HTTPS
Basic overview of HTTPS
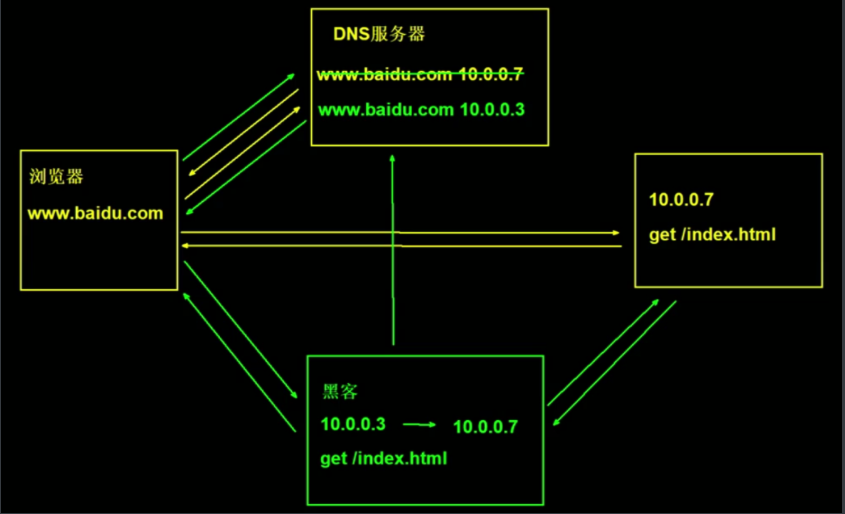
Why use HTTPS,because HTTP Unsafe when we use http The website will be hijacked and tampered with if used https Protocol, then the data is encrypted in the transmission process, so hackers can not steal or tamper with the data message information, but also avoid information leakage during website transmission. So what are we doing https You need to understand ssl Protocol, but we use more now TLS Encryption protocol. that TLS How to ensure that plaintext messages are encrypted? stay OSI In the seven layer model, the application layer is http Protocol, then under the application layer protocol, our presentation layer is ssl The layer in which the protocol plays a role is the application layer by means of handshake, secret key exchange, alarm, encryption, etc http The protocol achieves the secure encryption of data without perception
HTTPS certificate issuance process
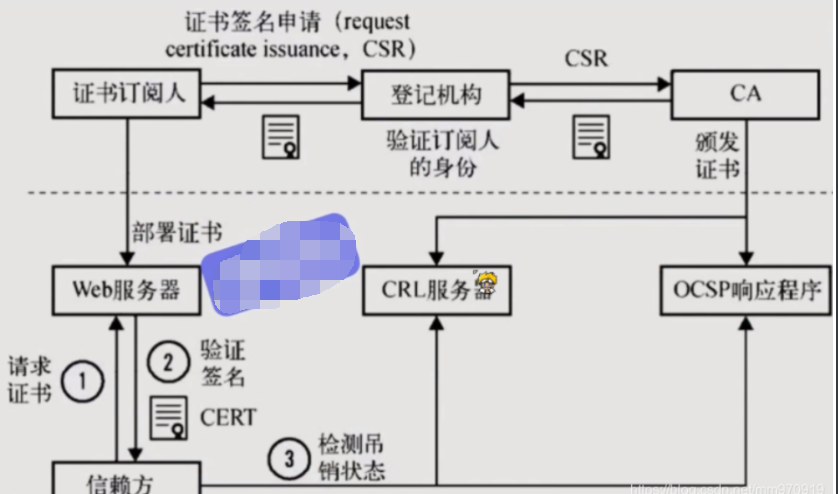
First of all, we need to apply for a certificate, go to the registration authority for identity registration, who I am, what I do, and what I want to do, and then pass the registration authority CSR issue CA,CA After the center passes, a pile of public keys and private keys will be generated, and the public keys will be CA The public key and private key certificates are saved in the certificate chain. After we get them, we will deploy them in WEB On the server 1.When the browser accesses our https When the site, he will ask for our certificate 2.Nginx In this way web The server will send our public key certificate to the browser 3.The browser will verify whether our certificate is legal and valid 4.CA The organization will place expired certificates in CRL The server, CRL The validation efficiency of the service is very poor, so CA Yes OCSP Response procedure, OCSP The responder can query whether a specified certificate has passed, so the browser can query directly OSCP Response procedure, but OSCP The performance of the response program is not very high 5.Nginx There will be one OCSP When we turn it on, Nginx Will take the initiative OCSP Query on such a large number of clients directly from Nginx Whether the obtained certificate is valid
Simulated website hijacking
Configure hijacked websites
#Configure a my website
[root@web01 conf.d]# vim jc.linux.com.conf
server {
listen 80;
server_name jc.linux.com;
root /code/jc;
index index.html;
charset utf8;
}
#Configure a my page
[root@web01 conf.d]# vim /code/jc/index.html
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<title>LOVE YOU</title>
<script src="http://apps.bdimg.com/libs/jquery/2.1.4/jquery.min.js"></script>
<link rel="stylesheet" href="http://apps.bdimg.com/libs/bootstrap/3.3.4/css/bootstrap.min.css" >
<script src="http://apps.bdimg.com/libs/bootstrap/3.3.4/js/bootstrap.min.js" ></script>
<meta name="viewport" content="width=device-width, initial-scale=1, maximum-scale=1, user-scalable=no">
</head>
<body>
<div class="container">
<div class="row col-md-3"></div>
<div class="row col-md-6" >
<div class="row question">
<div class="col-md-6 col-xs-12">
<p style="line-height: 50px;font-size: 10px;">"Little Pingping, I've been watching you for a long time. "</p>
<p style="line-height: 50px;font-size: 20px;">Will you be my girlfriend?</p>
</div>
<div class="col-md-6 col-xs-12">
<img src="http://ozef40uqu.bkt.clouddn.com/1.png" alt="" style="height: 200px;">
</div>
</div>
<div class="row question" style="margin-top: 20px;">
<div class="col-md-6 col-xs-6" style="text-align: center;">
<button type="button" class="btn btn-success" style="width: 80%" id="no">good</button>
</div>
<div class="col-md-6 col-xs-6" style="text-align: center;">
<button type="button" class="btn btn-danger" style="width: 80%" id="ok">Not good</button>
</div>
</div>
<div class="col-md-12 col-xs-12 hide" id="success">
<img src="http://ozef40uqu.bkt.clouddn.com/666.jpg" alt="" style="width: 100%;">
</div>
</div>
<div class="row col-md-3"></div>
</div>
<script>
var i=1;
var ok=false;
$(document).ready(function(){
$("#no").click(function(){
alert("Really? You promised?");
alert("Send me a message, love you");
$(".question").addClass('hide');
$("#success").removeClass('hide');
ok=true;
});
$("#ok").click(function(){
switch(i){
case 1:
alert("Pay wages");
break;
case 2:
alert("All housework");
break;
case 3:
alert("Write your name on the real estate certificate");
break;
case 4:
alert("Baoda");
break;
case 5:
alert("My mother can swim");
break;
case 6:
alert("If I don't quarrel with you, I will be coquettish and cute");
break;
default:
alert("Promise me");
}
i++;
});
});
</script>
</body>
</html>
[root@web01 conf.d]#chown -R www.www /code/index.html
[root@web01 conf.d]# systemctl restart nginx
#Configure local hosts
192.168.15.7 jc.linux.com
Configure web sites for hijacking web sites
[root@lb01 conf.d]# vim jc.linux.com.conf
server {
listen 80;
server_name jc.linux.com;
location / {
proxy_pass http://192.168.15.7:80;
include proxy_params;
}
}
[root@lb01 conf.d]# systemctl restart nginx
1,Tampering hosts test 192.168.15.7 jc.linux.com
Tampering with websites
[root@lb01 conf.d]# cat linux12.jc.com.conf
server {
listen 80;
server_name linux12.jc.com;
location / {
proxy_pass http://10.10.0.7:80;
include proxy_params;
sub_filter '<title>LOVE YOU</title>' <title>Mildew</title> ;
}
}
## nginx -t check and restart
[root@web01 ~]# systemctl restart nginx
#Configure hosts
192.168.15.7 jc.linux.com
Introduction to certificate type
| contrast | Domain name DV | Enterprise OV | Enhanced EV |
|---|---|---|---|
| Green address bar | Small lock mark + https | Small lock mark + https | Small lock mark + enterprise name + https |
| General purpose | Personal sites and applications; Simple https encryption requirements | E-commerce sites and applications; SME site | Large financial platform; Large enterprise and government agency sites |
| Audit content | Domain name ownership verification | Comprehensive enterprise authentication; Domain name ownership verification | The highest level of enterprise authentication; Domain name ownership verification |
| Issuance duration | 10 minutes - 24 hours | 3-5 working days | 5-7 working days |
| Single application period | 1 year | 1-2 years | 1-2 years |
| Compensation guarantee fund | - | $1.25-1.75 million | $1.5-1.75 million |
Purchase certificate selection
1.Protect a domain name www.mumusir.com 2.Protect multiple domain names www. test. cdn. image. class. 3.Protect wildcard domain names *.mumusir.com
HTTPS certificate considerations
1.https Renewal is not supported. You need to reapply and replace the certificate when it expires 2.https Level 3 domain name resolution is not supported, such as test.m.haoda.com 3.https The display is green, indicating the of the whole website url All https of https Because the website contains yellow code http Unsafe links https If red is displayed, the certificate is false or expired.
Configure single machine HTTPS certificate
Check whether nginx can use the certificate
[root@web01 ~]# nginx -V --with-http_ssl_module
Create a directory for storing certificates
[root@web01 ~]# mkdir /etc/nginx/ssl_key [root@web01 ~]# cd /etc/nginx/ssl_key/
Generate certificate
[root@web01 ssl_key]# openssl genrsa -idea -out server.key 2048 Generating RSA private key, 2048 bit long modulus ..................................................................................................................................+++ ...............................................................................+++ e is 65537 (0x10001) Enter pass phrase for server.key: Verifying - Enter pass phrase for server.key: [root@web01 ssl_key]# openssl req -days 36500 -x509 -sha256 -nodes -newkey rsa:2048 -keyout server.key -out server.crt Generating a 2048 bit RSA private key ...................................................+++ .................+++ writing new private key to 'server.key' ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [XX]:China string is too long, it needs to be less than 2 bytes long Country Name (2 letter code) [XX]:zg State or Province Name (full name) []:riben Locality Name (eg, city) [Default City]:bali Organization Name (eg, company) [Default Company Ltd]:oldboy Organizational Unit Name (eg, section) []:oldboy Common Name (eg, your name or your server's hostname) []:maliao Email Address []:123@qq.com You have new mail in /var/spool/mail/root [root@web01 ssl_key]# openssl req -days 36500 -x509 -sha256 -nodes -newkey rsa:2048 -keyout server.key -out server.crt # Req -- > used to create a new certificate # New -- > indicates that a new certificate is created # X509 -- > indicates that the format of the defined certificate is standard format # Key -- > indicates the private key file information called # Out -- > indicates the output certificate file information # Days -- > indicates the validity period of the certificate [root@web01 ssl_key]# ll total 8 -rw-r--r-- 1 root root 1375 Mar 5 15:15 server.crt -rw-r--r-- 1 root root 1704 Mar 5 15:15 server.key
nginx certificate configuration syntax
#Start ssl function Syntax: ssl on | off; Default: ssl off; Context: http, server #Certificate file Syntax: ssl_certificate file; Default: — Context: http, server #Private key file Syntax: ssl_certificate_key file; Default: — Context: http, server
Configure nginx certificate
#Configure nginx
[root@web01 ssl_key]# vim /etc/nginx/conf.d/s.linux.com.conf
server {
listen 443 ssl;
server_name s.linux.com;
ssl_certificate /etc/nginx/ssl_key/server.crt;
ssl_certificate_key /etc/nginx/ssl_key/server.key;
location / {
root /code/https;
index index.html;
}
}
#Restart nginx
[root@web01 ssl_key]# systemctl restart nginx
#Configure site
[root@web01 ssl_key]# echo "test https" > /code/https/index.html
Configure hosts access test
10.0.0.7 discuz.linux.com jc.linux.com s.linux.com
Whole station HTTPS
Environmental preparation
| host | Internet IP | Intranet IP | identity |
|---|---|---|---|
| lb01 | 172.168.15.5 | 172.16.1.5 | load balancing |
| web01 | 172.168.15.7 | 172.16.1.7 | web server |
| web02 | 172.168.15.8 | 172.16.1.8 | web server |
Configure web server (two)
[root@web01 conf.d]# vim s.linux.com.conf
server {
listen 80;
server_name s.linux.com;
location / {
root /code/https;
index index.html;
}
}
[root@web01 conf.d]# systemctl restart nginx
#Sync profile
[root@web01 conf.d]# scp s.linux.com.conf 172.16.1.8:/etc/nginx/conf.d/
#Configure site catalog file
[root@web01 conf.d]# mkdir /code/https
[root@web01 conf.d]# echo "https1111" > /code/https/index.html
[root@web02 conf.d]# mkdir /code/https
[root@web02 conf.d]# echo "https2222" > /code/https/index.html
[root@web01 conf.d]# chown -R www.www /code/https/
[root@web02 conf.d]# chown -R www.www /code/https/
[root@web01 conf.d]# systemctl restart nginx
#Join hosts access
Push and upload certificate files
[root@web01 conf.d]# scp -r /etc/nginx/ssl_key 172.16.1.4:/etc/nginx/
Configure the load balancing machine nginx
[root@lb01 conf.d]# vim s.linux.com.conf
upstream webserver {
server 172.16.1.7:80;
server 172.16.1.8:80;
}
server {
listen 443 ssl;
server_name s.linux.com;
ssl_certificate /etc/nginx/ssl_key/server.crt;
ssl_certificate_key /etc/nginx/ssl_key/server.key;
location / {
proxy_pass http://webserver;
}
}
server {
listen 80;
server_name s.linux.com;
return 302 https://$server_name$request_uri;
}
Configure hosts and access test
Project wide HTTPS (I discuz as an example)
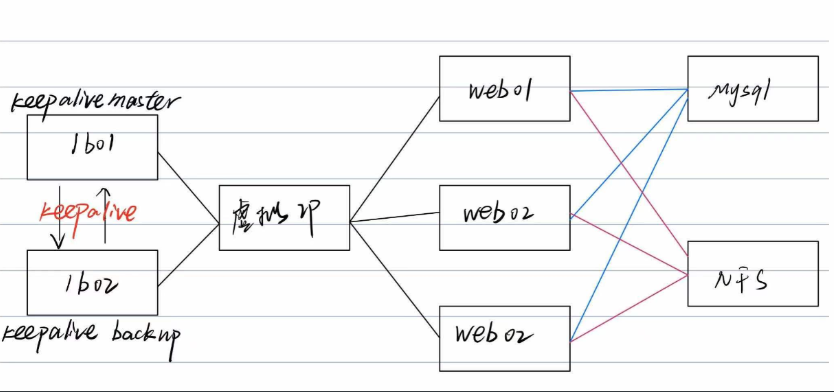
Three web servers mount conf and web on nfs side
[root@web01 nginx]# mount -t nfs 172.16.1.31:/conf /etc/nginx/conf.d/ [root@web01 web]# mount -t nfs 172.16.1.31:/web /web/ #View mount [root@web01 web]# df -h Filesystem Size Used Avail Use% Mounted on 172.16.1.31:/conf 99G 2.7G 97G 3% /etc/nginx/conf.d 172.16.1.31:/web 99G 2.7G 97G 3% /web
Write nginx configuration file
[root@web01 conf.d]# cat discuz.conf
server {
listen 80;
server_name luntan123.com;
root /web/DiscuzX/upload;
location / {
index index.php;
}
location ~* \.php$ {
fastcgi_pass 127.0.0.1:9000;
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
#fastcgi_param HTTPS ON;
include fastcgi_params;
}
}
Upload the code to the web directory and unzip it
[root@web01 web]# ll total 16616 drwxrwxrwx 6 www www 95 Apr 23 14:08 DiscuzX drwxr-xr-x 13 www www 4096 May 6 20:28 phpMyAdmin-5.1.0-all-languages -rw-rw-r-- 1 www www 17005138 May 6 23:02 web.tar.gz drwxr-xr-x 5 www www 4096 May 6 23:05 wordpres #Note: if the DiscuzX installation is not writable, authorize the 777 site directory
The three web s are tested with ip access respectively
#db01 adds a discuz database #Create a user and log in [root@db01 ~]# mysqladmin -uroot password '***' [root@db01 ~]# mysql -uroot -p*** #Create database MariaDB [(none)]> create database discuz; Query OK, 1 row affected (0.00 sec) # Create users to use the web and other websites MariaDB [mysql]> grant all privileges on *.* to baimo@'%' identified by 'baimo'; Query OK, 0 rows affected (0.01 sec) MariaDB [mysql]> flush privileges;#Refresh Query OK, 0 rows affected (0.00 sec) #Install according to the process
Configure pseudo static
[root@web01 conf.d]# cat discuz.conf
server {
listen 80;
server_name luntan123.com;
root /web/DiscuzX/upload;
rewrite ^([^\.]*)/topic-(.+)\.html$ $1/portal.php?mod=topic&topic=$2 last;
rewrite ^([^\.]*)/article-([0-9]+)-([0-9]+)\.html$ $1/portal.php?mod=view&aid=$2&page=$3 last;
rewrite ^([^\.]*)/forum-(\w+)-([0-9]+)\.html$ $1/forum.php?mod=forumdisplay&fid=$2&page=$3 last;
rewrite ^([^\.]*)/thread-([0-9]+)-([0-9]+)-([0-9]+)\.html$ $1/forum.php?mod=viewthread&tid=$2&extra=page%3D$4&page=$3 last;
rewrite ^([^\.]*)/group-([0-9]+)-([0-9]+)\.html$ $1/forum.php?mod=group&fid=$2&page=$3 last;
rewrite ^([^\.]*)/space-(username|uid)-(.+)\.html$ $1/home.php?mod=space&$2=$3 last;
rewrite ^([^\.]*)/blog-([0-9]+)-([0-9]+)\.html$ $1/home.php?mod=space&uid=$2&do=blog&id=$3 last;
rewrite ^([^\.]*)/archiver/(fid|tid)-([0-9]+)\.html$ $1/archiver/index.php?action=$2&value=$3 last;
rewrite ^([^\.]*)/([a-z]+[a-z0-9_]*)-([a-z0-9_\-]+)\.html$ $1/plugin.php?id=$2:$3 last;
if (!-e $request_filename) {
return 404;
}
location / {
index index.php;
}
location ~* \.php$ {
fastcgi_pass 127.0.0.1:9000;
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
fastcgi_param HTTPS ON; #The returned from http is turned on by https garbled code
include fastcgi_params;
}
}
Configure load balancing lb01
Demand analysis:
1. ssl with certificate
2. Load balancing
3. Automatically jump to https when the user accesses (. *);
Generate certificate
[root@lb01 nginx]# mkdir ssl_key [root@lb01 nginx]# cd ssl_key/ [root@lb01 ssl_key]# openssl genrsa -idea -out server.key 2048 [root@lb01 ssl_key]# openssl req -days 36500 -x509 -sha256 -nodes -newkey rsa:2048 -keyout server.key -out server.crt [root@lb01 ssl_key]# ll -rw-r--r-- 1 root root 1220 May 9 14:57 server.crt -rw-r--r-- 1 root root 1704 May 9 14:57 server.key
Configure discuz Conf parsing
[root@lb01 conf.d]# cat discuz.conf
upstream web {
server 172.16.1.7:80;
server 172.16.1.8:80;
server 172.16.1.9:80;
} #Link pool forwarded by proxy
server {
listen 80;
server_name luntan123.com;
rewrite (.*) https://$server_name$request_uri;
} #Listen to port 80 and domain name, and forward any request to https://luntan123.com
server {
listen 443 ssl; #http default port
server_name luntan123.com;
ssl_certificate /etc/nginx/ssl_key/server.crt;
ssl_certificate_key /etc/nginx/ssl_key/server.key;#certificate
location / { #Load balancing forwarding after receiving the request
proxy_pass http://web;# ip forwarded to link pool
proxy_set_header host $http_host;#Forward with domain name
}
}
Configuration code
[root@lb01 conf.d]# cat /etc/nginx/conf.d/discuz.conf
upstream web {
server 172.16.1.7:80;
server 172.16.1.8:80;
server 172.16.1.9:80;
}
server {
listen 80;
server_name luntan123.com;
return 302 https://$server_name$request_uri;
}
server {
listen 443 ssl;
server_name luntan123.com;
ssl_certificate /ssl_key/server.crt;
ssl_certificate_key /ssl_key/server.key;
location / {
proxy_pass http://web;
include proxy_params;
}
}
Configure hosts access
#Visit successful
==============================================================================================================
Page format disorder
Problem: because load balancing requests web End is http Request, web End request php Also http Format, php The returned content is http Format content, what our browser requests is https,Therefore, the format display is disordered, and we need to configure it so that php The format returned is https format
#The page format is chaotic, and the HTTPS mode is enabled when the proxy arrives at php
[root@web01 ~]# vim /etc/nginx/conf.d/blog.linux.com.conf
server {
... ...
location ~* \.php$ {
root /code/wecenter;
fastcgi_pass 127.0.0.1:9000;
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
#Enable https mode
fastcgi_param HTTPS on;
include fastcgi_params;
}
}
Alicloud configuring https
1.Purchase virtual machine 2.Resolve domain name 3.Corresponding to the application domain name https certificate 4.take https Deploy certificate to server