Download Caddy
caddy official website download address https://caddyserver.com/download . You can also directly Click here Download the Linux amd 64 version. The latest version is 2.4.6
If you need to apply for a pan domain name certificate, you need to check the plug-in of the corresponding dns provider, such as cloudflare
Note: cloudflare is no longer supported cf, .ga, .gq, .ml, . tk suffix domain names use api to manage dns, that is, domain names with these suffixes cannot apply for Pan domain name certificates through cloudflare.
After downloading, rename it caddy and copy it to / usr/local/bin.
Profile Caddyfile
Create a new Caddyfile in any directory. The recommended location is / etc/caddy/Caddyfile
Enter the following to indicate that you will www.mydomain.com CF forwards it to localhost:16325, and automatically applies for ssl certificate through let's encrypt. The application mailbox is my@qq.com. If tls is enabled, http will be redirected to https by default
www.mydomain.cf { reverse_proxy localhost:16325 tls my@qq.com }
If http and https access are enabled at the same time, then
www.mydomain.cf:80 www.mydomain.cf:443{
reverse_proxy localhost:16325
tls my@qq.com
}
Reverse proxy is generally used for back-end sites. Front-end sites can be static sites directly. If docker runs, reverse proxy can also be used
The following is the static site configuration. Open https and the site root directory is / www/vue
www.mydomain.cf {
tls my@qq.com
root * /www/vue
file_server
}
Start caddy
Run the following command to make caddy run in the background. Where / etc/caddy/Caddyfile is the path where the configuration file caddyfile is located, - a dapter caddyfile indicates that the specified configuration file adapter is in caddyfile format, the default is json, and caddyfile can also be translated into json
For example, caddy adapt -- config / etc / caddy / caddyfile > / etc / caddy / file json is to translate caddy file into json and output it, and then specify the config parameter of caddy start as json file.
caddy start --config /etc/caddy/Caddyfile --adapter caddyfile
caddy start is started in the background, but the log will be output on the current console. Closing the current console will continue to run
caddy run is started by the foreground, and the current console shutdown process will also be closed
The two parameters are consistent
The certificate directory is in $XDG_DATA_HOME/certificates/acme-v02.api.letsencrypt.org-directory,$XDG_ DATA_ The corresponding relationship of home in different systems is as follows
| OS | Data directory path |
|---|---|
| Linux, BSD | $HOME/.local/share/caddy |
| Windows | %AppData%\Caddy |
| macOS | $HOME/Library/Application Support/Caddy |
| Plan 9 | $HOME/lib/caddy |
| Android | $HOME/caddy (or /sdcard/caddy) |
In other words, it is ~ /. Under linux local/share/caddy/certificates/acme-v02.api.letsencrypt.org-directory.
Modify data storage directory [optional]
The ssl certificate can be stored in another path by modifying the data store directory
Caddyfile adds global configuration storage. As shown below, the data directory will be modified to / etc/ssl/caddy, so that the path where the certificate is located will become / etc/ssl/caddy / certificates / acme-v02 api. letsencrypt. org-directory.
However, it is necessary to ensure that / etc/ssl/caddy exists and that the current user has permissions to read, write and modify, such as sudo chmod 747 /etc/ssl/caddy -R
{ storage file_system { root /etc/ssl/caddy } }www.mydomain.cf { reverse_proxy localhost:16325 tls my@qq.com }
Add to systemd run
New file / usr / lib / SYSTEMd / system / caddy Service, as follows Remember to change my in User=my to a user name with permission.
[Unit]
Description=Caddy HTTP/2 web server
After=network-online.target
Wants=network-online.target systemd-networkd-wait-online.service[Service]
User=my
Restart=on-abnormalExecStart=/usr/local/bin/caddy run --config=/etc/caddy/Caddyfile --adapter=caddyfile
ExecReload=/bin/kill -USR1 $MAINPID
; Use graceful shutdown with a reasonable timeout
KillMode=mixed
KillSignal=SIGQUIT
TimeoutStopSec=5s
ProtectSystem=full
[Install]
WantedBy=multi-user.target
Then execute
systemctl enable caddy.service
systemctl start caddy.service
systemctl status caddy.service
Application and use of Pan domain name certificate
The universal domain name certificate can only be verified through dns records, so you need to configure the dns provider information
For cf, .ga, .gq, .ml, . tk suffix domain names basically bid farewell to the automatic pan domain name certificate. cloudflare does not allow dns to be modified through api calls, and such domain names are not allowed to be filed in China.
1. Install the dns module of the corresponding domain name provider. Alibaba cloud and Tencent cloud are commonly used in China, and cloudflare, Microsoft and Google clouddns are used abroad
You can check the corresponding module when downloading caddy. If it is not checked, it doesn't matter. You can download it from the command line
cloudflare
cadd add-package github.com/caddy-dns/cloudflare
Alibaba cloud
cadd add-package github.com/caddy-dns/alidns
Tencent cloud
cadd add-package github.com/caddy-dns/dnspod
Modify caddyfile after installation. The module configurations of different dns providers are slightly different
cloudflare
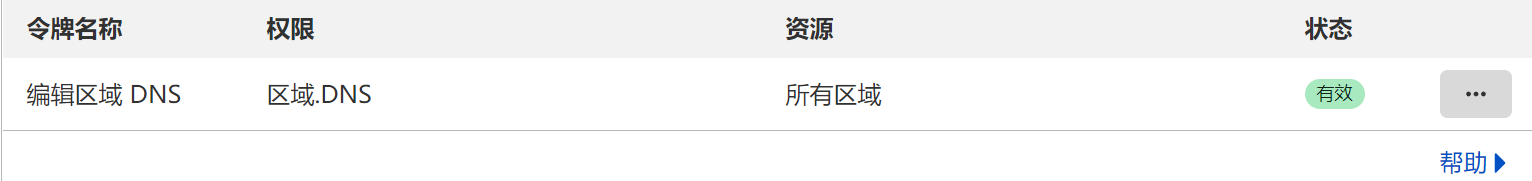
Add cloudflare_ Replace the key with your own key from here Just create a dns api token
*.my.com {
tls cloudflare cloudflare_apikey
}
Alibaba cloud
key_id and key_secret comes from the accesskey created on the console here It can be created. Region is the region to which the account belongs. It can be left blank. It defaults to zh Hangzhou
*.my.com {
tls alidns {
access_key_id key_id
access_key_secret key_secret
region_id region
}
Tencent cloud
What dnspod needs is api token , composed of ID and token, separated by English commas here There are instructions on how to create a token If the account id is 3245 and the token is sf3fwr234, the auth is complete_ The token is {3245,sf3fwr234
*.my.com {
tls alidns {
auth_token token
}
Use of Pan domain name certificate
The default directory configuration is my
*.my.com { tls cloudflare cloudflare_apikey } www.my.com { proxy localhost:5000 tls /home/my/.local/share/caddy/certificates/acme-v02.api.letsencrypt.org-directory/wildcard_.my.com/wildcard_.my.com.crt /home/my/.local/share/caddy/certificates/acme-v02.api.letsencrypt.org-directory/wildcard_.my.com/wildcard_.my.com.key }
Modify the configuration after the data directory is / etc/ssl/caddy
{ storage file_system { root /etc/ssl/caddy } }*.my.com { tls cloudflare cloudflare_apikey }www.mydomain.cf { reverse_proxy localhost:5000 tls /etc/ssl/caddy/certificates/acme-v02.api.letsencrypt.org-directory/wildcard_.my.com/wildcard_.my.com.crt /etc/ssl/caddy/certificates/acme-v02.api.letsencrypt.org-directory/wildcard_.my.com/wildcard_.my.com.key
}