What is spring MVC
springMVC Is based on MVC Architecture to simplify WEB Application framework; A framework that belongs to the presentation layer.
How spring MVC works
The user sends a request to the front-end controller. The front-end controller receives the request and calls the processor mapper. The processor mapper calls the processor mapper according to the request URL Find the specific processor, generate the processor object and the processor interceptor (if any), and return it to the front-end controller. The front-end controller calls the processor through the processor adapter, and then executes the controller. After execution, it returns to the view and model. The processor adapter returns the view and model of the controller execution result to the front-end controller; The front-end controller transmits the view and model to the view parser and returns to the specific view after parsing. The front-end controller renders the view (that is, fills the model data into the view), and the front-end controller responds to the user.
Understanding of spring MVC
springMVC The entrance is a servlet Front end controller. springMVC Method based development (a URL For a method), the formal parameters passed from the request parameters to the method can be designed as single instance mode or multiple instances; It is recommended to use singleton, which is singleton by default. Why is a single example recommended? 1,Performance (not every request) New Object). 2,Multiple instances are not required (do not define member variables in the controller).
What is the spring framework
It is a lightweight open source framework, which creates good performance, easy to test and reusable code; It is based on IOC(Reverse control) and AOP(Slice Oriented Architecture Jzee(The framework of enterprise application system. advantage: 1,It can effectively organize middle tier objects, whether they are used or not EJB(Enterprise level JavaBean). 2,It eliminates the excessive use of singleton pattern in work, and reduces the testability and object-oriented of the system. 3,It eliminates the need for various custom format attribute files and is easy to unit test. 4,Reduce the code for interface programming rather than class programming, and develop good programming habits. 5,Applications created with it depend as little as possible on its( APIS)Programming interface.
Understanding of spring
Its two cores: IOC(Control reversal) and AOP(Facing the section). 1,IOC: It reduces the coupling degree of the program and makes the project a pluggable component-based project. 2,AOP: So that the energy of the development process can be released, more focused on solving customer needs, and high maintainability. 3,It provides a transaction management mechanism, which configures transactions in a declarative way, so that there is no need to change the source code during maintenance, and solves the problem of program hard coding. 4,It provides DAO(The data access object (deao) template gives the persistence layer one more use. 5,It can integrate any current framework and make it clearer when managing projects. spring There are two ways to manage transactions. 1,Programming transactions, hard coded in code. 2,Declarative transaction, which is configured in the configuration file; (recommended) There are two types of declarative transactions: 1,be based on XML Declarative transaction. 2,Annotation based declarative transactions.
What is dependency injection
Dependency injection is an idea to realize control inversion (the other is dependency lookup). In the process of development, when we need an instance of a class, the user provides us with the instance of the class instead of obtaining it by himself. There are two ways to implement dependency injection: 1,Inject using the construction method. 2,set Method injection.
What is control reversal
IOC yes spring One of the core of. Inversion of control means that when we acquire an object, we change from active to passive reception; In other words, when programming a class, you only need to provide a class member of an interface type, not a specific implementation class, but provided by the user when using, which reduces the coupling between classes.
MyBatis
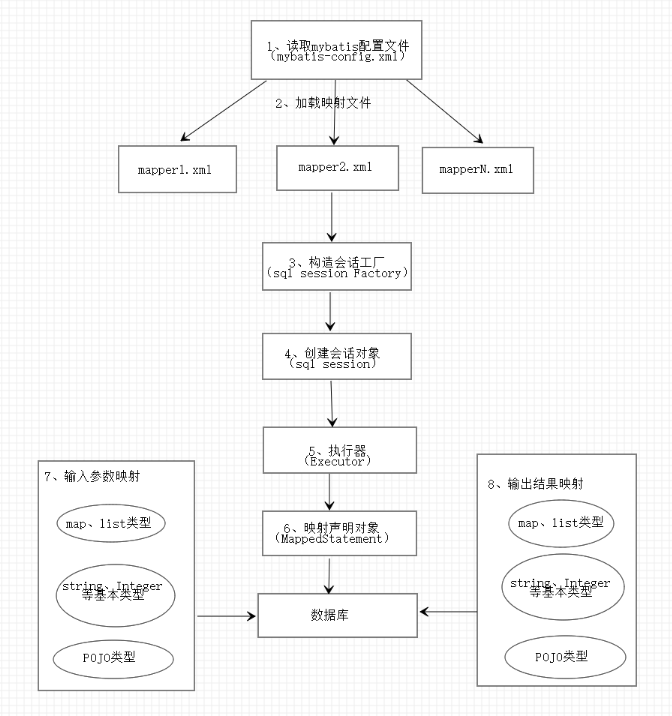
MyBatis Is a support common SQL Excellent persistence framework for queries, stored procedures and advanced mapping. Eliminated almost all JDBC(Java Database connection) manual setting of code and parameters and retrieval encapsulation of result set. You can use simple XML Or annotations are used for configuration and original mapping, and the interface and Java of POJO(ordinary Java Object) is mapped to records in the database. MyBatis working principle
What is springBoot
from pivotal A new framework provided by the team to simplify the new spring Application initialization, construction and development process. The framework uses a specific way to configure, so that developers do not need to define a templated configuration. springBoot assembly 1,springBoot Auto configuration: spring Startup can detect the availability of some frameworks, and once the framework is detected, it will automatically configure it. 2,springBoot Core: It's other spring Model basis, which provides some functions and can be completed by itself through verification. 3,springBoot starters: Help start projects, which automatically add start projects and dependencies. springBoot characteristic 1,Used to implement microservices 2,Auto configuration 3,Custom configuration 4,modularization 5,Independent packaging and direct operation 6,Embedded server (e.g.: Tomcat Server) 7,spring Cloud Foundation of
spring Security security framework
spring Security It is a powerful authentication and control framework. It is guaranteed based on spring Practical standards for application security. Main functions: 1,Authentication: verify whether the user name and password are legal (whether there are users in the system) 2,Authorization: being a system user doesn't mean you can use some functions because you don't have permission for 3,Defense against fixed session, click hijacking, Cross Site Request Forgery and other attacks 4,servlet API integrate 5,And springWebMVC Optional integration
Java multithreading, collection, happy / pessimistic lock
What is multithreading Multiple threads can be started in a process, and each thread can execute different tasks in parallel (at the same time). For example: process A Workshop, thread A Workshop workers; Multithreading technology can improve the execution efficiency of programs. Multithreading is a concurrent means and a special form of multitasking, but multithreading uses less resource overhead. There are three ways to create threads: 1,realization Runnable Interface 2,inherit Thread Class itself 3,adopt Callable and Fature Create thread Principle of multithreading 1,At the same time, CPU Only one thread can be processed, and only one thread is working (executing) 2,Multithreading concurrent (simultaneous) execution is actually CPU Quickly switch directly across multiple threads 3,If CPU Scheduling threads fast enough creates the illusion of concurrent execution of multiple threads What happens if there are many threads? 1,CPU Will be N Switching between multiple threads, CPU Will be exhausted and consume a lot of energy CPU resources 2,The execution efficiency of threads is reduced Thread life cycle 1,New status 2,Ready status 3,running state 4,Blocking status: 1,Wait for blocking 2,Synchronous blocking 3,Other obstruction 5,State of death Several main concepts of thread: 1,Thread synchronization 2,Inter thread communication 3,thread deadlock 4,Thread control: suspend, stop and resume Optimistic lock and pessimistic lock 1,Optimistic lock holds an optimistic state, which is to assume that my data will not be accidentally modified. If it is modified, I will give up and start from scratch. 2,Pessimistic lock holds a pessimistic state, that is, assuming that my data will be modified, I can simply lock it directly.
Introduction to Java collections
Three sub interfaces of the collection interface:
1,set
2,list
3,Queue
The set can be roughly divided into the following four systems:
1. Set: an unordered and non repeatable set
2. list: an ordered and repeatable set
The classes commonly used to implement the list interface are LinkedList ArrayList Vector and Stack
3. Map: represents the collection with mapping relationship
4. Queue: it is newly added in Java 5 to represent a queue collection implementation
The difference between set and array
1. Array length initialization specifies that only fixed length data can be saved. The collection can save uncertain data and data with mapping relationship.
2. An array element can be either a value of a basic type or an object. A collection can only be an object. The reference variables of the object are actually saved. The variables of the basic type can only be put into the collection after being converted into the corresponding wrapper class.
Map and collection are the root interfaces of the Java collection framework. The key in the map cannot be repeated. It is used to save the data with mapping relationship.
Redis
What is cache penetration
When the database is queried, there will be more pressure to query the data in the database every time. If there is no data in the database, there will be no data in the database.
solve:
1. Cache null value, that is, set the key not in the cache to null.
2. Bloom filter, which is similar to an Hbase set, is used to judge whether an element (key) exists in the set. We put the key of the data in the bloom filter and judge it every time. If it doesn't, it will directly return null. It has no deletion operation and can be combined with caching null values.
What is cache avalanche
When a large-scale cache failure is sent at a certain time, for example, the cache server is down.
solve:
1. Use clusters to reduce the probability of service downtime.
2. ehcache local cache + Hystrix current limiting and degradation.
The L2 cache can be supported for a while when redis Cluster is completely unavailable.
Use Hystrix for current limiting or degradation, such as 5000 requests in 1 second, set it to 2000 requests, and the rest go through logical flow.
What is cache breakdown
In the case of high concurrency, when a large number of requests query the same key at the same time, the key just fails, which will cause these requests to query the database at the same time, resulting in excessive database requests at a certain time.
resolvent:
1. Distributed lock
Only the first request (thread) that gets the lock requests the database and then inserts the cache. Of course, every time you get the lock, you have to check whether the cache is available.
Solve the failure problem of hot data set
For hot data, when the cache fails, there will be a large number of requests coming and then hitting the database, resulting in the collapse of the database. resolvent: 1,Set failure time 2,Adopt buffer breakdown method and lock 3,Setting the cache to never expire is to update the cache and expiration time of the cache that is about to expire by using scheduled tasks.