The words written in the front
HTTP/1.1 has gone through a long development process from 1991 to 2014:
- HTTP/0.9– 1991
- HTTP/1.0– 1996
- HTTP/1.1
- RFC 2068– 1997
- RFC 2616- 1999
- RFC 7230- 2014
This means that various servers and clients in the Internet may have many security problems, which will also create opportunities for HTTP smuggling attack (HTTP data receiving asynchronous attack).
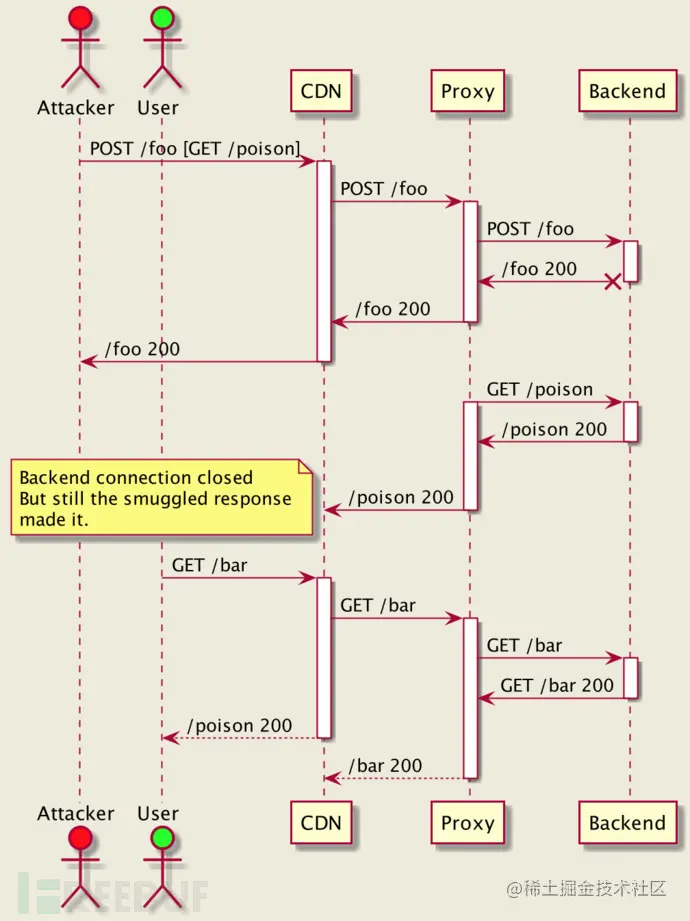
\
It seems easy to follow the latest RFC recommendations. However, for large systems that have existed for some time, it may bring many unacceptable effects on system availability.
http_desync_guardian came into being as a tool library. This tool can help researchers analyze HTTP requests to prevent HTTP smuggling attacks (HTTP data receiving asynchronous attacks), and also take into account security and availability. The tool can classify requests and provide processing suggestions for each layer.
The tool can analyze both the original HTTP request Header and the request data that has been analyzed by the HTTP engine.
Tool properties
1. The unity of services is the key. This means that request classification, logging, and measurement must be done in the background and use the least available settings (for example, the destination address of the log file).
2. Focus on auditability. The test suite does not need knowledge about the library / programming language, but only about the HTTP protocol. Therefore, it is easy to review, contribute code, and reuse.
3. Security is the most important for users.
4. Lightweight, very low overhead, and no additional overhead is required to process requests.
Supported HTTP versions
The tool is mainly aimed at HTTP/1.1. For details, please refer to the coverage test cases provided.
The predecessor of HTTP/1.1 does not support connection reuse, which limits the opportunity of HTTP desynchronization. However, some agents may upgrade such requests to HTTP/1.1 and reuse back-end connections, which may lead to malicious HTTP/1.0 requests. This is why we chose to analyze them using the same standards as HTTP/1.1. For other protocol versions, please refer to this [document].
Tool download
Researchers can use the following commands to clone the source code of the project locally:
git clone https://github.com/aws/http-desync-guardian.git Copy code
C code usage
The tool library mainly uses the HTTP engine developed by C/C + +. The tool installation and configuration methods are as follows:
1. To install cbindgen:
cargo install --force cbindgen Copy code
2. Generate Header file:
C:
cbindgen --output http_desync_guardian.h --lang c Copy code
C++:
cbindgen --output http_desync_guardian.h --lang c++ Copy code
3. Run the following command, where the relevant code is located at“
./target/release/libhttp_desync_guardian.*” File:
cargo build --release Copy code
#include "http_desync_guardian.h"
/*
* http_engine_request_t - already parsed by the HTTP engine
*/
static int check_request(http_engine_request_t *req) {
http_desync_guardian_request_t guardian_request = construct_http_desync_guardian_from(req);
http_desync_guardian_verdict_t verdict = {0};
http_desync_guardian_analyze_request(&guardian_request, &verdict);
switch (verdict.tier) {
case REQUEST_SAFETY_TIER_COMPLIANT:
// The request is good. green light
break;
case REQUEST_SAFETY_TIER_ACCEPTABLE:
// Reject, if mode == STRICTEST
// Otherwise, OK
break;
case REQUEST_SAFETY_TIER_AMBIGUOUS:
// The request is ambiguous.
// Reject, if mode == STRICTEST
// Otherwise send it, but don't reuse both FE/BE connections.
break;
case REQUEST_SAFETY_TIER_SEVERE:
// Send 400 and close the FE connection.
break;
default:
// unreachable code
abort();
}
}
Copy codeLicense agreement
The development and release of this project follows the Apache-2.0 open source license agreement.