Anyone who has used WebSecurityConfigurerAdapter knows that it is very important for Spring Security and is in charge of the configuration system of Spring Security. But this class will be abolished soon. You are right. This class will be marked by @ Deprecated in version 5.7. This class will be removed in the future.
In this regard, netizens shouted that "learning is abandoned". Since it will be abandoned soon, there must be a transition plan or a new way to play.
As early as March 2021, fat brother wrote it An article , make the new playing method clear. If you read it, you won't learn abandoned technology. Let's go over the whole set of alternatives here and stop learning outdated technology.
The version requires spring security 5.4 X and above.
Comparison of old and new playing methods of HttpSecurity
Old play:
@Configuration
static class SecurityConfig extends WebSecurityConfigurerAdapter {
@Override
protected void configure(HttpSecurity http) throws Exception {
http
.antMatcher("/**")
.authorizeRequests(authorize -> authorize
.anyRequest().authenticated()
);
}
}New play:
@Bean
SecurityFilterChain filterChain(HttpSecurity http) throws Exception {
return http
.antMatcher("/**")
.authorizeRequests(authorize -> authorize
.anyRequest().authenticated()
)
.build();
}Principle to see this article.
Comparison of old and new playing methods of WebSecurity
Using websecurity Ignoring () ignores some URL requests, which will be ignored by Spring Security, which means that these URLs may be attacked by CSRF, XSS, Clickjacking, etc. The following example is for demonstration only and should not be used in a production environment. Did you learn it again?
Old play:
@Configuration
public class SecurityConfiguration extends WebSecurityConfigurerAdapter {
@Override
public void configure(WebSecurity web) {
// Just as a demonstration
web.ignoring().antMatchers("/ignore1", "/ignore2");
}
}New play:
@Configuration
public class SecurityConfiguration {
@Bean
public WebSecurityCustomizer webSecurityCustomizer() {
// Just as a demonstration
return (web) -> web.ignoring().antMatchers("/ignore1", "/ignore2");
}
}If you need to ignore the URL, please consider using httpsecurity Authorizehttprequests is implemented by permitAll.
Comparison of old and new playing methods of authentication manager
Authentication manager configuration is mainly divided into Global and Local.
Old play
@Configuration
public class SecurityConfiguration extends WebSecurityConfigurerAdapter {
@Override
protected void configure(AuthenticationManagerBuilder auth) throws Exception {
auth.jdbcAuthentication();
}
}The above is enabled through WebSecurityConfigurerAdapter, which is local configuration. To enable global configuration, you need to override its authenticationManagerBean() method and mark it as Bean:
@Bean(name name="myAuthenticationManager")
@Override
public AuthenticationManager authenticationManagerBean() throws Exception {
return super.authenticationManagerBean();
}New play
Local configuration via httpsecurity AuthenticationManager implementation:
@Configuration
public class SecurityConfiguration {
@Bean
public SecurityFilterChain filterChain(HttpSecurity http) throws Exception {
http
.authorizeHttpRequests((authz) -> authz
.anyRequest().authenticated()
)
.httpBasic(withDefaults())
.authenticationManager(new CustomAuthenticationManager());
}
}Global configuration gets rid of the dependency on websecurityconfigureradapter The authenticationmanagerbean () method only needs to define a Bean of AuthenticationManager type:
@Bean
AuthenticationManager ldapAuthenticationManager(
BaseLdapPathContextSource contextSource) {
LdapBindAuthenticationManagerFactory factory =
new LdapBindAuthenticationManagerFactory(contextSource);
factory.setUserDnPatterns("uid={0},ou=people");
factory.setUserDetailsContextMapper(new PersonContextMapper());
return factory.createAuthenticationManager();
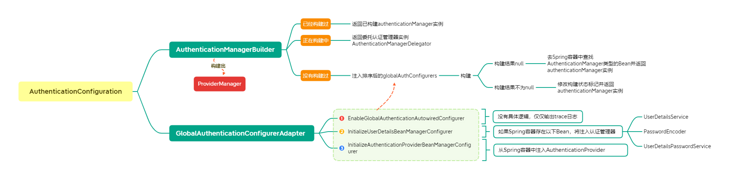
}Of course, you can also modify the AuthenticationManagerBuilder by customizing the GlobalAuthenticationConfigurerAdapter and injecting Spring IoC. There is no limit to the number, but you should pay attention to the sorting problem. Related mind maps:
last
Many technical solutions are not changed directly. There will be a change process. As long as you keep up with the change, there will be no change.
Pay attention to the official account: Felordcn for more information