Basic principles of computer network and explanation of terms
Equivalent entity
Equivalent entities refer to entities in the same layer, that is, entities that interact with each other in the same layer of different subsystems.
Physical media related layer
Defines the physical sublayer at which ATM traffic can be transferred to a given physical medium at what actual speed
Link management
Link management is the operation of establishing, maintaining and releasing data link layer connections
Wide area network
Wan is a collection of computer operating systems that connect multiple computer systems far away from each other through communication lines according to network protocols to realize mutual communication between computers
Remote login
A process in which one's own computer temporarily becomes a remote computer terminal with the support of the network communication protocol Telnct
Telnet: the telnet protocol is TCP/IP protocol A member of the family, it is the standard protocol and main mode of Internet remote login service
Virtual communication
The communication between the two parties without direct contact is conducted according to certain rules (i.e. protocol) through the services provided by the entity related to the virtual communication entity
information network
For some needs, more than two units exchange information in a common way to form an interconnected system, that is, information network
IP address
Each host is assigned a 32-bit address as the identification of the host. It is unique and is the logical address identifying the host in the Internet layer
disk mirroring
Two disk drives are installed on the same channel to drive the original disk and secondary disk respectively. The data is written on these two disks at the same time. When the original disk fails, the secondary disk is still working normally to ensure the correctness of the data
Risks and threats of computer network system
Risk refers to the level at which the system may suffer losses; Threat refers to the human, material, event, idea and other factors that pose a threat to the loss of assets
Network architecture
Network architecture is a hierarchical structure, which is a collection of network layers and their protocols. Its essence is to organize a large number of various types of protocols reasonably and divide them logically according to the order of functions
Frequency division multiplexing
Frequency division multiplexing is to divide the available transmission frequency range into multiple fine frequency bands, and each fine frequency band is allocated to users as an independent channel to form a data transmission sub path
error control
Error control is a technology and method to find, detect and correct errors in the process of data communication, so as to limit the errors to the smallest possible range allowed by data transmission
10. 25 recommendations
10. Recommendation 25 is the interface standard between DTE and DCE in which the terminal operates in packet form on the public data network. The network formed by this interface is called the public message packet switching network
Hypertext
Hypertext is a text file in which some words, symbols or phrases play the role of "hot chain". When the mouse cursor moves to a hot chain and clicks the mouse, it will jump to another place or another file along this link
Computer wind collaterals
A system that connects multiple computer systems with different geographical locations and independent functions through communication system equipment and line system, and realizes resource sharing in the network with fully functional network software
Transparent transmission
In the data link, all transmitted data, no matter what kind of bits they are combined, should be able to be transmitted on the data link
Text compression
It adopts some coding technology to reduce the amount of information transmitted or stored to meet the needs of communication bandwidth
DDN network
It is a data transmission network that uses digital channel to transmit signals. It is a digital transmission network that uses digital channel to provide semi permanent connection circuit and mainly transmits data signals. The transmission media of DDN include optical cable, satellite channel and ordinary cable and twisted pair available at the user end
Network interconnection
Also known as network interconnection, it refers to connecting more than computer networks and connecting them with one or more communication processing equipment through certain methods to form a larger network system
communication services
It is the external expression of the communication function in the communication system. The control operation of the communication function is provided to the users of the communication system in the form of "service"
Web server
In a network system, some computers or devices provide services at the request of other computers to enable other computers to share system resources through it. Such computers or devices are called network servers.
FDDI
It is a physical layer and data link layer standard, which specifies the specifications of optical fiber media, optical transmitter and receiver, signal transmission rate and coding, media access protocol, distributed management protocol and allowed network topology.
MIB
The management information base is a conceptual database composed of management objects. Each management agent manages the local management objects in the MIB, and the management objects controlled by each management agent together constitute the management information base of the whole network.
Interactive television
It is to add a decoder to the TV and connect the cable TV network with a specific computer, so that the system has the function of two-way communication.
Virtual communication
Virtual communication: also known as logical communication. This communication is different from physical communication. There is no direct contact between the two sides of the communication. The communication is carried out according to certain rules (i.e. protocol) through the services provided by the entities related to the process virtual communication entity
Frame synchronization
Frame synchronization: it means that the receiver should accurately distinguish the start and end of frames from the received bit stream.
Pre allocated buffer
Pre allocated buffer: in the real virtual circuit service mode, one or more buffers are pre allocated to the nodes of the established virtual circuit path
LAN
LAN: it is a data communication system, which connects several independent devices in a moderate geographical range, and realizes the direct communication between independent devices with high data transmission rate through physical communication channel.
Hypertext (multiple occurrences)
Hypertext: a text file in which some words, symbols or phrases play the role of "hot chain". When displayed, their font or color changes, or are marked with a horizontal line to distinguish it from the general text.
FDM frequency division multiplexing
The available transmission frequency range is divided into multiple fine frequency bands, and the frequency band of each packet is allocated to users as an independent channel as a data transmission sub path.
Distributed path selection
Each user message processor IMP periodically exchanges accurate path selection information with each adjacent IMP.
Each IMP keeps a path table that can be retrieved by all other imps in the subnet. The path table in the IMP is continuously modified through the exchange of adjacent IMP information to reflect the changes of adjacent imps and find out the best path to the target node.
Transparent transmission
Transparent transmission means that in the data link layer, the transmitted data, no matter what kind of bits they are combined, should be able to be transmitted on the data link layer.
If the bit combination in the transmitted data is exactly the same as some control information, measures shall be taken to separate it from the control information. For the information in the same frame, the data shall also be separated from the control information contained in the frame.
bridge
The bridge works in the data link layer. It can interconnect address compatible LANs.
It uses MAC address and store and forward function as information frame exchange between LANs. Users of a LAN can access the resources of another LAN transparently through the bridge.
Electronic bulletin board
Electronic bulletin board BBS is an information source and message transmission system obtained by computer through remote access.
BBS can provide a variety of shared resources, information and online to a variety of users
error rate
This is an index to measure the transmission reliability of the system in the communication system. It defines the probability of binary symbols being transmitted incorrectly in the transmission system. From the statistical theory, when the transmitted digital sequence is infinitely long, it is equal to the ratio of the number of transmitted binary symbols to the total number of transmitted symbols.
disk mirroring
A pair of two disk drives are installed on the same channel to drive the original disk and the auxiliary disk respectively. The data is written on the two disks at the same time. The two disks work serially and alternately. When the original disk has a problem, the auxiliary disk still works normally, so as to ensure the correctness of the data.
communication protocol
A set of semantic and grammatical rules used to specify the operation of relevant functional units in the communication process
physical layer
The physical layer channel entities reasonably provide mechanical, electrical, functional and procedural means for the activation, maintenance and deactivation of the physical connection required for bit transmission through the intermediate system
Computer network security
The security of software, hardware and other resources shared by users in the network system, so as to prevent all kinds of resources from being damaged intentionally or unintentionally and from being illegally occupied.
Brief answer
What is the principle of hierarchy division when ISO develops OSI reference model?
1. Each node in the network has the same level 2. The same level of different nodes has the same function 3. Adjacent layers in the same node communicate through interfaces 4. Each layer can use the services provided by the lower layer and provide services to its upper layer 5. The peer layer of different nodes implements the protocol between peer layers through protocol
The basic functions of frame relay switching are briefly described.
1. Route incoming frames to the correct output port 2. Check the check sequence area of the frame to determine whether the frame contains an error code. If so, discard the frame 3. Check and determine whether its buffer is full. If it is full, the incoming frame is discarded until the congestion is cleared
This paper briefly describes the concept and characteristics of frame relay.
Frame relay is a fast packet switching technology X.25 Simplification and improvement of packet switching protocol. The characteristics of frame relay mainly include: 1. Efficiency 2. Economy 3. reliability 4. flexibility
This paper briefly describes the concept and classification of network server.
Concept: in a network system, a device that provides services and shared resources for other computers is called a server Classification: 1. Device server 2. Communication server 3. Management server 4. database server
Briefly describe the meaning of path selection and the basic rules that must be observed.
Meaning: path selection is to find the best path to the destination node on the transmission path according to certain principles and algorithms The following principles must be observed when selecting the path: 1. The time for data transmission should be as short as possible 2. In the process of data transmission, the load of each node should be balanced and the information flow should be balanced 3. The algorithm is simple, practical and realizable 4. The algorithm has strong adaptability
This paper briefly describes the basic composition of client / server system
From an application perspective, C/S The structural system is mainly composed of three parts: 1. Customer: This is an end-user interface device or application 2. Server: usually a high-grade microcomputer with a large amount of memory, stable and fast network transmission and complete network security measures 3. Connector: hardware connection and software link between client and server
Characteristics of packet switching
1. Nodes temporarily store groups instead of the entire data file 2. Packets are temporarily stored in the memory of the node, thus ensuring a high switching rate 3. Packet switching adopts the strategy of dynamic channel allocation, which greatly improves the utilization of communication lines
This paper briefly describes the five basic stages of data communication.
1. Establish communication line 2. Establish data transmission link 3. Transmission of communication control signals and data 4. After data transmission, both parties confirm the end of communication through control signal 5. One of the communication parties notifies the switch of the end of communication and cuts off the physical link channel
Briefly describe the main functions of modem
1. The digital pulse signal sent by the source is changed into an analog signal, and the analog signal sent by the channel is restored into a digital pulse signal 2. Ensure that the source and sink are synchronized 3. Improve the anti-interference ability of data transmission 4. Channel multiplexing
This paper briefly describes the main functions of Internet layer in TCP/IP protocol cluster
1. Process the packet sending request from the transport layer, and load the packet after receiving the request IP Datagram, fill in the header, select the path, and then send the packet to the appropriate network interface 2. Processing datagrams 3. Processing network control message protocol
Briefly describe the operation process of token access control
1. A logical ring is established to connect all sites to the physical media to generate a control token 2. Tokens are passed from one site to another along a logical ring 3. When the station waiting to send the message receives the token, the station sends the message using physical media; After sending the message, the site passes the control token to the next site
Try to compare the similarities and differences between C/S structure and special server structure.
C/S The structure is basically the same as the professional server structure in terms of hardware composition, network topology, communication connection, etc. The biggest difference between the two lies in: C/S In the structure. The ability of server to control and manage data has risen from file management to database management, and database service is C/S One of the most basic service types in
This paper briefly describes the similarities and differences between distributed computer system and computer network.
They are basically the same in computer hardware connection, system topology and communication control. They both have the functions of data communication and resource sharing. Their very important differences are: distributed computer system is supported by distributed computer operating system to process distributed database and work in parallel among computers, assist each other and complete a task together; The computer network realizes the resource sharing among interconnected computers with the support of network operating system. Each computer in the computer network usually works independently.
What is circuit switching? What are its characteristics?
Circuit switching is a direct switching mode, which is a physical link that directly forms information between multiple input lines and multiple output lines. Circuit switching has the following characteristics: 1. Call loss: when the exchange encounters busy line or fault in the establishment stage, the user cannot communicate; 2. Users with different rates and codes cannot exchange; 3. The information delay is short and fixed; 4. It is suitable for continuous and mass data transmission
What is path selection? What are the principles of path selection?
Path selection is to find the best path to the target node on the data transmission path according to certain principles and algorithms. Principles of route selection: 1. The time for data transmission shall be as short as possible; 2. In data transmission, the load of each node should be balanced and the information flow should be uniform; 3. The selected path selection algorithm should be simple and realizable; 4. The algorithm has strong adaptability
Briefly describe the process of data communication (multiple occurrences)
1. Phase I: establish communication lines. The user will tell the switch the address information of the other party to be communicated, and the switch will query the address terminal. If the other party agrees to communicate, the switch will establish the physical channel for communication between both parties 2. The second stage: establish data transmission link. The communication parties shall establish synchronous contact to make the equipment of both parties in the correct sending and receiving state, and the communication parties shall check each other's addresses. 3. The third stage: transmitting communication control signals and transmitting data. 4. Stage 4: data transmission ends. Both parties confirm the end of the communication through the communication control information. 5. The fifth stage: one of the communication parties notifies the switch that the physical link channel can be cut off after the communication is completed
Briefly describe the difference between concentrator and multiplexer
1. Multiplexing is transparent, while concentrators are opaque. 2. The concentrator transmits in the unit of message, while the multiplexer transmits in the unit of character. 3. Concentrator is a microcomputer. It has storage capacity and programming capacity, and can be equipped with external equipment. Multiplexing does not have programming capacity and no external equipment 4. From the perspective of application configuration, multiplexing is used in pairs, while concentrator is used alone. 5. The function of concentrator is much stronger than that of multiplexer, which is similar to communication controller.
This paper briefly describes the function and classification of network bridge
1. Match the rate of different ports. 2. It can detect and filter frames 3. It can improve the network bandwidth and expand the geographical scope of the network. Classification of bridges: Network bridges are divided into three categories: internal bridge, external bridge and remote bridge
Network bridges are divided into three categories: internal bridge, external bridge and remote bridge
Five types of SNMP management operations
1. GET Operation: used to extract pending network management information; 2. GET-NEXT Operation: provide powerful management information extraction capability by traversing activities. 3. SET Operation: used to control management information. 4. GET Response Processing: for response GET,GET-NEXT and SET Operation and return their operation results. 5. TRAP(Trap) operation: used to report important events.
Briefly describe the characteristics of remote login
1. Provides a general access service 2. Allows a program running on a remote computer to receive input from the local computer user, respond to the input, and then send the output back to the local computer user. 3. Enable users with small personal computers to rely on remote login to complete operations they cannot complete on their own computers. (There are five points altogether, two points are missing)
Characteristics of packet switching
1. Nodes temporarily store groups instead of the entire data file. 2. Packets are temporarily stored in the memory of the node, not in the external memory of the node; 3. Packet switching has high switching rate; 4. Packet switching adopts the strategy of dynamic channel allocation; 5. Packet switching greatly improves the utilization of communication lines.
Briefly describe the characteristics of ATM
1. ATM The network does not perform any functions of the data link layer. It hands over the error control and flow control to the user ATM The end station does it instead of giving it to the switch, which further simplifies the network function. 2. ATM It can provide satisfactory services for any type of business, regardless of business speed, burst size, real-time and quality requirements 3. ATM It has great flexibility and can make maximum use of network resources; Working ratio of switching node X.25 The work of nodes in packet switching networks is much simpler. 4. ATM The connector oriented working mode is adopted to further improve the data processing speed, reduce the delay, and make the network processing very simple. 5. Complete business integration is realized; It is the only way to realize the integrated digital service network technology.
The composition of network software system is briefly described
1. Protocol software 2. Online service software 3. communication software 4. Management software 5. Network operating system 6. Device driver software 7. Network application software
In the ISO network management standard system, what functional domains are the open system network management functions divided into?
1. fault management 2. configuration management 3. Performance management 4. security management 5. Bookkeeping management
Briefly describe the composition of the e-mail system
1. Message memory 2. Message transfer agent 3. user agent
Briefly describe the characteristics of data communication
1. Data communication is the communication between physical computers and computers and between people and computers 2. The communication process between computers needs to define strict communication protocols or standards, and has high requirements for the reliability of data transmission. 3. The data transmission efficiency of data communication is high and the amount of information is sudden. 4. The "users" of data communication use a variety of computers, terminals and other equipment, which are very different in communication rate, coding format, synchronization mode and communication procedures 5. The average information length and delay of communication services of different users and applications in data communication system vary greatly.
What are the functions and main functions of network layer traffic control?
Ensure that the communication subnet provides a path that can make the information flow smoothly between nodes. Main functions: 1. Prevent the decrease of network data throughput and increase of delay caused by network overload. 2. Avoid deadlocks. 3. Allocate resources fairly among users
Briefly describe the functions of network operating system
1. Coordinate users and reasonably allocate and schedule system resources 2. Provide network communication services 3. Control user access, set access restrictions for users, ensure system security and provide reliable confidentiality. 4. Manage files. In the system, there are tens of thousands of files, which are usually stored in a special equipment in the system. It is a very important task to manage files quickly, accurately, safely and reliably. 5. System management, track network activities, establish and modify network services, and manage network application environment
This paper briefly describes the advantages of NMIS in information management
1. establish NMIS The required capital investment and high efficiency 2. Short network construction time 3. It has good universality and applicability 4. Have stronger, more timely and more accurate processing ability for data 5. It increases the overall safety and reliability of the system
This paper briefly describes the characteristics and principles of multi-level data information encryption
1. Every visit follows the rule of absolute confidentiality 2. Illegal modification between data is not allowed 3. Effective verification of access correctness Principles to be followed: 1. Users can only read user information data at the same level or lower than their level 2. Users can only write user information data at the same level or higher than their level
This paper briefly describes the working process and main characteristics of Ethernet network using CSMA / CD technology
CSMA/CD Refers to "multiple access"/Media access control mode for conflict detection. use CSMA/CD Technical Ethernet Working process of network; Before each node uses the bus to send data, first listen to whether there is data signal transmission on the bus; If the node is ready to send data frames and the bus is idle, it can send them. At the same time of sending, conflict detection is carried out to prevent multiple nodes from sending data at the same time. In case of conflict, the node stops sending data and randomly delays retransmission until the data transmission is completed. CSMA/CD The main characteristics of access methods are; The technical method is simple, easy to implement, light load and small delay, but when the communication load is heavy, the network throughput is small and the transmission delay increases
This paper briefly describes the seven layer structure and main functions of ISO / OSI reference model
1. Physical layer: use physical media to provide physical connection for data link layer, realize binary data transmission, and describe line type, transmission rate, signal level and other parameters 2. Data link layer: Based on the physical layer, establish data link connection between nodes in the network, and specify the format of transmission unit frame, error control method and flow control method, etc 3. Network layer: select the most appropriate path for packets through the communication subnet through routing algorithm, mainly including routing, congestion control and network interconnection. 4. Transport layer: provide end-to-end services for user processes and transmit data. 5. Session layer: organize the communication between two session processes and manage the exchange of data. 6. Presentation layer: a representation that handles the exchange of information between two communication systems. 7. Application layer: responsible for application management and execution of applications to meet the needs of users.
Briefly describe the advantages of storage switching over line switching
Multiple messages can share communication channels, so as to improve the utilization of communication lines. It can dynamically select the communication path of the message, smooth the traffic, and the system efficiency is high. The nodes in the communication subnet have error checking and error correction processing, which reduces transmission errors and has high system reliability. The communication rate can be dynamically converted
Try to explain the role of routers, gateways and bridges from the perspective of OSI reference model
Router can be used to connect multiple networks and has routing function. It belongs to the equipment of network layer. Gateway has the function of protocol conversion, and its function includes cover OSI The multiple layers of the reference model are divided into application gateway and transmission gateway. Bridge is a mixture of bridge and router. It has the functions of bridge and router. The bridge router can be configured at both the network protocol level and the routing protocol level
Briefly describe Telnet and remote login (multiple occurrences)
Telent It is a communication protocol developed for network system, which can make the local computer temporarily become a remote computer terminal. The protocol allows the user to establish a similar connection with the server on the remote computer on the local computer, and then send the string input on the local computer directly to the remote computer for execution. The user can use the corresponding resources developed by the remote computer in real time. Remote login refers to the communication protocol through the network Telnet Support is the reason why the local computer has temporarily become a remote computer terminal. Remote login service is an extension of login mechanism on ordinary time-sharing computer system.
Telnet: the telnet protocol is TCP/IP protocol A member of the family, it is the standard protocol and main mode of Internet remote login service
Please write down the three sharing modes of communication channel and their characteristics.
1. There are three sharing modes of communication channel: fixed allocation channel, random allocation channel and queued allocation channel. 2. Characteristics of fixed allocation channel: a physical communication channel is divided into multiple logical subchannels. There are two ways to divide logical channels: time and space. 3. Characteristics of random channel allocation: it also divides a physical communication channel into multiple logical subchannels, but each subchannel is no longer fixedly allocated to each pair of users. Each pair of users must apply for communication, and release the use right of the occupied channel after the communication. 4. Characteristics of queued channel allocation: sub channels are no longer divided, and users do not have to apply. The data sent by the user is divided into data units of a certain length, and then sent to the queue buffer queue of the network node. The system carries out communication services according to the principle of first come, first serve.
Please write down three common error control methods and their characteristics.
1. There are three common error control methods: automatic request retransmission, forward error correction and feedback verification 2. Automatic request retransmission feature: it can only detect that the error code is among those received codes, but it can not determine the exact location of the error code, so it can be applied ARQ The system is required to have bidirectional channels 3. Forward error correction features: the receiver can accurately determine the position of the error code, which can be used in the application FEC No reverse channel is required and there is no retransmission delay problem, so it has strong real-time performance, but the error correction equipment is more complex than the error detection equipment. 4. Feedback detection features: the method, principle and equipment are relatively simple, but the system needs to provide two-way channel. Because each information code is transmitted at least twice, the transmission efficiency is low
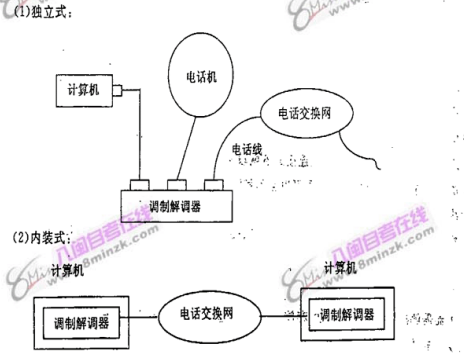
What kinds of modems are there according to how they are connected to the computer? And draw its connection.
What functions does the server provide in a client / server architecture system?
On client/In the server structure system, the server provides the following functions: 1. Establish process and network service address 2. Listen for customer calls 3. Processing customer requests 4. Give the response results to the user 5. Release the connection to the client
What precautions can be taken to ensure the security of the e-mail system?
1. Make security an integral part of your e-mail implementation plan 2. Budget the necessary security hardware and software 3. Safety education for end users 4. Prevent someone from using some defect of the operating system to invade the system 5. Realize the monitoring of the system 6. Establish a slogan order mechanism 7. Establish a call system for incoming calls 8. Encrypt e-mail data 9. Computer virus prevention 10. Protect computer infrastructure