View ifconfig of docker server
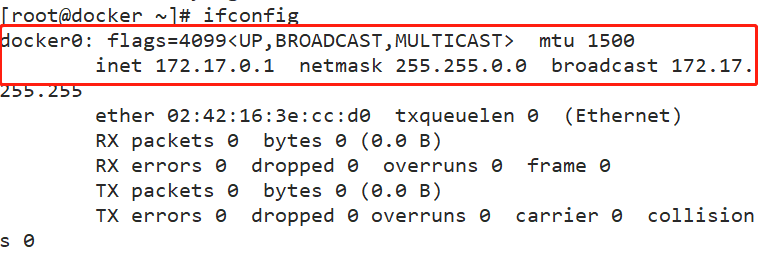
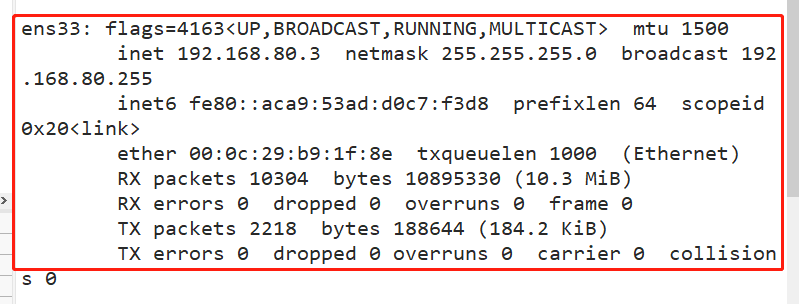
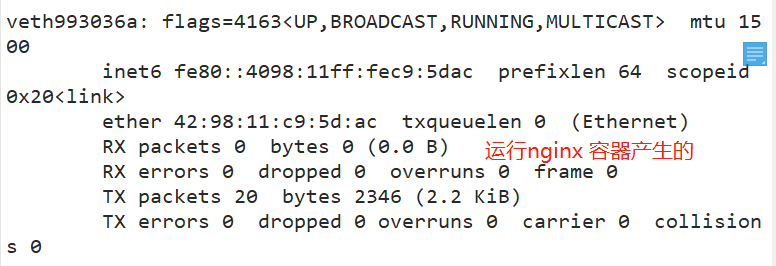
docker network principle
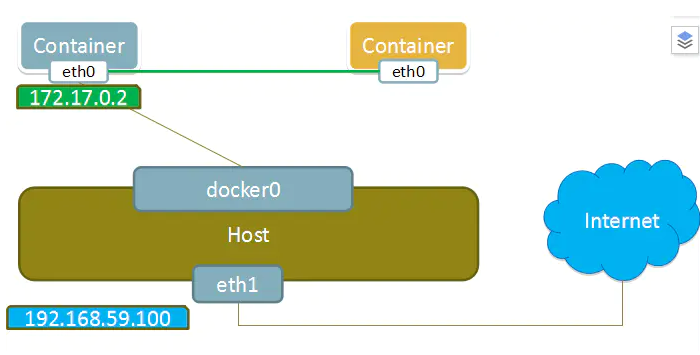
- Docker uses Linux bridging. A docker container bridge (docker0) is virtualized in the host. When docker starts a container, it will assign an IP address to the container according to the network segment of docker bridge, which is called container IP. At the same time, docker bridge is the default gateway of each container. Because the containers in the same host are t connected to the same bridge (the container and container bridge communicate through veth pair), the containers can communicate directly through the container IP of the container.
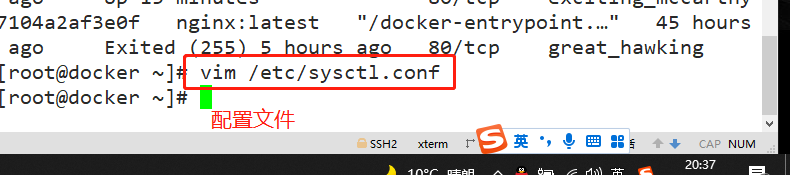
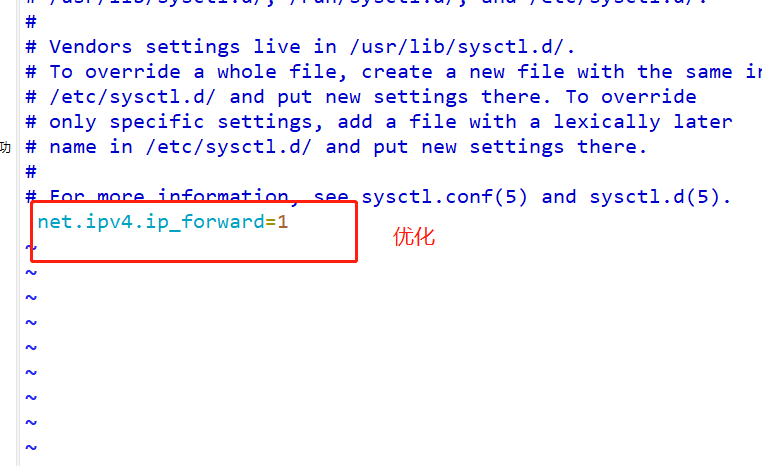
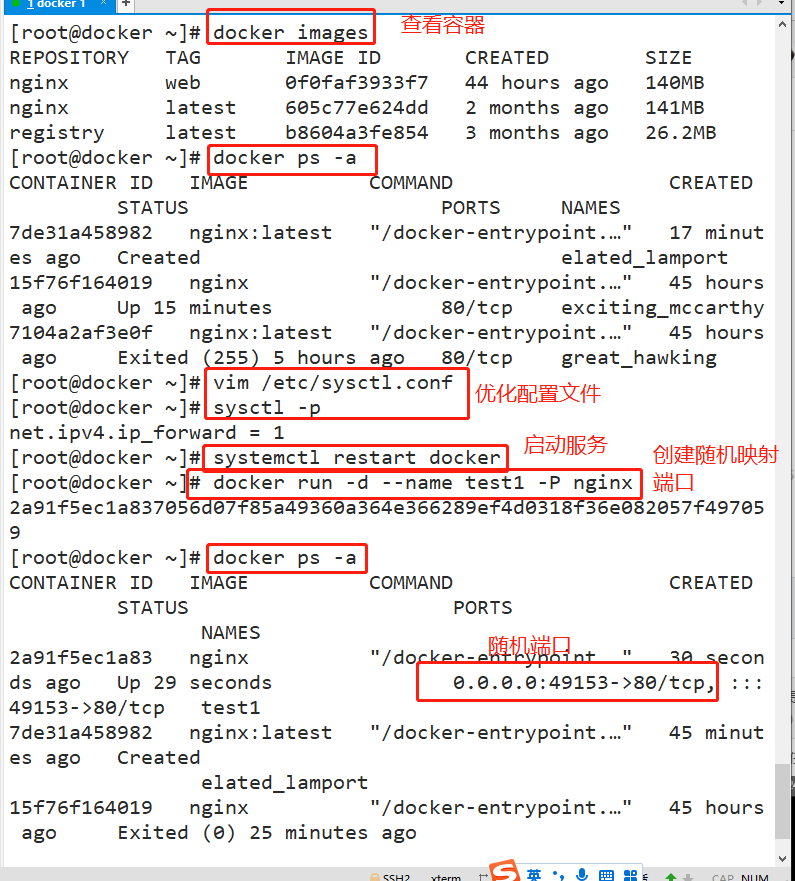
Note: there can be multiple docker bridges - Docker bridge is virtualized by the host computer, not a real network device. The external network cannot be addressed, which also means that the external network cannot access the container directly through container IP. If the container wants external access, it can be accessed by mapping the container port to the host host (port mapping), that is, when docker run creates the container, it can be enabled through the - P (specify exposed port) or - P (randomly assign exposed port) parameter. When accessing the container, it can access the container through [host IP]: [mapping port].
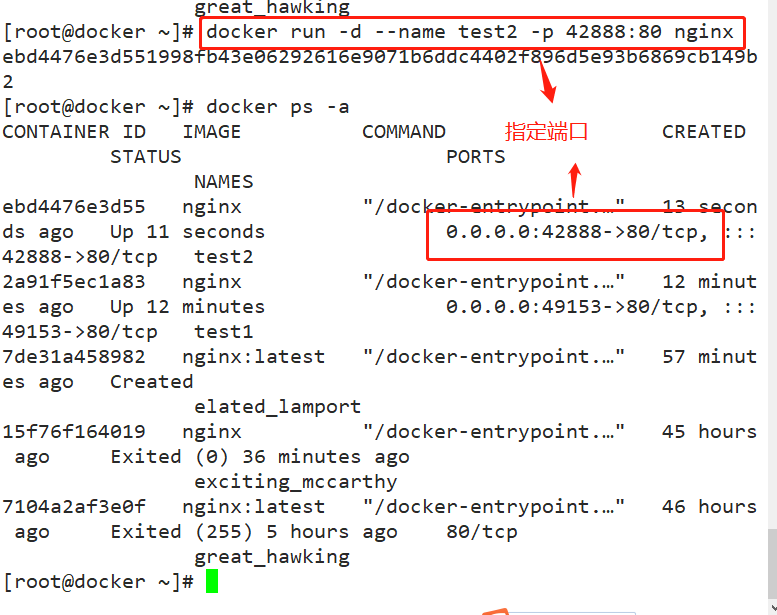
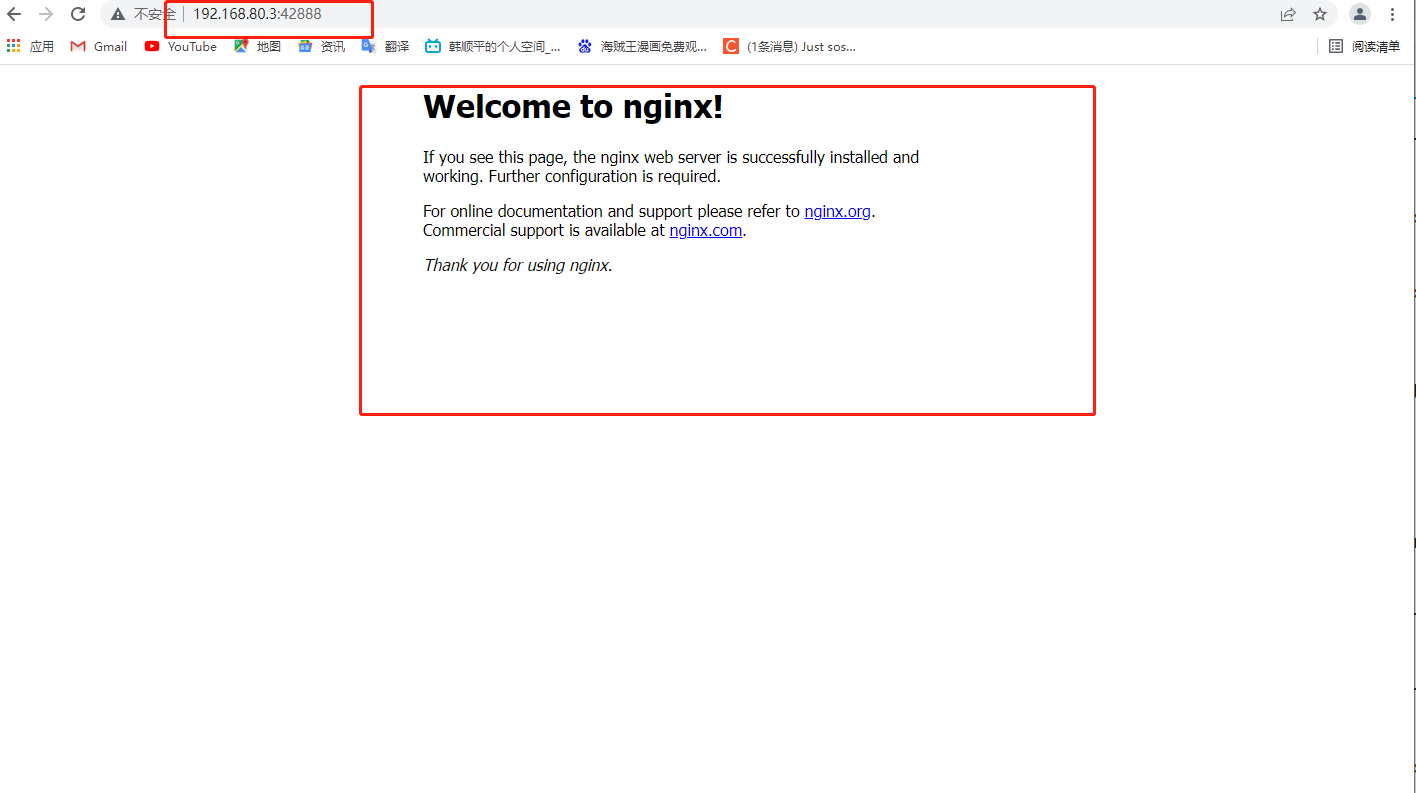
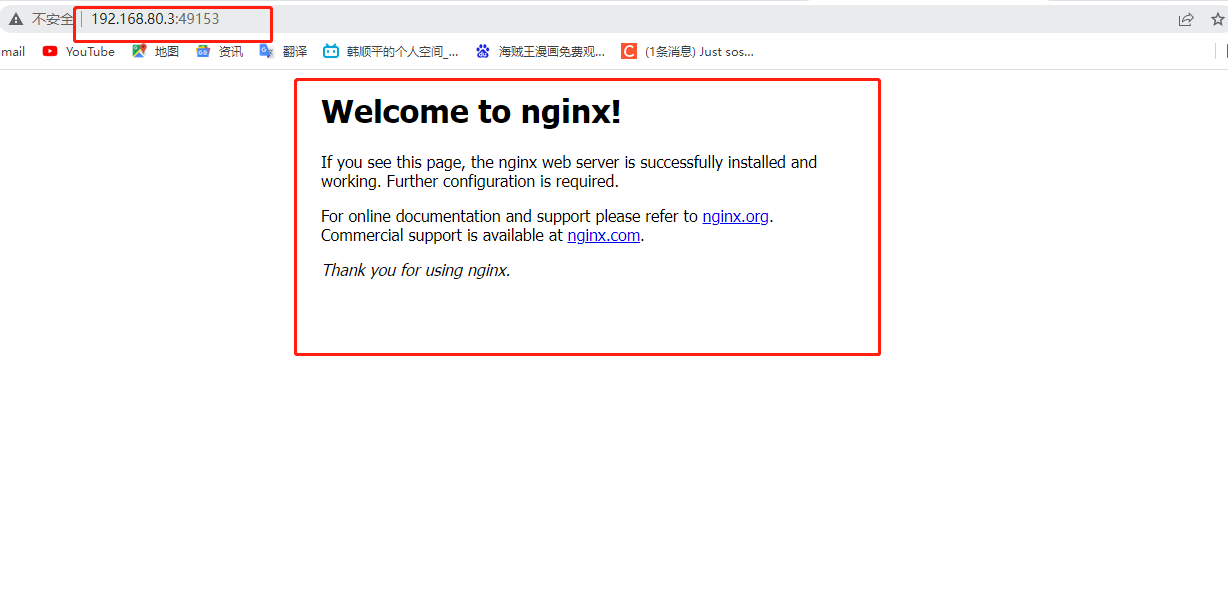
docker rm $(docker ps -a -q) #Batch cleaning containers stopped in the background Format: docker run -d --name test1 -P nginx #-P do not specify, random mapping port (starting from 32768) docker run -d --name test2 -p 43999:80 nginx #-p specifies the mapping port docker ps-a Browser access: http://192.168.80.3:49153 and http://192.168.80.3:43999 #View the output and log information of the container docker logs Container ID/name
2, Four modes of docker network
| Docker network mode | explain |
|---|---|
| host mode | Container and host share Network namespace (- - net=host) |
| container mode | The container shares the Network namespace with another container. pod in kubernetes means that multiple containers share a Network namespace (– net=container:NAME_or_ID) |
| none mode | The container has an independent Network namespace and a closed network environment without any network settings, such as assigning veth pair and bridge connection, configuring IP, etc. (– net=none) |
| bridge mode | (default to this mode) – net=bridge different dockers use different bridges docker run --net=br0 xxxxx... docker run --net=br1 xxxxx |
(1)
- Host: the container will not virtualize its own network card and configure its own IP, but use the IP and port of the host
- The container and the host share the same IP, but the container port cannot be the same
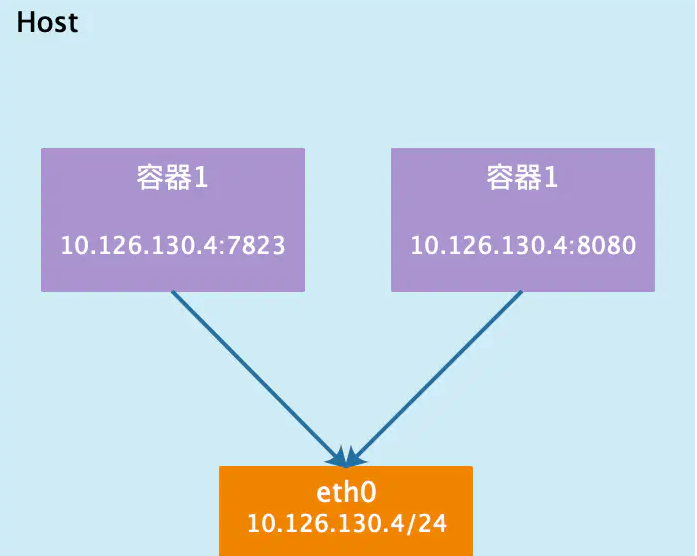
Summary: if the host mode is used when starting the container, the container will not obtain an independent Network Namespace, but share a Network Namespace with the host. The container will not virtualize its own network card and configure its own IP, but use the IP and port of the host. However, other aspects of the container, such as file system, process list, etc., are still isolated from the host.
The container using the host mode can directly use the IP address of the host to communicate with the outside world. The service port inside the container can also use the port of the host without NAT. The biggest advantage of the host is that the network performance is relatively good, but the ports already used on the docker host can no longer be used, and the network isolation is not good.
(2)
container mode
- Container: the created container will not create its own network card and configure its own IP, but share the IP and port range with a specified container
Summary: this mode specifies that the newly created container shares a Network Namespace with an existing container, rather than with the host. The newly created container will not create its own network card and configure its own IP, but share IP and port range with a specified container. Similarly, in addition to the network, the two containers are isolated from each other, such as file system and process list. The processes of the two containers can communicate through the lo network card device.
(3)
none mode
- This mode turns off the network function of the container.
Summary: using the none mode, the Docker container has its own Network Namespace, but it does not carry out any network configuration for the Docker container. In other words, the Docker container has no network card, IP, routing and other information. We need to add network card and configure IP for Docker container.
In this network mode, the container has only lo loopback network and no other network card. The none mode can be specified by – network=none when the container is created. This type of network has no way to network, and the closed network can well ensure the security of the container.
(4)
bridge mode
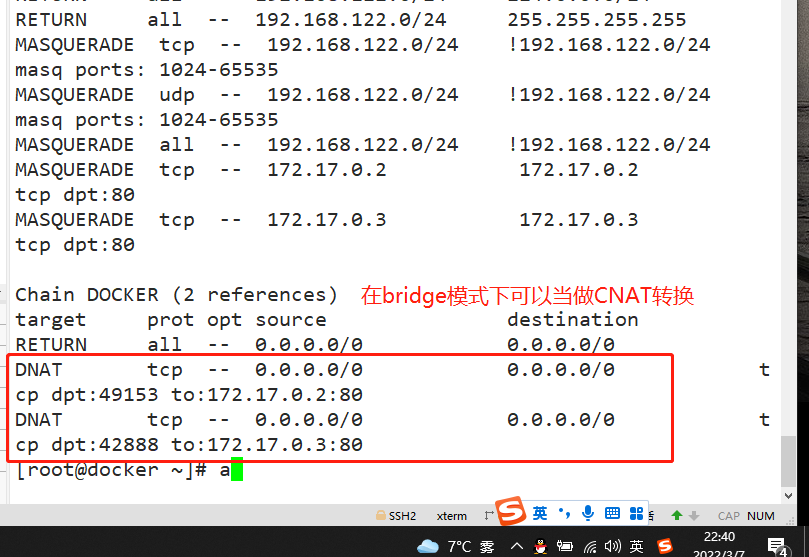
- The default mode is this mode. This mode will assign and set IP for each container, connect the container to a docker0 virtual bridge, and communicate with the host through the docker0 bridge and iptables nat table configuration.
Summary: each container has its own ip address, port range and is not shared
Each container will be connected to the virtual network card on Docker0 bridge
-
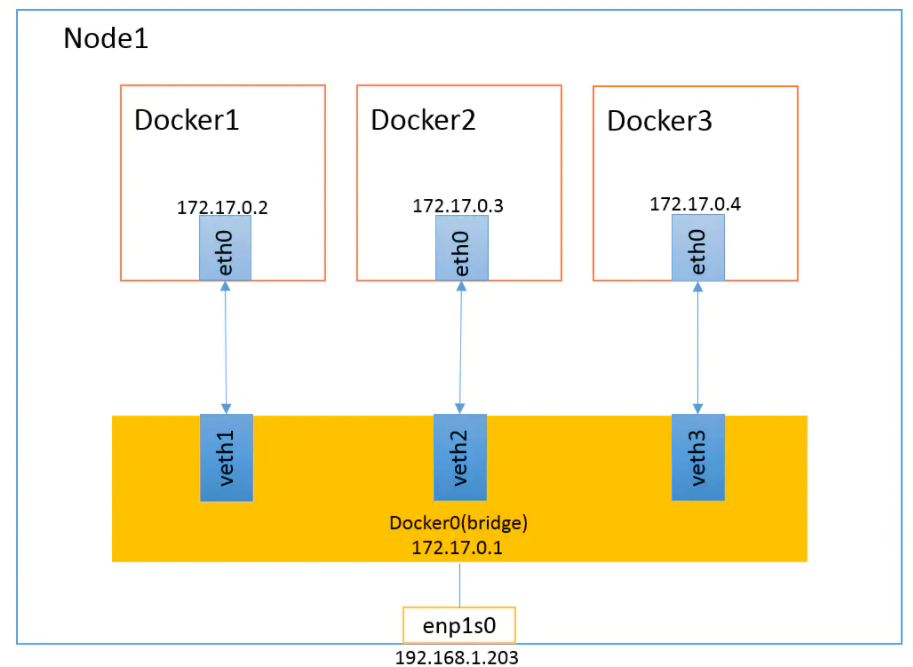
Overview: when the Docker process starts, a virtual bridge named docker0 will be created on the host, and the Docker container started on the host will be connected to this virtual bridge. The working mode of virtual bridge is similar to that of physical switch, so that all containers on the host are connected to a layer-2 network through the switch.
-
Assign an IP to the container from the docker0 subnet, and set the IP address of docker0 as the default gateway of the container. Create a pair of virtual network card veth pair devices on the host. Docker puts one end of the veth pair device in the newly created container and names it eth0 (network card of the container), and the other end in the host with a similar name like vethxxx, and adds this network device to the docker0 bridge. You can view it through the brctl show command.
-
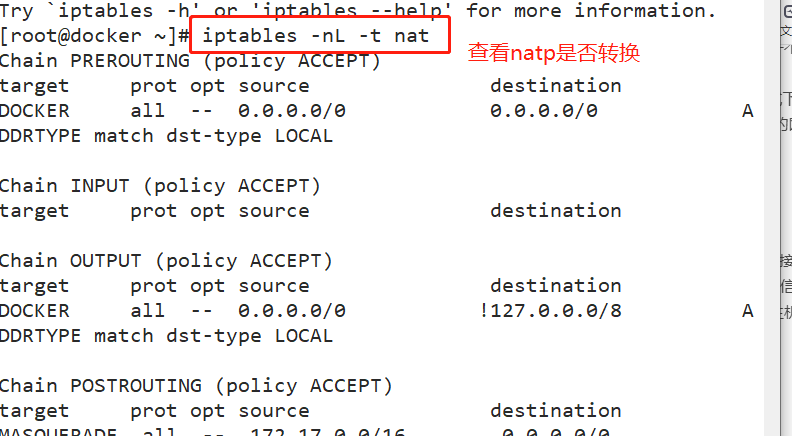
The bridge mode is the default network mode of docker. If the – net parameter is not written, it is the bridge mode. When using docker run -p, docker actually makes DNAT rules in iptables to realize port forwarding function. You can use iptables -t nat -vnL to view.
(5)
Custom network
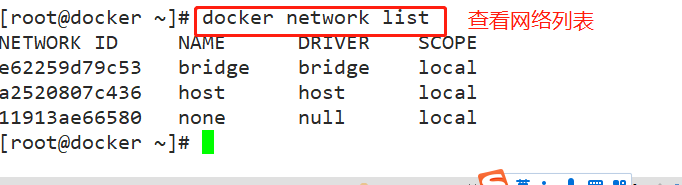
When Docker is installed, it will automatically create three networks: bridge (the container is connected to this network by default), none and host
docker network ls or docker network list #View docker network list
3, Docker specifies the network mode of the container
use docker run establish Docker When using containers, you can use–net or–network Option specifies the network mode of the container
- Host mode: use – net=host to specify
- None mode: use – net=none to specify
- Container mode: use – net=container:NAME_or_ID assignment
- Bridge mode: specified with – net=bridge, default setting, can be omitted
4, Docker network model overview and detailed explanation
(1) host mode
It is equivalent to the bridge mode in Vmware. It is in the same network as the host, but there is no independent IP address.
Docker uses Linux Namespaces technology to isolate resources, such as PID Namespace to isolate processes, Mount Namespace to isolate file systems, and Network Namespace to isolate networks.
A Network Namespace provides an independent network environment, including network card, routing and iptable rules, which are isolated from other network namespaces.
A Docker container is usually assigned an independent Network Namespace.
However, if the host mode is used when starting the container, the container will not get an independent NetworkNamespace, but share a Network Namespace with the host. The container will not virtualize its own network card or configure its own IP, but use the IP and port of the host.
(2) container mode
After understanding the host mode, this mode is easy to understand. This pattern specifies that the newly created container shares a Network Namespace with an existing container, rather than with the host. The newly created container will not create its own network card and configure its own IP, but share IP and port range with a specified container. Similarly, in addition to the network, the two containers are isolated from each other, such as file system and process list. The processes of the two containers can communicate through the lo network card device
#Create a new container
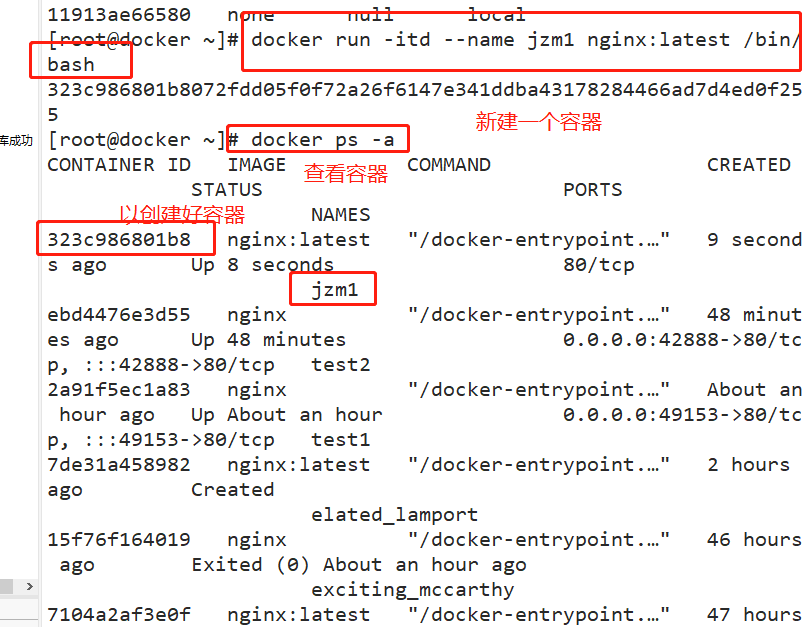
docker run -itd --name jzm1 nginx:latest /bin/bash
docker ps -a
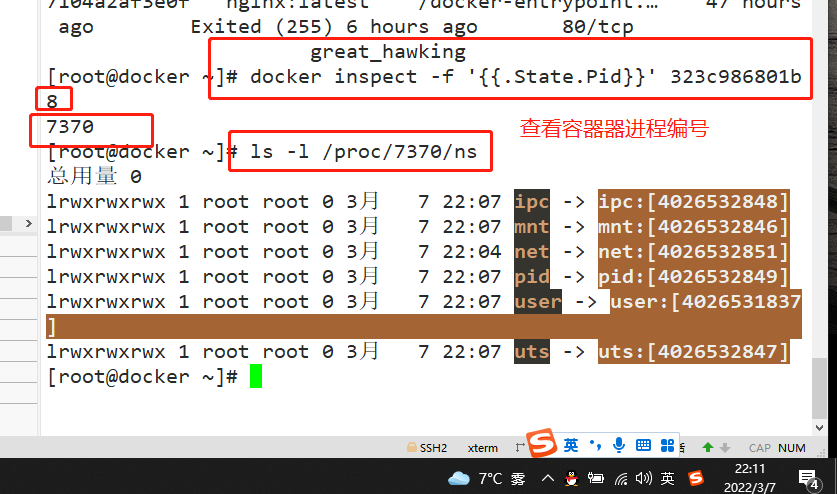
docker inspect -f '{{.State.Pid}}' 323c986801b8 #View container process number
ls -l /proc/7370/ns
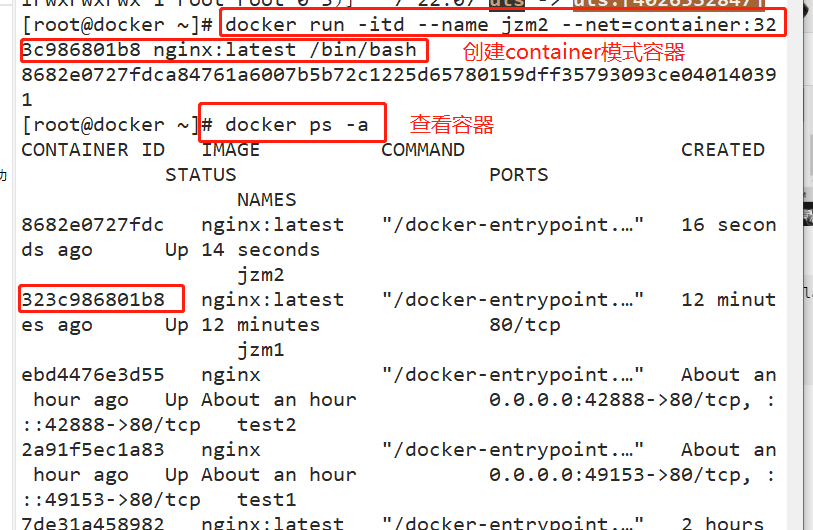
docker run -itd --name jzm2 --net=container:323c986801b8 nginx:latest /bin/bash
docker ps -a
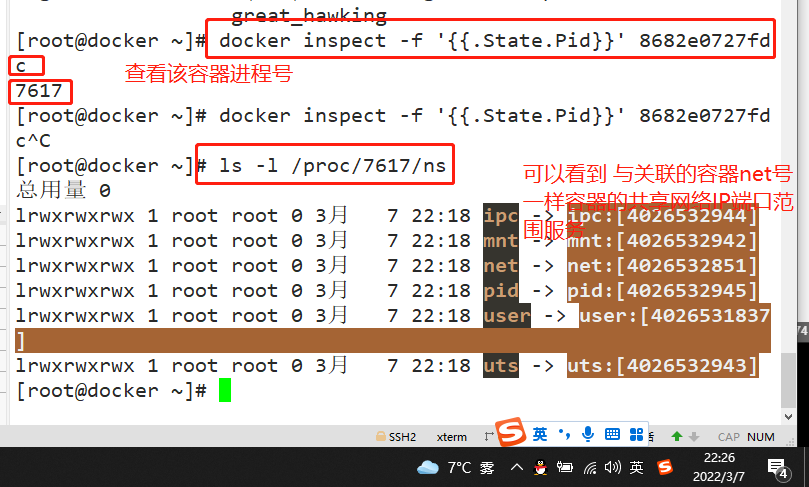
docker inspect -f '{{.State.Pid}}' 8682e0727fdc
ls -l /proc/7617/ns
(3) none mode
Using the none mode, the Docker container has its own Network Namespace, but no network configuration is made for the Docker container.
In other words, the Docker container has no network card, IP, routing and other information. In this network mode, the container has only lo loopback network and no other network card. This type of network has no way to network, and the closed network can well ensure the security of the container.
(4) bridge mode
Bridge mode is the default network mode of docker. Without the – net parameter, it is the bridge mode.
Equivalent to the nat mode in Vmware, the container uses an independent network namespace and is connected to the docker0 virtual network card. Configure communication with the host through docker0 bridge and iptables nat table. This mode will assign network namespace, set IP, etc. to each container, and connect the Docker container on a host to a virtual bridge.
Custom network
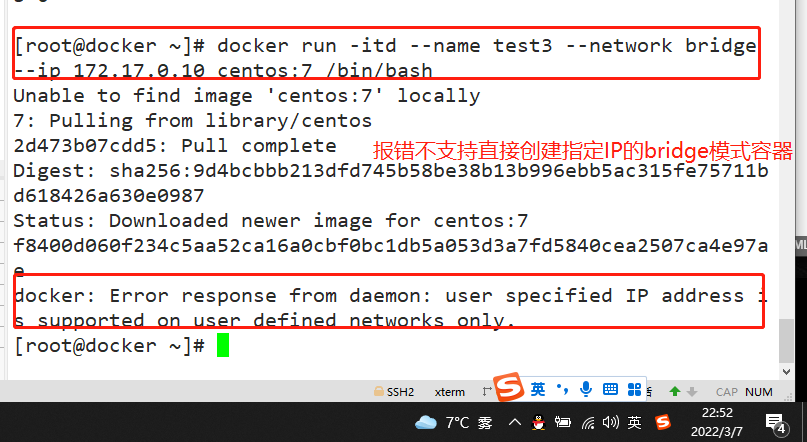
- Using the bridge mode directly cannot support the specified ip to run docker. For example, if you execute the following command, an error will be reported
docker run -itd --name test3 --network bridge --ip 172.17.0.10 centos:7 /bin/bash
- Create custom network
- You can customize the network first, and then run docker with the specified IP
docker network create --subnet=172.20.0.0/16 --opt "com.docker.network.bridge.name "="nanjing" mynetwork
docker1 For execution ifconfig -a Command, the network card name displayed if not used–opt Parameter specifies this name, then you are using ifconfig -a When using the command to view network information, you will see something similar br-110eb56a0b22 Such a name is obviously not easy to remember. #mynetwork is the name of the bridge network mode displayed when the docker network list command is executed.
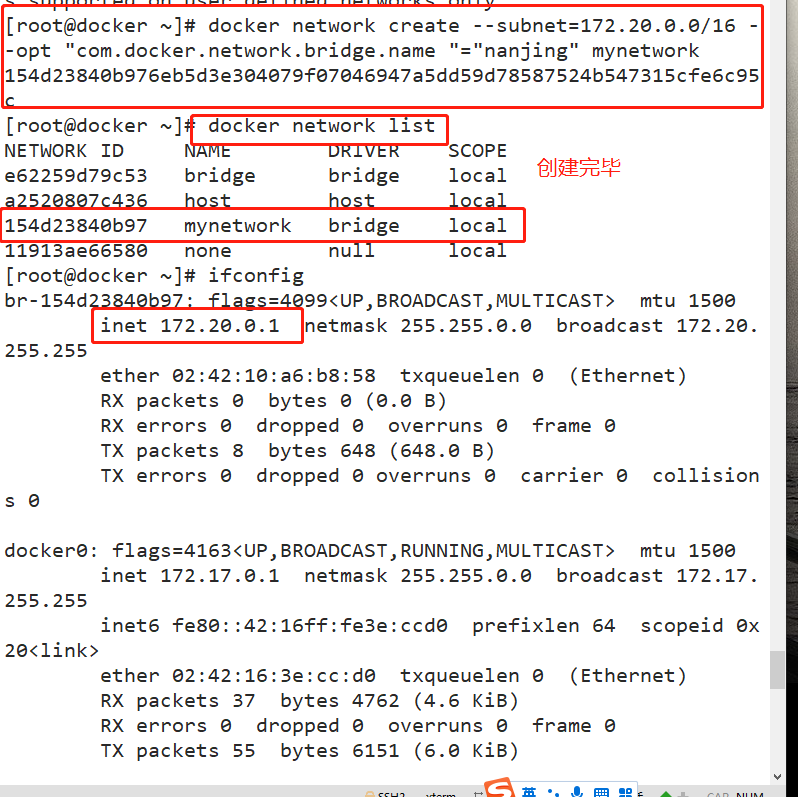
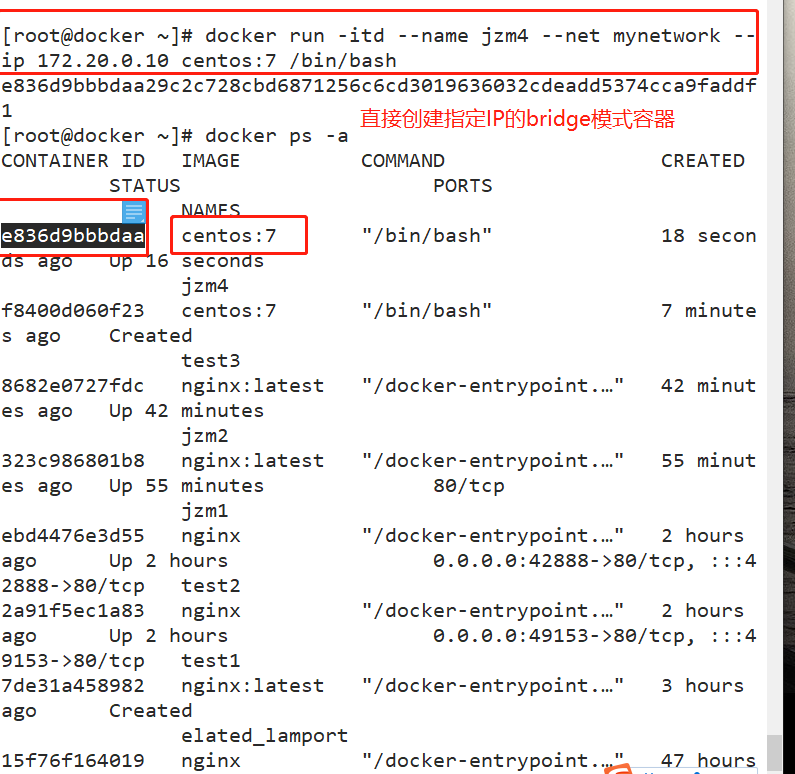
docker run -itd --name jzm4 --net mynetwork --ip 172.20.0.10 centos:7 /bin/bash docker exec -it e836d9bbbdaa bash ifconfig #This command requires net tools to be installed
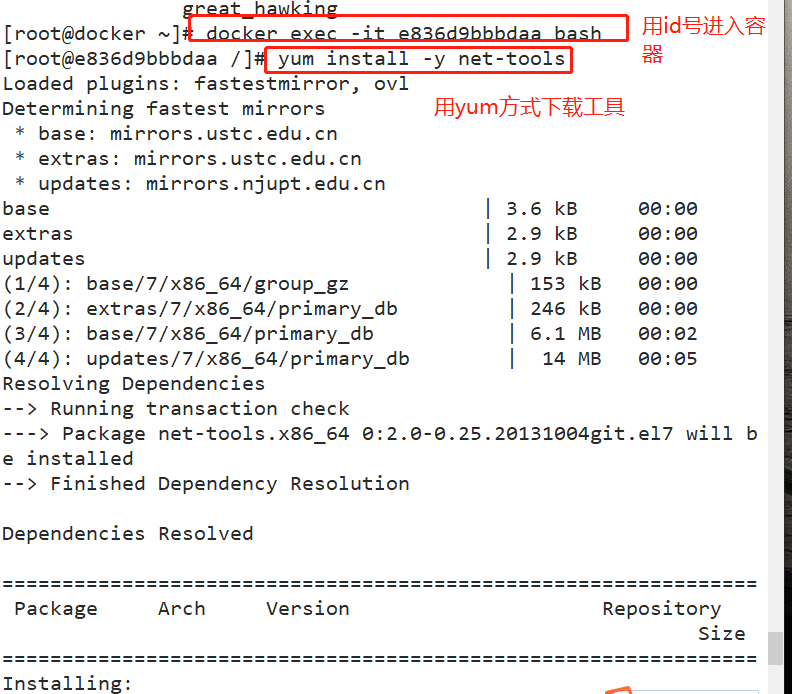
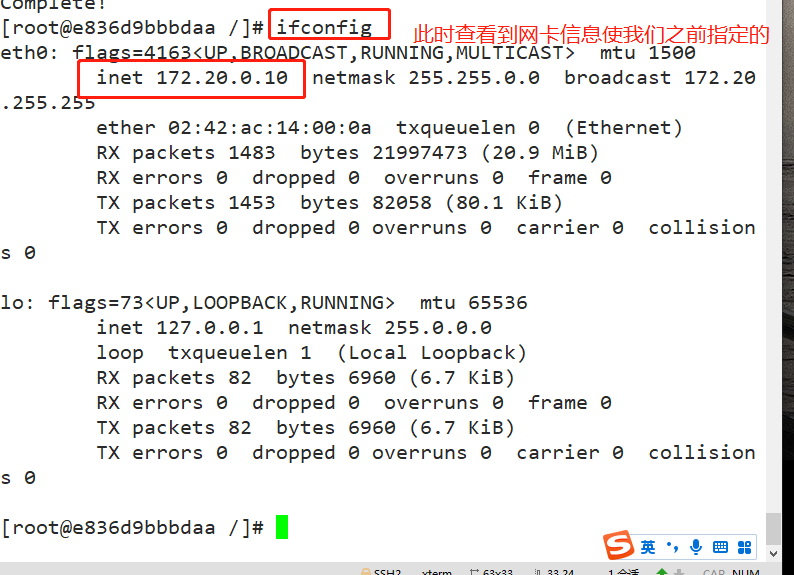
3, Resource control
1, Control of CPU resources
cgroups,Is a very powerful linux Kernel tools, he can not only be limited namespace Isolated resources, You can also set weights for resources, calculate usage, control the start and stop of processes, and so on. therefore cgroups ( Control groups) It realizes the quota and measurement of resources.
cgroups has four functions:
- Resource limit: you can limit the total amount of resources used by the task
- Priority allocation: by allocating the number of cpu time slices and the size of disk IO bandwidth, the task running priority is actually controlled
- Resource statistics: it can count the resource usage of the system, such as cpu duration, memory usage, etc
- Task control: cgroup can suspend and resume tasks
1. Set CPU usage cap
- Linux uses CFS (fully fair scheduler) to schedule the CPU usage of various processes. The default scheduling cycle of CFS is 100ms.
- We can set the scheduling cycle of each container process and how much CPU time each container can use in this cycle.
- Use – CPU period to set the scheduling cycle;
- Use – CPU quota to set the CPU time that the content container can use in each cycle. The two can be used together.
- The effective range of CFS cycle is 1ms1s, and the corresponding value range of – CPU period is 1000-1000000.
- The CPU quota of the container must not be less than 1ms, that is – the value of CPU quota must be > = 1000.
View CPU usage
docker run -itd --name jzm8 centos:7 /bin/bash docker ps -a CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES ec171594190c centos:7 "/bin/bash" 6 seconds ago Up 5 seconds jzm8 cd /sys/fs/cgroup/cpu/docker/2a91f5ec1a837056d07f85a49360a364e366289ef4d0318f36e082057f497059/ cat cpu.cfs_period_us cpu.cfs_quota_us 100000 -1 ---------------------------------------------- #cpu.cfs_period_us: the cycle allocated by the CPU (microseconds, so the file name is represented by us). The default is 100000. #cpu.cfs_quota_us: indicates the time (in microseconds) occupied by the control group. The default is - 1, indicating no limit -----------------------------------------------
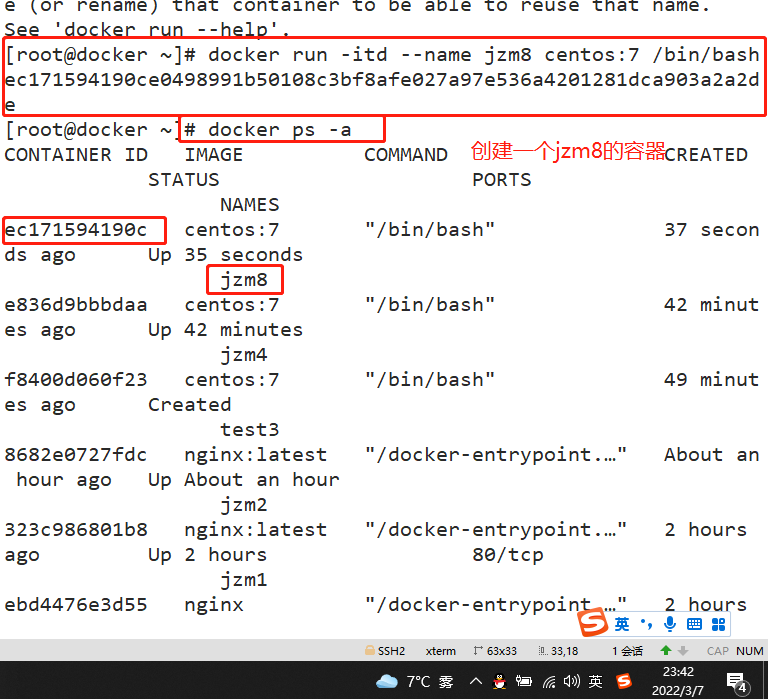
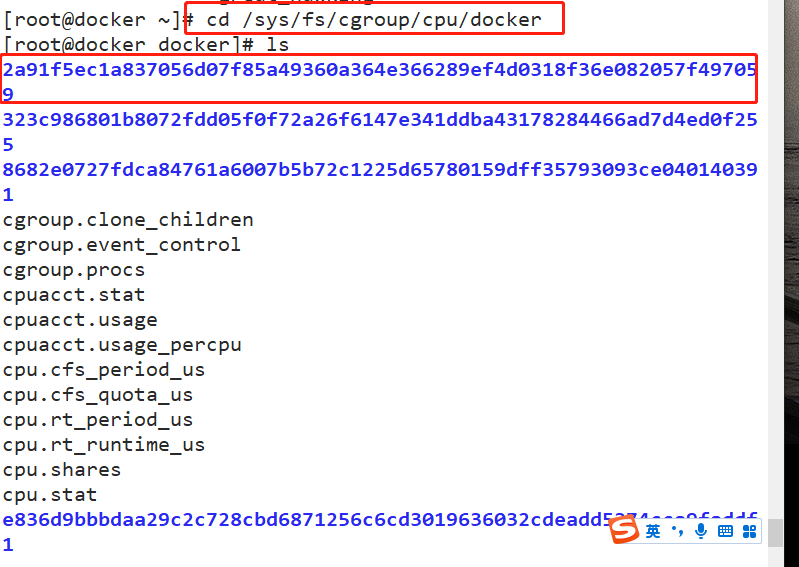
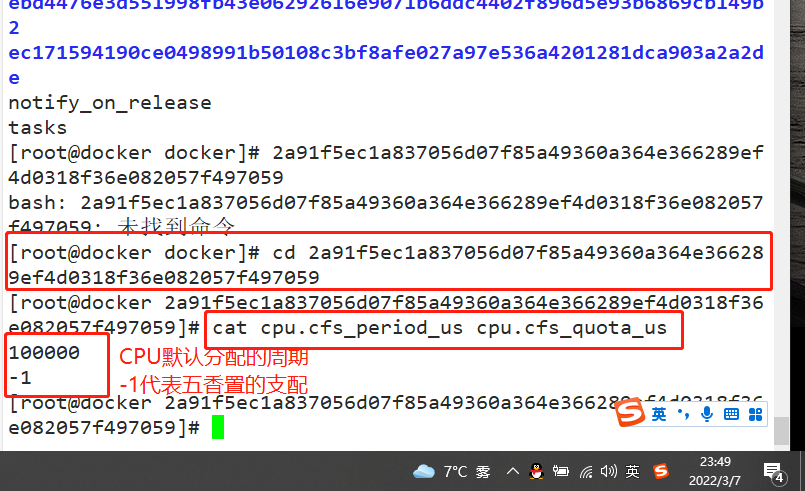
Test CPU usage
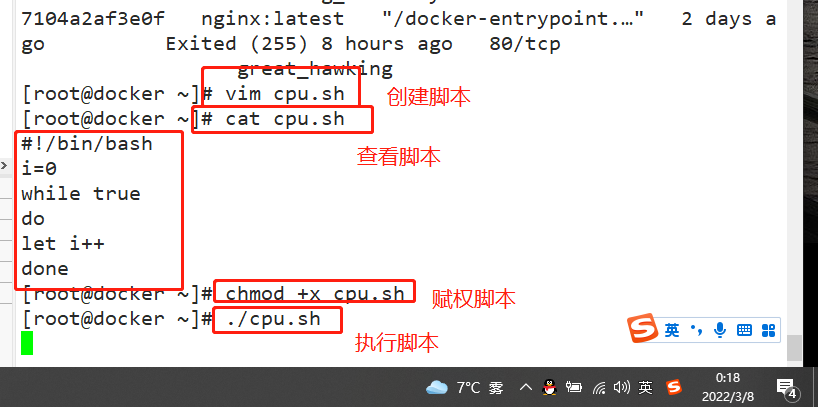
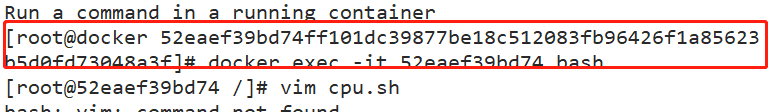
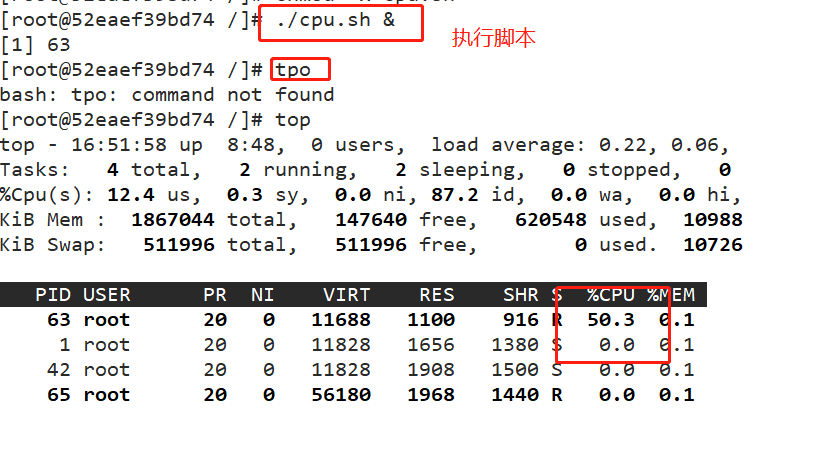
docker exec -it ec171594190c bash vi cpu.sh #!/bin/bash i=0 while true do let i++ done chmod +x cpu.sh ./cpu.sh & Used by another terminal top see
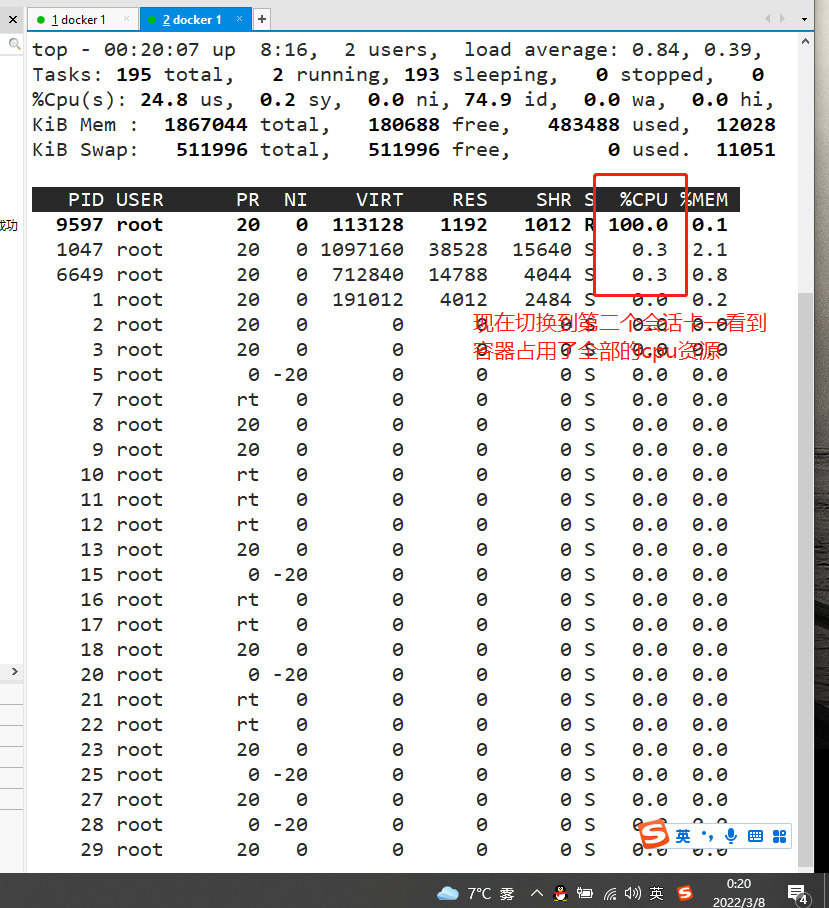
Set CPU usage
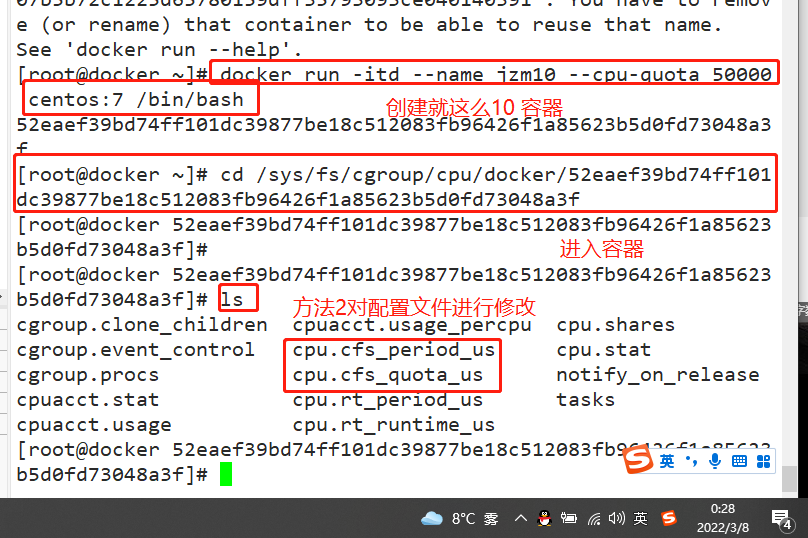
#Set the upper limit of 50% proportional allocation CPU usage time docker run -itd --name jzm10 --cpu-quota 50000 centos:7 /bin/bash #You can recreate a container and set limits perhaps cd /sys/fs/cgroup/cpu/docker/52eaef39bd74ff101dc39877be18c512083fb96426f1a85623b5d0fd73048a3f/ echo 50000 > cpu.cfs_quota_us #modify parameters cat cpu.cfs_quota_us cpu.cfs_period_us 50000 100000 docker exec -it 52eaef39bd74 bash ./cpu.sh Used by another terminal top see
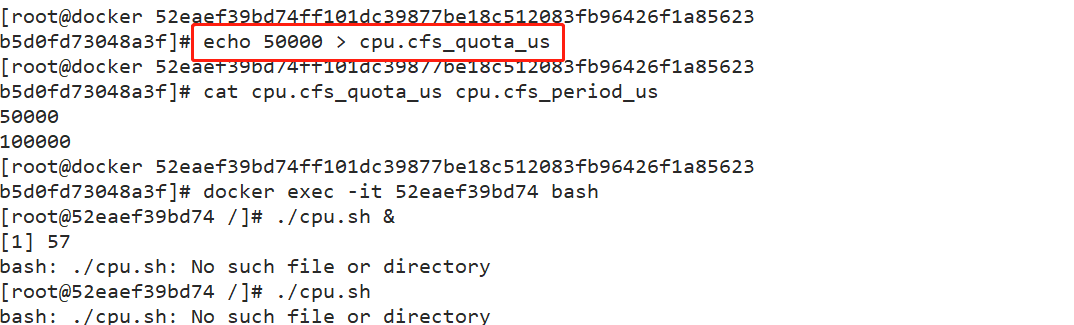
2. Set CPU resource occupancy ratio (only valid when multiple containers are set)
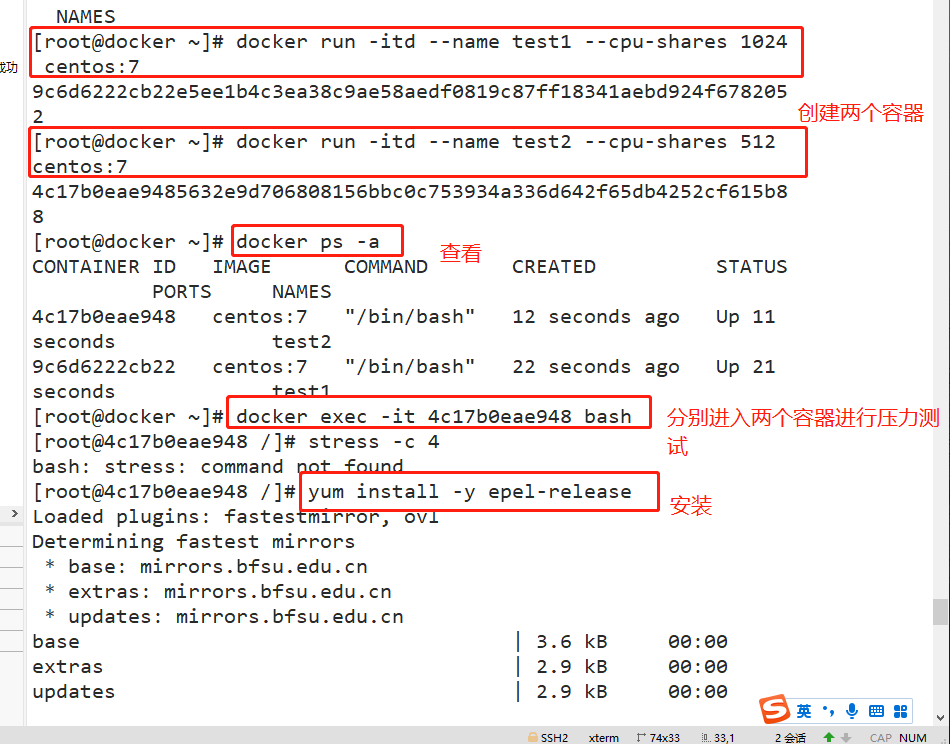
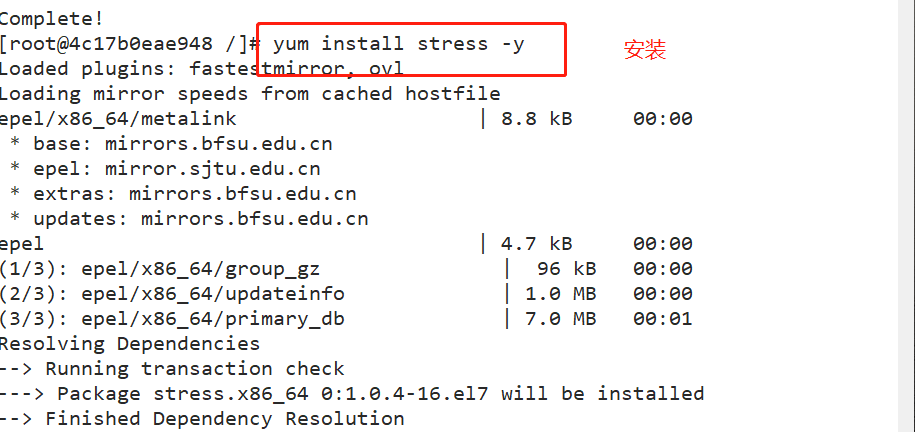
Docker adopt--cpu-shares appoint CPU Share, the default value is 1024, and the value is a multiple of 1024. Example: create two containers for test1 and test2, If there are only two containers, set the weight of the container so that test1 and test2 of CPU The proportion of resources is 1/3 And 2/3. docker run -itd --name test1 --cpu-shares 1024 centos:7 docker run -itd --name test2 --cpu-shares 512 centos:7 #Enter the container respectively for pressure test docker exec -it 9c6d6222cb22 bash yum install -y epel-release yum install stress -y stress -c 4 #Four processes are generated, and each process repeatedly calculates the square root of the random number #View the running status of the container (dynamic update) docker stats CONTAINER ID NAME CPU % MEM USAGE / LIMIT MEM % NET I/O BLOCK I/O PIDS 4c17b0eae948 test2 122.38% 177.7MiB / 3.686GiB 4.71% 30.4MB / 165kB 0B / 50.1MB 7 9c6d6222cb22 test1 275.43% 177.6MiB / 3.686GiB 4.71% 30.5MB / 211kB 0B / 50MB 7 #View container running status (dynamic update) docker stats
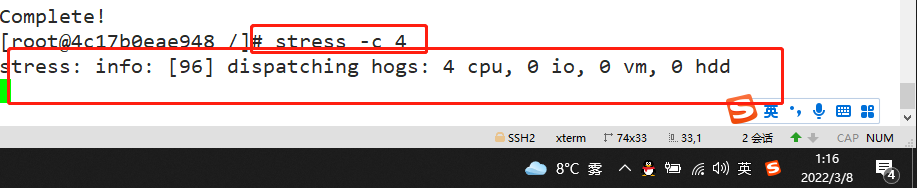
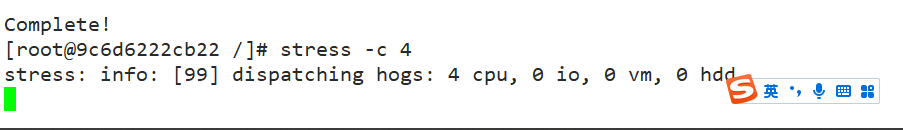
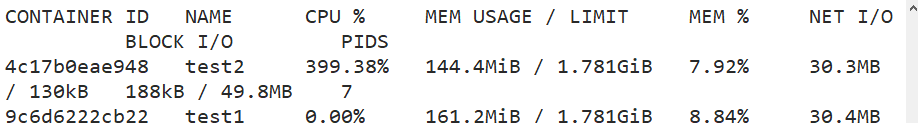
2, Restrictions on memory usage
#Creates a container for the specified physical memory -m(--memory=)Option is used to limit the maximum memory the container can use docker run -itd --name jzm1 -m 512m centos:7 /bin/bash docker stats #Creates a container that specifies physical memory and swap docker run -itd --name jzm2 -m 512m --memory-swap 1g centos:7 /bin/bash To emphasize,--memory-swap Yes, it must be with--memory Used together Normally,--memory-swap The value of contains the container's available memory and available memory swap therefore-m 300m --memory-swap=1g Means:The container can use 300 M Physical memory, and can use 700 M (1G - 300M)of swap If--memory-swap Set to 0 or not, the container can use swap Size-m Twice the value If--memory-swap Sum of values-m If the values are the same, the container cannot be used swap If--memory-Swap Value is-1,It indicates that the memory used by the container program is limited and can be used swap Unlimited space usage (how many hosts are there, swap How many containers can be used)
3, Limit on disk IO quota
Set restrictions
--device-read-bps: Limit the read speed on a device bps(Data quantity), the unit can be kb,mb(M)perhaps gb. Example: docker run -itd --name jzm1 --device-read-bps /dev/sda:1M centos:7 /bin/bash --device-write-bps: Limit write speed on a device bps(Data quantity), the unit can be kb,mb(M)perhaps gb. Example: docker run -itd --name jzm2 --device-write-bps /dev/sda:1mb centos:7 /bin/bash --device-read-iops: Restrict access to a device iops(Times) --device-write-iops: Restrict writes to a device iops(Times)
Create containers and limit write speed
docker run -itd --name jzm1 --device-write-bps /dev/sda:5mb centos:7 /bin/bash
Verify the write speed through dd
docker exec -it a2770dee54b5 bash #Enter container dd if=/dev/zero of=test.out bs=1M count=50 oflag=direct #Add oflag parameter to avoid file system cache
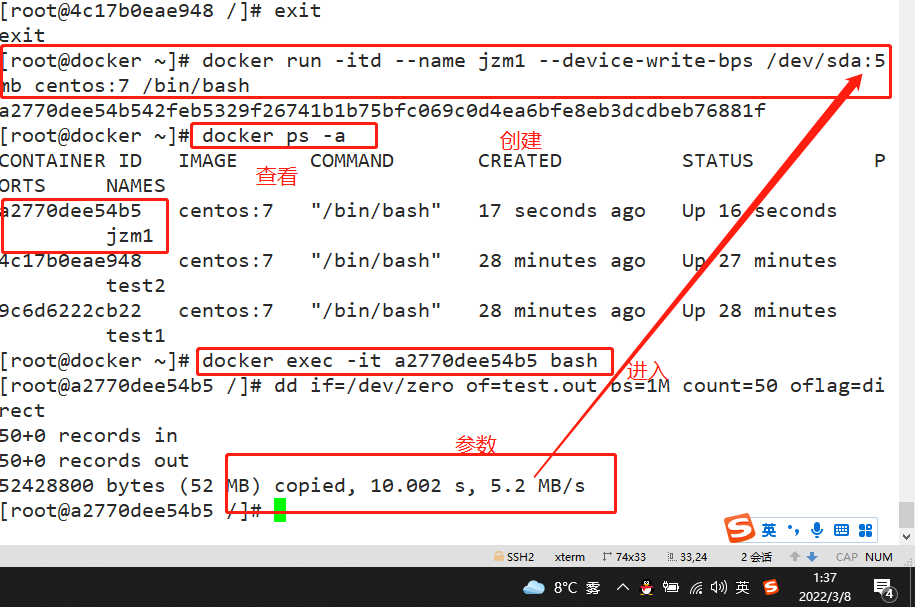
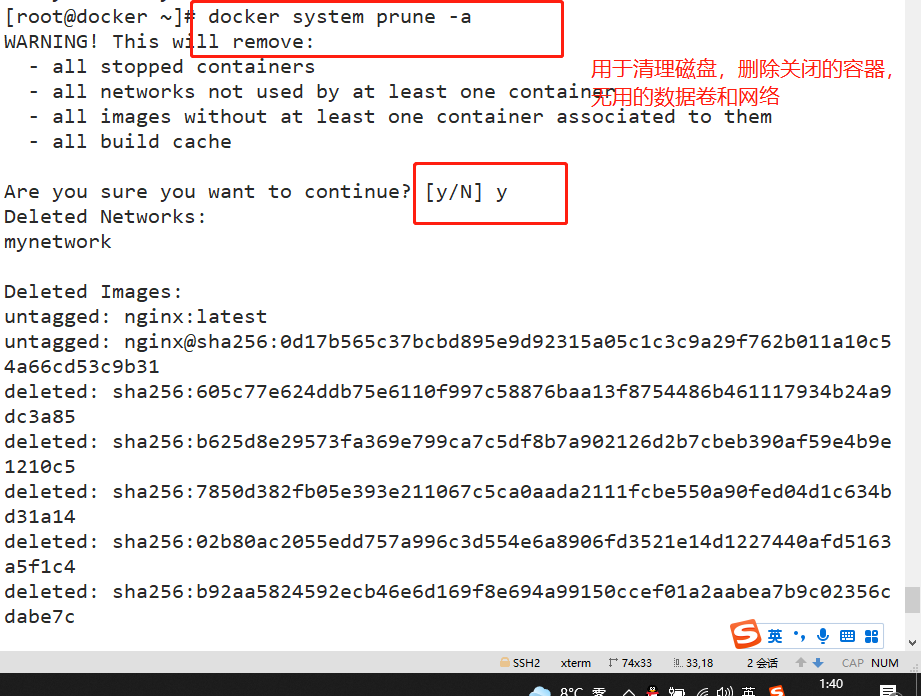
Clean up the disk space occupied by docker
docker system prune -a #It can be used to clean up disks and delete closed containers, useless data volumes and networks
- Tired Yami