https certificate
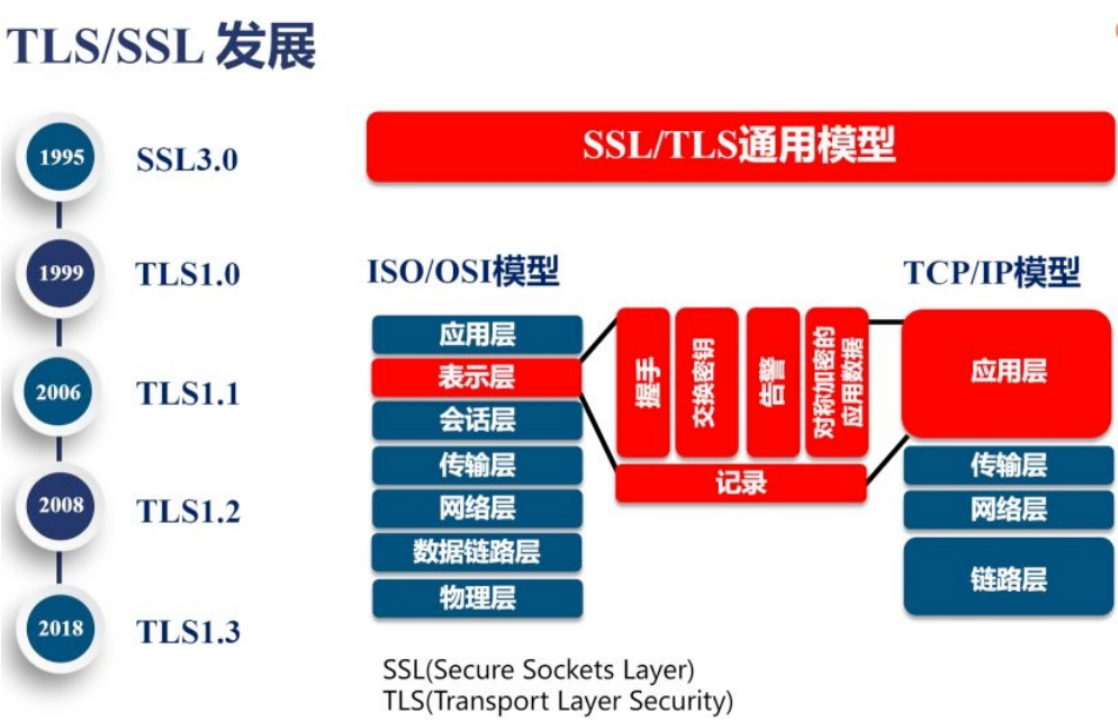
How to determine the identities of both parties in the process of data encryption and decryption?
At this time, there needs to be an authority to verify the identities of both parties, so this authority is the CA authority.
So how does CA issue certificates?
We first need to apply for a certificate, go to the registration authority for identity registration, and then the registration authority sends it to Ca through CSR. After passing the CA center, a pile of public keys and private keys will be generated. The public keys will be saved in the CA certificate chain. After we get the public key and private key certificates, we will deploy them on the WEB server
The simulated website has been tampered with
# Writing nginx configuration files on web01
[root@web01 conf.d]# vim zhuzhan.conf
server {
listen 80;
server_name www.zhuzhan.com;
location / {
root /zhuzhan;
index index.html;
}
}
# Create a site directory and edit the default page
[root@web01 conf.d]# mkdir /zhuzhan
[root@web01 conf.d]# vim /zhuzhan/index.html
<!DOCTYPE html>
<html lang="zh">
<head>
<meta charset="UTF-8">
<meta http-equiv="X-UA-Compatible" content="IE=edge">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<title>This website is about to be tampered with</title>
</head>
<body>
<h1>Zeng Laoshi main site</h1>
<img src="https://img11.51tietu.net/pic/2016-
071418/20160714181543xyu10ukncwf221991.jpg" alt="">
<p>This is Zeng Laoshi site. Zeng Laoshi all rights reserved</p>
</body>
</html>
# Hacker attack
server {
listen 80;
server_name www.zhuzhan.com;
location / {
proxy_pass http://172.16.1.7;
include /etc/nginx/proxy_params;
sub_filter '<title>This website is about to be tampered with</title>' '<title>The website has been tampered with
</title>';
sub_filter '<p>This is Zeng Laoshi site. Zeng Laoshi all rights reserved</p>' '<p>Not Zeng Laoshi. All rights reserved
</p>';
sub_filter '<img src="https://img11.51tietu.net/pic/2016-
071418/20160714181543xyu10ukncwf221991.jpg" a
lt="">' '<img src="https://blog.driverzeng.com/zenglaoshi/xingganheguan.gif">';
}
}
Single web Implementation certificate
Type of certificate
| Domain name type | Enterprise OV | Enhanced EV | |
| Greenly Address column | Small lock mark + https | Small lock mark + https | Small lock mark + enterprise name + https |
| General use Way | Personal sites and applications; ordinary https encryption requirements | E-commerce sites and applications; middle-sized and small Enterprise site | Large financial platform; Large enterprises and government Government agency site |
| Within audit Allow | Domain name ownership verification | Comprehensive enterprise authentication; domain name Ownership verification | The highest level of enterprise authentication; field Name ownership verification |
| When issued long | 10 minutes - 24 hours | 3-5 working days | 5-7 working days |
| Single application Please years | 1 year | 1-2 years | 1-2 years |
| Indemnity insurance Barrier gold | 0 | $1.25-1.75 million | $1.25-1.75 million |
Certificate selection
Protect a domain name www
Protect five domain names www images cdn test m
Wildcard domain name * xxxxx.com
https considerations
web certificate implementation
# 1. Check whether nginx supports ssl certificates [root@web01 conf.d]# nginx -V --with-http_ssl_module # 2. Create a directory of certificates [root@web01 ~]# mkdir /etc/nginx/ssl # 3. Enter the certificate directory [root@web01 ~]# cd /etc/nginx/ssl # 4. Generate certificate [root@web01 ssl]# openssl genrsa -idea -out server.key 2048 Generating RSA private key, 2048 bit long modulus ............+++ ..................+++ e is 65537 (0x10001) Enter pass phrase for server.key: Verifying - Enter pass phrase for server.key: # 5. Self signed certificate [root@web01 ssl]# openssl req -days 36500 -x509 -sha256 -nodes -newkey rsa:2048 - keyout server.key -out server.crt Generating a 2048 bit RSA private key ...................................................................................... .............................+++ .+++ writing new private key to 'server.key' ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- # Country name, up to 2 characters Country Name (2 letter code) [XX]:CN # Full name of province State or Province Name (full name) []:Shanghai # Full name of the city Locality Name (eg, city) [Default City]:Shanghai # Company name Organization Name (eg, company) [Default Company Ltd]:niubi # Company name Organizational Unit Name (eg, section) []:niu # Domain name to be protected by certificate Common Name (eg, your name or your server's hostname) []:blog.tjh.com # mail Email Address []:123@qq.com
Configure ssl certificate
server {
listen 443 ssl;
server_name blog.tjh.com;
root /code/wordpress;
ssl_certificate /etc/nginx/ssl/server.crt;
ssl_certificate_key /etc/nginx/ssl/server.key;
}
80 forced rotation 443
vim /etc/nginx/conf.d/blog.tjh.com.conf
server {
listen 80;
server_name blog.tjh.com;
# return 302 https://$server_name$request_uri;
rewrite (.*) https://$server_name$1 redirect;
}
Implementation of HTTPS in nginx cluster
Environmental preparation
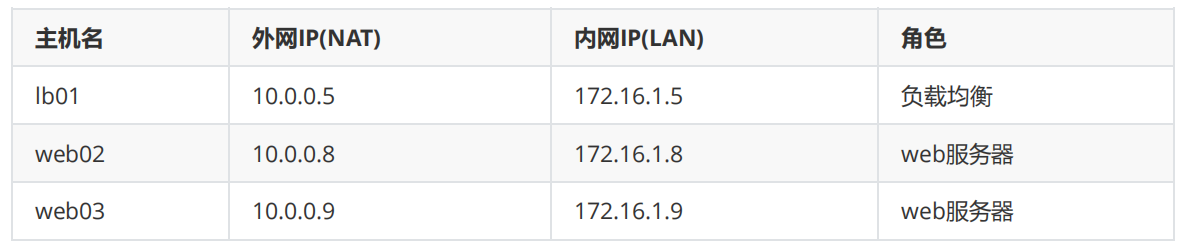
Deploy web
# web01
server {
listen 80;
server_name blog.tjh.com;
root /code/wordpress;
#ssl_certificate /etc/nginx/ssl/server.crt;
#ssl_certificate_key /etc/nginx/ssl/server.key;
location / {
index index.php index.html;
if ( -f $request_filename/index.html ){
rewrite (.*) $1/index.html break;
}
if ( -f $request_filename/index.php ){
rewrite (.*) $1/index.php;
}
if ( !-f $request_filename ){
rewrite (.*) /index.php;
}
if ($http_user_agent ~*
"Wget|ApacheBench|webBench|isouSpider|MJ12bot|YoudaoBot|Tomato|bingbot/2.0|compatible"
){
set $block_user_agent 1;
}
if ($block_user_agent = 1){
return 403;
}
}
location ~ \.php$ {
fastcgi_pass unix:/dev/shm/php71w.sock;
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
include /etc/nginx/fastcgi_params;
}
}
# web02
server {
listen 80;
server_name blog.tjh.com;
root /code/wordpress;
#ssl_certificate /etc/nginx/ssl/server.crt;
#ssl_certificate_key /etc/nginx/ssl/server.key;
location / {
index index.php index.html;
if ( -f $request_filename/index.html ){
rewrite (.*) $1/index.html break;
}
if ( -f $request_filename/index.php ){
rewrite (.*) $1/index.php;
}
if ( !-f $request_filename ){
rewrite (.*) /index.php;
}
if ($http_user_agent ~*
"Wget|ApacheBench|webBench|isouSpider|MJ12bot|YoudaoBot|Tomato|bingbot/2.0|compatible"
){
set $block_user_agent 1;
}
if ($block_user_agent = 1){
return 403;
}
}
location ~ \.php$ {
fastcgi_pass unix:/dev/shm/php71w.sock;
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
include /etc/nginx/fastcgi_params;
}
}
nginx -t
systemctl reload nginx
Deploy load balancing
1.Write configuration file
[root@lb01 ~]# vim /etc/nginx/conf.d/blog.conf
upstream blog_abc_com {
server 172.16.1.7;
server 172.16.1.8;
}
server {
listen 80;
server_name blog.abc.com;
rewrite (.*) https://$server_name$request_uri redirect;
}
server {
listen 443 ssl;
server_name blog.abc.com;
ssl_certificate /etc/nginx/ssl/server.crt;
ssl_certificate_key /etc/nginx/ssl/server.key;
location / {
proxy_pass http://blog_abc_com;
include /etc/nginx/proxy_params;
}
}
2. Create certificate storage directory
[root@lb01 ~]# mkdir /etc/nginx/ssl/
3.Enter certificate directory
[root@lb01 ~]# cd /etc/nginx/ssl
4.Generate certificate
[root@lb01 ssl]# openssl genrsa -idea -out server.key 2048
5.Self signed certificate
[root@web01 ssl]# openssl req -days 36500 -x509 -sha256 -nodes -newkey rsa:2048 -keyout server.key -out server.crt
6.visit blog.abc.comHTTPS leads to wordpress breaking
Reason: the front end uses port 443, the web uses port 80, and the PHP program uses port 80
Solution: let the PHP program know that the front end uses port 443
location ~ \.php$ {
fastcgi_pass unix:/dev/shm/php71w.sock;
# Tell PHP to go to port 443
fastcgi_param HTTPS on;
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
include /etc/nginx/fastcgi_params;
}
SSL optimization parameters
#After the ssl handshake is established, if the connection is disconnected, in the session_ If you connect again within the timeout time, you do not need to obtain the public key again to establish a handshake. You can take the previous connection ssl_session_cache shared:SSL:10m; #Timeout after ssl connection is disconnected ssl_session_timeout 1440m; #Configure cryptographic socket protocol ssl_ciphers ECDHE-RSA-AES128-GCM-SHA256:ECDHE:ECDH:AES:HIGH:!NULL:!aNULL:!MD5:!ADH:!RC4; #Use TLS version protocol ssl_protocols TLSv1 TLSv1.1 TLSv1.2; #nginx decides which protocols to use to communicate with the browser ssl_prefer_server_ciphers on;
blog configuration optimization
[root@lb01 conf.d]# cat blog.conf
upstream blog_abc_com {
server 172.16.1.7;
server 172.16.1.8;
}
# Prevent malicious parsing
server {
listen 80;
server_name _;
rewrite (.*) https://blog.abc.com redirect;
}
server {
listen 80;
server_name blog.abc.com;
rewrite (.*) https://$server_name$request_uri redirect;
}
server {
listen 443 ssl;
server_name blog.abc.com;
ssl_certificate /etc/nginx/ssl/server.crt;
ssl_certificate_key /etc/nginx/ssl/server.key;
#After the ssl handshake is established, if the connection is disconnected, in the session_ If you connect again within the timeout time, you do not need to obtain the public key again to establish a handshake. You can take the previous connection
ssl_session_cache shared:SSL:10m;
#Timeout after ssl connection is disconnected
ssl_session_timeout 1440m;
#Configure cryptographic socket protocol
ssl_ciphers ECDHE-RSA-AES128-GCM-SHA256:ECDHE:ECDH:AES:HIGH:!NULL:!aNULL:!MD5:!ADH:!RC4;
#Use TLS version protocol
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
#nginx decides which protocols to use to communicate with the browser
ssl_prefer_server_ciphers on;
location / {
proxy_pass http://blog_abc_com;
include /etc/nginx/proxy_params;
}
}