ADB summary of Android
The contents of this paper are as follows:
1. makefile analysis and summary
2. Introduction to adb framework
3. adbd source code analysis
3.1} adbd initialization process analysis
3.2 # adb # shell process analysis
3.3 # adb # root process analysis
4. adb common commands
1, makefile analysis and summary
Summary of key points:
2, Introduction to adb framework
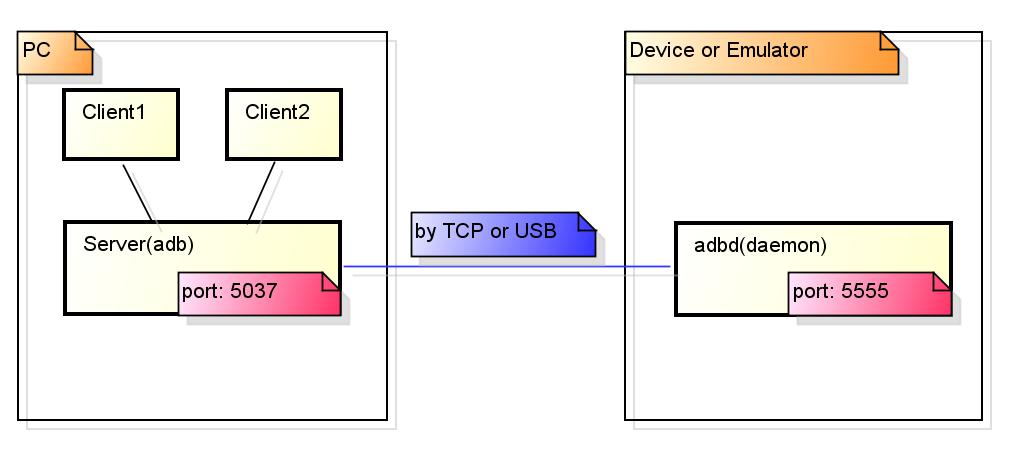
ADB It is the abbreviation of "Android Debug Bridge", which is essentially a command line tool based on "C/S" architecture. The whole ADB module consists of the following parts (see system / core / ADB / overviews.txt and transports.txt for details):
- The # ADB # server(adb): a background application running on the PC side, which is used to detect the connection or removal of Android # devices, and then maintain the device status list. In addition, ADB # Server will also be responsible for coordinating the data transmission between Client, Services and Android # devices.
- The # ADB # daemon (adbd): a background daemon running on Android # Devices or Emulator. This process is mainly used to connect to ADB} Server and provide some services for ADB} clients through USB (or TCP).
- The ADB command line client: the terminal that executes the ADB command. Specifically, it will connect to the ADB server and send a request command to the ADB server. If it is found that the ADB server is not started, it will automatically wake up the ADB server
- Services: some of The capabilities of ADB can be abstracted into services for The # ADB # command line # client to access. It can be divided into Host services and Local services, which are briefly described as follows:
Note: This article only analyzes the implementation of ADBD.
3, adbd source code analysis
- adbd initialization process analysis
ADB is divided into two modes: USB ADB and wifi ADB. They are mutually exclusive. USB ADB is used by default If you want to start wifi # ADB by default, you need to set the property service adb. tcp. The port value is 55555, and then restart adbd. ADB daemon(usb adb.) The main steps of program startup are shown in the figure below.
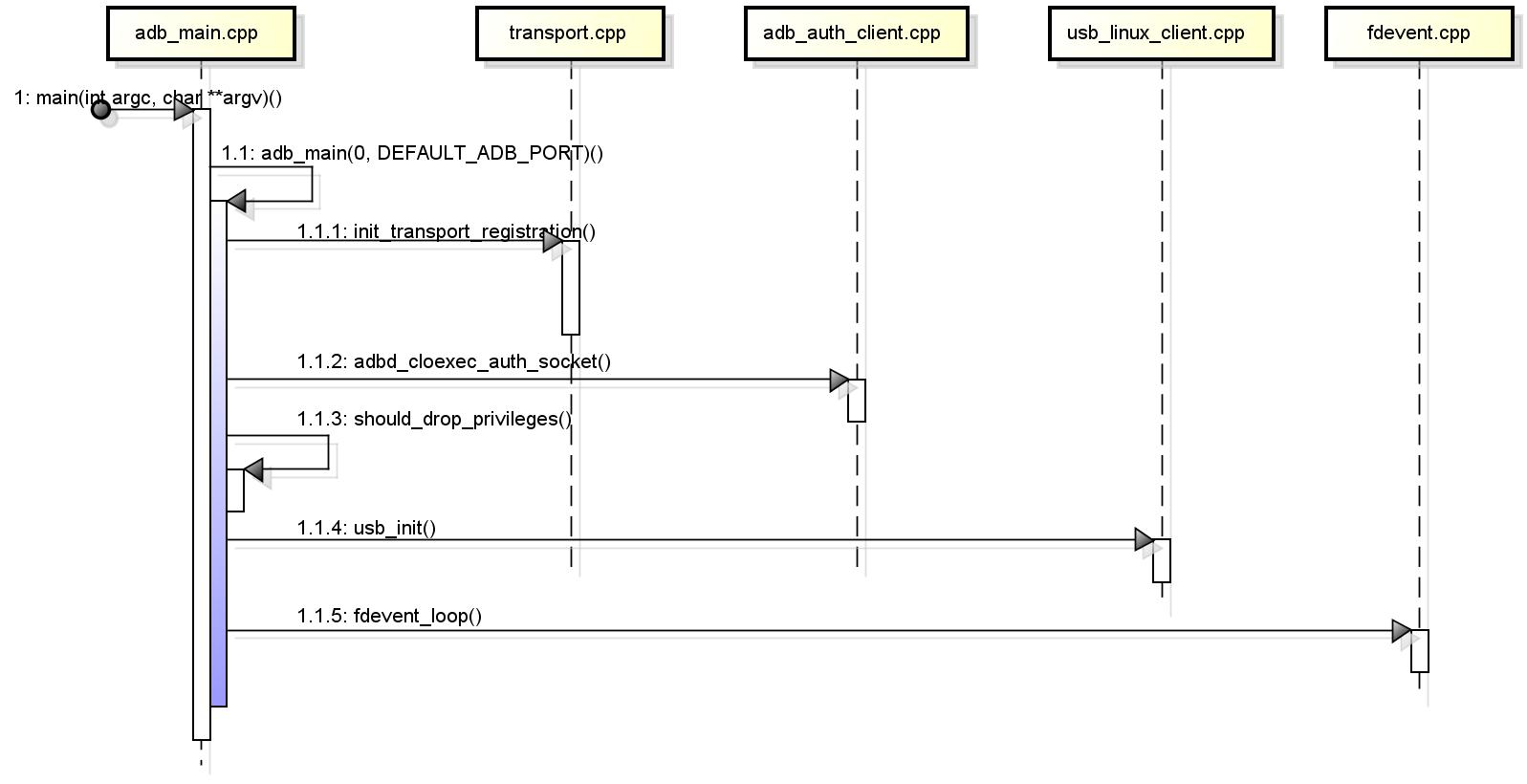
The description is as follows:
- DEFAULT_ADB_PORT is the port number of adb} server. It is defined as follows. The general value is 5037. Sometimes the ADB on the PC cannot be used, which may be because the port has been occupied by mobile assistants such as Tencent.
- 1.1.1-init_ transport_ The analysis of registration() is as follows:
Therefore, we need to analyze transport next_ registration_ Recv will receive data, i.e. transport_ registration_ When will send send data.
- 1.1.2-adbd_cloexec_auth_socket() is analyzed as follows:
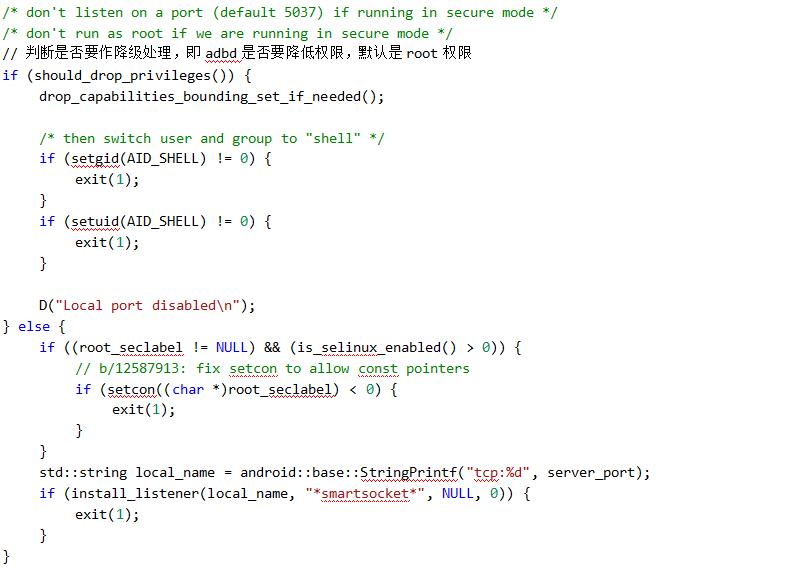
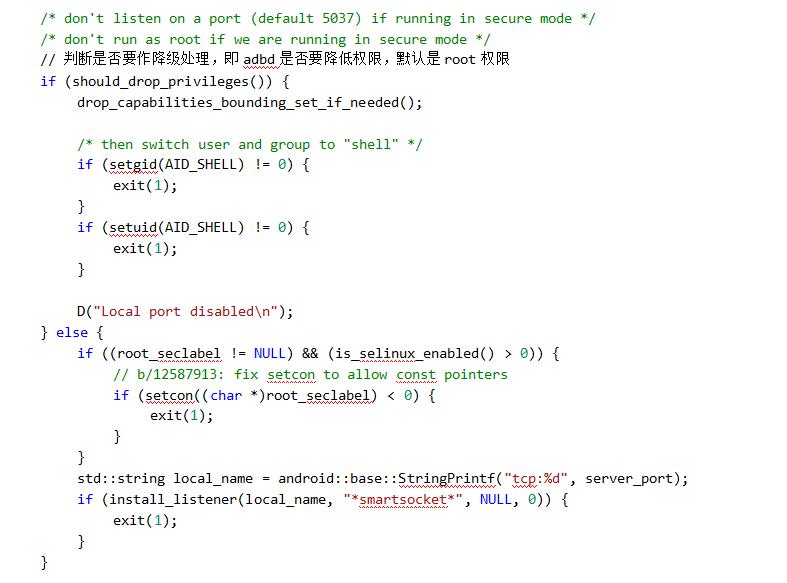
- 1.1.3-should_drop_privileges() is analyzed as follows:
- 1.1.4-usb_init() analysis is as follows:
- Transport will then be called_ registration_ func(int _fd, unsigned ev, void *data)
The follow-up process is as follows:
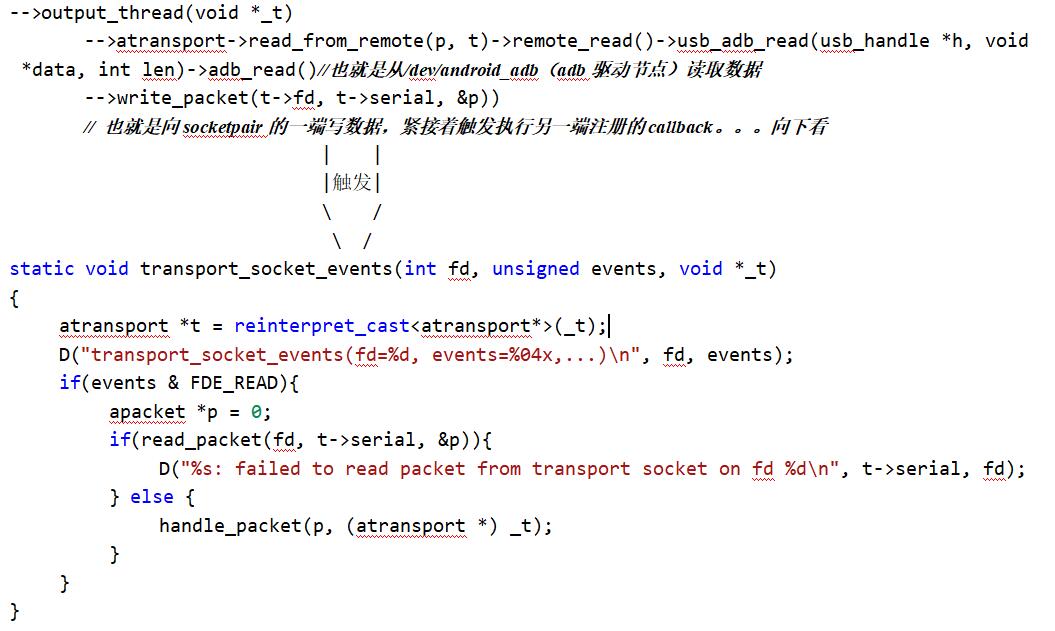
So far, the main initialization process of adbd has been analyzed. The key is to initialize the adb driver node and then create the output_thread constantly reads the changes of node content
2. adb} shell process analysis
According to Section 3.1, output_thread reads the data from the adb driver node and calls write_. Packet (T - > FD, T - > serial, & P)) triggers the call to transport_ socket_ The events () function performs data processing.

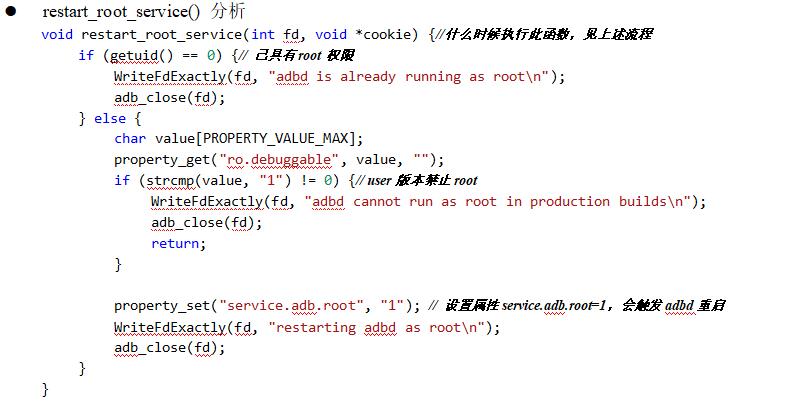
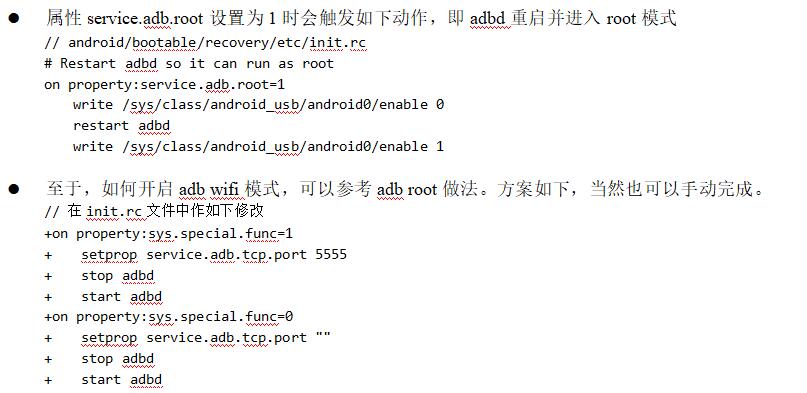
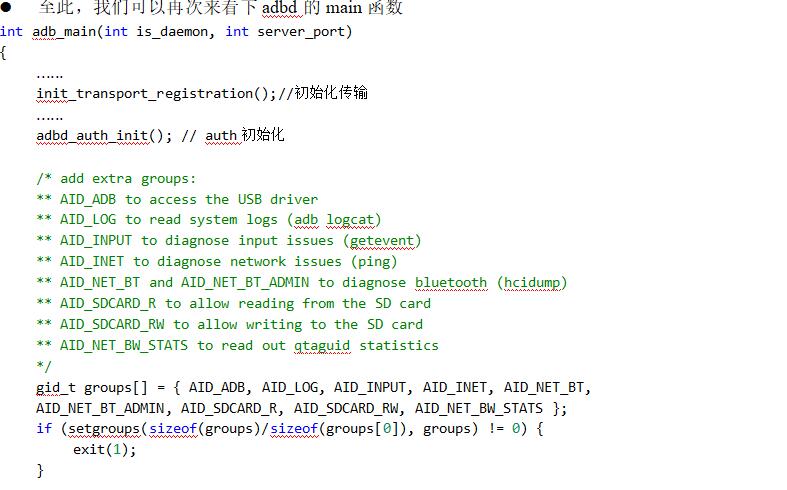
3. adb# root process analysis

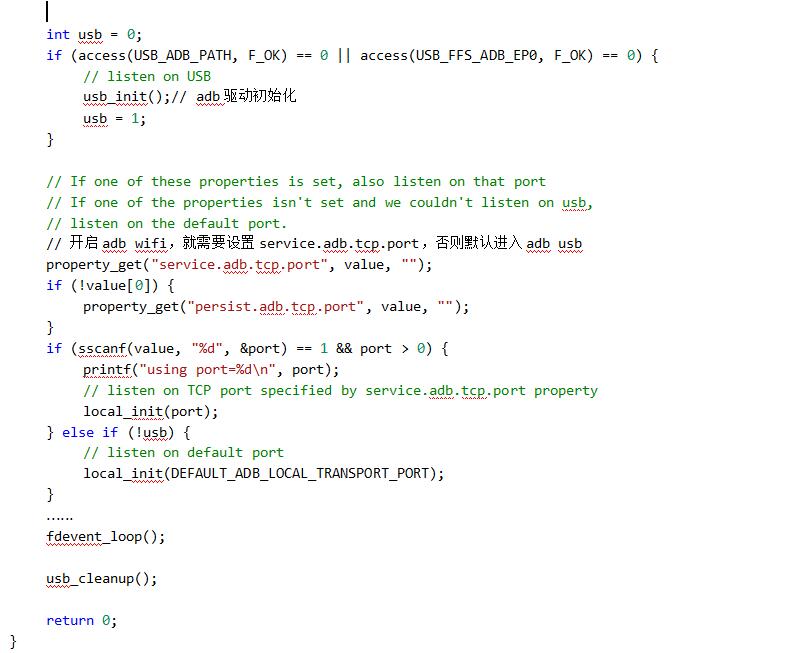
4, adb common commands
The general format of adb command is: adb [- e | - d | - s < device serial number >] < subcommand >
- adb} version to view the adb version
- ADB # tcpip # 5555, set the attribute ersist adb. tcp. Port = 5555, restart adbd and enter ADB # wifi mode.
- adb devices to get the device list and device status
- adb # get state: get the status of the device. The status of the device includes # 3 # minutes, device, offline and unknown
- adb kill-server , adb start-server
- adb # logcat, print the system log of # Android #
- adb bugreport
- adb install
Install the application, overwrite the installation is to use -r option
- adb uninstall
- adb # pull to copy the files or folders on the # Android # device to the local
- adb # push, push local files to # Android # devices
- adb , root, adb , remount, obtain , root , permission and mount the system file system in the read-write state
- adb # reboot, restart # Android # device
- adb # reboot # loader, restart the device and enter # fastboot # mode, the same as the # adb # reboot bootloader # command
- adb # reboot # recovery, restart the device and enter # recovery # mode
- adb connect <device-ip-address>/adb disconnect <device-ip-address>
The above commands are built-in commands of the adb program and have nothing to do with Android. The commands of the Android system are implemented in system/bin (pm, am, screenrecord, getprop, input, ime, wm, settings, monkey, dumpsys, logcat, log, uiautomator, etc.). In addition, it is the command that comes with linux. Check it yourself.
Postscript: due to the actual development needs of adb, I studied the adb source code. The above is a summary. In the spirit of open source, we will make progress together!
Reference article:
https://blog.csdn.net/wlwl0071986/article/details/50935496