Routing control
BGP route control includes controlling the release and reception of routes.
BGP routing control is generally realized through routing policy, that is, specific routes are matched through the routing matching tool, and the release and reception of routes are controlled through the routing policy tool
- Route matching tools: ACL (Access Control List), IP Prefix List, AS_Path Filter, Community Filter, etc
- Routing policy tools: filter policy and route policy
regular expression
Regular expression is a formula that matches strings according to a certain template, which is composed of ordinary characters (such as A-Z) and special characters. (it is not much different from the programmed regular expression, and the application scenario is simpler than the programming.)
| . | Matches any single character, including spaces | 0.0 matches 0X0 |
| ^ | Matches the position at the beginning of the line, that is, the beginning of a string | ^10. Match 10 x.x.x |
| $ | Matches the position at the end of the line, that is, the end of a string | 1 $matches x.x.x.1 |
| _ | Underscore to match any separator | _ 10. Match (10, {10, space 10, etc.) 10_ Match 10), 10}, 10 spaces, etc |
| | | Pipeline character, logical or. For example, x|y matches X or y | 100 | 200 matches 100 or 200 |
| \ | Escape character, used to mark the next character (special character or ordinary character) as ordinary character | \*Match* |
| * | Matches the previous subregular expression 0 or more times | 10 * match 1, 10, 100, 1000 | (10) * match empty, 10, 1010, 101010 |
| + | Matches the previous subregular expression 1 or more times | 10 + match 10, 100, 1000 | (10) + match 10, 1010, 101010 |
| ? | Matches the previous sub regular expression 0 or 1 times | 10? Match 1 or 10 | (10) ? match empty or 10 |
| [xyz] | Matches any character contained in the regular expression | [123] match 2 in 255 |
| [^xyz] | Matches characters not contained in the regular expression | [^ 123] matches any character other than 123 |
| [a-z] | Matches any character within the range specified by the regular expression | [0-9] matches all numbers between 0 and 9 |
| [^a-z] | Matches any character outside the range specified by the regular expression | [^ 0-9] matches all non numeric characters |
practice
^a. $: matches a string that starts with the character a and ends with any single character, such as a0, a! etc.
^100_: Match strings starting from 100, such as 100, 100 200, 100 300, 400, etc
^100 $: only match 100
100 $|400 $: matches strings ending with 100 or 400, such as 100, 1400, 300, 400, etc
^\(65000 \) $: match only (65000)
abc*d: match the c character 0 or more times, such as: abd, abcd, abcd, abcccd, abcccdxxx
abc+d: match the c character one or more times, such as abcd, abcd, abcccd, abcccdxxx
abc?d: Match c characters 0 or 1 times, such as abd, abcd, abcdxx
a(bc)?d: Match (BC) characters 0 or 1 times, such as ad, abcd, xxxabcdxxx
[abcd]: match any character in abcd, that is, any character in a, b, c and d, such as ax, xb
[a-c 1-2] $: matches strings ending with characters a, b, C, 1 and 2, such as a, a1, 62, xb
[^ act] $: matches strings that do not end with a, c, t, such as ax, d
[123]. [7-9] match 1x7, 2, 8
Route matching tool: AS_Path Filter
AS_Path Filter is the as in BGP_ The path attribute is used as the filter for matching conditions, and the as carried by BGP route is used_ The path list filters routes.
When you do not want to receive routes from some AS, you can use AS_Path Filter filters the routes carrying these AS numbers to reject some routes.
Regular expressions can be used to match the AS Path of the route
For example, 103 is included in the matching AS Path
AS_PATH: 103 102 101
String: 103 ﹐ 102 ﹐ 101
Regular expression: ^ 103, ^ 103_ etc.
\\establish AS_Path Filter.
[Huawei] ip as-path-filter { as-path-filter-number | as-path-filter-name }{ deny | permit } regular-expression
AS_Path Filter Use regular expressions to define matching rules.
be careful: AS_Path Filter The default behavior is deny.
\\application AS_Path Filter.
[Huawei-bgp-af-ipv4] peer { group-name | ipv4-address | ipv6-address } as-path-filter { as-path-filter-number | as-path-filter-name } { import | export }
stay BGP In the address family view, pair BGP When applying a routing policy based on routing information AS_Path Filter Filter out unqualified routing information.
stay Route-Policy Under view, create a AS_Path Filter Matching rules for.
[Huawei-route-policy] if-match as-path-filter { as-path-filter-number | as-path-filter-name }
Route matching tool: Community Filter
The Community Filter is used in conjunction with the Community attribute, which can be used when it is inconvenient to use IP Prefix List and AS_Path Filter reduces the difficulty of routing management.
There are two types of community attribute filters:
Basic Community Filter. Match the Community number or recognized Community attribute.
Advanced Community Filter. Use regular expressions to match community numbers.
\\In the routing policy, set the of the route Community Property value.
[Huawei-route-policy] apply community { community-number | aa:nn | internet | no-advertise | no-export | no-export-subconfed } [ additive ]
Publish community properties to peers (groups).
[Huawei-bgp-af-ipv4] peer { group-name | ipv4-address | ipv6-address } advertise-community
By default, BGP Do not publish community properties to any peers (groups).
\\Create basic Community Filter.
[Huawei] ip community-filter { basic comm-filter-name | basic-comm-filter-num } { permit | deny } [ community-number | aa:nn | internet | no-export-subconfed | no-advertise | no-export ]
basic Community Filter Number range: 1~99. In basic Community Filter Only community number or well-known community attribute can be specified in.
\\Create advanced Community Filter.
[Huawei] ip community-filter { advanced comm-filter-name | adv-comm-filter-num } { permit | deny } regular-expression
senior Community Filter Number range: 100~199. In advanced Community Filter You can specify a regular expression as a match condition in.
\\application Community Filter.
[Huawei-route-policy] if-match community-filter { basic-comm-filter-num [ whole-match ] | adv-comm-filter-num }
[Huawei-route-policy] if-match community-filter comm-filter-name [ whole-match ]
stay Route-Policy Under view, create a Community Filter Matching rules for.
Advanced features ORF
If the device wants to receive only the routes it needs, but the peer device cannot maintain different exit policies for each device connected to it. At this time, you can configure BGP prefix based ORF (Outbound Route Filters) to meet the needs of devices at both ends.
- The prefix based ORF capability of BGP can send the prefix based entry policy configured by the local device to the BGP neighbor through the route refresh message. BGP neighbors construct exit policies according to these policies (in the refresh message) and filter the route when sending the route.
- This not only avoids the local device from receiving a large number of useless routes, reduces the CPU utilization of the local device, but also effectively reduces the configuration of BGP neighbors and the occupation of link bandwidth.
\\Configure peer (Group) based IP Routing filtering policy for address prefix list.
[Huawei-bgp-af-ipv4] peer { group-name | ipv4-address } ip-prefix ip-prefix-name { import | export }
\\Enable BGP Peers (groups) are based on address prefixes ORF Function.
[Huawei-bgp] peer { group-name | ipv4-address } capability-advertise orf [ non-standard-compatible ] ip-prefix { both | receive | send } [ standard-match ]
be careful: ORF The function requires both ends of the peer to be turned on at the same time.
BGP peer group (simplified configuration command)
A Peer Group is a collection of peers with some of the same policies. When a peer is added to a Peer Group, it will get the same configuration as its Peer Group. When the configuration of a Peer Group changes, the configuration of members in the group will also change accordingly.
In large BGP networks, there are many peers, many of which have the same policy. Some commands will be reused during configuration. The configuration can be simplified by using peer groups.
\\Create a peer group.
[Huawei-bgp] group group-name [ external | internal ]
stay BGP View BGP-VPN example IPv4 Address family view BGP-VPN example IPv6 Create a peer group in the address family view.
\\(Optional) configure for the specified peer group AS number.
[Huawei-bgp] peer group-name as-number { as-number-plain | as-number-dot }
to configure EBGP Peer group AS number. about IBGP Peer group, AS be entitled as IBGP Local AS number.
\\Add peers to a peer group.
[Huawei-bgp] peer { ipv4-address | ipv6-address } group group-name
\\Specify send BGP The source interface of the message and specifies the source address used when initiating the connection.
[Huawei-bgp] peer group-name connect-interface interface-type interface-number [ ipv4-source-address ]
BGP security
There are two common BGP attacks:
- Establish illegal BGP neighbor relationship, announce illegal routing entries and interfere with the normal routing table.
- A large number of illegal BGP messages are sent, and the router sends them to the CPU after receiving them, resulting in an increase in CPU utilization
BGP uses authentication and GTSM (Generalized TTL Security Mechanism) to ensure the interaction security between BGP peers.
BGP certification
BGP authentication is divided into MD5 authentication and Keychain authentication. Authenticating the BGP peer relationship can prevent the establishment of illegal BGP neighbors
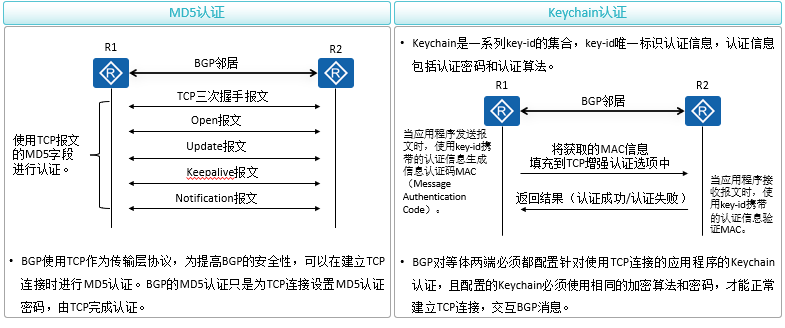
to configure BGP Peer is establishing TCP On connection BGP Message progress MD5 authentication.
[Huawei-bgp] peer { group-name | ipv4-address | ipv6-address } password { cipher cipher-password | simple simple-password }
to configure BGP Peer is establishing TCP When connecting Keychain authentication.
[Huawei-bgp] peer { group-name | ipv4-address | ipv6-address } keychain keychain-name
GTSM of BGP
The GTSM function of BGP detects whether the TTL (time to live) value in the IP message header is within a preset specific range, and discards the messages that do not meet the TTL value range, so as to prevent the network attacker from simulating the "legitimate" BGP message to attack the device.
to configure BGP Peer is establishing TCP On connection BGP Message progress MD5 authentication.
[Huawei-bgp] peer { group-name | ipv4-address | ipv6-address } password { cipher cipher-password | simple simple-password }
to configure BGP Peer is establishing TCP When connecting Keychain authentication.
[Huawei-bgp] peer { group-name | ipv4-address | ipv6-address } keychain keychain-name
4-byte AS number
With the expansion of network scale, the assignable AS number is on the verge of depletion.
At present, the AS number range used on the network is 1 to 65535 (2 bytes). It is necessary to expand the AS number range to 1 to 4294967295 (4 bytes), and BGP devices that support 4-byte AS numbers can be compatible with BGP devices that only support 2-byte AS numbers.
Route Reflector
In order to ensure the connectivity between IBGP peers, it is necessary to establish a full connection relationship between IBGP peers. Assuming that there are N devices in an AS, the number of IBGP connections established is n(n-1)/2. When the number of devices is large, the device configuration will be very complex, and the consumption of network resources and CPU resources will be large after configuration. Using routing reflectors between IBGP peers can solve the above problems.
Routing reflector related roles
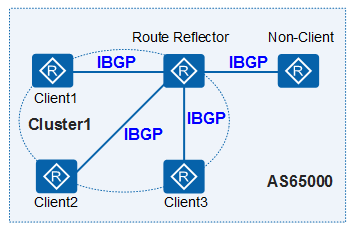
- Route Reflector RR (Route Reflector): allows the routes learned from IBGP peers to be reflected to BGP devices of other IBGP peers, similar to DR in OSPF network.
- Client: IBGP device that forms a reflective neighbor relationship with RR. Within AS, the client only needs to connect directly with RR.
- Non client: IBGP device that is neither RR nor client. A full connection relationship must still be established between non clients and RRs within the AS, AS well AS between all non clients.
- Originator: the device that initiates routing within the AS. The Originator_ID property is used to prevent routing loops in the cluster.
- Cluster: a collection of routing reflectors and their clients. The Cluster_List property is used to prevent routing loops between clusters.
Reflector rule (II)
- Routes learned from non clients are published to all clients.
- Routes learned from clients are published to all non clients and clients (except the client that initiated this route).
- Routes learned from EBGP peers are published to all non clients and clients.
Experiment 1
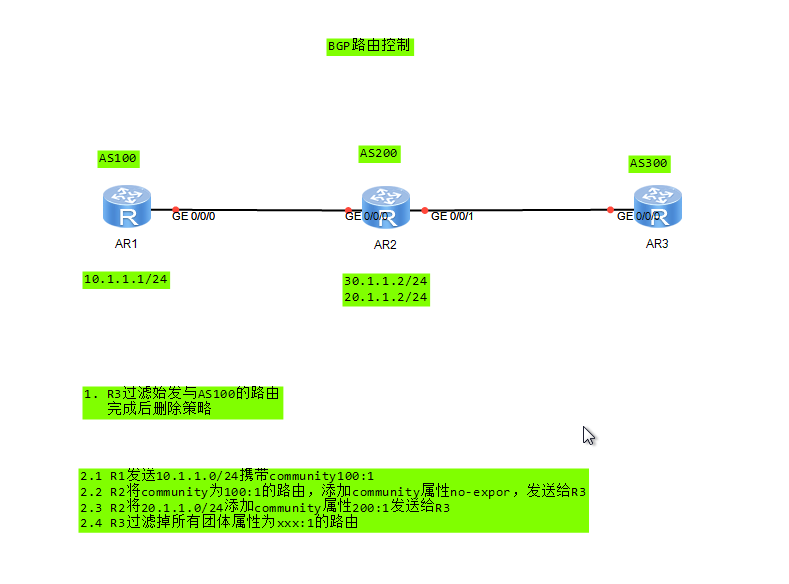
1. R3 Filter origination and AS100 Routing Delete policy when finished R3: ip as-path-filter 100 deny _100$ ip as-path-filter 100 permit .* bgp 300 ipv4-family unicast peer 23.0.0.2 as-path-filter 100 import
2.1 R1 Send 10.1.1.0/24 carry community100:1 R1: ip ip-prefix to2 index 10 permit 10.1.1.0 24 route-policy to2 permit node 10 if-match ip-prefix to2 apply community 100:1 route-policy to2 permit node 1000 bgp 100 ipv4-family unicast peer 12.0.0.2 route-policy to2 export peer 12.0.0.2 advertise-community
2.2 R2 take community Is 100:1 Routing, adding community attribute no-expor,Send to R3 R2: ip community-filter 1 permit 100:1 route-policy to3 permit node 10 if-match community-filter 1 apply community no-export additive route-policy to3 permit node 1000 bgp 200 ipv4-family unicast peer 23.0.0.3 route-policy to3 export peer 23.0.0.3 advertise-community
2.3 R2 Will 20.1.1.0/24 add to community Property 200:1 Send to R3 R2: ip ip-prefix to3 index 10 permit 20.1.1.0 24 route-policy to3 permit node 20 if-match ip-prefix to3 apply community 200:1
2.4 R3 Filter out all group attributes as xxx:1 Routing R3: ip community-filter 100 permit .*:1$ route-policy d1 deny node 10 if-match community-filter 100 route-policy d1 permit node 100 bgp 300 ipv4-family unicast peer 23.0.0.2 route-policy d1 import
Experiment 2
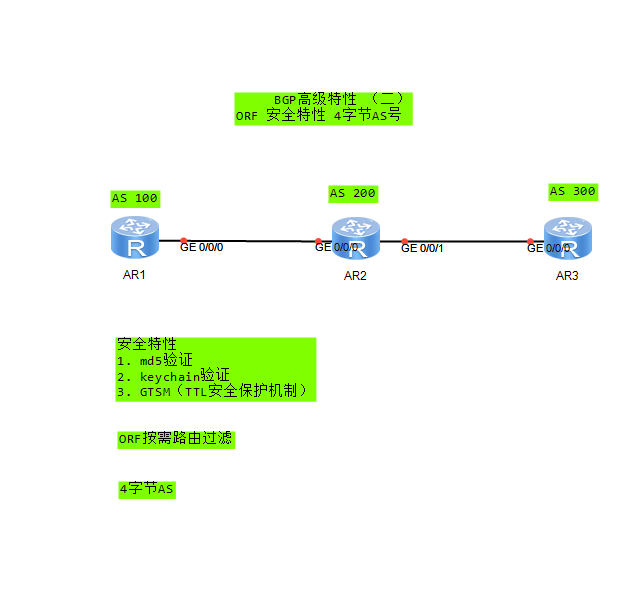
Safety characteristics 1. md5 verification [R1-bgp]peer 12.0.0.2 password simple 123 [R2-bgp]peer 12.0.0.1 password cipher 123 Neighbor dual engines need to use the same password 2. keychain verification keychain 1 mode periodic daily key-id 1 key-string cipher 123 send-time daily 00:00 to 11:59 receive-time daily 00:00 to 11:59 key-id 2 key-string cipher 321 send-time daily 12:00 to 23:59 receive-time daily 12:00 to 23:59 Neighbor double hair key-id and key-string Need same 3. GTSM(TTL Security protection mechanism bgp 100 peer 12.0.0.2 valid-ttl-hops 1 be careful: Enable gtsm After, ttl The value automatically changes to 255 In configuration hops Is effective TTL Value, the formula is:[255-hops+1,255] Namely: hops=1 Time effective ttl Interval time[255,255]
ORF On demand routing filtering R1: ip ip-prefix 1 permit 0.0.0.0 32 peer 12.0.0.2 ip-prefix 1 import peer 12.0.0.2 capability-advertise orf ip-prefix send R1 Configure the input policy and send it to R2 R2: peer 12.0.0.1 capability-advertise orf ip-prefix receive R2 receive R1 And automatically construct its own output strategy dis bgp peer 12.0.0.1 orf ip-prefix see R2 Received ORF strategy
4 byte AS R3: bgp 30 peer 23.0.0.2 as-number 200 undo peer 23.0.0.2 capability-advertise 4-byte-as R2: bgp 2.2 peer 23.0.0.3 as-number 300 peer 23.0.0.3 fake-as 200 \\Forge your own AS The number is 200 R2 Send to R3 There will be two routing updates as attribute 1. as-path 4 byte AS No. is replaced by 23456 2. as4-path Still keep the real 4 bytes AS number as-notation plain \\BGP 4 byte AS The display format of the number is integer undo as-notation plain \\BGP 4 byte AS The display format of the number is dotted By default, BGP 4 The display format of bytes is dotted, i.e x.y