ACL (access control list)
ACL has two main functions:
· flow control
· matching streams of interest
Concept:
Access control list (ACL) is the instruction list of router and switch interface, which is used to control the data packets in and out of the port
Classification (including naming ACL):
| standard | Extended ACL | AppleTalk | IPX | |
|---|---|---|---|---|
| Numerical number | 1-99 and 1300 ~ 1999 | 100-199 and 2000-2699 | 600~699 | 800~899 |
| remarks | AppleTalk is the name of a group of network protocols created by Apple company, which is used for Apple series personal computers | IPX refers to the Internet packet switching protocol, which provides packet addressing and routing functions to ensure reliable arrival, which is equivalent to the function of datagram |
3P principle:
· set an ACL(per protocol) based on each protocol
· set an ACL(per direction) based on each direction
· set an ACL(per interface) based on each interface
Working principle:
· inbound ACL: process the incoming packet and route it to the master interface. efficient.
· outbound ACL: route the packet to the outbound interface, and then process it according to the ACL
· ACL S are applied to either inbound data streams or outbound data streams
· ACL order: one statement at a time from top to bottom
Matching principle:
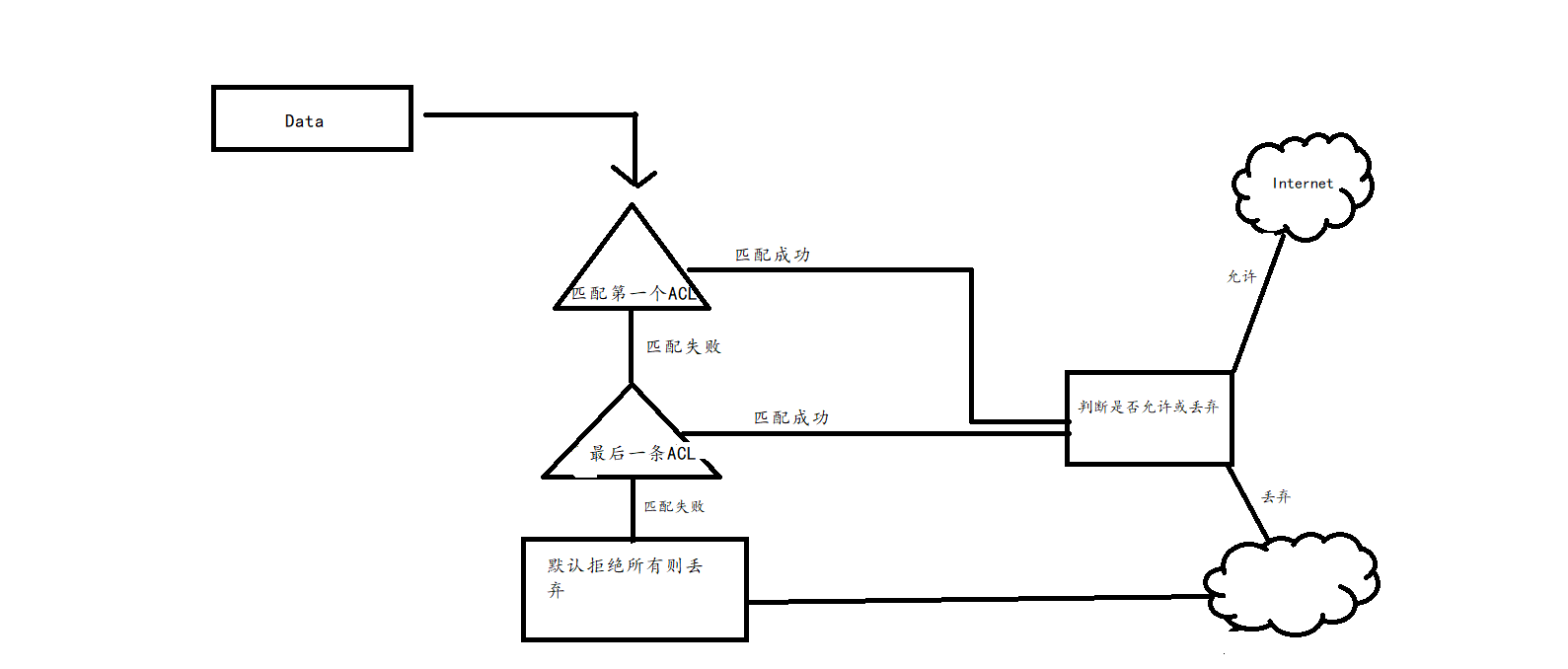
Configuration tips:
- Only one access list can be used for each port, direction and protocol
- The contents of the access list determine the control order of the data
- Statements with strict restrictions should be placed first
- The last implicit declaration in the access list is: deny any
- The access list cannot filter the data generated by the router itself
Configuration direction: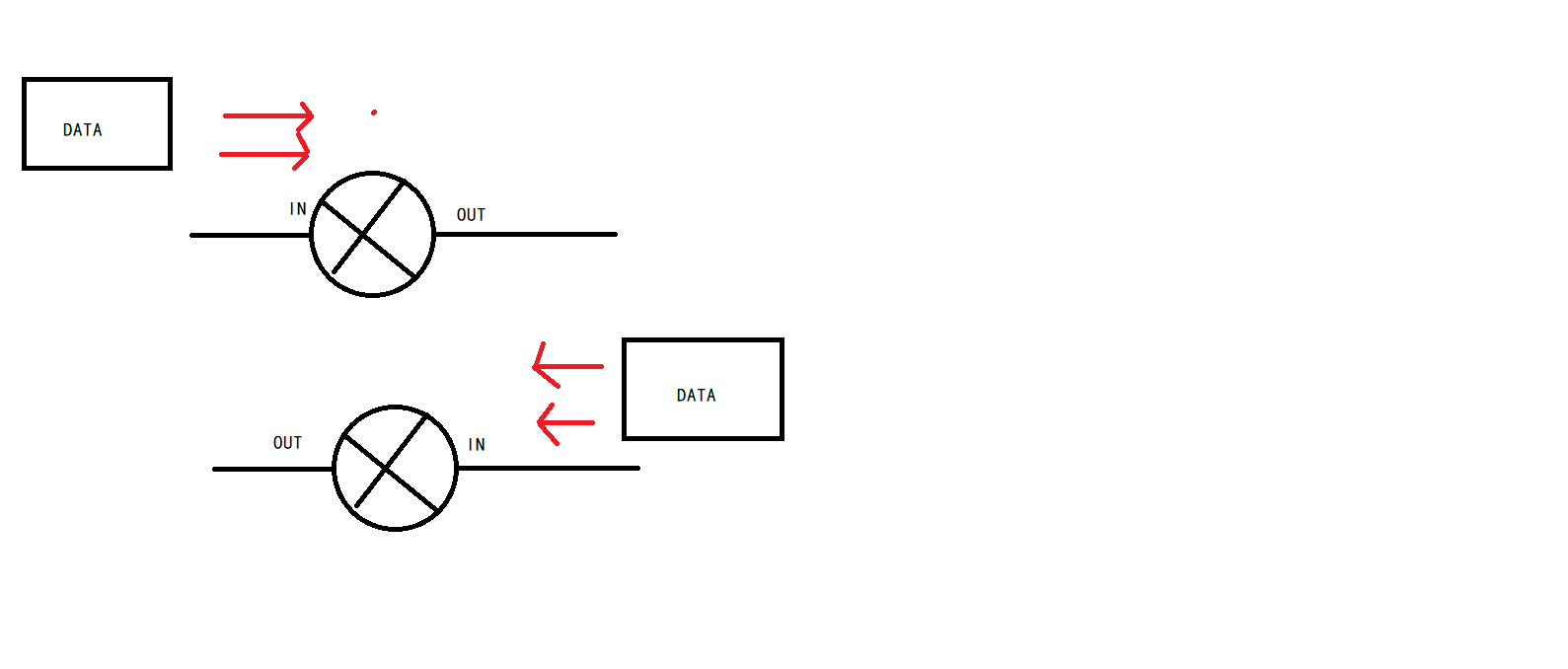
The IN direction is for our packets to enter the interface, and the OUT direction is for our packets to exit the interface. We should configure IN or OUT according to the actual situation
Later, I will also say when to use IN and when to use out (I also tell you according to my personal understanding)
Standard access control list command details:
//Standard ACL
access-list {1~99 | 1300~1999 } permit|deny {host|any|IP address}
//Naming standard ACL
ip access-list standard { 1~99 | 1300~1999} //You can enter the access group mode and configure the control entries in it. Why do you use the named ACL? I will tell you
Standard access control list experiment:
Topology diagram:
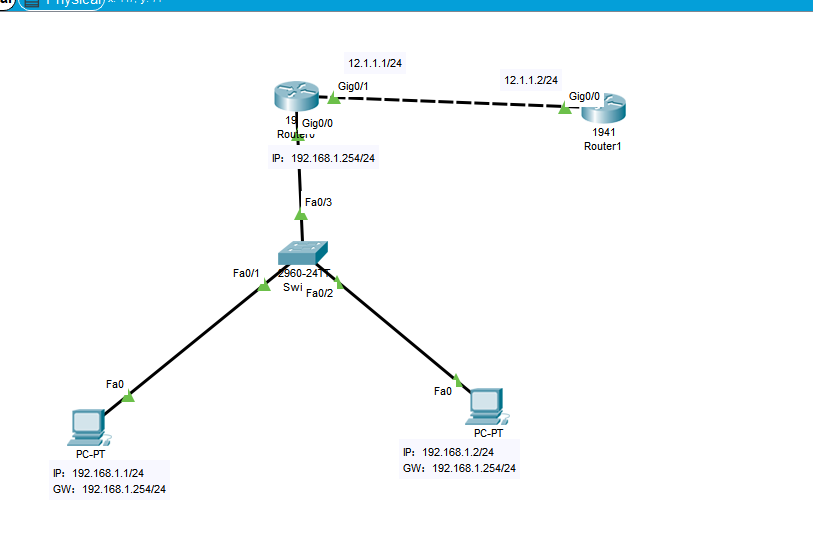
Basic configuration commands:
R1: ena conf t hostname R1 int g0/0 ip add 192.168.1.254 255.255.255.0 no sh exit int g0/1 ip add 12.1.1.1 255.255.255.0 no sh exit R2 ena conf t hostname R2 int g0/0 ip add 12.1.1.2 255.255.255.0 no sh exit ip route 192.168.1.0 255.255.255.0 12.1.1.1 exit
From the topic requirements, we know that we want to prohibit the PC from ping R2, so we need to make restrictions (we use the standard ACL to limit first). As for the direction, it can be in or out, right? Let's use out first!
On R1:
#Prohibition 192.168.1.1
#HOST writing
R1(config)# access-list 1 deny host 192.168.1.1
//Host is a single host (there is no need to write network segments). The subnet of host is 0.0.0.0, which is a single host
#IP writing
access-list 1 deny 192.168.1.1 0.0.0.0
//The unmask form (255.255.255.255-255.255.255.255.255) is 0.0.0, which is a single IP, but we only need to limit one IP and use HOST directly
#execute start using (IN/OUT)
This time we use OUT By the way IN/OUT Differences between
R1(config-if)#ip access-group 1 out
Check out our ACL:
R1#show ip access-lists
Standard IP access list 1
10 deny 192.168.1.1 (20 matches) #The 20 matches here means that 20 packets have been intercepted because I ping ed them before
R1#
So what happens in the OUT direction?
If you think about the direction of the IN, I can kill it directly. Why do you need to further check the routing table, encapsulate it, and then kill it when the OUT interface sends it
Demonstration (I'll use PT simulator to realize it here – let's see it more clearly):
Click on simulation first
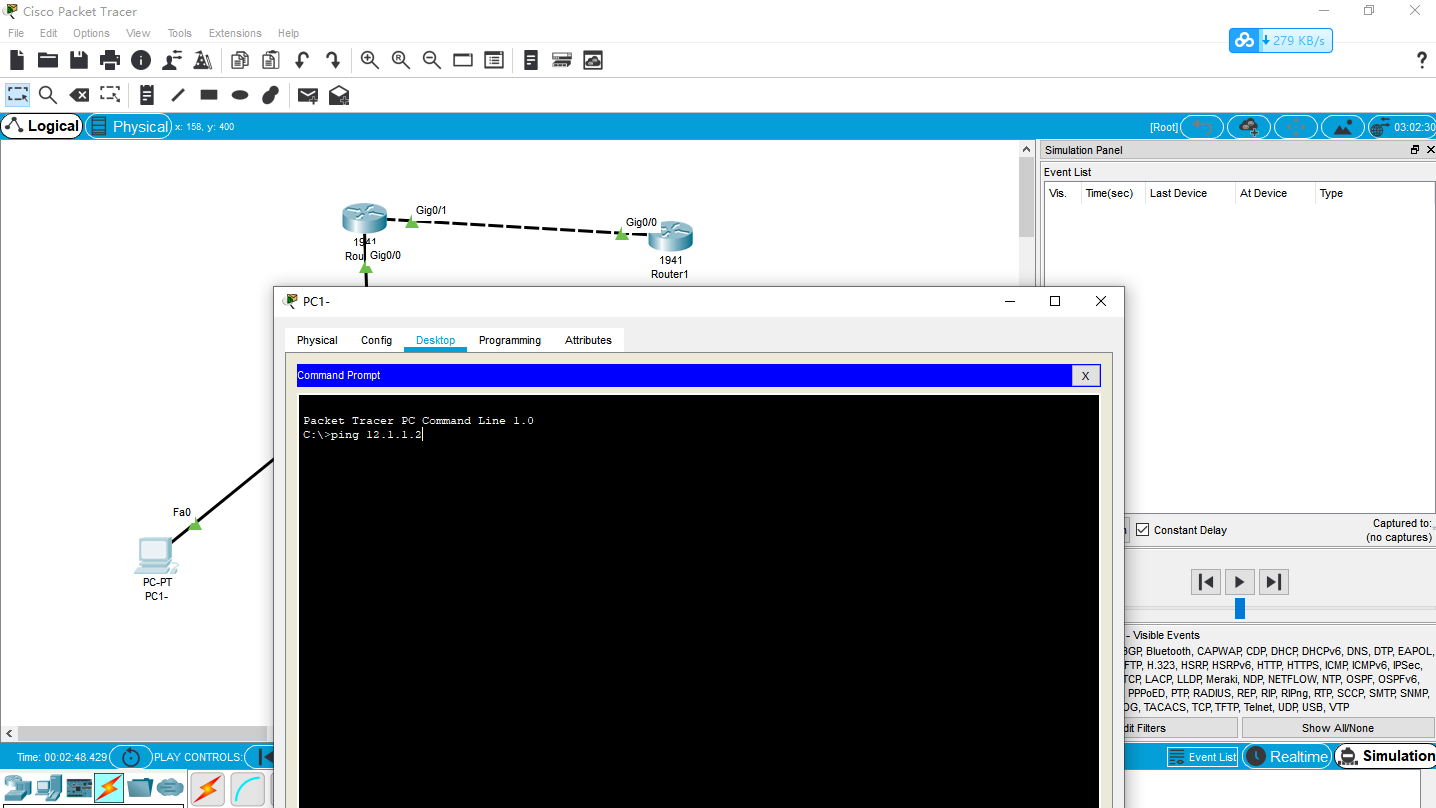
Then use PC1 to input ping 12.1.1.2 in the terminal window, and then send it to the gateway first (if you don't know the MAC address of the gateway, send ARP packet first to obtain the MAC of the gateway), so we need to click continue first
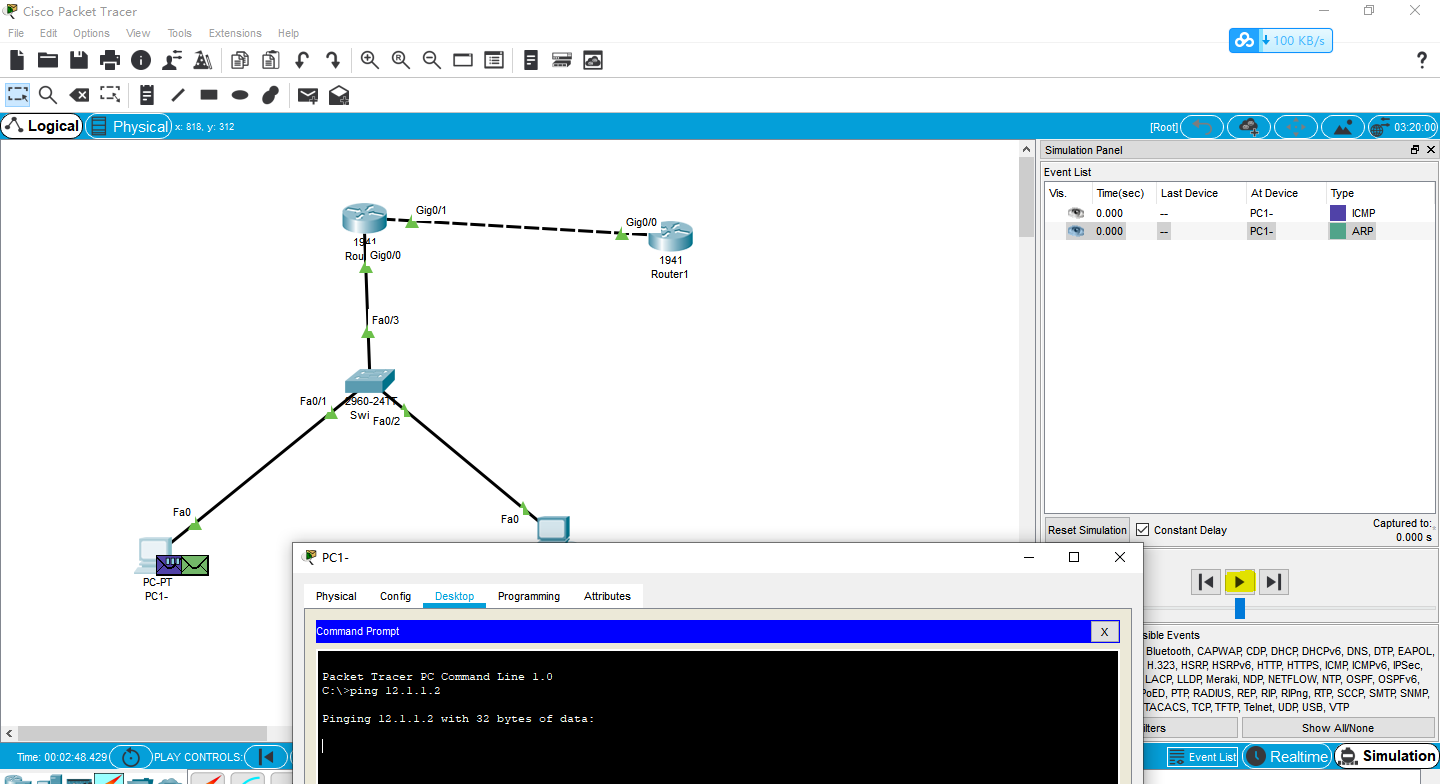
In the PT simulator, we can see that the packet enters the router and kills it when it wants to go out (in fact, it's not necessary). Let's think about a packet. I didn't let it access originally. Why don't I kill it when he comes in?
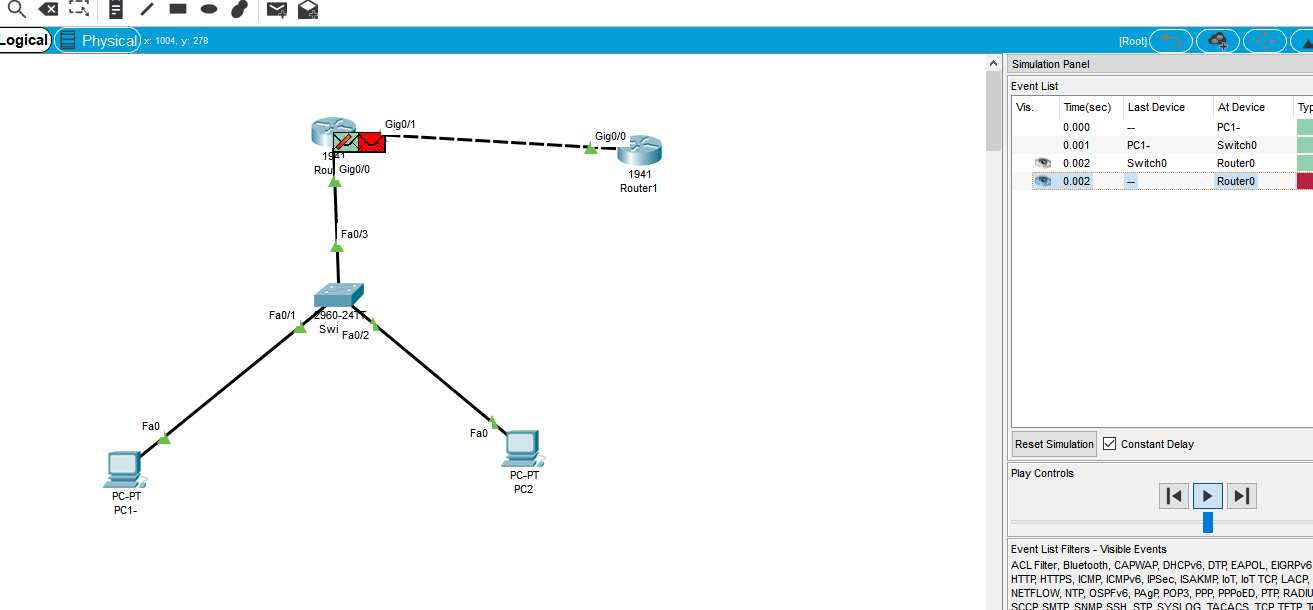
What happens when we apply the interface to the in direction of g0/0? (what will be sent when the data is killed as soon as it comes in)
Although the picture is the same as the above, we should understand that although both can be realized, do you want to kill a thief when he comes into your house, or do you want to kill him when he walks around in your living room and wants to go out?
Of course, you can also apply out on the G0/0 port, but it is not necessary because it will affect the bandwidth of the two routers and improve the CPU utilization
Then we use PC2 to ping R2 to see if it is restricted (normal will not be restricted)
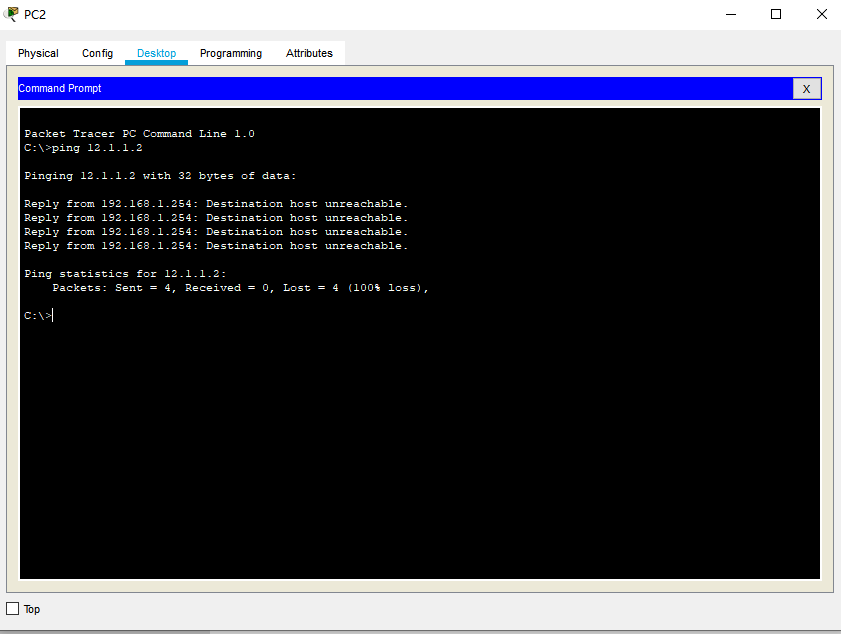
The result was killed (why? I also said above (the last item of ACL is rejected by default)
Then we're going to write an article that allows all
Router(config)#access-list 1 permit any
//Then we'll look at the allowed ACL S
Router#show access-lists
Standard IP access list 1
10 deny host 192.168.1.1 (201 match(es))
20 permit any
Router#
You can use PC2 ping 12.1.1.2 again~
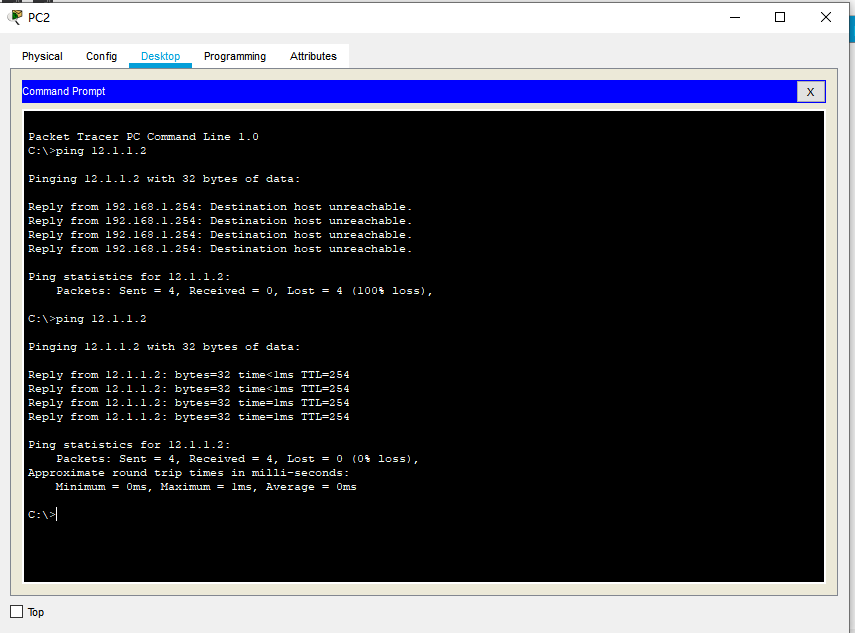
Check the ACL again
Router#show access-lists
Standard IP access list 1
10 deny host 192.168.1.1 (201 match(es))
20 permit any (4 match(es))
//Four packets are allowed (do you know what it is? Four ICMP packets and one ARP packet are increased by 10(seq) each time)
Router#
So why do we use named access control lists?

Hypothetical environment
Xiao Wang restricted PC1 from pinging 12.1.1.2 and only PC2 from pinging 12.1.1.2 according to the company's requirements
The topology is still above, but Xiao Wang's configuration command is as follows:
R1(config)#access-list 1 deny host 192.168.1.1
R1(config)#access-list 1 deny host 192.168.1.2
R1(config)#access-list 1 permit any
It was found that there was no Xiao Wang. Once he was excited, he was wrong. It was originally forbidden 192.168.1.1 The result was a wrong number, and both computers were restricted ping It doesn't work
But Xiao Wang thought he could delete him no [command]
R1(config)#no access-list 1 deny host 192.168.1.2
Xiao Wang is full of confidence show The results are as follows:
R1#show access-lists
R1#
(There's nothing left) Why is this???
Xiao Wang use?see
R1(config)#no access-list 1 ?
<cr>
R1(config)#no access-list 1
It is found that the standard access control list can only delete this entry, which is the first reason why we need to name the access control list
The second route is when a topology is large, do we use numerical values to represent our table entries? What does 1 stand for and what does 100 stand for? In short, it is poor readability
After modification
R1(config)#ip access-list standard Limit_PC1
//After naming, reading becomes better
R1(config-std-nacl)#deny host 192.168.1.1
R1(config-std-nac1)#deny host 192.168.1.2
//You're right. Xiao Wang still writes too much
R1(config-std-nacl)#permit any
#Apply to interface
R1(config)#int g0/0
R1(config-if)#ip access-group 1 in
#Xiao Wang found that you can enter the naming ACL configuration and delete the corresponding commands without deleting all of them
R1(config)#ip access-list standard Limit_PC1
R1(config-std-nac1)#no deny host 192.168.1.2
#Check again
R1#show access-lists
Standard IP access list Limit_PC1
10 deny host 192.168.1.1
30 permit any
//20 disappeared because it was deleted by us
R1#
Xiao Wang's progress:
In the above study, Xiao Wang learned how to delete ACLS and how to use control ACLS
Further requirements of the company:
After Xiao Wang's setting, PC1 cannot Ping R2's 12.1.1.2, but it can't access the Internet, which seriously affects the office work of PC1 colleagues
Topology diagram (add a server on the basis of the above (simulate the Internet) and change the equipment. We'll configure the IP first
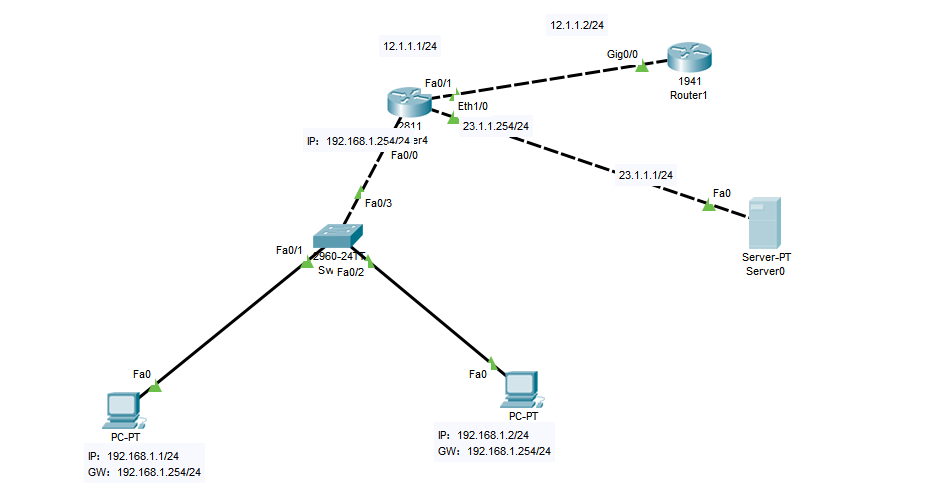
According to Xiao Wang's previous configuration
R1(config)#ip access-list standard Limit_PC1 R1(config-std-nacl)#deny host 192.168.1.1 R1(config-std-nacl)#permit any R1(config)#int f0/0 R1(config-if)#ip access-group Limit_PC1 in
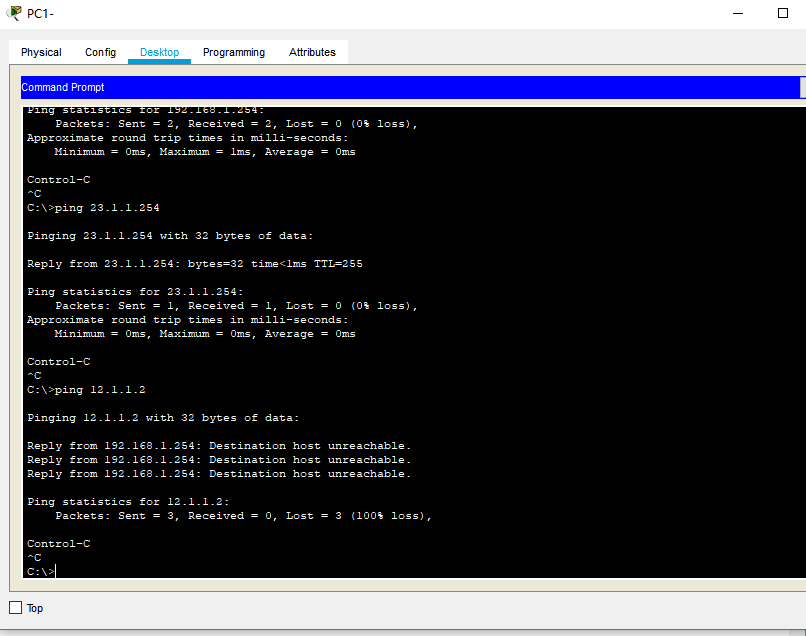
We use PC1 to ping 12.1.1.2 (of course, ping fails, but ping 23.1.1.254 should have pinged, but it also fails, because the standard ACL is restricted based on the source)
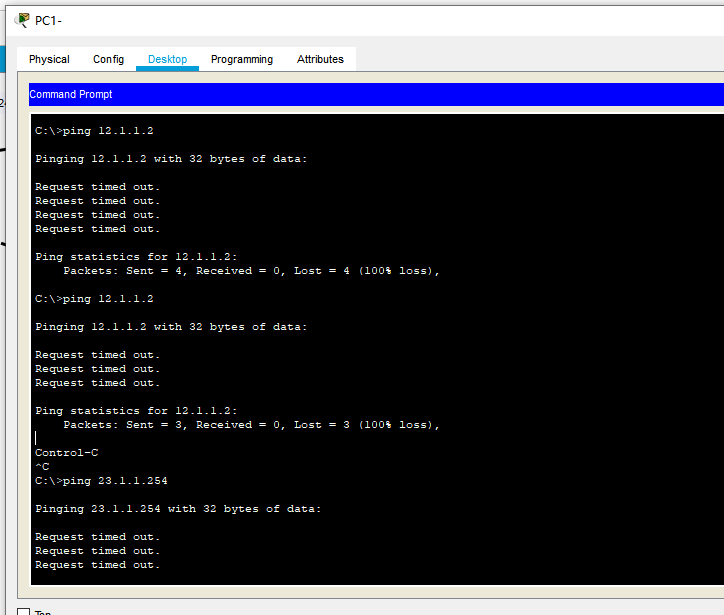
deny host 192.168.1.1 is the f0/0 port of R1 that directly disables PC1 and sends data from PC1, that is, R1 will directly discard the data from PC1(192.168.1.1) as long as it receives the data from PC1)
Two methods:
1. Location of application interface
2. Extend ACL
Method 1:
Xiao Wang found that it can be applied to f0/1 of R1. In this way, restricting f0/1 is equal to not allowing PC1(192.168.1.1) to access
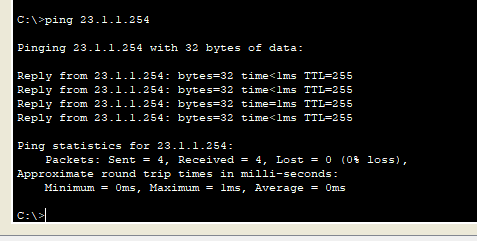
In this way, you can ping the server (simulate the Internet), but it will occupy R1 resources. As we said above, you can only go through your front door and living room at the back door
Method 2:
Xiao Wang thought of using extended ACL (restricted based on protocol, port number and source)
According to the requirements of the topic: PC1 cannot access 12.1.1.2/24 of R1
ip access-list extended Limit_PC1 deny icmp host 192.168.1.1 host 12.1.1.2 permit ip any any int f0/0 ip access-group Limit_PC1 in
Extended ACL experiment
Topology diagram:
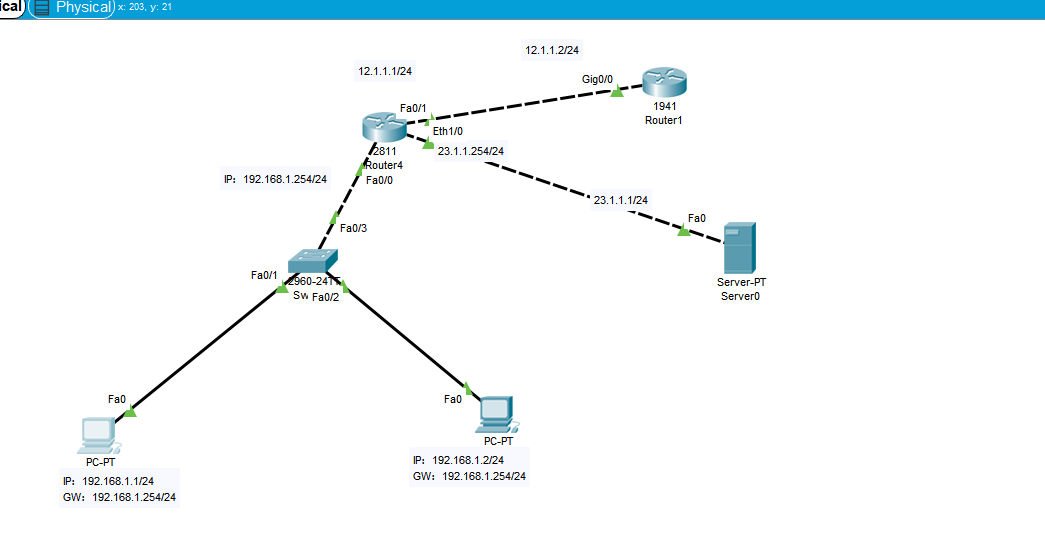
requirement:
1.PC1 cannot ping the server
2.PC2 cannot access the server web page
ip access-list extended Limit deny icmp host 192.168.1.1 host 23.1.1.1 deny tcp host 192.168.1.2 host 23.1.1.1 eq www permit ip any any int f0/0 ip access-group Limit in