Author: auok007[1]
Above
Last time I sent it, I saw a lot of people and commented on the analysis of a honeypot contract [2], which is the most commented article in my articles.
In the process of writing, I also tried and analyzed while writing. The previous part misled some people who read the article. I apologize. I also learned a lot in the process of writing. I'll talk about the last process again, and send out the links of each call on ethscan. Later, I'll restore the contract code calling New.
technological process
1. Deploy the contract, Ethereum Transaction Hash (Txhash) Details | Etherscan[3]2, call New to set the answer hash Ethereum Transaction Hash (Txhash) Details | Etherscan[4]3, Start, input two eth Ethereum Transaction Hash (Txhash) Details | Etherscan[5]4, someone Try, Invest at least one eth Ethereum Transaction Hash (Txhash) Details | Etherscan[6]5, Stop income and transfer it back to your wallet. Ethereum Transaction Hash (Txhash) Details | Etherscan[7]
Call history list of contracts:
Contract d732e40d353aa772a7f82b4b310e75925853a040 in Ethereum - Ethereum Contract Library by Dedaub (contract-library.com)[8]
Summary
Now it seems that this contract has no technical content. There are two advantages: 1. Set the administrator when deploying the contract. 2. Hide the New call on ethscan.
Contract call hiding
Let's talk about the contract for calling New: from the above New call record, we can know that it hides the call through the contract call contract, and the contract for initiating the call is not audited, so you can't see the function name of initiating New call on ethscan. input Ethereum Transaction Hash (Txhash) Details | Etherscan[9]
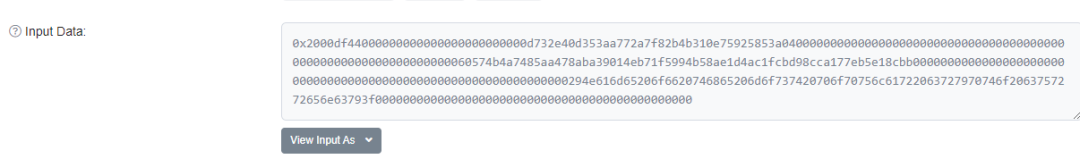
Contract Code: contract 0x1ba21c6ccdcd3d082d8bbe95bc5b78f4edc3e80d4 in Ethereum - Ethereum contract library by dedaub (contract library. Com) [10]
// Decompiled at www.contract-library.com
// 2022.01.21 17:07 UTC
// Data structures and variables inferred from the use of storage instructions
address owner; //STORAGE[0x0] bytes 0 to 19
function fallback() public payable {
find similar
}
function 0x2000df44(address varg0, uint256 varg1, uint256 varg2) public payable {
find similar
require(msg.data.length - 4 >= 96);
require(varg0 == varg0);
require(varg1 <= 0xffffffffffffffff);
require(4 + varg1 + 31 < msg.data.length);
require((?).length <= 0xffffffffffffffff);
require(4 + varg1 + (?).length + 32 <= msg.data.length);
require(msg.sender == owner);
v0 = new array[]((? "").length);
MEM[4 + MEM[64] + (?).length + 96] = 0;
require(varg0.code.size);
v1 = varg0.New(v0, varg2).gas(msg.gas);
require(v1);
// checks call status, propagates error data on error
}
// Note: The function selector is not present in the original solidity code.
// However, we display it for the sake of completeness.
function __function_selector__(uint256 function_selector) public payable {
MEM[64] = 128;
require(!msg.value);
if(msg.data.length >= 4) {
if(0x2000df44 == function_selector >> 224) {
0x2000df44();
}
}
fallback();
}
Translated into solid code as follows:
contract Hacker {
address owner;
constructor() {
owner = msg.sender;
}
function myCall(
address varg0,
uint256 varg1,
uint256 varg2
) public payable {
require(owner == msg.sender);
defi_game(varg0).New(varg1, varg2);
}
}
So it's as simple as that. There is no call record of this contract on ethscan. Not on ethscan, but in other places.
A little guess
I think changing multicall should be able to hide better.
function multicall(bytes[] calldata data) public payable override returns (bytes[] memory results) {
results = new bytes[](data.length "");
for (uint256 i = 0; i < data.length; i++) {
(bool success, bytes memory result) = address(this).delegatecall(data[i]);
if (!success) {
// Next 5 lines from https://ethereum.stackexchange.com/a/83577
if (result.length < 68) revert();
assembly {
result := add(result, 0x04)
}
revert(abi.decode(result, (string)));
}
results[i] = result;
}
}
How to change it? Just change the function name. Don't do bad things. I'm just a technical exchange.
reference material
[1]
auok007: https://learnblockchain.cn/people/6025
[2]
Analysis of a honeypot contract: https://learnblockchain.cn/article/3509
[3]
Ethereum Transaction Hash (Txhash) Details | Etherscan: https://etherscan.io/tx/0x691A0B51049B0A53B2E6AC8AE3D6D0B5EC8D90AF69092E022AAB809DC2BC8262
[4]
Ethereum Transaction Hash (Txhash) Details | Etherscan: https://etherscan.io/tx/0x8874F555001B19A735CDB5224F67DF3EC83DB5F25782D5BEC698C433D270133B
[5]
Ethereum Transaction Hash (Txhash) Details | Etherscan: https://etherscan.io/tx/0x741C21A737D485FE23F03116C5B8E49A44FC896D473520B32AC994D3283C61F5
[6]
Ethereum Transaction Hash (Txhash) Details | Etherscan: https://etherscan.io/tx/0x9765B44C3E3ACF2A9609E89C41D8D67FD926DE8EB43B8D41F0948A2D9147CD73
[7]
Ethereum Transaction Hash (Txhash) Details | Etherscan: https://etherscan.io/tx/0xD270AC214EDAA775D68BAD267C678D782DDCE58A44835B2B2625ECF19C4F1AE1
[8]
Contract d732e40d353aa772a7f82b4b310e75925853a040 in Ethereum - Ethereum Contract Library by Dedaub (contract-library.com): https://contract-library.com/contracts/Ethereum/d732e40d353aa772a7f82b4b310e75925853a040/transactions
[9]
Ethereum Transaction Hash (Txhash) Details | Etherscan: https://etherscan.io/tx/0x8874F555001B19A735CDB5224F67DF3EC83DB5F25782D5BEC698C433D270133B
[10]
Contract 0x1ba21C6cfcD3D082d8Bbe95bC5B78F4eDC3e80D4 in Ethereum - Ethereum Contract Library by Dedaub (contract-library.com): https://contract-library.com/contracts/Ethereum/0x1ba21C6cfcD3D082d8Bbe95bC5B78F4eDC3e80D4