Encrypt script first:
import org.apache.commons.codec.binary.Base64; import java.io.ByteArrayOutputStream; import java.security.Key; import java.security.KeyFactory; import java.security.KeyPair; import java.security.KeyPairGenerator; import java.security.PrivateKey; import java.security.PublicKey; import java.security.Signature; import java.security.interfaces.RSAPrivateKey; import java.security.interfaces.RSAPublicKey; import java.security.spec.PKCS8EncodedKeySpec; import java.security.spec.X509EncodedKeySpec; import java.util.HashMap; import java.util.Map; import javax.crypto.Cipher; String RSA_PUB_KEY="Your public key";//Remove the head and tail String KEY_ALGORITHM = "RSA"; String SIGNATURE_ALGORITHM = "MD5withRSA"; int MAX_ENCRYPT_BLOCK = 117; int MAX_DECRYPT_BLOCK = 128; public static byte[] decryptByPublicKey(byte[] encryptedData, String publicKey) throws Exception { byte[] keyBytes = Base64.decodeBase64(publicKey); X509EncodedKeySpec x509KeySpec = new X509EncodedKeySpec(keyBytes); KeyFactory keyFactory = KeyFactory.getInstance(KEY_ALGORITHM); Key publicK = keyFactory.generatePublic(x509KeySpec); Cipher cipher = Cipher.getInstance(keyFactory.getAlgorithm()); cipher.init(Cipher.DECRYPT_MODE, publicK); int inputLen = encryptedData.length; ByteArrayOutputStream out = new ByteArrayOutputStream(); int offSet = 0; byte[] cache; int i = 0; // Segment decryption of data while (inputLen - offSet > 0) { if (inputLen - offSet > MAX_DECRYPT_BLOCK) { cache = cipher.doFinal(encryptedData, offSet, MAX_DECRYPT_BLOCK); } else { cache = cipher.doFinal(encryptedData, offSet, inputLen - offSet); } out.write(cache, 0, cache.length); i++; offSet = i * MAX_DECRYPT_BLOCK; } byte[] decryptedData = out.toByteArray(); out.close(); return decryptedData; } public static byte[] encryptByPublicKey(byte[] data, String publicKey) throws Exception { byte[] keyBytes = Base64.decodeBase64(publicKey); X509EncodedKeySpec x509KeySpec = new X509EncodedKeySpec(keyBytes); KeyFactory keyFactory = KeyFactory.getInstance("RSA"); Key publicK = keyFactory.generatePublic(x509KeySpec); // Encrypt data Cipher cipher = Cipher.getInstance("RSA"); cipher.init(Cipher.ENCRYPT_MODE, publicK); int inputLen = data.length; ByteArrayOutputStream out = new ByteArrayOutputStream(); int offSet = 0; byte[] cache; int i = 0; // Segment encryption of data while (inputLen - offSet > 0) { if (inputLen - offSet > MAX_ENCRYPT_BLOCK) { cache = cipher.doFinal(data, offSet, MAX_ENCRYPT_BLOCK); } else { cache = cipher.doFinal(data, offSet, inputLen - offSet); } out.write(cache, 0, cache.length); i++; offSet = i * MAX_ENCRYPT_BLOCK; } byte[] encryptedData = out.toByteArray(); out.close(); return encryptedData; } String str=vars.get("body"); String result =""; try { result = Base64.encodeBase64String(encryptByPublicKey(str.getBytes(), RSA_PUB_KEY)); System.out.println(result); } catch (Exception e) { // TODO Auto-generated catch block e.printStackTrace(); } print(result); vars.put("sign",result); vars.put("RSA_PUB_KEY",RSA_PUB_KEY); log.info("Encrypted string=",result); log.info("encryption body=",str); return result;
1. Because the encrypted parameters are put into the request body, I define a string in json format in another beanshell, and then this causes a problem: string with escape character, jmeter will directly report an error if it uses $to reference the string with escape character!!!! The solution is to use vars.get("body") instead to get public variables
2. The encrypted string is directly inserted into the request body
3. The returned message is the ciphertext encrypted by private key and decrypted by public key. Here I choose to decrypt it by post processor:
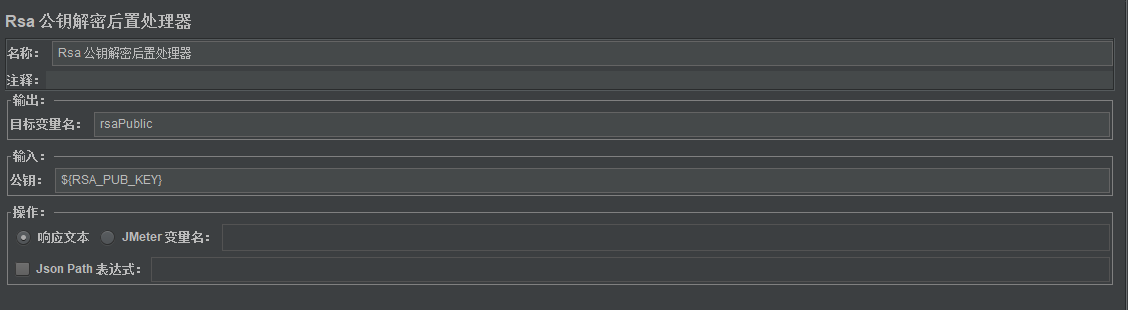
Output: name the output parameter of decryption result
Input: import rsa public key, which has been defined in the above script in advance
Action: if the decrypted json is the response, check the response text - jsonpath expression
If the returned ciphertext is encrypted, check only the response text and not jsonpath. Here I use this method
For other variables decryption, check the variable name and enter
Version of jmeter used: 5.1.1 r1855173
Download address:
Links: https://pan.baidu.com/s/1lpvmNd7jd5v7vG3IGfum2A Extraction code: q8ym
Reference: https://www.cnblogs.com/artoftest/p/7298929.html
https://blog.csdn.net/q13554515812/article/details/99298387