Like it and watch it again. Form a habit. Wechat searches "little big white log" to pay attention to the brick mover.
The article synchronizes the official account without any time. There are also a variety of front-line interview questions and my learning series notes.
What is sentinel
- Sentinel is an important component of Spring Cloud Alibaba. It is similar to spring cloud's hystrix. Like the hystrix dashboard console, sentinel dashboard console can provide real-time traffic monitoring, online maintenance of traffic rules and fuse rules. The premise is that the micro service integrates sentinel
- Contrast hystrix
| Sentinel | Hystrix | |
|---|---|---|
| Isolation strategy | Semaphore isolation | Thread pool isolation / semaphore isolation |
| Fuse degradation strategy | Based on response time or failure rate | Thread pool isolation / based on response time or failure ratio |
| Real time index realization | sliding window | Sliding window (based on RxJava) |
| Rule configuration | Support multiple data sources | Support multiple data sources |
| Expansibility | Multiple extension points | Form of plug-in |
| Annotation based support | support | support |
| Current limiting | Based on QPS, current limiting based on call relationship is supported | Limited support |
| Flow shaping | Support slow start and homogenizer mode | I won't support it |
| System load protection | support | I won't support it |
| Console | Out of the box, you can configure rules, view second level monitoring, machine discovery, etc | imperfect |
| Adaptation of common frames | Servlet, Spring Cloud, Dubbo, gRPC, etc | Servlet,Spring Cloud Netflix |
hystrix has officially stopped updating, while sentinel remains open source
Basic concepts
- Resource: resource resources can be code blocks, methods (ordinary methods, interfaces), etc. after defining them as resources, define flow restriction rules, and then use them in combination with sentinel
- Slot: seven kinds of slot are defined in sentinel. Sentinel implements current limiting through the fixed call sequence between slots, because the subsequent slots may depend on the calculation results of the previous slot
- Entry: whether to pass the current limited voucher. sentinel has three forms to define resources
- Call sphu Entry ("resource") to define the resource: if the definition is successful, an entry object will be returned. Otherwise, an exception will be thrown to refuse to execute the flow limiting code. It means that the resource has been defined and other processing codes need to be executed. Entry should be executed at the end whether the resource is successfully defined or not Exit() exits the resource
- Call spho Entry ("resource") to define the resource: returning true indicates that the definition is successful. If the definition of the resource fails, returning false to refuse to execute the current limiting code. Other processing codes need to be executed. Spho should be executed at the end whether the resource is successfully defined or not Exit() exits the resource call
- Define resources by annotation: the above two methods are highly intrusive to the code. You can use @ SentinelResource annotation to act on the method, and configure blockHandler to specify the current limiting processing method
- Node node: DefaultNode = link node, which can count the data of a resource on the calling link; ClusterNode = cluster node, which can count the global data of a resource; StatisticNode = Basic node, and its data structure has a sliding window structure of second / minute level; EntranceNode = entry node, containing some entry data
- Context: context, ThreadLocal transmission, including all information of a link call, such as link node DefaultNode, entry node EntranceNode
Use sentinel: define flow restriction rules and define resources
- Introduce dependency
<dependency>
<groupId>com.alibaba.csp</groupId>
<artifactId>sentinel-core</artifactId>
<version>1.7.1</version>
</dependency>
- Define rules and define resources
Rules are intended to act on resources. First define rules, and then define resources in the form of [SphU.entry()] or [SphO.entry()] or comments:
public class demo {
public static void main(String[] args) {
// Define rules
initFlowRules();
//Use sphu Define resources in the form of entry()
while (true) {
try (Entry entry = SphU.entry("myResource")) {//And the rule in the rule definition Setresource ("myresource") is consistent
// Protected business logic
System.out.println("Business resource access succeeded!");
} catch (BlockException ex) {
// Handling flow controlled logic: current limiting or degradation
System.out.println("Resource access failed!!!");
} finally {
if (entry != null) {
entry.exit();//You must exit the resource call
}
}
}
//Use spho Define resources in the form of entry()
while (true) {
if(SphO.entry("myResource")){//And the rule in the rule definition Setresource ("myresource") is consistent
try{
// Protected business logic
System.out.println("Business resource access succeeded!");
} catch (BlockException ex) {
// Handling flow controlled logic: current limiting or degradation
System.out.println("Resource access failed!!!");
}finally{
SphO.exit();//You must exit the resource call
}
}
}
//The above two methods are highly intrusive to code, and resources can be defined by annotation
while(true){
getUserById("111");
}
}
//Define rules
private static void initFlowRules(){
List<FlowRule> rules = new ArrayList<>();// Storage rule FlowRule
FlowRule rule = new FlowRule();
rule.setResource("myResource"); // Specify which resource the flow restriction rule applies to. The resource name is a string, which can be any meaningful method name / interface name / other string. Here, the resource name is "myResource"
rule.setGrade(RuleConstant.FLOW_GRADE_QPS); // The current limiting type is QPS mode: limit QPS
rule.setCount(10); // QPS shall not exceed 10
rule.setLimitApp("default"); // For the calling source of, default means that the source is not distinguished
rules.add(rule);
FlowRuleManager.loadRules(rules);// Loading rules
}
//Define the "myResource" resource and set the processing method handlerException() when the sentinel flow control rule is violated
@SentinelResource(value="myResource",blockHandler="handlerException")
public User getUserById(String id){
return new User("Database user");
}
//Note: the parameters of this processing method must be consistent with the getUserById parameter () of the method defining resources, and the [BlockException exception] parameter must be added at the same time
public User handlerException(String id,BlockException exception){
return new User("Flow control user");
}
}
Entry entry = null;
try {
entry = SphU.entry("myResource"); //Resources described here
// Protected business logic
...
} catch (BlockException e1) {
// Resource access is blocked, restricted or degraded, and corresponding processing operations are performed
...
} finally {
if (entry != null) {
entry.exit();
}
}
Start sentinel separately
-
Download sentinel-dashboard-1.6.0 Jar package (++ link ++), start: java -jar
-Dserver.port=8888 sentinel-dashboard-1.6.0.jar
-
Visit localhost:8888 and log in to the sentinel dashboard console. The default user name / password is sentinel/sentinel
You can see that the console does not monitor the traffic of any microservices -
Project integration sentinel
- pom.xml import dependency
<dependency> <groupId>org.springframework.cloud</groupId> <artifactId>spring-cloud-starter-alibaba-sentinel</artifactId> </dependency>- Add in the properties file of the project:
spring.clound.sentinel.transport.dashboard=localhost:8888 #Set the address of sentinel console spring.application.name=myapp #Project name
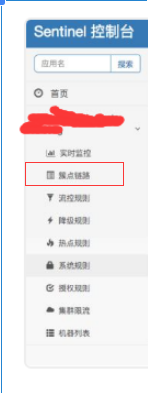
- After the browser accesses the project, return to the sentinel console again to see all the monitoring of the controller interface in the myapp project. You can add flow control rules in the "cluster point link" on the left and set the QPS of each interface (how many accesses are allowed per second)

OK, if there are errors or deficiencies in the article, you are welcome to leave a message.
It's not easy to create. Your "three companies" are the biggest driving force for the creation of the two young people! See you next time!