, FALSE);
if(channellist&(0x01<<10))
{
strcpy(idvalue,"checked=\"CHECKED\" />\n");
}
else
{
strcpy(idvalue,"/>\n");
}
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
* Id_type=0x01;
*/
break;
case Web_ChannlListCh12_Id:
/*
tls_param_get(TLS_PARAM_ID_CHANNEL_LIST, (void *)&channellist, FALSE);
if(channellist&(0x01<<11))
{
strcpy(idvalue,"checked=\"CHECKED\" />\n");
}
else
{
strcpy(idvalue,"/>\n");
}
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
* Id_type=0x01;
*/
break;
case Web_ChannlListCh13_Id:
/*
tls_param_get(TLS_PARAM_ID_CHANNEL_LIST, (void *)&channellist, FALSE);
if(channellist&(0x01<<12))
{
strcpy(idvalue,"checked=\"CHECKED\" />\n");
}
else
{
strcpy(idvalue,"/>\n");
}
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
* Id_type=0x01;
*/
break;
case Web_ChannlListCh14_Id:
/*
tls_param_get(TLS_PARAM_ID_CHANNEL_LIST, (void *)&channellist, FALSE);
if(channellist&(0x01<<13))
{
strcpy(idvalue,"checked=\"CHECKED\" />\n");
}
else
{
strcpy(idvalue,"/>\n");
}
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
* Id_type=0x01;
*/
break;
case Web_WebPort_Id:
/*
{
struct tls_webs_cfg webcfg;
tls_param_get(TLS_PARAM_ID_WEBS_CONFIG, (void *)&webcfg, FALSE);
if(1<webcfg.PortNum<10000)
sprintf(idvalue, "%d", webcfg.PortNum);
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
}
*/
break;
case Web_Baud_Id: /BAUDRATE_115200
/*
tls_param_get(TLS_PARAM_ID_UART, (void *)&uart_cfg, FALSE);
#if 0
strcpy(idvalue,Web_Baud[pSysVal->CfgPara.UartCfg.BaudRate]);
#else
{
int i;
char str[] = "<option value=\"0\" selected=\"selected\">115200</option> ";
for(i=0;i<BAUDRATE_BELOW;i++)
{
sprintf(str, "<option value=\"%d\" %s>%d</option>", i, \
(Web_Baud[i] == uart_cfg.baudrate)? "selected=\"selected\"" : "", \
Web_Baud[i]);
strcat(idvalue, str);
}
strcat(idvalue, "\n");
}
#endif
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
* Id_type=0x01;
*/
break;
case Web_Check_Id:
/*
tls_param_get(TLS_PARAM_ID_UART, (void *)&uart_cfg, FALSE);
if(uart_cfg.parity==0)
{
strcpy(idvalue,"<option value=\"0\" selected=\"selected\">None </option> <option value=\"1\">Odd </option> <option value=\"2\">Even </option>\n");
}
else if(uart_cfg.parity==1)
{
strcpy(idvalue,"<option value=\"0\" >None </option> <option value=\"1\" selected=\"selected\">Odd </option> <option value=\"2\">Even </option>\n");
}
else
{
strcpy(idvalue,"<option value=\"0\" >None </option> <option value=\"1\">Odd </option> <option value=\"2\" selected=\"selected\">Even </option>\n");
}
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
* Id_type=0x01;
*/
break;
case Web_StopSize_Id:
/*
tls_param_get(TLS_PARAM_ID_UART, (void *)&uart_cfg, FALSE);
if(uart_cfg.stop_bits==0)
{
strcpy(idvalue,"<option value=\"0\" selected=\"selected\">1</option> <option value=\"1\">2</option>\n");
}
else if(uart_cfg.stop_bits==1)
{
strcpy(idvalue,"<option value=\"0\" >1</option> <option value=\"1\" selected=\"selected\">2</option>\n");
}
else
{
}
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
* Id_type=0x01;
*/
break;
case Web_DataSize_Id:
/*
//strcpy(idvalue,Web_DataSize[pSysVal->CfgPara.UserIntfCfg.Uart.DataBits]);
// kevin modify 20131227 only 8 bit
strcpy(idvalue,Web_DataSize[0]);
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
* Id_type=0x01;
*/
break;
case Web_EscChar_Id:
/*
{
u8 escapechar;
tls_param_get(TLS_PARAM_ID_ESCAPE_CHAR, (void *)&escapechar, FALSE);
sprintf(idvalue, "%X", escapechar);
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
}
*/
break;
case Web_EscP_Id:
/*
{
u16 EscapePeriod;
tls_param_get(TLS_PARAM_ID_ESCAPE_PERIOD, (void *)&EscapePeriod, FALSE);
sprintf(idvalue, "%d", EscapePeriod);
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
}
*/
break;
case Web_EscDataP_Id:
/*
{
u16 PeriodT;
tls_param_get(TLS_PARAM_ID_AUTO_TRIGGER_PERIOD, (void *)&PeriodT, FALSE);
sprintf(idvalue, "%d", PeriodT);
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
}
*/
break;
case Web_EscDataL_Id:
/*
{
u16 LengthT;
tls_param_get(TLS_PARAM_ID_AUTO_TRIGGER_LENGTH, (void *)&LengthT, FALSE);
sprintf(idvalue, "%d", LengthT);
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
}
*/
break;
#if 0
case Web_GPIO1_Id:
if(pSysVal->CfgPara.IOMode==0)
{
strcpy(idvalue,"<option value=\"0\" selected=\"selected\">system function</option> <option value=\"1\">input</option> <option value=\"2\">output</option>\n");
}
else if(pSysVal->CfgPara.IOMode==1)
{
strcpy(idvalue,"<option value=\"0\" >system function</option> <option value=\"1\" selected=\"selected\">input</option> <option value=\"2\">output</option>\n");
}
else
{
strcpy(idvalue,"<option value=\"0\" >system function</option> <option value=\"1\" >input</option> <option value=\"2\" selected=\"selected\">output</option>\n");
}
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
* Id_type=0x01;
break;
case Web_CmdMode_Id:
if(pSysVal->CfgPara.CmdMode==0)
{
strcpy(idvalue,"<option value=\"0\" selected=\"selected\">AT+Instruction set mode</option> <option value=\"1\">Compatible protocol mode</option>\n");
}
else
{
strcpy(idvalue,"<option value=\"0\" >AT+Instruction set mode</option> <option value=\"1\" selected=\"selected\">Compatible protocol mode</option>\n");
}
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
* Id_type=0x01;
break;
#endif
case Web_BssidEable_Id:
/*
tls_param_get(TLS_PARAM_ID_BSSID, (void *)&bssid, TRUE);
tls_param_get(TLS_PARAM_ID_WPROTOCOL, (void* )&mode, FALSE);
if(mode==0)//sta
{
if(bssid.bssid_enable==0)
{
strcpy(idvalue,able_type[0]);
}
else
{
strcpy(idvalue,able_type[1]);
}
}
else
{
strcpy(idvalue,able_type[2]);
}
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
* Id_type=0x01;
*/
break;
case Web_PassWord_Id:
/*
{
u8 password[6];
tls_param_get(TLS_PARAM_ID_PASSWORD, password, FALSE);
sprintf(idvalue, "%c%c%c%c%c%c", \
password[0],\
password[1],\
password[2],\
password[3],\
password[4],\
password[5]);
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
}
*/
break;
case Web_TCP_TimeOut_id:
/*
tls_param_get(TLS_PARAM_ID_AUTOMODE, (void *)&auto_mode, FALSE);
tls_param_get(TLS_PARAM_ID_DEFSOCKET, &remote_socket_cfg, FALSE);
if(remote_socket_cfg.client_or_server && remote_socket_cfg.protocol == 0&&auto_mode) /// TCP Sever
{
strcpy(idvalue, (char *)remote_socket_cfg.host);
}
else
{
sprintf(idvalue, "0\" disabled=\"disabled\"");
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset+1;
break;
}
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
*/
break;
case Web_SysInfo_Macaddr:
/*
{
u8 *mac = wpa_supplicant_get_mac();
sprintf(idvalue, "%02x-%02x-%02x-%02x-%02x-%02x", \
mac[0], \
mac[1], \
mac[2], \
mac[3], \
mac[4], \
mac[5]);
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
}
*/
break;
case Web_SysInfo_HardVer:
/*
{
struct tls_cmd_ver_t ver;
tls_cmd_get_ver(&ver);
sprintf(idvalue, "%c.%x.%02x.%02x.%02x%02x", \
ver.hw_ver[0],
ver.hw_ver[1],
ver.hw_ver[2],
ver.hw_ver[3],
ver.hw_ver[4],
ver.hw_ver[5]);
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
}
*/
break;
case Web_SysInfo_FirmVer:
/*
{
struct tls_cmd_ver_t ver;
tls_cmd_get_ver(&ver);
sprintf(idvalue, "%c.%x.%02x.%02x", \
ver.fw_ver[0], ver.fw_ver[1], ver.fw_ver[2], ver.fw_ver[3]);
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
}
*/
break;
case Web_SysInfo_RelTime:
/*
sprintf(idvalue, "%s %s", \
SysCreatedTime, SysCreatedDate);
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
*/
break;
case Web_SiteInfo_Copyright:
/*
//if (!(pSysVal->CfgPara.DebugMode & DBGMODE_COPYRIGHT))
{
strcpy(idvalue, PRODUCT_MANUFACTOR);
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
}
*/
break;
case Web_Try_times_id:
/*
{
u8 auto_retry_cnt;
tls_param_get(TLS_PARAM_ID_WPROTOCOL, (void* )&mode, FALSE);
tls_param_get(TLS_PARAM_ID_AUTO_RETRY_CNT, (void* )&auto_retry_cnt, FALSE);
if(mode!=2)
{
sprintf(idvalue, "%d", auto_retry_cnt);
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
}
else
{
strcpy(idvalue,"255\" size=\"3\" maxlength=\"3\" disabled=\"disabled\" />\n");
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
* Id_type=0x01;
}
}
*/
break;
case Web_roam_id:
/*
{
u8 roam;
tls_param_get(TLS_PARAM_ID_WPROTOCOL, (void* )&mode, FALSE);
tls_param_get(TLS_PARAM_ID_ROAMING, (void* )&roam, FALSE);
if(mode==0)
{
if(roam)
{
strcpy(idvalue,able_type[1]);
}
else //disable
{
strcpy(idvalue,able_type[0]);
}
}
else
{
strcpy(idvalue,able_type[2]);
}
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
* Id_type=0x01;
}
*/
break;
case Web_powersave_id:
/*
{
u8 autoPowerSave;
tls_param_get(TLS_PARAM_ID_PSM, (void *)&autoPowerSave, FALSE);
tls_param_get(TLS_PARAM_ID_WPROTOCOL, (void* )&mode, FALSE);
if(mode==0)
{
if(autoPowerSave)
{
strcpy(idvalue,able_type[1]);
}
else //disable
{
strcpy(idvalue,able_type[0]);
}
}
else
{
strcpy(idvalue,able_type[2]);
}
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
* Id_type=0x01;
}
*/
break;
case Web_SsidBroadcast_Id: /* ap mode */
/*
tls_param_get(TLS_PARAM_ID_WPROTOCOL, (void* )&mode, FALSE);
if(mode==2)
{
u8 ssid_set;
tls_param_get(TLS_PARAM_ID_BRDSSID, (void *)&ssid_set, FALSE);
if(ssid_set)
{
strcpy(idvalue,able_type[1]);
}
else //disable
{
strcpy(idvalue,able_type[0]);
}
}
else
{
strcpy(idvalue,able_type[2]);
}
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
* Id_type=0x01;
*/
break;
case Web_Autocreateadhoc_Id:
/*
tls_param_get(TLS_PARAM_ID_WPROTOCOL, (void* )&mode, FALSE);
if(mode==1)
{
u8 auto_create_adhoc;
tls_param_get(TLS_PARAM_ID_ADHOC_AUTOCREATE, (void *)&auto_create_adhoc, FALSE);
if(auto_create_adhoc)
{
strcpy(idvalue,able_type[1]);
}
else //disable
{
strcpy(idvalue,able_type[0]);
}
}
else
{
strcpy(idvalue,able_type[2]);
}
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
* Id_type=0x01;
*/
break;
case Web_scan_id:
#if 0
{
char *tempbuf=NULL;
char *tempbuf2=NULL;
int i, j, k, n;
u8 nettab[32];
u8 channel;
tls_param_get(TLS_PARAM_ID_CHANNEL, (void *)&channel, FALSE);
tempbuf = OSMMalloc(1536);
if (tempbuf == NULL){break;}
tempbuf2 = OSMMalloc(128);
if (tempbuf2 == NULL){ OSMFree(tempbuf);break;}
memset(tempbuf,0,1536);
memset(tempbuf2,0,128);
memset(nettab,0,sizeof(nettab));
/* total number */
for(i=0;i<32;i++)
{
if (channel <= 0){
break;
}
nettab[i] = i;
};
n = i;
for(i=0;i<n-1;i++)
{
for(j=0;j<n-i-1;j++)
{
if (pSysVal->Wifi.Aplist[nettab[j]].rSignalAgility < pSysVal->Wifi.Aplist[nettab[j+1]].rSignalAgility){
k = nettab[j];
nettab[j] = nettab[j+1];
nettab[j+1] = k;
}
}
}
/* Limit the max display number */
if (n > 16)
{
n=16;
}
sprintf(tempbuf, "<option value=\"%s\" selected=\"selected\">%s </option> ", \
pSysVal->Wifi.Aplist[nettab[0]].SSID,pSysVal->Wifi.Aplist[nettab[0]].SSID);
for(i=1;i<n;i++)
{
sprintf(tempbuf2, "<option value=\"%s\">%s </option> ", \
pSysVal->Wifi.Aplist[nettab[i]].SSID,pSysVal->Wifi.Aplist[nettab[i]].SSID);
strcat(tempbuf,tempbuf2);
}
strcpy(idvalue,tempbuf);
OSMFree(tempbuf);
OSMFree(tempbuf2);
}
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
* Id_type=0x01;
#endif
break;
case Web_WebEncry_id:
/*
#if 0
strcpy(idvalue,Encry_Open[6]);
#endif
strcpy(idvalue,Encry_Open[2]);
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
* Id_type=0x01;
*/
break;
case Web_Id_my_param1:
{
char my_param[32];
tls_param_get(TLS_PARAM_ID_MY_PARAM1, (void *)my_param, FALSE);
memcpy(idvalue, my_param, sizeof(my_param));
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
printf("\nget idvalue = %s, *after_id_len = %d, *Value_Offset = %d\n", idvalue, *after_id_len, *Value_Offset);
}
break;
case Web_Id_my_param2:
{
char my_param[32];
tls_param_get(TLS_PARAM_ID_MY_PARAM2, (void *)my_param, FALSE);
memcpy(idvalue, my_param, sizeof(my_param));
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
printf("\nget idvalue = %s, *after_id_len = %d, *Value_Offset = %d\n", idvalue, *after_id_len, *Value_Offset);
}
break;
case Web_Id_my_param3:
{
char my_param[32];
tls_param_get(TLS_PARAM_ID_MY_PARAM3, (void *)my_param, FALSE);
memcpy(idvalue, my_param, sizeof(my_param));
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
printf("\nget idvalue = %s, *after_id_len = %d, *Value_Offset = %d\n", idvalue, *after_id_len, *Value_Offset);
}
break;
case Web_Id_my_param4:
{
char my_param[32];
tls_param_get(TLS_PARAM_ID_MY_PARAM4, (void *)my_param, FALSE);
memcpy(idvalue, my_param, sizeof(my_param));
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
printf("\nget idvalue = %s, *after_id_len = %d, *Value_Offset = %d\n", idvalue, *after_id_len, *Value_Offset);
}
break;
case Web_Id_my_param5:
{
char my_param[32];
tls_param_get(TLS_PARAM_ID_MY_PARAM5, (void *)my_param, FALSE);
memcpy(idvalue, my_param, sizeof(my_param));
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
printf("\nget idvalue = %s, *after_id_len = %d, *Value_Offset = %d\n", idvalue, *after_id_len, *Value_Offset);
}
break;
case Web_Id_my_param6:
{
char my_param[32];
tls_param_get(TLS_PARAM_ID_MY_PARAM6, (void *)my_param, FALSE);
memcpy(idvalue, my_param, sizeof(my_param));
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
printf("\nget idvalue = %s, *after_id_len = %d, *Value_Offset = %d\n", idvalue, *after_id_len, *Value_Offset);
}
break;
case Web_Id_my_param7:
{
char my_param[32];
tls_param_get(TLS_PARAM_ID_MY_PARAM7, (void *)my_param, FALSE);
memcpy(idvalue, my_param, sizeof(my_param));
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
printf("\nget idvalue = %s, *after_id_len = %d, *Value_Offset = %d\n", idvalue, *after_id_len, *Value_Offset);
}
break;
case Web_Id_my_param8:
{
char my_param[32];
tls_param_get(TLS_PARAM_ID_MY_PARAM8, (void *)my_param, FALSE);
memcpy(idvalue, my_param, sizeof(my_param));
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
printf("\nget idvalue = %s, *after_id_len = %d, *Value_Offset = %d\n", idvalue, *after_id_len, *Value_Offset);
}
break;
case Web_Id_my_param9:
{
char my_param[32];
tls_param_get(TLS_PARAM_ID_MY_PARAM9, (void *)my_param, FALSE);
memcpy(idvalue, my_param, sizeof(my_param));
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
printf("\nget idvalue = %s, *after_id_len = %d, *Value_Offset = %d\n", idvalue, *after_id_len, *Value_Offset);
}
break;
case Web_Id_my_param10:
{
char my_param[32];
tls_param_get(TLS_PARAM_ID_MY_PARAM10, (void *)my_param, FALSE);
memcpy(idvalue, my_param, sizeof(my_param));
*after_id_len=idtble->Idlen;
*Value_Offset=idtble->Value_Offset;
printf("\nget idvalue = %s, *after_id_len = %d, *Value_Offset = %d\n", idvalue, *after_id_len, *Value_Offset);
}
break;
default:
break;
}
return(strlen(idvalue));
}
Selection of page execution order
We don't have hedbasic HTML, which needs to be changed to the actual basic HTML and index HTML, the specific execution sequence. You can print the debugging information where Res is used.
Because only IP is specified when accessing the W800 on-chip HTTP server e.g. http://192.168.8.1 So who is the first page? index. Which html is included in html is specified here.
char *Res[] = {
// Must be index HTML comes first
"/index.html",
"/basic.html",
// The following is the official html, which can't be used. Write your own html on it
// "/hedbasic.html",
// "/hedadvance.html",
// "/hedfirmware.html",
// "/hedindex.html",
//#if WEB_SERVER_RUSSIAN
// "/hed_basic_en.html",
// "/hed_basic_ru.html",
// "/hed_firmware_en.html",
// "/hed_firmware_ru.html",
//#endif
};
static int HtmlConvertURLStr(char *drc, char *src, int len)
Add your own page processing function definition
//#define CGI_CONFIG MK_CGI_ENTRY( \ // "/ hedbasic.html", \ / / the official w800 does not provide hedbasic html // do_cgi_config \ // ) #define CGI_CONFIG_MY MK_CGI_ENTRY( \ "/basic.html", \ do_cgi_config \ ) /* static void set_default_socket(struct tls_param_socket *remote_socket_cfg)
Specify the query package sent by the http request to the http server
You can add serial port debugging statements to see.
extern u8 gucssidData[33];
extern u8 gucpwdData[65];
u8 gwebcfgmode = 0;
char * do_cgi_config(int iIndex, int iNumParams, char *pcParam[], char *pcValue[],u8 * NeedRestart)
{
/*
int i;
int Value;
/// int EnableAutoMode = 0;
u32 Ip;
int KeyType = 0;
int KeyLen = 0;
u8 encrypt;
struct tls_param_ip ip_param;
struct tls_param_key param_key;
struct tls_param_original_key* orig_key;
struct tls_param_sha1* sha1_key;
u8 auto_mode;
u8 mode;
struct tls_param_socket remote_socket_cfg;
*/
int i;
int KeyLen = 0;
struct tls_param_ssid ssid;
struct tls_param_key param_key;
struct tls_param_original_key* orig_key;
struct tls_param_sha1* sha1_key;
char my_param[32];
printf("\n>> do_cgi_config(%d, %d)\n", iIndex, iNumParams);
for (i = 0; i < iNumParams; i++)
{
if (pcParam[i] == NULL || pcValue[i] == NULL)
{
continue;
}
printf("\npcParam[%d] = %s, pcValue[%d] = %s\n", i, pcParam[i], i, pcValue[i]);
}
if (iNumParams == 0)
Save the live contents of the new repackaging field parameters to FLASH
The user changes the variable value from the interface, click save, confirm and submit. That's all.
sha1_key = (struct tls_param_sha1*)¶m_key;
memset((u8* )sha1_key, 0, sizeof(struct tls_param_sha1));
tls_param_set(TLS_PARAM_ID_SHA1, (void *)sha1_key, FALSE);
}
else if (strcmp(pcParam[i], "my_param1") == 0)
{
memset(&my_param, 0, sizeof(my_param));
HtmlConvertURLStr((char *)my_param, pcValue[i], strlen(pcValue[i]));
tls_param_set(TLS_PARAM_ID_MY_PARAM1, (void *)my_param, FALSE);
}
else if (strcmp(pcParam[i], "my_param2") == 0)
{
memset(&my_param, 0, sizeof(my_param));
HtmlConvertURLStr((char *)my_param, pcValue[i], strlen(pcValue[i]));
tls_param_set(TLS_PARAM_ID_MY_PARAM2, (void *)my_param, FALSE);
}
else if (strcmp(pcParam[i], "my_param3") == 0)
{
memset(&my_param, 0, sizeof(my_param));
HtmlConvertURLStr((char *)my_param, pcValue[i], strlen(pcValue[i]));
tls_param_set(TLS_PARAM_ID_MY_PARAM3, (void *)my_param, FALSE);
}
else if (strcmp(pcParam[i], "my_param4") == 0)
{
memset(&my_param, 0, sizeof(my_param));
HtmlConvertURLStr((char *)my_param, pcValue[i], strlen(pcValue[i]));
tls_param_set(TLS_PARAM_ID_MY_PARAM4, (void *)my_param, FALSE);
}
else if (strcmp(pcParam[i], "my_param5") == 0)
{
memset(&my_param, 0, sizeof(my_param));
HtmlConvertURLStr((char *)my_param, pcValue[i], strlen(pcValue[i]));
tls_param_set(TLS_PARAM_ID_MY_PARAM5, (void *)my_param, FALSE);
}
else if (strcmp(pcParam[i], "my_param6") == 0)
{
memset(&my_param, 0, sizeof(my_param));
HtmlConvertURLStr((char *)my_param, pcValue[i], strlen(pcValue[i]));
tls_param_set(TLS_PARAM_ID_MY_PARAM6, (void *)my_param, FALSE);
}
else if (strcmp(pcParam[i], "my_param7") == 0)
{
memset(&my_param, 0, sizeof(my_param));
HtmlConvertURLStr((char *)my_param, pcValue[i], strlen(pcValue[i]));
tls_param_set(TLS_PARAM_ID_MY_PARAM7, (void *)my_param, FALSE);
}
else if (strcmp(pcParam[i], "my_param8") == 0)
{
memset(&my_param, 0, sizeof(my_param));
HtmlConvertURLStr((char *)my_param, pcValue[i], strlen(pcValue[i]));
tls_param_set(TLS_PARAM_ID_MY_PARAM8, (void *)my_param, FALSE);
}
else if (strcmp(pcParam[i], "my_param9") == 0)
{
memset(&my_param, 0, sizeof(my_param));
HtmlConvertURLStr((char *)my_param, pcValue[i], strlen(pcValue[i]));
tls_param_set(TLS_PARAM_ID_MY_PARAM9, (void *)my_param, FALSE);
}
else if (strcmp(pcParam[i], "my_param10") == 0)
{
memset(&my_param, 0, sizeof(my_param));
HtmlConvertURLStr((char *)my_param, pcValue[i], strlen(pcValue[i]));
tls_param_set(TLS_PARAM_ID_MY_PARAM10, (void *)my_param, FALSE);
}
}
//set sta mode and reset the system.
tls_param_to_flash(TLS_PARAM_ID_ALL);
#if TLS_CONFIG_WEB_SERVER_MODE
gwebcfgmode = 1;
#endif
/*
httpd_deinit();
tls_wifi_oneshot_connect(ssid.ssid, param_key.psk);
*/
return Res[iIndex];
}
//#define CGI_ADVANCE MK_CGI_ENTRY( \
// "/hedadvance.html", \
// do_cgi_advance \
// )
//char * do_cgi_advance(int iIndex, int iNumParams, char *pcParam[], char *pcValue[], u8 * NeedRestart)
//{
Comment out the package back implementation that does not need html
//#define CGI_ADVANCE MK_CGI_ENTRY( \
// "/hedadvance.html", \
// do_cgi_advance \
// )
//char * do_cgi_advance(int iIndex, int iNumParams, char *pcParam[], char *pcValue[], u8 * NeedRestart)
//{
// /*
// int i;
// int Value;
// u32 HexValue;
Processing of adding stored variables
The stored variable is do_ cgi_ Implemented by webindex().
#define CGI_WEBINDEX MK_CGI_ENTRY( \
"/index.html", \
do_cgi_webindex \
)
char * do_cgi_webindex(int iIndex, int iNumParams, char *pcParam[], char *pcValue[], u8 * NeedRestart)
{
int i;
int Value;
//int KeyLen = 0;
u8 encrypt;
//struct tls_param_key param_key;
printf("\n\n");
printf("\n>> do_cgi_webindex(%d, %d)\n", iIndex, iNumParams);
for (i = 0; i < iNumParams; i++)
{
if (pcParam[i] == NULL || pcValue[i] == NULL)
{
continue;
}
printf("\npcParam[%d] = %s, pcValue[%d] = %s\n", i, pcParam[i], i, pcValue[i]);
}
for (i = 0; i < iNumParams - 1; i++) //not care about "Save"
{
if (pcParam[i] == NULL || pcValue[i] == NULL || *pcValue[i] == '\0')
{
continue;
}
printf("\npcParam[i] = %s, pcValue[%d] = %s\n", i, pcParam[i], i, pcValue[i]);
if (strcmp(pcParam[i], "SsidSL") == 0)
{
struct tls_param_ssid ssid;
memset(&ssid, 0, sizeof(struct tls_param_ssid));
HtmlConvertURLStr((char *)ssid.ssid, pcValue[i], strlen(pcValue[i]));
ssid.ssid_len = strlen(pcValue[i]);
tls_param_set(TLS_PARAM_ID_SSID, (void *)&ssid, FALSE);
}
else if (strcmp(pcParam[i], "Encryweb") == 0)
{
tls_param_get(TLS_PARAM_ID_ENCRY, (void *)&encrypt, FALSE);
strtodec(&Value, pcValue[i]);
if(Value==0) ///open
{
encrypt=ENCRYPT_TYPE_OPEN_SYS;
//pSysVal->CfgPara.AuthMode=0;
}
else if(Value==1)///
{
encrypt=ENCRYPT_TYPE_WEP_64_BITS;
//pSysVal->CfgPara.AuthMode=0;
}
else if(Value==2)///
{
encrypt=ENCRYPT_TYPE_WEP_128_BITS;
//pSysVal->CfgPara.AuthMode=0;
}
#if 0
else if(Value==3)///
{
encrypt=ENCRYPT_TYPE_TKIP;
pSysVal->CfgPara.AuthMode=AUTHMODE_WPA;
}
else if(Value==4)///
{
encrypt=ENCRYPT_TYPE_CCMP;
pSysVal->CfgPara.AuthMode=AUTHMODE_WPA;
}
else if(Value==5)///
{
encrypt=ENCRYPT_TYPE_TKIP;
pSysVal->CfgPara.AuthMode=AUTHMODE_WPA2;
}
else if(Value==6)///
{
encrypt=ENCRYPT_TYPE_CCMP;
pSysVal->CfgPara.AuthMode=AUTHMODE_WPA2;
}
#endif
else
{
}
tls_param_set(TLS_PARAM_ID_ENCRY, (void *)&encrypt, FALSE);
}
else if(strcmp(pcParam[i], "ApEnableweb") == 0)
{
//strtodec(&Value, pcValue[i]);
u8 mode= 0; // 1
tls_param_get(TLS_PARAM_ID_WPROTOCOL, (void* )&mode, FALSE);
}
}
tls_param_to_flash(TLS_PARAM_ID_ALL);
* NeedRestart=1;
return Res[iIndex];
}
TLS is used to read and write field variables_ param_ set(), tls_ param_ Get (), you can know the specific process of saving and reading parameters by looking at the call point. Because the program has run normally, you don't pay much attention.
An array of handles to register when http is initialized
This handle array specifies which html is processed by which function
//#if WEB_SERVER_RUSSIAN
//
#define CGI_CONFIG_EN MK_CGI_ENTRY( \
"/hed_basic_en.html", \
do_cgi_config \
)
//
#define CGI_CONFIG_RU MK_CGI_ENTRY( \
"/hed_basic_ru.html", \
do_cgi_config \
)
//
#define CGI_FIRMWARE_EN MK_CGI_ENTRY( \
"/hed_firmware_en.html", \
do_cgi_firmware \
)
//
/*#define CGI_FIRMWARE_RU MK_CGI_ENTRY( \
"/hed_firmware_ru.html", \
do_cgi_firmware \
) */
//
//#endif
tCGI Cgi[8]=
{
CGI_WEBINDEX,
CGI_CONFIG_MY,
// CGI_CONFIG,
// CGI_ADVANCE,
// CGI_CONTROL,
//#if WEB_SERVER_RUSSIAN
// CGI_CONFIG_EN,
// CGI_CONFIG_RU,
// CGI_FIRMWARE_EN,
// CGI_FIRMWARE_RU,
//#endif
};
Operation effect drawing of modified project
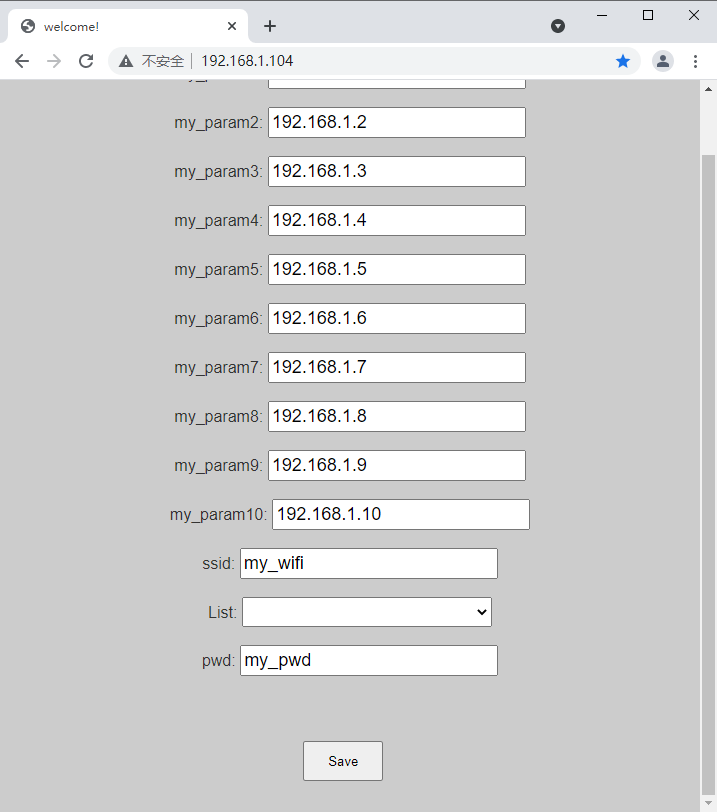
summary
Next time, on other computers, as long as there is an official W800SDK and the CDK of pingtouge community is installed, I can make a new web page that can run interactive according to this note.