Problems encountered
Normal access to k8s cluster through VPN enables the local development environment to normally access the virtual ip of pod and service in the cluster. However, for microservice development, there is still a need to access the local machine from k8s cluster
resolvent
At this time, we need to bridge VPN to virtual network card, then forward the traffic of VPN network segment to virtual network card through linux kernel forwarding function, and then broadcast the virtual network card to VPN network
Specific configuration method
network environment
k8s cluster
pod Subnet: 192.168.0.0/19 service Subnet 192.168.48.0/21 node Subnet 192.168.32.0/20
vpn server
I use a separate vpn server here. You can also use a node node as a vpn server. The server I use here is centos
192.168.32.100
Compile and install VPN service
yum install -y git gcc make mkdir /vpn-server cd /vpn-server git clone https://gitee.com/xuejike/soft-ether-vpn_open_route.git cd soft-ether-vpn_open_route ./configure make cp -rf bin/vpnserver ../ cd ../vpnserver ./vpnserver start
VPN server configuration
After starting the vpn service, download the service client to configure the server
http://softether.fishinfo.cn/cn.aspx
https://github.com/SoftEtherVPN/SoftEtherVPN_Stable/releases/download/v4.36-9754-beta/softether-vpnserver_vpnbridge-v4.36-9754-beta-2021.06.07-windows-x86_x64-intel.exe
Turn off centos default firewall and install iptables
systemctl stop firewalld.service #Stop firewall systemctl disable firewalld.service #Disable firewall startup yum install -y iptables
After the first connection, you need to set the server management password
Then initialize the server configuration
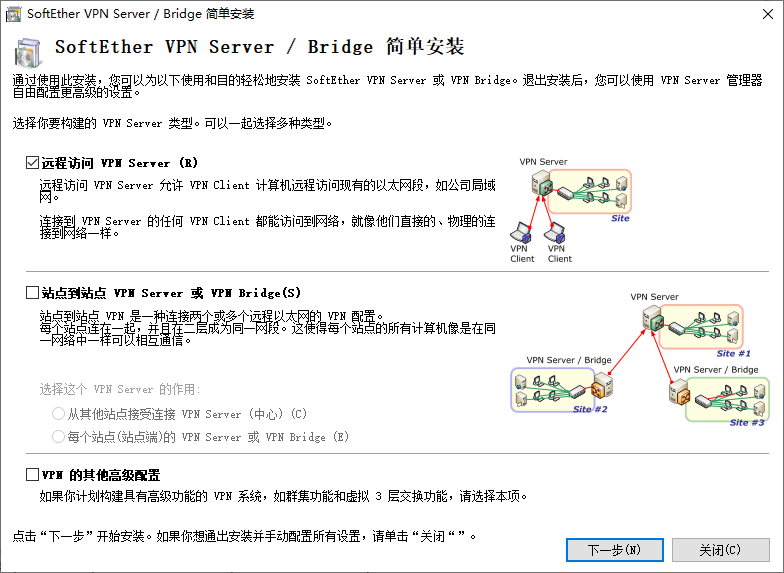
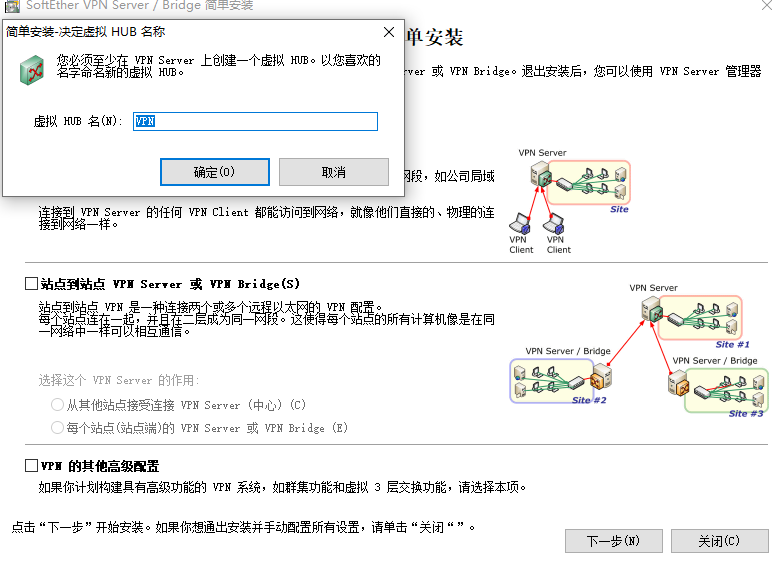
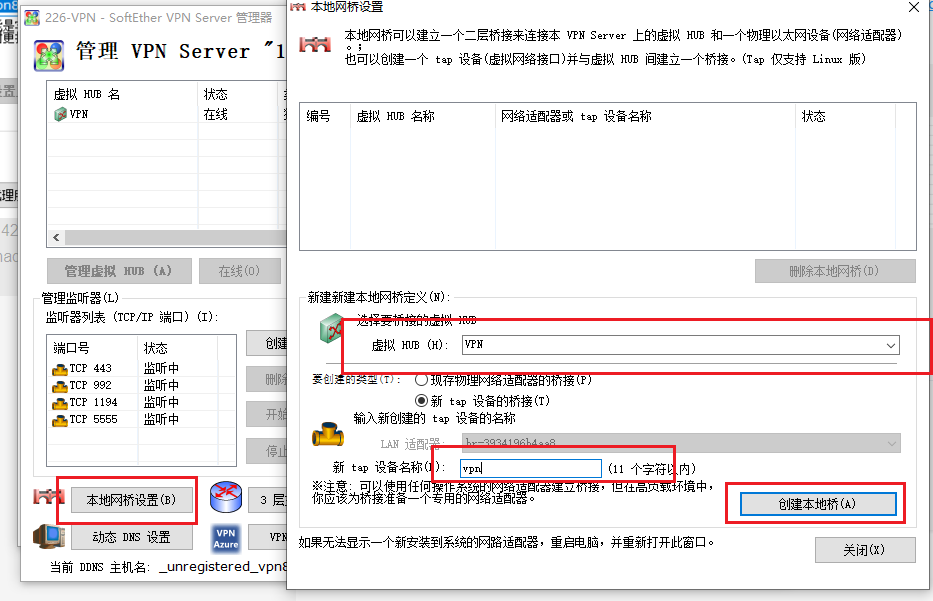
After initializing the configuration, perform the bridge configuration
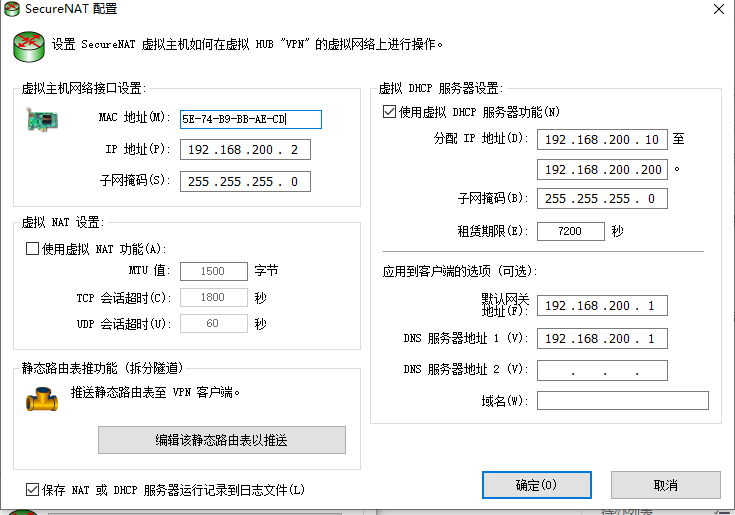
Configure DHCP service of VPN and turn off NAT forwarding function
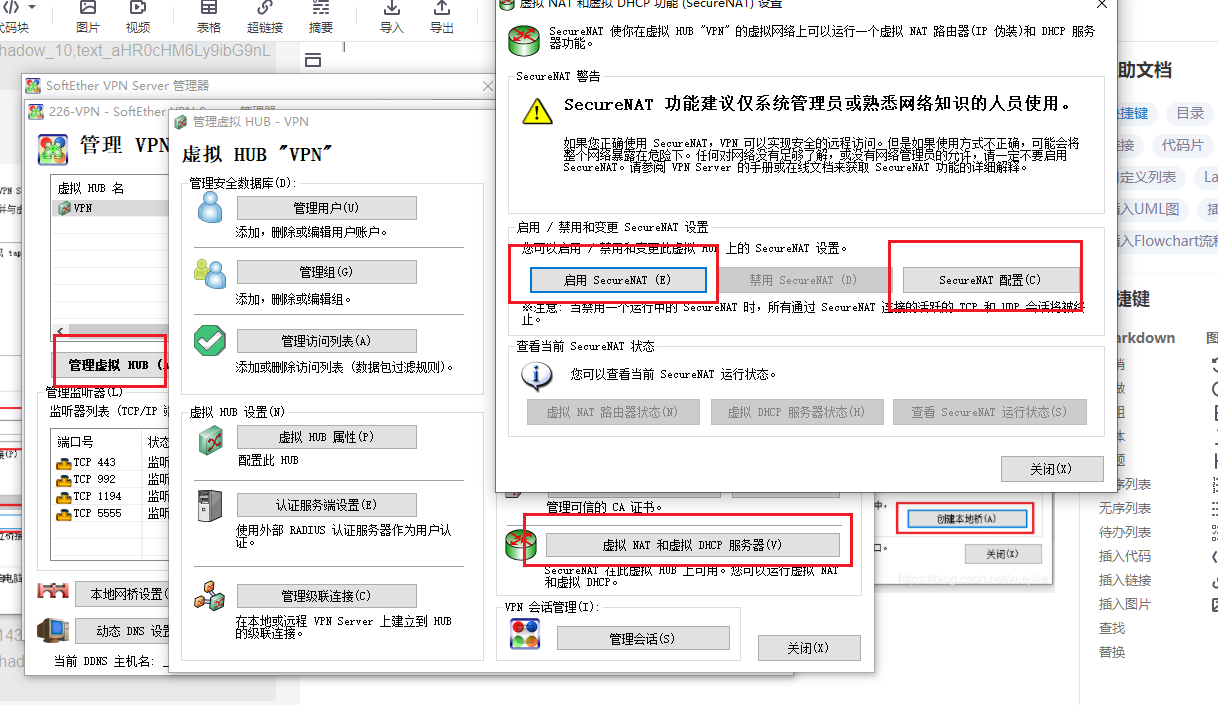
Turn off the NAT function and reset the VPN network segment. Do not conflict with the k8s cluster network segment
Bridging VPN network
Set the ip address of the previously added tap network card
ifconfig tap_vpn 192.168.200.1
tap_vpn: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.200.1 netmask 255.255.255.0 broadcast 192.168.200.255
inet6 fe80::5c94:65ff:fe0f:36c7 prefixlen 64 scopeid 0x20<link>
ether 5e:94:65:0f:36:c7 txqueuelen 1000 (Ethernet)
RX packets 636 bytes 46046 (44.9 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 739 bytes 61106 (59.6 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
Configure iptables forwarding
# Turn on kernel forwarding echo "net.ipv4.ip_forward = 1" >> /etc/sysctl.conf sysctl -w net.ipv4.ip_forward=1 # Network card forwarding iptables -I FORWARD -i tap_vpn -j ACCEPT iptables -I FORWARD -o tap_vpn -j ACCEPT iptables -t nat -I POSTROUTING -o tap_vpn -j MASQUERADE
Add static routing tables to k8s hosts
192.168.200.0/24 points to 192.168.32.100
Static routing table configuration
At present, after VPN is connected to the server, all traffic will be forwarded through the server. When we are developing, we only need to use the ip in the k8s network segment to go through VPN, and others can go through the normal network. In this way, we need to use the static route distribution function of VPN
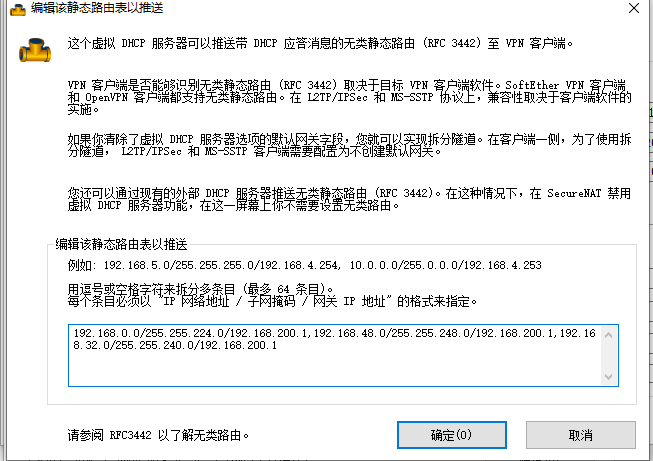
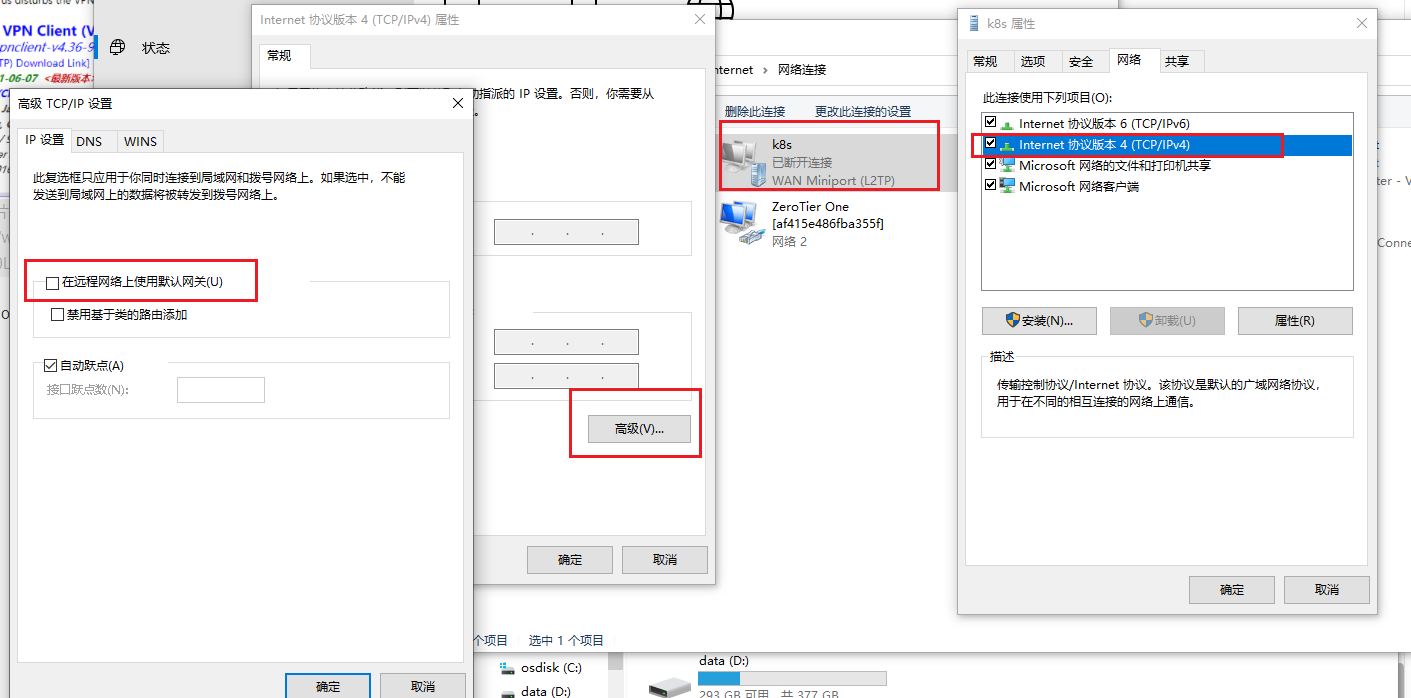
After configuring this, you need to delete the default gateway
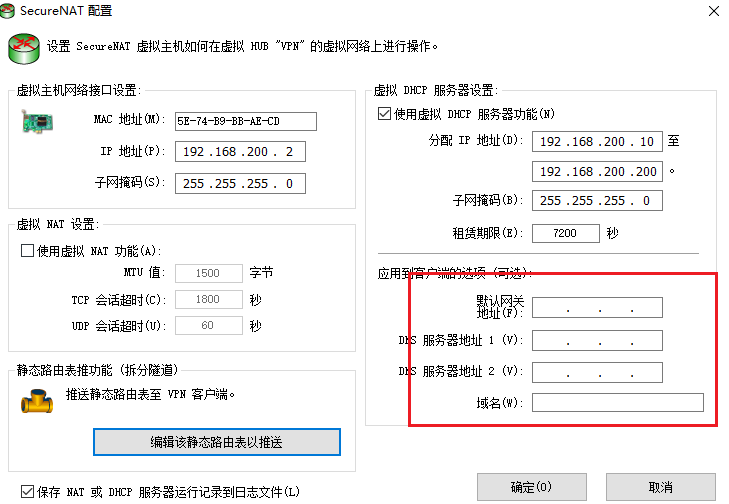
After configuring the static routing table, only the network segments in the routing table can go through vpn after vpn connection
VPN client
The client can use the official
You can also use L2TP that comes with window. L2TP that uses window needs to set and cancel the default gateway on VPN