The code was written in the last class. Unfortunately, we found that it crash ed when we clicked, because CHANGE_COMPONENT_ENABLED_STATE permission requires system permission
2021-12-17 23:09:15.078 4198-4198/com.android.things.privateapplication1 E/AndroidRuntime: FATAL EXCEPTION: main
Process: com.android.things.privateapplication1, PID: 4198
java.lang.SecurityException: Attempt to change component state; pid=4198, uid=10064, component=com.panzq.applicationb/com.panzq.applicationb.TcpMainActivity
at android.os.Parcel.readException(Parcel.java:2004)
at android.os.Parcel.readException(Parcel.java:1950)
at android.content.pm.IPackageManager$Stub$Proxy.setComponentEnabledSetting(IPackageManager.java:4732)
at android.app.ApplicationPackageManager.setComponentEnabledSetting(ApplicationPackageManager.java:2276)
at com.android.things.privateapplication1.MainActivity$1.onClick(MainActivity.java:51)
at android.view.View.performClick(View.java:6294)
at android.view.View$PerformClick.run(View.java:24770)
at android.os.Handler.handleCallback(Handler.java:790)
at android.os.Handler.dispatchMessage(Handler.java:99)
at android.os.Looper.loop(Looper.java:164)
at android.app.ActivityThread.main(ActivityThread.java:6494)
at java.lang.reflect.Method.invoke(Native Method)
at com.android.internal.os.RuntimeInit$MethodAndArgsCaller.run(RuntimeInit.java:438)
at com.android.internal.os.ZygoteInit.main(ZygoteInit.java:807)
How to give?
1. Find out what degree of protection this authority itself is
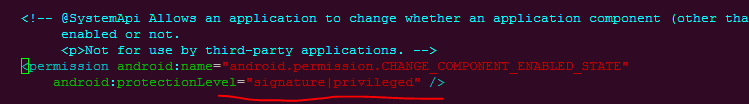
It can be seen that it is platform signature or privileged app level protection, that is, as long as you are platform signature and priv app
2. Grant permissions
Here, we have learned in the previous course that when the prefabricated system apk is used, the signature can be specified. Here, we only need to set it as platform signature
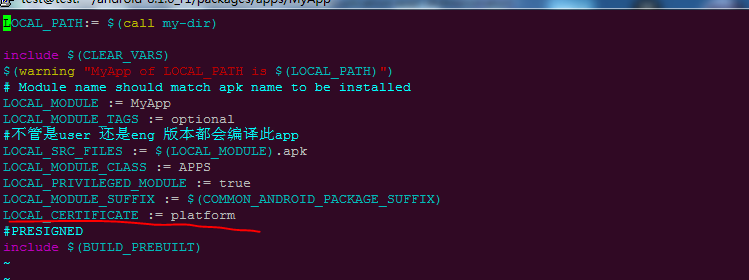
In this way, you can satisfy that the signature belongs to the platform level, and you can obtain permissions
3. Another scheme is priv app permission level
Priv app here refers to the prefabrication to the system / priv app directory. Originally, we are system/app, so how to prefabricate to system / priv app here is actually very simple. Just add a sentence in mk
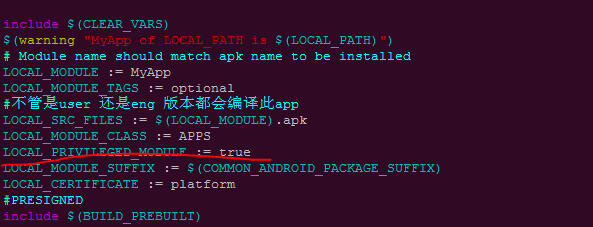
Add:
LOCAL_PRIVILEGED_MODULE := true
This sentence is OK, but please note that it's not over here. We also need to put the corresponding permissions into the white list. The specific operations are as follows:
1 stay frameworks/base/data/etc Medium privapp-permissions-platform.xml Let's make our permission statement. Here we can refer to how other applications are declared:
<privapp-permissions package="com.android.things.privateapplication1">
<permission name="android.permission.CHANGE_COMPONENT_ENABLED_STATE"/>
</privapp-permissions>
That's it. The two permission granting methods have been put into practice. If you need to learn more framework and videos, you can pay attention to it at station b: Qianli horse learning framework. You'd better join the 422901085 group to find Qianli horse for discounts and Q & A
Course Q & A and new course information: QQ communication group: 422901085 for course discussion, plus QQ to enjoy preferential treatment
Video link of FrameWork introductory course: https://edu.csdn.net/course/detail/30298
Video link of FrameWork practical lesson 1: https://edu.csdn.net/course/detail/30275
FrameWork cross process communication video link: https://edu.csdn.net/course/detail/35911
Special blog series:
Android 8.1 zygote startup process source code
Android Framework combat video – the fork process of Zygote
Android Framework combat Video - SystemServer launch
Android Framework combat video – SystemServer launches FallbackHome
Android Framework combat video – FallbackHome process startup and Activity startup
Android Framework combat video – FallbackHome ends launch Launcher
Android Framework combat Video - BootAnimation startup source code analysis (Android 8.1)