1. The database data is damaged due to misoperation of drop statement. Please write down the recovery idea and actual general steps?
#The recovery of all data depends on backup. If there is no backup, it cannot be recovered In case of recovery after misoperation, the incremental recovery method shall be used for recovery. The specific steps are as follows:
(1)View Backup and binlog file (2)Refresh and backup binlog File strikethrough format #mysqladmin -uroot -p123456 -S /data/mysql.sockflush-logs (-S, --socket=name appoint soc**ket Documents.) (3)take binlog File recovery as sql sentence #mysqlbinlog –no-defaults mysql-bin.000061 mysql-bin.000062 >bin.sql (4)Delete the misoperated statement (i.e drop (action of) (5)Unzip the full file and restore the full file #gzip -d mysql_backup_2016-10-12.sql.gz #mysql -uroot -pmysql123 -S/data/3306/mysql.sock < mysql_backup_2016-10-12.sql (If there are operations on the table, the table name needs to be followed when recovering data) (6)Recover the before misoperation binlog Documented sql sentence #mysql -uroot -pmysql123 -S/data/3306/mysql.sock < bin.sql (Finally, log in the database to check whether the data is recovered successfully. If there is a certain misoperation time, directly recover the data during this time.)*
2. Give an example of actual production. The slow website access is caused by the slow database access
(1)Situation description: #One day, my colleagues responded that the visit speed of the website was slow There is even a situation that the web page cannot be opened Refresh wait for a long time and can be opened again (2)Solutions #Log in to the database and execute show full processlist (check which threads are running), check that there are many identical SQL queries, and determine that the website cannot be opened for this reason. The solution is to prohibit access to this IP #Suggestions: (1) in order to avoid such problems Middleware can be installed to realize read-write separation (2)Install data cache server,Try not to connect most read requests directly to the database
3. Kill the database brutally and rudely through kill -9, resulting in database startup failure. Give troubleshooting methods or experience
(1)see MySQL start log(see log,find mysql The system table is lost, because the database data is all test data, and the reconstruction of the database will not be affected.) (2)Execute the initialization script to create the table:(Enter database directory# ./scripts/mysql_install_db --user=mysql --datadir=/var/lib/mysql) (3)Execute the startup script again:+WX:machinegunJoe666 Free access to information
4. The broadband of IDC room suddenly increases from 100M to 400M. Please analyze the reasons and give solutions
(1)May suffer DDOS***(Write a prevention DDOS Script for) (2)Internal server poisoning,Large amount of outgoing traffic(Internal operation and maintenance specifications and systems) (3)Elements of the website were stolen,Being promoted on the portal page leads to a large amount of traffic(Basic optimization of website) (4)The partner company came to catch the data
5. The working Linux system finds that the file system is read-only. Analyze the reason and how to solve it
(1)inspect /etc/fstab Configure and check whether the disk is mounted. (2)Check whether the current actual mounted disk status is correct. (3)about Ubuntu perhaps Debian System, check the disk mounting parameters barrier Settings of. (4)adopt fsck And other tools to check the file system status.
6. The disk reports "No sapce left on device", but the disk space is not full after df -h. why
(1)df -h View not full,but df -i View full (2)resolvent: #Delete some files in the / backup directory and release some inode s in the / backup partition. Pay special attention to the files from the spool. Such files generally occupy more nodes because they are small and fragmented. At the same time, pay more attention to the log file information #Use soft connection to connect the newcache directory in the idle partition / opt to / data/cache, and use the inode of the / opt partition to alleviate the problem of insufficient inode of the / backup partition ln-s /opt/newcache /data/cache #Replace the server, and replace the low configuration server with the high configuration server
7. It is found that the disk space is full. After deleting some Nginx access logs, it can be found that the disk space is still full. Why
(1)Disk space not freed reason: stay Linux perhaps Unix In the system, through rm Or file manager deleting a file will unlink it from the directory structure of the file system(unlink).However, if the file is open (a process is using it), the process will still be able to read the file and disk space will always be occupied. And what I deleted was nginx of log The file should be in use when it is deleted (2)resolvent restart nginx Service, or use>/opt/nginx/logs/nginx.log Empty the log file instead of deleting it directly.
8. A tomcat startup script is manually executed ok, but it cannot be successfully executed in the planned task. Why
(1)The format of the scheduled task is incorrect (2)Unsuccessful due to environmental variables
9. Describe the principle of MySQL master-slave replication
(1)Generate two threads from the library, one I/O Thread, one SQL Thread; (2)i/o The thread requests the of the main library binlog,And will get binlog Log write relay log(Relay log) file; (3)The main library generates a log dump Thread, used to give the slave Library i/o Thread transmission binlog; (4)SQL Thread, will read relay log The logs in the file are parsed into specific operations to realize the consistency of master-slave operations and the consistency of final data;
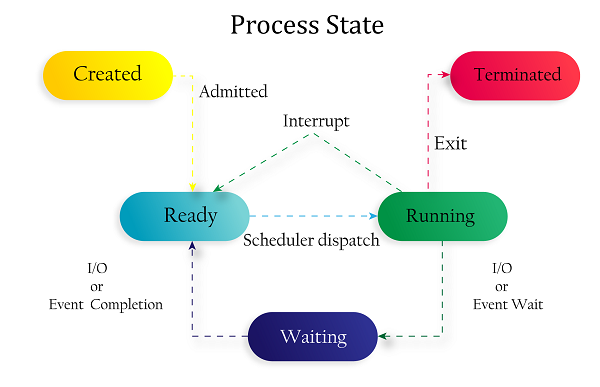
10. Common working modes and corresponding characteristics of Apache services
worker pattern: (1)Thread mode (2)Occupy less resources (3)Slightly poor stability (4) Large concurrency prefork pattern: (1)Process mode (2)Occupy more resources (3)stable (4)General concurrency+WX:machinegunJoe666 Free access to information
11. Displays all directories under the / test directory
ls -R /test ls -a /test
12. Compress and package all files except the b file in the file / etc/a under / home/a, with the name of a.gz
tar --exclude /etc/a/b -zPcvf /home/a/a.gz /etc/a
13. Commands and options that grant execution permission to a script
chmod +x The basic file is 644,Change to 647
14. What does umask022 mean
(1)The permission to create a new folder or file is subtracted from the so-called basic code, which is called umask Obtained by shielding bit of. (2)According to the regulations: the basic code of the folder is rwxrwxrwx(777),The basic code of the file is rw-rw-rw-(666) (3)Therefore, the new folder is 777-022=755(rwxr-xr-x),The new file is 666-022=644(rw-r--r--). (4)To sum up, umask 022 Indicates that the default permission to create a new file is 755, that is rxwr-xr-x(The owner has full permissions, which belongs to the group and can be read and written by others)
15. How to view all files opened by the test process
(1) lsof -c test (2)lsof -c string
16. Get the packet information of port 80 on eth0 network card
tcpdump -i eth0 port 80
17. Delete all files and directories under / a/b
rm -rf /a/b/*
18. Common network management tools (more than 5 kinds)
(1)Windows The following are: ipcofnig(/all,/renew,/release), ping, tracert, nslookup, telnet...... (2)Linux The following are: ifconfig, ping, traceroute, dig, nslookup ,telnet......
19. Port numbers of ftp, https, smtp, pops and ssh
21 443 25 110 22
20. How to enable 3-4G memory support on windows server 2003/2008
Right click on my computer and select properties, Click the "advanced" tab and click the "setting" button under [startup and fault recovery], Click the "Edit" button to Boot.ini Add a switch after the last line of the file“/PAE"(Without quotation marks), Restart the machine after saving

21. Please use iptables to control the 80 port request from the 192.168.1.2 host
iptables -A INPUT -p tcp -s 192.168.1.2 --dport 80 -j ACCEPT (Allow from 192.168.1.2 This host accesses port 80)
22. Please use the shell script to create a group class and a group of users with the user name stdx from 01-30 and belong to the class group
groupadd class
user=std
for i in {01..30}
do
useradd -G class ${user}$i
done
23. In the mysql client query tool, how to obtain all the current connection process information
mysql> show full processlist;
24. How to delete full database log information
(1)stay my.cnf Medium[mysqld]Add at the end of the paragraph:
expire-logs-days=7(Set to automatically clear 7-day money logs),restart mysql;
(2)Or log in mysql,
Execution: purge binary logs to 'mysql-bin.000003';
#Delete bin log (delete the one before mysql-bin.00000 3 without mysql-bin.00000 3)
(3)If it is mysql In the master-slave environment, delete the log. The statement format is as follows:
PURGE {MASTER | BINARY} LOGS TO 'log_name'
PURGE {MASTER | BINARY} LOGS BEFORE 'date'
+WX:machinegunJoe666 Free access to information25. Common methods for installing and uninstalling LINUX system software
(1)rpm Package uninstall: rpm -e xxx.rpm (2)yum remove xxx.rpm (3)Source package uninstall: cd Enter the compiled software directory and execute make uninstall Orders,
26. What are the commonly used remote connection tools for Windows and LINUX
Common remote connections Linux Tools include: XShell,Putty,SecureCRT windows:Teamviewer/Splashtop/Chrome Remote Desktop app/TightVNC/ PC Anywhere
27. How to modify the IP address, gateway and host name of LINUX
(1)A,modify IP Address and gateway: editing/etc/sysconfig/network-scripts/ifcfg-eth0, Modify inside IPADDR and GATEWAY Content. If there are no these two lines, you can add them, Ensure when adding BOOTPROTO=static,Static address, as IPADDR=192.168.1.100 GATEWAY=192.168.1.1 (2)B,Modify host name: Edit/etc/sysconfig/network, Modify the inside HOSTNAME Content, If the host name is set to mysql,Then: HOSTNAME=mysql OK;
28. Write scripts to realize the following functions;
1) Backup starts at 5:00 every morning
2) All files and directories in / var/mylog to be backed up can be compressed for backup
3) The backup can be saved to another device. 192, 168, 1, 2 FTP accounts aaa password bbb
4) To show that the daily backup file should be marked with the date of the day
bakdir=mylog
date=`date +%F`
cd /var
tar zcf ${bakdir}_${date}.tar.gz ${bakdir}
sleep 1
ftp -n <<- EOF
open 192.168.142.129 #Remote ftp server IP
user aaa bbb
put mylog_*.tar.gz
bye.
EOFworker pattern: (1)Thread mode (2)Occupy less resources (3)Slightly poor stability (4) Large concurrency +WX:machinegunJoe666 Free access to information prefork pattern: (1)Process mode (2)Occupy more resources (3)stable (4)General concurrency

In order to better help my friends, I am still preparing for the essence interview questions of the big factories.

Finally, I wish you all success in your studies as soon as possible, get a satisfactory offer, get a quick promotion and raise, and reach the peak of your life.
If you can, please give me a three company to support me~~
→[data acquisition]←