1, Target
Boss Li: Feifei, you've written several articles on x-sign and have been running around Apk. When shall we analyze its so?
Fenfei: step by step. We just located its so last time. Today we will analyze it.
App version: v4 fifteen point one
2, Steps
Entrance of Native layer
Remember this stack first
[NewStringUTF] bytes:x-sign Rc Full call stack:dalvik.system.VMStack.getThreadStackTrace(Native Method) tt: java.lang.Thread.getStackTrace(Thread.java:1538) tt: com.txxxao.wireless.security.adapter.JNICLibrary.doCommandNative(Native Method) tt: com.axxbxxx.wireless.security.mainplugin.а.doCommand(Unknown Source:0) tt: com.axxbxxx.wireless.security.middletierplugin.c.d.a.a(Unknown Source:280) tt: com.axxbxxx.wireless.security.middletierplugin.c.d.a$a.invoke(Unknown Source:56) tt: java.lang.reflect.Proxy.invoke(Proxy.java:913) tt: $Proxy12.getSecurityFactors(Unknown Source) tt: mtopsdk.security.d.a(lt:620) tt: mtopsdk.mtop.a.a.a.a.a(lt:218) tt: mtopsdk.framework.a.b.d.b(lt:45) tt: mtopsdk.framework.b.a.a.a(lt:60) 0xcb434e10 libsgmiddletierso-6.5.50.so!0x33e10 0xcb404e28 libsgmiddletierso-6.5.50.so!0x3e28 0xc9dd5536 libsgmainso-6.5.49.so!0x10536 0xc9dd71c8 libsgmainso-6.5.49.so!0x121c8 0xf365607a libart.so!art_quick_generic_jni_trampoline+0x29 0xf364068a libart.so!MterpAddHotnessBatch+0x29 0xf3651b76 libart.so!art_quick_invoke_stub_internal+0x45
He can talk, he told us
1. The jni function is called com txxxao. wireless. security. adapter. JNICLibrary. doCommandNative.
2. doCommandNative is implemented in libsgmainso-6.5 49. So, it may be near the offset 0x121c8.
Hook jni function first
jni function will tell us type of the return value of the input parameter, so we can't let it go.
The jni function is declared in libsgmain So this fake so inside
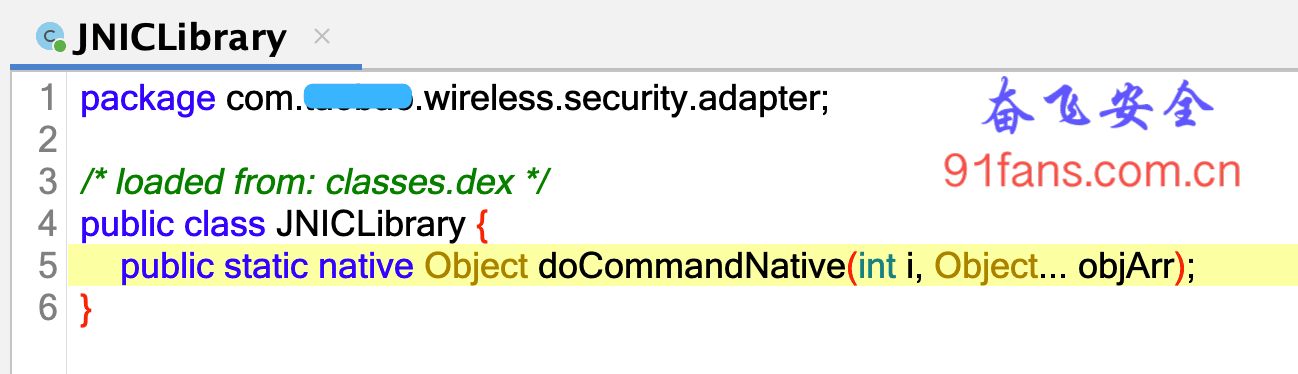
This jni function has two parameters. The first parameter is int and the second parameter is Object array
Let's go to frida first to see if it's our goal.
Java.enumerateClassLoaders({
"onMatch": function(loader) {
if (loader.toString().indexOf("libsgmain.so") >= 0 ) {
Java.classFactory.loader = loader; // Specify the loader in the current class factory as the one we need
console.log("loader = ",loader.toString());
}
},
"onComplete": function() {
console.log("success");
}
});
// You need to use Java classFactory. use
var signCls = Java.classFactory.use('com.txxxao.wireless.security.adapter.JNICLibrary');
signCls.doCommandNative.implementation = function(a,b){
var retval = this.doCommandNative(a,b);
console.log(" #### >>> a = " + a);
if( a == 70102){
console.log(" #### >>> Obj = " + b);
}
console.log(" #### >>> rc= " + retval) // .entrySet().toArray());
// var stack = threadinstance.currentThread().getStackTrace();
// console.log("#### >>> Rc Full call stack:" + Where(stack));
return retval;
}
// */Let's explain the origin of this 70102. doCommandNative obviously undertakes many functions. It's too messy for us to print all of them.
From the previous stack com axxbxxx. wireless. security. middletierplugin. c. In the class d.a.a, it is known that the command parameter used for x-sign signature is 70102 (the corresponding code is in the false so of libsgmiddletier.so)
Run
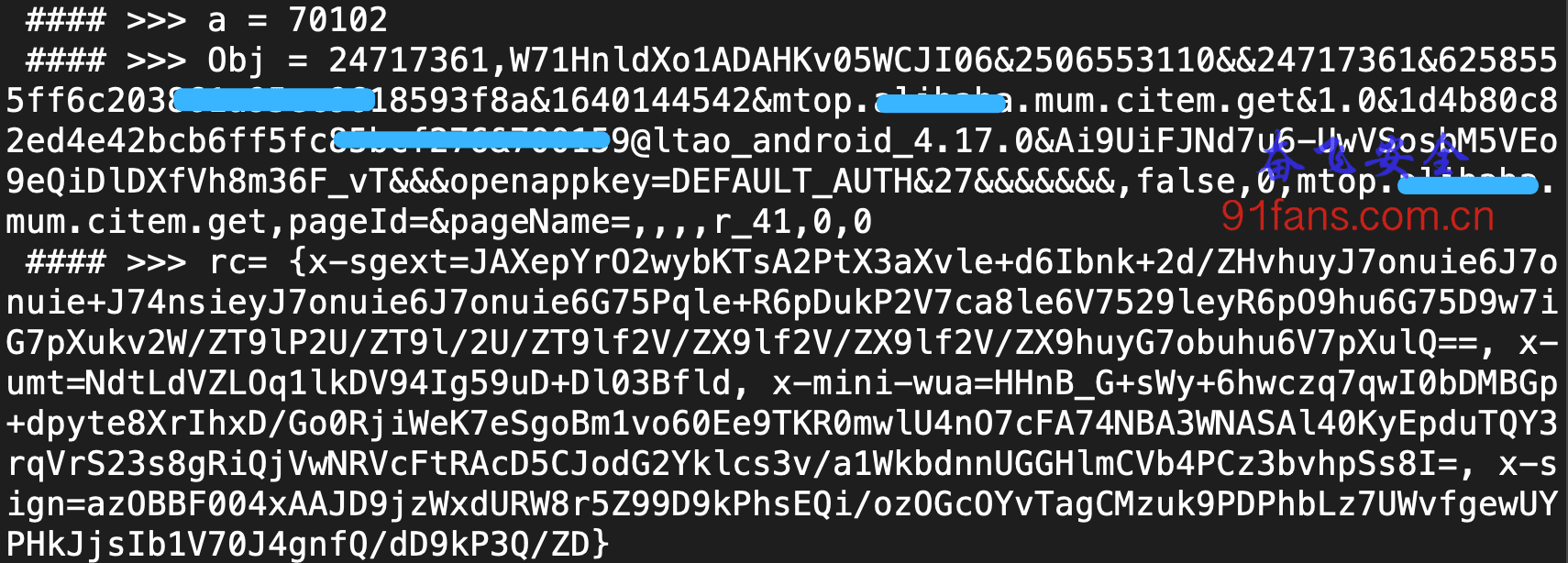
Confirmed the eyes, that's it.
Tip: when running this script in Frida spawn mode, the loader does not output. At this time, modify the script to any space, and then save it. Frida will be automatically reloaded and output will be available at this time.
ida libsgmainso-6.5 49.so
This so is very interesting.
Firstly, doCommandNative cannot be found in his export function, indicating that it is dynamically registered.

The second is that the functions with a little identity in so are all dynamic jumps. Effectively resisted the F5 of ida.
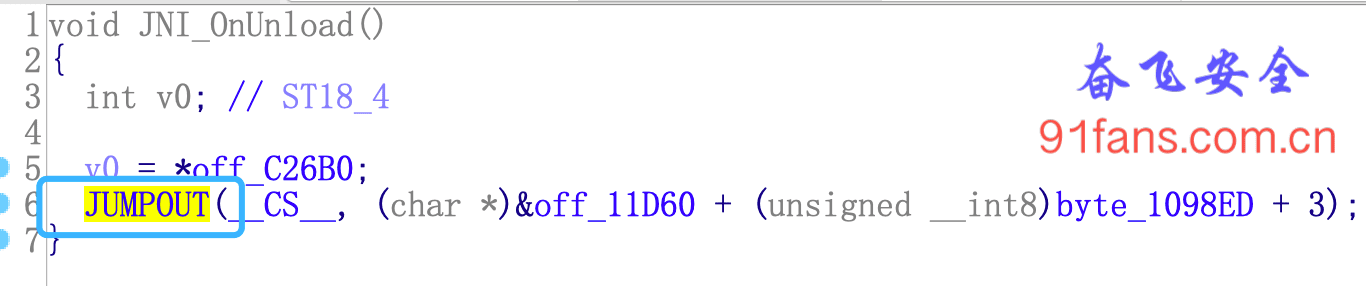
Let's solve it one by one.
We are not afraid of dynamic registration. Hook RegisterNatives can handle it
[RegisterNatives] java_class: com.txxxao.wireless.security.adapter.JNICLibrary name: doCommandNative sig: (I[Ljava/lang/Object;)Ljava/lang/Object; fnPtr: 0x7637c25ba4 module_name: libsgmainso-6.5.49.so module_base: 0x7637c07000 offset: 0x1eba4
As a result, our goal is 0x1eba4
It's embarrassing that the position of 0x1eba4 in ida doesn't look like a function.
What should I do?
From the various performances of this so, will it have some self modification methods at runtime?
No matter how much, let's talk about this so from the run-time dump.
Tip: dump so method reference http://91fans.com.cn/post/carcommunitytwo/
My test phone is 64 bit, so dump comes up with a 64 bit so

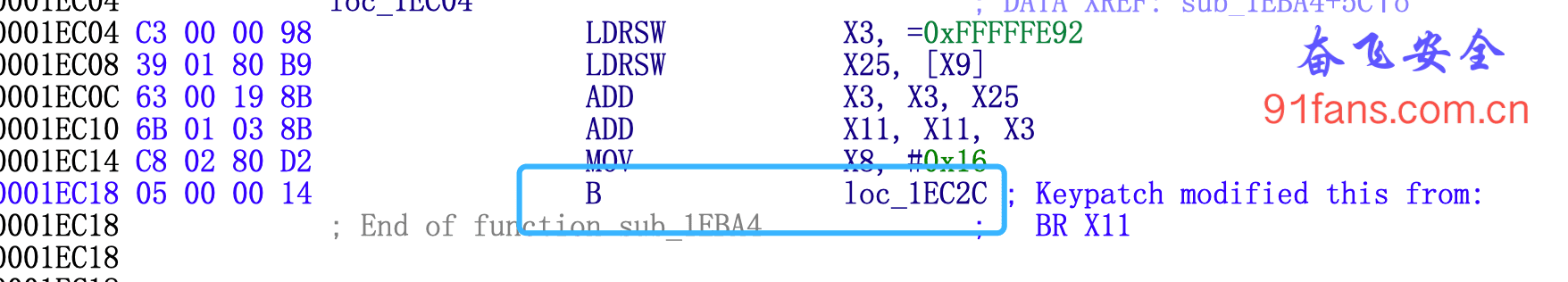
It's so interesting this time, but due to the annoying dynamic jump of BR X11, we still can't be happy f5
Fix it
If we know the x11 value of the BR X11 instruction and change it to a static jump, can we fix the poor F5?
Just do it
var mbase = Module.getBaseAddress('libsgmainso-6.5.49.so');
Interceptor.attach(mbase.add(0x1EC18),{
onEnter:function(args){
console.log('Context : ' + JSON.stringify(this.context));
}
});Print out
Context : {"pc":"0x7637921c18","sp":"0x7639089340","x0":"0x20","x1":"0x76390893e4","x2":"0x2776","x3":"0x28","x4":"0x1","x5":"0x0","x6":"0x4","x7":"0x0","x8":"0x16","x9":"0x7639089350","x10":"0x7637a6cd60","x11":"0x7637921c2c","x12":"0x76390893e8","x13":"0x76390893d8","x14":"0x1","x15":"0x0","x16":"0x76dadbf000","x17":"0x76da67d440","x18":"0x0","x19":"0x76506125e0","x20":"0x0","x21":"0x2776","x22":"0x76390896bc","x23":"0x7650261ddf","x24":"0x8","x25":"0x196","x26":"0x763908d588","x27":"0x2","x28":"0x76390893e8","fp":"0x76390893b0","lr":"0x76dadbf60c"}The current address is 0x7637921c18 - 0x1EC18 = 0x763793000, indicating that the so base address is 0x763793000, and the value of X11 is 0x7637921c2c - 0x763793000 = 0x1EC2C, indicating that you want to jump to 0x1EC2C here
Then change this line of instruction to b 0x1EC2C
F5 again, it will be more beautiful than before
Hook is the doCommandNative of the Native layer
Here we mainly introduce how to print the parameters of Object [] type in the Hook Native function
var mbase = Module.getBaseAddress('libsgmainso-6.5.49.so');
// 1ed4c
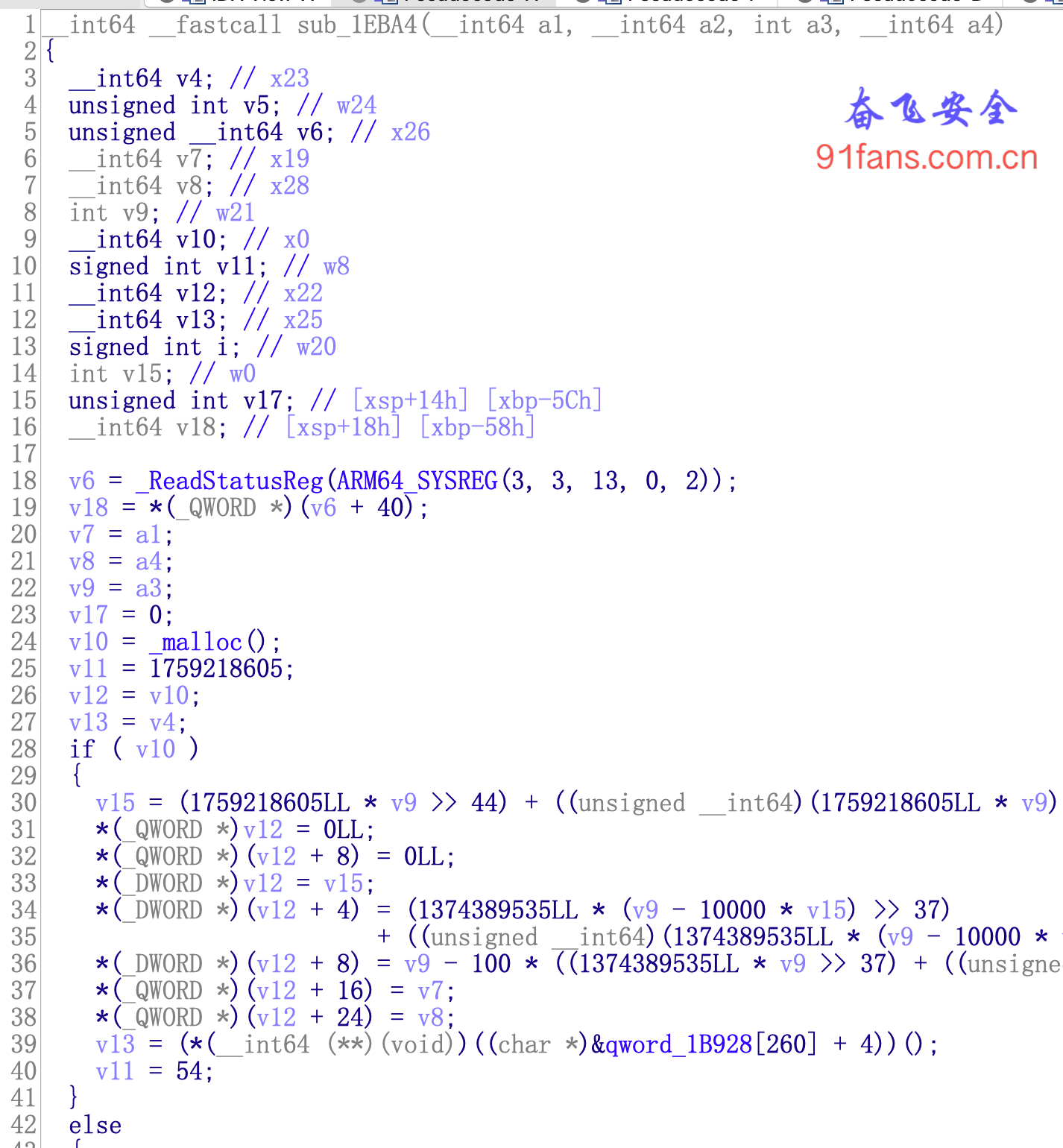
Interceptor.attach(mbase.add(0x1EBA4),{
onEnter:function(args){
console.log('doCommandNative = ' + args[2].toString(10));
var Object_javaArray = Java.use('[Ljava.lang.Object;');
var ArrayArgs_3 = Java.cast(args[3], Object_javaArray);
var ArrayClz = Java.use("java.lang.reflect.Array");
var len = ArrayClz.getLength(ArrayArgs_3);
if( args[2].toString(10) == 70102) {
for(let i=0;i!=len;i++){
var objUse = ArrayClz.get(ArrayArgs_3,i);
if(objUse != null){
console.log("args[3] String value:", objUse.toString());
}
}
}
}
});Start with Java Cast type, and then Java lang.reflect. Array to traverse.
The result is quite beautiful
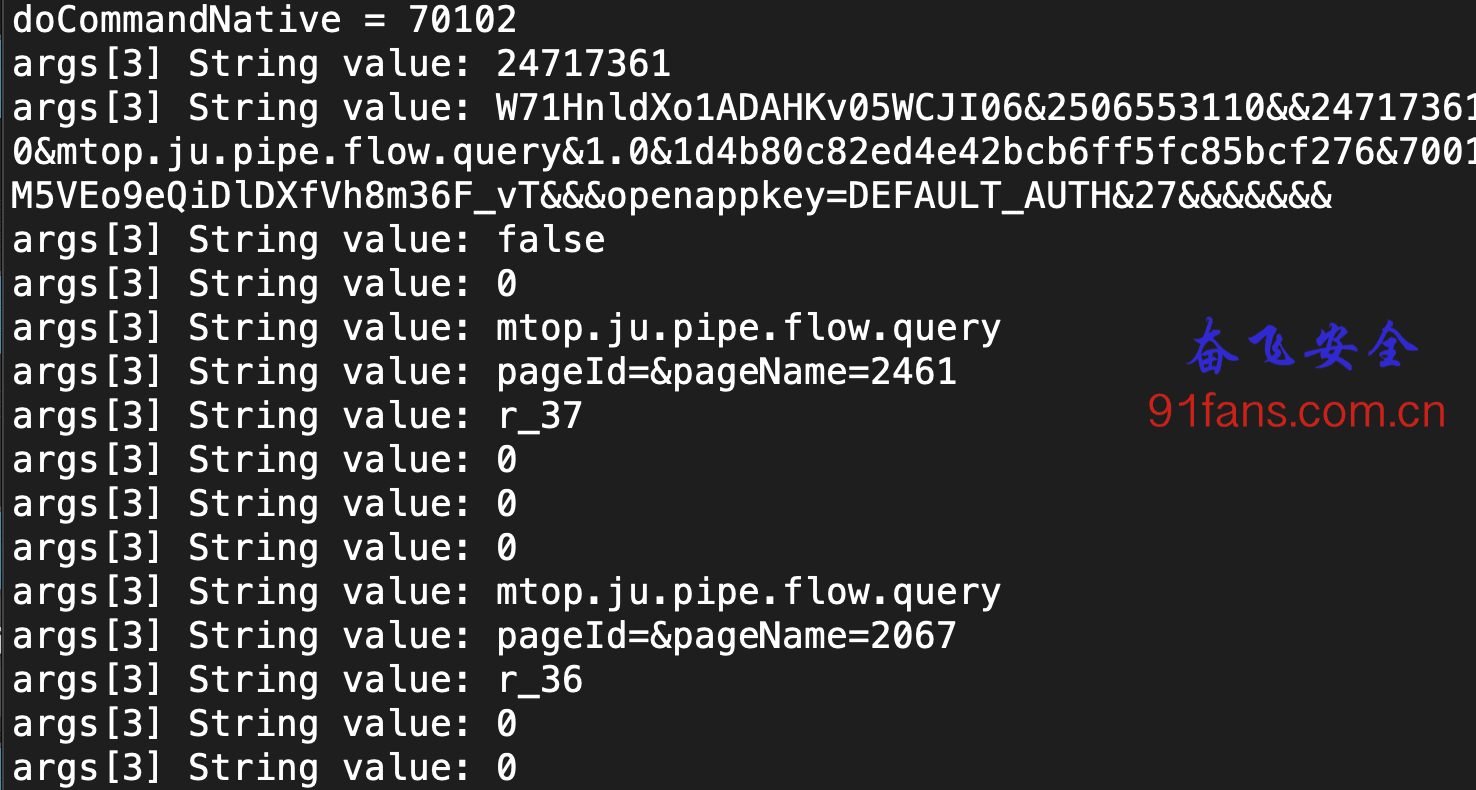
3, Summary
There are more protection measures in the Native layer. Everyone is too voluminous.
Mastering the reflection usage of java is a necessary condition for playing frida well.
ida's F5 is also strictly guarded, so we should also understand the repair scheme.

I wanted to play in the world. Why did I end up playing in the world.
TIP: the only purpose of this article is to learn more reverse skills and ideas. If someone uses this technology to engage in illegal business and obtain benefits, the legal responsibility is borne by the operator, which has nothing to do with this article and the author. The code projects involved in this article can be taken by the friends who are struggling, Welcome to join the knowledge planet to learn and explore technology. If you have any questions, you can add me wx: fenfei331 to discuss them.
WeChat official account: flair safety, latest technology dry cargo push in real time