base64 (base password)
Learn about base64 first:
The result of base64 encoding is a string, in which the characters can include A-Z, A-Z, 0-9, +, \ a total of 64 characters. If these characters appear, consider base64.
Generally, if there is = (filling character) after it, it can be determined as base64!
Y3liZXJwZWFjZXtXZWxjb21lX3RvX25ld19Xb3JsZCF9
This string of characters includes A-Z, A-Z and 0-9: very similar. Solve it online.
According to the title name, we can decrypt online base64 directly.
Online tools: http://ctf.ssleye.com/
Share a great tool:
CaptfEncoder is a cross platform network security tool suite, which supports Windows, Linux and MacOS platforms. CaptfEncoder provides network security related coding conversion, classical cryptography, cryptography, special coding and other tools, and aggregates various online tools.
Baidu network disk!
Link: https://pan.baidu.com/s/1Ap27KnDCGBlrHegytQZiGA
Extraction code: mxnb
Flag: cyberpeace{Welcome_to_new_World!}
caesar code
Learn about caesar first:
Caesar's password belongs to substitution password. It converts each character in plaintext into n characters in order. We call it Caesar's password. Advantages: the simplest encryption scheme is realized and easy to understand. Disadvantages: for friends with a little basic knowledge of cryptography, the security intensity is almost zero.
Ciphertext of this topic:
oknqdbqmoq{kag_tmhq_xqmdzqp_omqemd_qzodkbfuaz}
Obviously, we can get flag{XXXX} as long as we move each letter to a certain number of digits!
Of course, look directly at the title and get twice the result with half the effort‘
Let's just solve the online tool or the tool I share.
However, you also need to enter a key key (0-25), which is also called displacement.
Just try one by one. From 0 - try to 25. Of course, you can also list them all directly with tools
But it's manual.
By the way, share a python script
#coding:utf-8
#caesar code
import string
s = 'Enter the ciphertext here'
def decrypt(strs):
for i in range(26):
dec_str = ''
for j in strs:
if j in string.ascii_letters:
if j.isupper():
dec_str = dec_str + chr( (ord(j)-ord('A')-i) %26 + ord('A'))
if j.islower():
dec_str = dec_str + chr( (ord(j)-ord('a')-i) %26 + ord('a'))
else:
dec_str += j
print(str(i) + ':' + dec_str + '\n')
if __name__ == '__main__':
decrypt(s)
However, it is best to decrypt online and test key0-25.
Flag: cyberpeace{you_have_learned_caesar_encryption}
morse (morse code)
What is morse? It looks very advanced, but it's just like that, hehe.
Give the password correspondence table directly!
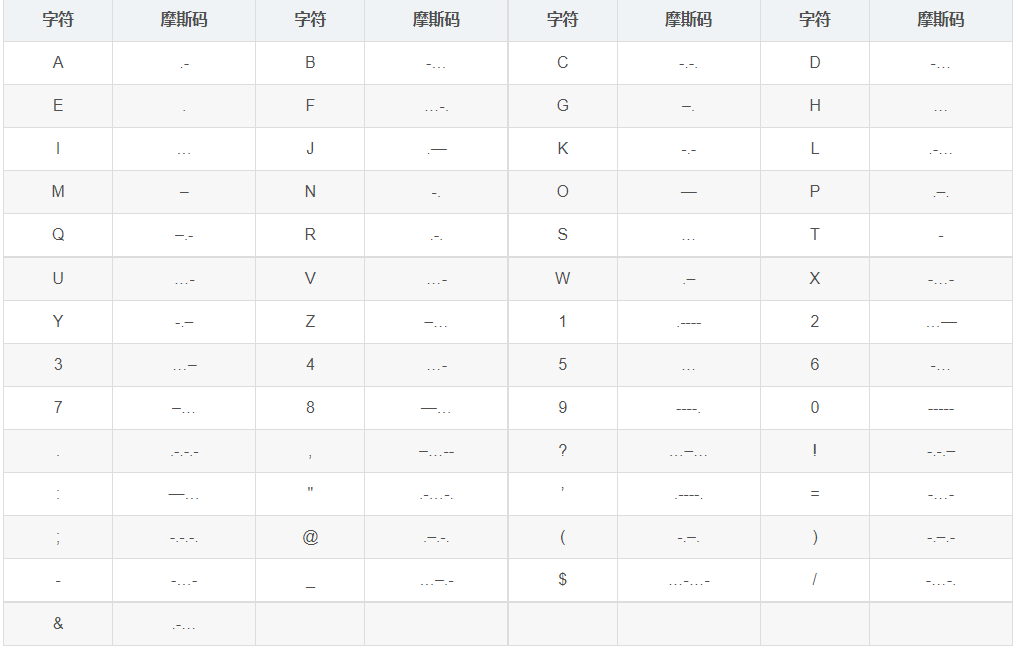
Here you can use "." to replace "0" / "1" / "A" / "B", use "-" to replace "1" / "0" / "B" / "A", and so on
It's all right. Use tools directly. It doesn't matter if it's XX. Replace XX and solve it directly!
(click the three bars in the upper left corner to switch other codes)
Link: https://pan.baidu.com/s/1Ap27KnDCGBlrHegytQZiGA
Extraction code: mxnb
This question wp:
11 111 010 000 0 1010 111 100 0 00 000 000 111 00 10 1 0 010 0 000 1 00 10 110
Morse code use- To express different meanings, only 0 and 1 are used here, so 01 should be used instead of. -. So it's represented by 1 It's still represented by 0 And? Just give it a try
First, convert to the standard moss password format, that is, '1' to '-' and '0' to '.'
Morse decoding:
morsecodeissointeresting
Tip: the flag format is cyberpeace {xxxxxxxxx}, all in lowercase
Construct the flag according to the prompt
Flag: cyberpeace{morsecodeissointeresting}
It can be converted manually, but it takes a little time.
Convert with python script
key = '11 111 010 000 0 1010 111 100 0 00 000 000 111 00 10 1 0 010 0 000 1 00 10 110' result = '' for i in key: if i == '1': result += '-' elif i == '0': result += '.' else: result += ' ' print(result.lower())
Flag: cyberpeace{morsecodeissointeresting}
Idempotent encryption (cloud shadow password)
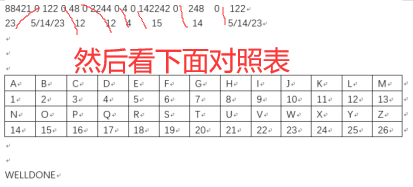
Title: 8842101220480224404014224202480122
It's over. What's this???
Baidu idempotent encryption
It's called cloud shadow password
 Tip: flag is cyberpeace {the eight capital letters you solved}
Tip: flag is cyberpeace {the eight capital letters you solved}
Because the prompt is eight capital letters and seven zeros are found, we can guess that it is divided into eight paragraphs
Manual decryption:
python script:
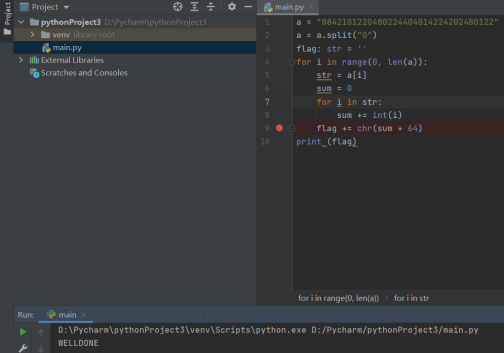
a = "8842101220480224404014224202480122"
a = a.split("0")
flag: str = ''
for i in range(0, len(a)):
str = a[i]
sum = 0
for i in str:
sum += int(i)
flag += chr(sum + 64)
print (flag)
Or:
a=["88421","0122","048","02244","04","0142242","0248","0122"]
flag=""
for j in range(0,len(a)):
str = a[j]
list=[]
sum=0
for i in str:
list.append(i)
length = len(list)
for i in range(0,length):
sum+=int(list[i])
flag+=chr(64+sum)
print (flag)
Flag: cyberpeace{WELLDONE}
Not just Morse (MOSS code + bacon code)
Title:
–/.-/-.–/...–.-/-..././...–.-/.../.-/...-/./...–.-/.-/-./—/-/..././.-./...–.-/-..././-.-./—/-..././.../.../.../.../.-/.-/.-/.-/.-/-.../.-/.-/-.../-.../-.../.-/.-/-.../-.../.-/.-/.-/.-/.-/.-/.-/.-/-.../.-/.-/-.../.-/-.../.-/.-/.-/.-/.-/.-/.-/-.../-.../.-/-.../.-/.-/.-/-.../-.../.-/.-/.-/-.../-.../.-/.-/-.../.-/.-/.-/.-/-.../.-/-.../.-/.-/-.../.-/.-/.-/-.../-.../.-/-.../.-/.-/.-/-.../.-/.-/.-/-.../.-/.-/-.../.-/-.../-.../.-/.-/-.../-.../-.../.-/-.../.-/.-/.-/-.../.-/-.../.-/-.../-.../.-/.-/.-/-.../-.../.-/-.../.-/.-/.-/-.../.-/.-/-.../.-/.-/-.../.-/.-/.-/.-/-.../-.../.-/-.../-.../.-/.-/-.../-.../.-/.-/-.../.-/.-/-.../.-/.-/.-/-.../.-/.-/-.../.-/.-/-.../.-/.-/-.../.-/-.../.-/.-/-.../-.../.-/-.../.-/.-/.-/.-/-.../-.../.-/-.../.-/.-/-.../-.../.-
Obviously moss password, decrypt it!
Give me another online website:
http://www.zhongguosou.com/zonghe/moErSiCodeConverter.aspx
This site supports single slashes and spaces for Morse code separation
But the tools are also OK. It's convenient
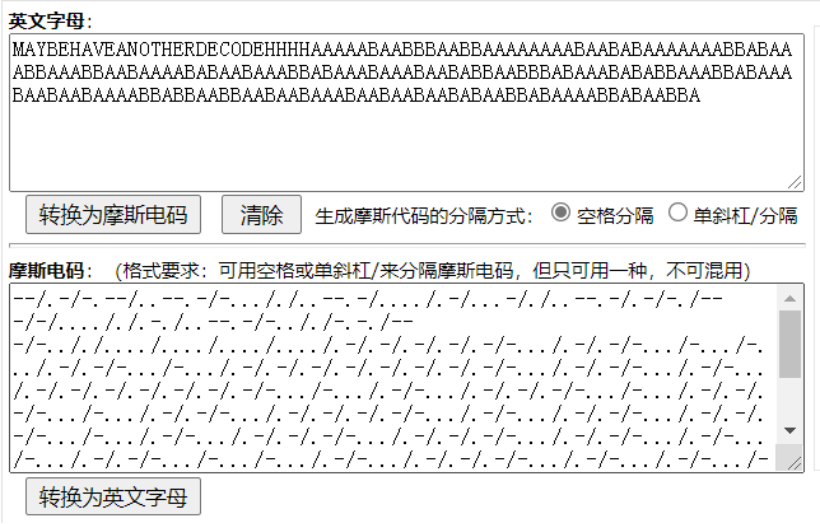 MAYBEHAVEANOTHERDECODEHHHHAAAAABAABBBAABBAAAAAAAABAABABAAAAAAABBABAAABBAAABBAABAAAABABAABAAABBABAAABAAABAABABBAABBBABAAABABABBAAABBABAAABAABAABAAAABBABBAABBAABAABAAABAABAABAABABAABBABAAAABBABAABBA
MAYBEHAVEANOTHERDECODEHHHHAAAAABAABBBAABBAAAAAAAABAABABAAAAAAABBABAAABBAAABBAABAAAABABAABAAABBABAAABAAABAABABBAABBBABAAABABABBAAABBABAAABAABAABAAAABBABBAABBAABAABAAABAABAABAABABAABBABAAAABBABAABBA
After decryption, there was a lot of cracks.
Look at a wave of tips:
Maybe have another decode... It doesn't mean to change from the beginning, but decrypt the Morse password in another way.
It is characterized by only two characters, which is A typical feature of bacon password. (grab cake, package A, package B)
Know the bacon Code:
Also known as Bacon's cipher, it is a steganography invented by Francis Bacon.
Bacon password is actually a replacement password, which can be encrypted and decrypted according to the one-to-one corresponding conversion of the given table. Its special feature is that it can hide password information through unobtrusive features, such as case, forward and italic, etc. as long as there are two different attributes, the password can be hidden.
Give me a decryption script first:
# coding:utf8
import re
alphabet = ['a','b','c','d','e','f','g','h','i','j','k','l','m','n','o','p','q','r','s','t','u','v','w','x','y','z']
first_cipher = ["aaaaa","aaaab","aaaba","aaabb","aabaa","aabab","aabba","aabbb","abaaa","abaab","ababa","ababb","abbaa","abbab","abbba","abbbb","baaaa","baaab","baaba","baabb","babaa","babab","babba","babbb","bbaaa","bbaab"]
second_cipher = ["aaaaa","aaaab","aaaba","aaabb","aabaa","aabab","aabba","aabbb","abaaa","abaaa","abaab","ababa","ababb","abbaa","abbab","abbba","abbbb","baaaa","baaab","baaba","baabb","baabb","babaa","babab","babba","babbb"]
def encode():
upper_flag = False # Used to determine whether the input is uppercase
string = raw_input("please input string to encode:\n")
if string.isupper():
upper_flag = True
string = string.lower()
e_string1 = ""
e_string2 = ""
for index in string:
for i in range(0,26):
if index == alphabet[i]:
e_string1 += first_cipher[i]
e_string2 += second_cipher[i]
break
if upper_flag:
e_string1 = e_string1.upper()
e_string2 = e_string2.upper()
print "first encode method result is:\n"+e_string1
print "second encode method result is:\n"+e_string2
return
def decode():
upper_flag = False # Used to determine whether the input is uppercase
e_string = raw_input("please input string to decode:\n")
if e_string.isupper():
upper_flag = True
e_string = e_string.lower()
e_array = re.findall(".{5}",e_string)
d_string1 = ""
d_string2 = ""
for index in e_array:
for i in range(0,26):
if index == first_cipher[i]:
d_string1 += alphabet[i]
if index == second_cipher[i]:
d_string2 += alphabet[i]
if upper_flag:
d_string1 = d_string1.upper()
d_string2 = d_string2.upper()
print "first decode method result is:\n"+d_string1
print "second decode method result is:\n"+d_string2
return
if __name__ == '__main__':
print "\t\tcoding by qux"
while True:
print "\t*******Bacon Encode_Decode System*******"
print "input should be only lowercase or uppercase,cipher just include a,b(or A,B)"
print "1.encode\n2.decode\n3.exit"
s_number = raw_input("please input number to choose\n")
if s_number == "1":
encode()
raw_input()
elif s_number == "2":
decode()
raw_input()
elif s_number == "3":
break
else:
continue
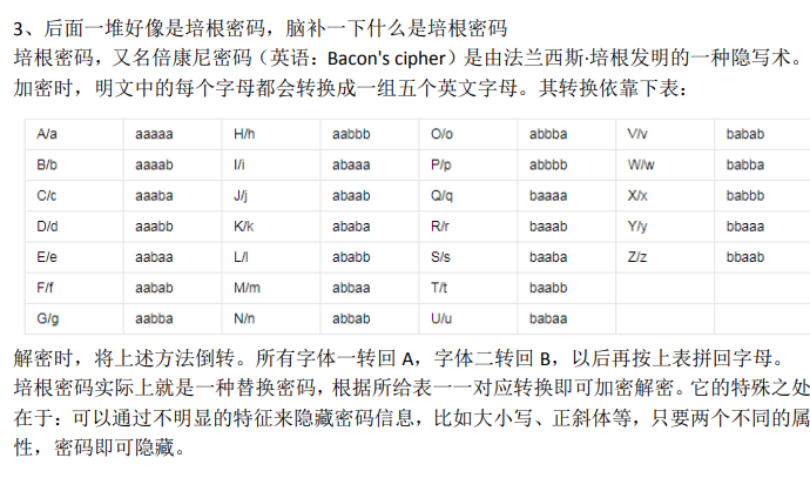
We can see that the password comparison table has only a, b and uppercase
So we delete maybehave an other codehhh
Then the online decryption tool, the tool I shared, captcoder and script can be solved
Keep only A/B and decrypt with Bacon:
attackanddefenceworldisinteresting
Tip: cyberpeace {lowercase answer}
Flag: cyberpeace{attackanddefenceworldisinteresting}
Mixed encoding (Base64 Unicode (HTML) - base64 ascll)
Mixed password???
It's all right, just set the doll!!!
Title:
JiM3NjsmIzEyMjsmIzY5OyYjMTIwOyYjNzk7JiM4MzsmIzU2OyYjMTIwOyYjNzc7JiM2ODsmIzY5OyYjMTE4OyYjNzc7JiM4NDsmIzY1OyYjNTI7JiM3NjsmIzEyMjsmIzEwNzsmIzUzOyYjNzY7JiMxMjI7JiM2OTsmIzEyMDsmIzc3OyYjODM7JiM1NjsmIzEyMDsmIzc3OyYjNjg7JiMxMDc7JiMxMTg7JiM3NzsmIzg0OyYjNjU7JiMxMjA7JiM3NjsmIzEyMjsmIzY5OyYjMTIwOyYjNzg7JiMxMDU7JiM1NjsmIzEyMDsmIzc3OyYjODQ7JiM2OTsmIzExODsmIzc5OyYjODQ7JiM5OTsmIzExODsmIzc3OyYjODQ7JiM2OTsmIzUwOyYjNzY7JiMxMjI7JiM2OTsmIzEyMDsmIzc4OyYjMTA1OyYjNTY7JiM1MzsmIzc4OyYjMTIxOyYjNTY7JiM1MzsmIzc5OyYjODM7JiM1NjsmIzEyMDsmIzc3OyYjNjg7JiM5OTsmIzExODsmIzc5OyYjODQ7JiM5OTsmIzExODsmIzc3OyYjODQ7JiM2OTsmIzExOTsmIzc2OyYjMTIyOyYjNjk7JiMxMTk7JiM3NzsmIzY3OyYjNTY7JiMxMjA7JiM3NzsmIzY4OyYjNjU7JiMxMTg7JiM3NzsmIzg0OyYjNjU7JiMxMjA7JiM3NjsmIzEyMjsmIzY5OyYjMTE5OyYjNzc7JiMxMDU7JiM1NjsmIzEyMDsmIzc3OyYjNjg7JiM2OTsmIzExODsmIzc3OyYjODQ7JiM2OTsmIzExOTsmIzc2OyYjMTIyOyYjMTA3OyYjNTM7JiM3NjsmIzEyMjsmIzY5OyYjMTE5OyYjNzc7JiM4MzsmIzU2OyYjMTIwOyYjNzc7JiM4NDsmIzEwNzsmIzExODsmIzc3OyYjODQ7JiM2OTsmIzEyMDsmIzc2OyYjMTIyOyYjNjk7JiMxMjA7JiM3ODsmIzY3OyYjNTY7JiMxMjA7JiM3NzsmIzY4OyYjMTAzOyYjMTE4OyYjNzc7JiM4NDsmIzY1OyYjMTE5Ow==
Discovery = =, base64
LzExOS8xMDEvMTA4Lzk5LzExMS8xMDkvMTAxLzExNi8xMTEvOTcvMTE2LzExNi85Ny85OS8xMDcvOTcvMTEwLzEwMC8xMDAvMTAxLzEwMi8xMDEvMTEwLzk5LzEwMS8xMTkvMTExLzExNC8xMDgvMTAw
Solve a lot of things.
Note: the% multiple is URL code ± multiple is xxencoding &#, \ U is Unicode
This question is obviously Unicode
Unicode decoding (HTML decoding):
LzExOS8xMDEvMTA4Lzk5LzExMS8xMDkvMTAxLzExNi8xMTEvOTcvMTE2LzExNi85Ny85OS8xMDcvOTcvMTEwLzEwMC8xMDAvMTAxLzEwMi8xMDEvMTEwLzk5LzEwMS8xMTkvMTExLzExNC8xMDgvMTAw
For a long time, consider Base64 decoding:
/119/101/108/99/111/109/101/116/111/97/116/116/97/99/107/97/110/100/100/101/102/101/110/99/101/119/111/114/108/100
It can be seen that the numbers between / / and / / may correspond to a letter and are decimal numbers
Consider decimal ascll
Online tools:
http://ctf.ssleye.com/jinzhi.html
Or: captcoder
Ascll decoding (decimal to abc)
/w/e/l/c/o/m/e/t/o/a/t/t/a/c/k/a/n/d/d/e/f/e/n/c/e/w/o/r/l/d
be careful!!!!! Sometimes it may not work out. Try other online tools and try more!
cyberpeace {lowercase answer you solved} (to remove /)
Flag: cyberpeace{welcometoattackanddefenceworld}
easy_RSA (RSA algorithm RSA tool solution)
RSA algorithm, very complex!!! I don't understand chicken dishes
This question is very simple
Direct tool: rsatool 2v17
Link: https://pan.baidu.com/s/1idmYZOv6u4JUsM00P4wQfw
Extraction code: mxnb
Tips:
In the primary RSA key pair generation, assume p=473398607161, q=4511491, e=17
Solve d
Use tools directly!
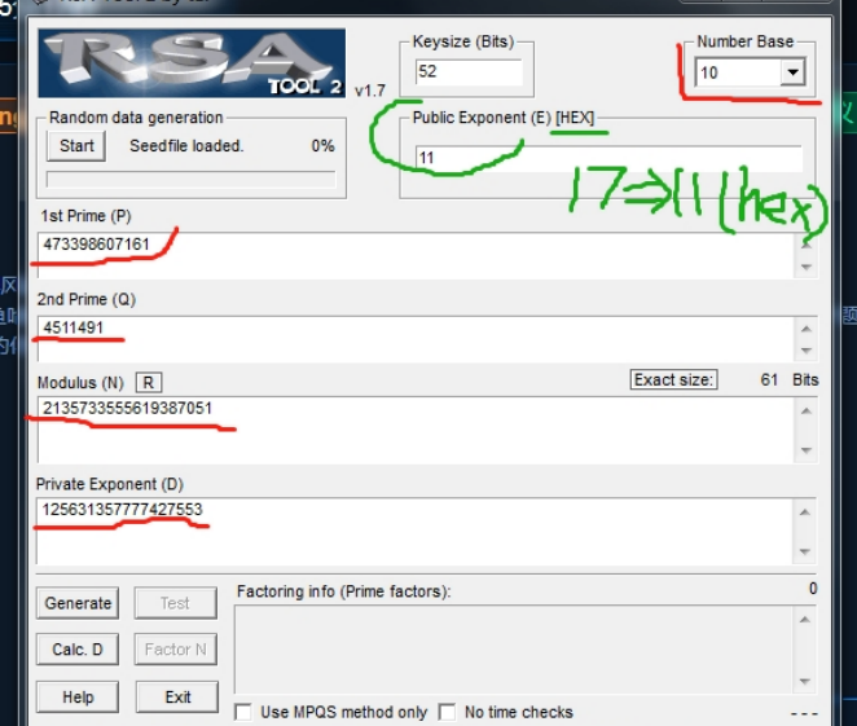
Note that the value of e is represented in hexadecimal, that is, decimal 17, and its corresponding hexadecimal is 11
The data source is Number Base, including P, Q, R and D
E is hexadecimal
Title: p=473398607161, q=4511491, e=17
public exponent(E)[HEX]=11
Enter 1 P=473398607161 2. q=4511491 3. E = 17 = 11 (HEX) hex
Number base to be changed to 10
Then directly Calc.D
The flag format is cyberpeace {the answer you solved in lowercase}
Flag: cyberpeace{125631357777427553}
Easychallenge (pyc decompile decoding)
Objective: to master the method of pyc decompilation and the ability to read python code
This problem is a very simple XOR encryption
Decompiler can use uncompyle6 or decompile pyc online
Online decompilation: https://tool.lu/pyc/
Or install uncompyle6, pip install uncompyle6
Decompile command uncompyle6 XXXXX PyC, get
UC7KOWVXWVNKNIC2XCXKHKK2W5NLBKNOUOSK3LNNVWW3E===
You can also use python scripts:
import base64
def encode1(ans):
s = ''
for i in ans:
x = ord(i) ^ 36
x = x + 25
s += chr(x)
return s
def encode2(ans):
s = ''
for i in ans:
x = ord(i) + 36
x = x ^ 36
s += chr(x)
return s
def encode3(ans):
return base64.b32encode(ans)
flag = ' '
print 'Please Input your flag:'
flag = raw_input()
final = 'UC7KOWVXWVNKNIC2XCXKHKK2W5NLBKNOUOSK3LNNVWW3E==='
if encode3(encode2(encode1(flag))) == final:
print 'correct'
else:
print 'wrong'
Then we decompile the flag by reverse XOR
python script:
import base64 s="UC7KOWVXWVNKNIC2XCXKHKK2W5NLBKNOUOSK3LNNVWW3E===" s=base64.b32decode(s) m = '' for i in s: x = ord(i) ^ 36 x = x - 36 m+= chr(x) h = '' for i in m: x = ord(i) - 25 x = x ^ 36 h+= chr(x) print h
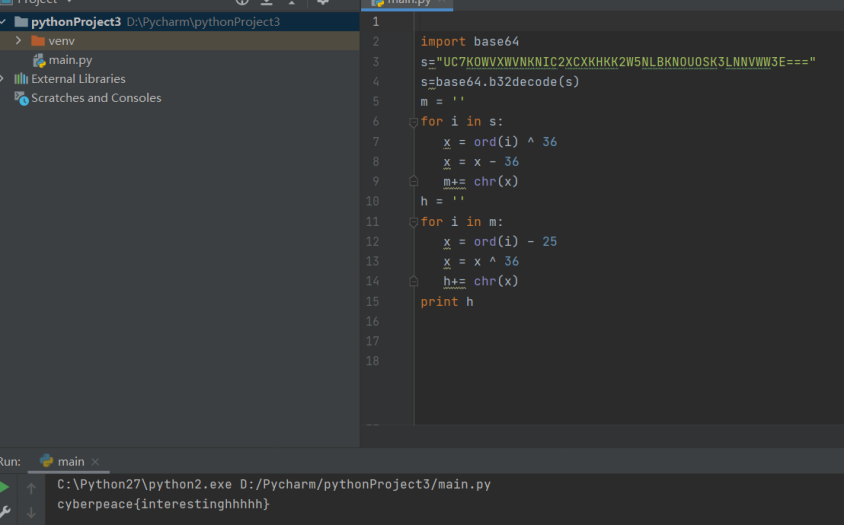
Flag: cyberpeace{interestinghhhhh}
Broadcast
Tip: careless Alice left the plaintext when making the password. Can you find it quickly if you are smart?
Tool: notepad + + (other coding tools can also be used)
Link: https://pan.baidu.com/s/10MKRkPpMPnIXxsywRkHYGw
Extraction code: mxnb
Extract the task directly Py open (notepad + +) to get the flag
Flag: flag{fa0f8335-ae80-448e-a329-6fb69048aae4}
Runner encryption
Tip: Thomas Jefferson. flag is a string in lowercase.
1: < ZWAXJGDLUBVIQHKYPNTCRMOSFE <
2: < KPBELNACZDTRXMJQOYHGVSFUWI <
3: < BDMAIZVRNSJUWFHTEQGYXPLOCK <
4: < RPLNDVHGFCUKTEBSXQYIZMJWAO <
5: < IHFRLABEUOTSGJVDKCPMNZQWXY <
6: < AMKGHIWPNYCJBFZDRUSLOQXVET <
7: < GWTHSPYBXIZULVKMRAFDCEONJQ <
8: < NOZUTWDCVRJLXKISEFAPMYGHBQ <
9: < XPLTDSRFHENYVUBMCQWAOIKZGJ <
10: < UDNAJFBOWTGVRSCZQKELMXYIHP <
11: < MNBVCXZQWERTPOIUYALSKDJFHG <
12: < LVNCMXZPQOWEIURYTASBKJDFHG <
13: < JZQAWSXCDERFVBGTYHNUMKILOP <
The keys are: 2,3,7,5,13,12,9,1,8,10,4,11,6
Ciphertext: NFQKSEVOQOFNP
Working principle of rotating turbine: the rotating wheel cipher machine is composed of multiple rotating wheels, and the rotating speed of each rotating wheel is different. For example, there are three rotating wheels, labeled 1,2,3 respectively. After the No. 1 rotating wheel rotates 26 letters, the No. 2 rotating wheel rotates one letter. When the No. 2 rotating wheel rotates 26 letters, the No. 3 rotating wheel rotates one letter. Therefore, when the wheel cipher machine rotates 26X26X26 times, all wheels return to the initial state, that is, a multi table substitution password with a cycle length of 26X26X26 (17576) of the three wheel ciphers.
(it's so complicated, alas)
Master the code encoding and decoding method of the turbine
See: traditional cryptography (III) - the runner cipher is a multi table replacement cipher. The basic operation is "rotation", and the rest has nothing to do with this problem.
Characteristics of encryption table, key and ciphertext
Each row of the encryption table has 26 different letters. The length of the key, the length of the ciphertext and the number of rows of the table are 13. The letters in the ciphertext have duplicate letters.
Conjecture 1:
It is inferred that the ciphertext is connected by the letters in a column of the encryption table of the rolling machine. However, this is not the case after trying. The difference between the serial number corresponding to the letter in each line and the serial number corresponding to the letter in the next line cannot be deduced according to the key! Adjust adjust!!! Are there other solutions?
Conjecture 2:
Jump out of the previous thinking. The previous thinking point is to try to come up with its encryption scheme in reverse. However, if there are ciphertext and key at the same time, in fact, it is good to know the decryption scheme. Although encryption and decryption are reverse processes, the methods are different. Therefore, we can think and crack in both directions:
According to the characteristics of ciphertext key, guess the encryption method and attack the password.
According to the ciphertext key, speculate the decryption method, and decrypt the ciphertext using the decryption method.
Since conjecture 1 seems to have no way out, next try the corresponding idea of 2. Construct the mapping of decryption and encryption, encryption decryption, ciphertext plaintext, key key; Current plaintext: NFQKSEVOQOFNP current key: 2,3,7,5,13,12,9,1,8,10,4,11,6. Each number of the key corresponds to a row. If the plaintext letter corresponds to a column (such as starting with this letter), a table can be uniquely determined. Then a column of the encryption table should have ciphertext (mapping the original plaintext).

You need to shout fire in the hole when the grenade is thrown closer

Method 2:

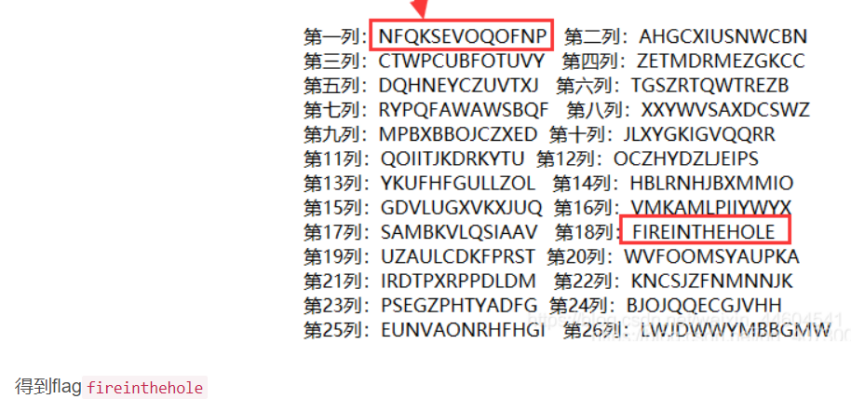
flag: fireinthehole
Normal_RSA
God!!! rsa again??? Or normal!!!
The rsatool 2v17 tool doesn't seem to work
I can't solve it with this. I may be able to solve it, but I'm more delicious!
I use the RSA toll tool on kali
kali didn't bring this tool with him. It's cracked. It's troublesome to install it!
Use the python --version terminal command to check if Python is installed
(usually)
1. Install mpfr
Enter the command first:
wget https://www.mpfr.org/mpfr-current/mpfr-4.1.0.tar.bz2
Then enter the command:
tar -jxvf mpfr-4.1.0.tar.bz2 && cd mpfr-4.1.0
Enter the command again:
./configure
Last input:
sudo make && sudo make install
This is only the first step... Harm
2. Then install mpc
Enter the command first:
wget ftp://ftp.gnu.org/gnu/mpc/mpc-1.2.1.tar.gz
Then enter the command:
tar -zxvf mpc-1.2.1.tar.gz && cd mpc-1.2.1
Enter the command again:
./configure
Last input:
sudo make && sudo make install
3. Install RsaCtfTool
Enter the command first:
git clone https://github.com/Ganapati/RsaCtfTool.git
Then enter the command:
Command update apt get update & & apt get upgrade
Enter the command again:
Install PIP command (pip3 for python3 version) sudo apt get install python3 pip
Last input:
The pip3 -v command checks to see if the installation was successful
4. Configuration library
Enter command:
pip3 install -r requirements.txt
After installation, it can be used
python3 RsaCtfTool.py
You can also use this tool:
https://github.com/3summer/CTF-RSA-tool
Command:
python solve.py --verbose -k examples/jarvis_oj_mediumRSA/pubkey.pem --decrypt examples/jarvis_oj_mediumRSA/flag.enc
Get flag
easy_ecc
ECC algorithm and decoding method
python script:
import collections
import random
EllipticCurve = collections.namedtuple('EllipticCurve', 'name p a b g n h')
curve = EllipticCurve(
'secp256k1',
# Field characteristic.
p=int(input('p=')),
# Curve coefficients.
a=int(input('a=')),
b=int(input('b=')),
# Base point.
g=(int(input('Gx=')),
int(input('Gy='))),
# Subgroup order.
n=int(input('k=')),
# Subgroup cofactor.
h=1,
)
# Modular arithmetic ##########################################################
def inverse_mod(k, p):
"""Returns the inverse of k modulo p.
This function returns the only integer x such that (x * k) % p == 1.
k must be non-zero and p must be a prime.
"""
if k == 0:
raise ZeroDivisionError('division by zero')
if k < 0:
# k ** -1 = p - (-k) ** -1 (mod p)
return p - inverse_mod(-k, p)
# Extended Euclidean algorithm.
s, old_s = 0, 1
t, old_t = 1, 0
r, old_r = p, k
while r != 0:
quotient = old_r // r
old_r, r = r, old_r - quotient * r
old_s, s = s, old_s - quotient * s
old_t, t = t, old_t - quotient * t
gcd, x, y = old_r, old_s, old_t
assert gcd == 1
assert (k * x) % p == 1
return x % p
# Functions that work on curve points #########################################
def is_on_curve(point):
"""Returns True if the given point lies on the elliptic curve."""
if point is None:
# None represents the point at infinity.
return True
x, y = point
return (y * y - x * x * x - curve.a * x - curve.b) % curve.p == 0
def point_neg(point):
"""Returns -point."""
assert is_on_curve(point)
if point is None:
# -0 = 0
return None
x, y = point
result = (x, -y % curve.p)
assert is_on_curve(result)
return result
def point_add(point1, point2):
"""Returns the result of point1 + point2 according to the group law."""
assert is_on_curve(point1)
assert is_on_curve(point2)
if point1 is None:
# 0 + point2 = point2
return point2
if point2 is None:
# point1 + 0 = point1
return point1
x1, y1 = point1
x2, y2 = point2
if x1 == x2 and y1 != y2:
# point1 + (-point1) = 0
return None
if x1 == x2:
# This is the case point1 == point2.
m = (3 * x1 * x1 + curve.a) * inverse_mod(2 * y1, curve.p)
else:
# This is the case point1 != point2.
m = (y1 - y2) * inverse_mod(x1 - x2, curve.p)
x3 = m * m - x1 - x2
y3 = y1 + m * (x3 - x1)
result = (x3 % curve.p,
-y3 % curve.p)
assert is_on_curve(result)
return result
def scalar_mult(k, point):
"""Returns k * point computed using the double and point_add algorithm."""
assert is_on_curve(point)
if k < 0:
# k * point = -k * (-point)
return scalar_mult(-k, point_neg(point))
result = None
addend = point
while k:
if k & 1:
# Add.
result = point_add(result, addend)
# Double.
addend = point_add(addend, addend)
k >>= 1
assert is_on_curve(result)
return result
# Keypair generation and ECDHE ################################################
def make_keypair():
"""Generates a random private-public key pair."""
private_key = curve.n
public_key = scalar_mult(private_key, curve.g)
return private_key, public_key
private_key, public_key = make_keypair()
print("private key:", hex(private_key))
print("public key: (0x{:x}, 0x{:x})".format(*public_key))
The last flag is the sum of the two values of the public key
See for specific principles https://www.jianshu.com/p/e41bc1eb1d81
There is a simpler script:
def power(x, y, mod): r = 1 while( y ): if y & 1: r = (r * x) % mod x = (x * x) % mod y >>= 1 return r Gx = 6478678675 Gy = 5636379357093 a = 16546484 b = 4548674875 p = 15424654874903 k = 546768 x = Gx y = Gy for i in range(k-1): if (x==Gx and y==Gy): inv = power(2*Gy, p-2,p) temp = (3*Gx*Gx+a)*inv%p else: inv = power((x-Gx), p-2,p) temp = (y-Gy)*inv%p #print(temp) xr = (temp*temp-Gx-x)%p yr = (temp*(x-xr)-y)%p #print(i,xr,yr) x = xr y = yr print(x+y)
The flag is: cyberpeace{19477226185390}